For a while after we wrote about hacking a bicycle, it seemed it couldn’t be beat as the most unlikely hack target ever. However, developers’ imagination seems to know no bounds — and hackers aren’t far behind in their ingenuity…
And so, here’s introducing the internet-connected mattress system — or “Pod” as it’s called — made by the company Eight Sleep, along with several ways it can be hacked as discovered by security researcher Dylan Ayrey.
Smart mattress Pod? What’s that?
Perhaps we should start by explaining what an Eight Sleep Pod is and why someone might want to buy this futuristic piece of tech. The Eight Sleep designers position their product as an “Intelligent Bed Cooling System”. The primary target audience is people with various sleep problems: insomnia, poor sleep quality, snoring, and similar issues that can significantly impact quality of life.
The Pod is made up of a sheet-like “high-tech layer” (“Cover”), and an external unit (“Hub”); optionally there’s also a motorized “Base”. It allows users to adjust the temperature of the bed — heating it up or cooling it down as instructed by the owner. It can do it automatically too — more on this later. There’s a network of tubes with water circulating through them built into it. The external unit connected to this system handles the heating and cooling. The Eight Sleep Pod is divided into two independent zones of a double-bed — each with its own settings. The temperature range is fairly broad: from 12 to 43°C.

At $4699, the Eight Sleep Pod 4 Ultra package is the most expensive version of the system made by the company Source
But wait: there’s more to it! The Pod has several dozen “clinical-grade sensors” that track users’ sleep quality. It also has vibration motors to wake you up, and sensors for ambient temperature and humidity. The ultimate version — the Pod 4 Ultra — comes with a transformable, electronically-controlled bed base.
It goes without saying that the system connects to the internet. It does this via a Wi-Fi receiver in the Hub. Eight Sleep Pods are configured and controlled almost exclusively via an app. We say “almost”, because the latest (and most expensive) generation — Pod 4 — has pressure-sensitive areas on the sides that you can tap to control certain functions.
Autopilot and sleep by subscription
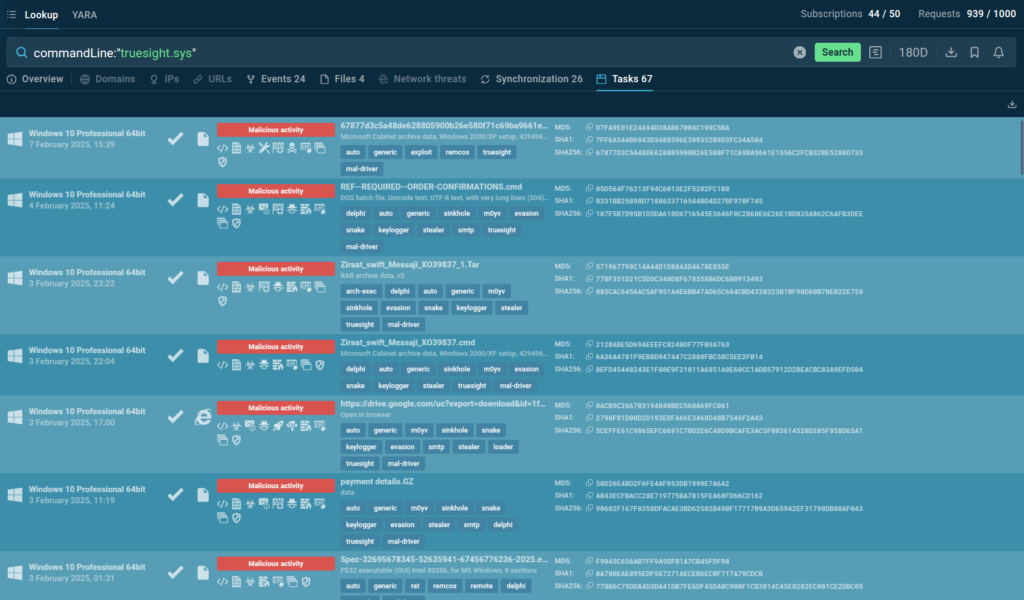
The main software component of an Eight Sleep Pod is the “Autopilot” system, which uses sensors built into the Cover to collect lots of statistics about the quality and quantity of users’ sleep, and generate detailed reports for them. In addition, Autopilot has a number of other interesting options. For example, the system can detect when the user starts snoring and change the geometry of the Base to fix the problem.

Autopilot uses vibration sensors to track snoring, and combats it by adjusting the geometry of the bed base Source
The Pod also has a physical alarm clock that wakes the user by changing the temperature of the bed and turning on vibration. However, the key Autopilot feature (and the one Eight Sleep touts the most) is, well, autopilot mode. What this does is continuously monitor the users’ sleep quality — automatically adjusting the temperature to ensure the deepest and most comfortable sleep possible.
In case you thought this was an Eight Sleep Pod ad, let’s look at this product’s numerous flaws…
To start with, these things are eye-wateringly expensive: retail prices start at $3000, and the top-of-the-line Pod 4 Ultra costs a whopping $4700.
An Autopilot subscription would set you back at least $200 per year — without it, the most exciting features simply won’t work Source
But the outlay doesn’t end there: the user will almost certainly have to pay for a subscription that costs between $200 and $300 per year. In theory, you could choose not to pay it, but without the subscription most of the smart features remain inactive.
Also, like any modern tech company, Eight Sleep constantly collects data about its users. CEO Matteo Franceschetti talks quite openly about this on X:
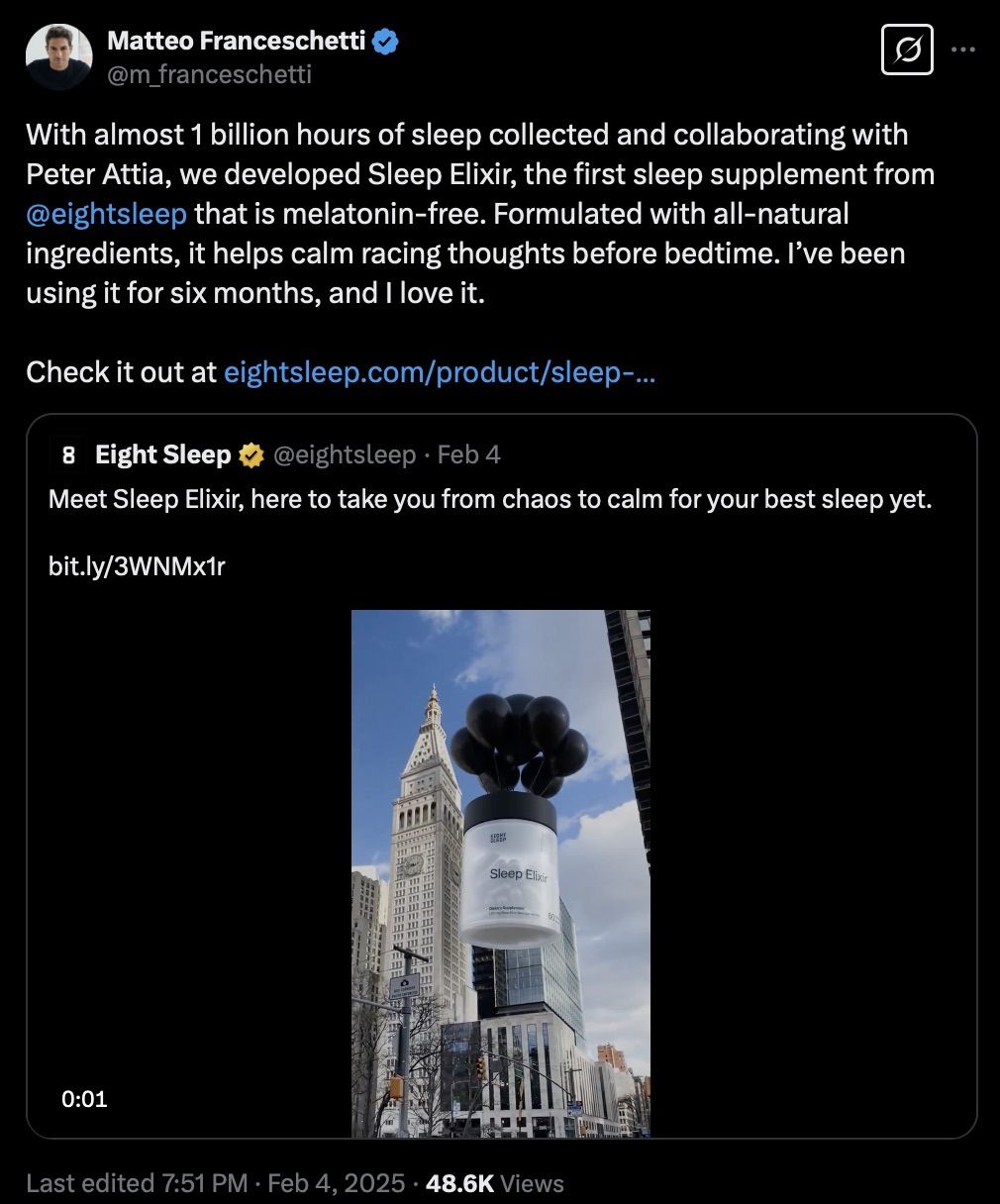
Eight Sleep has accumulated data on almost a billion hours of their users’ sleep Source
Smart mattress hack No. 1: developer backdoor
Now let’s shift the focus to why this post was written: hacking this smart-mattress system. Dylan Ayrey, a security researcher, decided to look into Eight Sleep’s security — simply out of curiosity, he said, as Dylan is the happy owner of an Eight Sleep Pod, which helps him with his insomnia.
You might remember Dylan for his other notable investigations, such as the possibility of using phantom corporate accounts uncontrollable by workspace admins, or attacking Google OAuth via abandoned domains.
To begin analyzing the Pod’s security, Ayrey needed a copy of its firmware. Security-conscious vendors don’t just give their firmware away, so trying to find a copy often becomes a quest unto itself. Not so with Eight Sleep. The update server lets anyone who follows the link download the firmware for any of the company’s Pod models, no questions asked.
While examining the code, Dylan found a number of noteworthy things, including an API for remote connection via SSH. Given that an Eight Sleep Pod is essentially a computer running Linux (as many other modern devices are), a connection like this allows running arbitrary code remotely on the mattress pad Hub.
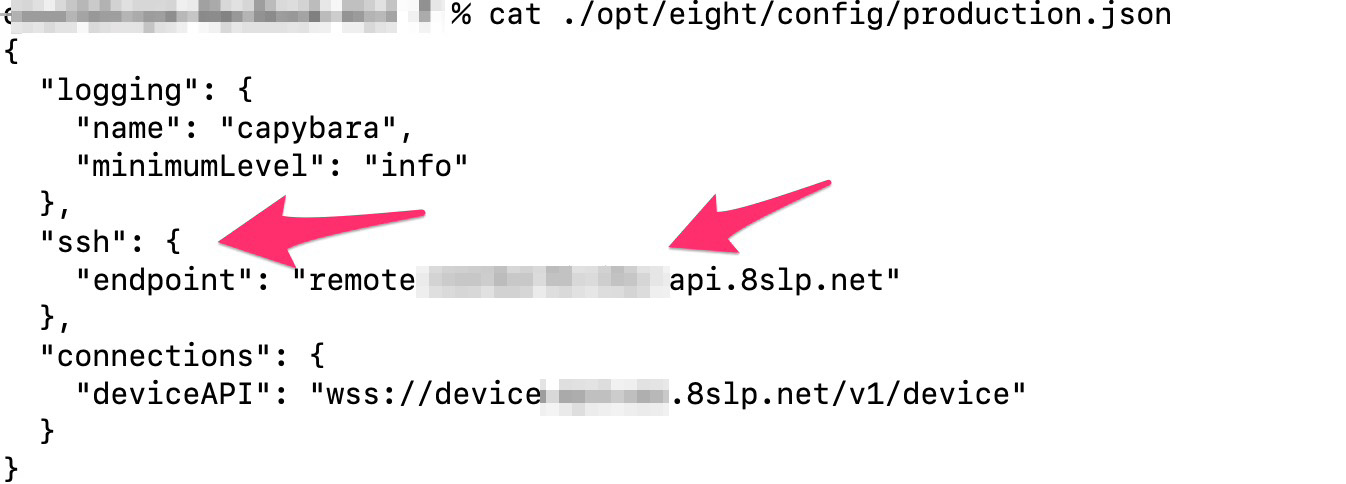
The Eight Sleep Pod firmware was found to contain an API for remote access to the smart mattress Source
Judging by the email address associated with the SSH public key found in the firmware code, all (or at least many) Eight Sleep engineers could have remote access to any Pod.
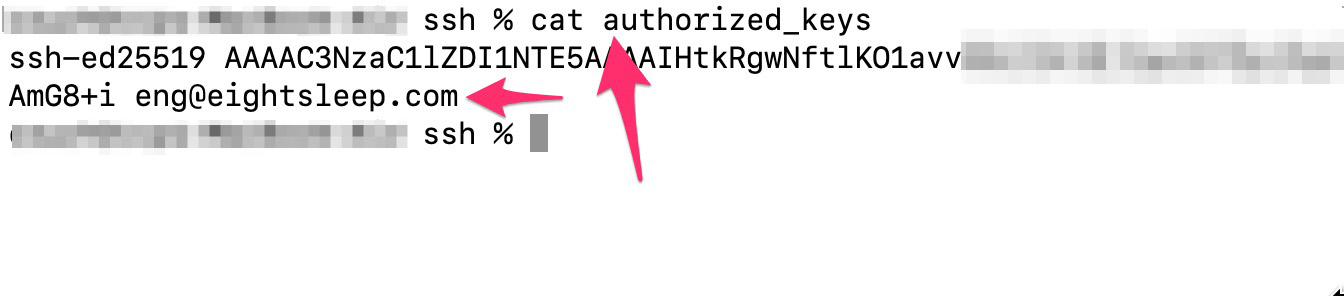
Judging by the email address associated with the SSH public key, every Eight Sleep engineer has remote access to any Pod Source
One could use an SSH connection like this to spy on the Pod’s owner — to find out when they’re sleeping or when they spend the night away from home. It would even be possible to check if there’s one person in bed or two. Having this type of control could also let someone play pranks on the owner by changing the temperature of the Pod, turning the alarm clock on or off, adjusting the geometry of the bed base, and so on.
Nothing like that seems to have happened to Eight Sleep Pod owners yet, but something like it could; theoretical possibilities like this sometimes do materialize. This is what recently happened with Ecovacs robot vacuums: pranksters used vulnerabilities in these devices to harass their owners.
Smart mattress hack No. 2: an AWS key in the firmware
While still looking at the Eight Sleep Pod firmware, Dylan discovered a valid AWS (Amazon Web Services) key in its code — used to continuously upload telemetry to the cloud. Again this is only theoretical, but if the key fell into the wrong hands it could lead to serious violations of user privacy.
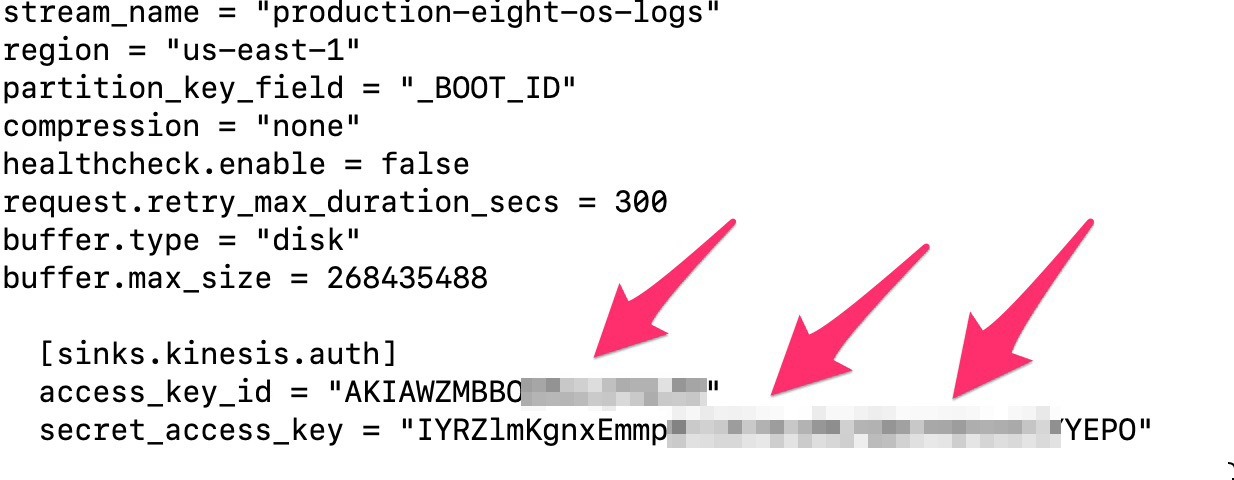
(Not the) best practices for programming smart devices: hardcoded AWS key in the firmware accessible to anyone Source
For better or for worse, the full truth about the presence of an Amazon key won’t come out. Dylan notified Eight Sleep, and by the time his research was published the key had already been revoked. However, the mere presence of the key within the firmware, where it was accessible to anyone, was clear evidence that user security and privacy were taken lightly.
Dylan further adds that the key could have, at the very least, been used to cause financial damage to the company by sending a large number of meaningless requests to the AWS cloud.
Smart mattress hack No. 3: jailbreaking with the help of an aquarium chiller
Clearly inspired by his earlier findings, Dylan decided to attempt jailbreaking the Pod — that is, detaching it from Eight Sleep’s cloud services. Dylan took a drastic approach: he disconnected the external unit (with all its smart electronics and internet connectivity).

Detaching an Eight Sleep smart mattress from the cloud using a $150 aquarium chiller Source
Dylan replaced the Eight Sleep Hub with… a common aquarium chiller. This system, in contrast, doesn’t require an app or a subscription fee, collects no user data, comes without any backdoors, and runs perfectly well without an internet connection. What it does do is effectively adjust the temperature of your bed, and, just as importantly, it costs only $150.
For those who prefer a less radical approach to the issue of Eight Sleep products being tied to the vendor cloud, Free Sleep offers a solution. This is an open-source software suite that allows you to take control of your smart mattress.
Want to know what other unexpected devices have been successfully hacked? Here you go!…
Kaspersky official blog –