Major Cyber Attacks in November 2025: XWorm, JSGuLdr Loader, Phoenix Backdoor, Mobile Threats, and More
Stealers, loaders, and targeted campaigns dominated November’s activity. ANY.RUN analysts examined cases ranging from PNG-based in-memory loading used to deploy XWorm to JSGuLdr, a three-stage JavaScript-to-PowerShell loader pushing PhantomStealer.
Alongside these public cases, three Threat Intelligence Reports detailed new activity across Windows, Linux, and Android, including loader-enabled hijackers, Tor-based cryptotrojan communication, Linux ransomware in Go, MaaS stealers, and a WhatsApp-propagating campaign with geofencing controls.
Each case was analyzed inside ANY.RUN’s Interactive Sandbox, revealing execution flows, persistence mechanisms, and behavioral indicators that help teams tune detections and trace related activity.
Let’s break down how these attacks unfolded, where they hit, and what security teams can take away to strengthen their defenses before the next wave arrives.
1. XWorm: PNG Files Used as Containers for an In-Memory Loader
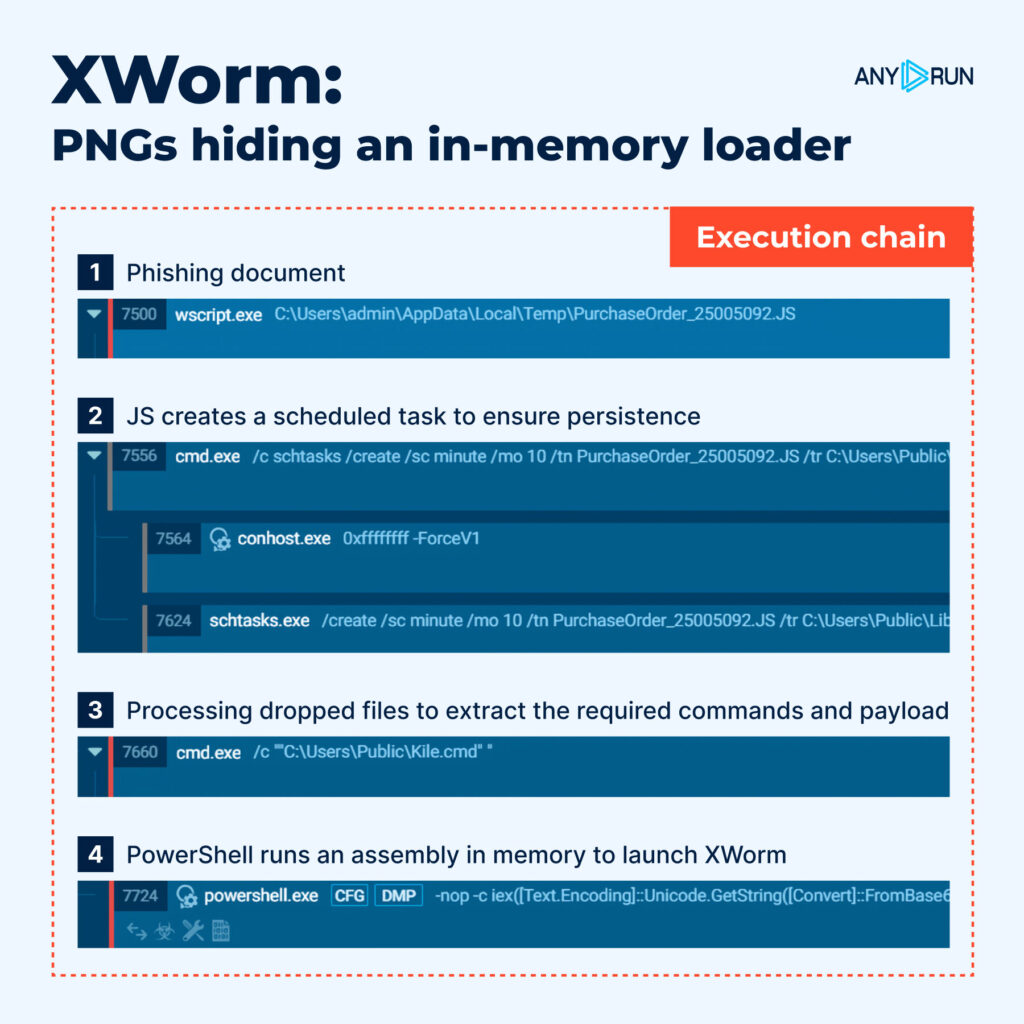
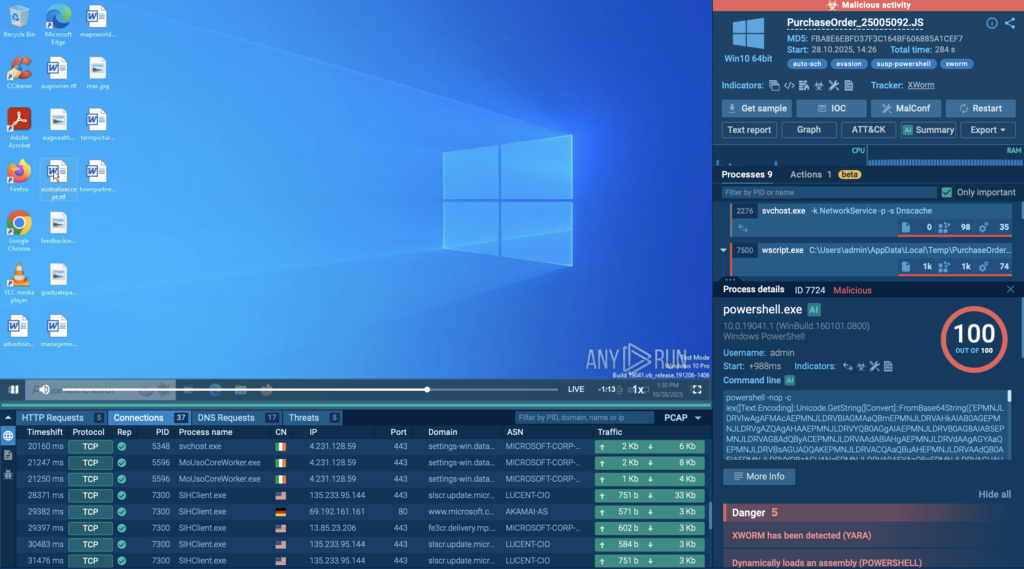
ANY.RUN analysts observed a new wave of XWorm infections in November, delivered through phishing pages and emails that distribute a JavaScript dropper named PurchaseOrder_25005092.js. While it appears benign at first glance, the script unpacks a full multi-stage chain designed to bypass quick checks, hide payloads inside PNG files, and execute a .NET assembly directly in memory.
How the attack begins
The campaign begins with a phishing lure (T1566.001) delivering a heavily obfuscated JavaScript installer (T1027). Once executed, the script checks whether the required components exist on the system and writes the missing files to C:UsersPUBLIC using Base64-encoded and AES-encrypted data (T1027.013). The staged components are later used during the PowerShell-driven decryption and in-memory execution stages.
The three staged files are:
- Kile.cmd: A heavily obfuscated batch script filled with variable noise, percent-encoding, and fragmented Base64
- Vile.png: Not an image but a Base64-encoded and AES-encrypted payload
- Mands.png: Another encrypted data blob used during the second stage
Attackers deliberately use the “.png” extension (T1036.008) to make the files look harmless and evade quick manual reviews.
In-memory execution chain
After writing the staged components to C:UsersPUBLIC, the JavaScript dropper reconstructs readable commands from its fragments and launches a PowerShell payload (T1059). This PowerShell script operates as a two-stage AES-CBC loader.
Stage 1: Command runner
Reads C:UsersPUBLICMands.png as Base64 → AES-decrypt → yields Base64-encoded commands. Each command is decoded and executed via Invoke-Expression, enabling the script to run attacker-controlled instructions without a traditional executable.
Stage 2: In-memory assembly load
Reads C:UsersPUBLICVile.png as Base64 → AES-decrypt → raw bytes. Loader attempts to execute the resulting .NET assembly directly from memory (T1620).
This creates an in-memory loader that launches XWorm without dropping a traditional executable. A successful compromise enables credential theft, remote control, and lateral movement across corporate environments.
See the full execution inside ANY.RUN
Enrich this case using Threat Intelligence Lookup
Below are ready-to-use TI Lookup queries for finding similar campaigns:
- PowerShell with .Replace() obfuscation: imagePath:”\powershell.exe$” AND commandLine:”.Replace(“
- PowerShell invoking IEX: imagePath:”\powershell.exe$” AND commandLine:”iex”
- JavaScript droppers writing to PublicLibraries: filePath:”^C:\Users\Public\Libraries\*.js$”
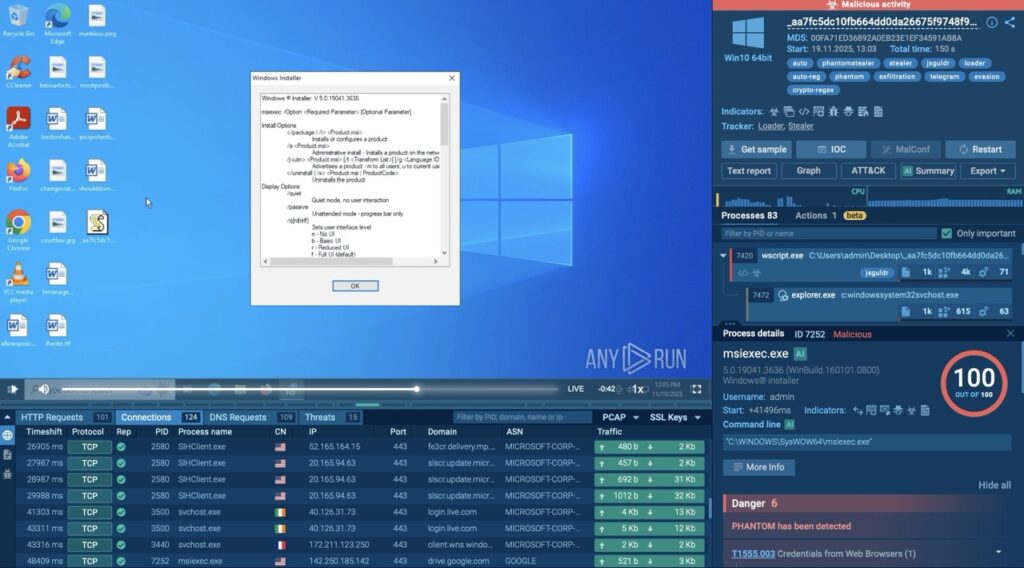
2. JSGuLdr: Multi-Stage Loader Delivering PhantomStealer
In November, ANY.RUN analysts identified JSGuLdr, a multi-stage loader that moves from JScript to PowerShell and ultimately deploys PhantomStealer. The chain relies on obfuscation, COM-based execution, cloud-hosted payloads, and in-memory loading, allowing the final payload to run with limited on-disk exposure.
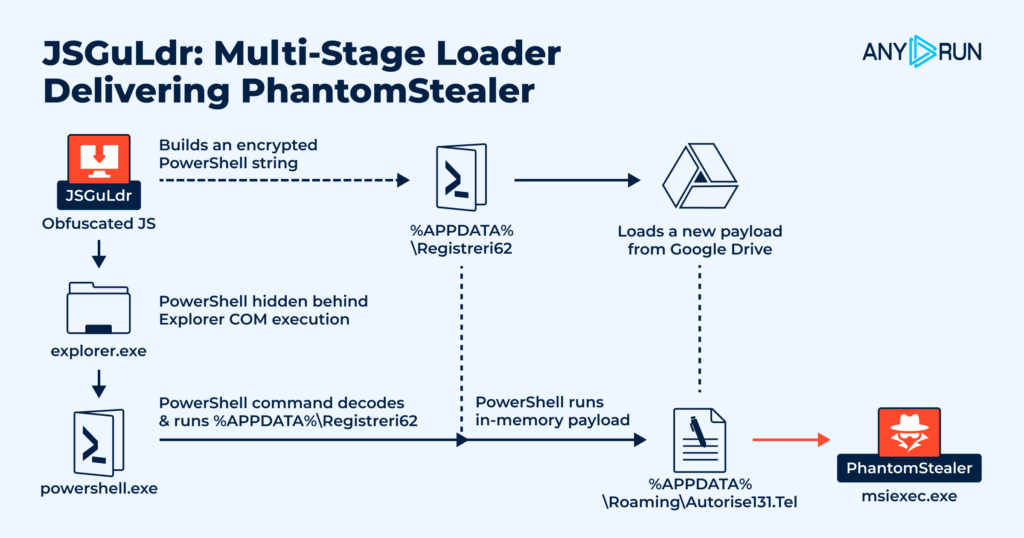
Stage 1: JScript Execution and COM-Based PowerShell Launch
The first stage is an obfuscated JScript file signed with a fake Authenticode certificate to appear trustworthy (T1027, T1553.006). It generates an encrypted PowerShell string and writes it to %APPDATA%Registreri62, forming the second-stage component.
Execution then shifts to Shell.Application and Explorer COM interaction, which launches powershell.exe under explorer.exe, masking the activity as normal user behavior (T1559.001, T1218).
Stage 2: PowerShell Loader, Cloud Retrieval, and In-Memory Execution
The PowerShell code decodes the contents of Registreri62, reconstructs hidden commands, and downloads an encrypted payload from Google Drive using a WebClient request (T1105). This payload is stored as %APPDATA%Autorise131.Tel, used as the on-disk container for the next stage (T1074.001).
Stage 3: In-Memory Loading and PhantomStealer Injection
PowerShell decrypts Autorise131.Tel, extracts raw bytes, and loads the resulting .NET assembly directly in memory (T1620). The final payload, PhantomStealer, is then injected into msiexec.exe, allowing it to run under a trusted Windows process and steal data without creating a conventional executable on disk (T1055, T1218.007).
Execution chain: wscript.exe → explorer.exe → explorer.exe (COM) → powershell.exe → msiexec.exe
Review the complete execution chain and behavioral indicators in the JSGuLdr analysis session.
Track similar activity with TI Lookup
Use the following TI Lookup query to identify related JSGuLdr activity, pivot from shared IOCs, and uncover additional loader variants across recent submissions.
commandLine:”windowssystem32″ and imagePath:”explorer.exe”
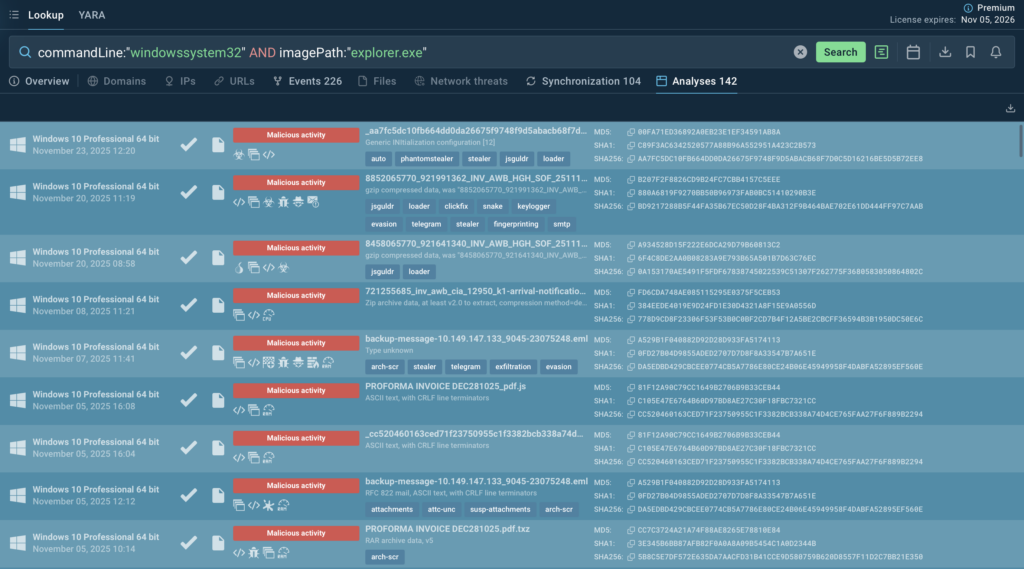
Gathered IOCs:
- URL: hxxps://drive[.]google[.]com/uc?export=download&id=1gUB_fKBej5Va_l3ZSEXk_7r5Q4EeJuwd
- Files: %APPDATA%Registreri62, %APPDATA%Autorise131[.]Tel
- CMD: powershell.exe “$Citize=$env:appdata+’Registreri62′;$Guazuma=gc $Citize;$Aristape=$Guazuma[4460..4462] -join ””
Threat Intelligence Report 1: PDFChampions, Efimer, and BTMOB
This Threat Brief provides a focused breakdown of three active threats, including how each sample behaves in the sandbox, its persistence and execution patterns, and the key detection points analysts can rely on. The report includes details about process activity, file system changes, network behavior, and extracted indicators, along with TI Lookup queries tailored to each malware family; PDFChampions’ mutex-based signature, Efimer’s Tor-based curl command, and BTMOB’s Android configuration file.
PDFChampions (Windows)
A browser hijacker distributed via malvertising that also acts as a loader. It changes the default search engine, terminates competing browsers, and can download and run additional payloads directly in memory.
Detection note: identify activity via the mutex “Champion.”
TI Lookup: syncObjectName:”Champion”
Efimer (Windows)
A cryptocurrency-focused trojan spread through phishing and compromised WordPress sites. It steals wallets and credentials and uses curl.exe to reach a Tor-hidden C2 endpoint (.onion/route.php).
Detection note: monitor curl connections to .onion/route.php.
TI Lookup: commandLine:”curl.exe*.onion/route.php”
BTMOB RAT (Android)
An Android RAT sold as MaaS. It abuses Accessibility Services for full device control, records screen and audio, and targets financial apps. Distributed through phishing APKs.
Detection note: presence of BTConfig.xml in the app’s shared preferences.
TI Lookup: filePath:”/data/data/*/shared_prefs/BTConfig.xml”
Threat Intelligence Report 2: Monkey, Phoenix, and NonEuclid
This month’s Threat Brief examines three threats in detail, with execution-flow screenshots, detection indicators, persistence artifacts, and public-sample telemetry. The report also provides ready-to-use TI Lookup queries and IOCs so teams can expand visibility and identify similar cases in their environments.
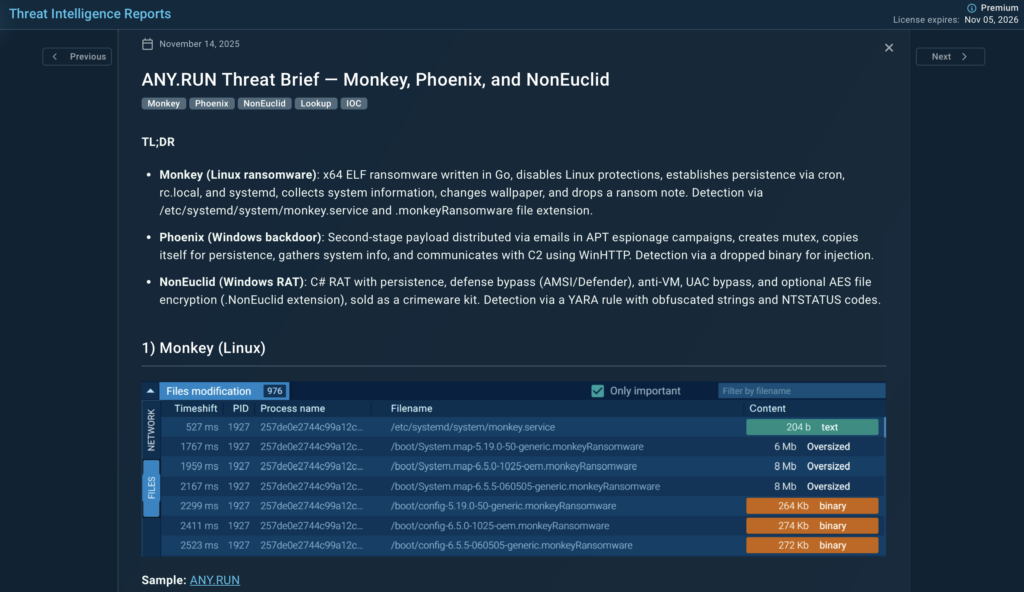
Monkey (Linux)
Monkey is a Go-based x64 ELF ransomware that disables security controls, establishes persistence through cron, rc.local, and systemd, collects system information, and encrypts files with a .monkeyRansomware extension. It also drops a ransom note and changes the system wallpaper.
Detection note: creation of /etc/systemd/system/monkey.service.
Lookup: filePath:”/etc/systemd/system/monkey.service”
Phoenix (Windows)
Phoenix is a Windows backdoor delivered as a second-stage payload in targeted email campaigns. It creates a mutex, copies itself for persistence, gathers system information, and communicates with its C2 via WinHTTP. The malware also uses process injection during execution.
Detection note: dropped binary sysProcUpdate.exe used for injection.
Lookup: registryValue:”sysProcUpdate.exe”
NonEuclid (Windows)
NonEuclid is a C# RAT with persistence, AMSI and Defender bypass, anti-VM checks, UAC bypass, and optional AES-based file encryption using the .NonEuclid extension. Sold as a crimeware kit, it combines remote control features with ransomware capabilities and uses obfuscated strings and NTSTATUS codes that can be detected via a dedicated YARA rule.
Detection note: YARA detection based on obfuscated Unicode strings and NTSTATUS markers.
Threat Intelligence Report 3: Valkyrie, Sfuzuan, and Sorvepotel
This Threat Brief examines three Windows-based threats with different infection vectors and persistence patterns. The report includes sandbox screenshots, process activity, on-disk artifacts, and TI Lookup queries for tracking related behavior across public submissions.
Valkyrie (Windows)
Valkyrie is a credential-stealing MaaS platform linked to Prysmax. It collects browser and system data, stores temporary output in Valkyrie.zip under the Temp directory, and exfiltrates the archive to a remote C2. Detection is possible through the Temp-path signature or a dedicated YARA rule included in the report.
TI Lookup: filePath:”C:\Users\admin\AppData\Local\Temp\Valkyrie.zip”
Sfuzuan (Windows)
Sfuzuan is a backdoor distributed through multiple, unrelated sources. It bypasses system protections to gain access, gathers system and location details, and connects to a set of rotating command-and-control domains. The malware drops a distinctive TXT file that serves as a reliable detection point.
TI Lookup: filePath:”C:\Windows\864ac8″
Sorvepotel (Windows)
Sorvepotel is a self-propagating campaign spread through WhatsApp messages containing malicious ZIP archives. After launch, it uses PowerShell and VBS scripts for execution and persistence, creates scheduled tasks, and automatically sends the same archive to all WhatsApp Web contacts. The campaign targets Portugal and Brazil using geofencing based on IP and system language.
TI Lookup: filePath:”Orcamento-2025*”
Empower Your SOC with Real-Time Behavioral Insights
Multi-stage loaders, encrypted payload containers, and region-aware campaigns are getting harder to catch with static filtering alone. While these threats unfold across PowerShell chains, COM-triggered executions, Linux services, or Android components, attackers move quickly, and manual triage can’t keep up. ANY.RUNgives SOC teams the behavioral visibility they need to respond at the speed of modern attacks.
Here’s how teams stay ahead:
- Surface hidden execution paths immediately: Detonate loaders, encrypted payloads, and cloud-hosted components inside a live VM and watch each stage, JavaScript, PowerShell, .NET, Linux services, or APK behavior, as it unfolds.
- Shorten investigation time: Automated unpacking, network tracing, and live indicators turn multi-stage chains into readable timelines, reducing time spent reversing obfuscated scripts or in-memory loaders.
- Catch stealthy techniques earlier: From fileless PowerShell commands to COM-based execution and WhatsApp-triggered propagation, behavioral cues expose activity that traditional tools overlook.
- Strengthen detections with instant enrichment: Use Threat Intelligence Lookup to pivot from a single IOC, file path, mutex, command line, or domain, to related submissions and shared TTPs across hundreds of cases.
- Feed continuous intelligence into your stack: Integrate Threat Intelligence Feeds with your SIEM, SOAR, or XDR to keep detections updated as new loader variants, stealer kits, and region-specific campaigns emerge.
For SOC teams, MSSPs, and threat researchers, ANY.RUN provides the depth and real-time visibility needed to investigate faster, validate threats quickly, and turn emerging behaviors into reliable detection logic.
Explore ANY.RUN with a 14-day trial →
About ANY.RUN
ANY.RUN supports more than 15,000 organizations worldwide across finance, healthcare, telecom, retail, and technology, helping security teams investigate threats with clarity and confidence.
Built for speed and deep visibility, the solution combines interactive malware analysis with live threat intelligence, allowing SOC analysts to observe real execution behavior, extract indicators, and understand attacker techniques in seconds.
By integrating ANY.RUN’s Threat Intelligence suite into existing security workflows, teams can accelerate investigations, reduce uncertainty during incidents, and strengthen resilience against fast-evolving malware families and multi-stage attack chains.
The post Major Cyber Attacks in November 2025: XWorm, JSGuLdr Loader, Phoenix Backdoor, Mobile Threats, and More appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

