X (formerly Twitter) has long had a solid reputation as a primary source of crypto scams, which are often promoted on the social network by compromised or fake accounts of celebrities or major companies. Meanwhile, Meta’s ubiquitous platforms — Instagram, Facebook, and WhatsApp — are earning a similar reputation in a different category: investment fraud involving deepfakes.
Criminals are eagerly exploiting AI tools to create fake videos of prominent figures in the financial sector — from famous economists and TV hosts to heads of government. Attackers then promote these videos by placing ads on social media. In this post, we explain how these schemes work, how victims are duped after watching these videos, the role WhatsApp plays in the schemes, and how you can avoid falling for them.
Instagram, deepfakes, and WhatsApp: investment scams in Canada
To understand how these scams work, we’ll start with a recent campaign that targeted customers of Canadian banks. Attackers began by running Instagram ads in the name of BMO Belski.
The abbreviation BMO was a deliberate choice; Canadian users consistently associate it with the country’s oldest bank, the Bank of Montreal. The mention of the Belski surname was no accident either: Brian Belski is BMO’s chief investment strategist and head of the bank’s investment strategy team.
The BMO Belski ads showed AI-generated deepfake videos of Belski himself promising users the chance to join a private investment group on WhatsApp. The criminals’ strategy was to dupe unsuspecting Canadian users into believing they’re getting trustworthy financial and investment advice from a recognized expert. The users would then rush to chat with the scammers through WhatsApp.
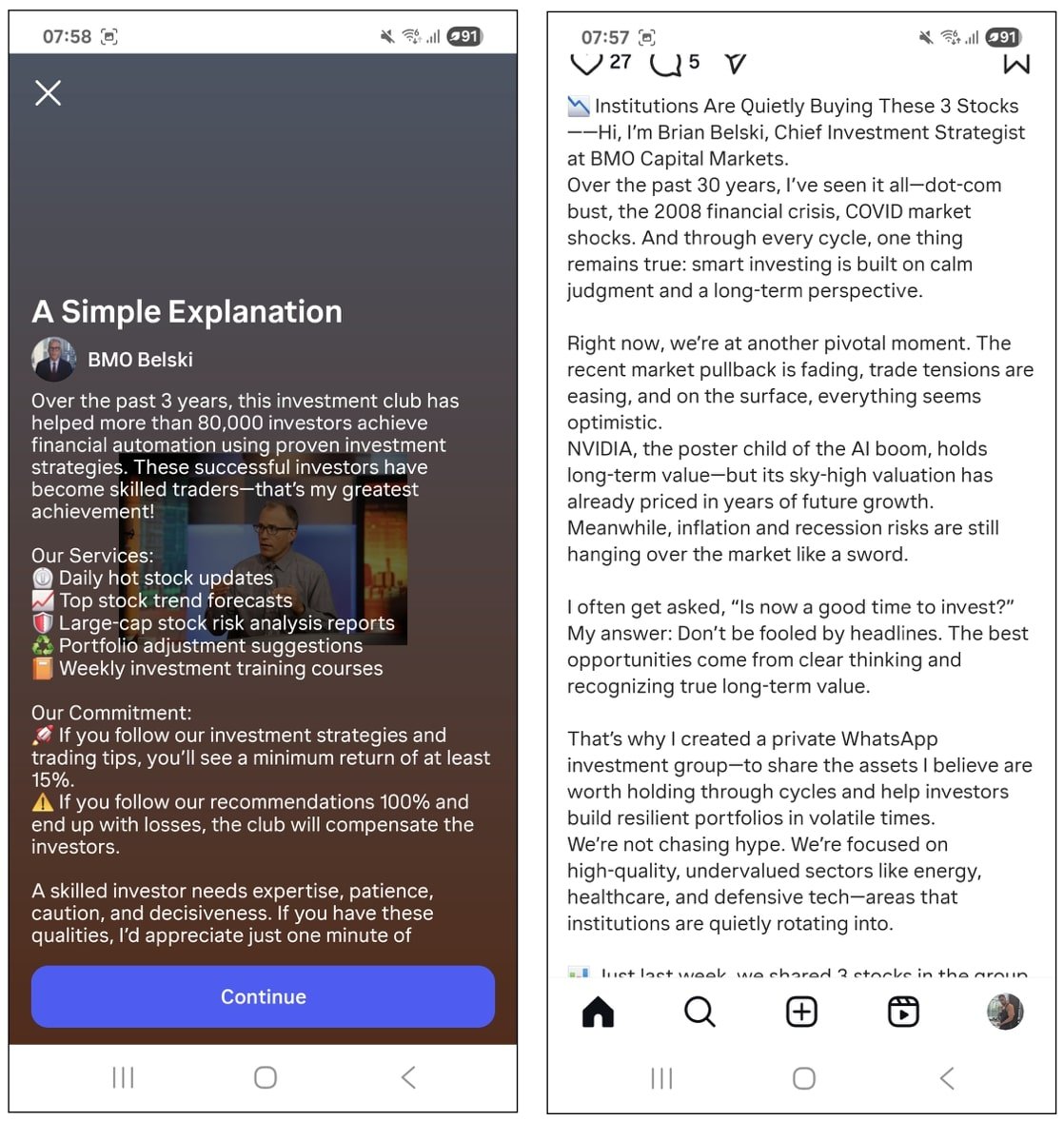
This is what an Instagram ad for a fraudulent investment club with a deepfake Brian Belski looks like: users are encouraged to join a private group on WhatsApp. Source
A curious detail: the BMO Belski account that ran these ads on Instagram had no profile on that social media platform at all. The ads ran through BMO Belski’s Facebook page. Meta, the company that owns both social networks, lets advertisers run Instagram ads from a Facebook business page, thus eliminating the need to create a separate Instagram account.
It’s also interesting that the Facebook page used to promote the fraudulent ads had existed since October 27, 2023, and was previously titled “Brentlinger Matt Blumm” — whatever or whoever that may be. The scammers likely used a pre-made or previously stolen account that was “marinated” for a few years to avoid suspicion and bypass moderation.
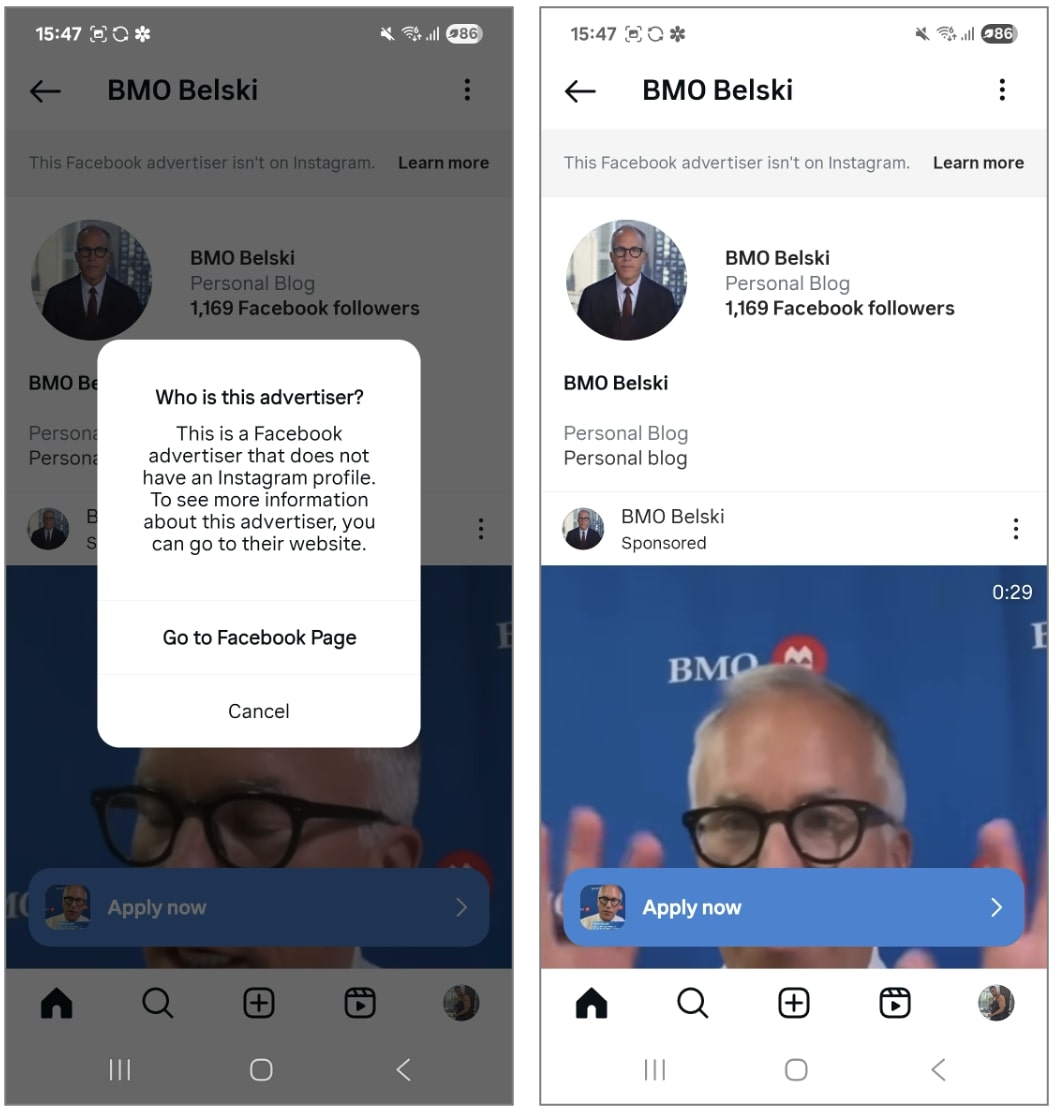
The ad with the Brian Belski deepfake was launched on Instagram, but on behalf of a Facebook page. Meta allows promoting ads on Instagram even if the advertiser doesn’t have an account there. Source
Researchers don’t know exactly what went on in the WhatsApp private investment chats promoted by the deepfake. There’s also no information about victims of the ad featuring the fake banker, or the amount of their losses. However, other cases involving similar schemes, which we discuss later in this post, give us an idea of how this could’ve looked.
Scammers impersonate Financial Times’ chief economics commentator
Several months ago in the UK, scammers employed a similar scheme, which featured a deepfake of Martin Wolf, the chief economics commentator for the Financial Times. Similarly to the Canadian bank scam, the fraudsters disseminated ads on Instagram that showed a fake Martin Wolf inviting people to join his WhatsApp group for investment advice.
A former colleague of Wolf’s first alerted the journalist to the ad in March 2025. Once alerted, Wolf started pushing Meta to block the ads because they violated several of the platform’s own advertising policies. After some back-and-forth with Meta, the journalist managed to get one of the fraudulent ads taken down. However, Wolf soon began receiving links to other similar videos.
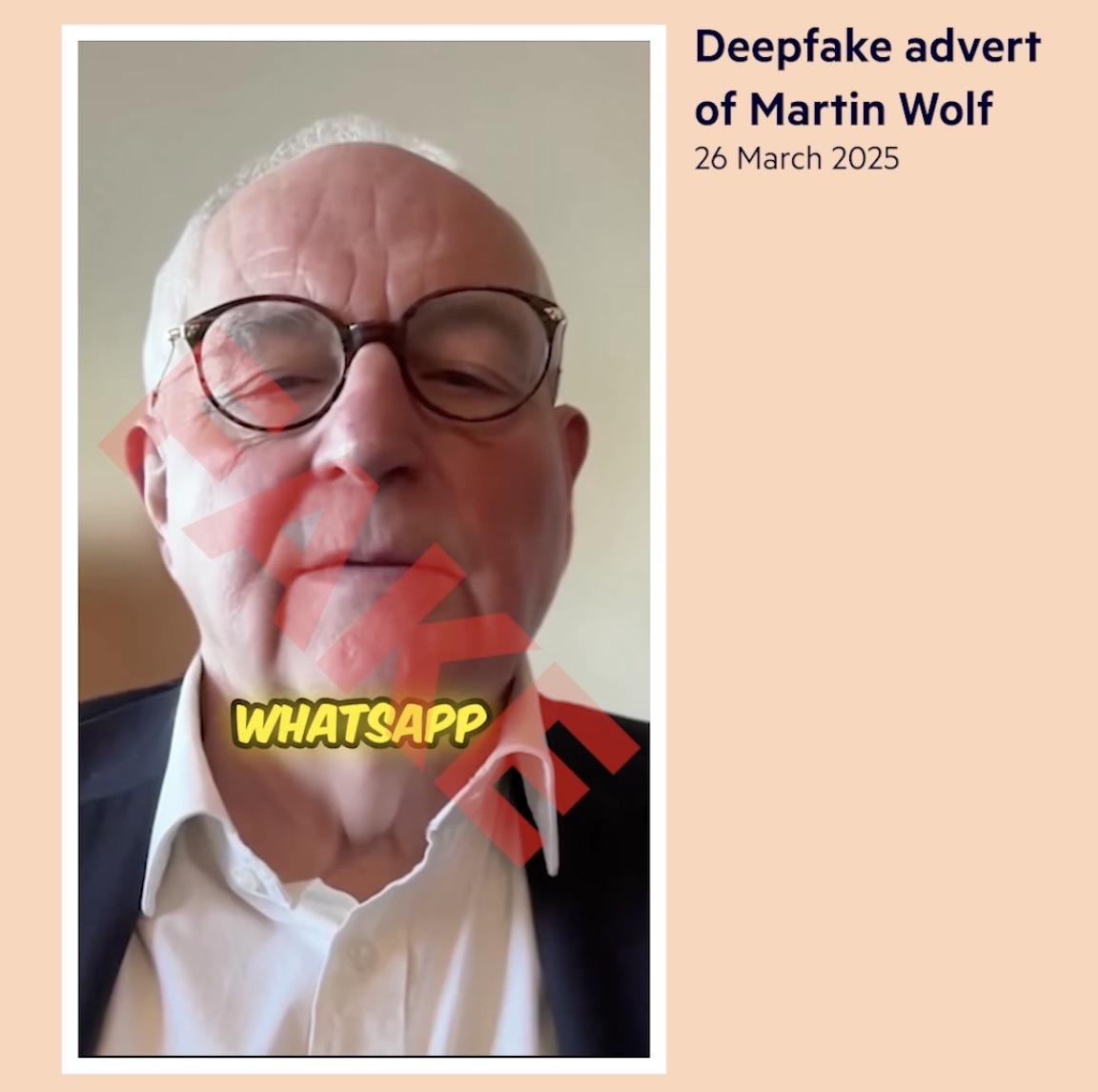
An example of an investment deepfake video of the Financial Times journalist, which scammers advertised on Instagram. Source
A subsequent investigation by the journalist’s colleagues at the Financial Times showed that the scam campaign included at least three different deepfake videos and several digitally manipulated images of Martin Wolf. These materials appeared in more than 1700 ads across Facebook and Instagram.
According to data from the Meta Ad Library, these ads reached more than 970 000 users in EU countries alone (excluding the UK), where legislation requires platforms to disclose such information. At least ten accounts ran the campaign, with new profiles joining the game as soon as the previous ones were blocked.
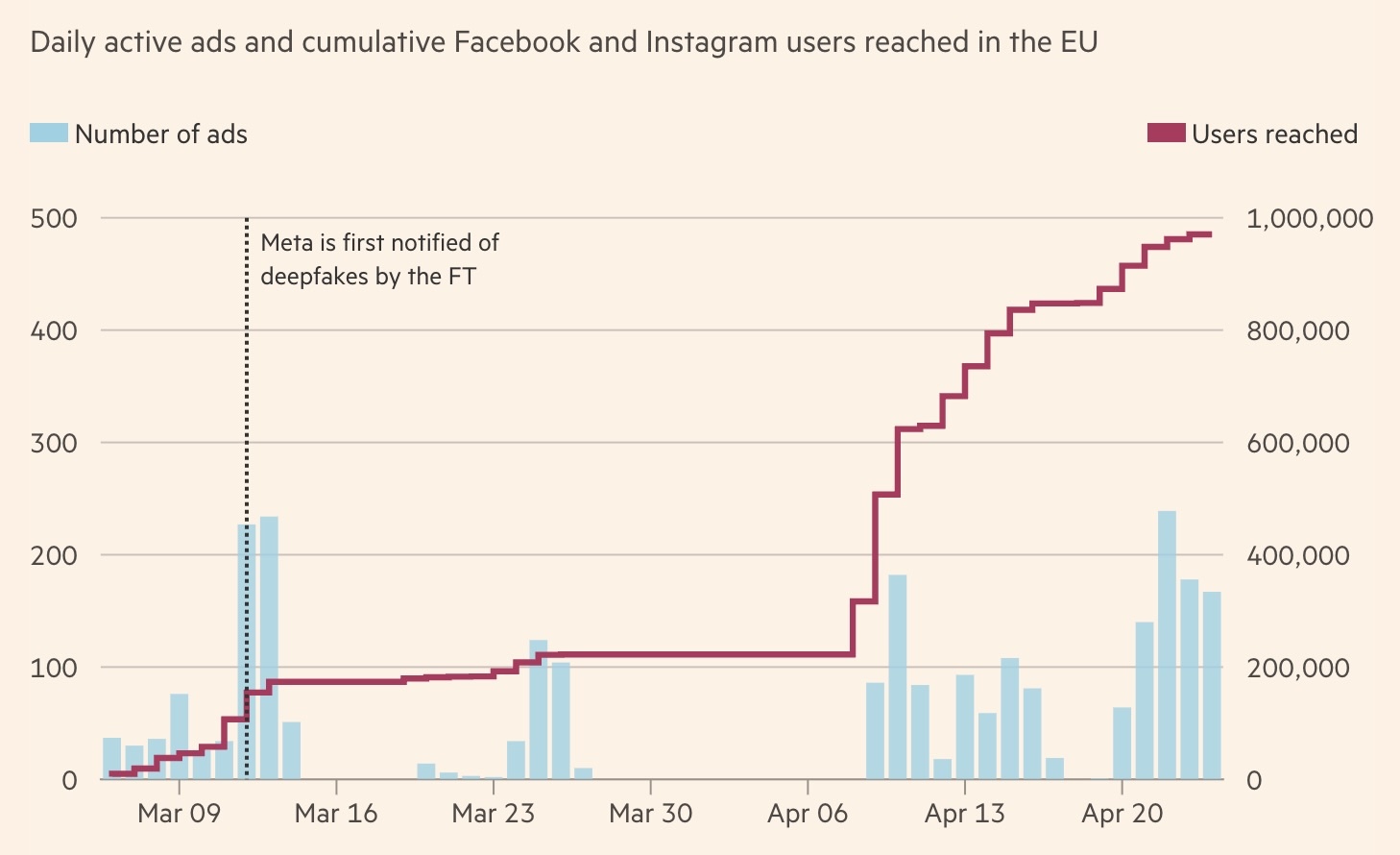
In just six weeks, a fraudulent advertising campaign featuring a deepfake of a Financial Times journalist reached nearly a million users in the EU alone. Source
The most shocking part? All of this occurred even though Martin Wolf was enrolled in Meta’s new face recognition system, which is specifically designed to automatically detect and remove this kind of content. The journalist himself questions why an organization as large as Meta, with plenty of resources and AI-powered tools, is unable to detect and block such schemes — if not fully automatically, then at least after direct notifications. Is it really that difficult?
What goes on inside WhatsApp scam chats: a British victim’s story
A British office manager named Sarah shared what happens inside “exclusive communities” on WhatsApp after she became a victim of scammers. She joined a WhatsApp group after watching an Instagram ad that featured Peter Hargreaves, the co-founder of the UK’s largest investment platform, Hargreaves Lansdown. You guessed it: the video was also a deepfake.
After Sarah gave the scammers her number, they contacted her and sent her an invitation to the WhatsApp group. Following that, they sent a link to download a supposed investment app to her smartphone. Sarah was told a “mentor” would assist her by telling her when and at what price to buy and sell assets to lock in a profit.
Initially, Sarah invested £50, but she soon began putting more and more of her savings into assets recommended in the WhatsApp group. Sarah believed she was investing in small, growing companies and quickly earning a profit. In just two weeks, her account showed about £300 in profits on a total investment of about £2 000.
Problems only began several weeks later when Sarah wanted to transfer the profit to her bank account. She started receiving requests to pay taxes, withdrawal fees, and regulatory fees. She continued to pay, convinced that she’d soon get her money back with a large profit.
When Sarah suspected a scam, it was already too late: all the money was gone. The WhatsApp group disappeared, her “mentor” stopped responding, and the investment app quit working. Along with the app, the £4000 she had invested and all of her supposed profits vanished.
More than 600 advertisements featuring deepfakes of Peter Hargreaves were found on the Meta platform. One of these ads led Sarah into the hands of scammers. Twenty-two fraudulent accounts placed the ads, and Hargreaves Lansdown had them removed in May of this year after filing a trademark infringement complaint.
To lure victims, the scammers also deployed deepfakes of other British financial celebrities besides Peter Hargreaves and Martin Wolf. These included Anthony Bolton, a former Fidelity International fund manager, and Stephanie Flanders, a former JP Morgan Asset Management economist.
From The Wolf of Wall Street to WhatsApp groups: how deepfake pump-and-dump schemes work
Malicious actors also employ deepfake videos in Facebook and Instagram ads to carry out another type of investment scam known as pump and dump. This scheme involves genuine financial assets — not fictional tokens in a fake application. The catch is that criminals buy up cheap, unattractive stocks to inflate their price. They then launch an aggressive advertising campaign on social media urging users to invest and promising rapid returns.
Due to the heightened interest, the stock price continues to rise for a time, and more people invest with hopes of easy profit. Once the value peaks, the scammers quickly sell off their shares and disappear with the earnings. After that, the price plummets, and everyone else is left with almost worthless stock.
A similar scheme existed long before the widespread adoption of deepfakes. One of the most famous examples of its execution was the work of Jordan Belfort, the inspiration for the main character in the movie The Wolf of Wall Street. In the early 1990s, his brokerage firm sold cheap, little-known stocks to clients, artificially inflating demand for them before dumping them at an inflated price.
Whereas stock market scammers in the past relied on their own asserted authority to convince victims to purchase dubious stocks, deepfake technology now allows them to exploit the reputations of experts and well-known figures.
For example, a scheme was recently uncovered in Israel where bad actors artificially inflated the stock price of Ostin Technology Group Co. Ltd. (OST). To do this, they circulated deepfake videos featuring business journalist Guy Rolnik, entrepreneur Eyal Waldman, and businesswoman Shari Arison. The scammers also impersonated reputable financial institutions, including the Tel Aviv Stock Exchange, the Israel Securities Authority, Bank Hapoalim, and Israel Discount Bank.
The fraudsters distributed fake promotional videos on Facebook and Instagram and, as in the previous scheme, invited users to join WhatsApp groups, where they provided them with advice on how to purchase OST stock. It didn’t take much persuading; a quick Google search confirmed that OST stock was, in fact, on the rise.
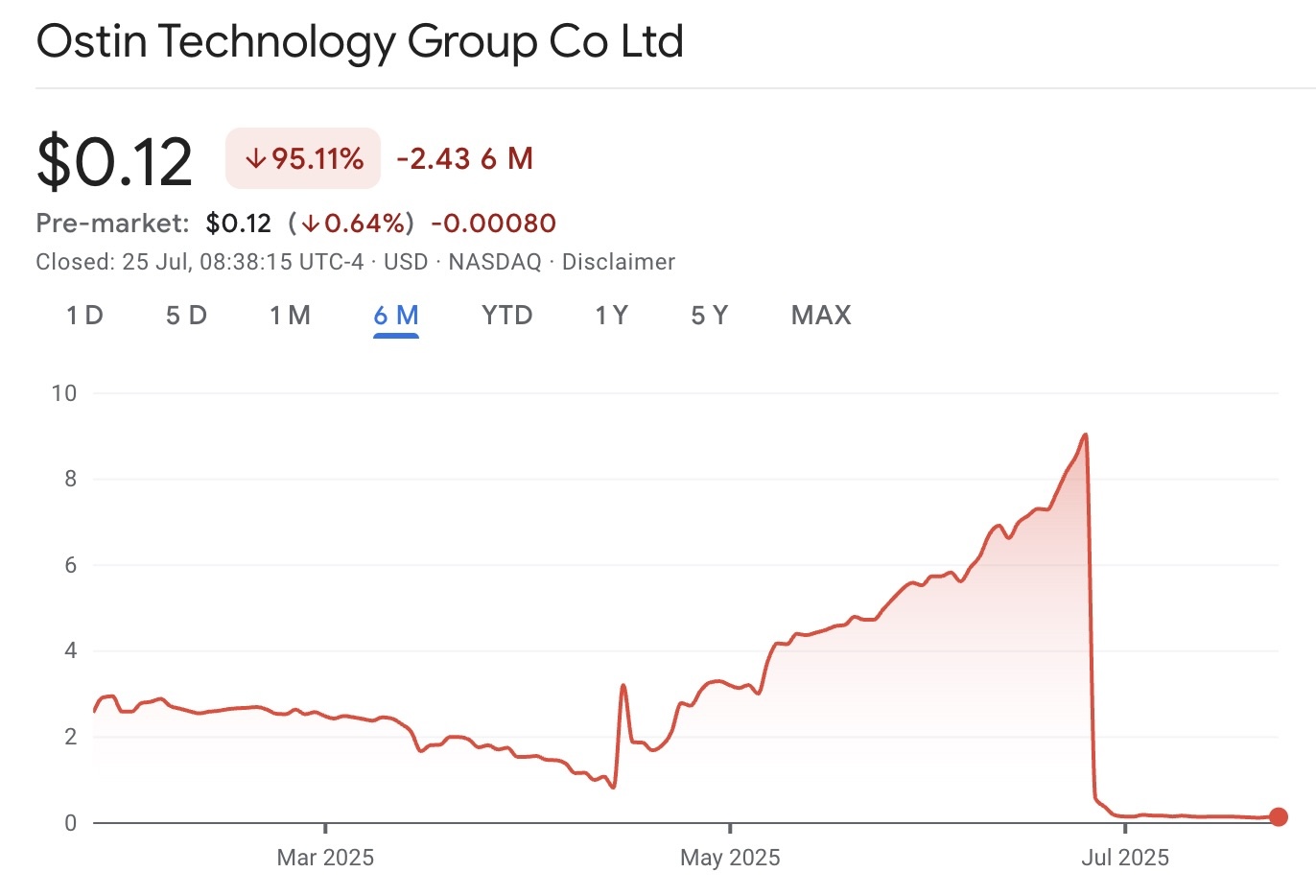
Rise and fall: Ostin Technology Group stock grew multiple times over, and then collapsed by 95% — after a scam campaign with deepfakes and investment chats in Israel. Source
Over several weeks, the company’s stock rose multiple times, reaching US$9.02 at its peak, after which it collapsed by 93%, with the stock price falling to 13 cents. In the two most serious cases, two victims lost 250 000 and 150 000 shekels (about US$75 000 and US$45 000), respectively.
Meta can’t protect users from deepfakes: a story from Australia
Scam ads that targeted Australian Facebook and Instagram audiences employed deepfake videos of several well-known personalities to promote fraudulent investment schemes. These videos featured TV host and financial journalist David Koch, billionaire Gina Rinehart, conservationist and TV host Robert Irwin, and even Australia’s current prime minister, Anthony Albanese.
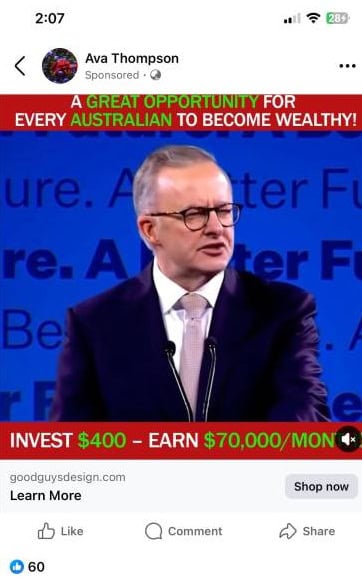
In a fraudulent ad on Facebook, a deepfake of the Australian prime minister advertises investments Source
In a deepfake video, Anthony Albanese enthusiastically advertised an investment program that promised significant returns for minimal outlay. The links within the deepfake videos of him and the other personalities directed viewers to a fake news story. The article included what appeared to be quotes from famous Australian public figures to support investments in cryptocurrencies, or other get-rich-quick schemes. Facebook users were asked to sign up for the program, after which scammers would contact them to convince them to deposit money.
In response to user complaints about fraudulent ads, Facebook sent out the following boilerplate message:
“We didn’t remove the ad. Thanks again for your report. This information helps us improve the integrity and relevance of advertising on Facebook. […]
We understand this might be frustrating, so we recommend influencing the ads you see by hiding ads and changing your ad preferences”.
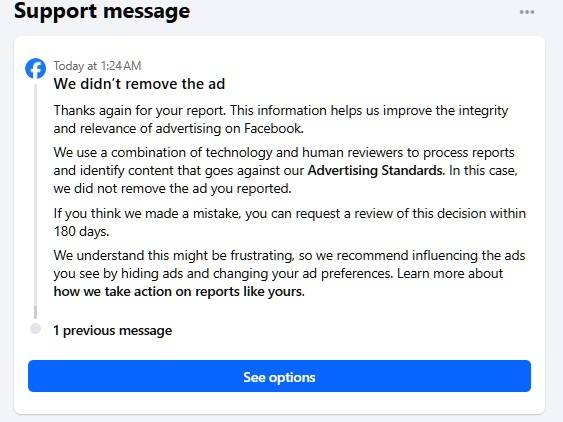
The message suggests that Meta isn’t particularly eager to combat fraudulent advertising — even when users try to assist the company. Source
In short, Meta’s efforts to fight deepfakes and investment scams on its platforms remain inadequate. Even with its plentiful resources and AI-powered tools, the company is unable to quickly detect and block obviously fake videos that exploit the likeness of public figures.
These ads appear daily in users’ feeds as paid promotions from fake yet seemingly legitimate accounts. This means that Facebook and Instagram ultimately profit from their being spread.
How to avoid falling victim to deepfake ads on Instagram and Facebook
To avoid suffering from questionable and outright fraudulent investment advice, our primary recommendation is not to make financial decisions based on information from Instagram or Facebook. In addition to that:
- Approach ads on social media with caution. As the stories in this post clearly show, ad moderation on Facebook and Instagram (and X, too) is less than ideal.
- Don’t forget about deepfakes. For several years now, we’ve been living in a reality where videos of any famous person can be easily, quickly, and cheaply faked. You should keep this in mind and verify any information you receive from dubious sources.
- Remember the universal rule of investing: the higher the potential return, the greater the risk involved. Therefore, you shouldn’t invest money you aren’t prepared to lose in schemes with supposedly high profits (which actually have a high risk).
- Be especially careful with offers that promise quick profits with minimal outlay. This is one of the most obvious signs of a scam — you know what they say about free lunch.
- Use only reliable investment apps from vetted brokers downloaded from official app stores. You shouldn’t trust download links sent by strangers in messaging apps.
- Tell your family and friends about deepfake video scams. This will help protect them from losing money and the emotional distress that can follow.
Learn more about deepfakes:
Kaspersky official blog –