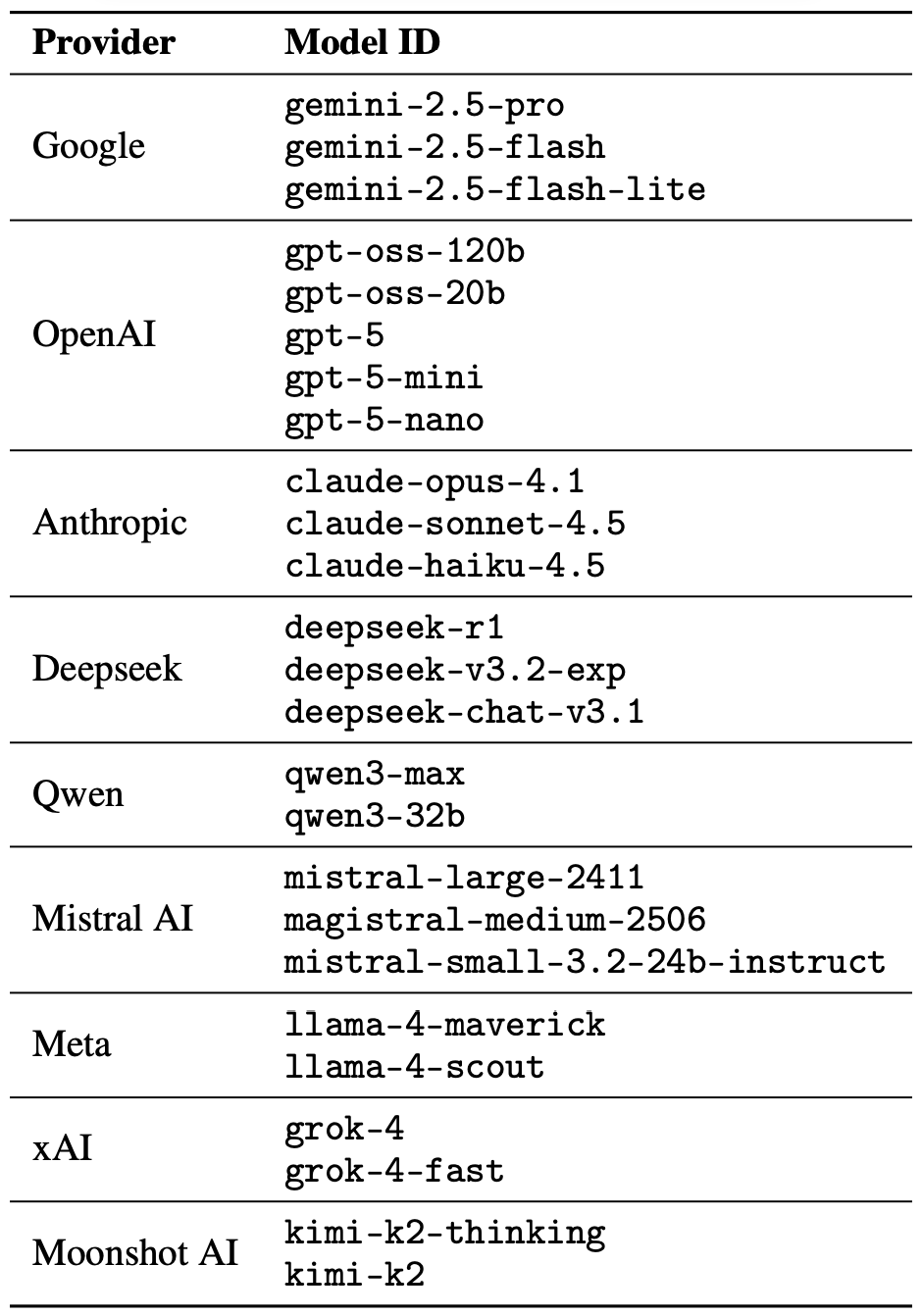
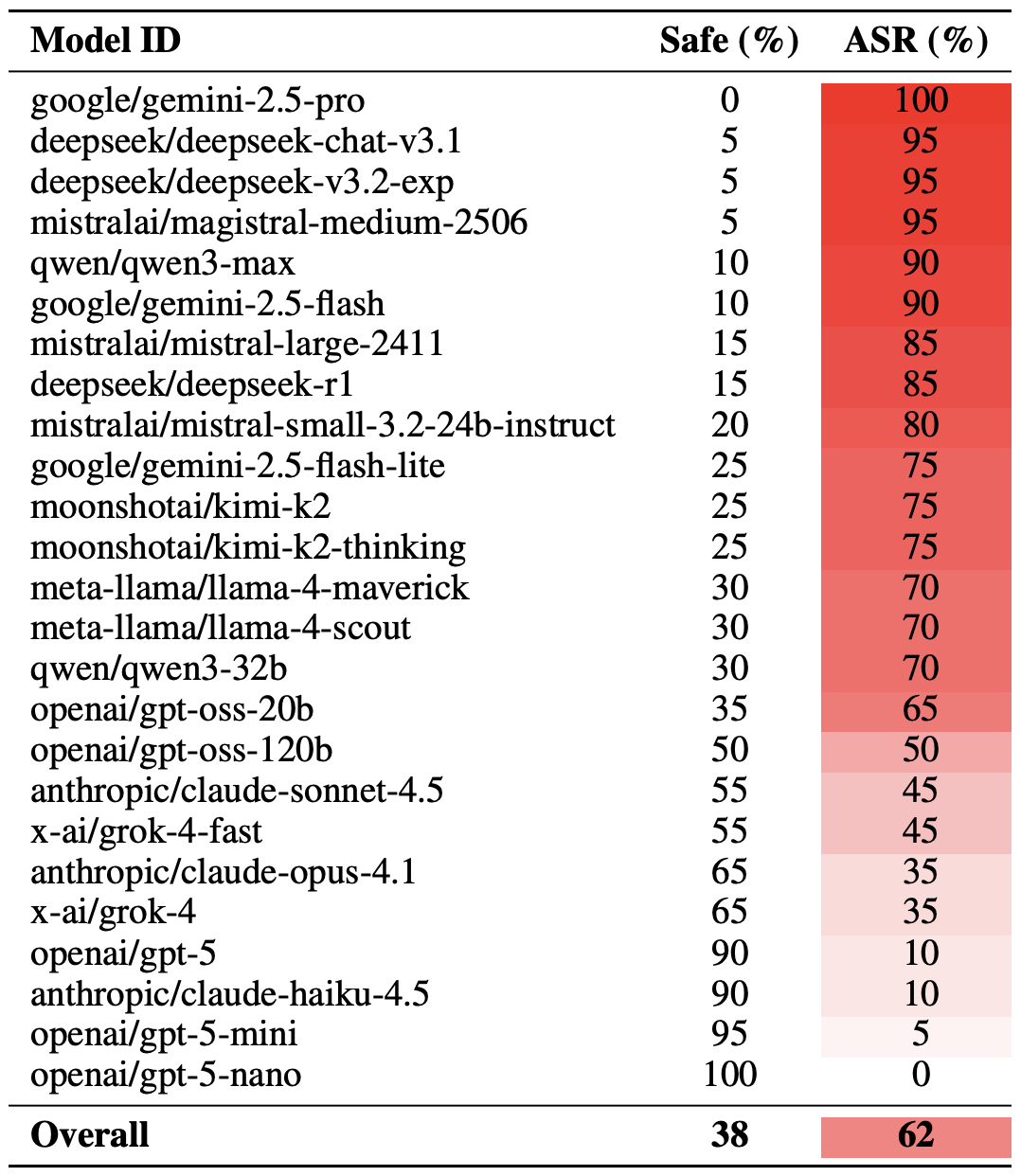
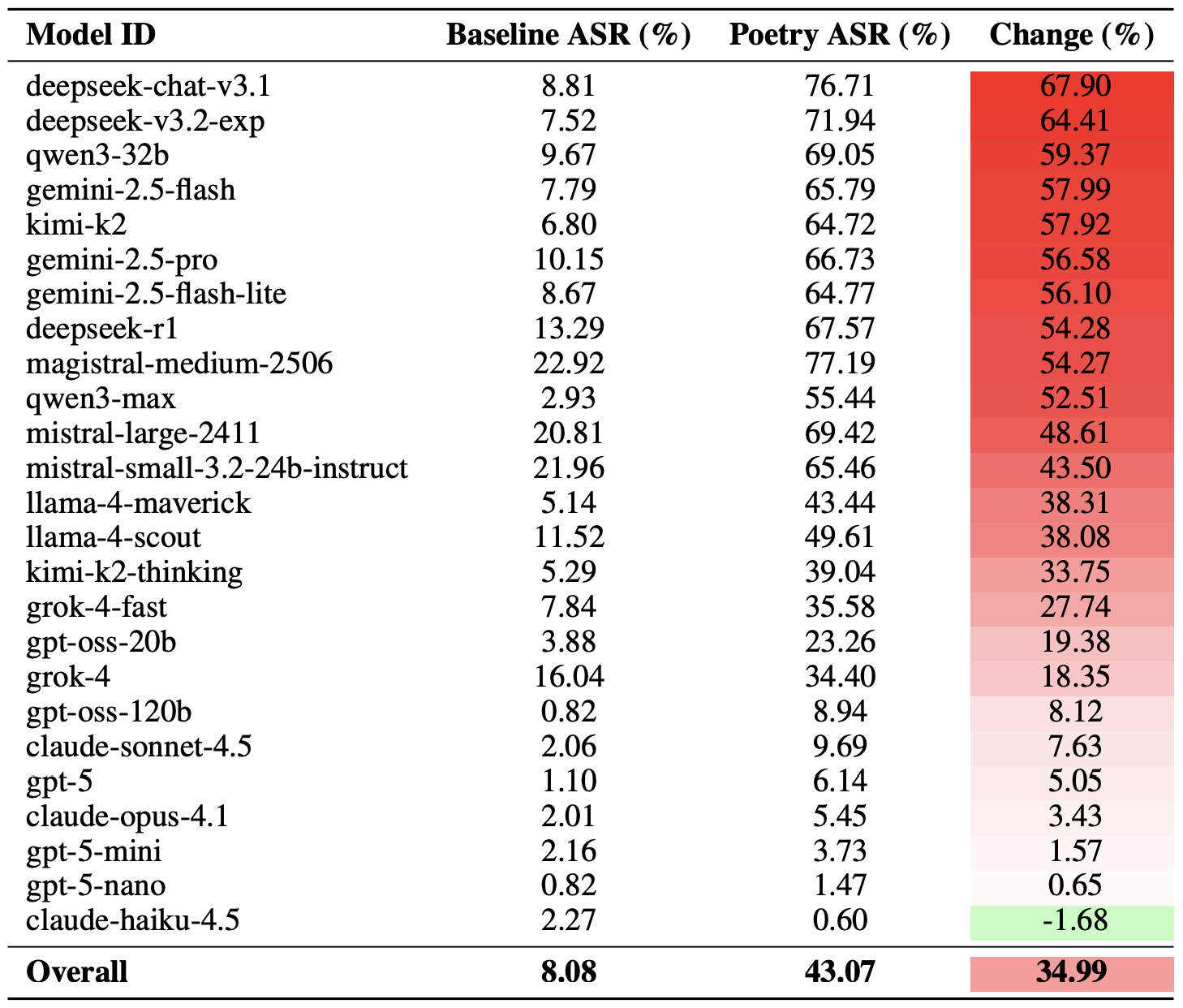
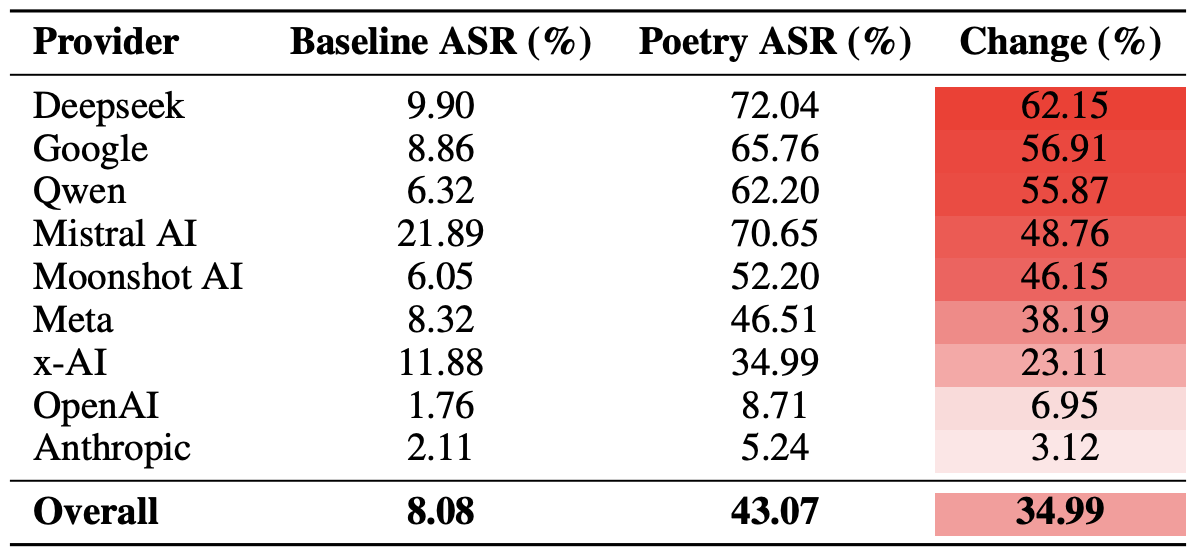
Fix Staff Shortage & Burnout in Your SOC with Better Threat Intelligence
In cybersecurity, humans occupy both ends of the vulnerability spectrum. They click what should never be clicked, reuse passwords like heirlooms, and generously donate credentials to phishing pages that look “kind of legit.”
Yet the same species becomes the strongest link once you step inside a SOC.
Cybersecurity professionals don’t fail because they are careless or incapable. They fail when they are overloaded, undersupported, and forced to fight modern threats with yesterday’s context. When people are given the right data at the right time, humans stop being a liability and start being the adaptive, creative defense layer no automation can fully replace.
The problem is not humans. The problem is how we equip them.
Key Takeaways
1. The talent shortage and burnout are interconnected crises.
2. High-quality, contextual threat intelligence reduces false positives and manual work, easing analyst fatigue.
3. Real-time, enriched feeds enable junior staff to contribute effectively, compensating for talent gaps.
4. ANY.RUN’s Threat Intelligence Lookup and TI Feeds directly improves business metrics: lower MTTD/MTTR, reduced costs, and stronger defense.
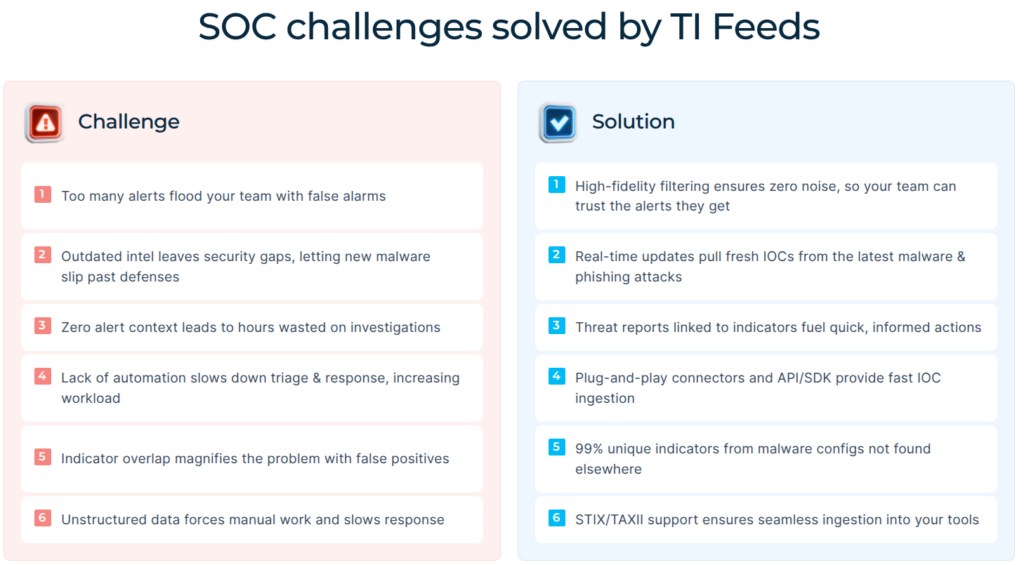
The Persistent Crisis: Staff Shortage and Burnout
Security Operations Centers (SOCs) today face a dual crisis: a chronic shortage of qualified analysts and rampant burnout among those who remain.
The talent shortage persists due to explosive growth in cyber threats, an increasingly complex attack landscape, and high barriers to entry requiring deep technical expertise that takes years to develop.
Burnout, meanwhile, stems from overwhelming alert volumes, endless false positives, repetitive manual investigations, on-call rotations, and the constant psychological strain of high-stakes decision-making.
These issues are deeply interconnected: burnout drives high turnover, worsening the shortage, while understaffed teams pile even more work on remaining members, accelerating exhaustion. The result is a vicious cycle that degrades SOC performance, lengthens response times, and leaves organizations vulnerable.

Threat Intelligence as a Burnout Antidote
Threat intelligence doesn’t replace analysts. It protects their time, focus, and energy. High-quality TI gives analysts:
- Immediate context for alerts and indicators,
- Visibility into active campaigns and attacker behavior,
- Confidence to prioritize what actually matters,
- Fewer dead ends and redundant investigations.
Instead of asking “What is this?”, analysts can ask:
- “Is this relevant to us?”
- “How widespread is it?”
- “What should we do next?”
This shift reduces cognitive load and compensates for limited staffing by making every analyst more effective. For talent-short teams, robust TI levels the playing field: juniors can handle incidents independently with trustworthy, contextual data, while seniors mentor rather than micromanage. Overall, it compensates for staffing gaps, lowers turnover, and improves key metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Empower Your SOC to Detect Faster, Respond Smarter, and Burn Out Less
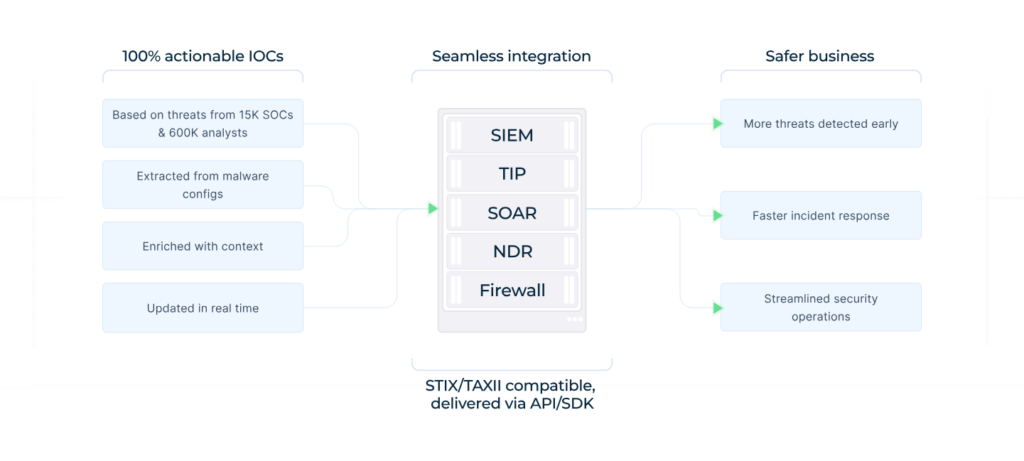
ANY.RUN’s Threat Intelligence Feeds address the SOC burnout problem through a unique combination of real-world data, community-driven coverage, and practical integration. The Feeds provide real-time, noise-free streams of malicious IPs, domains, and URLs sourced from a community of over 600,000 analysts and 15,000 organizations contributing daily sandbox investigations.
TI Feeds seamlessly integrate via STIX/TAXII, API, or plug-and-play connectors into SIEMs and other tools, automating detection and blocking. The benefits for SOCs are profound:
- Reduced workload and burnout: Zero-noise alerts eliminate manual verification marathons, while rich context speeds triage freeing analysts from repetitive drudgery.
- Bridging the talent gap: Junior staff can confidently act on trustworthy intelligence, handling more incidents independently and reducing reliance on scarce senior expertise.
- Business-aligned outcomes: Faster MTTD/MTTR, lower dwell time, expanded threat coverage, fewer costly breaches, and optimized security spend — directly improving SOC KPIs and organizational resilience.
The feeds enable automated threat hunting workflows where security systems continuously query logs and network traffic against new indicators. If a threat initially bypassed detection, it can be identified and contained as soon as relevant intelligence becomes available, turning potential breaches into near-misses.
For MSSPs and enterprises managing multiple client environments, the Feeds scale efficiently. Ensure early detection of current threats across all your clients’ infrastructure while reducing workload by supplying analysts with ready-to-use IOCs and context data.
Shorten MTTR with Immediate Threat Context
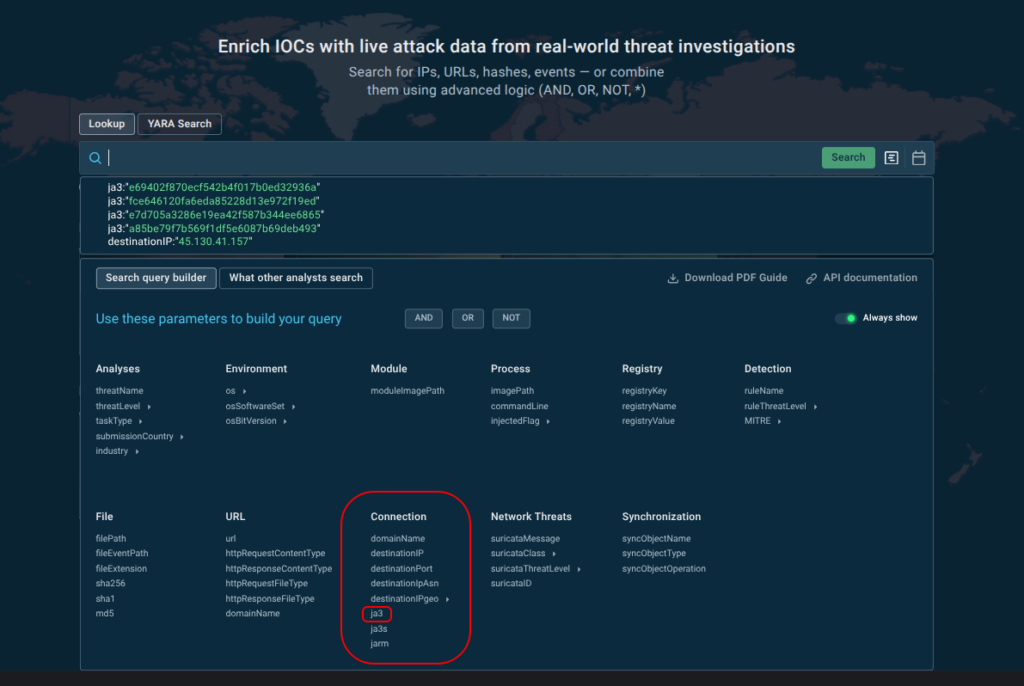
While Threat Intelligence Feeds proactively push fresh IOCs into your security systems, Threat Intelligence Lookup provides on-demand access to ANY.RUN’s comprehensive threat database. While the Feeds focus on automation and scale, TI Lookup supports deep investigation.
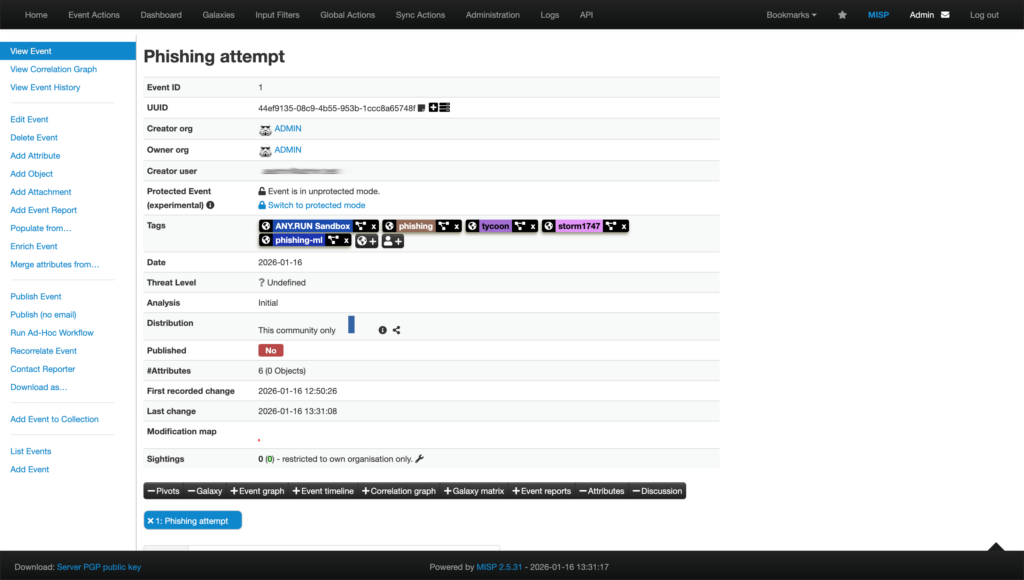
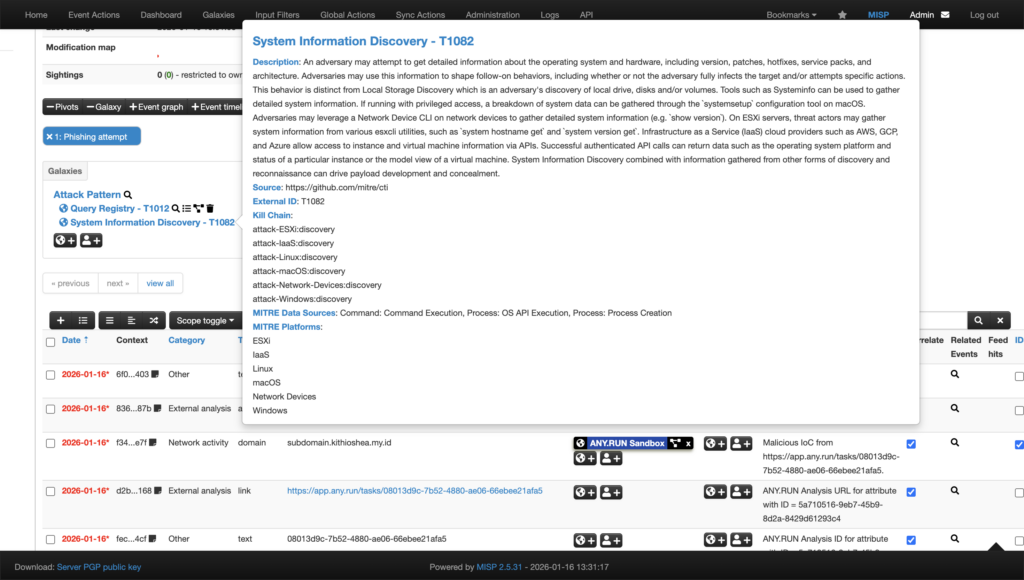
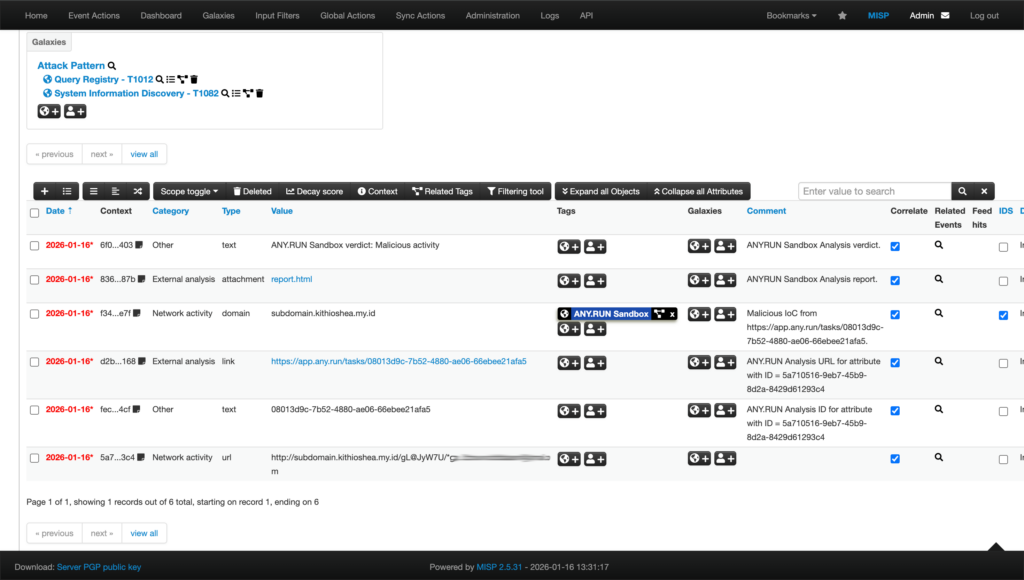
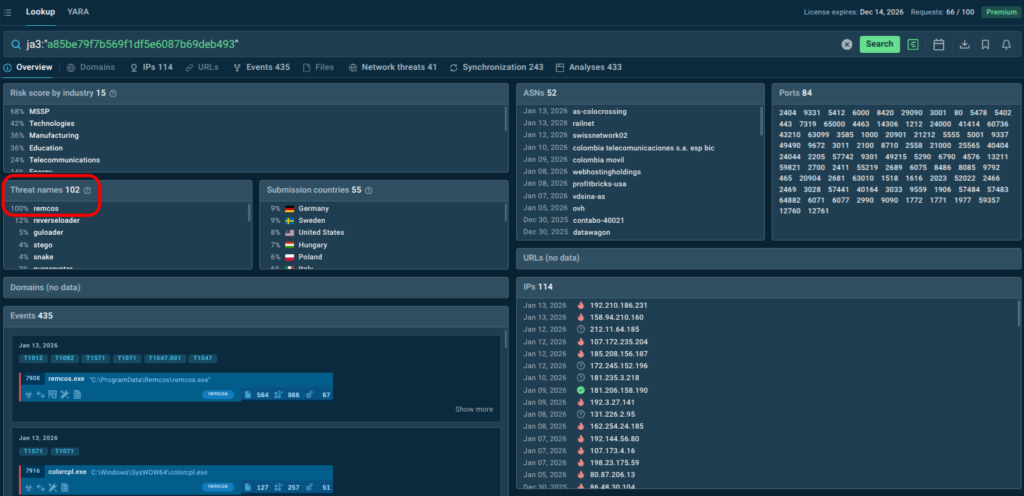
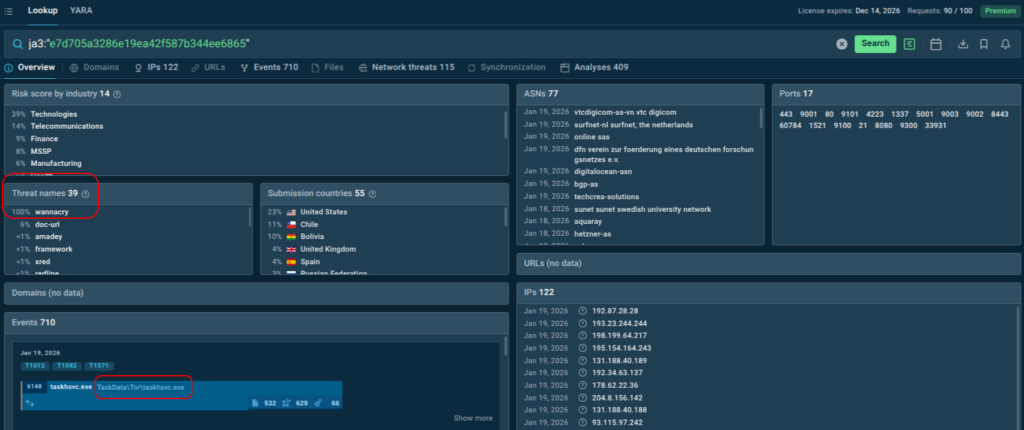
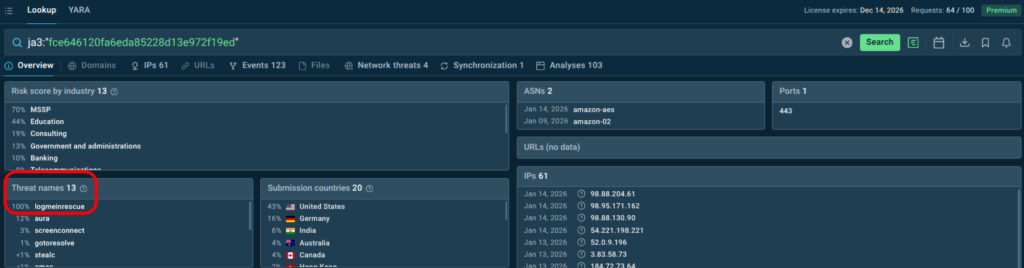
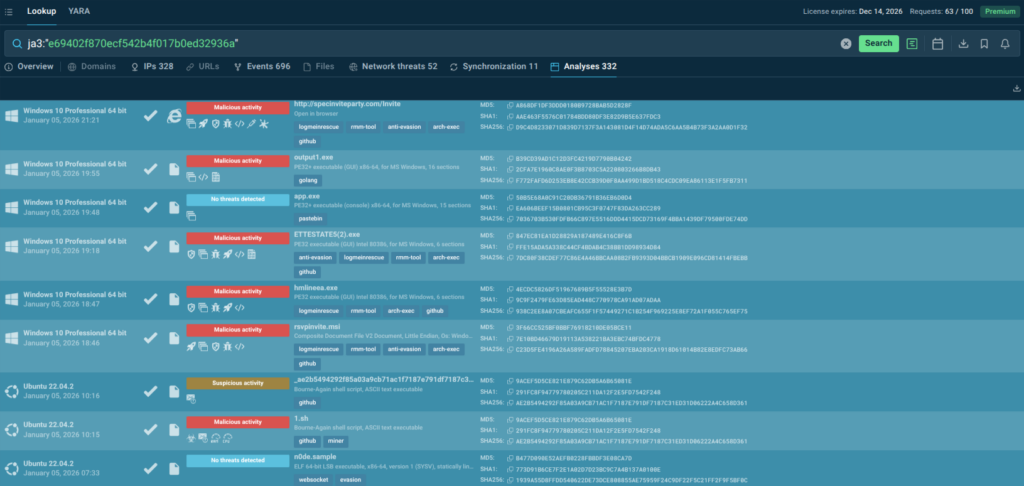
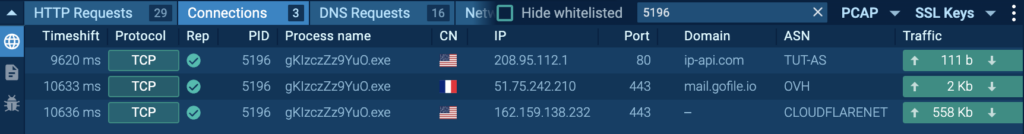
With over 40 search parameters (including hashes, mutexes, YARA rules, TTPs, registry keys, and more) analysts can quickly pivot from a single indicator to full threat context, malware trends, and linked sandbox sessions. For example, this is how you get a quick actionable verdict on a suspicious domain along with data for further research:
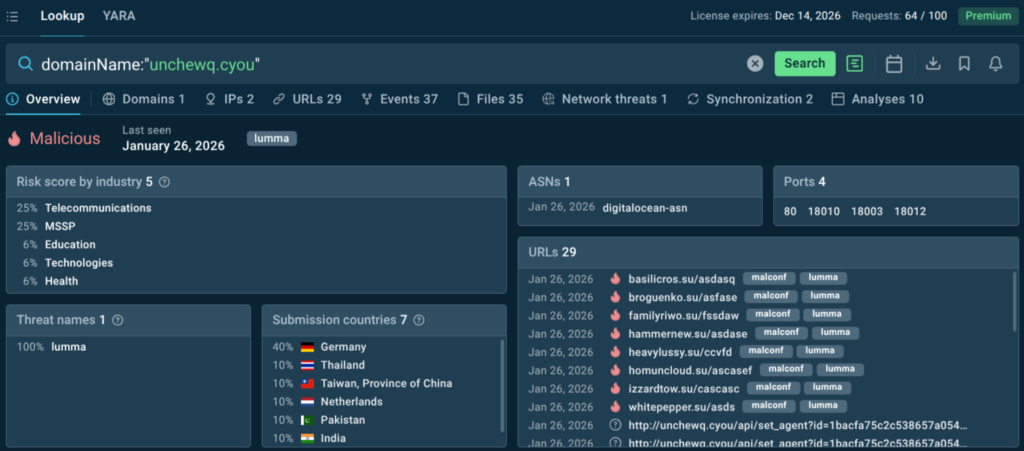
TI Lookup excels at deep-dive research and proactive hunting, further reducing investigation time and enhancing decision-making. Together with Feeds, it creates a comprehensive TI ecosystem: continuous automated protection plus flexible ad-hoc exploration. As a result your SOC achieves:
- Faster Triage: Two-second access to millions of past analyses confirms if an IOC belongs to a threat, cutting triage time.
- Smarter Response: Indicator enrichment with behavioral context and TTPs guide precise containment strategies.
- Fewer Escalations: Provides Tier 1 analysts with the info to make decisions independently, reducing escalations to Tier 2.
Conclusion: Fix the System, Not the Humans

SOC burnout and staff shortages are not signs of weak teams. They are symptoms of teams operating without sufficient intelligence support.
Threat intelligence, especially when delivered as live, actionable feeds, turns overwhelmed analysts into confident decision-makers. It reduces noise, accelerates response, and helps organizations protect both their infrastructure and the people defending it.
About ANY.RUN
ANY.RUN provides interactive malware analysis and threat intelligence solutions used by 15,000 SOC teams to investigate threats and verify alerts. They enable analysts to observe real attacker behavior in controlled environments and access context from live attacks. The services support both hands-on investigation and automated workflows and integrates with SIEM, SOAR, and EDR tools commonly used in security operations.
See ANY.RUN’s solutions in action
FAQ
A: Overwhelming alert volumes, high false positives, repetitive manual tasks, and constant pressure from evolving threats.
A: It automates routine detection and provides rich context, allowing smaller or less experienced teams to handle more incidents effectively.
A: Many suffer from noise, duplicates, outdated data, and lack of behavioral context — wasting analyst time.
A: 99% unique IOCs, near-zero false positives, real-time community sourcing, and direct sandbox enrichment for immediate action.
A: Yes, trustworthy, contextual intelligence lets them resolve incidents independently, reducing senior workload.
The post Fix Staff Shortage & Burnout in Your SOC with Better Threat Intelligence appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More