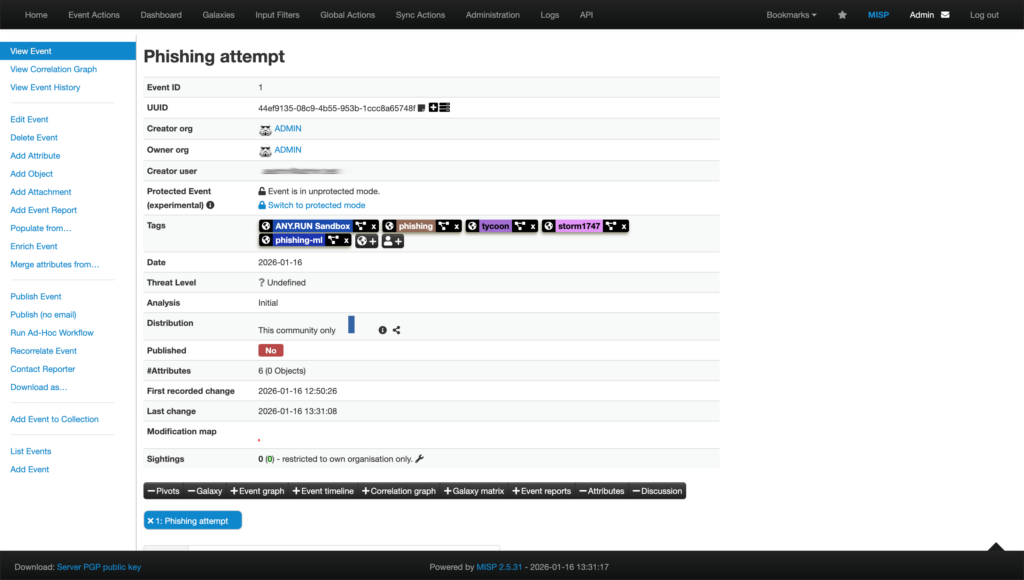
ANY.RUN Sandbox & MISP Integration: Confirm Alerts Faster, Stop Incidents Early
Most SOC teams are overloaded with routine work. Tier 1 & 2 analysts spend too much time validating alerts, moving samples between tools, and chasing missing context. When integrations are weak, investigations slow down, MTTR grows, and SLAs suffer delays. That directly increases operational risk and cost for the business.
ANY.RUN has already helped teams close part of this gap with continuous, high-quality Threat Intelligence Feeds. Now, with the ANY.RUN Sandbox integration for MISP, analysts can go further: enrich alerts with real execution behavior, speed up triage, and use actionable evidence to stop incidents before they have a chance to escalate.
ANY.RUN x MISP: Boost Your Triage & Response
With this integration, analysts can send suspicious files and URLs from MISP straight into the ANY.RUN Sandbox. The integration is deployed through native MISP modules. There is no need to export samples or switch tools. Everything happens inside the analyst’s usual workspace.
Integrate the modules using these links:
The analysis uses Automated Interactivity, which means the sandbox behaves like a real user. It clicks, opens files, and waits when needed. This matters because many modern threats stay quiet until they see user activity.
As a result, the sandbox reveals evasive malware that most detection systems miss, giving the SOC earlier and clearer signals.
After execution, the results are automatically returned to MISP, including the verdict, related IOCs, a link to the interactive analysis session, an HTML report, and mapped MITRE ATT&CK techniques and tactics.
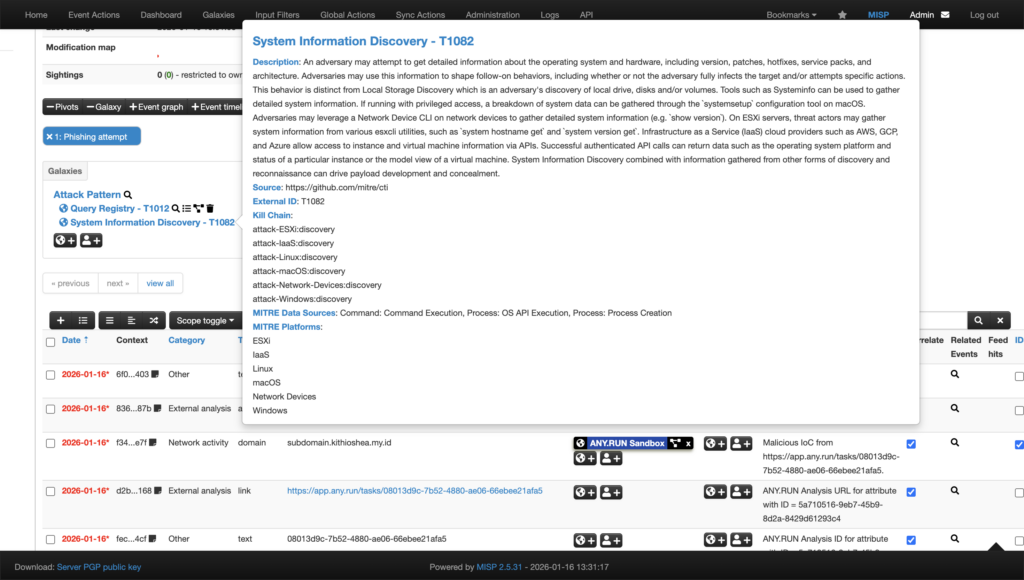
Here’s what your SOC can do with the integration:
- Catch evasive threats earlier by triggering delayed or user-driven malware behavior that bypasses traditional detection.
- Validate alerts using real execution evidence instead of relying on static indicators.
- Enrich investigations automatically with verdicts, IOCs, MITRE ATT&CK techniques, and detailed reports attached to MISP events.
- Work faster by running analysis and reviewing results without leaving MISP.
- Make confident escalation or closure decisions backed by real behavioral evidence.
Benefits for Your SOC and Business
For your organization, this integration means:
- Lower incident costs: Shorter investigations reduce operational effort per case.
- Reduced MTTR: Faster response limits business impact.
- Stronger SLA performance: Help MSSPs meet response time and quality commitments.
- No extra headcount: Scale SOC performance without growing the team.
- Zero integration costs: No need for custom development if MISP is already in use.
For MSSPs, the integration helps meet customer SLA requirements by reducing response times, increasing analysis quality, and improving the overall value of managed security services without increasing operational costs.
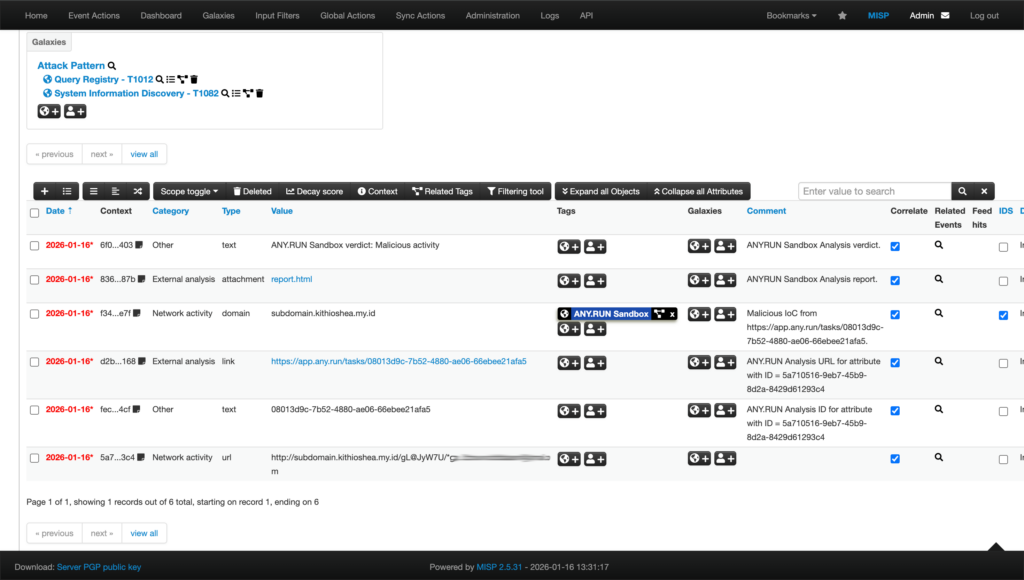
Expand Threat Coverage in MISP with ANY.RUN TI Feeds
Sandbox analysis helps with individual investigations, while ANY.RUN’s Threat Intelligence Feeds help the SOC stay ahead at scale.

ANY.RUN’s Threat Intelligence Feeds continuously deliver verified malicious network IOCs extracted from real attacks observed across more than 15,000 organizations. Indicators come directly from live sandbox executions and are delivered in STIX/TAXII format, ready for use in MISP, SIEM, or SOAR platforms.
Learn more about TI Feeds integration with MISP
- Early detection: New IOCs appear as soon as they are seen in real attacks.
- Expanded coverage: 99 percent unique indicators expose threats traditional feeds miss.
- Reduced false positives: Only confirmed malicious data reaches analysts.
- Better correlation: Shared attributes help link incidents and campaigns faster.
- Lower analyst workload: Continuous enrichment removes manual lookup and curation.
Conclusion
The ANY.RUN Sandbox integration turns MISP into a practical investigation tool, not just an IOC repository. Analysts get real behavior, faster verdicts, and better context without changing how they work. TI Feeds add continuous visibility into active attacker infrastructure. Together, these capabilities reduce MTTR, lower analyst workload, and help protect the business more effectively.
Discover all ANY.RUN integrations and simplify your analysis flow →
About ANY.RUN
ANY.RUN is a leading provider of interactive malware analysis and threat intelligence solutions trusted by more than 500,000 cybersecurity professionals and 15,000 organizations worldwide.
The platform gives defenders a clear view of real attacker behavior by combining:
- Interactive Sandbox: Runs files, URLs, and entire infection chains with automatic user-like activity to reveal tactics hidden from classic detection tools.
- Threat Intelligence Lookup: Verified reputation data, history, and related indicators gathered from real attacks.
- TI Feeds: Continuous delivery of fresh, confirmed-malicious network indicators in STIX/TAXII format.
- Enterprise-grade workflows: API, SDK, SSO, teamwork tools, and privacy-focused private analysis modes for large SOCs and MSSPs.
ANY.RUN helps analysts work faster, strengthen decisions, and investigate advanced threats with clarity and confidence.
FAQ
No. The integration sends files/URLs directly from the MISP event to ANY.RUN. Everything stays in the same workflow.
Some malware won’t run until it sees something that looks like a real human action, opening a document, clicking a dialog, waiting a few seconds, or browsing a link. Automated Interactivity performs those actions, helping expose behavior that static tools or non-interactive sandboxes never trigger.
Yes. Analysts can confirm or dismiss alerts faster because they work with real execution evidence, not just metadata. This speeds up triage, shortens response cycles, and lowers the number of cases that require escalation.
Yes. Faster verdicts, better evidence, and fewer manual steps mean MSSPs can return higher-quality reports to customers and stay within SLA targets without increasing team size.
The MISP modules are built into the platform and can be enabled without custom development. However, running analyses still requires an active ANY.RUN subscription. Once the account is connected, the integration can be used right away.
TI Feeds bring fresh, confirmed-malicious indicators into MISP through STIX/TAXII. They complement sandbox analysis by improving correlation and early detection.
The post ANY.RUN Sandbox & MISP Integration: Confirm Alerts Faster, Stop Incidents Early appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

