Unmasking AsyncRAT: Navigating the labyrinth of forks
ESET researchers map out the labyrinthine relationships among the vast hierarchy of AsyncRAT variants
WeLiveSecurity – Read More
ESET researchers map out the labyrinthine relationships among the vast hierarchy of AsyncRAT variants
WeLiveSecurity – Read More
This year marks the 20th anniversary of the Common Vulnerability Scoring System (CVSS), which has become a widely accepted standard for describing software vulnerabilities. Despite decades of use and four generations of the standard — now at version 4.0 — CVSS scoring rules continue to be misused, and the system itself remains the subject of intense debate. So, what do you need to know about CVSS to effectively protect your IT assets?
According to its developers, CVSS is a tool for describing the characteristics and severity of software vulnerabilities. CVSS is maintained by the Forum of Incident Response and Security Teams (FIRST). It was created to help experts speak a common language about vulnerabilities, and to facilitate automatic processing of data on software flaws. Almost every vulnerability published in major vulnerability registries like CVE, EUVD, or CNNVD includes a severity assessment based on the CVSS scale.
An assessment typically consists of two main parts:
Here’s an example using the highly severe and actively exploited vulnerability CVE-2021-44228 (Log4Shell): Base Score 10.0 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H)
Let’s break that down: the attack vector is network-based, attack complexity is low, privileges required: none, user interaction isn’t required, the scope indicates the vulnerability impacts other system components, and the impact on confidentiality, integrity, and availability is high. Detailed descriptions of each component are available in the CVSS 3.1 and CVSS 4.0 specifications.
A crucial part of the CVSS system is its scoring methodology — also known as the calculator, and available for both 4.0 and 3.1. By filling in all the vector components, you can automatically get a numerical criticality score.
The original CVSS calculation methodology included three metric groups: Base, Temporal, and Environmental. The first group covers the fundamental and unchanging characteristics of a vulnerability, and forms the basis for calculating the CVSS Base Score. The second group includes characteristics that can change over time — such as the availability of published exploit code. The third group is designed for internal organizational use to account for context-specific factors like the vulnerable application’s scope or the presence of mitigating security controls in the organization’s infrastructure. In CVSS 4.0, the Temporal metrics have evolved into Threat metrics, and a new group of Supplemental metrics has been introduced.
Here’s how the metrics are interconnected. Software vendors or cybersecurity companies typically assess the Base criticality of a vulnerability (referred to as “CVSS-B” in the 4.0 specification). They also often provide an assessment related to the availability and public disclosure of an exploit (CVSS-BT in 4.0, and Temporal in 3.1). This assessment is a modified Base Score; therefore CVSS-B can be higher or lower than CVSS-BT. As for the Environmental score (CVSS-BTE), it’s calculated within a specific organization based on the CVSS-BT, with adjustments made for their unique conditions of using the vulnerable software.
The first two versions of CVSS, released in 2005 and 2007, are hardly used today. While you might still find older CVSS scores for modern vulnerabilities, CVSS 3.1 (2019) and CVSS 4.0 (2023) are the most common scoring systems. However, many software vendors and vulnerability registries aren’t in a rush to adopt version 4.0, and they continue to provide CVSS 3.1 scores.
The core idea behind the first CVSS version was to quantify the severity of vulnerabilities via a scoring system — with an initial separation into Base, Temporal, and Environmental metrics. At that stage, the textual descriptions were loosely formalized, and the three groups of metrics were calculated independently.
CVSS 2.0 introduced a standardized vector string and a new logic: a mandatory and unchangeable Base score, a Temporal score calculated from the Base score but accounting for changing factors, and an Environmental score used within specific organizations and conditions derived from either the Base or Temporal score.
Versions 3.0 and 3.1 added the concept of Scope (impact on other system components). They also more precisely defined parameters related to required privileges and user interaction, and they generalized and refined the values of many parameters. Most importantly, these versions attempted to solidify the fact that CVSS measures the severity of a vulnerability — not the risks it creates.
In version 4.0, the creators aimed to make the CVSS metric more useful for business-level assessments of how vulnerabilities impact risk. This is still not a risk metric, though. Attack complexity was split into two distinct components: attack requirements and attack complexity. This highlights the difference between the inherent engineering difficulty of an attack and the external factors or conditions necessary for the attack to succeed. In practical terms, this means a flaw that requires a specific, non-default configuration on the vulnerable product to be exploited will have higher attack requirements and, consequently, a lower overall CVSS score.
The often-misunderstood Scope metric, which simply offered “yes” or “no” options for “impact on other components”, has been replaced. Developers have introduced the clearer concept of “subsequent systems”, which now specifies what aspect of their operation the vulnerability affects. Additionally, a range of supporting indicators has been added — such as the automatability of an exploit and the impact of exploitation on human physical safety. The formulas themselves have also undergone substantial revisions. The influence of various components on the numerical threat score has been re-evaluated based on a vast database of vulnerabilities and real-world exploitation data.
For cybersecurity professionals, CVSS 4.0 aims to be more practical and relevant to today’s realities. We’re facing tens of thousands of vulnerabilities — many of which receive a high CVSS score. This often leads to them being automatically flagged for immediate remediation in many organizations. The problem is, these lists are constantly growing, and the average time to fix a vulnerability is nearing seven months.
When vulnerabilities are re-evaluated from CVSS 3.1 to CVSS 4.0, the Base Score for defects with a severity between 4.0 and 9.0 tends to slightly increase. However, for vulnerabilities that were considered critically severe in CVSS 3.1, the score often remains unchanged or even decreases. More importantly, while Temporal metrics had little impact on a vulnerability’s numerical rating before, the influence of Threat and Environmental metrics is now much more significant. Orange Cyberdefense conducted a study to illustrate this. Imagine a company is tracking 8000 vulnerabilities, and their IT and security teams are required to fix all defects with a Base CVSS score above 8 within a specified timeframe. What percentage of these 8000 real-world vulnerabilities would fall into that category — with or without considering exposure of the exploit to the public (Temporal/Threat adjustment)? The study found that CVSS 4.0, in its base version, assigns a score of 8 or higher to a larger percentage of vulnerabilities (33% compared to 18% in version 3.1). However, when adjusted for the availability of exploits, this number drops significantly — leaving fewer truly critical flaws to prioritize (8% versus 10%).
What’s the difference between a “critical” vulnerability and one that’s just plain dangerous? A text-based severity description is part of the specification — but it’s not always required in a vulnerability description:
In practice, many software vendors take a creative approach to these text descriptions. They might modify the names or incorporate their own assessments and factors not included in CVSS. A case in point is June’s Microsoft Patch Tuesday — specifically CVE-2025-33064 and CVE-2025-32710. The first is described as “Important” and the second as “Critical”, yet their CVSS 3.1 scores are 8.8 and 8.1, respectively.
Kaspersky official blog – Read More
Editor’s note: The current article was originally published on April 10, 2024, and updated on July 15, 2025.
Modern cybersecurity teams face growing pressure: more threats, tighter SLAs, and less time to investigate. The difference between fast containment and a damaging breach often comes down to visibility, collaboration, and control.
ANY.RUN’s Enterprise plan is a complete malware analysis plan built for organizations that can’t afford to miss a threat. It combines interactive sandboxing, robust privacy settings, centralized team management, and flexible integrations.
It provides SOCs with the full picture of every threat, helping them respond quickly and accurately, no matter the size or sector of your organization.
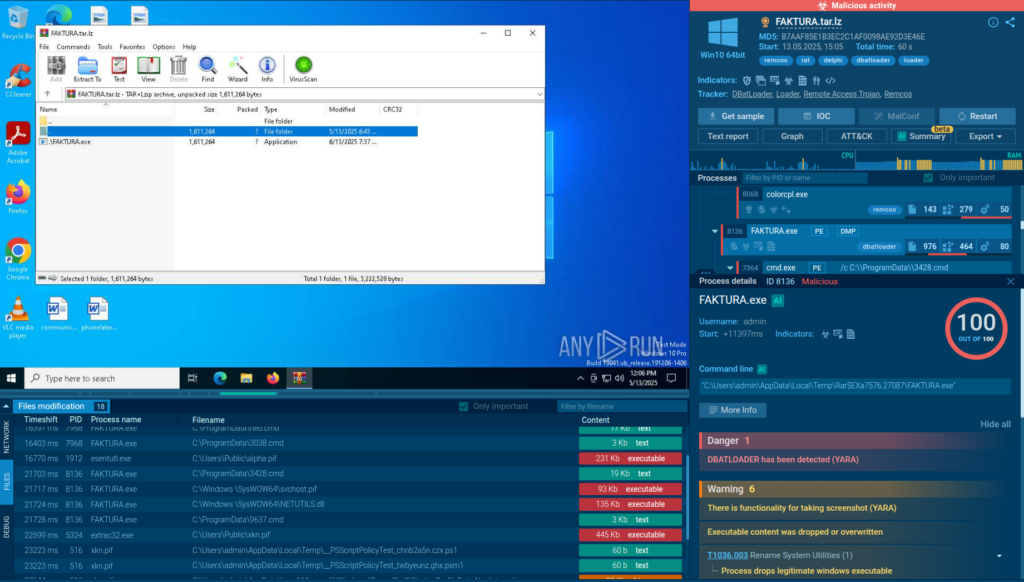
Enterprise gives security teams all the essentials in a single, unified solution—from threat visibility and secure collaboration to automation and ecosystem integration. With a setup designed to fit into existing workflows, it removes bottlenecks and accelerates decision-making at every stage of investigation.
ANY.RUN helps teams cut through alert noise, validate threats faster, and stay ahead of what’s coming next.
 Enterprise Plan:
Enterprise Plan:ANY.RUN’s Enterprise plan is trusted by leading organizations to solve real problems, streamline operations, and stay ahead of threats.
From managed security providers to financial institutions, more than 15,000 organizations around the world use Enterprise to improve visibility, accelerate response, and strengthen their security posture.
Expertware, a leading European IT consultancy, needed to accelerate investigations, reduce manual overhead, and deliver faster results to clients. With Enterprise, they achieved a 50% reduction in malware investigation turnaround time.
By replacing time-consuming manual setups with interactive sandboxing, Expertware improved visibility into complex threats, streamlined collaboration across their SOC, and scaled operations without adding overhead.
Besides the faster investigation, Expertware achieved:
A Brussels-based investment bank adopted ANY.RUN’s Enterprise plan to overhaul its overloaded cybersecurity operations. Facing constant phishing and ransomware threats, their lean SOC team needed a solution that could speed up investigations, enhance visibility, and reduce manual work.
With ANY.RUN, they replaced slow, manual triage processes with interactive sandboxing and automated analysis, allowing them to detect and contain attacks faster, without adding headcount.
The combination of speed and knowledge allowed us to identify and prevent cyber attacks better than ever before.
Head of Cybersecurity, EU-based investment bank
Key improvements after adopting the Enterprise plan:
ANY.RUN became a central part of their modernized SOC, delivering speed, visibility, and control without increasing complexity.
In threat investigations, privacy plays an important role. A single public task launched by mistake can expose sensitive data, damage trust, or break compliance. The Enterprise plan helps your team avoid those risks with flexible private analysis options, role-based visibility controls, and secure access through SSO.
Enterprise customers can choose the model that fits their team structure best:
This flexibility makes sure your investigations stay private, without limiting your team’s ability to scale or collaborate.
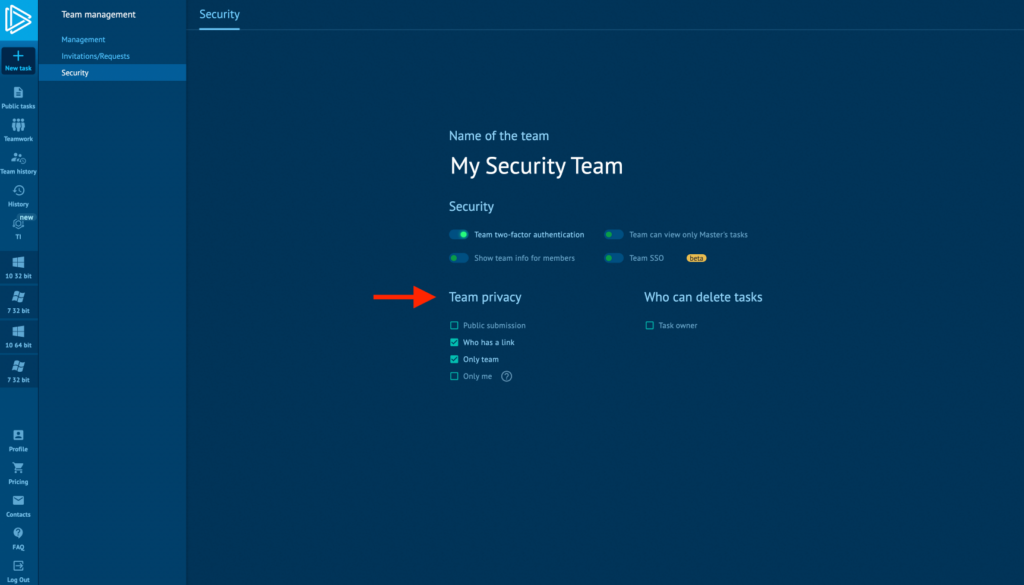
You can control each user’s access to the sandbox, including the default privacy level of their analyses; whether tasks are visible only to the user, shared with the team, or accessible via a link. Team masters can define what analysts are allowed to share and ensure sensitive investigations aren’t exposed by mistake.
In large or distributed teams, one misconfigured setting can lead to accidental data leaks. Granular privacy controls help reduce that risk by enforcing visibility rules at the user level, keeping your analysis environment secure without slowing your team down.
Let us show you how ANY.RUN can help your SOC team – book a call with us 
For busy security teams, managing multiple logins can slow things down, and increase risk. With Single Sign-On (SSO) in the Enterprise plan, your team can log in to ANY.RUN using the same credentials they use across the rest of your organization.
That means:
SSO helps your SOC stay efficient and secure, giving every team member fast, reliable access to the sandbox, without extra friction. It also reduces the chance of human error, making it easier to stay compliant with internal policies and external standards.
Automated Interactivity, powered by machine learning, enables security teams to automate file/URL analysis by letting the sandbox simulate human actions to outsmart evasion tactics like CAPTCHAs and redirects. Available exclusively in Enterprise plan, it gives a massive boost to SOC efficiency by automating detonation of attacks and accelerating threat detection.
It identifies and detonates malicious content, such as email attachments, payloads inside archives, URLs in QR codes. Thanks to this feature, your SOC team can reduce workload, improve the detection rate and alert processing capabilities, while focusing on critical incidents only.
This sandbox has provided features we didn’t have previously and helps to make the team more efficient
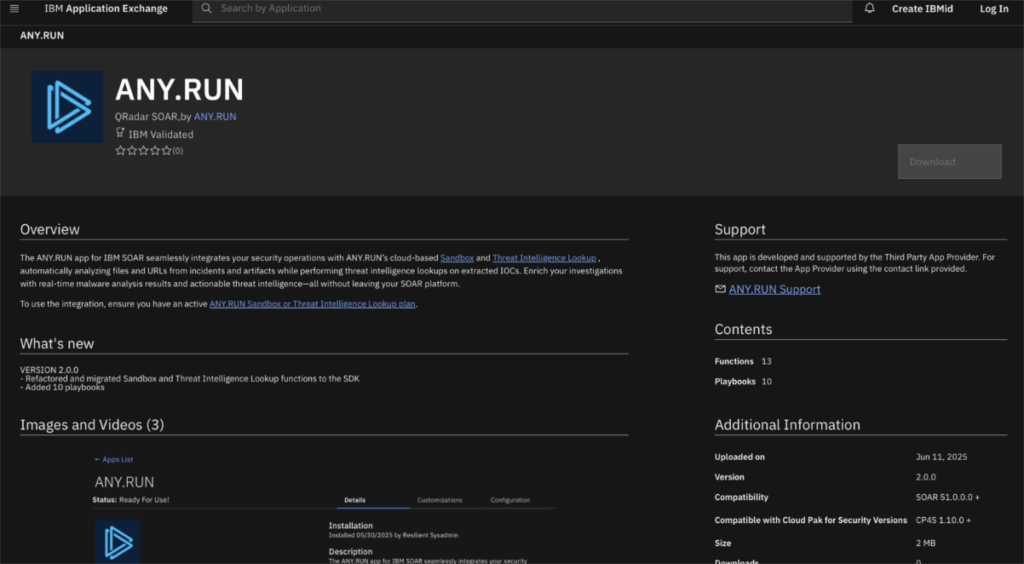
The Enterprise plan gives your team full access to API and SDK integrations, so you can embed ANY.RUN directly into your existing workflows, automate routine tasks, and enrich investigations with real-time behavioral data.
Whether you use a SIEM, SOAR, or case management platform, ANY.RUN connects seamlessly, helping analysts cut down on manual effort and focus on what matters most.

One of our latest integrations is with IBM QRadar SOAR, a popular platform for incident response. With ANY.RUN’s official app, teams can:
Setup takes minutes; just plug in your API key and get started.
With integrations like this, ANY.RUN becomes a natural part of your security workflow, helping your team move faster, stay aligned, and act with greater precision.
Even the most advanced tools fall short when teams can’t work together effectively. In many SOCs, analysts work in silos, communication breaks down, and duplicated work or missed alerts slow down investigations.
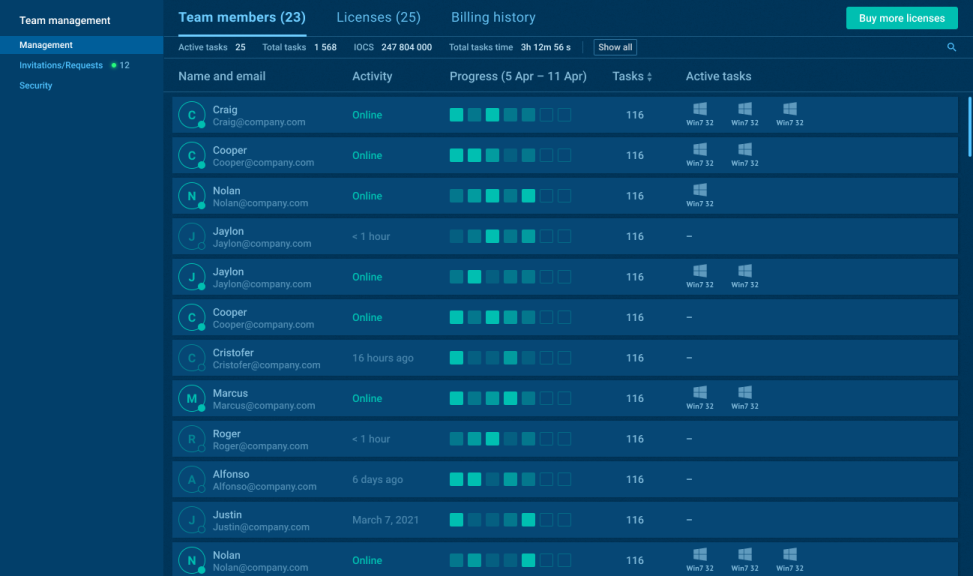
The Teamwork feature in Enterprise makes collaboration seamless, whether your team sits in the same room or operates across time zones. Analysts can join a shared workspace, while team leads assign roles, track progress, and manage licenses, all from one central interface.
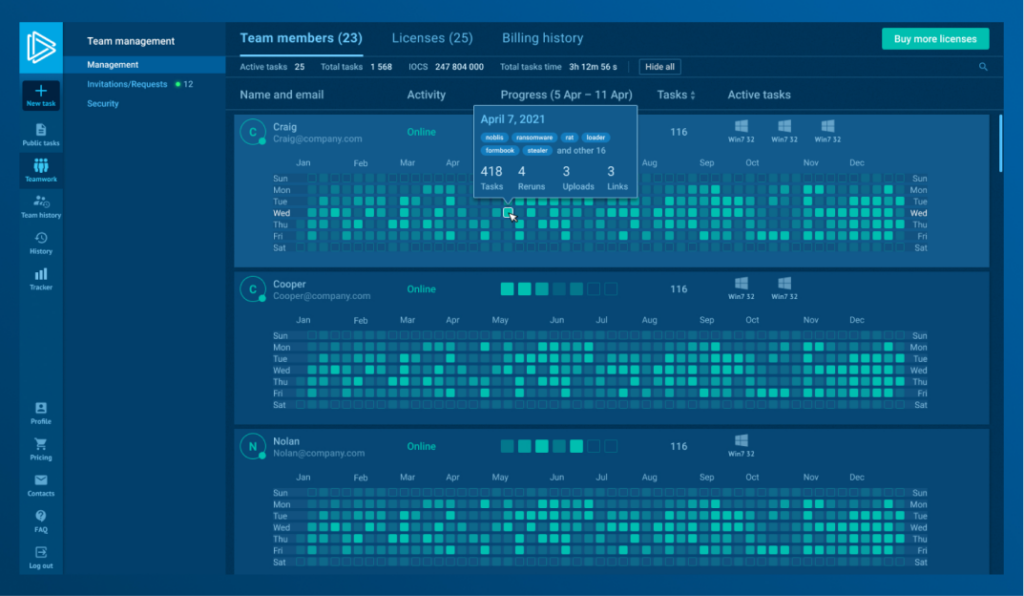
When every analyst knows what to focus on, and team leads can oversee without micromanaging, you reduce delays, avoid duplication, and build a stronger response process.
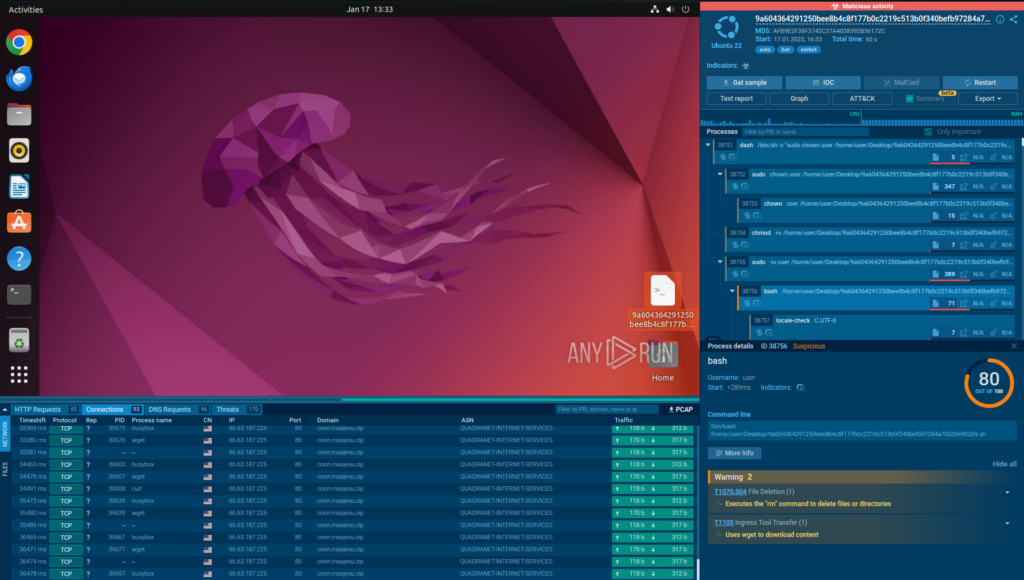
The Enterprise plan gives your analysts the technical depth and flexibility to run more realistic, multi-stage investigations and uncover even the most evasive threats.
These capabilities make Enterprise more practical for real-world, high-stakes investigations that demand clarity, completeness, and context.
ANY.RUN is consistently rated as a leading solution on major platforms.
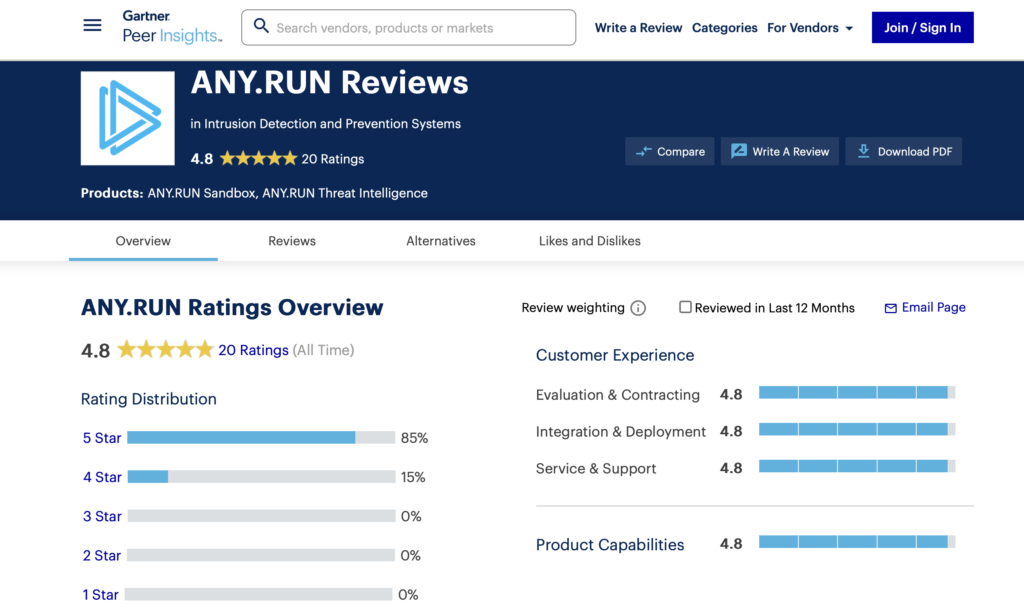
From MSSPs to financial institutions, teams around the world choose ANY.RUN to investigate faster, detect smarter, and simplify their daily workflows. These ratings reflect what thousands of users already know: interactive analysis makes all the difference.
Teams using ANY.RUN’s Interactive Sandbox also utilize advanced Threat Intelligence solutions that help you enrich your security, from detection to prevention.
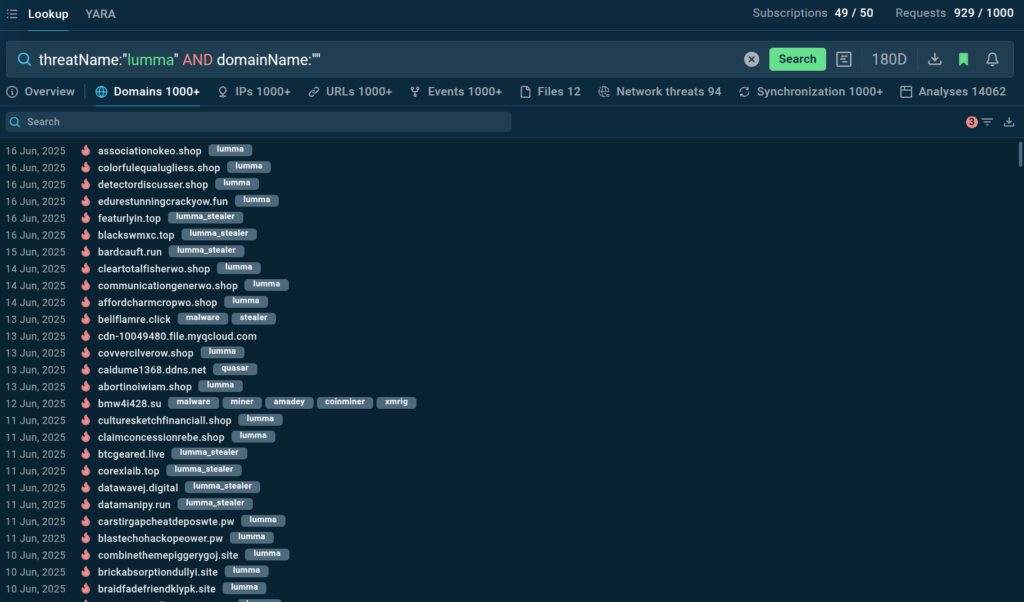
Quickly assess suspicious IPs, domains, hashes, and URLs with real-time context from live sandbox detonations across 15,000 organizations. TI Lookup lets you uses over 40 behavioral and static indicators to help SOC teams make faster decisions, reduce false positives, and respond to threats before they escalate, minimizing business risk and cutting investigation time.
Explore Threat Intelligence Lookup
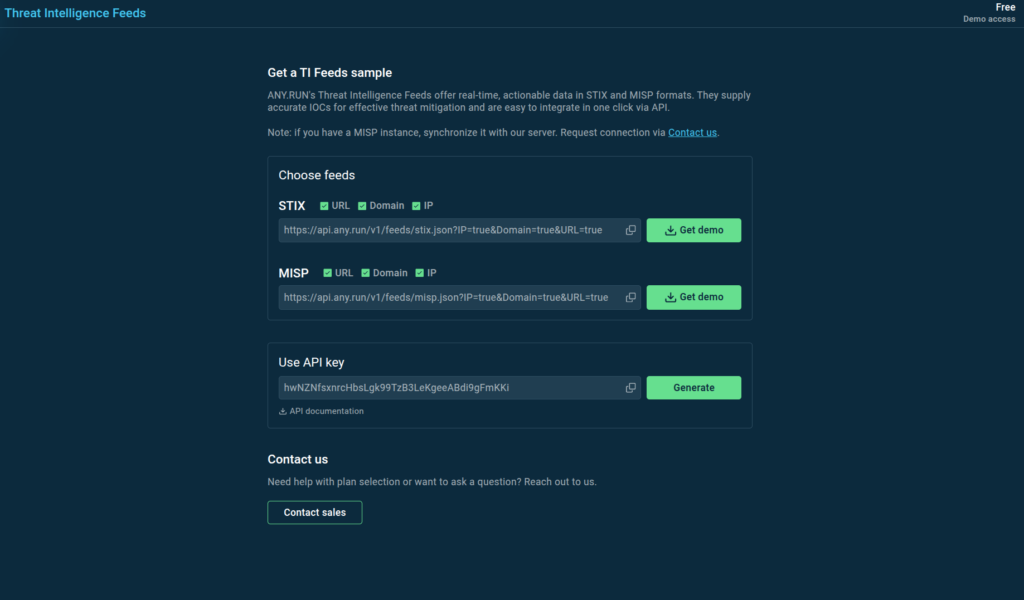
Receive continuously updated network indicators pulled from the latest malware samples analyzed in our sandbox. ANY.RUN’s TI Feeds help you proactively block threats and improve detection rules across your entire security stack.
Explore Threat Intelligence Feeds
Designed to accelerate threat detection and improve response times, ANY.RUN equips teams with interactive malware analysis capabilities and real-time threat intelligence.
ANY.RUN’s cloud-based sandbox supports investigations across Windows, Linux, and Android environments. Combined with Threat Intelligence Lookup and Feeds, our solutions give security teams full behavioral visibility, context-rich IOCs, and automation-ready outputs, all with zero infrastructure overhead.
Ready to see how ANY.RUN’s services can power your SOC?
The post Enterprise Plan: Boost SOC Performance, Reduce Business Risks with ANY.RUN appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
Many companies today operate a Bring Your Own Device (BYOD) policy, allowing employees to use their own devices for work purposes. This practice is especially prevalent in organizations that embrace remote working. BYOD brings many obvious advantages, but its implementation creates new risks for companies in terms of cybersecurity.
To protect systems from threats, information security departments often require that security software is installed on all devices used for work. At the same time, some employees – especially hotshot techies – may view antivirus software more as a hindrance than a help.
Not the most sensible attitude for sure, but convincing them otherwise can be hard. The main problem is that employees who believe they know better may find a way to dupe the system. Today, we investigate one such method: a new research tool known as Defendnot, which disables Microsoft Defender on Windows devices by registering fake antivirus software.
To understand exactly how Defendnot disables Microsoft Defender, we need to turn the clock back a year. Back then, a researcher with the X handle es3n1n created and published the first version of the tool on GitHub. Called no-defender, it was tasked with disabling the built-in Windows Defender antivirus.
To accomplish this task, es3n1n exploited a weakness in the Windows Security Center (WSC) API. Through it, antivirus software informs the system that it is installed and ready to start protecting the device in real time. Upon receiving such a message, Windows automatically disables Microsoft Defender to avoid conflicts between different security solutions all running on the same device.
Using the code of an existing security solution, the researcher created their own fake antivirus that registered in the system and passed all Windows checks. Once Microsoft Defender was disabled, the device was left unprotected – since no-defender offered no protection of its own.
The no-defender project quickly drew a following on GitHub, where it was starred over two thousand times. However, the antivirus developer company whose code was reused filed a complaint for violation of the Digital Millennium Copyright Act (DMCA). So es3n1n was forced to remove the project code from GitHub, leaving only a description page.
But the story doesn’t end there. Almost a year later, New Zealand programmer MrBruh prompted es3n1n into developing a version of no-defender that didn’t rely on third-party code. Piqued by the challenge and poor sleep, es3n1n wrote a new tool in four days flat, which was dubbed Defendnot.
At the heart of Defendnot was a stub DLL posing as a legitimate antivirus. To bypass all WSC API checks – including Protected Process Light (PPL), digital signatures and other mechanisms – Defendnot injects its DLL into Taskmgr.exe, which is signed and already considered as trusted by Microsoft. The tool then registers the fake antivirus, prompting Microsoft Defender to immediately turn off and leave the device without active protection.
On top of that, Defendnot allows the user to assign any name to the “antivirus”. Similarly to its predecessor, this project became a hit on GitHub, having been starred 2100 times at the time of writing. To install Defendnot, the user must have administrator rights (which employees most likely have on personal devices).
Defendnot and no-defender are positioned as research projects, with both tools demonstrating how trusted system mechanisms can be manipulated to disable protective functions. The conclusion is obvious: you can’t always trust what Windows says.
Therefore, so as not to endanger your company’s digital infrastructure, we recommend beefing up its BYOD policy with a number of additional security measures:
Kaspersky official blog – Read More
Fake text messages pretending to be from banks, delivery services, or municipal agencies are scammers’ tactic of choice to trick people into revealing financial information and passwords. This type of phishing is often referred to as “smishing” (from “SMS phishing”). While nearly every carrier filters dangerous text messages, and only a fraction reach recipients, scammers have come up with something new. Over the past year, criminals have been arrested in the UK, Thailand, and New Zealand for sending messages that bypassed carrier networks and went directly to victims’ phones. This technology is known as “SMS blasting”.
An SMS blaster pretends to be a cellular base station. About the size of an old computer tower, it bristles with antennas. Scammers often stash it in the trunk of a car or even in a backpack. Once activated, the blaster prompts all nearby phones to connect to it, as it appears to be the most powerful base station with the best signal. When a phone connects, it receives a fake SMS. Depending on the blaster model and reception conditions, the SMS broadcast range is between around 500 and 2000 meters. This is why criminals prefer to operate in crowded areas like shopping malls, or tourist and business centers: these are where all known attacks have been recorded. What’s more, the tech the scammers use provides them with all sorts of tricks: they don’t pay for the messages, they can spoof any sender, and they’re free to include any links at all; they don’t even need to know victims’ phone numbers: any phone will receive a message if it connects to the fake cell tower.
An SMS blaster exploits vulnerabilities in the 2G (GSM) communication standard. While 2G is primarily used today in remote, sparsely populated areas, all phones still support it. First, the blaster sends a technical signal over modern 4G/5G networks. When any phone or smartphone receives this signal, it attempts to switch to a 2G network. Simultaneously, the blaster broadcasts fake 2G base-station signals. The victim’s smartphone recognizes these as legitimate carrier signals and connects. Unlike the 3G, 4G, and 5G standards – where the smartphone and base station always perform a mutual cryptographic check during connection – this feature was only optional in 2G. This loophole allows an SMS blaster to mimic any carrier. Once connected, it can send any text message to a smartphone. After transmitting the SMS, the fake base station disconnects, and the smartphone reverts to its normal 4G/5G network with its legitimate carrier.
Perhaps surprisingly, this technology isn’t new. Similar to blasters, devices known as IMSI catchers, StingRays, or cell site simulators, have been used by law enforcement and intelligence agencies to gather data on individuals attending events of interest. However, criminals have found a new use for the technology.
You can block fake text messages by disabling 2G network connectivity on your smartphone, but that’s a double-edged sword. If you live in an area with poor signal or far from major cities, your phone might still occasionally use 2G. This is why many carriers haven’t completely phased out the outdated technology.
If you haven’t seen the 2G icon (an “E” or “G” next to your signal-strength indicator) in years, you might want to consider this option. Android phones running version 12 or newer offer the ability to disable 2G, but not every vendor makes this toggle visible and accessible. Android 16 introduced notifications that alert you if your smartphone might be connected to a fake 2G tower, but due to hardware limitations these only work on certain newer smartphones.
There’s no similar option in iOS, but you can effectively disable 2G by activating Lockdown Mode. Unfortunately, this does far more than just turn off 2G; it significantly restricts many iPhone functions in the name of maximum security (many would say it renders an iPhone practically unusable).
To avoid sacrificing your phone’s functionality while still protecting yourself from dangerous text messages, consider using a comprehensive smartphone security system. SMS blasts will still be delivered to your phone, but they won’t cause harm thanks to two layers of protection. The system identifies malicious messages regardless of the cellular network and blocks SMS spam (only on Android devices), while phishing protection prevents you from navigating to dangerous websites (on all smartphones).
Beyond technical measures, vigilance and general precautions are crucial in combating fake text messages. Instead of tapping links, sign in to your banking app or delivery service website directly from your bookmarks, your smartphone’s home screen, or by manually typing the address into your browser.
What other tricks do scammers use to try and sneak into your smartphone?
Kaspersky official blog – Read More

Welcome to this week’s edition of the Threat Source newsletter.
We’ve made it halfway through 2025 already! It’s been a while since I last wrote about CVEs and how free support for Windows 10 will end on October 14, 2025, leaving you with no more security fixes.
While the CVE system remains the global standard for vulnerability reporting, recent developments have sparked concerns within the community about its long-term stability. Currently, the program operates solely as a U.S. government-funded initiative. Following the last-minute funding extension, we’re now seeing competing ideas and projects emerging. Whether it’s the CVE Foundation working to transition from a single funding stream to a diversified and stable model, ENISA’s EUVD, or the Global CVE Allocation System (GCVE), the landscape is changing.
On one hand, a multi-source environment enhances availability and resilience. On the other, this fragmentation raises practical concerns for both researchers and practitioners. We now face questions like “Where should I report a vulnerability?” and “How do I integrate and correlate vulnerability data across multiple sources with multiple identifiers?”
Looking back at the first six months of this year, we see that the rapid pace of CVE publications in 2024 has continued into 2025, with no signs of slowing down. In fact, the current trend suggests that 2025 will surpass last year’s total of a little more than 40,000 CVEs. To illustrate: the first half of 2024 saw an average of 113 CVEs published per day, whereas the first half of 2025 is running at a rate of 131 CVEs per day.

What concerns me even more is the steep increase in Known Exploited Vulnerabilities (KEVs). It wasn’t just the spike in March — we’re seeing a generally sharper rise overall.

Vendor diversity also continues to expand, increasing from 45 vendors during the first half of last year to 61 so far this year. Additionally, the proportion of KEVs affecting network-related gear has grown from 22.5% in 2024 to 25% in 2025.
But there’s a small piece of good news: So far, I haven’t seen any CVEs from as far back as 2012 being added to the KEV catalogue like we saw last year. This time, the oldest additions “only” go back to 2017.

Keep in mind that the CVE year merely indicates when a vulnerability was reserved or assigned. The vulnerability itself may have existed for many years prior. For example, the recent sudo/chroot issue remained undiscovered for over 12 years.
In a nutshell: Keep tracking, keep patching. Vulnerabilities certainly won’t patch themselves.
Microsoft’s July 2025 security update addresses 132 vulnerabilities, including 14 marked as “critical,” with several remote code execution (RCE) issues affecting Windows, Office, SharePoint and Hyper-V. Although none have been exploited in the wild yet, some vulnerabilities — like those in SharePoint and SPNEGO NEGOEX — are more likely to be targeted and could allow attackers to execute code remotely or locally.
These vulnerabilities could let attackers take control of your systems, steal information or disrupt business operations, even if you haven’t seen any attacks yet. If you’re running Windows servers, SharePoint or Microsoft Office, your environment could be at risk, especially for organizations that rely on these products daily.
Don’t wait. Make sure you’re applying Microsoft’s July patches as soon as possible. If you use Cisco Security Firewall or SNORT®, update your rulesets to the latest versions to maximize your protection.
Alleged Chinese hacker tied to Silk Typhoon arrested for cyberespionage
A Chinese national was arrested in Milan, Italy for allegedly being linked to the state-sponsored Silk Typhoon hacking group, which is responsible for cyberattacks against U.S. organizations and government agencies. (Bleeping Computer)
Jailbreaking AI with information overload
Researchers say you can trick AI chatbots like ChatGPT or Gemini into teaching you how to make a bomb or hack an ATM if you make the question complicated, full of academic jargon, and cite sources that do not exist. (404 Media)
SatanLock is shutting down
The announcement that the group was closing its doors first came through its official Telegram channel and dark web leak site. Hunters International, another well-known ransomware group, also recently announced that it was shutting down its operations. (Dark Reading)
Ingram Micro scrambling to restore systems after ransomware attack
The IT distributor giant confirmed over the weekend that a ransomware attack was responsible for a widespread outage over its services, and they were forced to take certain systems offline on Friday afternoon, in response to the incident. (SecurityWeek)
Malicious Chrome extensions with 1.7M installs found on Web Store
Malicious extensions with 1.7 million downloads in Google’s Chrome Web Store pose as legitimate tools but could track users, steal browser activity, and redirect to potentially unsafe web addresses. (Bleeping Computer)
Scams, jailbreaks and poetic justice
In this episode of the TTP, Hazel Burton sits down with Talos’ Jaeson Schultz to explore the underground world of criminal LLM abuse, from elaborate scams to role-playing jailbreak prompts designed to trick AI into ignoring its own rules.
Vulnerability Roundup
Cisco Talos’ Vulnerability Discovery & Research team has disclosed and coordinated patches for two vulnerabilities each in Asus Armoury Crate and Adobe Acrobat.
PDFs: Portable documents, or perfect deliveries for phish?
A popular social engineering technique returns: callback phishing, or TOAD attacks, which leverage PDFs, VoIP anonymity and even QR code tricks.
Beers with Talos: Terms and conceptions may apply
In this episode, the crew reassembles after a totally intentional and not-at-all accidental hiatus. They cover AI-assisted IVF, a possible underground war against dairy, and the real heroes: conference dogs.
SHA 256: a31f222fc283227f5e7988d1ad9c0aecd66d58bb7b4d8518ae23e110308dbf91
MD5: 7bdbd180c081fa63ca94f9c22c457376
VirusTotal: https://www.virustotal.com/gui/file/a31f222fc283227f5e7988d1ad9c0aecd66d58bb7b4d8518ae23e110308dbf91/details
Typical Filename: IMG001.exe
Detection Name: Simple_Custom_Detection
SHA 256: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
MD5: 2915b3f8b703eb744fc54c81f4a9c67f
VirusTotal: https://www.virustotal.com/gui/file/9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
Typical Filename: VID001.exe
Claimed Product: N/A
Detection Name: Win.Worm.Coinminer::1201
SHA256: 47ecaab5cd6b26fe18d9759a9392bce81ba379817c53a3a468fe9060a076f8ca
MD5: 71fea034b422e4a17ebb06022532fdde
VirusTotal: https://www.virustotal.com/gui/file/47ecaab5cd6b26fe18d9759a9392bce81ba379817c53a3a468fe9060a076f8ca/details
Typical Filename: VID001.exe
Claimed Product: N/A
Detection Name: Coinminer:MBT.26mw.in14.Talos
Cisco Talos Blog – Read More
Our researchers have uncovered several malicious fake extensions targeting Solidity developers in the Open VSX marketplace. At least one company has fallen victim to the attackers distributing these extensions — losing approximately US$500 000 in crypto assets.
Threats associated with malware distribution in open-source repositories have been known about for a long time. Despite this, users of AI-powered code editors like Cursor AI and Windsurf are forced to use the open-source extension marketplace Open VSX, as they have no other source for the extensions these platforms need.
However, extensions on Open VSX do not undergo the same rigorous checks as those on the Visual Studio Marketplace. This loophole allows attackers to distribute malicious software disguised as legitimate solutions. In this post, we dive into the details of the malicious Open VSX extensions investigated by our experts, and explain how to prevent similar incidents within your organization.
In June 2025, a blockchain developer who had just lost approximately US$500 000 in crypto assets to attackers reached out to our experts and requested an incident investigation. While examining a disk image from the compromised system, our researchers noticed a suspicious component of an extension named Solidity Language for the Cursor AI development environment. The component was executing a PowerShell script — a sure sign of malicious activity.
The extension was installed from the Open VSX marketplace, where it had tens of thousands of downloads (presumably inflated by bot activity). The description claimed to optimize development of smart contract code written in the Solidity language. However, analysis of the extension revealed it had no useful functionality whatsoever. The developers who installed it mistook the lack of advertised features for a bug, didn’t immediately investigate, and just continued their work.
The browser extension wasn’t actually faulty; it was fake. Once installed, it contacted a command-and-control server to download and run a malicious script. This script then installed ScreenConnect — a remote access application — on the victim’s computer.
The attackers used ScreenConnect to upload additional malicious payloads. In the incident our experts investigated, these tools specifically allowed the attackers to steal passphrases for the developer’s crypto wallets and then syphon off cryptocurrency. A detailed technical description of the attack, along with indicators of compromise, is available in a Securelist blog post.
A look into the Open VSX marketplace revealed a concerning trend: a fake extension, deceptively named “Solidity Language”, ranked fourth in search results, while the legitimate extension, simply called solidity, appeared all the way down at eighth. It’s no surprise then that the developer downloaded the counterfeit instead of the genuine article.
This ranking is quite surprising, especially considering that at the time of the search, the legitimate extension had more downloads: 61 000 compared to the fake’s 54 000.
The key lies in Open VSX’s ranking algorithm. It doesn’t solely rely on download counts to determine relevance; it also considers other factors like verification status, ratings, and recency. This is exactly how the attackers managed to outrank the genuine extension in search results: the fake one had a more recent update date.
The fake plugin was removed from the Open VSX marketplace on July 2, 2025, right after the cryptocurrency heist. However, the very next day, we found another malicious package with the same name as the original extension, “solidity”, and the same harmful functionality as Solidity Language.
Additionally, our researchers used an open-source component-monitoring tool to discover yet another malicious package in Open VSX. Several details link this package to the same cybercriminals.
The Visual Studio Marketplace, Microsoft’s official store, has long been the primary industry source for extensions. It includes automatic scanning for malicious code, sandboxed execution of extensions for behavioral analysis, monitoring for anomalies in extension usage, and a number of other features to help identify harmful extensions. However, its licensing agreement dictates that only solutions for use with Visual Studio products can be published in the Visual Studio Marketplace.
Consequently, users of increasingly popular AI-powered code editors like Cursor AI and Windsurf must install extensions from an alternative store: Open VSX. The problem is that this platform has less stringent extension vetting, which makes it easier to distribute malicious packages compared to Microsoft’s official marketplace.
To be fair, attackers sometimes manage to publish malicious extensions even in the more secure Visual Studio Marketplace. For instance, this spring, experts found three malicious extensions there with an infection scheme very similar to the one described in this post, also targeting Solidity developers.
No matter where you’re installing extensions from, we recommend the following:
Kaspersky official blog – Read More

Cisco Talos’ Vulnerability Discovery & Research team recently disclosed two vulnerabilities each in Asus Armoury Crate and Adobe Acrobat products.
The vulnerabilities mentioned in this blog post have been patched by their respective vendors, all in adherence to Cisco’s third-party vulnerability disclosure policy.
For Snort coverage that can detect the exploitation of these vulnerabilities, download the latest rule sets from Snort.org, and our latest Vulnerability Advisories are always posted on Talos Intelligence’s website.
Discovered by Marcin 'Icewall' Noga of Cisco Talos.
These vulnerabilities were recently covered in a deep-dive post, Decrement by one to rule them all.
Asus Armoury Crate is a software utility used to manage Asus and ROG lighting, performance, and updates.
TALOS-2025-2144 (CVE-2025-1533) is a stack-based buffer overflow vulnerability in the AsIO3.sys kernel driver of Asus Armoury Crate 5.9.13.0. A specially crafted I/O request packet (IRP) can lead to stack-based buffer overflow. An unprivileged attacker can run a program from user mode to trigger this vulnerability.
TALOS-2025-2150 (CVE-2025-3464) is an authorization bypass vulnerability in the AsIO3.sys functionality of Asus Armoury Crate 5.9.13.0. A specially crafted hard link can lead to an authorization bypass. An attacker can create a hard link to trigger this vulnerability.
Discovered by Kamlapati Choubey of Cisco Talos.
Adobe Acrobat Reader is one of the most popular PDF reading software currently available. Talos found an out-of-bounds read vuln, TALOS-2025-2159 (CVE-2025-43578), in the Font functionality of Adobe Acrobat Reader 2025.001.20435. A specially crafted font file embedded into a PDF can trigger this vulnerability which can lead to disclosure of sensitive information.
TALOS-2025-2170 (CVE-2025-43576) is a use-after-free vulnerability in the annotation object processing functionality of Adobe Acrobat Reader 2025.001.20435. A specially crafted Javascript code inside a malicious PDF document can trigger reuse of a previously freed object, which can lead to memory corruption and could result in arbitrary code execution.
An attacker needs to trick the user into opening the malicious file to trigger either of these vulnerabilities.
Cisco Talos Blog – Read More
On July 7, 2025, Google rolled out a Gemini update that gives its AI-powered assistant access to Phone, Messages, WhatsApp, and Utilities data on Android devices. The company announced this update via an email to the users of its chatbot — essentially presenting them with a fait accompli. “We’ve made it easier for Gemini to interact with your device”, the email read. “Gemini will soon be able to help you use Phone, Messages, WhatsApp, and Utilities on your phone, whether your Gemini Apps Activity is on or off”.
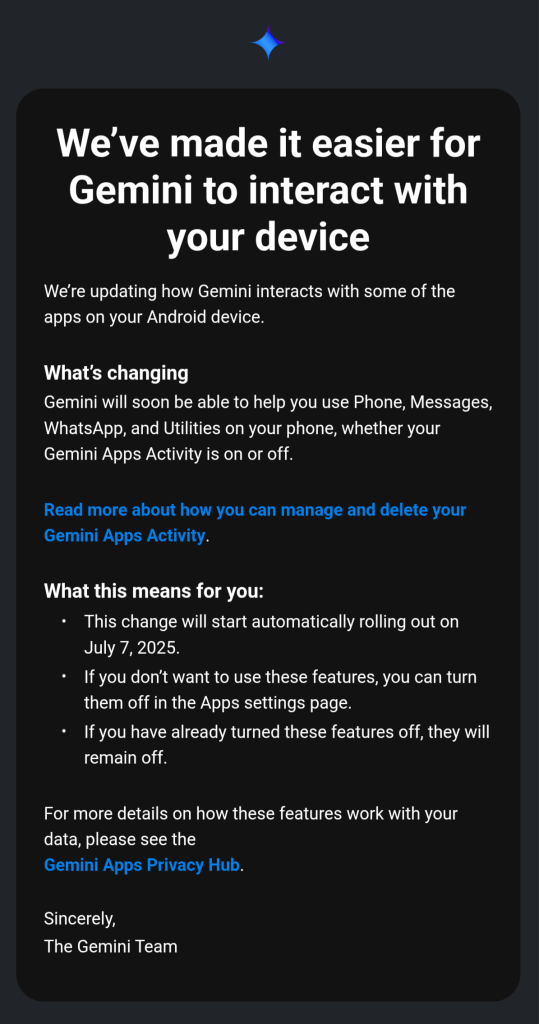
According to Google, the update improves privacy because users can now use Gemini’s features without having to enable Gemini Apps Activity. Pretty convenient, right?
The update applies regardless of whether the Gemini Apps Activity feature is enabled or not. Google pushed the update to all Android versions that support Gemini, starting with Android 10. So, although the company warned users, it clearly failed to ask for their explicit consent. Google has already practiced subtle coercion to use its features before: just a month ago, Gemini was integrated into the Gmail client without any warning.
The email itself contained neither clear instructions for how to disable the new features, nor detailed explanations as to what exactly Gemini would do with the collected data. Users received the email just two weeks before the update was launched.
As you’d expect, the tech community was on the verge of panic. Previously, users who wanted to integrate Gemini with their apps had to explicitly enable Gemini Apps Activity. This allowed Gemini to store and use their data long-term, and potentially gave developers access to it – of course, “only for the purpose of improving Google AI”.
Google isn’t alone in this. OpenAI, Anthropic, and other AI companies are guilty of the same “improving service quality” excuse. At least Google gives users the illusion of choice. What makes this case different is that, even with Gemini Apps Activity turned off, Google will still retain your conversations with the AI assistant for up to 72 hours — all for the same purposes of safety, security, and feedback.
We won’t debate whether this is good or bad — we’ll just show you how to completely block Gemini’s access to your apps and data. Grab your phone, and let’s go!…
Alternatively, you can reach that option directly to turn off Gemini Apps Activity right there.
If rather than disabling the AI assistant altogether you want to restrict Gemini’s access to data only from certain services like your email or photos, you can customize which apps it can work with and which it cannot.
Alternatively, you can reach that section of the settings directly.
If you plan not to use Gemini on your phone altogether, you can simply uninstall the app:
If you’re determined not to have any Google services on your phone, consider installing GrapheneOS; however, be forewarned that this is a solution for geeks with a Pixel phone only.
When you’re done with the settings, it’s a good idea to verify if your changes have been applied successfully:
To protect your Android device, use tried-and-true security solutions like Kaspersky for Android. This will give you peace of mind knowing you don’t have to worry about malware, your privacy, passwords, or personal and payment data.
Here are a few other posts about the subtleties of privacy in Google services and beyond.
Kaspersky official blog – Read More
Alert triage as one of the critical SOC and MSSP workflows implies evaluating, prioritizing, and categorizing security alerts to determine which threats require immediate attention and which can be safely dismissed or handled through automated processes.
Efficient alert triage, supported by robust threat intelligence, ensures that organizations stay ahead of adversaries while maintaining analyst productivity and morale. We shall see how it works on the example of ANY.RUN’s Threat Intelligence Lookup.
For SOCs, triage ensures that internal teams focus on high-priority incidents that could compromise critical systems or data. MSSPs, managing multiple clients, rely on triage to allocate resources efficiently across diverse environments, ensuring timely responses tailored to each client’s needs.
The triage process acts as the gateway between detection and action — the critical juncture where security alerts either trigger appropriate defensive measures or fade into background noise.
Alert triage is fraught with challenges that compromise its effectiveness in many organizations.
These obstacles create inefficiencies, delay responses, and increase organizational risk.
Speed in alert triage, measured by metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), is a critical KPI for SOCs and MSSPs. Rapid triage minimizes the window of opportunity for attackers, reducing potential damage from breaches, data loss, or system downtime. For businesses, fast triage aligns with key objectives:
Organizations with efficient triage processes can handle larger volumes of security data without proportionally increasing staff, improving operational efficiency and ROI on security investments.
Analyst fatigue occurs when security professionals become mentally and emotionally exhausted from processing endless streams of alerts, many of which prove to be false positives or low-priority events.
Cognitive overload increases when analysts must process more information than their mental capacity allows, leading to lower accuracy in threat assessment. Emotional exhaustion develops from the constant pressure of potentially missing critical threats, creating a state of chronic stress that affects both performance and well-being.
The business impact is profound and multifaceted. Fatigued analysts are more likely to miss genuine threats, increasing the exposure to successful attacks. They may also escalate false positives to avoid responsibility. High fatigue levels contribute to analyst turnover, creating recruitment and training costs while leaving organizations vulnerable during transition periods.
A negative feedback loop emerges where stressed analysts make more mistakes, leading to increased scrutiny and pressure, which further exacerbates fatigue. This cycle can devastate team morale.
The “need for speed” in alert triage is inseparable from the problem of analyst overload and fatigue. SOCs and MSSPs must analyze threats, incidents, and artifacts quickly to contain risks, but this analysis must be accurate and comprehensive to avoid missing critical threats or wasting resources on false positives.
Solutions that streamline triage without sacrificing accuracy are essential for overcoming this paradox. You do not choose between speed and accuracy but develop systems and processes that enable both.
ANY.RUN’s Threat Intelligence Lookup addresses both the speed and fatigue challenges by providing rapid, comprehensive threat context for indicators like files, URLs, domains, and IP addresses, and enabling teams to make informed decisions quickly.
Besides basic IOCs, this data contains attack and behavioral indicators including:
The data is derived from investigations of real-world cyberattacks on over 15,000 companies using ANY.RUN’s services.
When analysts encounter suspicious artifacts during triage, they can quickly query the service to obtain detailed information about the threat. This eliminates the time-consuming process of manually researching threats across multiple sources.
Instead of spending valuable time manually investigating suspicious artifacts, analysts can focus on higher-level analysis and decision-making. Here are a couple of examples.
A suspicious IP spotted in network connections can be checked against TI Lookup’s vast indicator database in a matter of seconds.
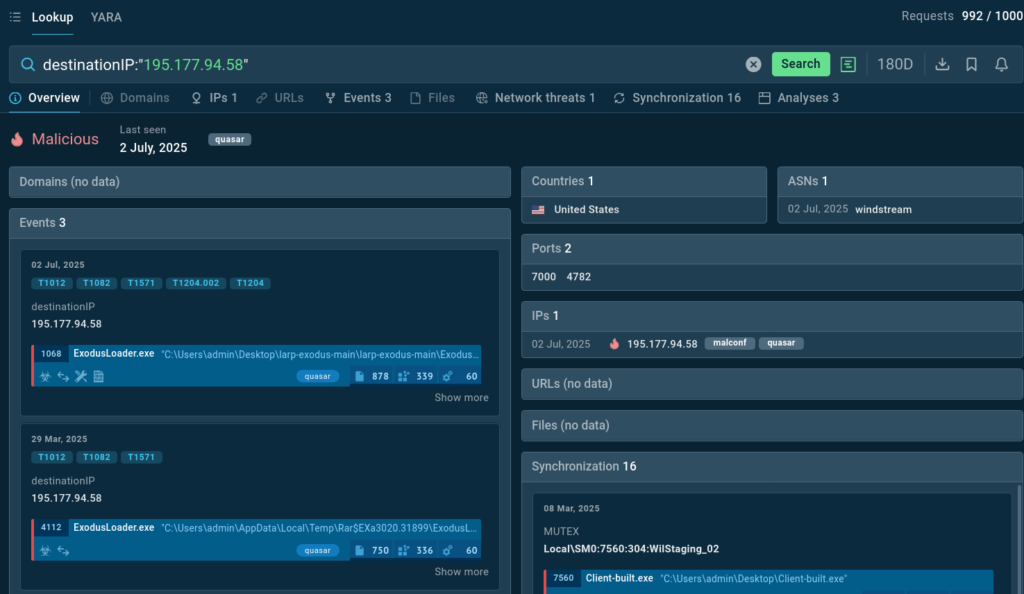
The IP address is exposed as malicious and a part of Quasar RAT inventory. It has been detected in recent malware samples, so it is an indicator of an actual threat.
Suppose an analyst notices a legitimate utility like certutil.exe is used for retrieving content from an external URL. All they have to do is copy a snippet of command line contents and paste it into TI Lookup search bar with the CommandLine search parameter:
commandLine:”certutil.exe -urlcache -split -f http”
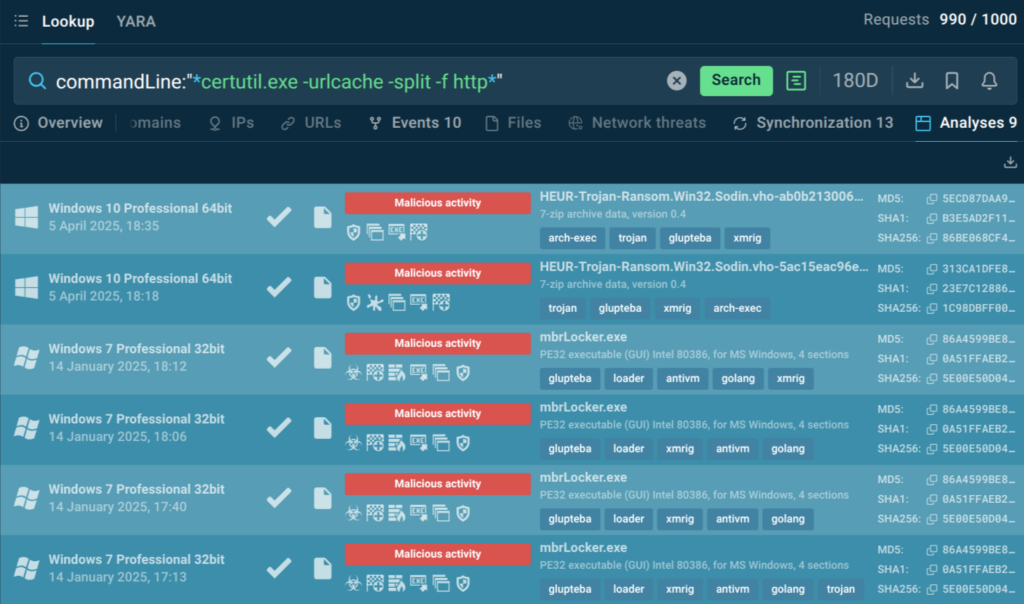
Switching to the Analyses tab of the search results, the analyst observes a selection of malware samples that performed this command during their execution chain. Now he knows that this behavior is typical for Glupteba trojan acting as a loader. Each sample analysis can be researched in depth and used for collecting IOCs.
Could it be okay if an app changes Windows registry key \CurrentVersion\Run responsible for default autoruns at system startup, by adding a command that initiates a script execution chain via mshta.exe using built-in VBScript? Query TI Lookup using RegistryKey and RegistryValue search parameters:
registryKey:”SOFTWAREMicrosoftWindowsCurrentVersionRun” AND registryValue:”mshtavbscript”
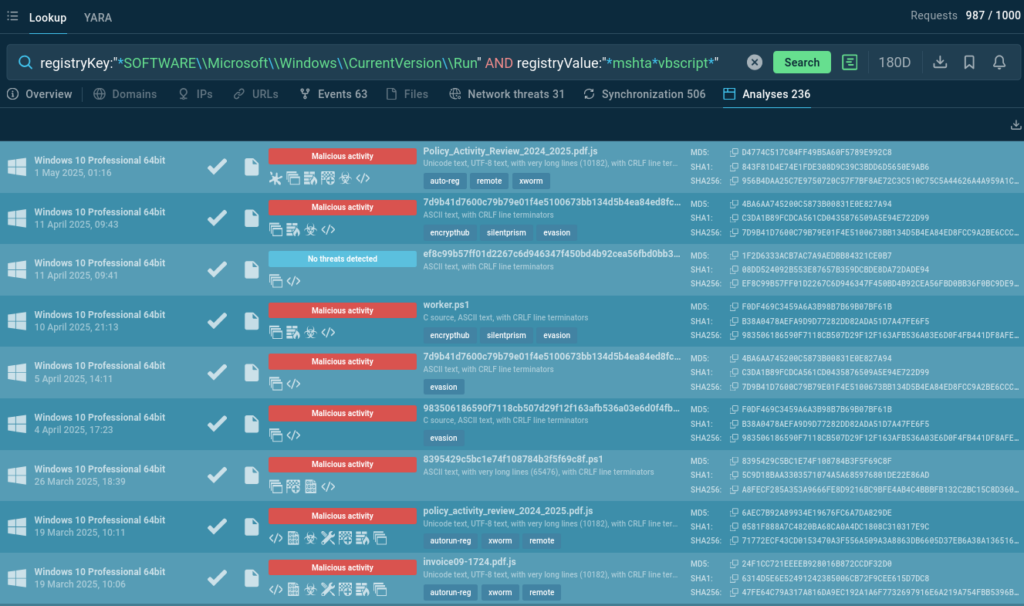
As we can notice looking at the found sandbox analyses, such registry modification is often associated with malware evasion and persistence techniques, and is typical for XWorm RAT.
When a new malware emerges, the available intelligence on it can be scarce. Nitrogen ransomware became notorious for targeting the valuable and vulnerable financial sector back in mid-2024. For months, a single research report was the source of public data on this strain. It provided analysts with two IOCs and two IOBs, one of the formers was a mutex.
Before encrypting files, Nitrogen creates a unique mutex (nvxkjcv7yxctvgsdfjhv6esdvsx) to ensure only one instance of the ransomware runs at a time. The mutex can be used for Nitrogen detection, and searching for it via Threat Intelligence Lookup delivers Nitrogen samples detonated in the Interactive Sandbox.
syncObjectName:”nvxkjcv7yxctvgsdfjhv6esdvsx”
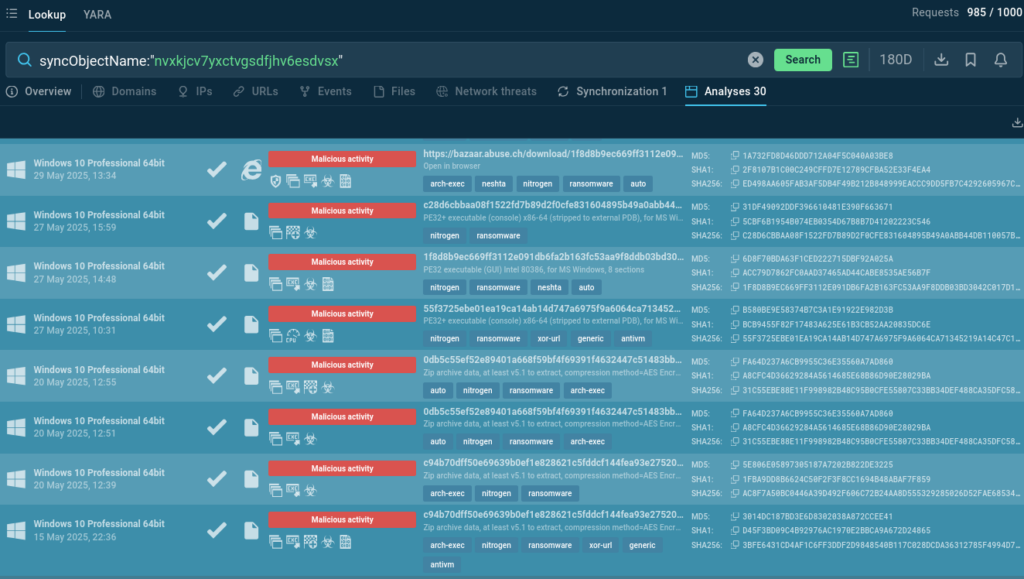
Each sample can be explored to enrich the understanding of the threat and gather additional indicators not featured in public research.
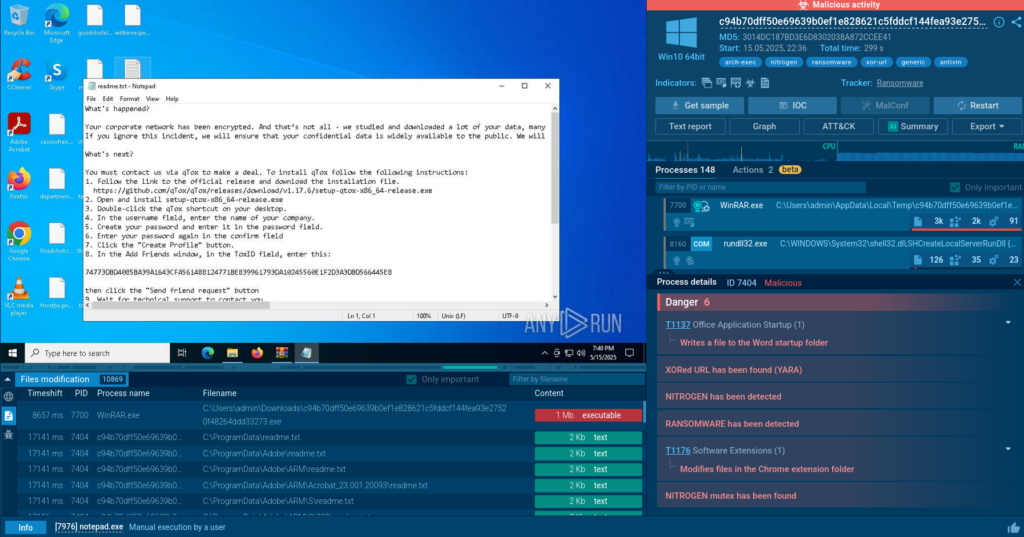
File hashes as unique digital fingerprints of a particular file are popular indicators of compromise. TI Lookup supports md5, sha256 and sha1 search parameters, but also allows to use a file name as a query.
filePath:”Electronic_Receipt_ATT0001″
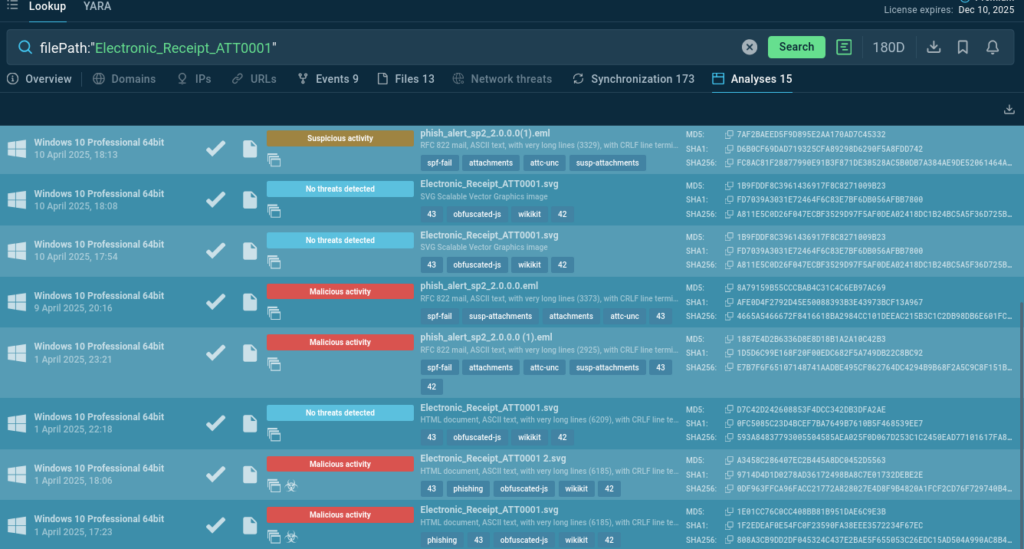
These lookup results show that a certain file name pattern can emerge in both malicious and benign samples: phishing kit campaigns often use filenames typical for popular documentation formats.
We can observe several samples of phishing attacks using the file with such name pattern in the Interactive Sandbox:
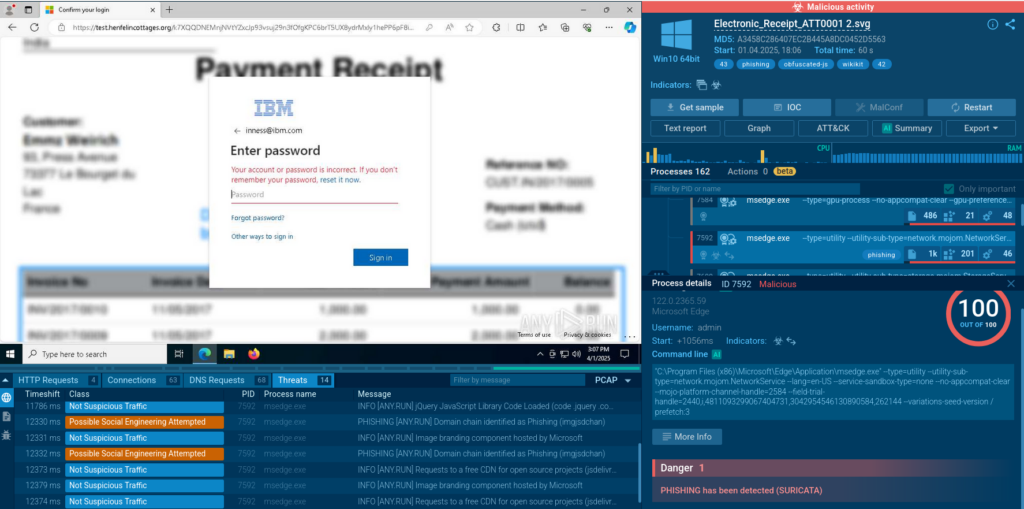
File name search can help understand the general mechanics of phishkit attacks and see a broader picture of emerging threats.
It’s up to you not to choose between speed and accuracy, nor to accept analyst fatigue as an unavoidable cost of doing business. Instead, embrace solutions that enable both rapid response and meticulous analysis.
ANY.RUN’s Threat Intelligence Lookup fuels this strategy by providing immediate, context-rich insights into suspicious artifacts and transforming reactive, manual investigations into proactive, informed decision-making. This translates into tangible business values:
Investing in solutions like ANY.RUN’s Threat Intelligence Lookup is not just about technology; it’s about building a sustainable and resilient security posture that protects an organization’s financial health, its most valuable assets, and its people.
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN. Our services streamline malware and phishing investigations for organizations worldwide.
Start 14-day trial of ANY.RUN’s solutions in your SOC today
The post How to Maintain Fast and Fatigue-Free Alert Triage with Threat Intelligence appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More