Syncro + Lovable: RAT delivery via AI-generated websites | Kaspersky official blog
We recently detected a new malicious campaign that employs a rather intriguing approach. The actor creates their own signed builds of a legitimate remote access tool. To distribute them, they use an AI-powered service to mass-generate malicious web pages that convincingly masquerade as the official sites of various applications.
Read on to find out how this attack works, why it’s particularly dangerous for users, and how to protect yourself.
How the attack works
It appears that the malicious actor is utilizing several launchpad options for their attacks. First, they are clearly banking on a significant number of users landing on their fake pages through simple Google searches. This is because the fake sites most often have addresses that match — or are very close to — what users are searching for.
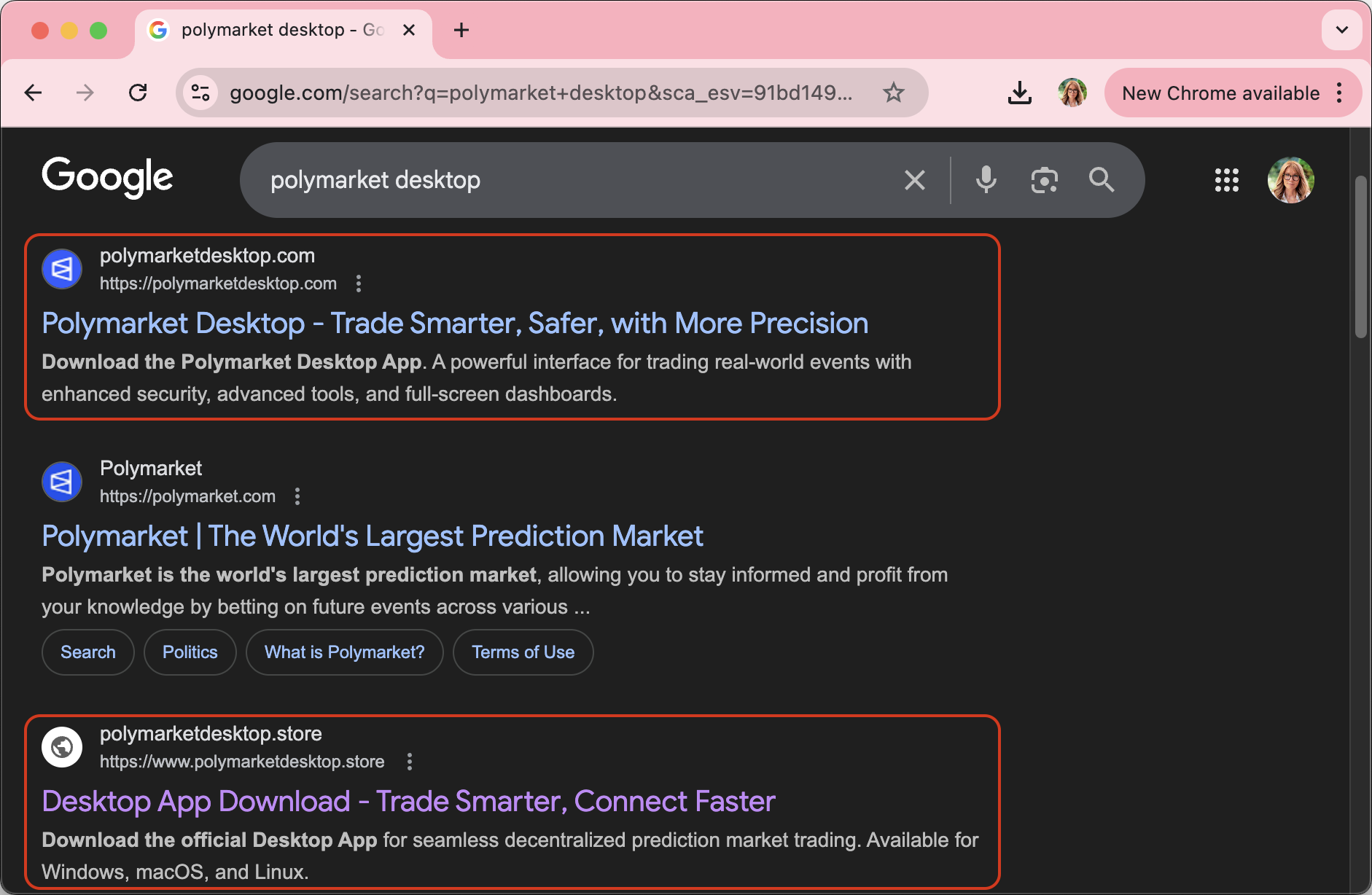
Looking through Google search results, you can sometimes catch a bunch of Pokémon fake sites masquerading as legitimate ones. In this case, we’re looking at Polymarket clones.
Second, they employ malicious email campaigns as an alternative. In this scenario, the attack kicks off with the user getting an email that contains a link to a fake website. The content might look something like this:
Dear $DOP holders,
The migration window from DOP-v1 to DOP-v2 has officially closed, with over 8B+ tokens successfully migrated.
We're excited to announce that the DOP-v2 Claim Portal is now OPEN!
All $DOP holders can now visit the portal to securely claim their tokens and step into the next phase of the ecosystem.
Claim Your DOP-v2 Tokens Now https://migrate-dop[dot]org/
Welcome to DOP-v2 — a stronger, smarter, and more rewarding chapter begins today.
Thank you for being part of this journey.
The DOP Team
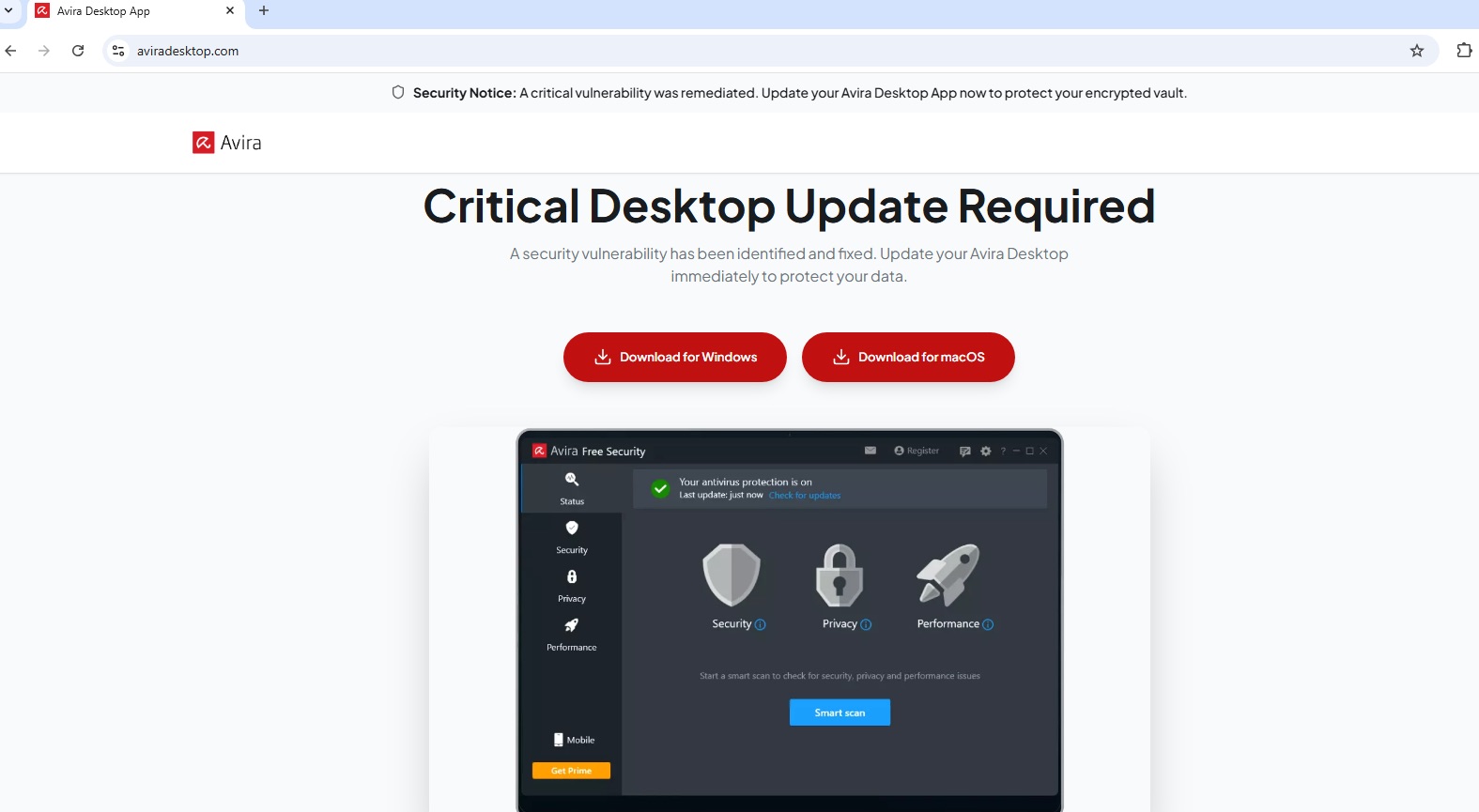
Some of the malicious pages we discovered in this campaign masquerade as the websites of antivirus or password management applications. Their content is clearly designed to scare the user with fake warnings about some kind of security issue.
So, the attackers are also leveraging a well-known tactic known as scareware: foisting an unsafe application on users under the guise of protection against an imaginary threat.
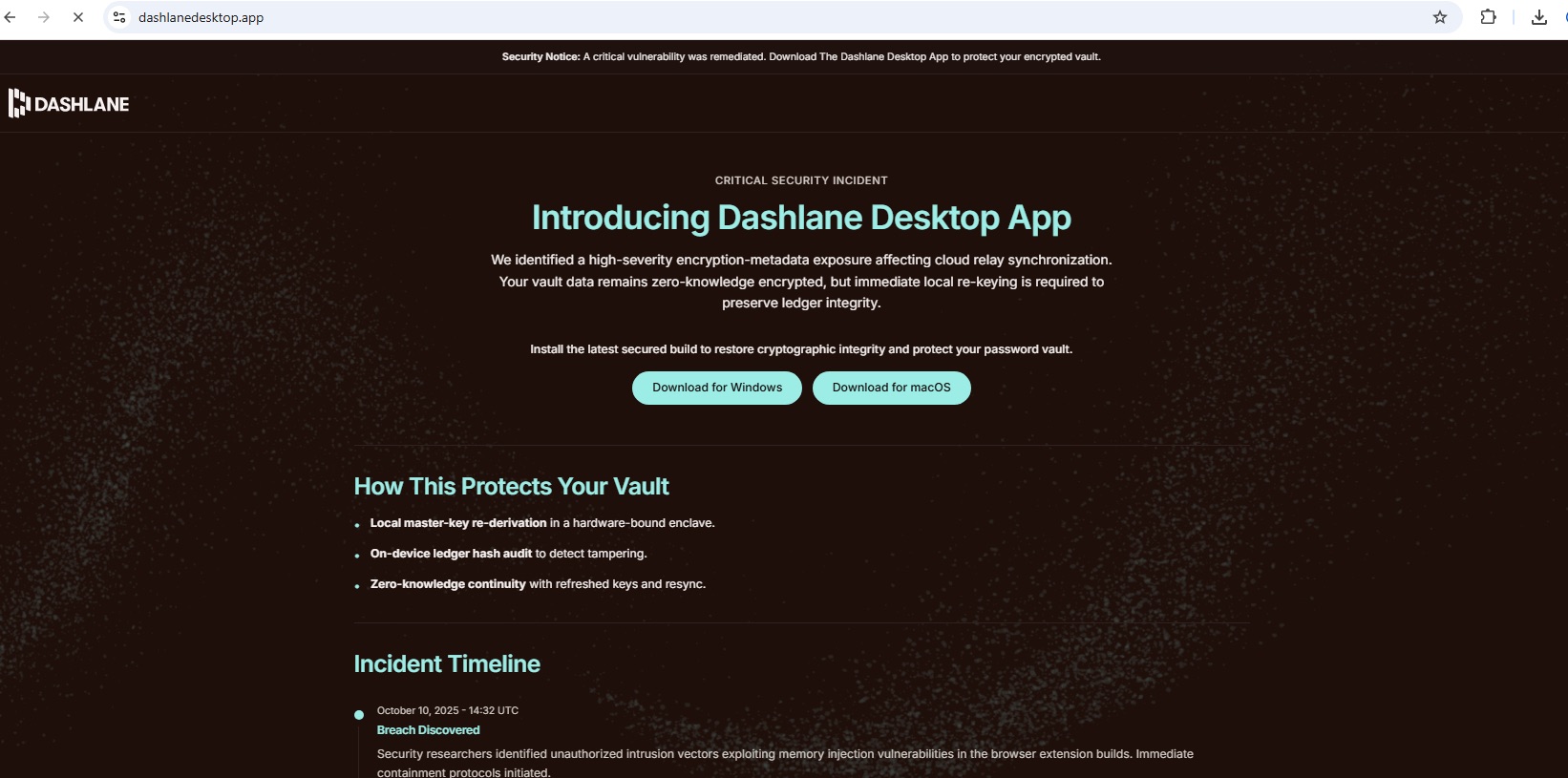
A fake Dashlane page warns of a “high-severity encryption-metadata exposure affecting cloud relay synchronization”, whatever that’s supposed to mean. And of course, you can’t fix it unless you download something
Fake websites built with Lovable
Despite differences in content, the fake websites involved in this malicious campaign share several common features. For starters, their addresses are most often constructed according to the formula: {popular app name} + desktop.com — a URL that closely matches an obviously common search query.
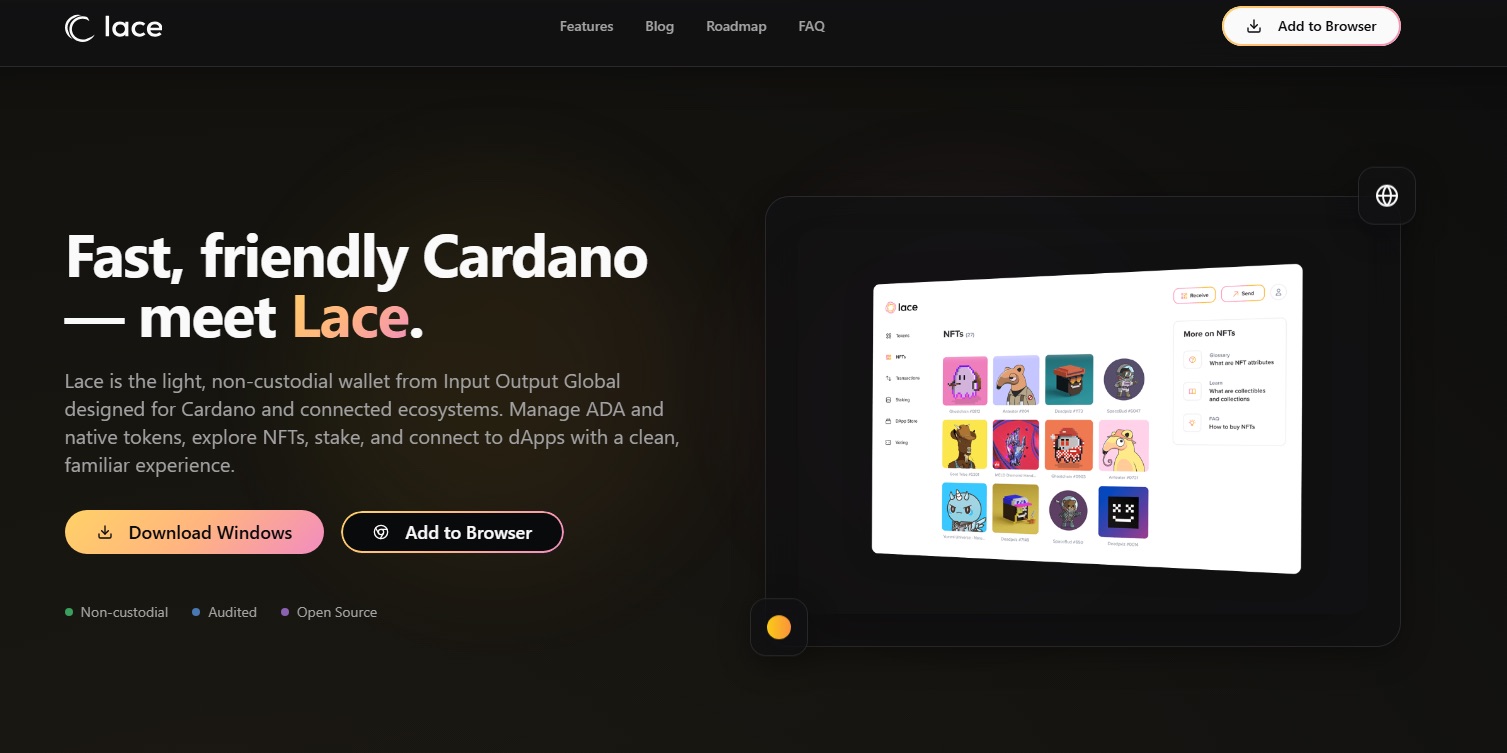
Besides, the fake pages themselves look quite professional. Interestingly, the appearance of the fake sites doesn’t exactly replicate the design of the originals — these are not direct clones. Rather, they are very convincing variations on a theme. As an example, we can look at some fake versions of the Lace crypto wallet page. One of them looks like this:
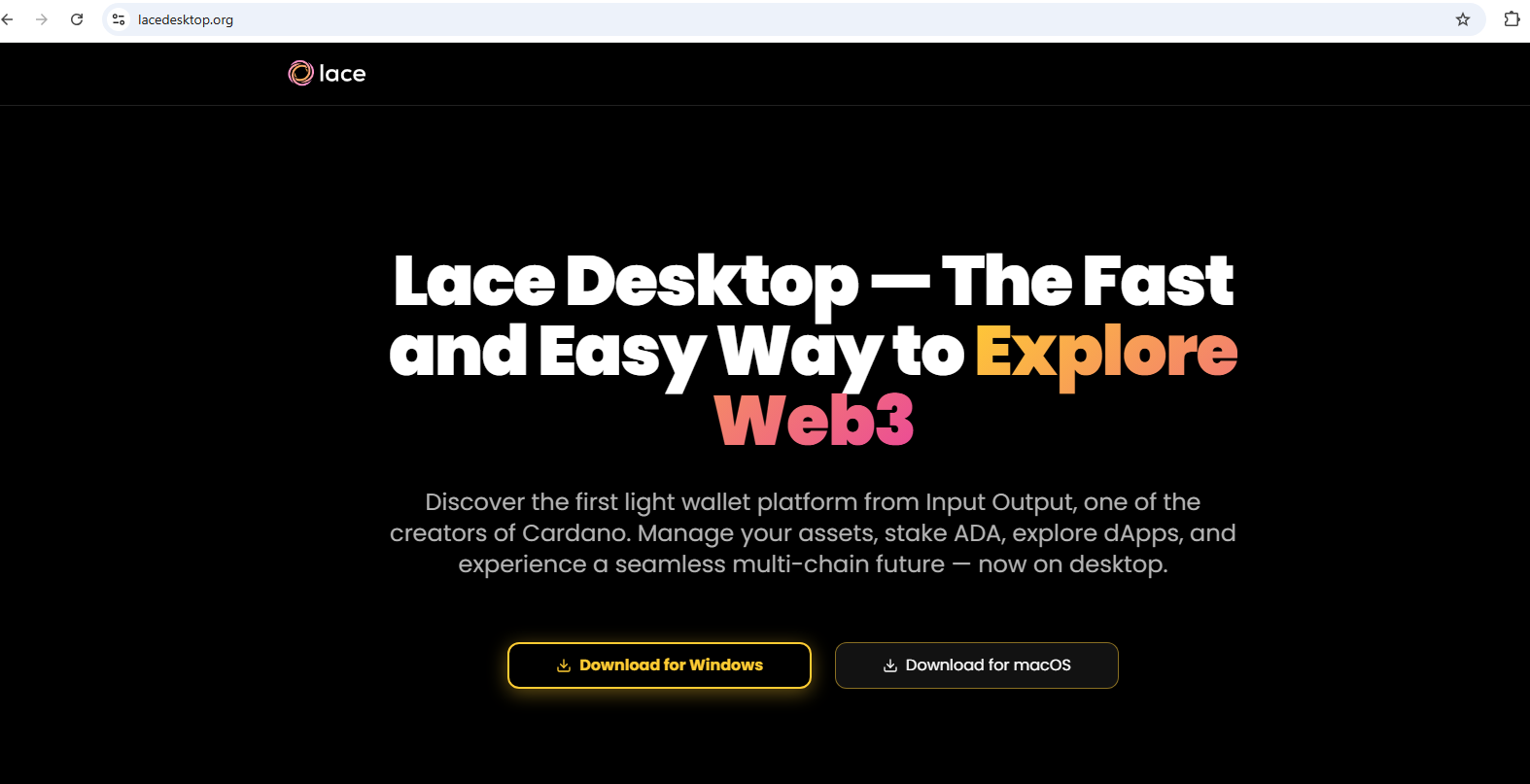
And the other looks like this:
The original Lace website looks a lot like these fakes, but it still differs from them in many obvious ways:
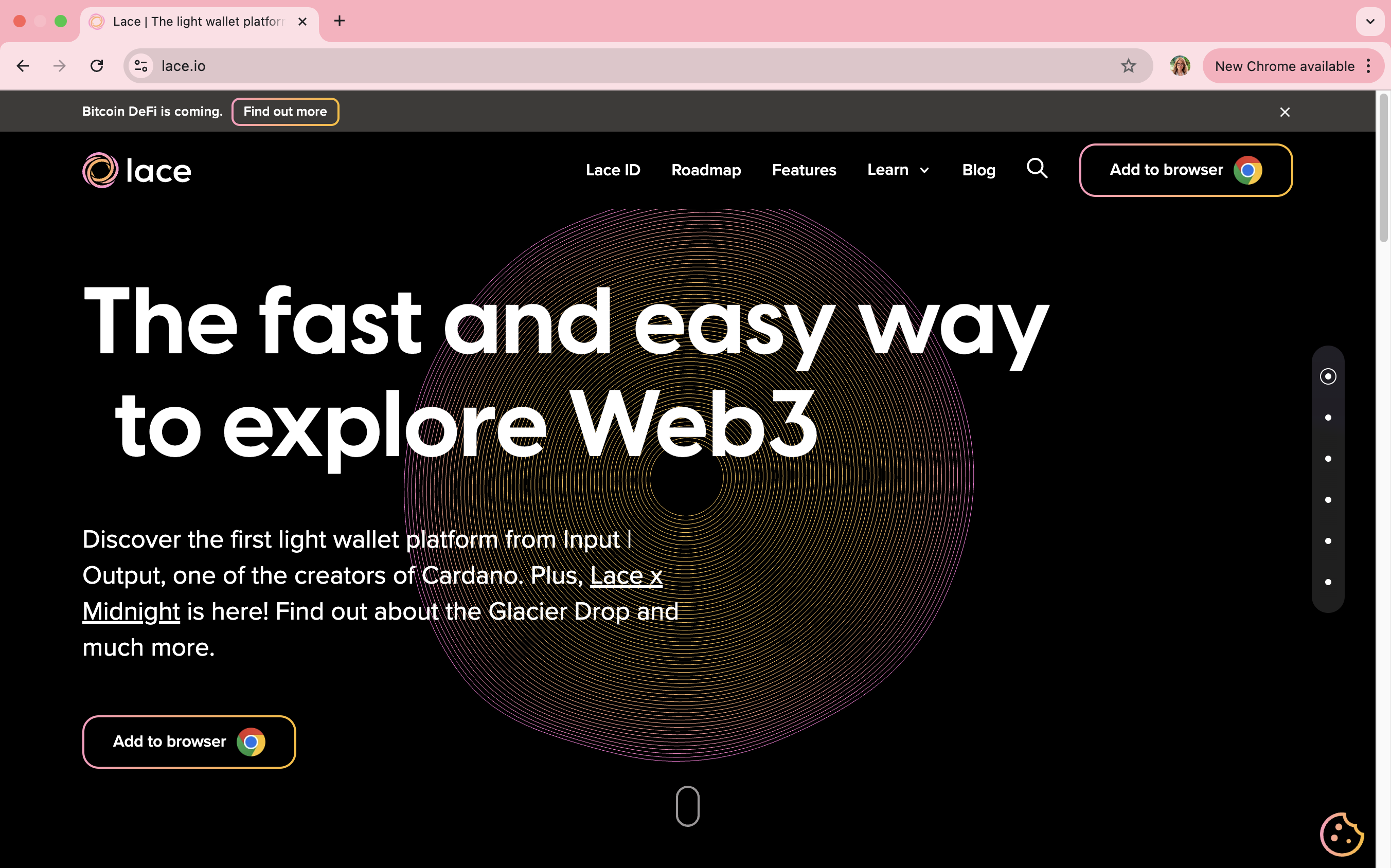
The real Lace website is simultaneously similar and dissimilar to the fake versions. Source
It turns out the attackers have weaponized an AI-powered web builder to create fake pages. Because the attackers cut corners and inadvertently left a few tell-tale artifacts, we managed to identify the exact service they are leveraging: Lovable.
Using an AI tool allowed them to significantly reduce the time required to create a fake, thereby churning out forgeries on an industrial scale.
Syncro remote administration tool
Another common feature of the fake sites involved in this campaign is that they all distribute the exact same payload. The malicious actor neither created their own Trojan nor bought one off the black market. Instead, they are using their own build of a perfectly legitimate remote access tool, Syncro.
The original app facilitates centralized monitoring and remote access for corporate IT support teams and managed service providers (MSPs). Syncro services are relatively inexpensive, starting at $129 per month with an unlimited number of managed devices.
At the same time, the tool possesses serious capabilities: in addition to screen sharing, the service also provides remote command execution, file transfer, log analysis, registry editing, and other background actions. However, Syncro’s main appeal is a simplified installation and connection process. The user — or, in this case, the victim — only has to download and run the installation file.
From that point, the installation runs completely in the background, secretly loading a malicious Syncro build onto the computer. Because this build has the attacker’s CUSTOMER_ID hardcoded, they instantly gain full control over the victim’s machine.
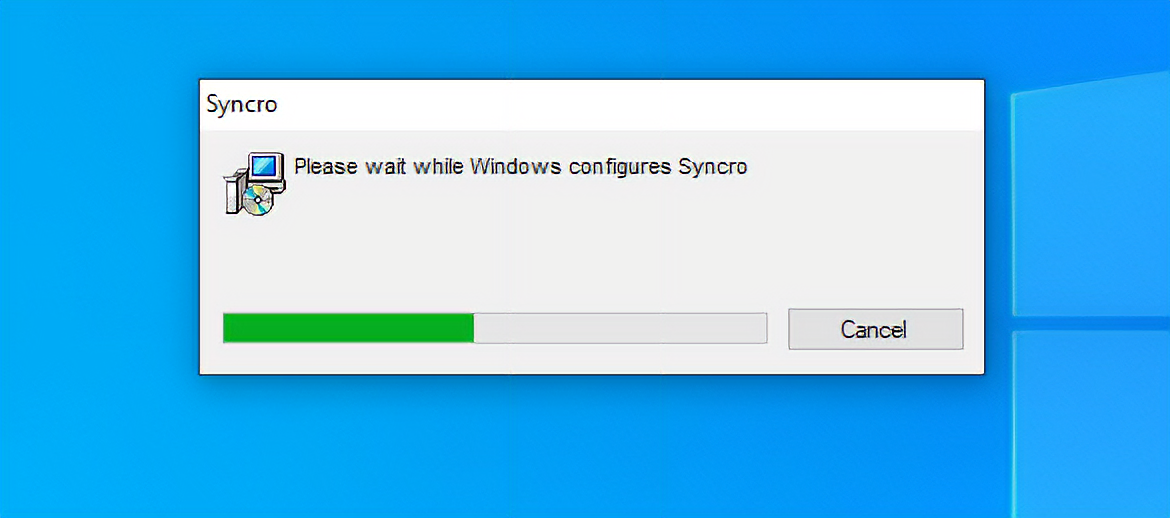
The Syncro installer window flashes on the screen for mere seconds, and only a keen-eyed user might notice that the wrong software is being set up.
Once Syncro is installed on the victim’s device, the attackers gain full access and can use it to achieve their objectives. Given the context, these appear to be stealing crypto wallet keys from victims and siphoning off funds into the attackers’ own accounts.
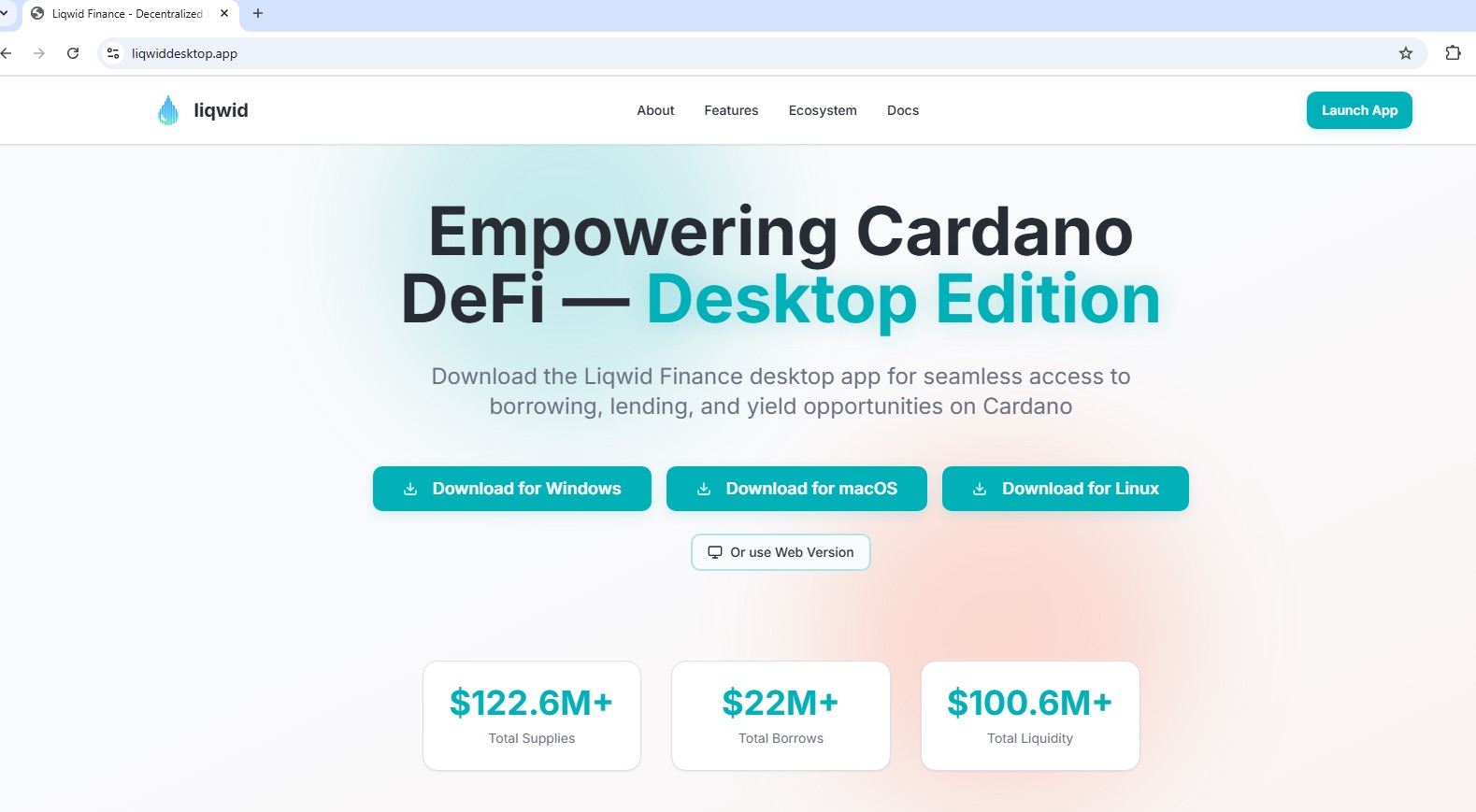
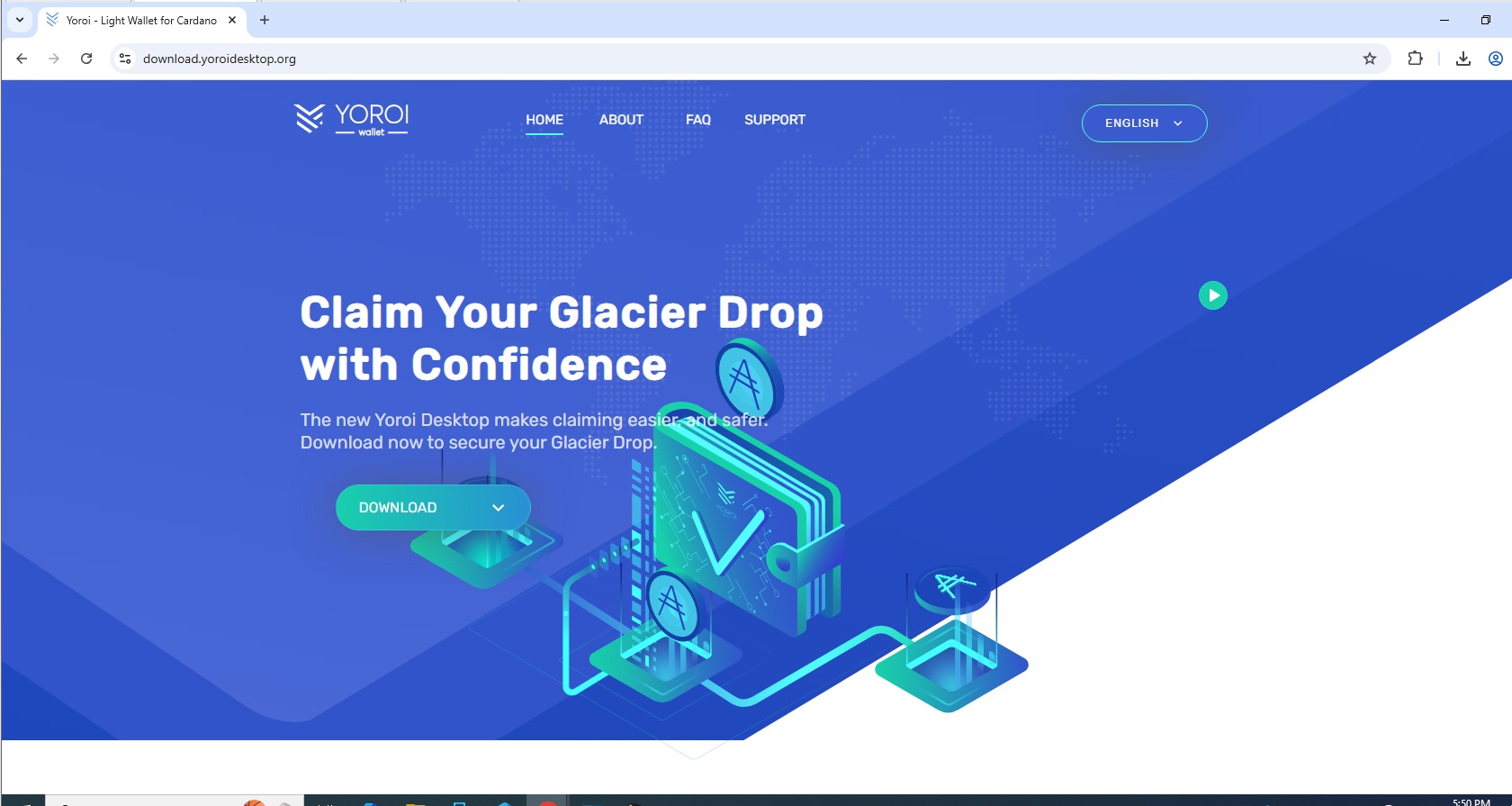
Another fake site, now for the Liqwid DeFi protocol. Although Liqwid offers only a web application, the fake site allows users to download versions for Windows, macOS, and even Linux
How to protect yourself against these attacks
This malicious campaign poses a heightened threat to users for two main reasons. First, the fake sites crafted with the AI service look quite professional, and their URLs aren’t overly suspicious. Of course, both the design of the fake pages and the domains used differ noticeably from the real ones, but this only becomes apparent in direct comparison. At a glance, however, it’s easy to mistake the fake for the original.
Second, the attackers are using a legitimate remote access tool to infect users. This means that detecting the infection can be difficult.
Our security solution has a special verdict, Not-a-virus for cases like this. This verdict is assigned, among other things, when various remote access tools — including the legitimate Syncro — are detected on the device. As for Syncro builds used for malicious purposes, our security solution detects them as HEUR:Backdoor.OLE2.RA-Based.gen.
It’s important to remember that an antivirus won’t block all legitimate remote administration tools by default to avoid interfering with intentional usage. Therefore, we recommend that you pay close attention to notifications from your security solution. If you see a warning that Not-a-virus software has been detected on your device, take it seriously and, at the very least, check which application triggered it.
If you have Kaspersky Premium installed, use the Remote Access Detection feature — and, if necessary, the app removal option — that come with your premium subscription. This feature detects around 30 of the most popular legitimate remote access applications, and if you know you didn’t install them yourself, that is cause for concern.
Further recommendations:
- Don’t download applications from dubious sources, especially on devices with financial or crypto apps installed.
- Always double-check the addresses of the pages you’re visiting before performing any potentially dangerous actions like downloading an app or entering personal data.
- Pay close attention to warnings from the antivirus and anti-phishing defenses built into our security solutions.
Kaspersky official blog – Read More