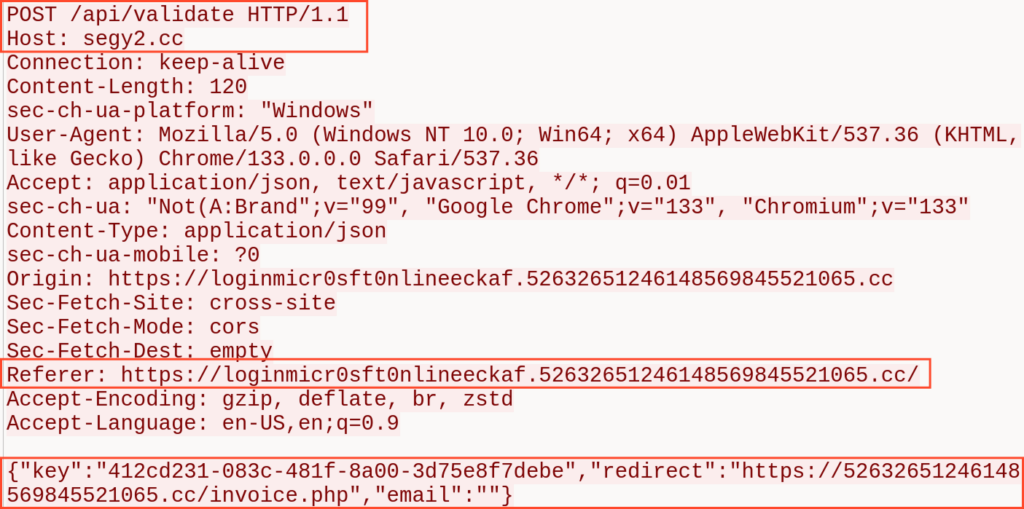
When we interact with artificial intelligence, we often share a significant amount of personal information without giving it much thought. This information can range from dietary preferences and marital status to our home address and even social security number. To ensure the security and privacy of this highly sensitive information, it’s essential to understand exactly what the AI does with your data: where it stores it and whether it uses it for training.
In this post, we take a closer look at the data collection policy of one of the most popular AI apps, ChatGPT, and explain how to configure it to maximize your privacy and security to the extent that OpenAI allows it. This is a long guide — but a comprehensive one.
Table of contents
What data ChatGPT collects about you
OpenAI, the owner and developer of ChatGPT, maintains two privacy policies. The specific policy that applies to users depends on the region where that individual registered their account:
Because these policies are similar, we’ll first cover the common elements, and then discuss the differences.
By default, OpenAI collects an extensive array of personal information and technical data about devices from all ChatGPT users.
- Account information: name, login credentials, date of birth, billing information, and transaction history
- User content: prompts as well as uploaded files, images, and audio
- Communication information: contact details the user provided when reaching out to OpenAI via email or social media
- Log data: IP address, browser type and settings, request date and time, and details about how the user interacts with OpenAI services
- Usage data: information about the user’s interaction with OpenAI services, such as content viewed, features used, actions taken, and technical details like country, time zone, device, and connection type
- Device information: device name, operating system, device identifiers, and the browser used
- Location information: the region determined by the IP address, rather than the exact location
- Cookies and similar technologies: necessary for service operation, user authentication, enabling specific features, and ensuring security; the complete list of cookies and their respective retention periods is available here
What exactly OpenAI does with the data it collects from individual users will be discussed in the next part of this post. Here, we indicate the key difference between the privacy policies for users from the European Economic Area (EEA) and those from other regions. European users have the right to object to the use of their personal data for direct marketing. They may also challenge data processing where the company justifies this by its “legitimate interests”, such as internal administration or improvements to services.
Note that OpenAI’s handling of data for business accounts is governed by separate rules that apply to ChatGPT Business and ChatGPT Enterprise subscriptions, as well as API access.
What OpenAI does with your data, and whether ChatGPT is trained on your chats
By default, ChatGPT can train its models on user prompts and the content that users upload. This policy applies to users of both the free version and the Plus and Pro subscriptions.
For business accounts — specifically ChatGPT Enterprise, ChatGPT Business, and API access — training on user data is disabled by default. However, in the case of the API (the application programming interface that connects OpenAI models to other applications and services — the simplest use case being ChatGPT-based customer support bots), the company provides developers with the option to voluntarily enable data transmission.
OpenAI outlines a comprehensive list of primary purposes for processing users’ personal information:
- To maintain services: to respond to queries and assist users
- To improve and develop services: to add new features and conduct research
- To communicate with users: to notify users about changes and events
- To protect the security of services: to prevent fraud and ensure security
- To comply with legal obligations: to protect the rights of users, OpenAI, and third parties
The company also states that it may anonymize users’ personal data, though it does not obligate itself to do so. Furthermore, OpenAI reserves the right to transfer user data to third parties — specifically its contractors, partners, or government agencies — if such transfer is necessary for service operation, compliance with the law, or the protection of rights and security.
As the company notes on its website: “In some cases, models may learn from personal information to understand how elements like names and addresses function in language, or to recognize public figures and well-known entities”.
It’s important to note that all user data is processed and stored on OpenAI servers in the United States. Although the level of personal information protection may vary from country to country, the company asserts that it applies uniform security measures to all users.
How to prevent ChatGPT from using your data for AI training
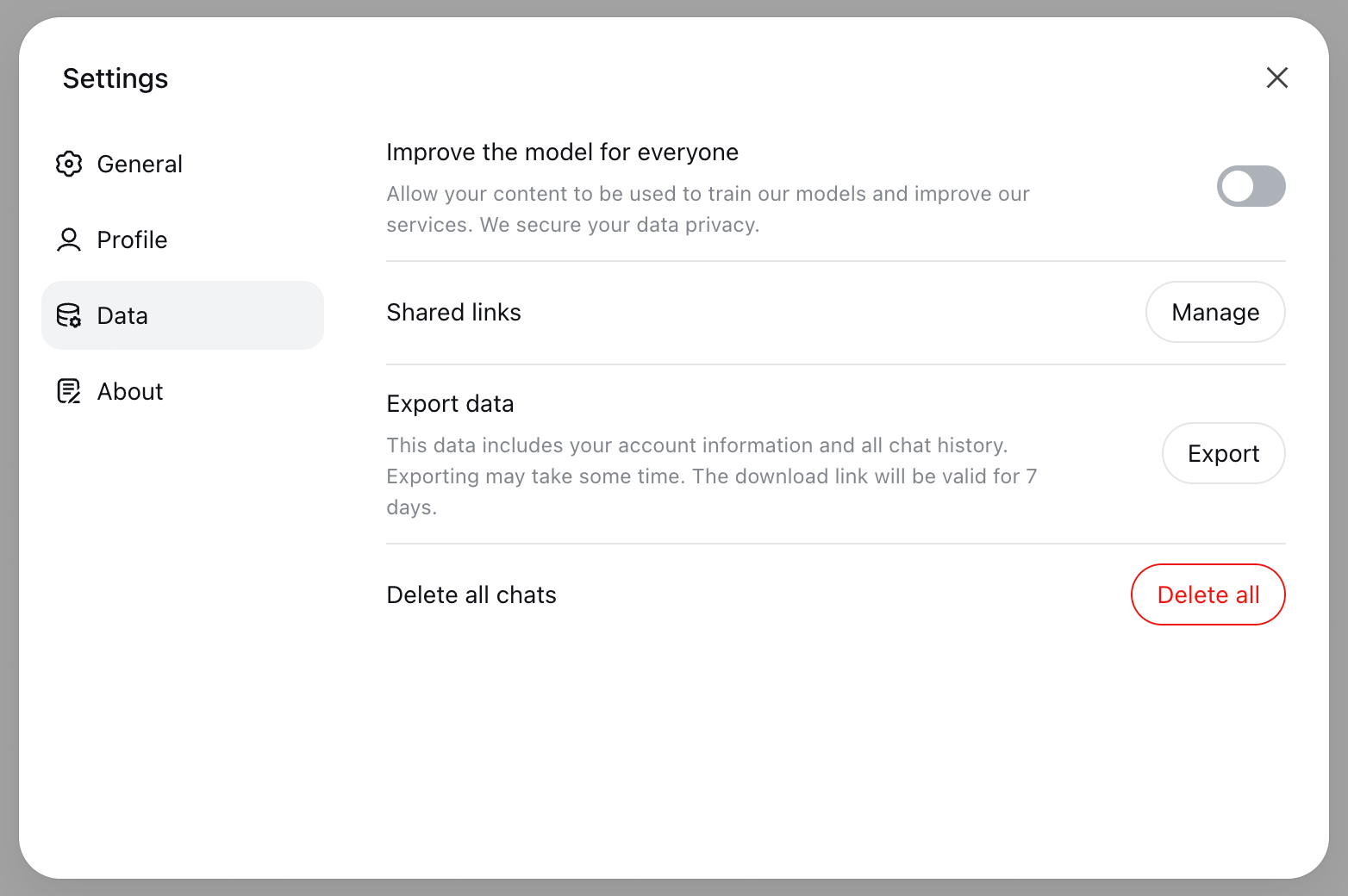
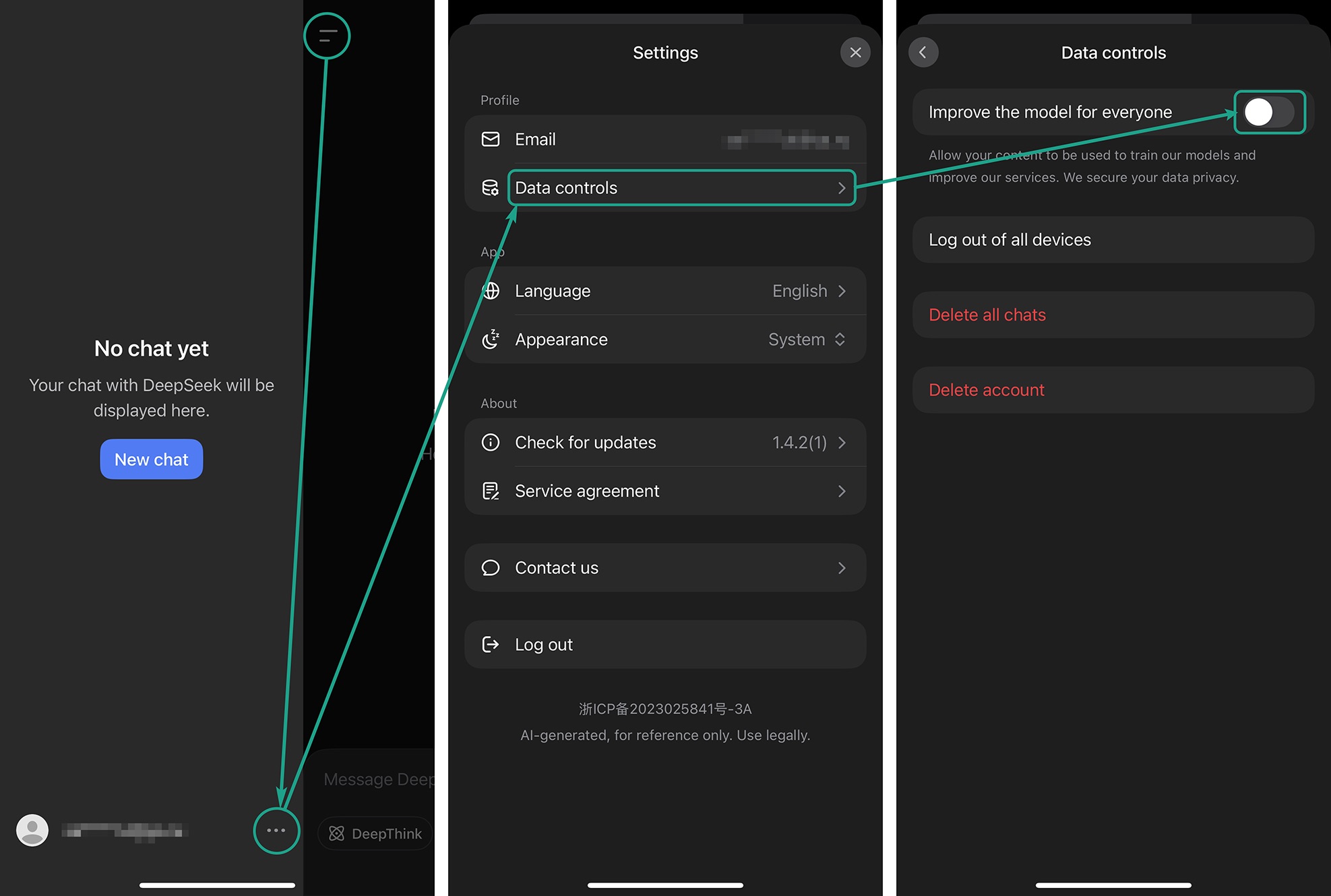
To disable the collection of your data within the app, click your account name in the lower left corner of the screen. Select Settings, then navigate to Data controls.
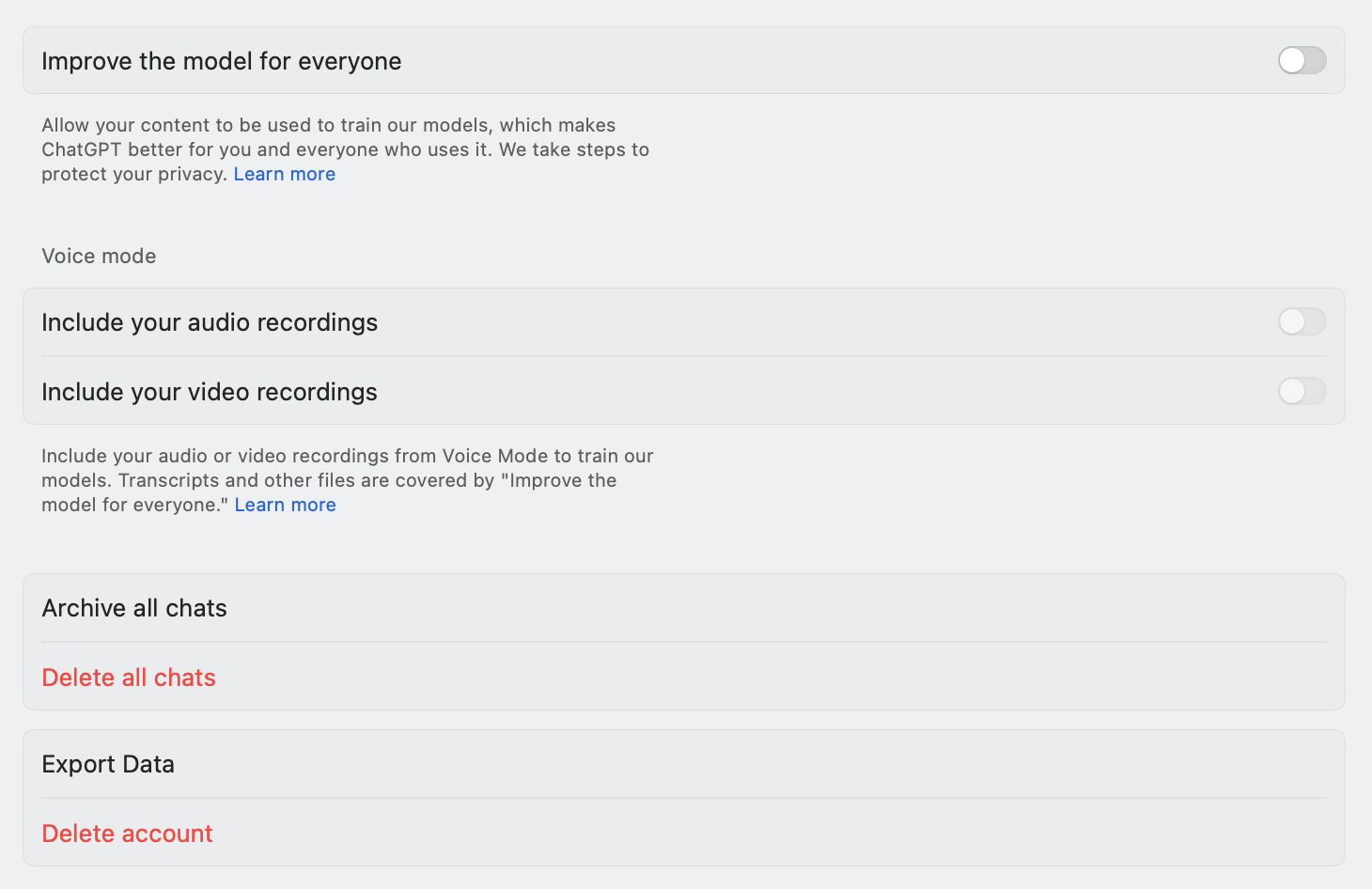
In the Data controls section of the ChatGPT settings, you can disable the use of your prompts for model training
In Data controls, turn off the toggles next to the following items:
- Improve the model for everyone: disabling this option prevents the use of your prompts and uploads (text, files, images) for model training. Turning this off deactivates the two items below it
- Include your audio recordings: disabling this option prevents the voice messages from the dictation feature from being used for model training. It’s disabled by default
- Include your video recordings: this refers to the feature that allows you to include a video stream from your camera during a voice chat in the ChatGPT apps for iOS and Android. This video stream may also be used for model training. You can also disable this option through the web application. It’s disabled by default
By turning off these settings, you prevent the use of new data for model training. However, it’s important to realize: if your prompts or content were already used for training before you disabled the option, it’s impossible to remove them from the trained model.
In this same section, you can delete or archive all chats, and also request to Export Data from your account. This allows you to check what information OpenAI stores about you. A data archive will be sent to your email. Please note that preparing an export may take some time.
The Delete account option is also available here. When your account is deleted, only your personal data is erased; information already used for model training remains.
Beyond the in-app settings, you can manage your data through the OpenAI Privacy Portal. On the portal, you can:
- Request and download all your data stored by OpenAI
- Completely delete your custom GPTs, as well as your ChatGPT account and the personal data associated with it
- Ask OpenAI not to train the AI on your data. If OpenAI approves your request, the AI will stop training on the data you provided before you disabled the Improve the model for everyone option in the settings
- Sometimes ChatGPT may also train on personal data from public sources — you can submit a request to stop this as well
- Request the deletion of personal data from specific conversations or prompts
Users from the European Economic Area, the UK, and Switzerland have additional rights under the GDPR. The law is in effect in European countries and regulates how companies collect and use personal data. These rights are not directly displayed on the OpenAI Privacy Portal, but they can be exercised by submitting a request through the portal, or by writing to dsar@openai.com.
How to clear your data from ChatGPT’s memory
Another critical element of privacy protection is ChatGPT’s memory. Unlike chat history, memory allows the model to recall specific details about you, such as your name, interests, preferences, and communication style. This data persists across sessions and is used to personalize the AI’s responses.
To review exactly what the AI remembers within the app, click your account name in the lower-left corner of the screen. Choose Settings, then navigate to Personalization, and select Manage memories.
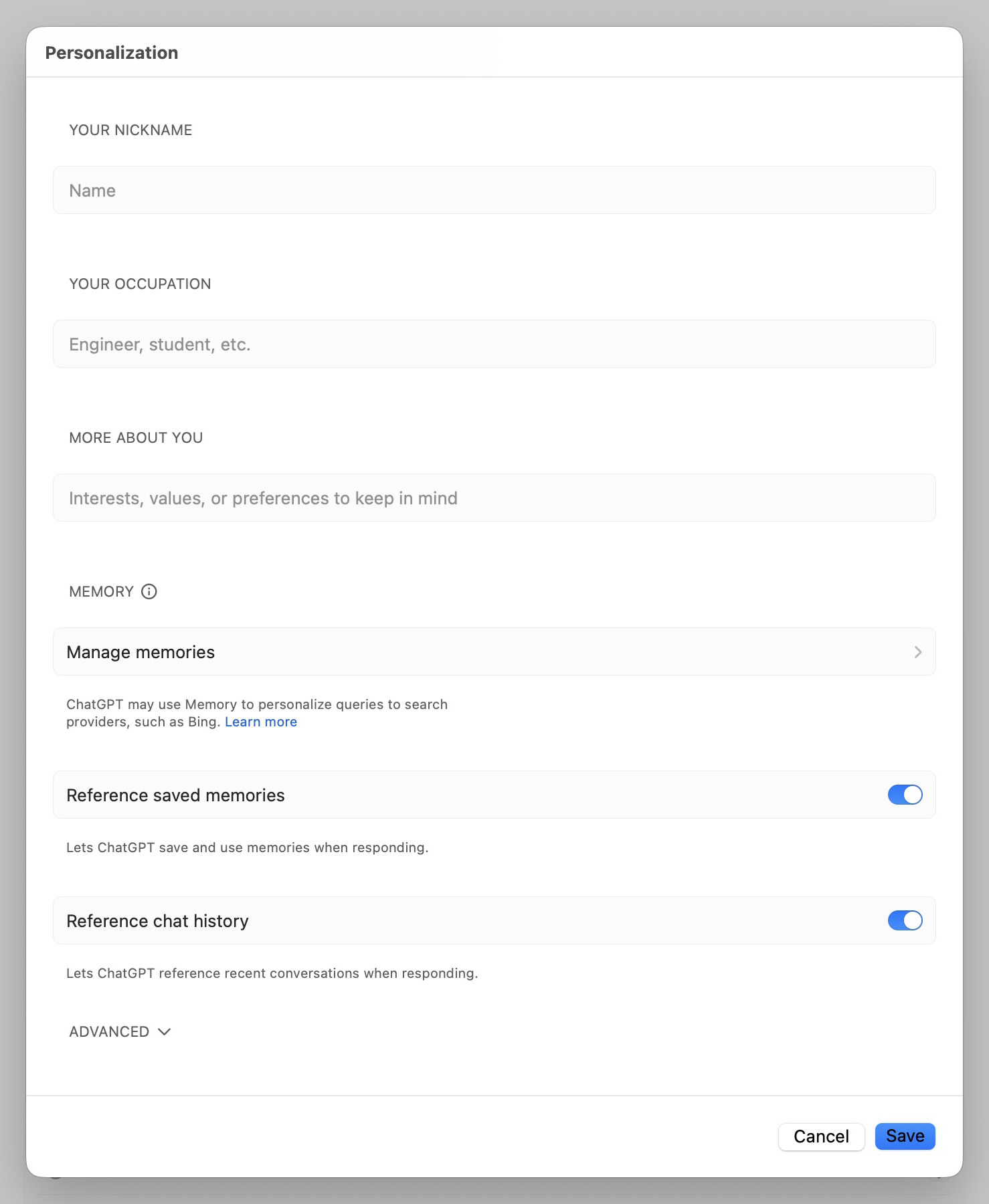
Under Personalization, you can manage saved memories, temporarily disable memory, or prevent the model from referring to chat history when responding
This section displays all stored information. If you wish for ChatGPT to forget a specific detail, click the trash can icon next to that memory. Important: for a memory to be completely erased, you need to also delete the specific chat the information was saved from. If you delete only the chat but not the memory, the data remains stored.
In Personalization, you can also configure what data ChatGPT will store about you in future conversations. To do this, you should familiarize yourself with the two types of memory available in the AI:
- Saved memories are fixed recollections about you, such as your name, interests, or communication style, which remain in the system until you manually delete them. These are created when you explicitly ask the chat to remember something
- Chat history is the model’s ability to consider specific details from past conversations to produce more personalized responses. In this case, ChatGPT doesn’t store every detail; instead, it selects only fragments that it deems useful. These types of memories can change and adapt over time
You can disable one or both of these memory types in the ChatGPT settings. To deactivate saved memories, turn off the toggle next to Reference saved memories. To do the same for chat history, turn off the toggle next to Reference chat history.
Disabling these features doesn’t delete previously saved information. The data remains within the system, but the model ceases to reference it in new responses. To completely delete saved memories, go to the Manage memories section as described above.
The Personalization menu in the web-based version of ChatGPT is slightly different, with an additional option: Record mode. This allows the AI to reference transcripts of your past recordings when generating responses. It is possible to disable this feature within the web interface.
In addition, the web version displays a memory usage indicator, such as 87% full, which shows how much space is occupied by memories.
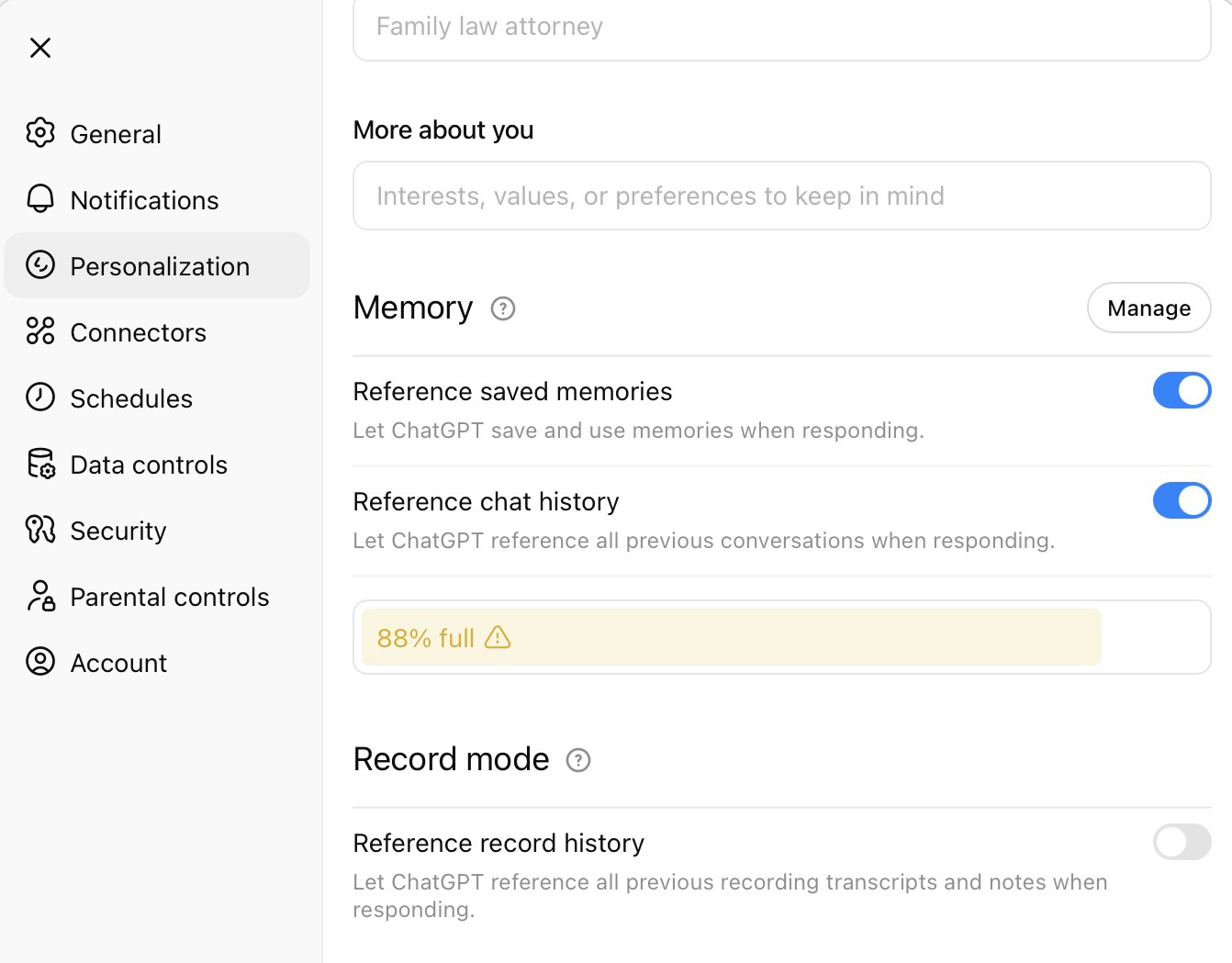
The web version of ChatGPT also includes a memory usage indicator under Personalization
For sensitive conversations, you can utilize special Temporary Chats, which the AI won’t remember.
How to use Temporary Chats in ChatGPT
Temporary Chats in ChatGPT are designed to resemble incognito mode in a web browser. If you want to discuss something particularly intimate or confidential with the AI, this mode helps reduce the risks. The chats are not saved in the history, they don’t become part of the memory, and they’re not used to train the models. This last point holds true for all Temporary Chats regardless of the settings selected in the Data controls section, which was discussed above.
Once a session ends, its contents disappear and cannot be recovered. This means Temporary Chats won’t appear in your history, and ChatGPT won’t remember their content. However, OpenAI warns that for security purposes, a copy of the Temporary Chat may be stored on the company’s servers for up to 30 days.
In June 2025, a court ordered OpenAI to preserve all user chats with ChatGPT indefinitely. The decision has already taken effect, and even though the company plans to appeal it, at the time of this publication, OpenAI is compelled to store Temporary Chat data permanently in a special secure repository that “can only be accessed under strict legal protocols”. This largely nullifies the entire concept of “Temporary Chats”, and confirms the old adage, “There’s nothing more permanent than the temporary”.
It’s important to note that when creating a Temporary Chat, you’re starting a conversation with the AI from a blank slate: the chatbot won’t remember any information from its previous chats with you.
To initiate a Temporary Chat in the web-based version of ChatGPT, open a new chat and click Turn on temporary chat button in the upper right corner of the page.
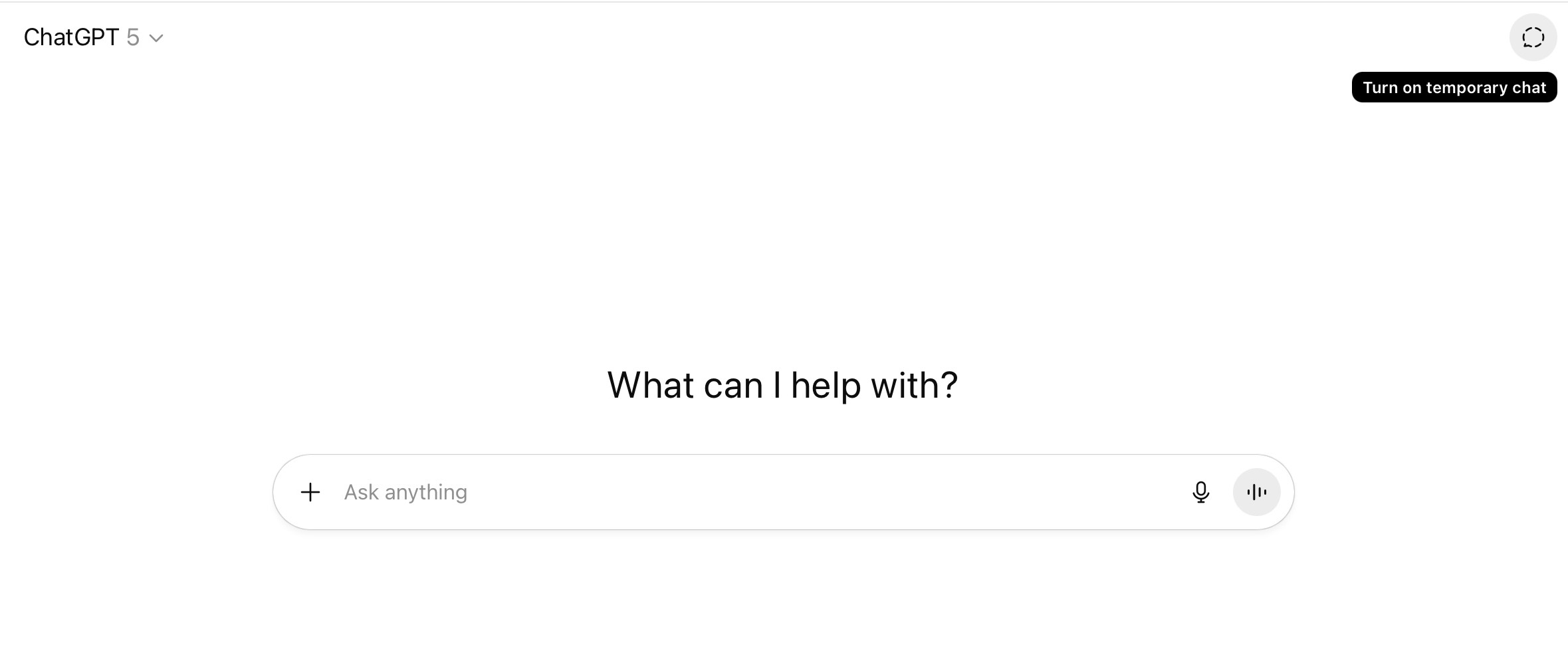
In the web version of ChatGPT, the Turn on temporary chat button is located in the upper right corner of the screen, and launches a new chat that won’t save any history or memory
To activate a Temporary Chat in the ChatGPT applications for macOS and Windows, click the AI model selection, and a Temporary Chat toggle will appear at the bottom of the window that opens.
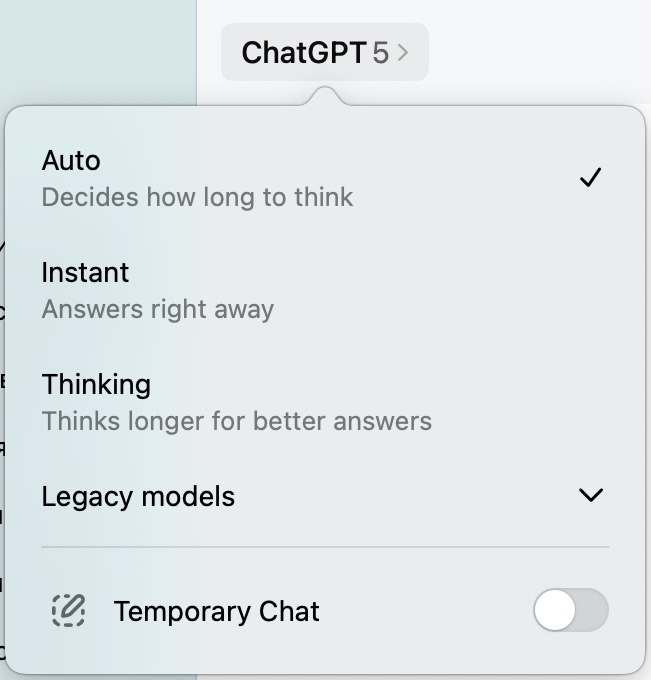
In the ChatGPT app for macOS, Temporary Chat activation is available in the model selection menu
After a Temporary Chat is activated, a special screen will open, which will look slightly different in the desktop and web versions. If you see this screen, it means things are working correctly.
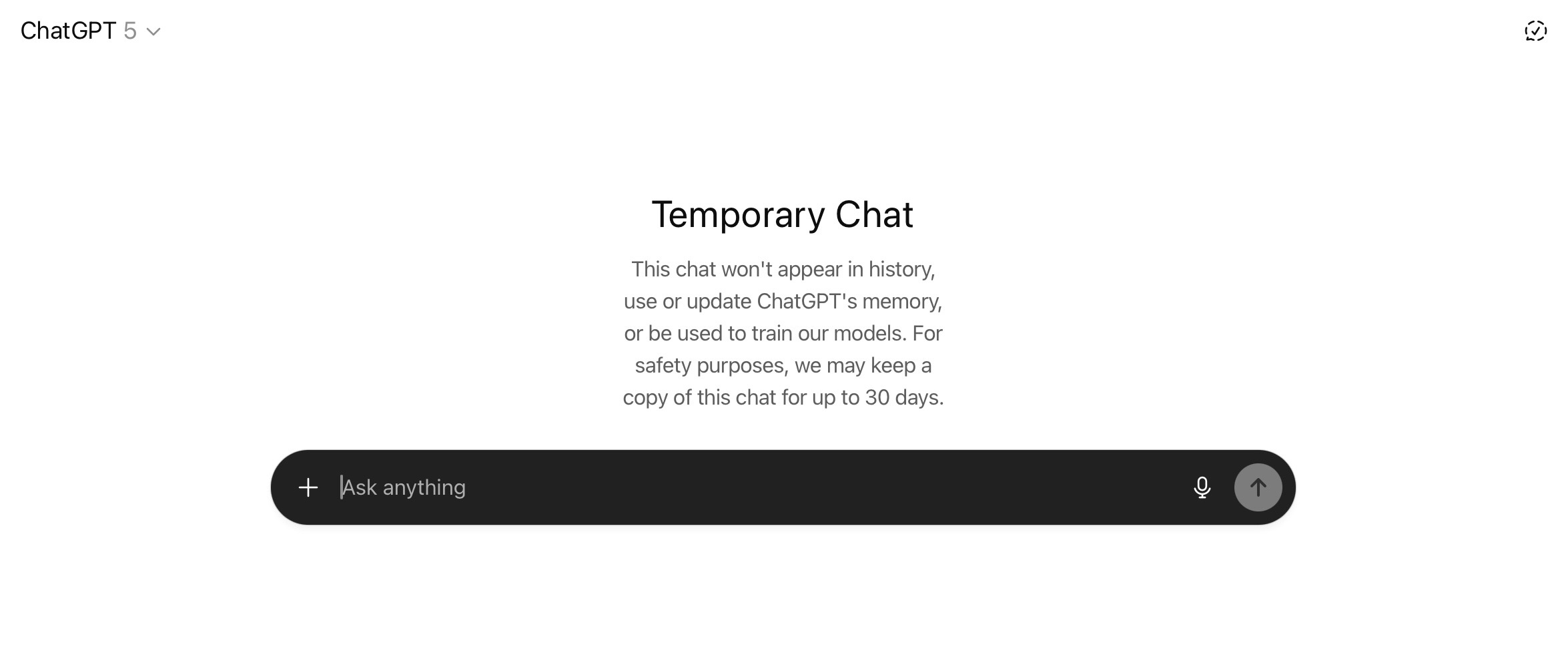
Temporary Chats are not saved in history, used to update memory, or utilized for model training
Integrating ChatGPT with your device applications
The ChatGPT application includes a feature named Work with Apps. This allows you to interact with the AI beyond the ChatGPT interface itself, extending its functionality into other apps on your device. Specifically, the model can connect to text editors and various development environments.
When you utilize this feature, you can receive AI suggestions and make edits directly within those apps, eliminating the need to copy text to a separate chat window. The core concept is to embed the AI into your existing, familiar workflows.
However, along with the convenience, this feature introduces privacy risks. By connecting to applications, ChatGPT gains access to the content of the files you’re working on. These files may include personal documents, work projects or reports, notes containing confidential information, and other similar content. A portion of this data may be sent to OpenAI’s servers for analysis and response generation.
Therefore, the more applications you grant access to, the higher the probability that sensitive information will be exposed to OpenAI.
At the time of this post, the ChatGPT application for macOS can connect to the following applications:
- Text-editing and note-taking apps: Apple Notes, Notion, TextEdit, Quip
- Development environments: Xcode, Script Editor, VS Code (Code, Code Insiders, VSCodium, Cursor, Windsurf)
- JetBrains IDEs: Android Studio, IntelliJ IDEA, PyCharm, WebStorm, PHPStorm, CLion, Rider, RubyMine, AppCode, GoLand, DataGrip
- Command-line interfaces: Terminal, iTerm, Warp, Prompt
No comparable list has been published for the Windows version of the app yet.
To check if this feature is currently enabled on your device, click your account name in the lower-left corner of the screen. Select Settings and scroll down to Work with Apps. If the toggle switch next to Enable Work with Apps is on, the feature is turned on.
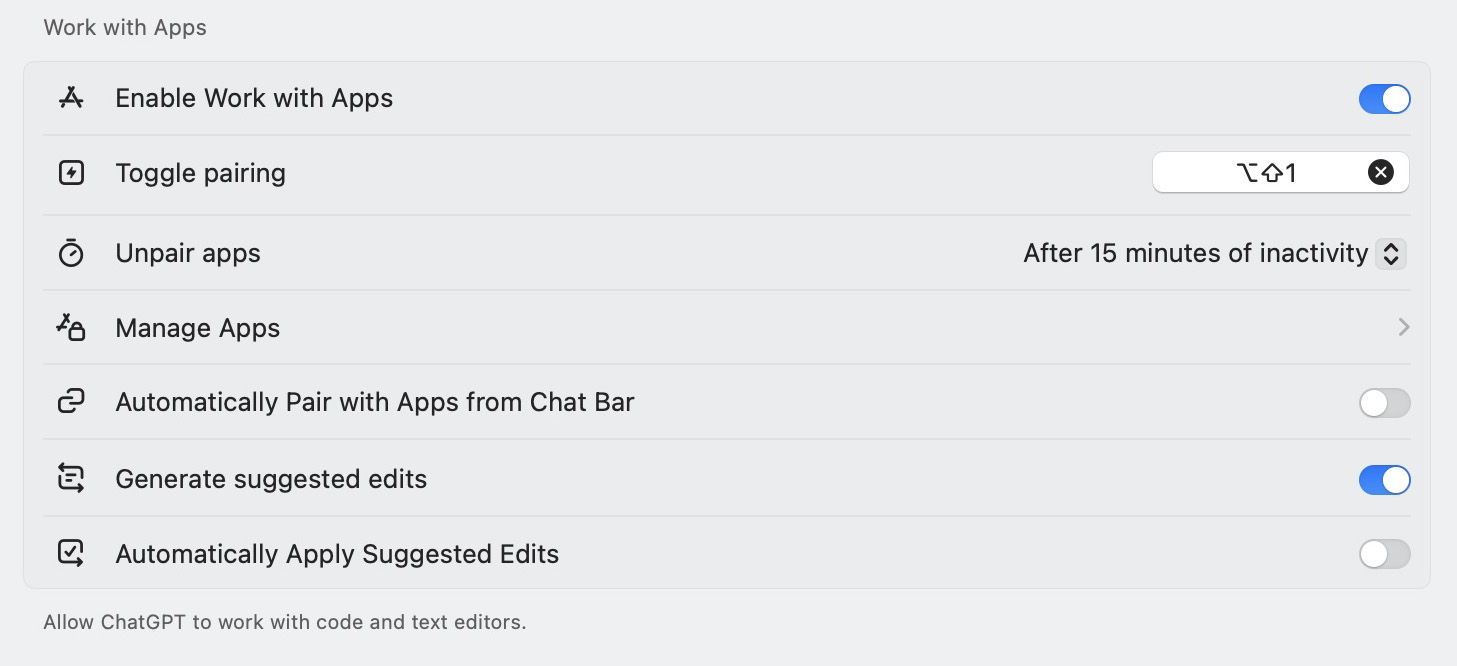
In Work with Apps, you can check if the feature is enabled, and manage connections to installed apps
It’s important to emphasize that enabling the feature doesn’t immediately give the ChatGPT app access to the applications on your device. For ChatGPT to analyze and make changes to content in other apps, the user must explicitly grant a separate permission to each individual app.
If you’re unsure whether you’ve granted ChatGPT any access permissions, you can verify this within the same section. To do this, select Manage Apps. The window that opens will display every app on your device that ChatGPT can potentially interact with. If each app shows Requires permissions underneath it, and Enable Permission on the right, it signifies that ChatGPT currently has no access to any apps.
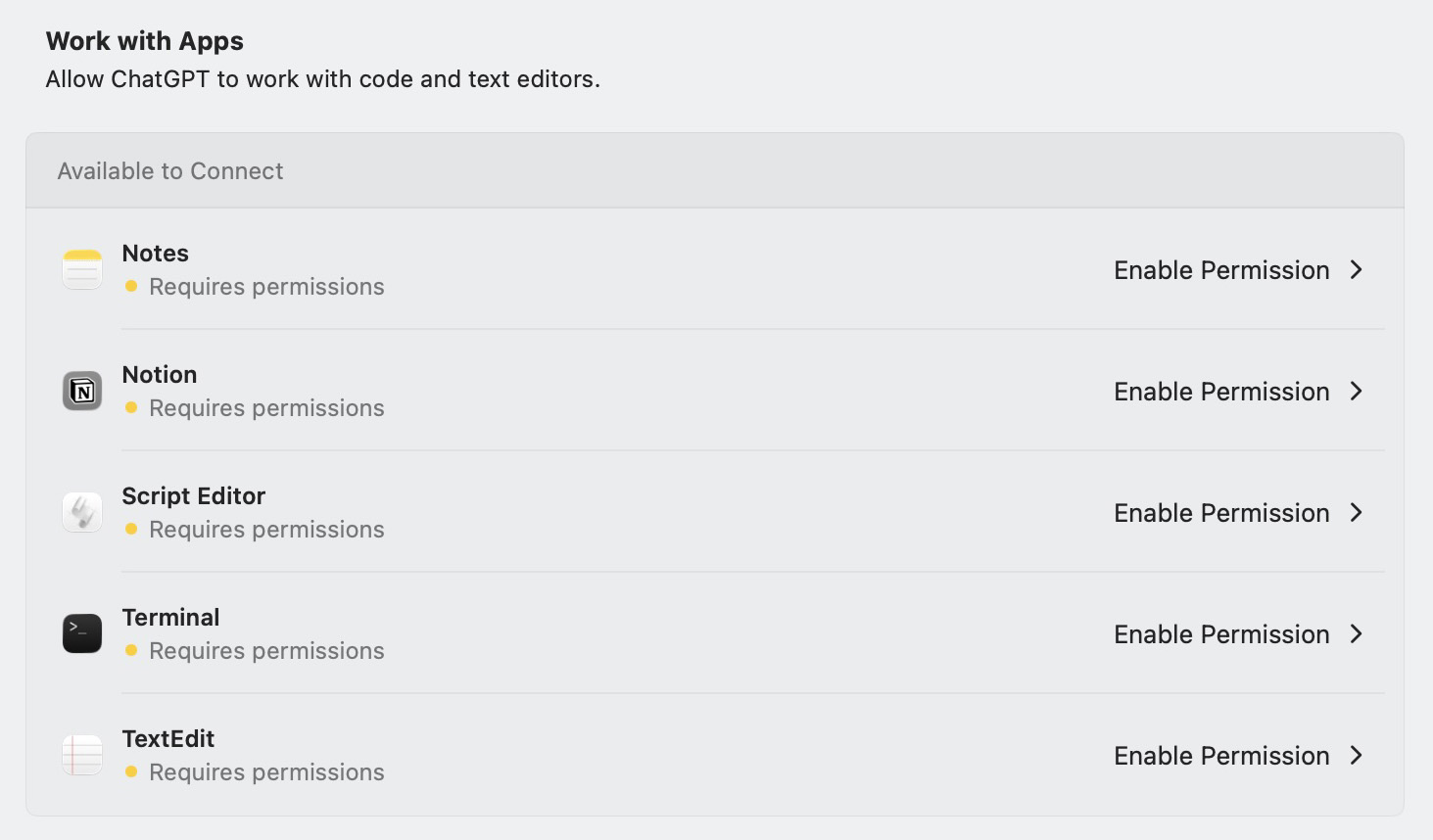
Manage Apps displays the apps ChatGPT can potentially access
On macOS, should you choose to grant ChatGPT access to an application, you must also enable the AI app to control your computer via the accessibility features in the system settings. This permission grants ChatGPT extensive extra capabilities: monitoring your activities, managing other applications, simulating keystrokes, and interacting with the user interface. For this very reason, these permissions are granted only manually and require the user’s explicit confirmation.
If you’re concerned about the uncontrolled sharing of your data with ChatGPT, we recommend you disable the Enable Work with Apps toggle switch and forgo using this feature.
However, if you want ChatGPT to be able to work with applications on your device, you should pay attention to the following three features, and configure them according to your personal balance of privacy and convenience:
- Automatically pair with apps from chat bar allows ChatGPT to automatically connect to supported applications directly from the chat UI without requiring manual selection each time. This speeds up your workflow, but increases the risk that the model will gain access to an application that the user didn’t intend to connect it to
- Generate suggested edits allows ChatGPT to propose changes to text or code within the connected application, but you’ll need to apply those changes manually. This is the safer option because the user retains control over changes being made
- Automatically apply suggested edits allows the model to immediately implement changes to files. While this maximizes process automation, it carries additional risks, as modifications could be applied without confirmation — potentially affecting important documents or work projects
How to connect ChatGPT to third-party online services
ChatGPT can also be connected to third-party online services for greater customization: this allows the AI to offer more precise answers and execute tasks better by considering, for example, your email correspondence in Gmail or schedule in Google Calendar.
Unlike Work with Apps, which enables ChatGPT to interact with locally installed applications, this feature involves external online platforms like GitHub, Gmail, Google Calendar, Teams, and many others.
The exact list of available services depends on your plan. The most extensive selection is available in the Business, Enterprise, and Edu tiers; a slightly more limited set is found in Pro; and the roster of services is significantly more modest in Plus. Free users have no access to this feature. Some regional restrictions also apply. You can view the full list for all plans by following the link.
When connecting to third-party services, it’s crucial to understand exactly what data OpenAI will process, how, and for what purposes. If you haven’t disabled training on your data, information received from connected services may also be used for model training. Furthermore, with the memory option enabled, ChatGPT is capable of remembering details obtained from third-party services and utilizing them in future chats.
To view the list of online services available for connection, click your account name in the bottom left corner of the screen. Then, select Settings and, in the Account section, navigate to Connectors.
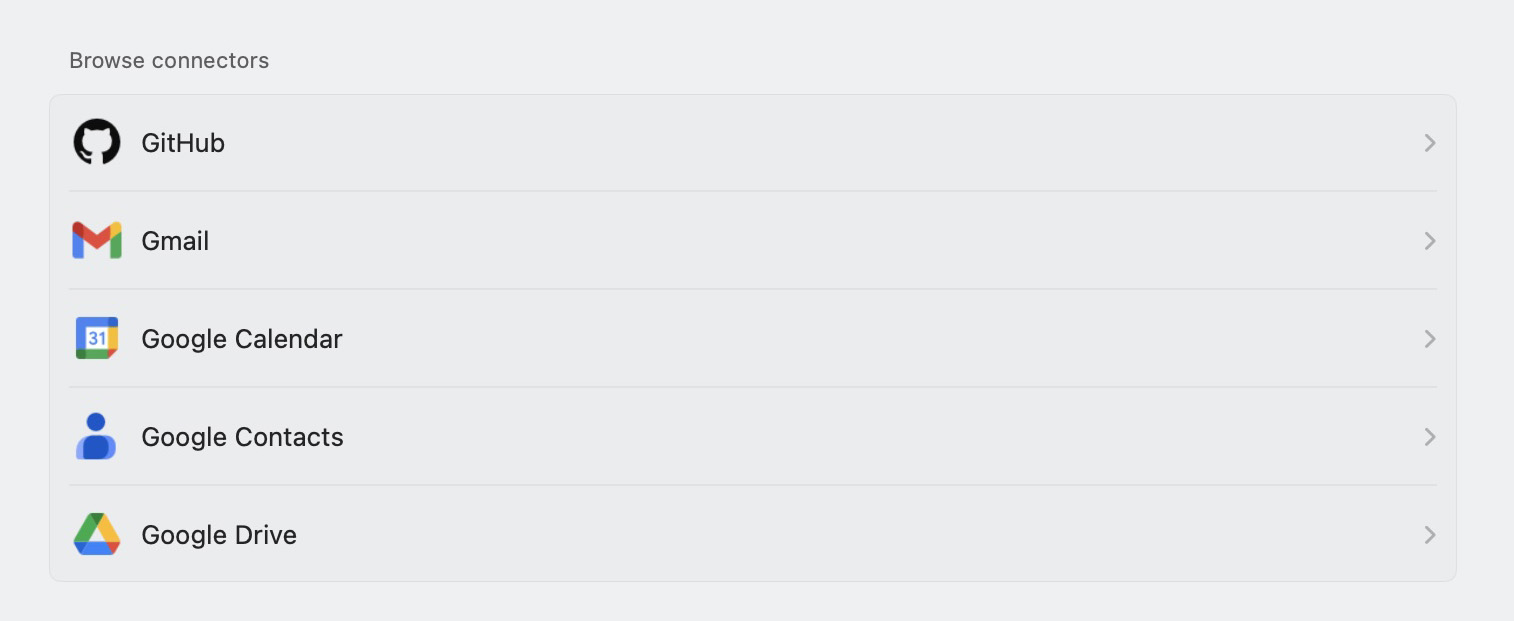
Connectors available in the ChatGPT settings
Under Connectors, you’ll see services that are already connected, as well as those that are available for activation. To disconnect ChatGPT from a service, select the service and click Disconnect.
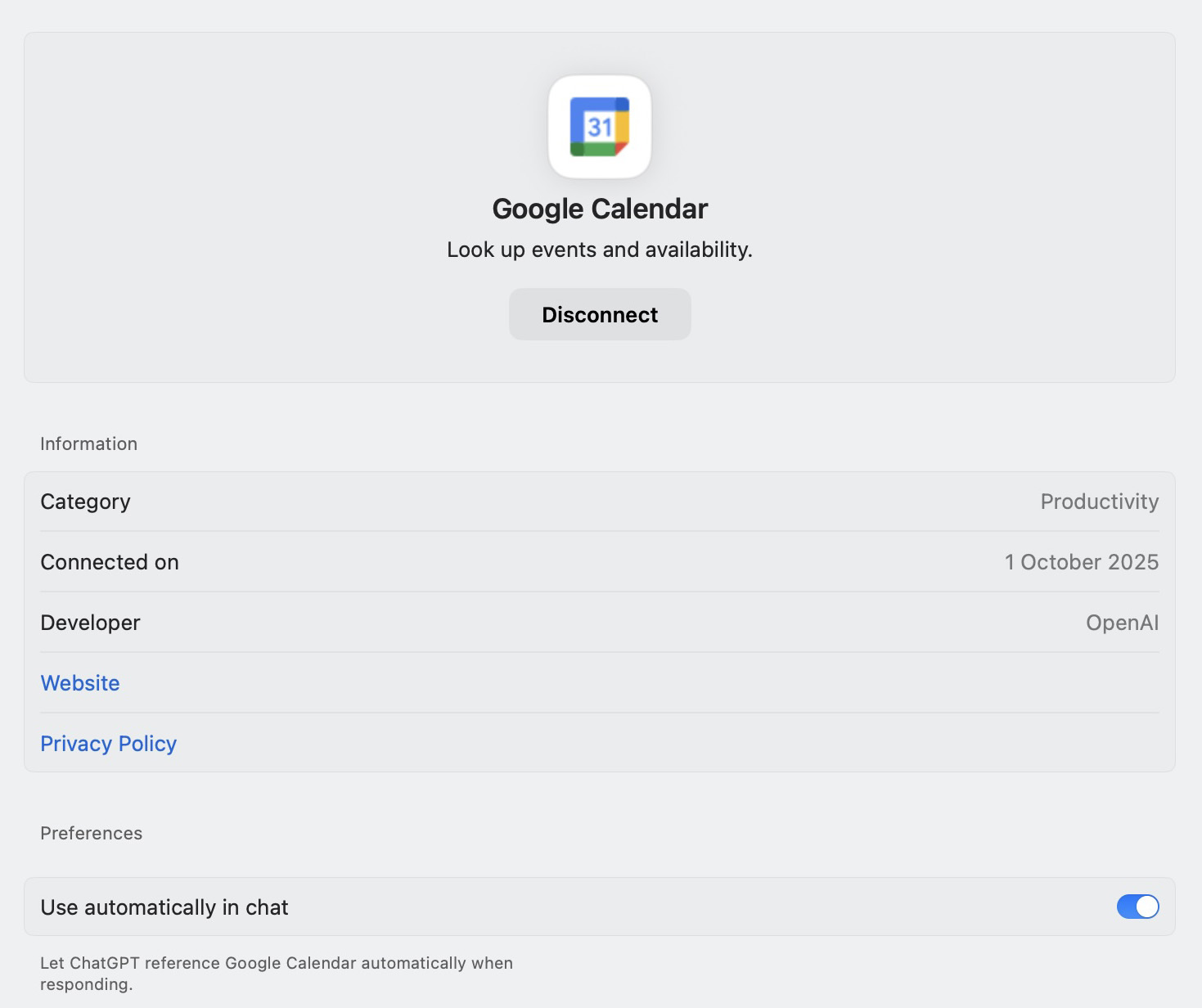
The settings for each connector allow you to disable ChatGPT’s access to the service, view the date when it was connected, and allow or disallow the automatic use of its data in chats
To mitigate privacy risks, we recommend connecting only the absolutely necessary services, and configuring the memory and data controls within ChatGPT in advance.
How to set up secure login to ChatGPT
If you are a frequent ChatGPT user, the service likely stores significantly more information about you than even social media. Therefore, if your account is compromised, attackers could gain access to data they can use for doxing, blackmail, fraud, theft of funds, and other types of attacks.
To mitigate these risks, it’s essential to set a complex password, and enable two-factor authentication for logging in to ChatGPT. What we have in mind when we say “complex” is a password that meets all of the following criteria:
- A minimum length of 16 characters
- A combination of uppercase and lowercase letters, numbers, and special characters
- Ideally, no dictionary words, no simple sequences like “12345” or “qwerty”, and no repeating characters
- Uniqueness: a different password for each website or online service
If your current ChatGPT password doesn’t satisfy these criteria, we strongly recommend you change it. While there’s no option to change the password as such in the ChatGPT settings, you can use the password reset procedure. To do this, log out of your account, select Forgot password? on the login screen, and follow the instructions to set up a new password.
You may be tempted to use the AI model itself to generate a password. However, we don’t recommend this: our research suggests that chatbots are often not very effective at this task, and frequently generate highly insecure passwords. Furthermore, even if you explicitly ask the neural network to create a random password, it won’t be truly random, and will therefore be more vulnerable.
For additional account protection, we also recommend enabling two-factor authentication: navigate to Settings, select Security, and turn on the Multi-factor authentication toggle switch. After this, scan the QR code in an authenticator application, or manually enter the secret key that appears on the screen, and verify the action with the one-time code.
In the Security section of the web version, you can also log out of all active sessions on all devices, including your current one. Unfortunately, you cannot view the login history. We recommend using this feature if you suspect that someone may have gained unauthorized access to your account.
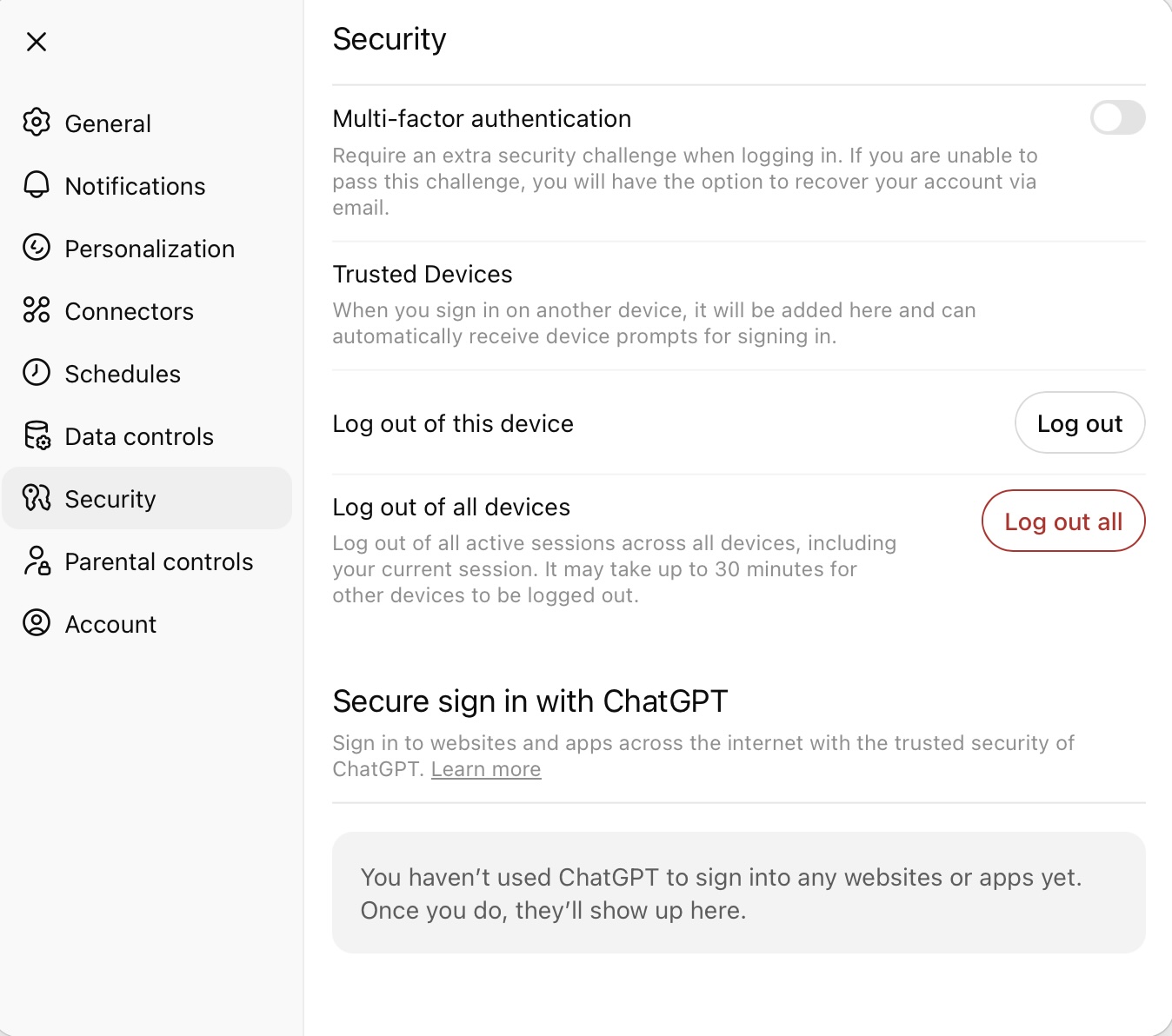
In the web version’s security settings, you can enable multi-factor authentication, and also log out of ChatGPT on all devices
Final tips to secure your data
When using AI chatbots, it’s important to remember that these applications create new privacy challenges. To protect our data, we now must account for things that were not a concern when setting up accounts in traditional apps and web services, or even in social media and messaging apps. We hope that this comprehensive guide to privacy and security settings in ChatGPT will help you with this tricky task.
Also, please remember to safeguard your ChatGPT account against hijacking. The best way to do this is by using an app that generates and securely stores strong passwords, while also managing two-factor authentication codes.
Kaspersky Password Manager helps you create unique, complex passwords, autofill them when logging in, and generate one-time codes for two-factor authentication. Passwords, one-time codes, and other data encrypted in Kaspersky Password Manager can be synchronized across all your devices. This will help provide robust protection for your account in ChatGPT and other online services.
If you’re looking for more information on the secure use of artificial intelligence, here are some more useful posts:
Kaspersky official blog –