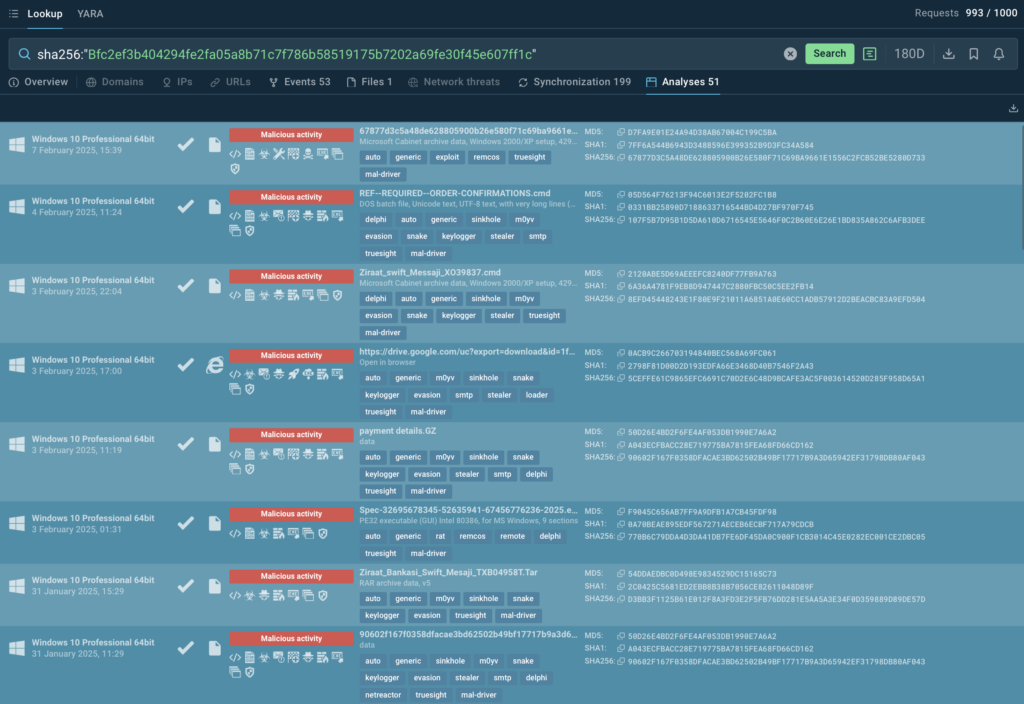
Spam campaign targeting Brazil abuses Remote Monitoring and Management tools
- Cisco Talos identified a spam campaign targeting Brazilian users with commercial remote monitoring and management (RMM) tools since at least January 2025. Talos observed the use of PDQ Connect and N-able remote access tools in this campaign.
- The spam message uses the Brazilian electronic invoice system, NF-e, as a lure to entice users into clicking hyperlinks and accessing malicious content hosted in Dropbox.
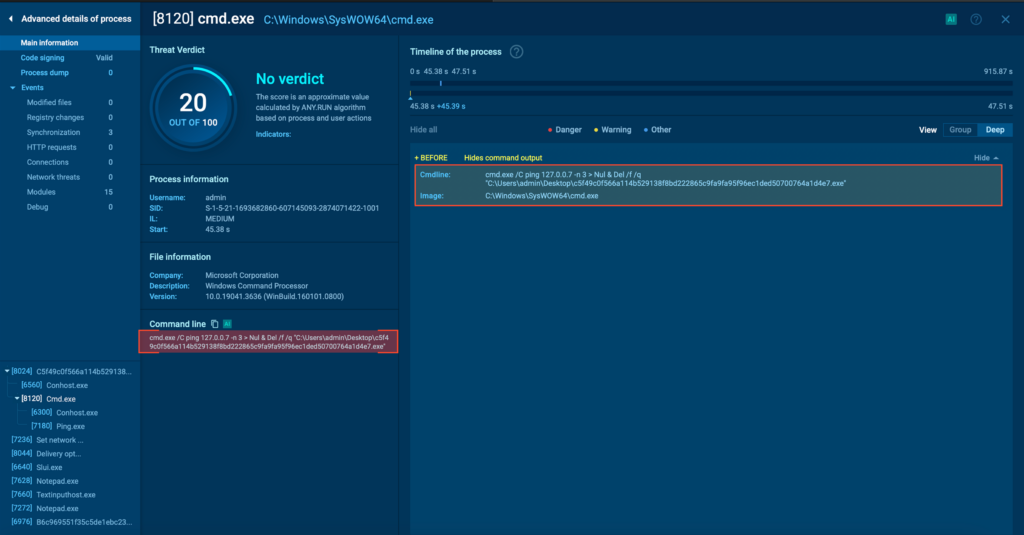
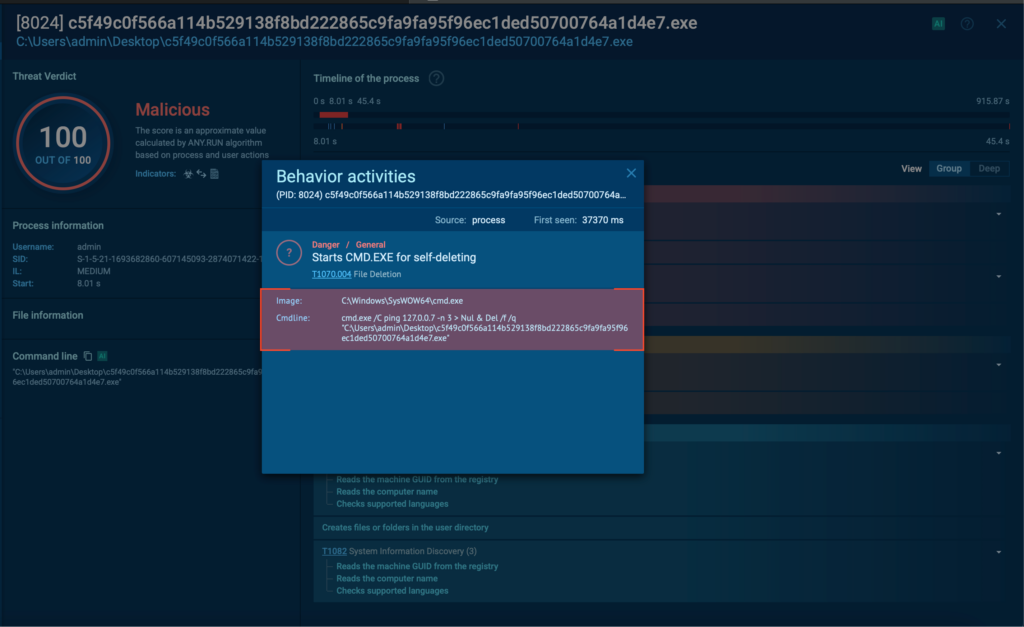
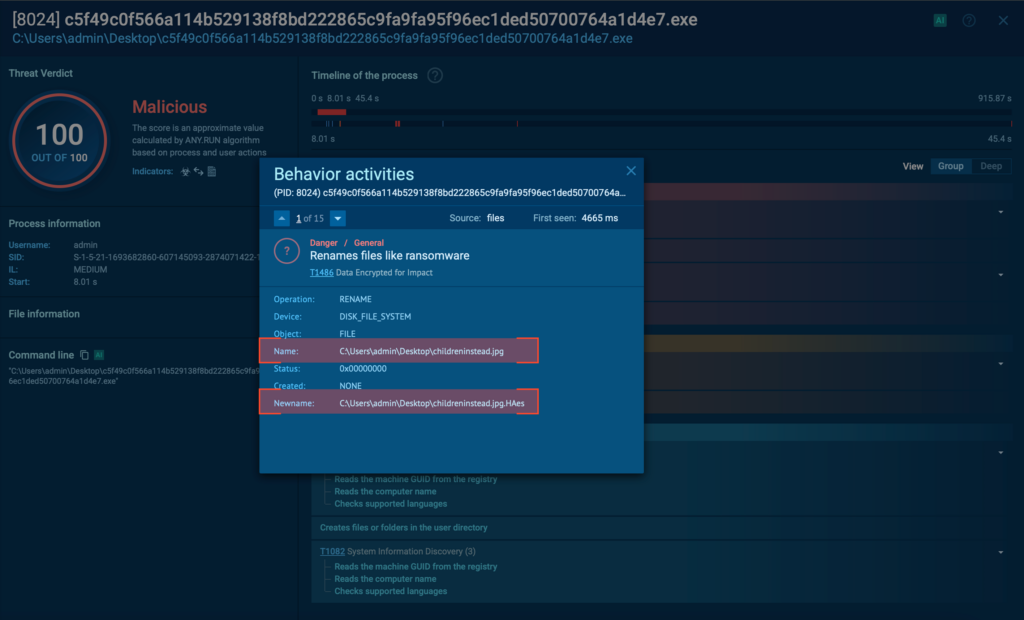
- Talos has observed the threat actor abusing RMM tools in order to create and distribute malicious agents to victims. They then use the remote capabilities of these agents to download and install Screen Connect after the initial compromise.
- Talos assesses with high confidence that the threat actor is an initial access broker (IAB) abusing the free trial periods of these RMM tools.

Talos recently observed a spam campaign targeting Portuguese-speaking users in Brazil with the intention of installing commercial remote monitoring and management (RMM) tools. The initial infection occurs via specially crafted spam messages purporting to be from financial institutions or cell phone carriers with an overdue bill or electronic receipt of payment issued as an NF-e (see Figures 1 and 2).


Both messages link to a Dropbox file, which contains the malicious binary installer for the RMM tool. The file names also contain references to NF-e in their names:
- AGENT_NFe_<random>.exe
- Boleto_NFe_<random>.exe
- Eletronica_NFe_<random>.exe
- Nf-e<random>.exe
- NFE_<random>.exe
- NOTA_FISCAL_NFe_<random>.exe
Note: <random> means the filename uses a random sequence of letters and numbers in that position.
The victims targeted in this campaign are mostly C-level executives and financial and human resources accounts across several industries, including some educational and government institutions. This assessment is based on the most common recipients found in the messages Talos observed during this campaign.

Abusing RMM tools for profit
This campaign’s objective is to lure the victims into installing an RMM tool, which allows the threat actor to take complete control of the target machine. N-able RMM Remote Access is the most common tool distributed in this campaign and is developed by N-able, Inc., previously known as SolarWinds. N-able is aware of this abuse and took action to disable the affected trial accounts. Another tool Talos observed in some cases is PDQ Connect, a similar RMM application. Both provide a 15-day free trial period.
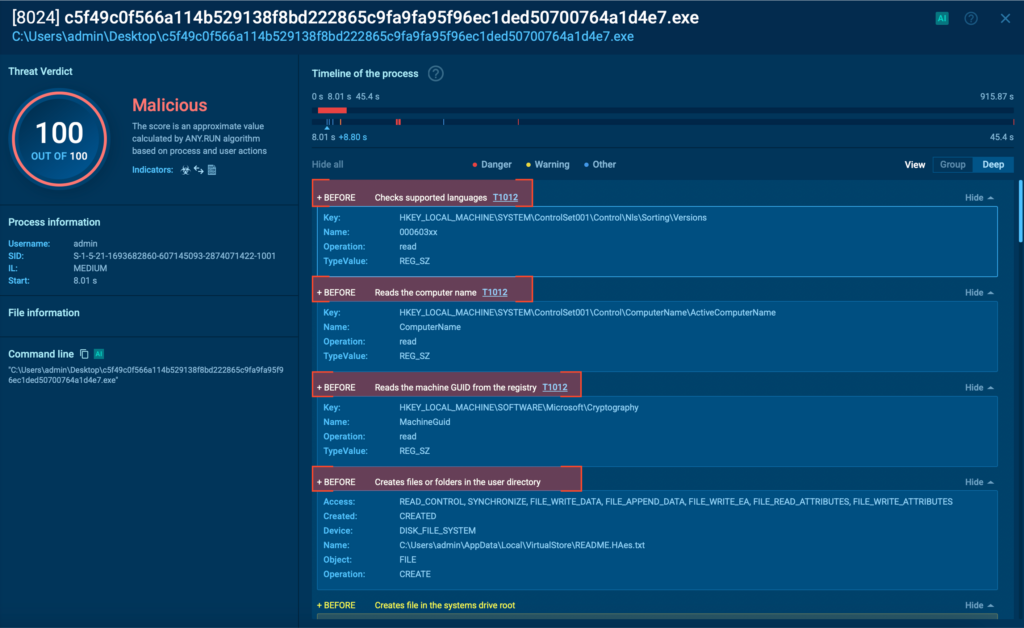
To assess whether these actors were using a trial version rather than stolen credentials to create these accounts, Talos checked samples older than 15 days and confirmed all of them returned errors that the accounts were disabled, while newer samples found in the last 15 days were all active.
Talos also examined the email accounts used to register for the service. They all use free email services such as Gmail or Proton Mail, as well as usernames following the theme of the spam campaign, with few exceptions where the threat actors used personal accounts. These exceptions are potentially compromised accounts which are being abused by the threat actors to create additional trial accounts. Talos did not find any samples in which the registered account was issued by a private company, so we can assess with high confidence these agents were created using trial accounts instead of stolen credentials.
N-able is aware of this abuse and took action to disable the affected trial accounts.
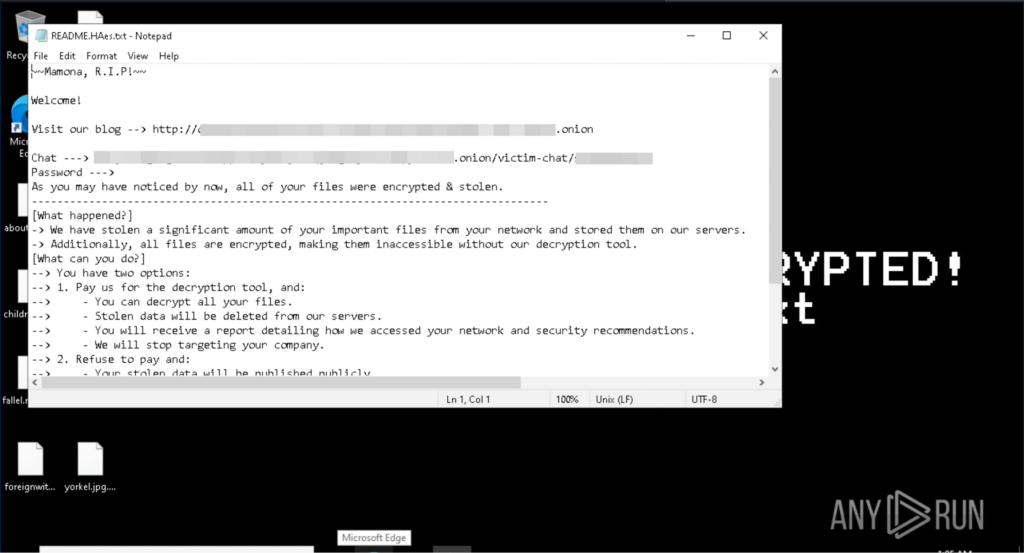
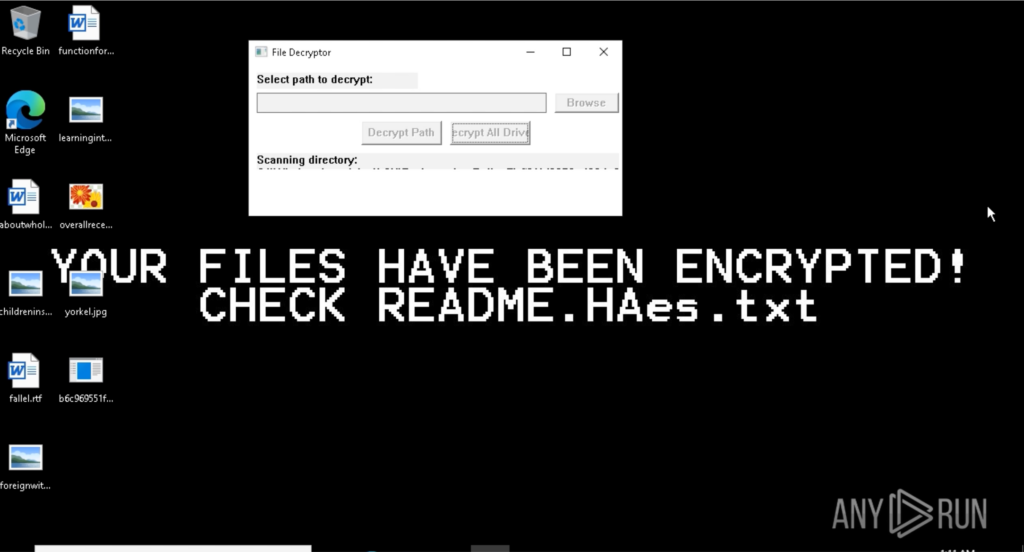
Talos found no evidence of a common post-infection behavior for the affected machines, with most machines staying infected for days before any other malicious activity was executed by the tool. However, in some cases, we observed the threat actor installing an additional RMM tool and removing all security tools from the machine a few days after the initial compromise. This is consistent with actions of initial access broker (IAB) groups.
An IAB’s main objective is to rapidly create a network of compromised machines and then sell access to the network to third parties. Threat actors commonly use IABs when looking for specific target companies to deploy ransomware on. However, IABs have varied priorities and may sell their services to any threat actors, including state-sponsored actors.
Adversaries’ abuse of commercial RMM tools has steadily increased in recent years. These tools are of interest to threat actors because they are usually digitally signed by recognized entities and are a fully featured backdoor. They also have little to no cost in software or infrastructure, as all of this is generally provided by the trial version application.
Talos created a trial account to test what features were available for a trial user. In the case of the N-able remote access tool, the trial version offers a full set of features only limited by the 15-day trial period. Talos was able to confirm that by using a trial account, the threat actor has full access to the machine, including remote desktop like access, remote command execution, screen streaming, keystroke capture and remote shell access.


The threat actor also has access to a fully featured file manager to easily read and write files to the remote file system.

The network traffic these tools create is also disguised as regular traffic, with many tools using communication over HTTPS and connecting to resources which are part of the infrastructure provided by the application provider. For example, N-able Remote Access uses a domain associated with its management interface, hosted on Amazon Web Services (AWS):
- hxxps://upload1[.]am[.]remote[.]management/
- hxxps://upload2[.]am[.]remote[.]management/
- hxxps://upload3[.]am[.]remote[.]management/
- hxxps://upload4[.]am[.]remote[.]management/
Disclaimer: The URLs above are part of the management infrastructure for the RMM tools described in this blog and are not controlled by the threat actor. Customers must complete an assessment before enabling block signatures for these domains.
The domain the agent uses is the same for any customer using the tool, with only the username and API key differentiating which customer the agent belongs to, as can be seen in Figure 7. This makes it even more difficult to identify the origin of the attacks and perform threat actor attribution.

By extracting the configuration files inside the agent installer files still available on Dropbox, we can see some email addresses follow the same theme of the spam emails, using names of finance-related users and domains, while others could be potentially compromised accounts being used to create trial accounts for N-able Remote Access.
With these trial versions being limited only by time and providing full remote-control features with little to no cost to the threat actors, Talos expects these tools to become even more common in attacks.
Cisco Secure Firewall Application control is able to detect the unintended usage of RMM tools in customer’s networks. Instructions on how to set up Application control can be found at Cisco Secure Firewall documentation.
Coverage
Ways our customers can detect and block this threat are listed below.

Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Network/Cloud Analytics (Stealthwatch/Stealthwatch Cloud) analyzes network traffic automatically and alerts users of potentially unwanted activity on every connected device.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Cisco Secure Access is a modern cloud-delivered Security Service Edge (SSE) built on Zero Trust principles. Secure Access provides seamless transparent and secure access to the internet, cloud services or private application no matter where your users work. Please contact your Cisco account representative or authorized partner if you are interested in a free trial of Cisco Secure Access.
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
ClamAV detections are also available for this threat:
Txt.Backdoor.NableRemoteAccessConfig-10044370-0
Txt.Backdoor.NableRemoteAccessConfig-10044371-0
Txt.Backdoor.NableRemoteAccessConfig-10044372-0
Indicators of Compromise
Disclaimer: The URLs below are part of the management infrastructure for the RMM tools described in this blog and are not controlled by the threat actor. An assessment must be done by customers before enabling block signatures for these domains.
IOCs for this threat can be found on our GitHub repository here.
Network IOCs
hxxps://upload1[.]am[.]remote[.]management/
hxxps://upload2[.]am[.]remote[.]management/
hxxps://upload3[.]am[.]remote[.]management/
hxxps://upload4[.]am[.]remote[.]management/
198[.]45[.]54[.]34[.]bc[.]googleusercontent[.]com
RMM Installer – Hashes
03b5c76ad07987cfa3236eae5f8a5d42cef228dda22b392c40236872b512684e
0759b628512b4eaabc6c3118012dd29f880e77d2af2feca01127a6fcf2fbbf10
080e29e52a87d0e0e39eca5591d7185ff024367ddaded3e3fd26d3dbdb096a39
0de612ea433676f12731da515cb16df0f98817b45b5ebc9bbf121d0b9e59c412
1182b8e97daf59ad5abd1cb4b514436249dd4d36b4f3589b939d053f1de8fe23
14c1cb13ffc67b222b42095a2e9ec9476f101e3a57246a1c33912d8fe3297878
2850a346ecb7aebee3320ed7160f21a744e38f2d1a76c54f44c892ffc5c4ab77
4787df4eea91d9ceb9e25d9eb7373d79a0df4a5320411d7435f9a6621da2fd6b
51fa1d7b95831a6263bf260df8044f77812c68a9b720dad7379ae96200b065dd
527a40f5f73aeb663c7186db6e8236eec6f61fa04923cde560ebcd107911c9ff
57a90105ad2023b76e357cf42ba01c5ca696d80a82f87b54aea58c4e0db8d683
63cde9758f9209f15ee4068b11419fead501731b12777169d89ebb34063467ea
79b041cedef44253fdda8a66b54bdd450605f01bbb77ea87da31450a9b4d2b63
a2c17f5c7acb05af81d4554e5080f5ed40b10e3988e96b4d05c4ee3e6237c31a
b53f9c2802a0846fc805c03798b36391c444ab5ea88dc2b36bffc908edc1f589
c484d3394b32e3c7544414774c717ebc0ce4d04ca75a00e93f4fb04b9b48ecef
ca11eb7b9341b88da855a536b0741ed3155e80fc1ab60d89600b58a4b80d63a5
d1efebcca578357ea7af582d3860fa6c357d203e483e6be3d6f9592265f3b41c
e2171735f02f212c90856e9259ff7abc699c3efb55eeb5b61e72e92bea96f99c
e34b8c9798b92f6a0e2ca9853adce299b1bf425dedb29f1266254ac3a15c87cd
ebdefa6f88e459555844d3d9c13a4d7908c272128f65a12df4fb82f1aeab139f
f52b4d81c73520fd25a2cc9c6e0e364b57396e0bb782187caf7c1e49693bebbf
f5efd939372f869750e6f929026b7b5d046c5dad2f6bd703ff1b2089738b4d9c
F68ae2c1d42d1b95e3829f08a516fb1695f75679fcfe0046e3e14890460191cf
a71e274fc3086de4c22e68ed1a58567ab63790cc47cd2e04367e843408b9a065
Cisco Talos Blog – Read More