Gravy Analytics leak: How to protect your location data | Kaspersky official blog
Our smartphones and other devices collect and then transmit massive amounts of data about us to dozens, maybe hundreds, of third-party companies every single day. This includes our location information, and the market for such information is huge. Naturally enough, the buying and selling goes on without our knowledge, creating obscure risks to our privacy.
The recent hack of location data broker Gravy Analytics clearly illustrates the potential pitfalls of such practices. This post analyzes how data brokers operate, and what can happen if the information they collect leaks. We also give tips on what you can do to protect your location data.
What location data brokers are
Data brokers are companies that collect, process, and sell information about users. They get this information from mobile apps, online ad networks, online analytics systems, telecom operators, and a host of other sources from smart-home devices to cars.
In theory, this data is only collected for analytics and targeted advertising. In practice, however, there are often no restrictions on usage, and seemingly anyone can buy it. So, out there in the real world, your data can be used for pretty much any purpose. For example, an investigation last year revealed that commercial data brokers — directly or through intermediaries — may even serve government intelligence agencies.
Data brokers collect all kinds of user information, of which one of the most important and sensitive categories is location data. It’s so in demand, in fact, that besides more generalized data brokers, firms exist that focus on it specifically.
Those are the location-data brokers — organizations that specialize in collecting and selling information about user location. One of the major players in this segment is U.S. location tracking firm Gravy Analytics, which merged with Norway’s Unacast in 2023.
The Gravy Analytics data leak
In January 2025, news broke of a data leak at Gravy Analytics. At first it was confined to unofficial reports based on a post that appeared on a private Russian-language hacker forum. The poster claimed to have hacked Gravy Analytics and stolen the location data of millions of users, providing screenshots of the data trove as proof.
It wasn’t long before official confirmation came through. Under Norwegian law, Gravy Analytics’ parent, Unacast, was legally required to notify the national regulator.
The company’s statement reported that on January 4, an unauthorized individual gained access to Gravy Analytics’ AWS cloud storage environment “through a misappropriated access key”. The intruder “obtained certain files, which could contain personal data”.
Analysis of the data Gravy Analytics leaked
Unacast and Gravy Analytics were in no hurry to specify what data could have been compromised. However, within a few days, an independent security researcher published their own in-depth analysis of the leaked information based on a sample of the stolen data they’d been able to obtain.
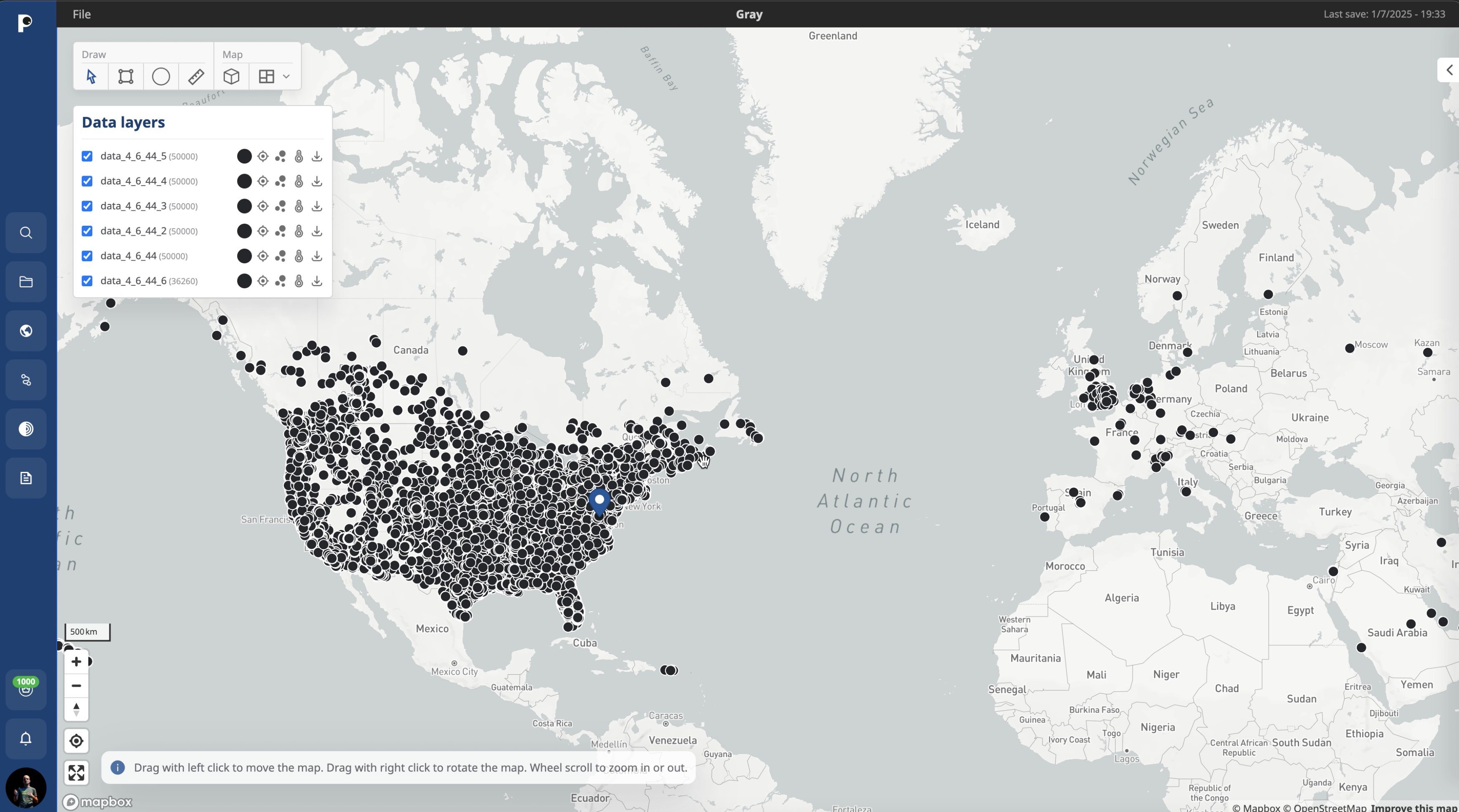
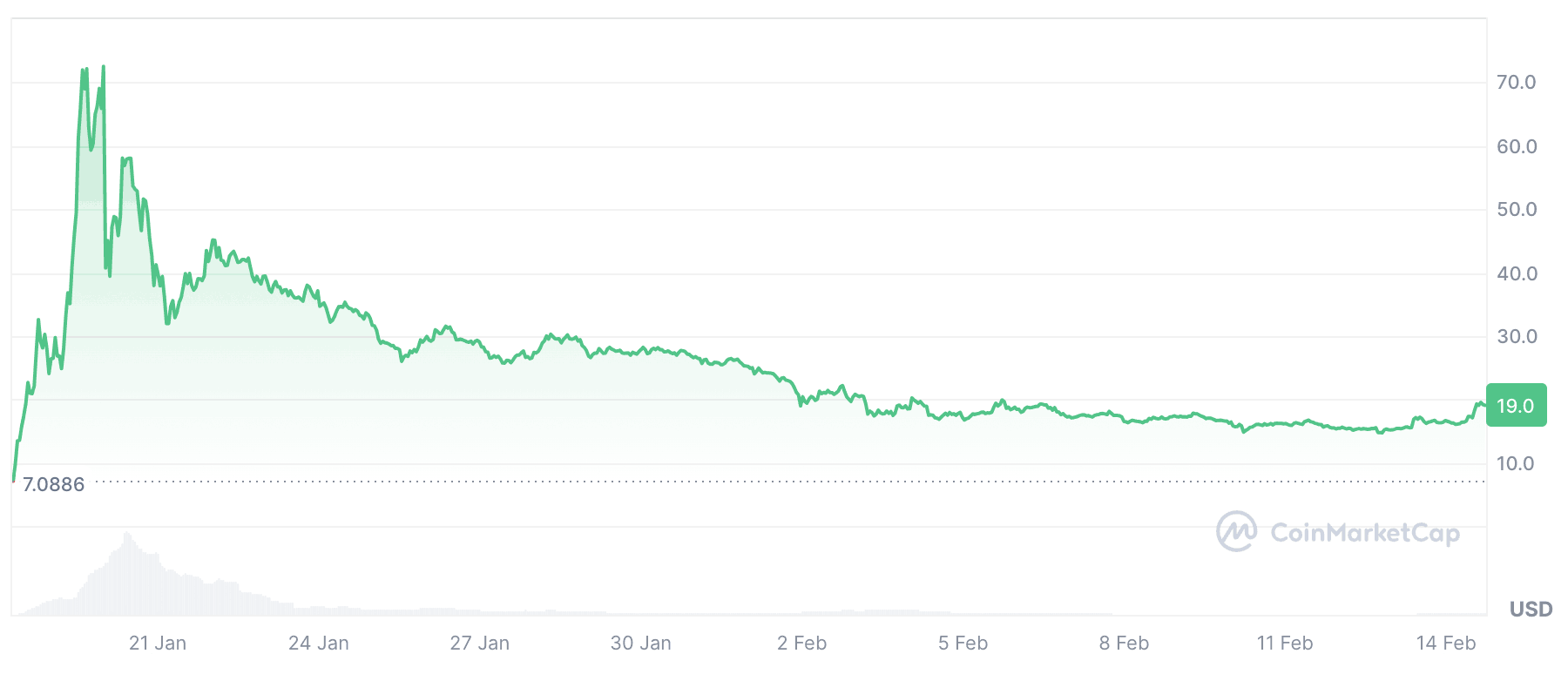
The Gravy Analytics leak included the location data of users worldwide. Source
It turned out that the Gravy Analytics hack did indeed leak a gigantic set of location data of users worldwide — from Russia to the United States. The fragment analyzed by the researcher was 1.4GB in size, and consisted of around 30 million records — mostly collected in the first days of January 2025. Meanwhile, the hacker claimed the stolen database is 10TB, meaning it could potentially contain over 200 billion records!
This data was collected by mobile apps and acquired by Gravy Analytics to be aggregated and subsequently sold to clients. As the analysis of the leak showed, the list of apps used to collect location data runs into the thousands. For example, the sample studied contained data collected from 3455 Android apps — including dating apps.
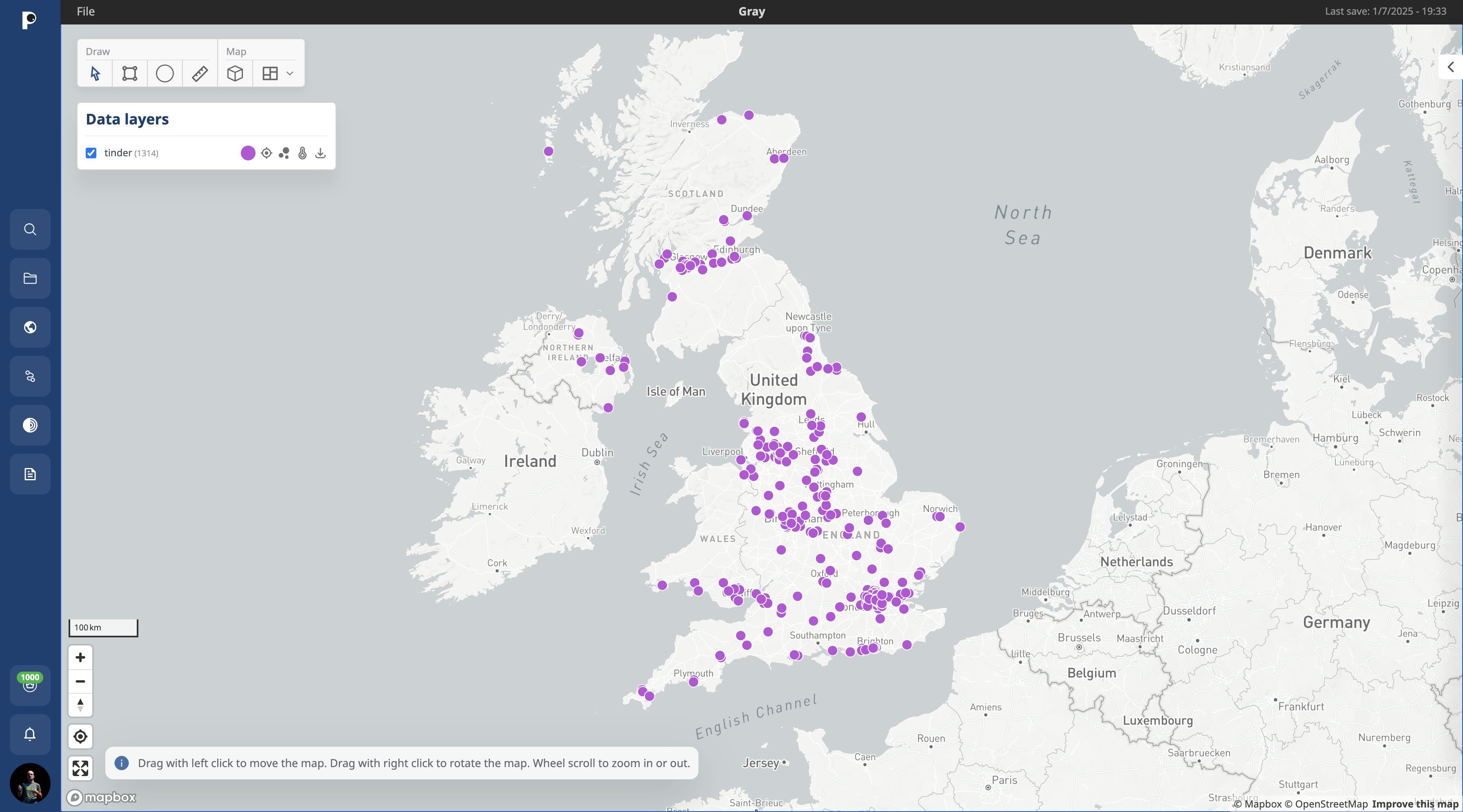
UK-based Tinder users’ location data is an example of what can be found in the data leaked from Gravy Analytics. Source
Tracking and deanonymizing users with the Gravy Analytics’ leak data
What’s most unpleasant about the Gravy Analytics hack is that the leaked database is linked to advertising IDs: IDFA for iOS and AAID for Android devices. In many cases, this makes it possible to track users’ movements over time. Here, for instance, is a map of such movements in the vicinity of the White House in Washington, D.C. (remember that this visualization uses only a small sample of the stolen data; the full database contains a lot more):
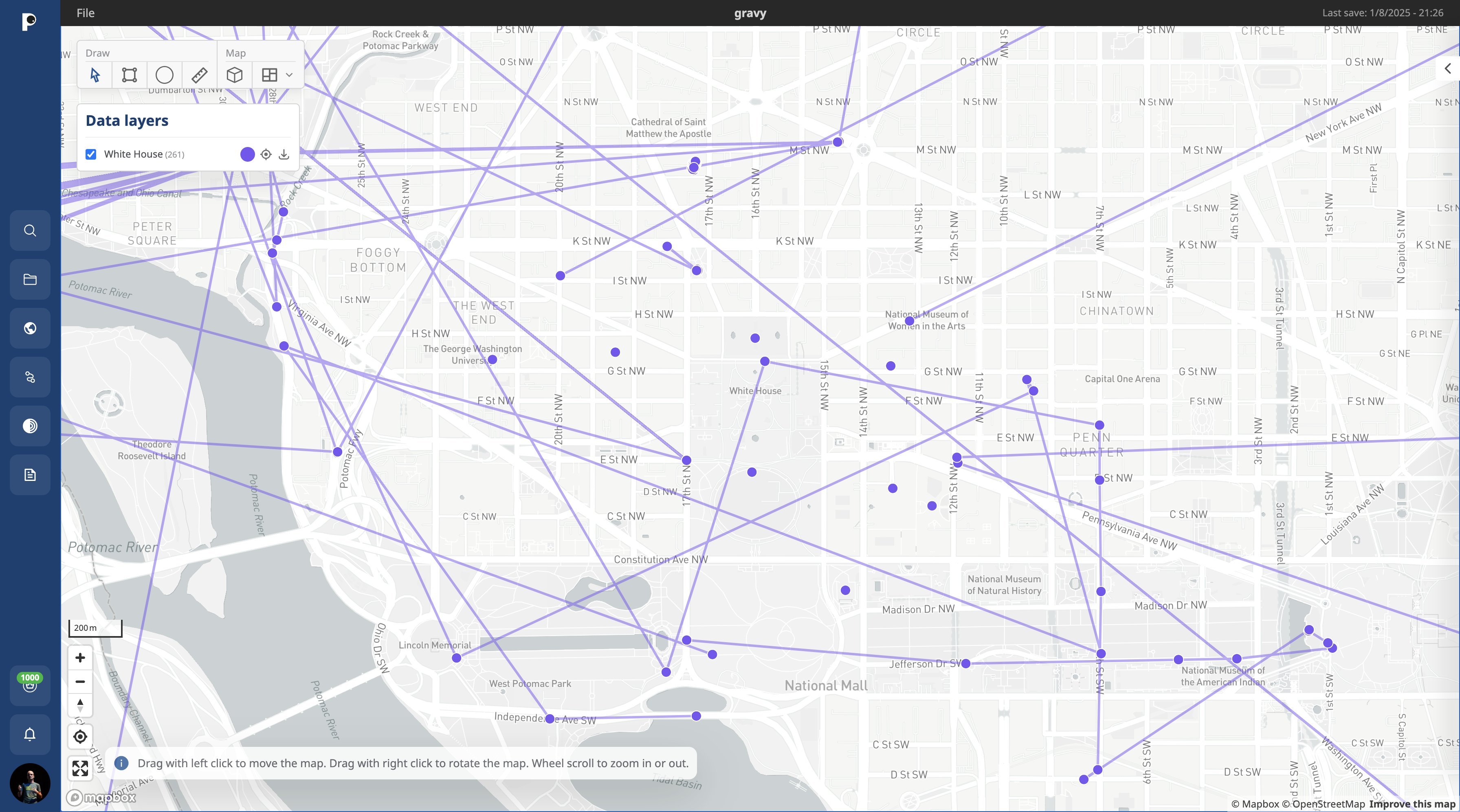
Data in the Gravy Analytics leak linked to advertising IDs can be used to track users’ movements over time. Source
Worse yet, some data can be deanonymized. For example, the researcher was able to track the movements of a user who visited the Blue Origin launch pad:
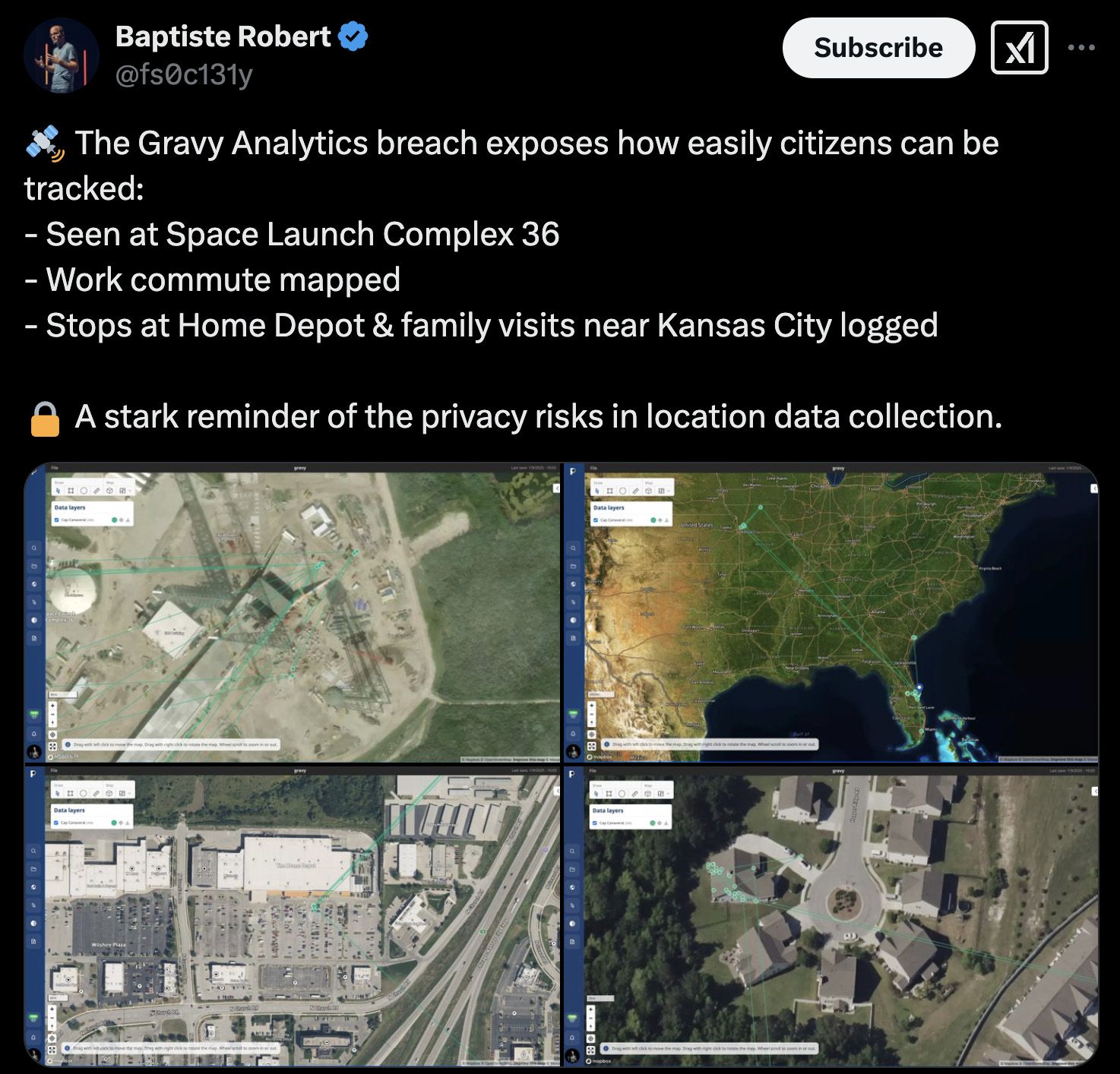
An example of user deanonymization using location data leaked from Gravy Analytics. Source
Another example: the researcher was able to track a user’s movements from the Columbus Circle landmark in Manhattan, New York City, to his home in Tennessee, and then to his parents’ house the next day. Based solely on OSINT data, the researcher learned a great deal about this individual, including their mother’s name and the fact that their late father was a U.S. Air Force veteran.
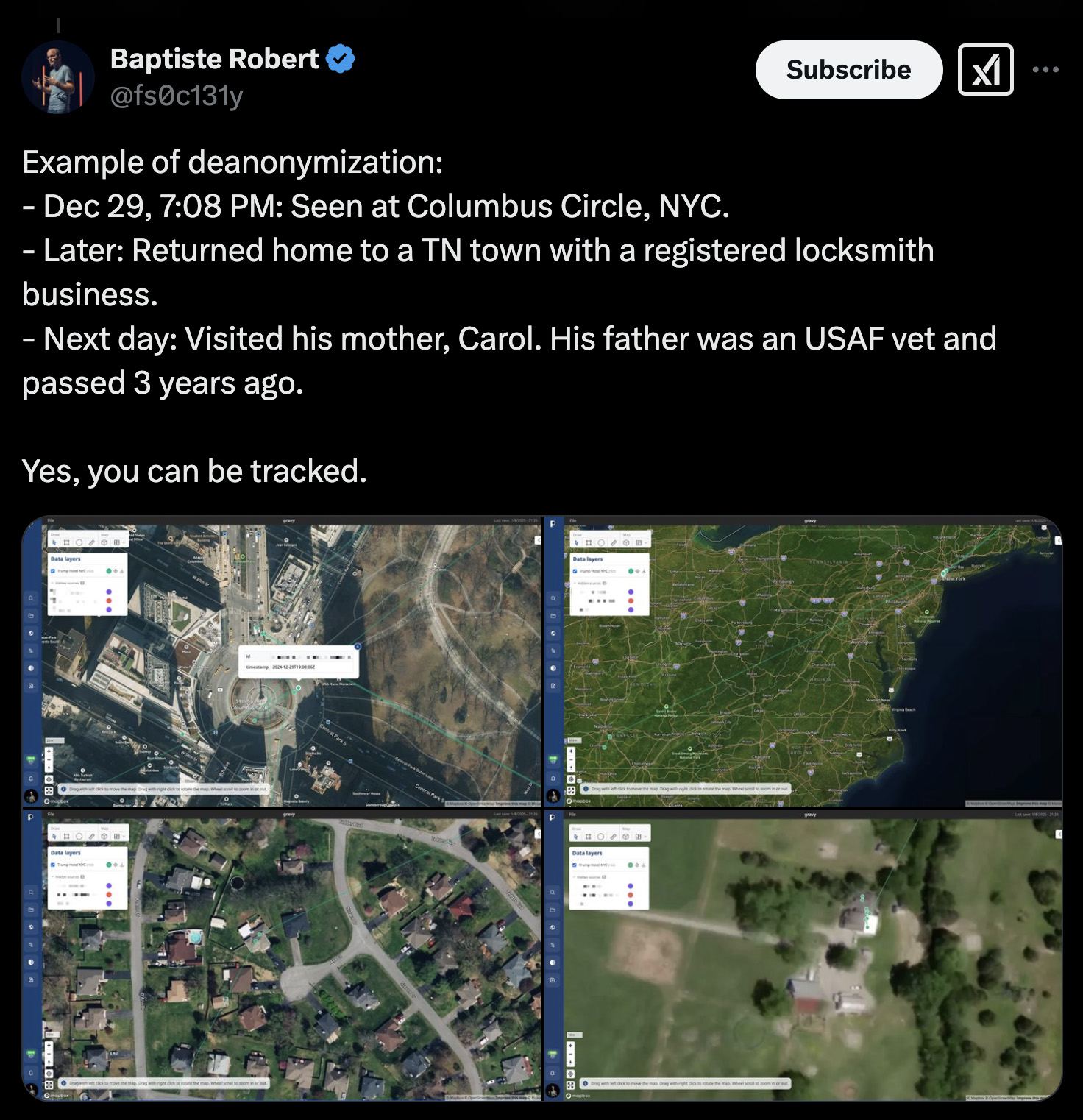
Another example of user deanonymization using location data leaked from Gravy Analytics. Source
The Gravy Analytics data breach demonstrates the serious risks associated with the data broker industry, and location data brokers in particular. As a result of the hack, a huge volume of user location records collected by mobile apps spilled out into the public domain.
This data makes it possible to track the movements of a great many people with fairly high accuracy. And even though the leaked database doesn’t contain direct personal identifiers such as first and last names, ID numbers, addresses, or phone numbers, the linkage to advertising IDs can in many cases lead to deanonymization. So, based on various quasi-identifiers, it’s possible to establish a user’s identity, find out where they live and work, as well as trace their social connections.
How to protect your location data?
Unfortunately, collecting user location data is now such a widespread practice that there’s no easy answer to this question. Alas, there’s no switch you can simply flick to stop all the internet companies worldwide harvesting your data.
That said, you can at least minimize the amount of information about your location that falls into the hands of data brokers. Here’s how:
- Be strict with apps asking for access to location data. Often, they’ll work just fine without it — so unless there’s a compelling reason for the app to know your location, just say no.
- Carefully configure privacy in apps that genuinely need your geolocation to function. For example, see our guides to configuring all the most popular running apps.
- Don’t allow apps to track your location in the background. When granting permissions, always select the “Only while using the app” option.
- Uninstall apps you no longer use. In general, try to keep the number of apps on your smartphone to a minimum — this will reduce the number of potential data collectors on your device.
- If you use Apple iOS, iPadOS, or tvOS devices, opt out of app tracking. This will prevent data collected on you from being deanonymized.
- If you use Android, delete your device’s advertising ID. If this option is unavailable in your OS version, reset the advertising ID regularly.
- Install a robust security solution capable of blocking ad-tracking on all your devices.
For more tips on how to put the brakes on generalized data brokers collecting information on you, see our post Advertisers sharing data about you with… intelligence agencies.
Kaspersky official blog – Read More