Protecting against attacks in ZIP, RAR, CAB, MSI, ISO and other archives | Kaspersky official blog
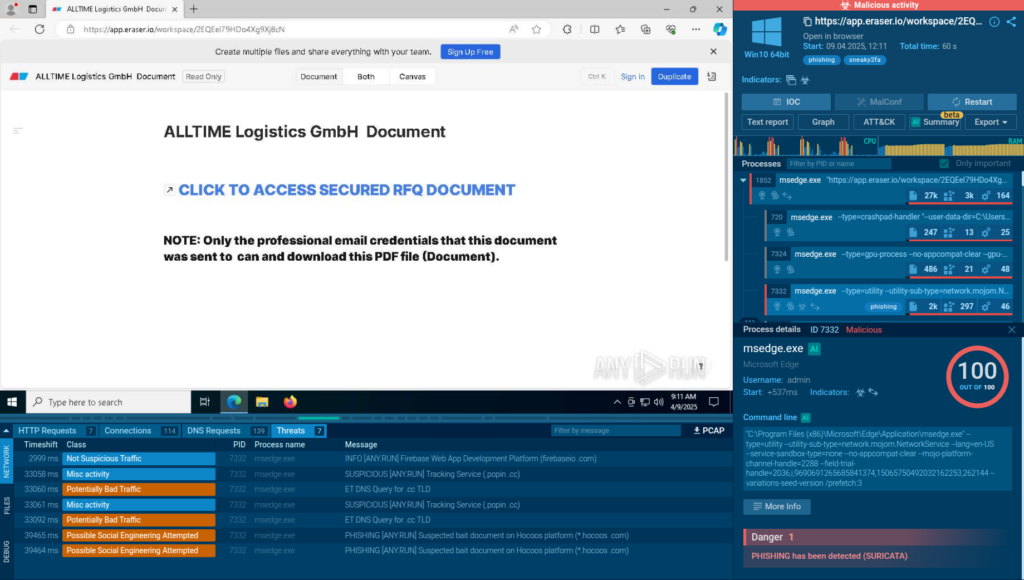
Archiving programs designed to simplify file storage and transfers have become common tools not only for users but also for attackers. Malicious archives are regularly found in both targeted attacks and ransomware incidents. Attackers mainly use them to bypass security measures, deceive users, and, of course, extract stolen data. This means cybersecurity and IT departments should pay close attention to how archives are handled in operating systems, business applications, and security tools. Let’s now look at how attackers can use archives.
Delivering malware by bypassing “Mark of the Web” warnings
Due to the logical features and vulnerabilities of certain archivers, when unpacked in Windows, the extracted files may not receive the “downloaded from the internet” attribute (Mark of the Web, or MotW). Technically, these attributes are stored in an NTFS alternate data stream: Zone.Identifier. If this identifier points to an external source (ZoneID = 3 or 4), Windows shows a warning when you attempt to run the executable file, and Office automatically opens potentially unsafe documents in Protected View.
By exploiting flaws in archivers, attackers bypass this layer of protection. The most recent vulnerability of this type is CVE-2025-31334 in WinRAR, but there are others: CVE-2025-0411 in 7-Zip, CVE-2024-8811 in WinZip, and more. Note that some archivers don’t support MotW at all, and only apply it to certain file extensions, or only do so when files are unpacked in a certain way. A table comparing MotW support in archivers is available on GitHub.
Automatic malware execution via archiver vulnerabilities
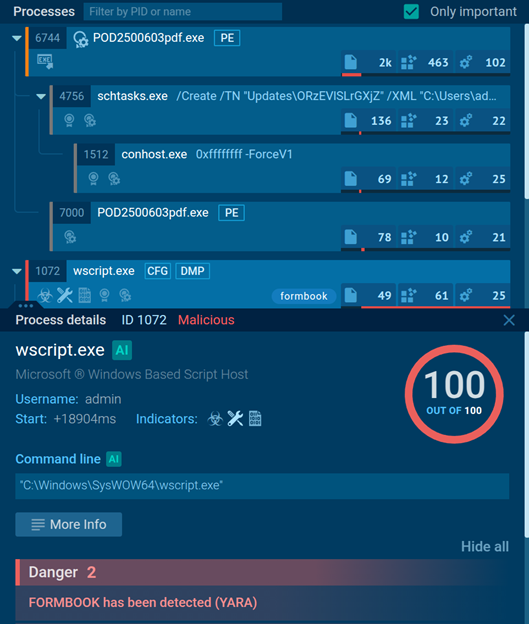
When a user performs a seemingly safe action (like viewing an archive or opening a harmless-looking file within it), under certain conditions the archiver can execute a malicious file or shellcode. A recent example of such a vulnerability was CVE-2024-11477 in the Zstandard algorithm, used by 7-Zip for compression. This flaw hasn’t been seen in real-world attacks yet — unlike CVE-2023-38831 in WinRAR, which was widely exploited by attackers ranging from APT espionage groups to initial access brokers. This WinRAR vulnerability allowed execution of a file from an archive when trying to view an image if the EXE file was placed in a folder with the same name as the image.
In March 2025, a similar defect was discovered in an unusual place — the Vim editor, popular among *nix users. Its standard tar.vim plugin lets users view and edit files directly inside TAR archives. CVE-2025-27423 allowed arbitrary shell command execution when editing a file from a malicious archive.
Server compromise via archive uploads
If an organization has a public web app that can handle archive uploads (such as attaching files to forms), vulnerabilities in archive unpacking can be used to hijack servers. A classic method is Zip Slip, which uses symbolic links in archives to bypass input sanitization and exploit path traversal vulnerabilities to compromise server-side applications. A list of various ZIP-handling libraries where this vulnerability has been patched (there are over 20 CVEs) is available on GitHub. It’s worth checking out to see how many instances of software can be affected by this flaw.
Even though Zip Slip was first described in 2018, logical flaws in server-side archive unpacking are still common — as seen in this 2025 pentest and the recent vulnerability CVE-2024-12905 in tar-fs.
Bypassing security with corrupted archives
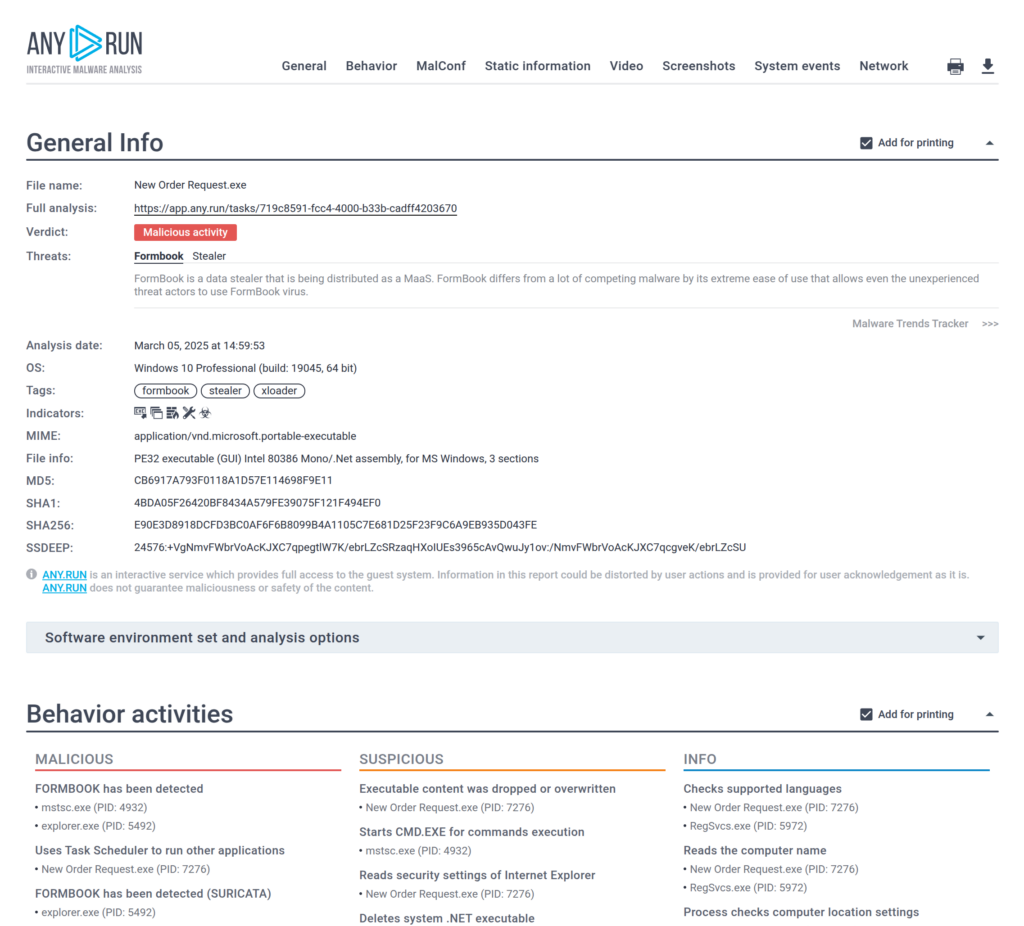
Attackers may intentionally corrupt archive contents so that automated scanners and security tools fail to analyze them fully. However, the victim can still manually recover and open the respective file with minimal effort. A recent example is the exploitation of MS Office’s “document recovery” feature — since Office files are essentially ZIP archives. Security tools and archivers may fail to scan such documents, but Word can restore and open them.
Masking malware with exotic formats
Beyond common formats like ZIP, RAR, and TAR/TAR.GZ, attackers frequently use disk image files (ISO, IMG, VHD), Windows archives (CAB, MSI), and even legacy or obscure archive types: ARJ, ACE, ICE, and others. Security tools often don’t handle these well, while modern universal archivers like WinRAR can still open them.
Disguising malware using the Matryoshka method
Mail scanners and other security tools often have configurable limits to reduce server load (for example, they may skip scanning very large files or nested archives). If an attacker creates a “matryoshka doll” (aka a “Russian doll”), of several nested archives, there’s a higher chance that the innermost archive won’t be automatically scanned in the targeted organization.
Bypassing security tools and tricking users using legitimate archive features
Attackers often combine social engineering and technical tricks to get users to perform desired actions with archives without triggering security alerts. These techniques include the following:
Encrypted archives. A classic trick from the early 2000s, which still works today. The victim receives a password-protected archive, and the password is either sent in a separate email or instant message, or hinted at within the original email itself: “The password is the current year repeated twice”. For example, this method was used in the Emotet malware campaigns.
Self-extracting archives. These were originally useful in the days before archive utilities were built into all operating systems. Today, they allow attackers to easily install malware by bundling all the necessary components into a single file. For instance, the NeedleDropper attack used a self-extracting archive to extract a popular legitimate tool, AutoIT, along with malicious AutoIT scripts, which were then executed. The attacker simply needs to trick the victim into running the archive.
A combination of the above. Some attacks use self-extracting archives that, once executed, unpack a password-protected inner archive. Technically, this password is stored within the outer archive, but few security tools can detect it there and use.
Double-extension archives. Another classic is a self-extracting archive with a “.pdf.exe” extension and an Acrobat Reader icon assigned by the archiver. For victims who are not too IT-savvy, these tricks are still convincing.
Multi-volume archives. This function was originally used to split large files across CDs, flash drives and so on. Today, this rarely-used feature is still supported by archivers. Attackers use it to divide malware among volumes, or bypass scanning entirely, as some tools are configured only to scan ZIP or RAR files, but not R01, R02, and so on.
Polyglot files. Attackers can combine different file types into a single one, so, for example, one app opens the file as a PDF and another as a ZIP archive. This works in part because technical ZIP file headers are located at the end of the file, not at the beginning. We recently covered an attack by the Head Mare group, where phishing emails contained a polyglot file made of both a malicious EXE file (with the PhantomPyramid backdoor) and a small, harmless ZIP archive. When clicked normally, it would open as a ZIP, but when launching the shortcut inside, the same polyglot file would execute as an EXE via PowerShell. Another version of the same method combines two archives in one polyglot file.
Self-extracting archives as launch tools. A more exotic variant — which has been seen in actual attacks — involves self-extracting archives that contain no actual files but include post-extraction commands to launch system tools like PowerShell or CMD, which are common in LotL attacks.
Data exfiltration
Compressing data and encrypting an archive before exiting the attacked network is well documented under MITRE ATT&CK technique T1560. Attackers use all options available: everything from basic archive tools on infected machines to popular archiving libraries built into the malware. In LotL attacks, attackers can combine techniques, using Windows utilities to collect files from other hosts and simultaneously archive them (diantz).
Protective measures when handling archives
These measures should be prioritized and adapted based on the profile of your organization, department, and role. To protect yourself:
Test your security tools with tricky cases: exotic archive formats, corrupted archives, and polyglot files. If direct testing is difficult, ask your vendor’s tech-support whether these cases are covered. At a minimum, test your mail gateway, NGFW, EDR/XDR solution, and sandbox (if it’s a separate solution). For example, in Kaspersky Secure Mail Gateway, the sandbox is an integral part of the security architecture and prevents most malicious attachments from opening.
Set up safe extraction. Ensure your security solution can scan deeply nested archives and large files. Different tools will vary in this area: while mail filters can thoroughly scan attachments and detonate them in a sandbox, NGFWs will probably just check the reputation of the archive itself and its visible files. Therefore, deeper analysis should be used on both endpoints and mail gateways, while web filters and NGFWs should apply lighter checks within their limitations. In any case, archives that exceed reasonable analysis capabilities should be blocked or quarantined.
Block dangerous archives. Uploading archives in exotic formats, as well as self-extracting archives, is rarely necessary, so this functionality can be blocked on hosts. Additionally, using trusted application management (apps allowlist, application control), you can prohibit the execution of all archivers except the one or two that are permitted and actually used within the organization. It’s important to analyze the use of built-in OS archiving tools and block those that aren’t used by employees or the IT department. Make sure that none of the approved tools for Windows machines are ones that have no support for Mark-of-the-Web (MotW).
Block automatic mounting of disk images. Although disk images are not exactly archives, attackers use them in similar ways. Usage of disk images should be disabled through group policy for all employees who don’t need it for legitimate business purposes.
Monitor the use of archivers on endpoints. Ensure that your EDR solution and monitoring tools (SIEM, XDR) have rules to help detect suspicious activity related to archives: launching files from temporary folders, launching processes from within an archiver, and so on. Monitoring is also needed to detect data theft attempts indicated by archiving data from network folders, creating password-protected archives, creating very large archives, and so on.
Restrict the use of archives in server-side applications. If uploading archived files is not a critically important business function, it’s better to disable this feature in CMS, CRM, and other online applications. Ensuring its security can be challenging. If archives are required, be sure that the folders where these archives are uploaded are monitored by an EDR agent on the server, that the server application itself is updated regularly, and that the permissions granted to the application don’t allow it to write files to any folders outside its designated directories.
Include archivers and archive-processing applications in your vulnerability management program. Archivers should be updated no less frequently than the operating system and office software.
Train employees. Cybersecurity training for employees should cover phishing as well as general rules for safe handling of archives: pay attention to any pop-ups or unexpected prompts when opening familiar file types (DOC, PDF), only extract archives using the archiving application approved by the company, and if an archive immediately prompts for a password upon clicking the file, don’t extract it under any circumstances and immediately report it to the security team.
Kaspersky official blog – Read More