Half of the world’s satellite traffic is unencrypted | Kaspersky official blog
The year is 2024. A team of scientists from both the University of California San Diego and the University of Maryland, College Park, discovers an unimaginable danger looming over the world — its source hiding in space. They start sounding the alarm, but most people simply ignore them…
No, this isn’t the plot of the Netflix hit movie Don’t Look Up. This is the sudden reality in which we find ourselves following the publication of a study confirming that corporate VoIP conversations, military operation data, Mexican police records, private text messages and calls from mobile subscribers in both the U.S. and Mexico, and dozens of other types of confidential data are being broadcast unencrypted via satellites for thousands of miles. And to intercept it, all you need is equipment costing less than US$800: a simple satellite-TV receiver kit.
Today, we explore what might have caused this negligence, if it’s truly as easy to extract the data from the stream as described in a Wired article, why some data operators ignored the study and took no action, and, finally, what we can do to ensure our own data doesn’t end up on these vulnerable channels.
What happened?
Six researchers set up a standard geostationary satellite-TV antenna — the kind you can buy from any satellite provider or electronics store — on the university roof in the coastal La Jolla area of San Diego, Southern California. The researchers’ no-frills rig set them back a total of US$750: $185 for the satellite dish and receiver, $140 for the mounting hardware, $195 for the motorized actuator to rotate the antenna, and $230 for a TBS5927 USB-enabled TV tuner. It’s worth noting that in many other parts of the world, this entire kit likely would have cost them much less.
What distinguished this kit from the typical satellite-TV antenna likely installed outside your own window or on your roof was the motorized dish actuator. This mechanism allowed them to reposition the antenna to receive signals from various satellites within their line of sight. Geostationary satellites, used for television and communications, orbit above the equator and move at the same angular velocity as the Earth. This ensures they remain stationary relative to the Earth’s surface. Normally, once you point your antenna at your chosen communication satellite, you don’t need to move it again. However, the motorized drive allowed the researchers to quickly redirect the antenna from one satellite to another.
Every geostationary satellite is equipped with numerous data transponders used by a variety of telecom operators. From their vantage point, the scientists managed to capture signals from 411 transponders across 39 geostationary satellites, successfully obtaining IP traffic from 14.3% of all Ku-band transponders worldwide.
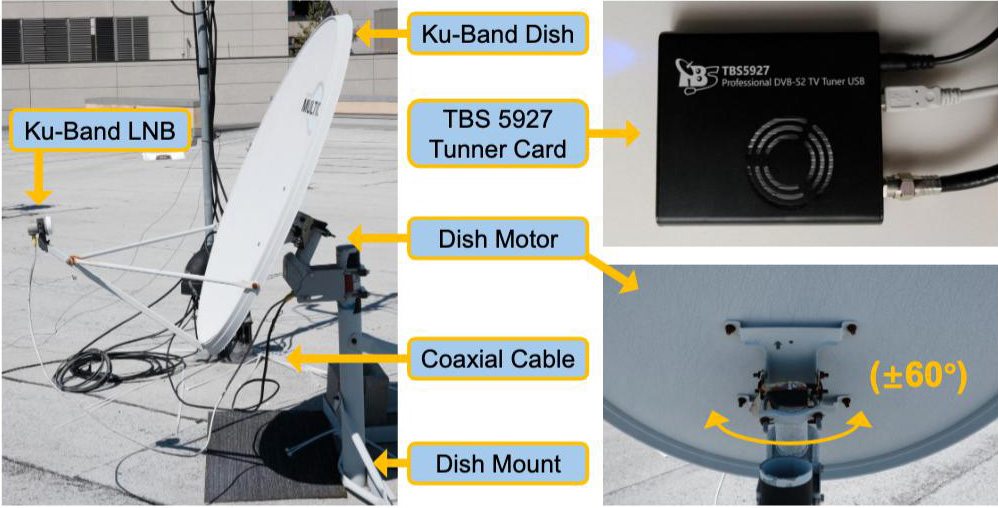
The researchers were able to use their simple US$750 rig to examine traffic from nearly 15% of all active satellite transponders worldwide. Source
The team first developed a proprietary method for precise antenna self-alignment, which significantly improved signal quality. Between August 16 and August 23, 2024, they performed an initial scan of all 39 visible satellites. They recorded signals lasting three to ten minutes from every accessible transponder. After compiling this initial data set, the scientists continued with periodic selective satellite scans and lengthy, targeted recordings from specific satellites for deeper analysis — ultimately collecting a total of more than 3.7TB of raw data.
The researchers wrote code to parse data transfer protocols and reconstruct network packets from the raw captures of satellite transmissions. Month after month, they meticulously analyzed the intercepted traffic, growing increasingly concerned with each passing day. They found that half (!) of the confidential traffic broadcast from these satellites was completely unencrypted. Considering that there are thousands of transponders in geostationary orbit, and the signal from each one can, under favorable conditions, be received across an area covering up to 40% of the Earth’s surface, this story is genuinely alarming.

Pictured at the University of San Diego roof setup, from left to right: Annie Dai, Aaron Schulman, Keegan Ryan, Nadia Heninger, and Morty Zhang. Not pictured: Dave Levin. Source
What data was broadcast with open access?
The geostationary satellites were found to be broadcasting an immense and varied amount of highly sensitive data completely unencrypted. The intercepted traffic included:
- Calls, SMS messages, and internet traffic from end-users; equipment identifiers and cellular encryption keys belonging to various operators, including T-Mobile and AT&T Mexico
- Internet data for users of in-flight Wi-Fi systems installed on commercial passenger aircraft
- Voice traffic from several major VoIP providers, including KPU Telecommunications, Telmex, and WiBo
- Government, law enforcement and military traffic: data originating from U.S. military ships; real-time geolocation and telemetry data from Mexican Armed Forces air, sea and ground assets; and information from Mexican law enforcement agencies — including data on drug trafficking operations and public assemblies
- Corporate data: internal traffic from major financial organizations and banks like Grupo Santander Mexico, Banjército, and Banorte
- Internal traffic from Walmart-Mexico, including details on warehouse inventory and price updates
- Messages from key U.S. and Mexican infrastructure facilities like oil and gas rigs and electricity providers
While most of this data seems to have been left unencrypted due to sheer negligence or a desire to cut costs (which we’ll discuss later), the presence of cellular data in the satellite network has a slightly more intriguing origin. This issue stems from what is known as backhaul traffic — used to connect remote cell towers. Many towers located in hard-to-reach areas communicate with the main cellular network via satellites: the tower beams a signal up to the satellite, and the satellite relays it back to the tower. Crucially, the unencrypted traffic the researchers intercepted was the data being transmitted from the satellite back down to the remote cell tower. This provided them access to things like SMS messages and portions of voice traffic flowing through that link.
Data operators’ response to the researchers’ messages
It’s time for our second reference to the modern classic by Adam McKay. The movie Don’t Look Up is a satirical commentary on our reality — where even an impending comet collision and total annihilation cannot convince people to take the situation seriously. Unfortunately, the reaction of critical infrastructure operators to the scientists’ warnings proved to be strikingly similar to the movie plot.
Starting in December 2024, the researchers began notifying the companies whose unencrypted traffic they’d successfully intercepted and identified. To gauge the effectiveness of these warnings, the team conducted a follow-up scan of the satellites in February 2025 and compared the results. They found that far from all operators took any action to fix the issues. Therefore, after waiting nearly a year, the scientists decided to publicly release their study in October 2025 — detailing both the interception procedure and the operators’ disappointing response.
The researchers stated that they were only publishing information about the affected systems after the problem had been fixed or after the standard 90-day waiting period for disclosure had expired. For some systems, an information disclosure embargo was still in effect at the time of the study’s publication, so the scientists plan to update their materials as clearance allows.
Among those who failed to address the notifications were: the operators of unnamed critical infrastructure facilities, the U.S. Armed Forces, Mexican military and law enforcement agencies, as well as Banorte, Telmex, and Banjército.
When questioned by Wired about the incident, in-flight Wi-Fi providers responded vaguely. A spokesperson for Panasonic Avionics Corporation said the company welcomed the findings by the researchers, but claimed they’d found that several statements attributed to them were either inaccurate or misrepresented the company’s position. The spokesperson didn’t specify what exactly it was that the company considered inaccurate. “Our satellite communications systems are designed so that every user-data session follows established security protocols,” the spokesperson said. Meanwhile, a spokesperson for SES (the parent company of Intelsat) completely shifted responsibility onto the users, saying, “Generally, our users choose the encryption that they apply to their communications to suit their specific application or need,” effectively equating using in-flight Wi-Fi with connecting to a public hotspot in a café or hotel.
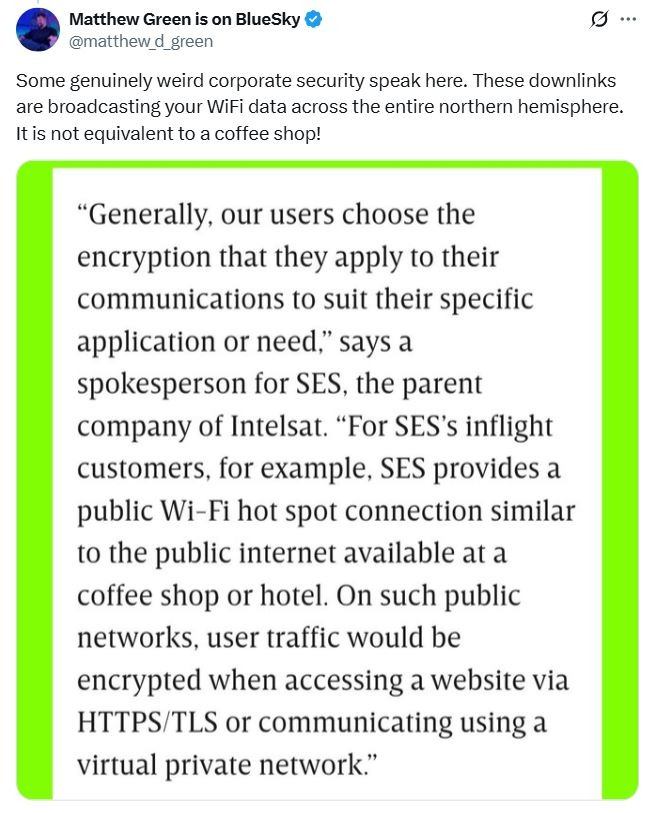
The SES spokesperson’s response to Wired, along with a comment by Matthew Green, an associate professor of computer science at Johns Hopkins University in Baltimore. Source
Fortunately, there were also many appropriate responses, primarily within the telecommunications sector. T-Mobile encrypted its traffic within just a few weeks of being notified by the researchers. AT&T Mexico also reacted immediately, fixing the vulnerability and stating it was caused by a misconfiguration of some towers by a satellite provider in Mexico. Walmart-Mexico, Grupo Santander Mexico, and KPU Telecommunications all approached the security issue diligently and conscientiously.
Why was the data unencrypted?
According to the researchers, data operators have a variety of reasons — ranging from technical to financial — for avoiding encryption.
- Utilizing encryption can lead to a 20–30% loss in transponder bandwidth capacity.
- Encryption requires increased power consumption, which is critical for remote terminals, such as those running on solar batteries.
- For certain types of traffic, such as VoIP for emergency services, the lack of encryption is a deliberate measure taken to increase fault tolerance and reliability in critical situations.
- Network providers claimed that enabling encryption made it impossible to troubleshoot certain existing network problems within their current infrastructure. The providers did not elaborate on the specifics of that claim.
- Enabling link-layer encryption may require additional licensing fees for using cryptography in terminals and hubs.
Why did some vendors and agencies fail to react?
It’s highly likely they simply did not know how to respond. It’s difficult to believe that such a massive vulnerability could remain unnoticed for decades, so it’s possible the problem was intentionally left unaddressed. The researchers note that no single, unified entity is responsible for overseeing data encryption on geostationary satellites. Each time they discovered confidential information in their intercepted data, they had to expend considerable effort to identify the responsible party, establish contact, and disclose the vulnerability.
Some experts are comparing the media impact of this research to the declassified Snowden archives, given that the interception techniques used could be deployed for worldwide traffic monitoring. We can also liken this case to the infamous Jeep hack, which completely upended cybersecurity standards in the automotive industry.
We cannot exclude the possibility that this entire issue stems from simple negligence and wishful thinking — a reliance on the assumption that no one would ever “look up”. Data operators may have treated satellite communication as a trusted, internal network link where encryption was simply not a mandatory standard.
What can we as users do?
For regular users, the recommendations are similar to those we give for using any unsecured public Wi-Fi access point. Unfortunately, while we can encrypt the internet traffic originating from our devices ourselves, the same cannot be done for cellular voice data and SMS messages.
- For any confidential online operations, enable a reliable VPN that includes a kill switch. This ensures that if the VPN connection drops, all your traffic is immediately blocked rather than being routed unencrypted. Use your VPN when making VoIP calls, and especially when using in-flight Wi-Fi or other public access points. If you lean toward the paranoid side, leave your VPN on at all times. An effective and fast solution for your needs could be Kaspersky VPN Secure Connection.
- Utilize 5G networks whenever possible, as they feature higher encryption standards. However, even these can be insecure, so avoid discussing sensitive information via text or standard cellular voice calls.
- Use messaging apps that provide end-to-end encryption for traffic on user devices, such as Signal, WhatsApp, or Threema.
- If you’re using a cellular service in remote locations, minimize SMS chats and voice calls, or use services from operators that integrate encryption at the subscriber equipment level.
What else you need to know about telecommunication security:
Kaspersky official blog – Read More









 Manual
Manual