Are cybercriminals hacking your systems – or just logging in?
As bad actors often simply waltz through companies’ digital front doors with a key, here’s how to keep your own door firmly locked tight
WeLiveSecurity – Read More
As bad actors often simply waltz through companies’ digital front doors with a key, here’s how to keep your own door firmly locked tight
WeLiveSecurity – Read More

Welcome to this week’s edition of the Threat Source newsletter.
I took a two-week vacation (thanks to Bill for covering my author shift last week) and made the deliberate choice to leave my laptop behind. No emails, IMs, no IT at all. Thank you, European work culture! It was a complete break.
Well, almost.
The weather didn’t always cooperate, so instead of freezing on a beach, I found myself catching up on TV — mostly news and a few series. But wherever I clicked, I just couldn’t escape the daily dose of AI. What can we do about invasive mosquitos? Ask AI. Government doesn’t move the needle? Ask AI. Want the weather forecast? AI, obviously. There are countless ads with people asking AI whether or not to wear a jacket “because it might rain.” Even with your favorite TV shows, gone are the days when the hoodied hacker sits in front of a black terminal with green text running a dangerous (haha) ping or nmap. Now, they’re writing lines like, “Did you try breaking the firewall with our latest AI algorithm, bro?”
Coming back to work and catching up on our industry news, I almost expected AI to be dominating the headlines. But it wasn’t, and neither was ransomware. Instead, they were all about breaches. Many — but not all — reports referenced compromised OAuth tokens linked to Salesloft’s Drift integration, with a notable number of high-profile victims. Sure, this isn’t a scientific or qualitative analysis (ransomware isn’t disappearing anytime soon), but the reporting and the headlines have definitely shifted from one to the other.
Looking past the buzzwords and catchphrases, the headlines really boiled down to two main themes: supply chain and identity attacks. In a SaaS world, I think it’s time to rethink their definitions and priority levels.
Why? First, supply chain attacks aren’t limited to hardware or software anymore. We need to consider the datapath (or where data possibly is processed) as a key part of the supply chain.
Second, identity attacks don’t just target users; interconnected applications are increasingly at risk, too. I’m not saying we can ignore the users, especially with current reporting that it started with access through a GitHub account or software vulnerabilities in our “classic” applications, but we absolutely need to broaden our focus. Last week’s headlines made that clear.
Cisco Talos’ latest blog post details the Cyber Threat Intelligence Capability Maturity Model (CTI-CMM), a framework that helps organizations assess and enhance their cyber threat intelligence programs across 11 key domains. By outlining clear maturity levels and improvement cycles, CTI-CMM can help your team benchmark your current capabilities and develop a strategy for continuous (and practical) growth.
Understanding and improving your CTI program’s maturity can help your organization better anticipate, detect, and respond to cyber threats, no matter your budget or staffing level. It also makes the security investments you do have more effective, and ensure your team’s efforts are aligned with business priorities.
Check out the CTI-CMM framework to assess where your organization stands, identify gaps and opportunities, and create a roadmap to practical improvements for your organization.
Huge NPM supply chain attack goes out with whimper
A supply chain attack involving multiple NPM packages had the potential to be one of the most impactful security incidents in recent memory, but such fears seemingly have proved unrealized. (Dark Reading)
Swiss Re warns of rate deterioration in cyber insurance
Increased competition among insurers has led to a third consecutive year of reduced rates, according to the report, as the available supply of cyber coverage has exceeded current demand. (Cybersecurity Dive)
Critical SAP vulnerability actively exploited by hackers
A critical security flaw has been found in several SAP products, and could allow a malicious actor to gain administrator-level control. (HackRead)
No gains, just pains: 1.6M fitness phone call recordings exposed
Sensitive info from hundreds of thousands of gym customers and staff was left sitting in an unencrypted, non-password protected database. Audio recordings spanned from 2020 to 2025. (The Register)
US offers $10M reward for Ukrainian ransomware operator
Volodymyr Tymoshchuk allegedly hit hundreds of organizations with the LockerGoga, MegaCortex, and Nefilim ransomware families. According to an indictment, the intrusions caused hundreds of millions of dollars in losses. (Security Week)
China accuses Dior’s Shanghai branch of illegal data transfer
China’s public security authority alleges that Dior’s Shanghai branch has transferred customers’ personal data to its headquarters in France illegally, leading to a data leak in May. (Reuters)
SHA 256: 41f14d86bcaf8e949160ee2731802523e0c76fea87adf00ee7fe9567c3cec610
MD5: 85bbddc502f7b10871621fd460243fbc
VirusTotal: https://www.virustotal.com/gui/file/41f14d86bcaf8e949160ee2731802523e0c76fea87adf00ee7fe9567c3cec610/details
Typical Filename: N/A
Claimed Product: Self-extracting archive
Detection Name: Win.Worm.Bitmin-9847045-0
SHA 256: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
MD5: 2915b3f8b703eb744fc54c81f4a9c67f
VirusTotal: https://www.virustotal.com/gui/file/9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
Typical Filename: VID001.exe
Claimed Product: N/A
Detection Name: Win.Worm.Coinminer::1201
SHA 256: c67b03c0a91eaefffd2f2c79b5c26a2648b8d3c19a22cadf35453455ff08ead0
MD5: 8c69830a50fb85d8a794fa46643493b2
VirusTotal: https://www.virustotal.com/gui/file/c67b03c0a91eaefffd2f2c79b5c26a2648b8d3c19a22cadf35453455ff08ead0
Typical Filename: AAct.exe
Claimed Product: N/A
Detection Name: PUA.Win.Dropper.Generic::1201
Cisco Talos Blog – Read More
Whether superintelligent AI arrives by 2027 is anyone’s guess. However, the forecast for 2026 is already clear: the year will be defined by easily accessible AI agents — large multimodal models capable of building and executing a chain of actions based on user commands. Agentic features are already available on the ChatGPT website and from other providers, but achieving maximum performance requires these agents to execute actions directly on the user’s computer rather than in the cloud. The ideal solution would probably be an AI-powered OS, but creating a new operating system is a challenge. Because of this, all minds are focused on a user-friendly and effective alternative: the AI browser. And by that we mean a regular web-browsing application with a deeply integrated LLM. The AI model can view all open web pages, process information from them, and issue the same commands a user typically would, such as opening, clicking, entering data, saving, and downloading.
The market leaders all see the value of this solution. For instance, Perplexity has released its own Comet Browser and recently made a multi-billion-dollar bid to buy Chrome, while OpenAI has started developing its own browser. Google and Microsoft are in a better position, integrating Gemini and Copilot into their existing Chrome and Edge browsers, respectively. Meanwhile, Mozilla is approaching the same goal from a different angle: gradually integrating AI features deeply into its Firefox browser.
As a result, you’re already seeing ads encouraging you to “upgrade your browser” by either downloading the latest version, or activating “smart features” in your current one. Next year, they’ll be wall to wall. The only thing left to decide will be why you need all this, and whether the benefits are worth the emerging risks.
An AI assistant perfectly integrated into your browser can free you from many tedious tasks. With the press of a button, you can get a quick summary of a long article or a two-hour video; or instead of reading a lengthy document, you can ask a question about its content. All of this happens quickly and naturally, without the need to copy and paste links or text into a chatbot tab.
But the real breakthrough will come with agentic features: the ability to perform specific actions rather than just process data. For example, you could open your favorite marketplace and tell the assistant to add everything you need for a three-day backpacking trip in August to your cart.
Unlike similar features already available on AI provider websites, this agentic activity takes place directly on your computer. Online services recognize you since you’re already logged in, and operations occur much faster than they would on a cloud virtual machine — though better results aren’t guaranteed.
Information retrieval features can also provide more relevant results in an AI browser running on your device because bots like ChatGPT, Claude, and Perplexity are blocked from many websites. This prevents LLMs from considering many up-to-date sources in their answers. With these features running from within the browser, the problem will be significantly alleviated as the AI assistant will access websites on your behalf. Additionally, if you’re subscribed to any restricted data sources, such as scientific journals or stock market reports, the AI agent will be able to use them as needed.
Some AI solution providers’ motivations they state themselves, while others require educated guesses based on the business models of Big Tech.
Billions of users. Successful entry into the browser market is a ticket to the largest possible user base. Sure, acquiring Chrome, or at least Firefox, would be ideal, but failing that, tech players can always push their own browser high up the popularity ladder.
“Stickiness”. A service that’s built directly into the browser will see more frequent use because it’s always within easy reach. Besides, it’s harder to switch from a familiar browser: it takes significant effort to migrate bookmarks and extensions to another browser and set it up. This is way more than simply closing one chat tab and opening another.
More information. If there are many users, and they access the service frequently, they feed the AI provider more information, allowing new versions of language models to be trained faster, helping to improve the product. A browser has access to all user web traffic, so training can be done on any website data — not just on conversations with the model.
New training methods. The provider gains a gold mine of behavioral data. Currently, AI agents work by looking at web pages and figuring out what button to press. This is similar to how humans think out loud: it’s a slow and not very efficient process. Training on mouse movements and clicks will allow for a completely new layer in the model, resembling motor memory which, just like in humans, will be faster and more efficient.
Sufficiently bold providers could even utilize user files on the computer for training. Newer versions of Facebook are already doing something similar by sending unpublished photos from the user’s phone gallery to the cloud.
Lower costs. AI providers’ enormous server costs would decrease because some of the work would be done directly on the user’s computer instead of on a virtual machine in the cloud.
Bypassing blocks and paywalls. AI model training is already facing a shortage of new information, with the problem exacerbated by many websites blocking access to AI agents. Cloudflare, which protects one in five websites, including the vast majority of larger ones, has enabled this policy by default. Sending data requests from the user’s computer addresses these challenges: the AI agent’s activity is indistinguishable from the computer owner’s.
A distributed network of browsers makes it possible to access websites for things like model training, without running into restrictions. In principle, this also allows downloading publicly unavailable data, such as articles in subscription-based journals.
All of this means that an AI browser creates significant, poorly controlled threats to your privacy. AI companies get access to all of your traffic, your entire web history, the full content of those websites, and all the files on your computer.
As a result, you might unintentionally feed deeply personal or restricted data — like books you purchased, or unpublished scientific papers — into a publicly available AI system. You could also accidentally leak highly confidential information from work websites, such as draft financial reports, in-progress designs, or other trade secrets.
This isn’t some sci-fi scenario: in 2023, ChatGPT mistakenly revealed snippets of users’ chats, and the “share chat” feature — available to ChatGPT users until July 31, 2025 — resulted in tens of thousands of user conversations being indexed by search engines and made available to anyone.
Incidents involving AI applications are becoming commonplace, and paint a worrying picture.
In a recent experiment, researchers successfully tricked an AI agent within the Comet browser into downloading malware onto its owner’s computer. They did this by sending a fake email to the victim’s account, which the agent could access, stating falsely that it contained blood test results. To download them, the user had to click a link and complete a CAPTCHA. When the AI agent tried to download the results and encountered a CAPTCHA, it was prompted to complete a special task, which the agent “successfully” handled by downloading a malicious file.
In another experiment by the same team, an AI assistant was persuaded to buy products from a scam site. Considering that passwords and payment information are often saved in browsers, deceiving an AI agent could lead to real financial losses.
The researchers noted that AI is highly susceptible to social engineering, and tried-and-true human deception tricks work well on it. While the tests were conducted in the Comet browser, the same thing would happen in any browser with AI agent capabilities.
Another risk is that a browser is a fully featured application with broad access to files on the computer. By obeying a prompt injection on a malicious site, a browser assistant can delete the user’s files, or upload them to fraudulent websites without permission. A recent example involving the hack of the Nx application demonstrated this: the malicious code didn’t search for crypto wallets or passwords on infected developers’ computers itself; instead, it simply instructed previously installed AI assistants to find the files it needed.
A third, still hypothetical, risk is related to the fact that more and more countries are passing laws against accessing illegal information online. The list of what’s forbidden differs from country to country, from child sexual abuse and terrorism to unlicensed books and cryptographic technology. If some players in the AI browser market decide to use their browser as a crawler (search bot) to train new LLMs, or if an AI agent is attacked with a prompt injection, the AI assistant could start searching for such information without the user’s request. How the user would prove that it was the AI looking for the data is an open question.
We also shouldn’t forget about traditional software vulnerabilities. Hundreds of dangerous defects are found in browsers every year because browser security is a complex engineering task. Even with the Chromium team doing the lion’s share of the work, there’s still plenty for wrapper developers to do. Will enough attention be paid to testing and fixing vulnerabilities in AI-powered browsers? It’s not a given.
Finally, sloppy implementation of AI features can lead to excessive memory and CPU consumption, as demonstrated by the recent release of Firefox 141. While this doesn’t directly threaten security, the lags and glitches annoy users and increase the chance of human error.
To enjoy the benefits of AI without creating unnecessary risks, you should choose a browser that:
No such browser with these specific features currently exists on the market. Also, all of these measures won’t suffice to protect you from phishing and scam sites and the risks associated with landing on them. So, in addition to a smart browser, it’ll be even more imperative to have an external system in place to deliver full-fledged protection of your computer and smartphone from cyberthreats.
Read about other AI-related risks:
- Should you disable Microsoft Recall in 2025?
- Is a Gemini AI update about to kill privacy on your Android device?
- Trojans masquerading as DeepSeek and Grok clients
- Google forcing Android System SafetyCore on users to scan for nudes
- Three approaches to workplace “shadow AI” from the cybersecurity standpoint
Kaspersky official blog – Read More

The familiar idiom “walk before you run” summarizes a fundamental truth about skill acquisition: you must master certain foundational capabilities before you can successfully execute more complex activities. This principle applies universally, from learning a new sport to developing highly specialized technical skills. Any area will have foundational skills, activities that anyone competent in the domain can perform, and characteristics that show that an individual (or team) has reached the highest levels of mastery.
Capability maturity models (CMMs) outline the hierarchy of skills and activities that may be required within a particular area. The capabilities and characteristics are listed for teams of different levels of maturity operating within a domain. These descriptions can be used to evaluate the current level of a team or to identify the capabilities that must be acquired in order to improve.
Despite its importance, the exact function of cyber threat intelligence (CTI) can vary widely across organizations. The community-developed Cyber Threat Intelligence Capability Maturity Model (CTI-CMM) shows how threat intelligence can help an organization and the various levels of capability that cyber threat intelligence teams can achieve.
The CTI-CMM lists 11 domains where CTI can greatly improve decision-making, and also details specific “missions” CTI can carry out to strengthen each domain.
|
Domain |
Abridged Description |
Example CTI Mission |
|
Asset, Change and Configuration Management |
Manage the organization’s IT and OT assets. |
Rapidly detect at-risk assets. |
|
Threat and Vulnerability Management |
Detect, identify, analyze, manage, and respond to cybersecurity threats and vulnerabilities. |
Reduce risk against new and emerging adversaries, malware, vulnerabilities, and exploits. |
|
Risk Management |
Identify, analyze and respond to cyber risk the organization is subject to. |
Improve risk decisions. |
|
Identity and Access Management |
Manage identities for entities that may be granted logical or physical access to the organization’s assets. |
Reduce incident detection times, accelerate remediation. |
|
Situational Awareness |
Establish situational awareness for operational state and cybersecurity state. |
Drive threat-informed decision-making based on the current and forecast threat landscape. |
|
Event and Incident Response, Continuity of Operations |
Respond to, and recover from cybersecurity events and incidents. |
Create an intelligence advantage for incident responders and strengthen the security posture. |
|
Third-Party Risk Management |
Manage the cyber risks arising from suppliers and other third parties |
Monitor, detect, assess and mitigate potential incidents posed by third-party vendors and suppliers. |
|
Fraud and Abuse Management |
Shield organizations from malicious digital scams and attacks. |
Share threats and findings with relevant stakeholders. |
|
Workforce Management |
Create a culture of cybersecurity and security competence. |
Support hardening of the human element. |
|
Cybersecurity Architecture |
Maintain the structure and behavior of the organization’s cybersecurity architecture. |
Provide insights into cyber threats that may target the organization. |
|
Cybersecurity Program Management |
Provides governance, strategic planning and sponsorship for the organization’s cybersecurity activities. |
Deliver tailored intelligence inputs to inform cybersecurity decision-making. |
The missions span a wide spectrum, from proactively monitoring an organization’s attack surface in support of asset management to providing crucial situational awareness of the evolving threat landscape and its direct relevance to organizational activities.
The CTI-CMM also defines distinct levels of maturity for threat intelligence activities, providing a clear progression path:
|
Level |
Characteristics |
|
CTI0 (Pre-Foundational) |
A placeholder for practices that are not executed. |
|
CTI1 (Foundational) |
Many threat intelligence activities begin here, characterized by basic, ad hoc and unplanned efforts focused on short-term, reactive results. |
|
CTI2 (Advanced) |
As an activity matures, it becomes planned, with documented procedures and metrics demonstrating its support for stakeholders. The focus shifts towards proactive and predictive intelligence, delivering short- and intermediate-term results. |
|
CTI3 (Leading) |
At the highest level, activities are highly refined, focusing on delivering long-term strategic outcomes for the business. This level integrates prescriptive intelligence and recommendations, combined with continuous improvement practices, making practices measurable and aligned directly to business objectives. |
The framework espouses an improvement process analogous to the “plan, do, check, act” management model. In this case, the steps within a cycle of improvement are “prepare, assess, plan, deploy, measure.” With each rotation through the cycle, the capabilities of the threat intelligence program are incrementally improved, growing the maturity of the program.

This approach to improving capabilities and benchmarking against defined standards is not new. CMMs originated in the mid-1980s, driven by the U.S. Department of Defense’s desire to compare and evaluate software contractors. Largely thanks to the efforts of the Software Engineering Institute (SEI) at Carnegie Mellon University, CMMs evolved into the widely-applied Capability Maturity Model Integration (CMMI).
The CTI-CMM adopts domains from the Cybersecurity Capability Maturity Model (C2M2), developed by the U.S. energy industry and first published in 2012. While the C2M2 acknowledged the importance of threat intelligence as a concept within overall cybersecurity posture, it did not specifically address the maturity of a dedicated threat intelligence program. However, the very first paper describing a maturity model for threat intelligence was published in the same year by the industry vendor Verisign. Thus, the origins of the CTI-CMM can be traced back to these two initiatives of the early 2010s.
It’s crucial for organizations to understand that aspiring to the highest level of CTI maturity is not always a practical goal. The intelligence program should focus on meeting the real needs of its users and stakeholders rather than seeking to hit a high score on an industry framework. An intelligence team with more resources may produce “better” intelligence and be more responsive. However, in a world of finite resources, those additional resources may be better spent in delivering “good enough” intelligence to teams that can use it well, rather than delivering the best intelligence to teams without the capacity or resources to effectively utilize the information.
Ultimately, the Cyber Threat Intelligence Capability Maturity Model (CTI-CMM) provides an invaluable resource for organizations to assess and evolve their CTI capabilities. As threat intelligence solidifies its role as an indispensable component of cybersecurity strategy, maturity models tools will become not only the drivers for internal organizational growth but also key instruments for external entities to benchmark and compare organizations’ overall cybersecurity maturity.
Cisco Talos Blog – Read More
The Lazarus Group, North Korea’s state-sponsored hacking collective, has held the title of the most notorious advanced persistent threat (APT) for almost two decades now. In 2025, it escalated its cyber operations, targeting tech industries with fake IT workers, fraudulent job interviews, and hijacked open-source software.
It’s time to take a closer look at its current activities and see how SOC teams can proactively detect and track the group attacks using ANY.RUN’s solutions.
Lazarus’s 2025 campaigns combine sophisticated social engineering and supply chain attacks, posing severe risks to businesses’ financial stability, data security, and operational continuity.
Since 2024, Lazarus Group has been deploying North Korean operatives posing as legitimate remote IT workers to infiltrate companies, particularly in the U.S. and UK. Using stolen or AI-enhanced identities, these operatives secure tech roles to steal sensitive data, deploy malware, or generate illicit revenue for North Korea.
According to the U.S. Department of Justice, these schemes compromised over 100 U.S. companies, including Fortune 500 firms. For example, an Atlanta-based blockchain company lost over $900,000 in virtual currency due to insider access by fake IT workers.
Beyond financial losses, businesses face reputational damage, loss of intellectual property, and regulatory scrutiny for hiring vulnerabilities. Extortion attempts, where operatives hold stolen data hostage, further disrupt operations and erode customer trust.
Operation 99 (aka “Contagious Interview”) is a campaign from Lazarus and its subgroups like Famous Chollima that targets tech, crypto developers and CEOs, with fake job and partnership interviews.
Posing as recruiters on LinkedIn, Telegram, or Calendly, Lazarus lures victims with fraudulent coding tests hosted on malicious GitLab repositories. As part of the scheme, Lazarus hackers utilize NPM packages.
For C-suite targets, criminals typically share fake Zoom executables and malware disguised as other software widely used in corporate environments.
The common losses for victims include stolen cryptocurrency and credentials, compromised systems, and disrupted operations. In some cases, device infections led to downstream supply chain attacks, affecting customers and partners. Crypto and tech firms rely on skilled developers, making them prime targets for social engineering. These attacks disrupt product development, expose proprietary code, and undermine trust in hiring processes, while recovery costs (e.g., system remediation, legal fees) strain budgets.
Despite doing it since September 2024, Lazarus Group continues to embed malicious backdoors in cloned open-source software packages on repositories like GitHub and PyPI, targeting developers in both medium and large enterprises. Over 230 malicious packages have been identified since the start of 2025, affecting 36,000 firms in Europe, India, and Brazil.
Victims face losses from stolen credentials, authentication tokens, and system data, with recovery costs exceeding millions. Open-source software is critical to tech and crypto industries.
Given that many IT companies work in tight cooperation, a successful attack on an endpoint at one firm can lead to major incidents in other businesses down the supply chain. A notable example here is the $1.5 billion ByBit hack orchestrated by Lazarus.
The initial compromise occurred on a developer’s machine at Safe{Wallet}, a multisignature provider used by ByBit, through a malicious Docker project. From there, the attackers gained access to Safe{Wallet}’s Amazon Web Services (AWS) S3 bucket and managed to push a malicious script to the system. This resulted in ByBit’s transaction being hijacked and the funds funneled to a wallet controlled by Lazarus Group.
Lazarus’s 2025 operations leverage advanced malware and TTPs, tailored to maximize damage to businesses through data theft, system compromise, and financial extortion.
To detect such attacks early, SOC teams require a reliable solution for proactive analysis of suspicious files and URLs. ANY.RUN’s Interactive Sandbox provides a fast, isolated, and hands-on way to expose malware and phishing in seconds.
Let’s take a look at several examples of malware families employed by Lazarus Group in their attacks and see how sandboxing simplifies their identification.
 How Interactive Sandbox boosts SOCs
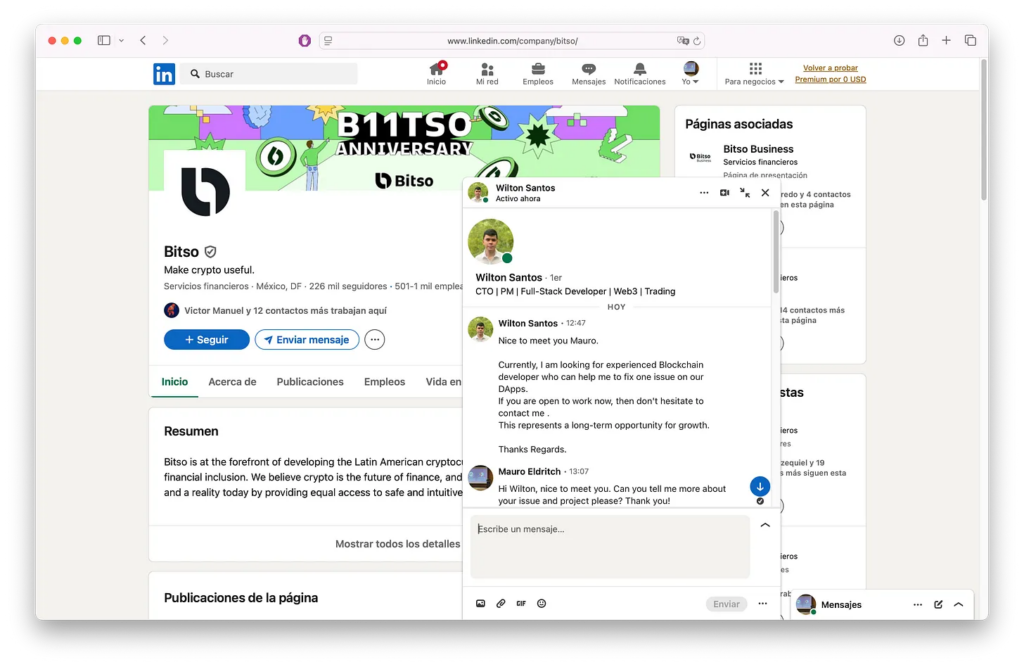
How Interactive Sandbox boosts SOCs InvisibleFerret is a modular malware often deployed by Lazarus hackers via fake job interviews, capable of keylogging, screen capturing, and establishing persistent C2 connections to steal sensitive data.
Read technical analysis of InvisibleFerret
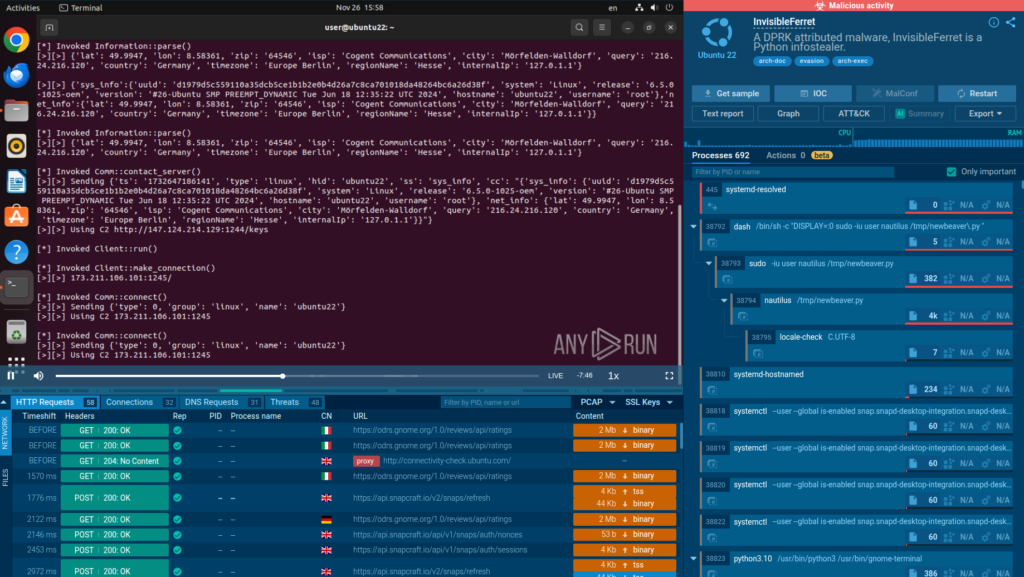
InvisibleFerret compromises developer endpoints, exposing proprietary code and client data.
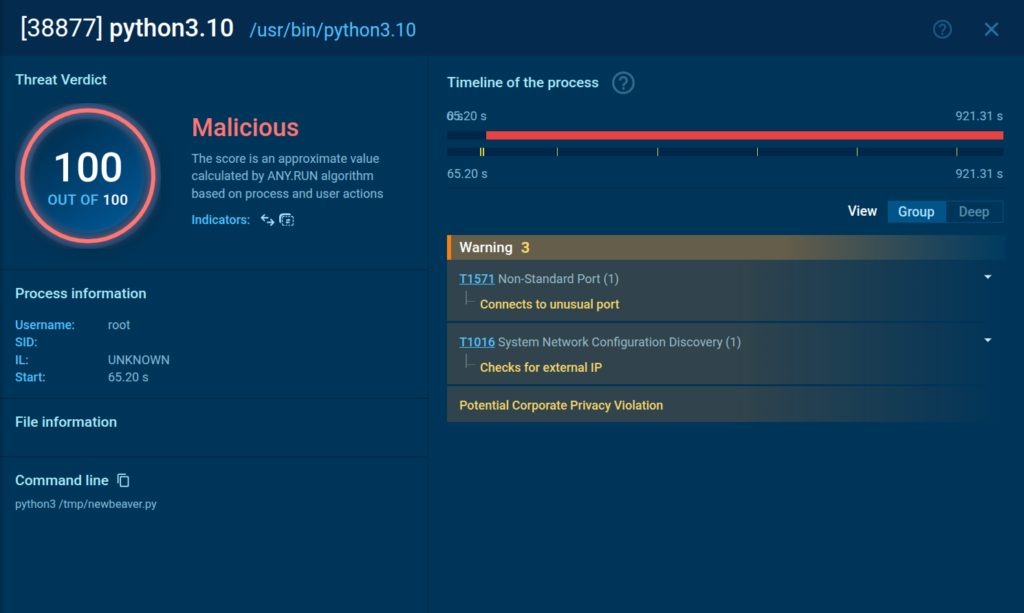
As shown in a sandbox analysis session, the malware engages in several activities on an infected system, such as attempting to connect to an unusual port. In a business setting, armed with this knowledge, SOCs can act proactively and prevent the incident, keeping the network safe.
OtterCookie is a malware which is often embedded in hijacked open-source packages. It is used as part of the Contagious Interview campaign to extract authentication tokens, session data, and crypto wallets. Stolen tokens allow attackers to bypass authentication, access corporate systems, or customer accounts.
Read technical analysis of OtterCookie
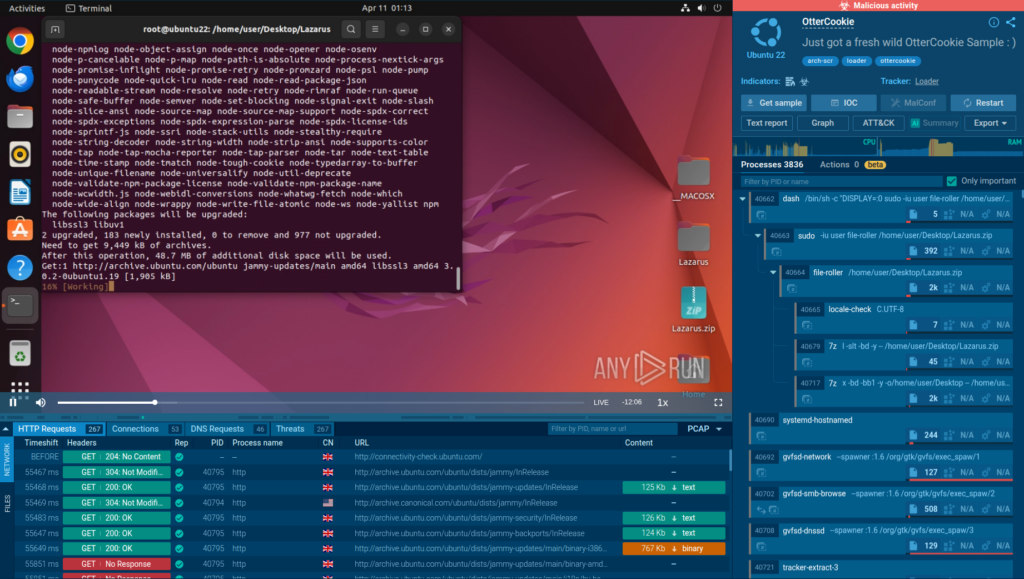
Thanks to the analysis inside ANY.RUN’s Interactive Sandbox, we can observe the entire attack chain for this malware.
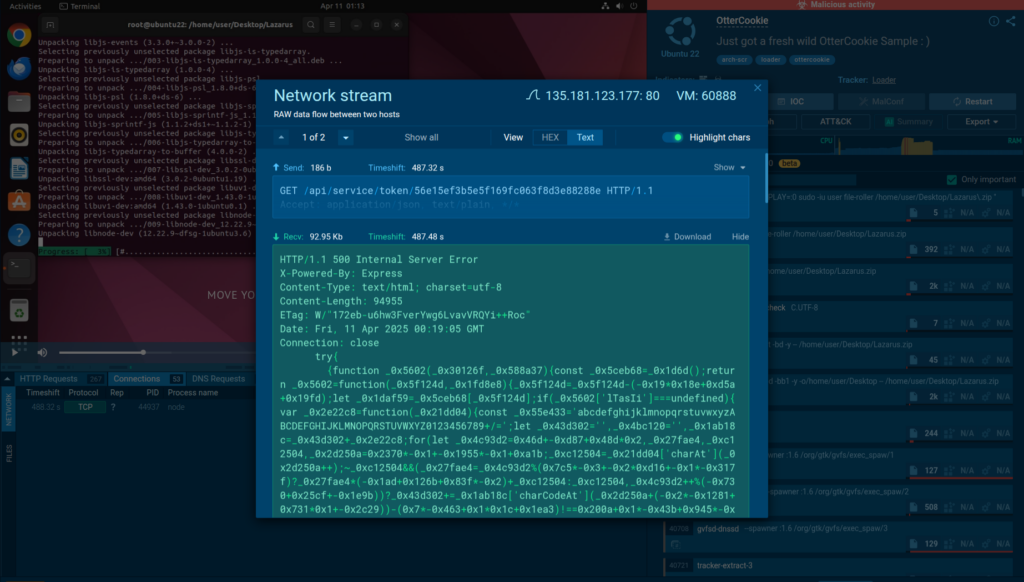
The sandbox session shows that attackers use a fake error and a try/catch block to download and run a piece of malicious code responsible for deploying OtterCookie on the system. This is an evasion technique which may escape detection by signature-based solutions.
With ANY.RUN’s advanced threat tracking, we get notified about the malicious activity and can stop the attack early, keeping our company’s infrastructure secure and free from disruptions.
PyLangGhost is a relatively new remote access trojan from Lazarus APT. Delivered via fake interviews or malicious packages, it enables long-term espionage and data theft, compromising trade secrets and customer data. As a result of its activities, businesses may face prolonged downtime during remediation and regulatory fines for data breaches.
Read technical analysis of OtterCookie
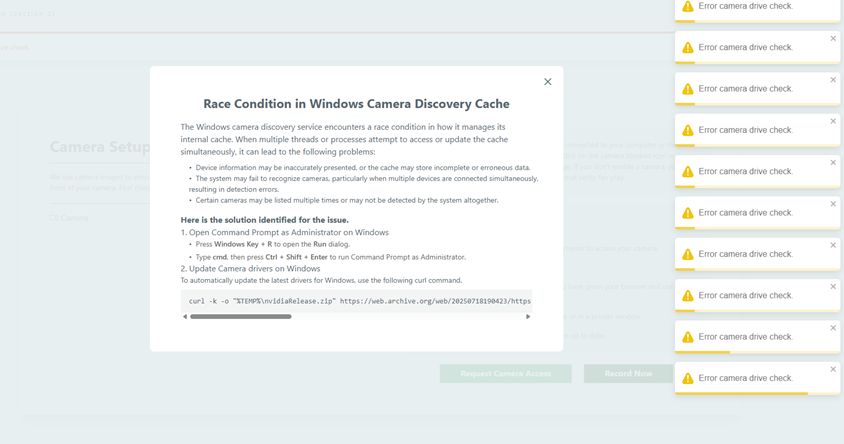
The malware has been observed in attacks involving the use of the ClickFix tactic, a trick that presents victims with a fake page instructing them to run a malicious script on their system as a way to solve an error or verify their identity.
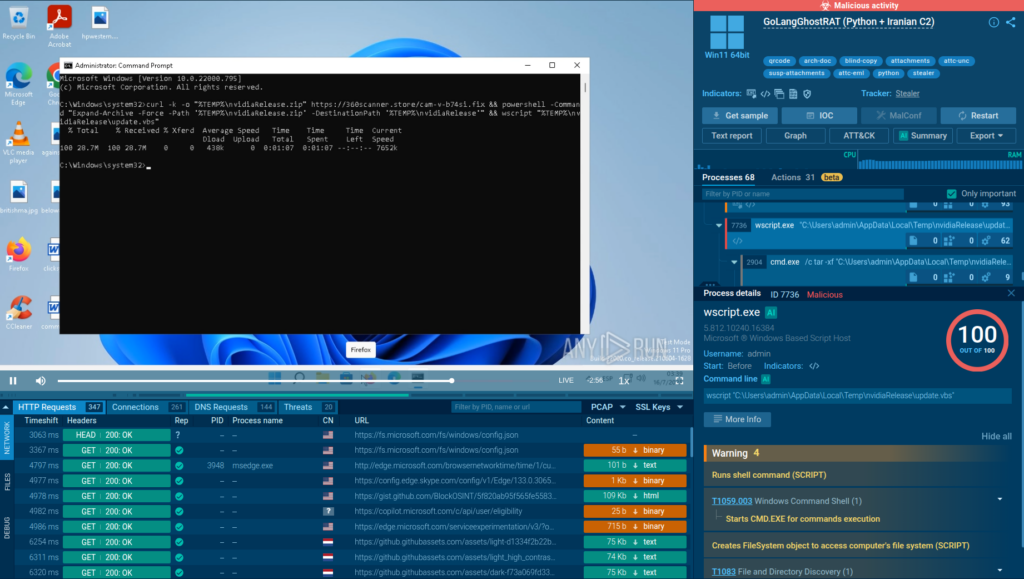
In the case of PyLangGhost, users were often asked to paste and run a command on their computer to fix an issue with their camera. Using the interactivity of ANY.RUN’s sandbox, we can manually perform these actions in an isolated, cloud-based virtual environment to trigger the threat’s execution. The result is a malware being installed on the system, as you can see in the analysis.
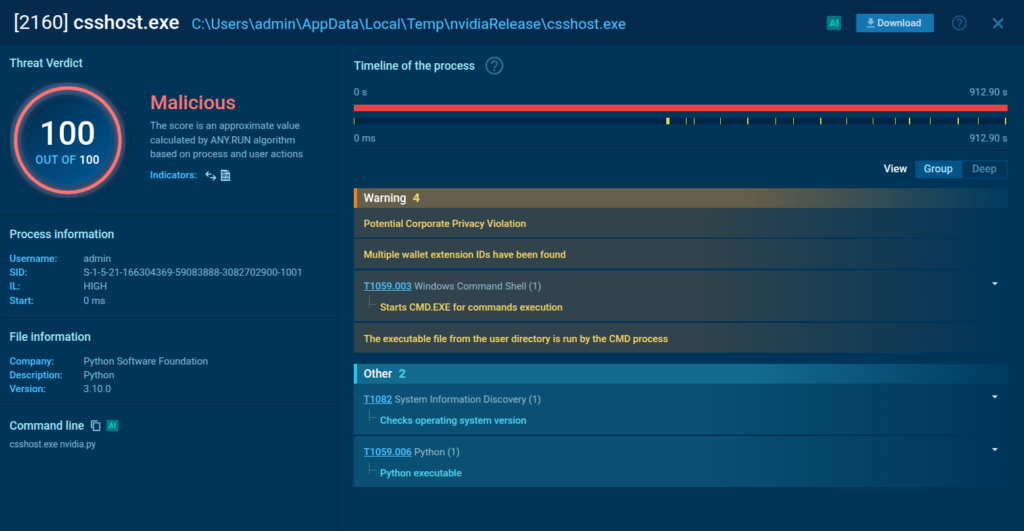
The sandbox marks the processes spawned by the threat as malicious, providing analysts with a definitive and actionable verdict for instant incident resolution.
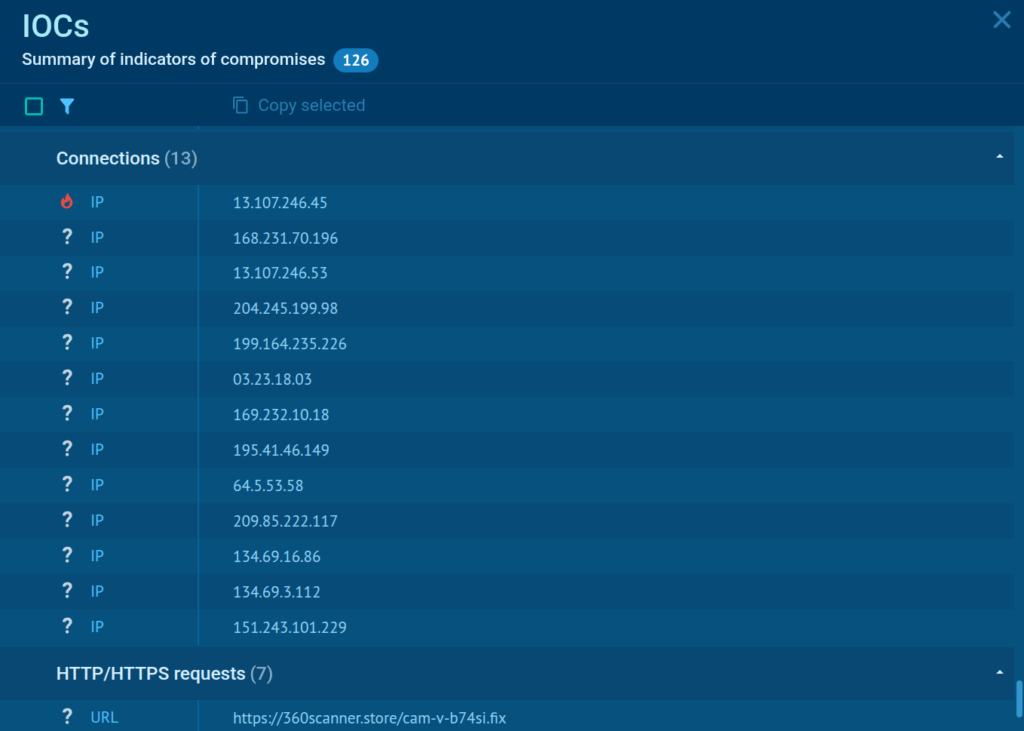
Once the investigation is over, we can collect the indicators of compromise (IOCs) gathered by ANY.RUN and use them to create detection rules to spot future attacks in advance.
To keep up with the evolution of Lazarus Group’s attacks, we can utilize ANY.RUN’s Threat Intelligence Lookup. It is a free-access database of the latest indicators of compromise, behavior (IOBs), and attack (IOAs). This data is extracted from live sandbox analyses of active malware and phishing attacks across 15,000 SOCs, ensuring the indicators are fresh and available quickly after an attack.
To see examples of Lazarus Group’s recent attacks, we can start with a simple query:
threatName:”lazarus”
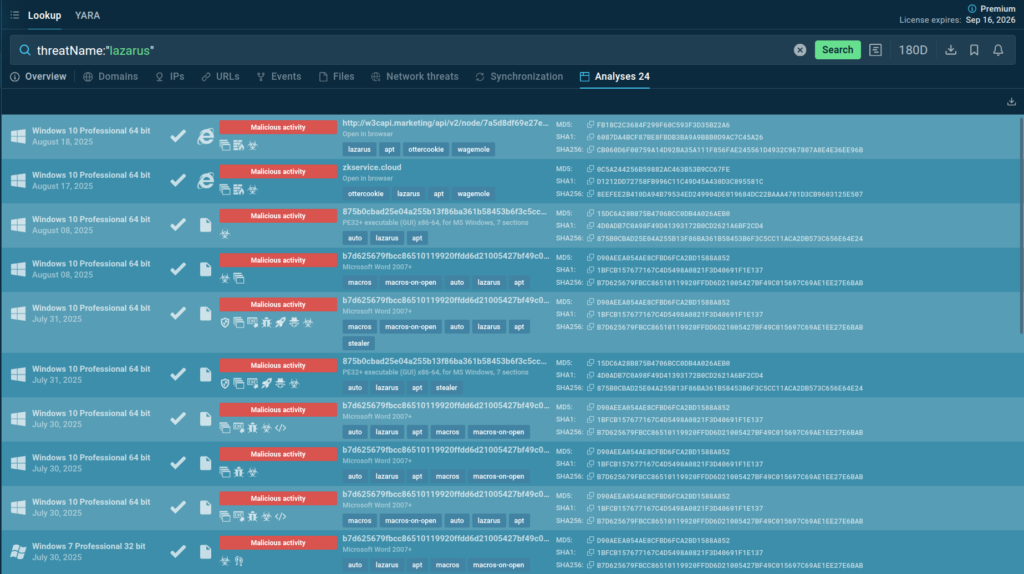
The service provides us with a list of sandbox sessions with threats attributed to the Lazarus APT. This provides us with rich context about the current malware families, TTPs, and campaigns run by the group. For example, as visible from a report from August 17, the OtterCookie malware is still in use.
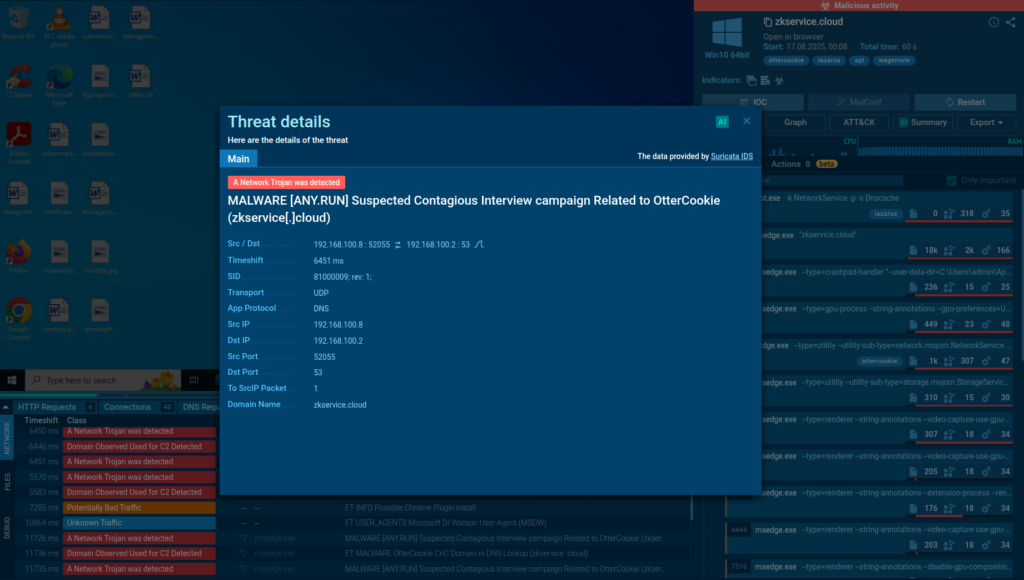
We can dive deeper into each report to collect actionable indicators for detection rules and see what threats the North Korean hackers are using right now.
With TI Lookup, SOC teams can:
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN to streamline malware investigations worldwide.
Speed up triage and response by detonating suspicious files in ANY.RUN’s Interactive Sandbox, observing malicious behavior in real time, and gathering insights for faster, more confident security decisions. Paired with Threat Intelligence Lookup and Threat Intelligence Feeds, it provides actionable data on cyberattacks to improve detection and deepen your understanding of evolving threats.
Explore more ANY.RUN’s capabilities during 14-day trial→
The post Lazarus Group Attacks in 2025: Here’s Everything SOC Teams Need to Know appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
Given the serious financial and reputational risks of incidents that grind business to a halt, organizations need to prioritize a prevention-first cybersecurity strategy
WeLiveSecurity – Read More

Microsoft has released its monthly security update for September 2025, which includes 86 vulnerabilities affecting a range of products.
In this month’s release, Microsoft observed none of the included vulnerabilities being exploited in the wild. However, there are eight vulnerabilities where exploitation may be likely. Five consist of elevation of privileges, two may result in information disclosure and only one, CVE-2025-54916, is a remote code execution (RCE) vulnerability.
CVE-2025-54916 is an RCE vulnerability caused by a stack-buffer overflow in Windows NTFS that allows an authorized attacker to execute code over the network. Microsoft has noted that this vulnerability affects different versions of Windows 10, 11, Server 2008, 2012, 2016, 2019, 2022 and 2025.
CVE-2025-54910 is an RCE vulnerability caused by a heap-based buffer overflow in Microsoft Office that allows an unauthorized attacker to execute code locally. This type of vulnerability is also known as Arbitrary Code Execution (ACE). Microsoft clarifies that the attack itself is carried out locally, and that the location of the attacker can be remote, but the vulnerability must be exploited locally. This vulnerability affects Microsoft 365 Apps, Office 2016, 2019 and LTSC 2021 and 2024.
CVE-2025-54918 is an elevation of privilege (EoP) vulnerability caused by improper authentication in Windows NTLM that allows an authorized attacker to elevate privileges over a network to gain SYSTEM privileges. This vulnerability affects various versions of Windows including Windows 10, 11, Server 2008, 2012, 2016, 2019, 2022 and 2025.
CVE-2025-54101 is an RCE vulnerability caused by a use-after-free in Windows SMB v3 Client/Server that allows an authorized attacker to execute code over a network. Successful exploitation requires the attacker to win a race condition. This vulnerability affects various versions of Windows including Windows 10, 11, Server 2008, 2012, 2016, 2019 and 2022.
Two RCE vulnerabilities in DirectX Graphics kernel may result in remote code execution: CVE-2025-55226 and CVE-2025-55236. CVE-2025-55226 is caused by concurrent execution using a shared resource and improper synchronization in the Graphics Kernel allowing an authorized attacker to execute code locally. Microsoft also notes that this vulnerability requires an attacker to prepare the target environment to improve exploit reliability. This vulnerability affects various versions of Windows including Windows 10, 11, Server 2008, 2012, 2016, 2019, 2022 and 2025.
CVE-2025-55236 is a time-of-check time-of-use (toctou) race condition in the Graphics Kernel allowing an authorized attacker to execute locally. This vulnerability affects various versions of Windows including Windows 10, 11, Server 2019, 2022 and 2025.
Talos would also like to highlight the following important vulnerabilities as Microsoft has assessed that their exploitation is more likely:
CVE-2025-53803: Windows Kernel Memory Information Disclosure Vulnerability.
CVE-2025-53804: Windows Kernel-Mode Driver Information Disclosure Vulnerability.
CVE-2025-54093: Windows TCP/IP Driver Elevation of Privilege Vulnerability.
CVE-2025-54098: Windows Hyper-V Elevation of Privilege Vulnerability.
CVE-2025-54110: Windows Kernel Elevation of Privilege Vulnerability.
A complete list of all the other vulnerabilities Microsoft disclosed this month is available on its update page.
In response to these vulnerability disclosures, Talos is releasing a new Snort ruleset that detects attempts to exploit some of them. Please note that additional rules may be released at a future date, and current rules are subject to change pending additional information. Cisco Security Firewall customers should use the latest update to their ruleset by updating their SRU. Open-source Snort Subscriber Ruleset customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Snort2 rules included in this release that protect against the exploitation of many of these vulnerabilities are: 65327 – 65334.
The following Snort3 rules are also available: 301310 – 301313.
Cisco Talos Blog – Read More
ANY.RUN’s Threat Intelligence Feeds are designed to power SOAR, SIEM, EDR/XDR, TIP, and other security systems. Our goal is simple: to fit naturally into a customer’s security ecosystem so analysts can investigate incidents faster, improve detection quality, and spend less time on repetitive tasks.
Now, IBM QRadar SIEM users can directly consolidate ANY.RUN’s Threat Intelligence Feeds to strengthen detection and triage capabilities — all from a single console.
IBM QRadar SIEM is a leading Security Information and Event Management solution that centralizes visibility across IT infrastructure, enables real-time threat detection through log and flow analysis, and incorporates advanced analytics like AI and user behavior monitoring.
The integration with TI Feeds helps teams using QRadar SIEM boost their security with high-quality threat intelligence. They deliver malicious IPs, domains, URLs extracted from live sandbox analyses of the latest threats hitting 15,000+ organizations worldwide. Unlike post-incident reports that lag behind, our feeds update in real time sending active attack indicators straight to clients.
Automatically correlate logs and events with the latest IOCs to spot the latest threats, reduce mean time to detect/respond (MTTD/MTTR), and lower analyst burnout.
ANY.RUN provides more than indicators — our data includes sandbox reports that provide actionable behavioral context (IOCs, IOBs, IOAs), helping SOC teams understand how threats operate.
Identify threats earlier in the kill chain to stop and mitigate attacks before they impact business operations
Automated correlation reduces manual research time, allowing analysts to focus on investigation and response rather than IOC verification and threat hunting.
Faster threat detection translates directly to reduced potential damage from security incidents, while improved analyst efficiency lowers operational costs.
API, SDK, and STIX/TAXII formats are supported to seamlessly bring the feeds into your existing architecture. No redesigning workflows, no extra costs.
For SOC level 1-2 analysts, the IBM-ANY.RUN connection fuels:
The ANY.RUN TI Feeds application is available through the IBM X-Force App Exchange marketplace, ensuring compatibility and support within IBM’s security ecosystem.
Deployment:
Requirements:
Consider a typical enterprise environment where network traffic and infrastructure logs flow into IBM QRadar SIEM. When the ANY.RUN TI Feeds connection is active:
This workflow turns reactive threat hunting into proactive threat detection, with verified threats automatically surfaced for investigation, near-zero false positives, and faster investigation and triage.
By combining QRadar’s proven correlation and alerting capabilities with ANY.RUN’s real-time, high-fidelity threat intelligence, organizations can achieve:
The ANY.RUN TI application is available now through the IBM X-Force App Exchange for organizations with active ANY.RUN Threat Intelligence Feeds subscriptions.
ANY.RUN is trusted by more than 500,000 cybersecurity professionals and 15,000+ organizations across finance, healthcare, manufacturing, and other critical industries. Our platform helps security teams investigate threats faster and with more clarity.
Speed up incident response with our Interactive Sandbox: analyze suspicious files in real time, observe behavior as it unfolds, and make faster, more informed decisions.
Strengthen detection with Threat Intelligence Lookup and TI Feeds: give your team the context they need to stay ahead of today’s most advanced threats.
Want to see it in action? Start your 14-day trial of ANY.RUN today →
The post ANY.RYN x IBM QRadar SIEM: Real-Time Intelligence for Wider Threat Coverage appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
Several popular npm packages used in a number of web projects have been compromised and trojanized by unknown attackers. The attackers, through a phishing attack on maintainers, were able to gain access to at least one repository and injected the packages with malicious code used to hunt for cryptocurrency. Thus, all web applications that used trojanized versions of the packages were turned into cryptodrainers. And there can be quite a few of them — as the compromised packages had more than two billion downloads per day (according to Aikido Security).
Obfuscated JavaScript was added to all affected packages. If the compromised package is used in a web application, the malicious code is activated on the devices that were used to access this application. Acting at the browser level, malware intercepts network traffic and API requests, and changes data associated with Ethereum, Bitcoin, Solana, Litecoin, Bitcoin Cash, and Tron cryptocurrency wallets. The malware spoofs their addresses and redirects transactions to the attackers’ wallets.
About three hours after the attack began, the npm administration started to remove the infected packages, but it’s not known exactly how many times they were downloaded during this time.
The attackers used a rather banal technique — they created a phishing email in which maintainers were urged to update their two-factor authentication credentials at the first opportunity. Otherwise, they were threatened with account lockout starting September 10, 2025. The emails were sent from a mailbox on the domain npmjs[.]help, similar to the legitimate npmjs.com. The same domain also hosted a phishing site that mimicked the official npm registry page. Credentials entered on this site immediately fell into the hands of the attackers.
The attack was successful against at least one maintainer, compromising the npm packages color, debug, ansi-regex, chalk, and several others. However, the phishing attack appears to have been more extensive, because other maintainers and developers received similar phishing emails, so the full list of trojanized packages may be longer.
At the time of writing this post, the following packages are known to be compromised:
However, as we have already written above, the list may grow. You can keep an eye on the GitHub advisory page for updates.
Kaspersky Lab products, both for home and for corporate users, successfully detect and stop the malware used in this attack.
Developers are advised to audit the dependencies in their projects, and if one of the compromised packages was used there, pin the safe version using the overrides function in package.json. You can find more detailed instructions here.
Maintainers and developers with access to open source software repositories are advised to be doubly careful when receiving emails urging them to log into their accounts. Better yet — also use security solutions with an anti-phishing engine.
Kaspersky official blog – Read More

Talos IR associates specific adversary actions with pre-ransomware activity. When threat actors attempt to gain enterprise-level domain administrator access, they often conduct a series of account pivots and escalations, deploy command-and-control (C2) or other remote access solutions, harvest credentials and/or deploy automation to execute the modification of the OS. Though the specific tools or elements in the attack chain vary by adversary, Talos IR has seen these same classic steps in practice for years. These actions, along with observed indicators of compromise (IOCs) or tactics, techniques and procedures (TTPs) that we associate with known ransomware threats without the end result of enterprise-wide encryption, lead us to categorize an incident as “pre-ransomware.”
It is worth noting that some of the above attack techniques are also often deployed by initial access brokers (IABs) who seek to gain and sell access to compromised systems, and it is possible some of the incidents involved in this case study could have therefore been perpetrated by IABs instead of ransomware operators. While it is often challenging to determine a threat actor’s end goal, we have high confidence that all incidents involved tactics are consistently seen preceding ransomware deployment. If the adversary was instead an IAB, we have seen these types of IAB campaigns very frequently result in a ransomware attack after access has been sold, rendering the activity relevant to this analysis.
Talos analyzed incident response engagements spanning the past two and a half years that we categorized as pre-ransomware attacks, identifying actions and security measures that we assessed were key in halting adversaries’ attack chains before encryption. An overview of our findings can be found in Figure 1, followed by a more thorough breakdown of each category to explore exactly how certain actions impeded ransomware execution.

Engaging Talos IR within one to two days of first observed adversary activity (though we advise engagement as quickly as possible) was credited with preventing a more serious ransomware attack in approximately a third of engagements, providing benefits such as:
We observed numerous incidents where Talos IR was not engaged by the customer immediately, which enabled the adversary to continue working through their attack chain and conduct data theft and/or ransomware deployment. This often results in consequences such as backup files being corrupted or encrypted, endpoint detection and response (EDR) and other security tools being disabled, disruption to day-to-day operations and more.
Vigilant monitoring of security solutions and logs allows network administrators to act quickly when a threat is first detected, isolate the malicious activity and cut off threat actors’ ability to escalate their attack. In our case study, action from the security team within two hours of an alert from the organization’s EDR or managed detection and response (MDR) solution correlated with successful isolation of the threat in almost a third of engagements. Some of the observed alerts that prompted swift response in pre-ransomware engagements included, amongst others:
whoamiIn almost 15 percent of engagements, targeted organizations were able to get ahead of the threat to their environment due to notification from U.S. government (USG) partners and representatives of their managed service provider (MSP) about possible ransomware staging in their environment. In particular, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) has launched an initiative to provide early warnings about potential ransomware attacks, aiming to help organizations detect threats and evict actors before significant damage occurs. CISA’s intelligence predominately derives from their partnerships with the cybersecurity research community, infrastructure providers and cyber threat intelligence companies.
In over 10 percent of Talos IR engagements, customers’ security solutions actively blocked and/or quarantined malicious executables, effectively stopping adversaries’ attack chains in their tracks.
Talos often observes organizations deploying endpoint protection technology in a passive manner, meaning the product is producing alerts to the user but not taking other actions. This configuration puts organizations at unnecessary risk, and Talos IR has responded to multiple engagements where passive deployment enabled threat actors to execute malware, including ransomware. A more aggressive configuration impeded ransomware deployment in this case study, underscoring its importance.
Based on our analysis, organizations’ robust security restrictions were key in impeding ransomware actors’ attack chains in nine percent of engagements. For example, in one engagement, the threat actors compromised a service account at the targeted organization, but appropriate privilege restrictions on the account prevented their attempts to access key systems like domain controllers.
Also of note, organizations who implemented thorough logging and/or had a SIEM in place to aggregate event data were able to provide Talos with forensic visibility to determine the exact chain of events and where additional security measures could be implemented. When an organization lacks these records, it can be challenging to identify the precise security weaknesses that enabled threat activity.
Upon categorizing TTPs observed in this case study per the MITRE ATT&CK framework, Talos found that the following in Figure 2 were most frequently seen across engagements.

We dove deeper into some of the top attack techniques and found the following:
The top observed TTPs serve as a reminder to security teams on what malicious activity often preempts a more severe attack. For example, prioritizing moderating the use of remote services and remote access software and/or securing the aforementioned credential stores could assist in limiting the majority of adversaries seen in these pre-ransomware engagements.
Talos IR crafts security recommendations for customers in each incident upon analyzing the environment and the adversary’s attack chain to help address any existing security weaknesses. Our most frequent recommendations include:
Cisco Talos Blog – Read More