How MSSPs Detect Incidents Early with Threat Intelligence Feeds from ANY.RUN
Managed Security Service Providers (MSSPs) are tasked with protecting multiple clients simultaneously while maintaining cost efficiency, rapid response times, and customer trust. The key to success lies in early threat detection, which requires access to high-quality, actionable threat intelligence that can be immediately applied across diverse client environments.
Main MSSP Challenges
MSSPs operate in a complex environment where they must deliver consistent security outcomes across varied client infrastructures.
Resource constraints create additional pressure. False positives consume valuable analyst time, while missed threats can damage client relationships and business reputation.
The heterogeneous nature of client environments means MSSPs must work with different security tools, network architectures, and threat landscapes. Additionally, MSSPs must demonstrate clear value to clients while competing on both service quality and cost.
Threat Intelligence Feeds: Boosting MSSP Performance
Threat intelligence turns raw data into actionable insights, helping MSSPs prioritize threats, streamline workflows, and respond quickly. Real-time, high-quality intelligence reduces false positives, improves detection accuracy, and optimizes resource use, enhancing client outcomes.
High-quality threat intelligence feeds are crucial for MSSPs to stay ahead of threats. They provide:
- Timely Data: Fresh indicators of compromise (IOCs) enable rapid action before threats spread.
- Contextual Insights: Detailed threat behavior data supports informed decision-making.
- Scalable Integration: Feeds must work seamlessly across varied client systems.
- Automation Support: Automated integration speeds up responses and reduces manual effort.
How ANY.RUN’s Threat Intelligence Feeds Help MSSPs Keep Ahead
ANY.RUN‘s Threat Intelligence Feeds empower Managed Security Service Providers (MSSPs) to detect threats early across diverse client infrastructures, delivering real-time, context-enriched indicators of active threat campaigns.
By integrating these feeds, MSSPs can optimize their workflows and directly support their clients’ business objectives. The key benefits of ANY.RUN’s feeds are designed to enhance operational efficiency and drive measurable business outcomes for MSSPs and their clients.
Expanding Threat Monitoring and Detection Across All Clients
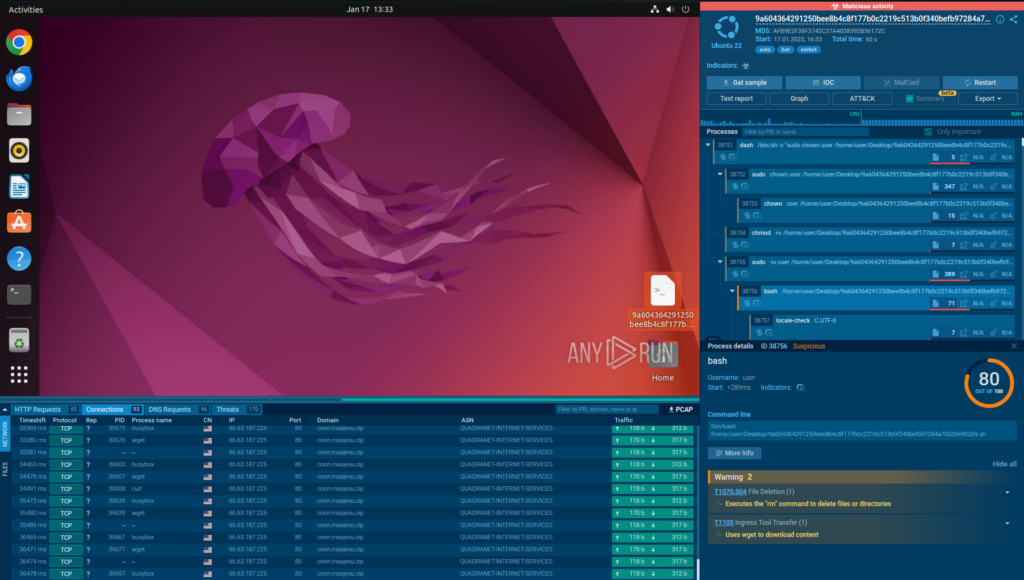
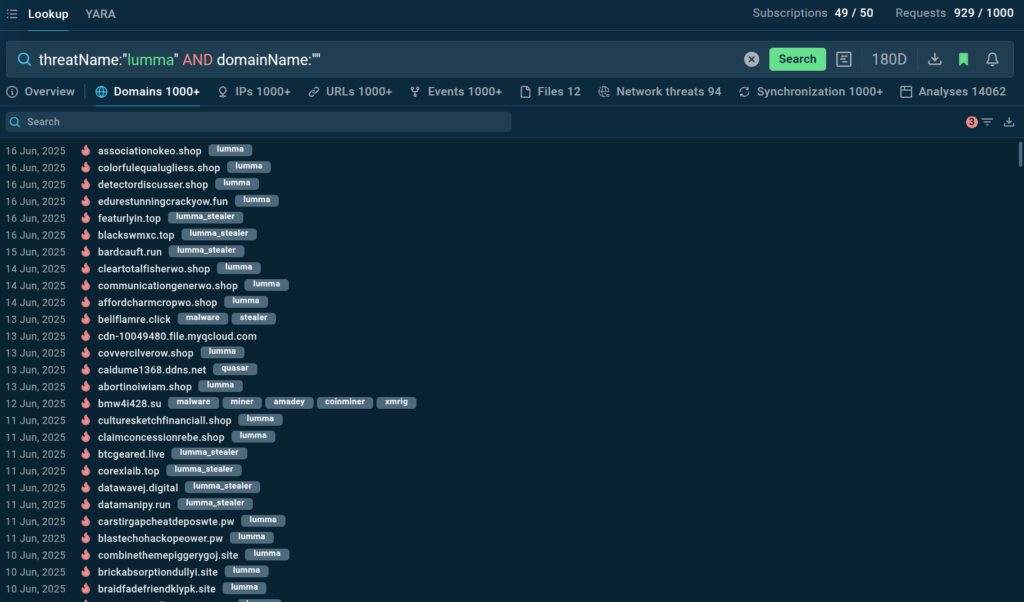
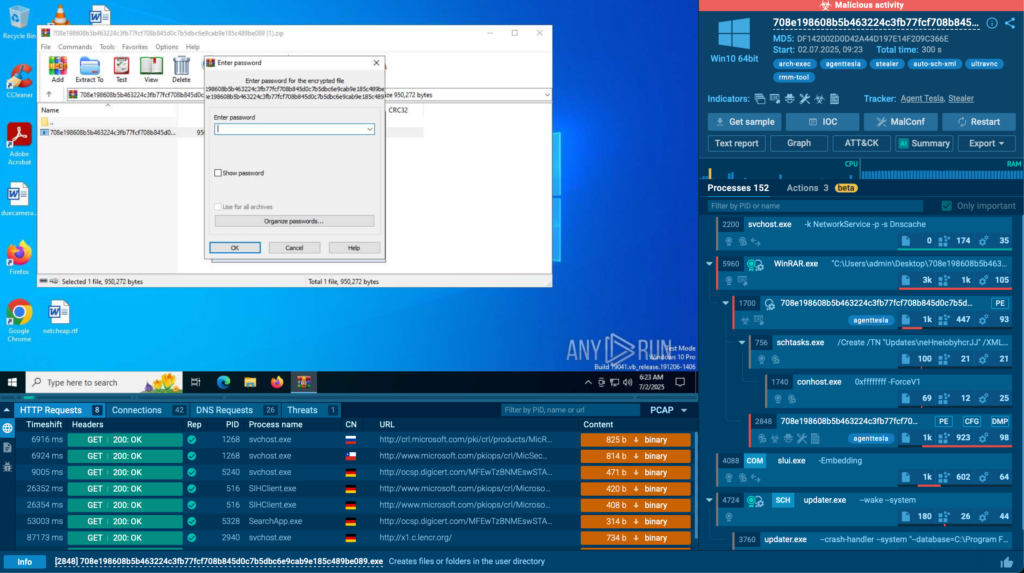
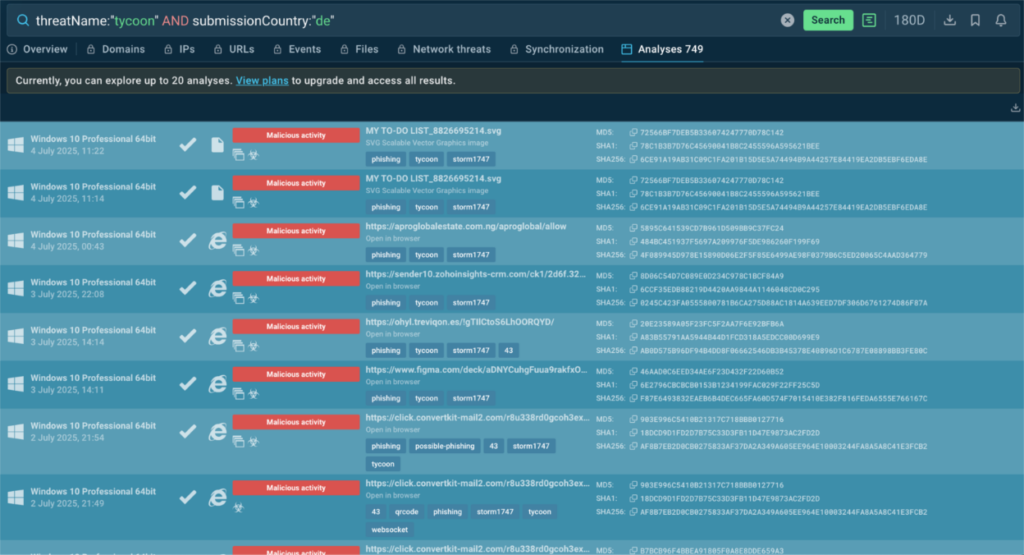
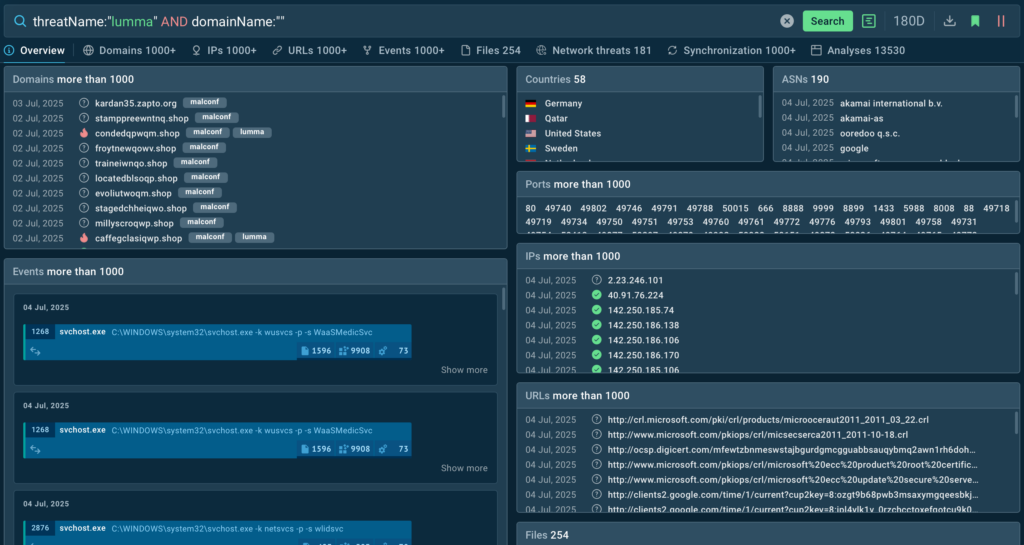
ANY.RUN’s TI Feeds draw from a vast, reliable data source, collecting threat indicators from live sandbox investigations of the latest threats by security teams at 15,000 organizations worldwide. Updated every two hours, these feeds provide fresh malicious IPs, domains, and URLs that have been used by threat actors for only a short time.
This near-instant delivery ensures MSSPs can spot threats that are still active right now across all client systems, whether they’re cloud-based or traditional setups. By catching threats early, MSSPs protect clients’ operations, prevent disruptions, and maintain trust across their customer base.
Informing Response to Stop Incidents Before Major Impact
Each threat indicator includes links to detailed sandbox reports that explain how attacks work, including their methods and behaviors (e.g., how malware communicates or spreads). This clear insight helps MSSPs build stronger defenses and respond quickly to specific threats.
For example, knowing an attack’s pattern allows security teams to block it before it causes harm, improving accuracy and reducing risks. The proactive approach prevents business interruptions, protects sensitive data, and reassures clients that their operations are secure.
Reducing Costs, Easing Team Workloads, and Scaling Services
ANY.RUN’s feeds are built for automation, working smoothly with common security tools like SIEM, XDR, threat intelligence platforms, and firewalls. They support standard formats (STIX, MISP, TAXII) and offer easy API and SDK integration for quick, automated setup.
Automation means less manual work for analysts, as threat data is automatically fed into systems to flag or block risks. By cutting down on repetitive tasks, MSSPs can manage more clients with less effort, lowering costs while maintaining top-notch protection.
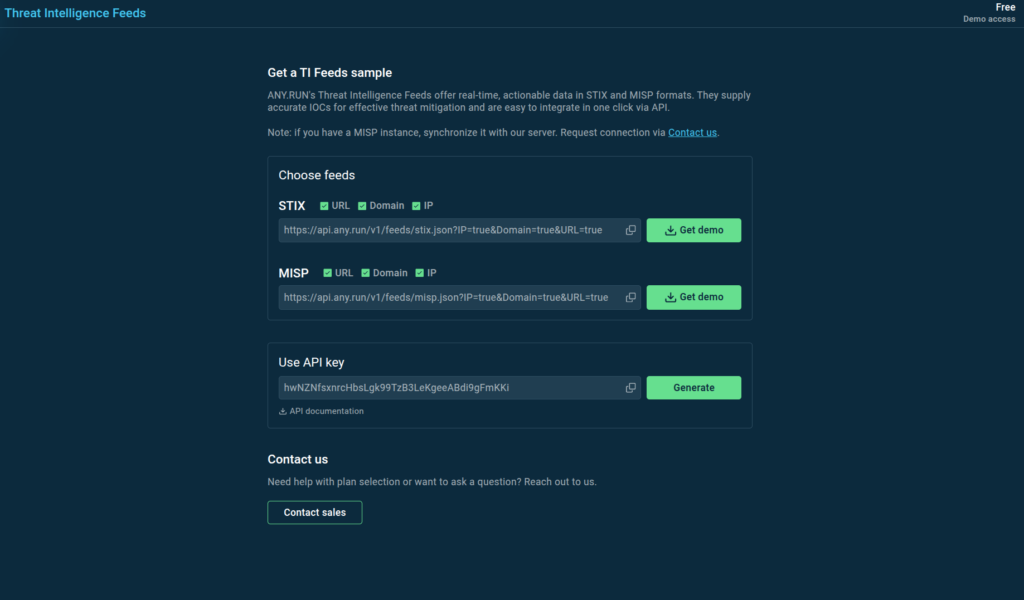
Get a demo sample of ANY.RUN’s Threat Intelligence Feeds with custom parameters.
TI Feeds Performance: Turning IOC Data into Business Value
ANY.RUN’s Threat Intelligence Feeds enable MSSPs to optimize their operations and deliver tangible business value to clients, including minimized downtime, enhanced competitiveness, cost efficiency, and stronger client retention through proactive threat prevention.
All these features and benefits transform into a number of business advantages for MSSPs. Threat Intelligence Feeds enable them to:
- Minimize client downtime and operational disruption: Early detection of threats protects against widespread incidents that could affect multiple clients. Real-time indicators of active threat campaigns enable identification of threats regardless of which client environment they target first, preventing cascading failures across the MSSP’s customer base.
- Optimize operational efficiency and reduce costs: Reduce analyst workload by supplying ready-to-use IOCs and comprehensive context data that eliminates time-consuming threat research and validation activities. Pre-processed, actionable intelligence allows analysts to manage more clients with existing resources, improving profit margins while maintaining service quality.
- Strengthen client retention and satisfaction: Block malware proactively before it strikes: the proactive approach prevents incidents rather than merely detecting them after they occur, reducing client impact and demonstrating measurable security value.
Integrate ANY.RUN’s Threat Intelligence Feeds
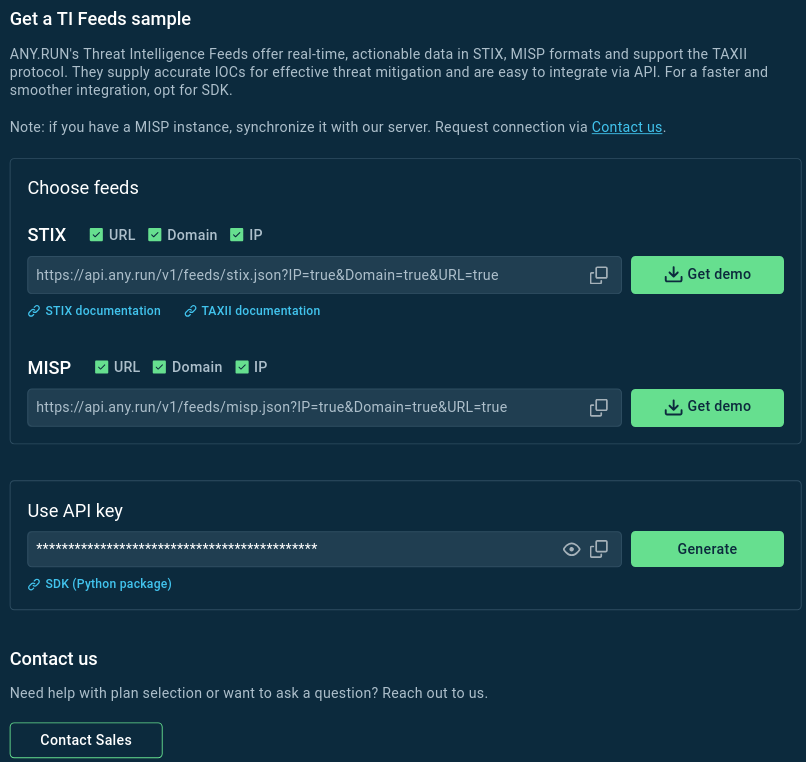
You can test ANY.RUN’s TI Feeds in STIX and MISP formats by downloading a free sample on this page.
To get access to the full version of TI Feeds with the latest indicators, please contact us for a trial.
- Spot and block attacks quickly to prevent disruptions and damage.
- Keep your detection systems updated with fresh data to proactively detect emerging threats.
- Handle incidents faster to lower financial and brand damage.
ANY.RUN also runs a dedicated MISP instance that you
Conclusion
ANY.RUN’s Threat Intelligence Feeds enable MSSPs to tackle their toughest challenges. With fresh, actionable, and context-rich IOCs, these feeds support early threat detection, streamline operations, and enhance client protection. MSSPs using ANY.RUN’s solution can strengthen their security posture, differentiate in a competitive market, and deliver exceptional value to clients.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals and 15,000 corporate security teams worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request trial of ANY.RUN’s services to test them in your organization→
The post How MSSPs Detect Incidents Early with Threat Intelligence Feeds from ANY.RUN appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More





















 Enterprise Plan:
Enterprise Plan: