5 Ways Threat Intelligence Drives SOC ROI: Board-Ready Cases for CISOs
When CISOs ask for budget, they are rarely competing against “no security.” They are competing against growth initiatives, product launches, and cost optimization.
Technical jargon and security metrics often fall flat here. To win the conversation, threat intelligence cannot be framed as more data for analysts. It must be positioned as a business enabler that reduces measurable risk, protects revenue, and accelerates decision-making.
Here are the board-ready cases that connect threat intelligence investments directly to business objectives.
1. Protecting Revenue and Avoiding Financial Loss
Boards understand one number very well: the cost of a breach. What they often underestimate is how much of that cost comes from late detection.
Reactive security means discovering threats after damage has already begun. By then, costs multiply across downtime, incident response, legal exposure, regulatory fines, and reputational damage.
Threat intelligence changes the equation.
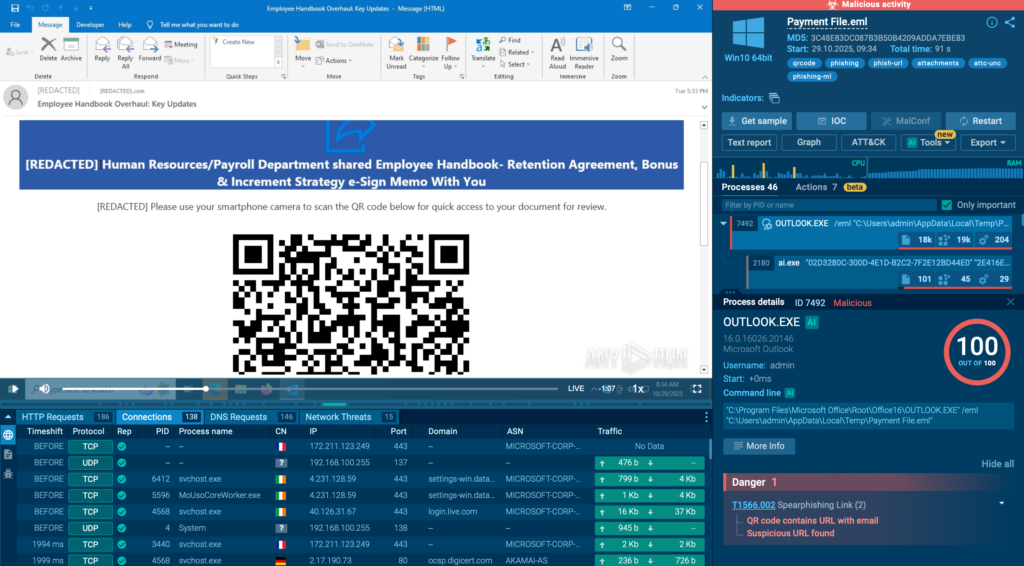
ANY.RUN’s Threat Intelligence Feeds deliver high-fidelity indicators sourced from interactive sandbox analyses of live malware samples and targeted attacks. This expands threat coverage, reduces the likelihood of successful breaches, and directly lowers potential financial impact — turning threat intelligence into a clear ROI driver.
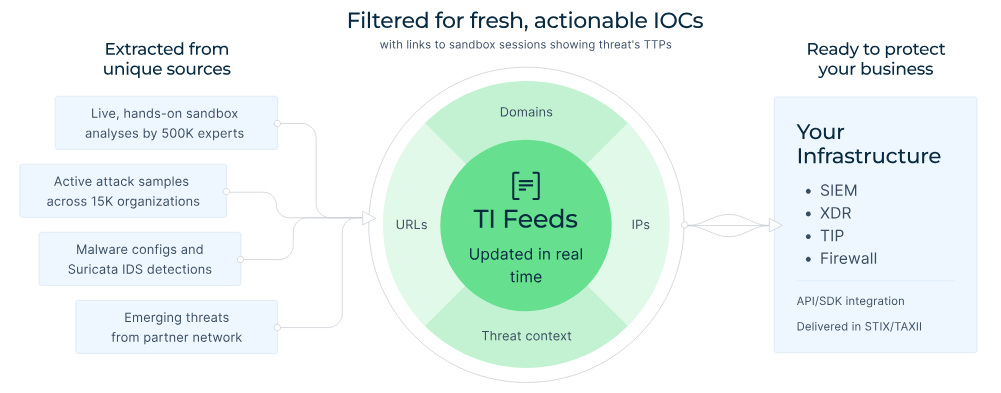
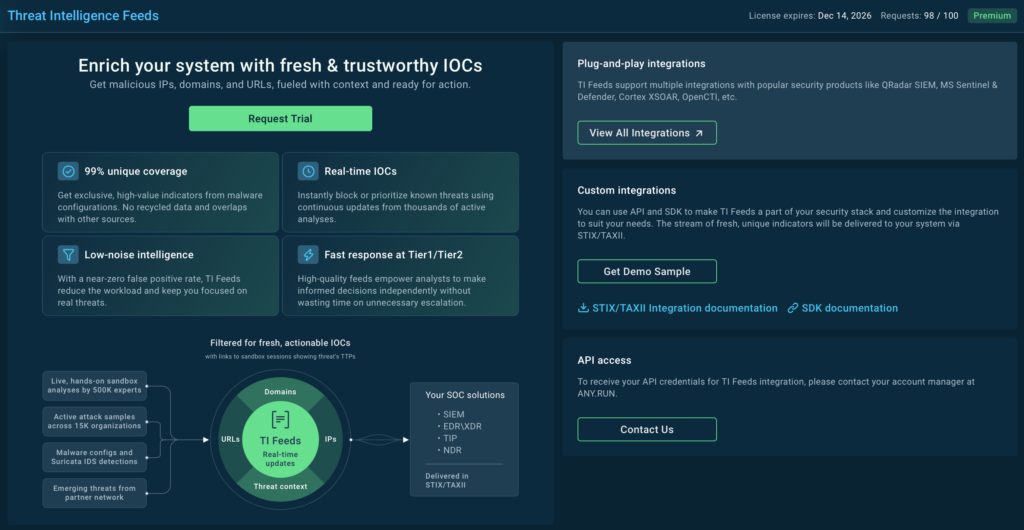
TI Feeds: features and data sources
Threat Intelligence Lookup is another decision-enabling service from ANY.RUN. It is an on-demand searchable database that provides instant access to detailed threat reports, behavioral insights, direct links to sandbox sessions, and contextual connections between IOCs and active campaigns, enabling rapid enrichment during investigations. Instead of asking “What could happen?”, security leaders can answer “What is actively targeting organizations like ours right now?”
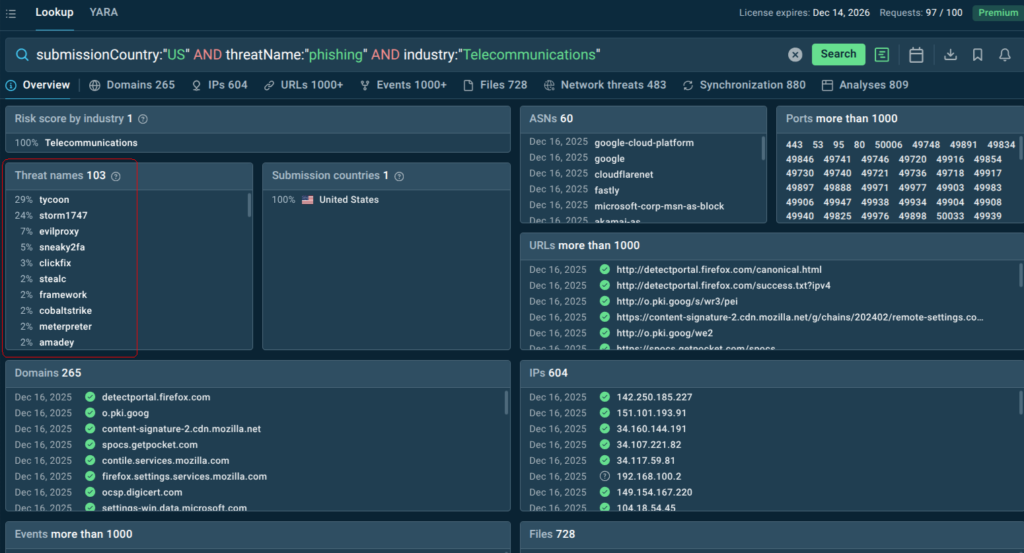
See what malware is threatening the organizations from your country and industry right now
Board-level takeaway:
Early detection driven by real-world threat intelligence materially lowers breach impact and recovery costs.
Message pattern: “Investing in threat intelligence reduces our average incident response cost by 60-70% by enabling early detection and prevention. For every major incident we prevent, we save the organization between $1-4 million in direct costs, not including reputational damage and customer trust.”
2. Ensuring Revenue-Critical Operations and Business Continuity
Board members understand downtime in dollars per minute. For e-commerce platforms, financial services, manufacturing operations, or SaaS providers, every minute of disruption translates directly to lost revenue, damaged customer relationships, and competitive disadvantage. Ransomware attacks alone now cost businesses an average of 25 days of downtime — a strike that many organizations cannot absorb.
Threat intelligence supports resilience by helping organizations:
- Identify emerging attack campaigns early;
- Anticipate shifts in attacker tactics;
- Prepare controls before attacks reach critical systems.
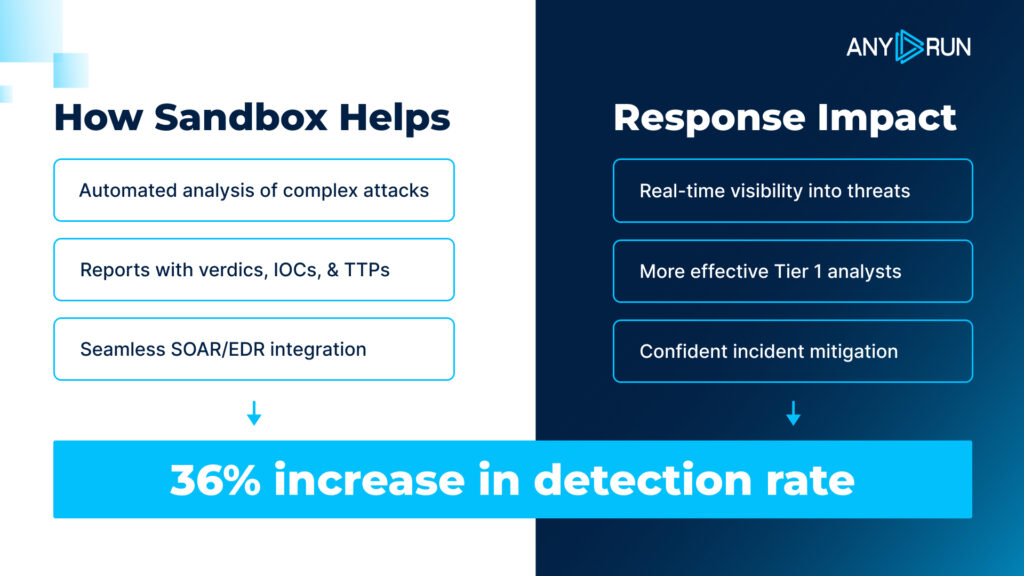
TI shortens mean time to detect (MTTD) and mean time to respond (MTTR) by providing actionable context during incidents. SOC teams correlate alerts against real-time feeds, quickly identifying and containing threats before they spread.

Threat intelligence supports quick informed decisions impacting KPIs
With ANY.RUN’s feeds, powered by community submissions from thousands of organizations, teams gain immediate access to indicators tied to active global campaigns. This accelerates incident response, limits disruption, and keeps critical systems online preserving revenue and operational momentum.
Board-level takeaway:
Threat intelligence reduces the likelihood that cyber incidents escalate into operational outages or prolonged downtime.
Message pattern: “Our revenue-critical operations represent $X million in daily transactions. Threat intelligence gives us advance warning of attacks targeting our industry, allowing us to prevent disruptions before they impact operations. The cost of this service is equivalent to less than one hour of system downtime.”
3. Maximizing ROI on Existing Security Investments
Most organizations have already invested heavily in security infrastructure: firewalls, SIEM platforms, EDR solutions, and of course SOC teams. However, tools are only as effective as the intelligence that drives them. Without current threat data, your security stack operates reactively, generating alerts based on generic signatures and outdated indicators.
Threat Intelligence Feeds dramatically amplify the effectiveness of your security investments. Context-rich current threat data transforms them from reactive alert generators into proactive defense mechanisms.
ANY.RUN’s Threat Intelligence Feeds integrate seamlessly with major security platforms through APIs and standard formats like STIX. Your existing tools immediately gain access to millions of current indicators and threat context without requiring additional headcount or infrastructure. Your SOC analysts can make faster, more accurate decisions because they have the context they need at their fingertips.
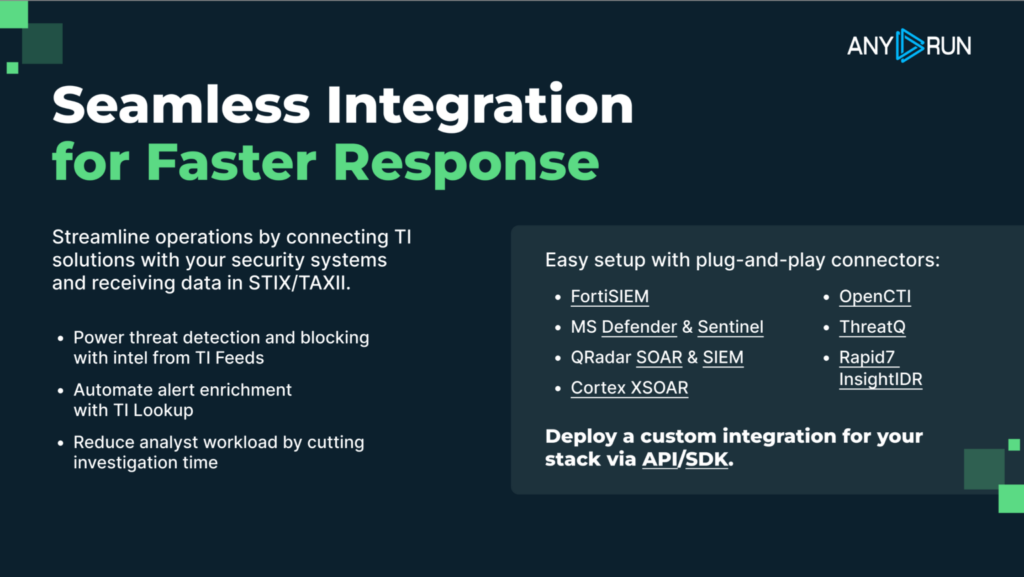
ANY.RUN integration options
Board-level takeaway:
Threat intelligence ensures security investments are aligned with real, current threats to the business, not theoretical risks.
Message pattern: “We’ve invested $X million in security infrastructure. Threat intelligence feeds cost a fraction of that while potentially doubling the effectiveness of every security tool we’ve already purchased.”
4. Optimizing Security Resource Allocation and Driving Efficiency
Cybersecurity budgets are under scrutiny, with boards demanding maximum value from every dollar. Overworked SOC teams drowning in alerts waste resources on false positives and low-priority events. Hiring more analysts is expensive, slow, and increasingly unrealistic. Boards want efficiency, not headcount inflation.
Threat intelligence enriches alerts with context, reduces noise, and allows teams to focus on high-risk threats. Pre-filtered, accurate IOCs improve detection rates while lowering analyst burnout.
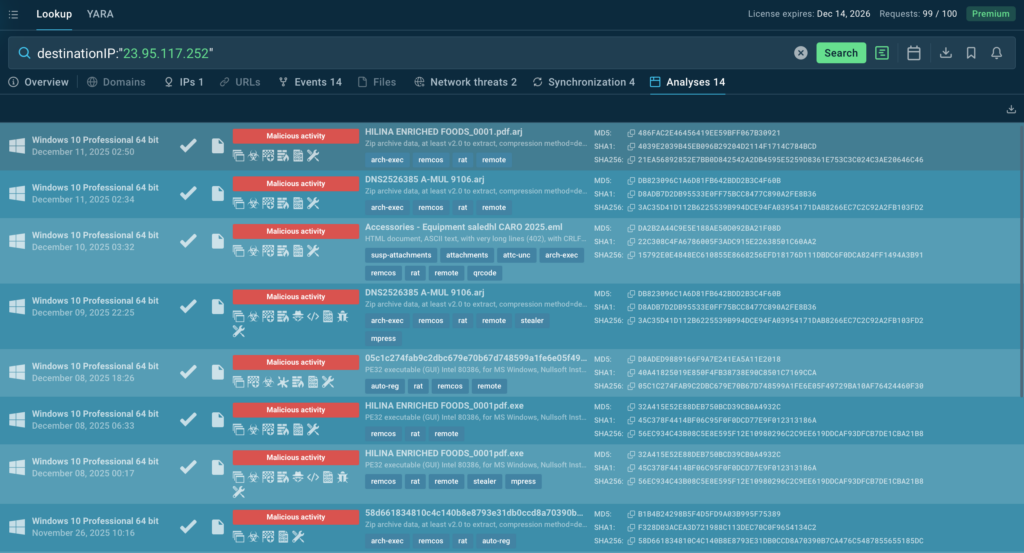
ANY.RUN’s feeds are designed for exactly this: clean, enriched indicators ready for automation, with low false-positive rates thanks to sandbox-verified data. The result is higher SOC productivity, better resource utilization, and a stronger return on existing security investments.
By feeding curated, high-confidence intelligence directly into detection and response workflows, ANY.RUN’s Threat Intelligence Feeds:
- Reduce false positives,
- Speed up alert triage,
- Shorten investigation time,
- Enable junior analysts to make better decisions faster.
This allows organizations to scale their security posture without scaling payroll.
Board-level takeaway:
Threat intelligence increases SOC productivity, delivering better protection without proportional increases in staffing costs.
Message pattern: “Our SOC team currently handles X,000 alerts monthly with Y analysts at an annual cost of $Z. Threat intelligence increases our team’s effective capacity by 50-70% without adding headcount, delivering better protection while keeping personnel costs stable.”
5. Demonstrating Regulatory Compliance and Due Diligence
Regulatory frameworks like GDPR, NIS2, DORA, and SOC 2 don’t just require security controls. They mandate demonstrable due diligence and continuous improvement. Failure to meet these standards results in crippling fines (up to 4% of global revenue under GDPR), potential business restrictions, and loss of customer trust. More importantly, regulators increasingly expect organizations to demonstrate proactive threat awareness and intelligence-driven security practices.
Threat intelligence feeds provide auditable evidence of continuous monitoring, proactive threat hunting, and intelligence-driven security operations. ANY.RUN’s TI Feeds deliver documented indicators of compromise with rich context, enabling your team to demonstrate to auditors that you’re actively monitoring the threat landscape relevant to your industry and geography.
Board-level takeaway:
Threat intelligence provides auditable evidence of proactive monitoring and rapid response capabilities. Non-compliance triggers fines, audits, and reputational damage.
Message pattern: “Threat intelligence isn’t just about preventing attacks — it’s about showing regulators, auditors, and customers that we take our security obligations seriously. This investment protects us from regulatory fines that could reach tens of millions of dollars and positions us favorably during audits and compliance reviews.”
Conclusion
Threat intelligence gives CISOs a way to translate cyber risk into business terms the board understands. It replaces reactive defenses with foresight, guesswork with evidence, and isolated security efforts with a unified, risk-driven strategy.
ANY.RUN’s Threat Intelligence Feeds are built on visibility into real attacker activity observed daily in live malware executions. This means decisions are based on what adversaries are doing now, not what they did months ago. For CISOs, this enables stronger protection. For boards, it delivers confidence that security investments directly support business objectives.
In budget discussions, threat intelligence should not be positioned as “more data.” It should be positioned as business assurance: fewer costly incidents, more efficient operations, and a clearer understanding of cyber risk across the organization.
When CISOs can demonstrate that intelligence-driven security reduces financial impact, protects revenue streams, and scales without ballooning costs, the budget conversation changes. Threat intelligence becomes a strategic pillar of the organization’s risk management program, not a line item to be negotiated away.
About ANY.RUN
As a leading provider of interactive malware analysis and threat intelligence, ANY.RUN is trusted by over 500,000 analysts across 15,000 organizations worldwide. Its solutions enable teams to investigate threats in real time, trace full execution chains, and surface critical behaviors within seconds.
Safely detonate samples, interact with them as they run, and instantly pivot to network traces, file system changes, registry activity, and memory artifacts in ANY.RUN’s Interactive Sandbox. For threat intelligence insights, integrate TI Lookup and TI Feeds supplying enriched IOCs and automation-ready intelligence. No infrastructure maintenance is required.
Start your 2-week trial of ANY.RUN’s solutions →
FAQ: Threat Intelligence for CISOs and Boards
Because boards fund outcomes, not tools. Threat intelligence helps CISOs demonstrate how security investments reduce financial risk, prevent costly incidents, and support business continuity.
Traditional monitoring reacts to alerts after suspicious activity occurs. Threat intelligence provides context about active attackers, campaigns, and techniques, enabling earlier detection and proactive defense.
It connects cyber activity to measurable business impact, such as reduced breach costs, lower downtime risk, and improved operational efficiency, which are metrics boards understand.
By delivering high-confidence indicators and attacker context, feeds reduce false positives, speed up investigations, and help analysts prioritize alerts that matter most to the business.
It cannot replace people, but it significantly increases analyst productivity. Many organizations use threat intelligence to scale security operations without proportional headcount growth.
Intelligence based on live, observed attacks reflects current adversary behavior. This ensures defenses are aligned with how threats operate today, not outdated assumptions.
Common metrics include faster detection times, fewer high-impact incidents, reduced investigation effort, and improved alignment between security spend and risk exposure.
The post 5 Ways Threat Intelligence Drives SOC ROI: Board-Ready Cases for CISOs appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More