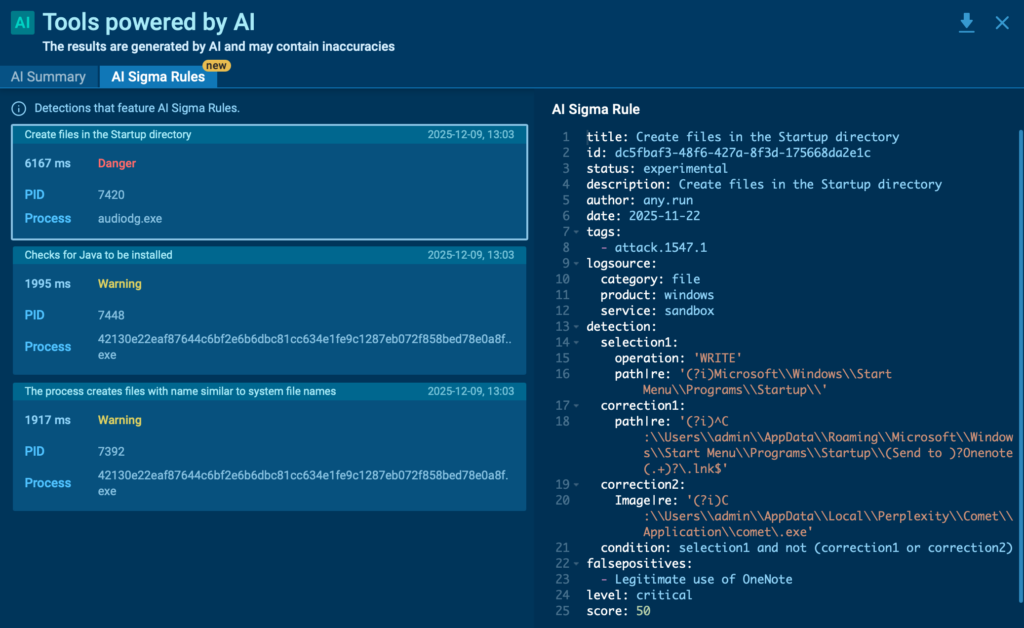
The Week in Vulnerabilities: Cyble Tracks New ICS Threats, Zero-Days, and Active Exploitation

Last week’s reports from Cyble Research & Intelligence Labs (CRIL) to clients highlighted new flaws from December 03 through December 09, 2025, including newly disclosed IT vulnerabilities, ICS vulnerabilities, active exploitation attempts, and dark-web discussions around weaponized CVEs. Drawing from CISA alerts, CRIL’s global sensor network, and Cyble’s vulnerability intelligence platform, the findings outline rapid PoC release cycles, persistent automated exploitation, and targeted attacks against critical infrastructure.
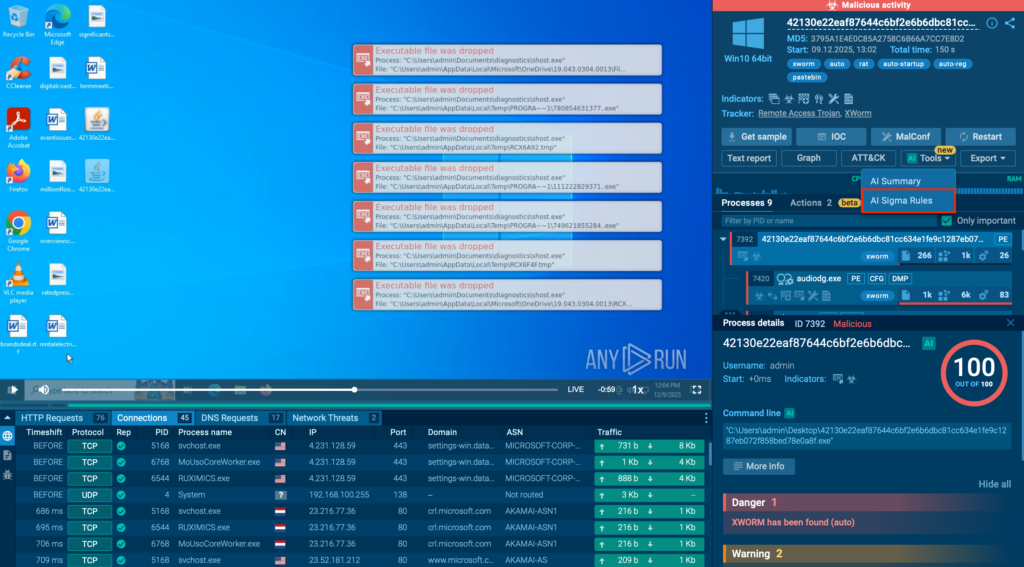
CRIL’s threat-hunting infrastructure deployed across multiple regions continues to record real-time malicious activity, including exploit attempts, brute-force intrusions, malware injections, and financially motivated attacks. There has been a sustained rise in botnet-driven campaigns and opportunistic exploitation of internet-exposed and misconfigured industrial devices throughout the reporting period.
More broadly, CRIL’s weekly insight reveals a sharp increase in newly disclosed vulnerabilities. The Vulnerability Intelligence (VI) module identified 1,378 vulnerabilities this week, including over 131 with publicly available PoCs and three new zero-days.
The Week’s Top IT Vulnerabilities
CRIL’s weekly vulnerability intelligence analysis found multiple high-impact issues affecting enterprise technologies, software ecosystems, and internet-facing applications. Major vendors reporting significant vulnerability counts included Linux distributions, Google, Microsoft, Siemens, and Nextcloud.
A subset of critical vulnerabilities drew community and industry attention:
- CVE-2025-67494: A critical server-side request forgery (SSRF) flaw in ZITADEL, enabling unauthorized network pivoting and data exposure.
- CVE-2025-59719: An authentication bypass impacting Fortinet products.
- CVE-2025-42880: A code injection flaw in SAP Solution Manager.
- CVE-2025-66516: A severe XML External Entity (XXE) vulnerability in Apache Tika affects modules such as tika-core, tika-pdf-module, and tika-parsers.
These IT vulnerabilities present a direct risk to organizations due to their potential to enable unauthorized access, data theft, and remote code execution. Across all disclosures, CRIL identified 68 critical vulnerabilities under CVSS v3.1 and 23 rated critical under CVSS v4.0, making it another high-activity week in vulnerability disclosure trends.
CISA – Known Exploited Vulnerabilities (KEV) Catalogue
Between December 3 and December 9, 2025, CISA added six new exploited vulnerabilities to its CVE catalog.
Notable additions include:
- CVE-2025-6218: A directory traversal flaw in RARLAB WinRAR enables remote code execution (RCE).
- CVE-2025-55182: A critical pre-authentication RCE in React Server Components (RSC) leveraging unsafe deserialization in the “Flight” protocol.
The exploitation of CVE-2025-55182 began around December 08, employing payloads that diverged from the December 04 PoC publicly released by researchers. The variant techniques suggest rapid adaptation by attackers following disclosure.
Notable Vulnerabilities Discussed in Open-Source Communities
CRIL identified multiple trending vulnerabilities drawing attention across open-source security and research forums.
Key discussions included:
- CVE-2025-62221: A use-after-free elevation of privilege vulnerability in the Windows Cloud Files Mini Filter Driver. A local attacker could gain SYSTEM-level privileges, and the flaw can be chained with phishing or browser exploits for full host compromise.
- CVE-2025-10573: A critical stored XSS vulnerability in Ivanti Endpoint Manager, allowing remote unauthenticated attackers to embed malicious JavaScript that executes when an administrator views the dashboard.
Vulnerabilities Under Discussion on the Dark Web
CRIL’s dark-web monitoring identified several vulnerabilities actively discussed, traded, or weaponized by threat actors:
- CVE-2025-6440: A critical arbitrary file upload vulnerability in the WooCommerce Designer Pro plugin for WordPress (also distributed with the Pricom Printing Company & Design Services theme). Allows unauthenticated file upload and remote code execution via malicious PHP web shells.
- CVE-2025-55182: Also referred to as “React2Shell” or “React4Shell,” actively weaponized on underground forums. The flaw affects React 19’s Server Components Flight protocol and frameworks such as Next.js.
- CVE-2025-66516: A severe XXE vulnerability in Apache Tika. The administrator of the “Proxy Bar” Telegram channel circulated exploit material demonstrating how malicious PDF files with embedded XFA forms could achieve arbitrary file read, SSRF, denial-of-service, and, in some cases, remote code execution.
CRIL’s vulnerability intelligence timeline notes:
| CVE | Product | CVE Release | DW Capture | PoC |
| CVE-2025-6440 | WooCommerce Designer Pro | Oct 24, 2025 | Dec 03, 2025 | Yes |
| CVE-2025-55182 | React Server Components | Dec 03, 2025 | Dec 05, 2025 | Yes |
| CVE-2025-66516 | Apache Tika Modules | Dec 04, 2025 | Dec 08, 2025 | Yes |
Top ICS Vulnerabilities Tracked This Week
CRIL highlighted multiple ICS vulnerabilities affecting industrial vendors across energy, manufacturing, and commercial facilities.
Key issues included:
- Sunbird – DCIM dcTrack & Power IQ (≤ 9.2.0): Authentication bypass and hard-coded credentials vulnerabilities (CVSS 6.5 and 6.7), risking unauthorized access and credential compromise.
- Johnson Controls OpenBlue Workplace (2025.1.2 and prior): A CVSS 9.3 Forced Browsing vulnerability enabling unauthorized access to sensitive operations in critical infrastructure environments.
Across the ICS landscape, most vulnerabilities were medium severity, while commercial facilities, critical manufacturing, and energy sectors accounted for 43% of total incidents. Multi-sector issues, including IT, government, healthcare, and transportation, accounted for an additional 29%.
Recommendations and Mitigations
CRIL’s report reiterates essential mitigation steps:
- Apply all vendor patches promptly, particularly for vulnerabilities listed in the KEV catalog.
- Implement a structured patch management program covering testing, deployment, and verification.
- Segment networks to isolate critical systems and reduce lateral movement.
- Maintain an incident response plan and test it regularly.
- Deploy comprehensive monitoring and logging with SIEM correlation.
- Track alerts from vendors, CERTs, and government authorities.
- Conduct routine VAPT exercises and security audits.
- Maintain visibility into internal and external assets.
- Enforce strong password policies, replace all default credentials, and adopt MFA across all environments.
Conclusion
The wide range of vulnerabilities identified this week highlights the expanding threat landscape facing industrial and operational environments. Security teams must act quickly and focus on risk-based vulnerability management to protect critical systems.
Key practices, such as network segmentation, restricting exposed assets, applying Zero-Trust principles, maintaining resilient backups, hardening configurations, and continuous monitoring, remain essential for reducing attack surface and improving incident response readiness.
Cyble’s attack surface management solutions can support these efforts by detecting exposures across network and cloud environments, prioritizing remediation, and providing early indicators of potential cyberattacks. To see how Cyble can strengthen your industrial security posture, request a demo today.
The post The Week in Vulnerabilities: Cyble Tracks New ICS Threats, Zero-Days, and Active Exploitation appeared first on Cyble.
Cyble – Read More