What is a Malware Sandbox? Everything SOC Analysts and CISOs Need to Know
Each cyberattack leaves behavioral evidence. A malware sandbox provides the secure environment analysts need to study that activity and uncover hidden tactics.
Teams using sandbox analysis report measurable gains:
- 90% faster detection of unknown malware
- Up to 3× improvement in investigation speed
- 60% fewer false positives in automated alerts
Behavior-based visibility gives SOCs the upper hand against stealthy attacks. Let’s see how sandbox security works, and why it has become essential for modern threat detection.
What’s a Malware Sandbox?
A malware sandbox is a controlled, isolated environment designed to safely run and observe suspicious files, links, or applications. It allows analysts to see exactly how a threat behaves without risking real systems or networks.
Instead of relying on signatures or predefined rules, a sandbox focuses on dynamic malware analysis, monitoring how code acts in motion. This approach helps detect new, unknown, or obfuscated malware that traditional antivirus tools often miss.
Watch the full video on how ANY.RUN’s malware sandbox works
Inside the sandbox environment, analysts can observe file system changes, registry modifications, network requests, and command execution in real time. Every action is recorded, creating a detailed behavioral profile that reveals the malware’s purpose, persistence methods, and communication patterns.
In short, a malware analysis sandbox turns hidden threats into visible data, giving cybersecurity teams the clarity they need to understand, detect, and stop complex attacks before they spread.
How Does a Malware Sandbox Work?
A malware sandbox operates by executing suspicious files, links, or processes in a virtual and fully isolated environment that imitates a real operating system. This lets analysts safely observe every action the sample performs, without exposing actual devices or networks to risk.
Modern sandboxes can be built on virtual machines, containers, or emulation frameworks. Each architecture recreates realistic conditions, including file systems, system registries, network connections, and even user interactions, so malware behaves as it would in the wild.
Here’s how sandbox analysis typically unfolds:
- Submission: A suspicious file or URL is uploaded to the sandbox environment for testing.
- Execution: The sample runs in isolation, often within multiple OS profiles or hardware simulations.
- Observation: The sandbox records every change; file creation, registry edits, system calls, and outbound connections.
- Reporting: Once execution completes, a detailed report summarizes the malware’s actions, persistence attempts, and communication patterns.
This approach, known as dynamic malware analysis, focuses on behavior instead of static code. It allows analysts to detect zero-day threats, hidden payloads, and polymorphic variants that traditional antivirus tools often miss.
Advanced malware detection sandboxes also counter evasion tactics by simulating real user activity, extending runtime to catch delayed triggers, and randomizing system identifiers to appear like genuine machines.
By sandboxing malware, security teams gain deep behavioral visibility, understanding not just what the file is, but what it tries to do.
Example: See Real Sandbox Analysis in Action
To see how this process works in practice, let’s look at a real-world example. Inside the ANY.RUN sandbox, a phishing sample pretending to be a Google Careers page was analyzed.
The sandbox reveals the entire attack chain in just 60 seconds, from the Salesforce redirect and Cloudflare CAPTCHA to the fake login page that stole credentials and sent them to its command server.
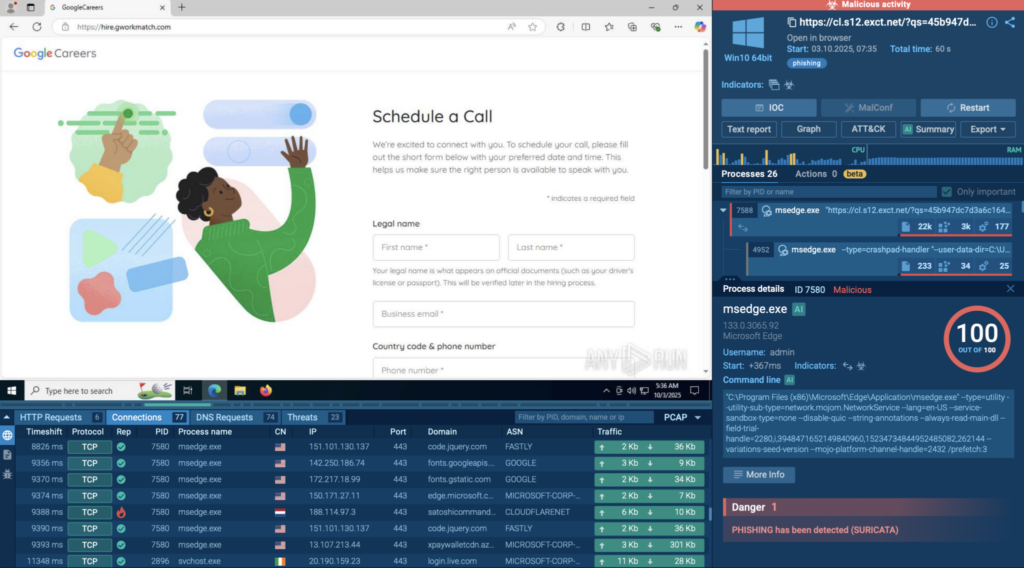
All stages were captured in real time: every request, redirection, and data theft attempt. The sandbox also generated a full picture of the attack: key indicators like file hashes and domains, the techniques the malware used, its network activity, and a clear process timeline. Everything an analyst would need to investigate or build detection rules was right there in one report.
Benefits of a Malware Sandbox
A malware sandbox gives analysts a clear view of what really happens when a threat runs. Instead of guessing based on static scans or file signatures, teams can watch the malware in action; safely, and in real time.
Here’s why that matters:
- Detect new threats early: Behavior-based detection helps catch zero-day malware before traditional tools even recognize it.
- See the full attack chain: From file creation to network communication, sandboxes reveal every step the malware takes.
- Cut down false alarms: Real behavior data separates real threats from harmless lookalikes, reducing alert fatigue.
- Save investigation time: Automated sandbox analysis delivers full behavioral reports in minutes, not hours.
- Strengthen threat intelligence: Indicators like domains, hashes, and payloads collected from sandbox runs can feed directly into your detection systems.
- Scale with ease: Cloud sandbox setups let teams analyze thousands of samples at once, keeping pace with large-scale attacks.
In short, a malware sandbox helps teams move from guessing to knowing, turning hidden behavior into clear, actionable insights that speed up detection and response.
Types of Malware Sandboxes
Not all sandboxes work the same way. Depending on how they’re deployed and what they’re used for, organizations can choose between several types, each offering a different balance of control, scalability, and performance.
1. On-Premise Sandboxes
These sandboxes run inside an organization’s own infrastructure. They’re ideal for teams that handle sensitive data and need full control over their analysis environment. On-premise setups can be customized to mimic internal systems closely, from OS configurations to network settings, but they often require more maintenance and hardware resources.
2. Cloud Sandboxes
A cloud sandbox runs remotely, making it easier to scale and share results across distributed teams. It’s especially useful for SOCs that need to analyze large volumes of samples daily or for companies that want access without complex local setup. Cloud solutions also stay up to date automatically, ensuring faster adaptation to new threats.
3. Open-Source Sandboxes
These types of sandboxes allow researchers and security teams to build their own sandbox environments from scratch. They’re highly customizable and great for experimentation or research, though they usually require more technical know-how to maintain.
Each of these types of malware sandboxes serves a different need; from enterprise-grade automation to hands-on analysis. Choosing the right one depends on how much control, customization, and scale your security operations require.
| Feature | On-Premise | Cloud | Open-Source |
|---|---|---|---|
| Easy setup & deployment |
 |
 |
 Manual Manual |
| Automatic updates |
 |
 |
 |
| Scalable for multiple analyses |
 Limited Limited |
 |
 Limited Limited |
| Customizable environment |
 |
 Partial Partial |
 |
| Real-time collaboration |
 |
 |
 |
| No maintenance required |
 |
 |
 |
| Integration with other tools (SIEM, SOAR, etc.) |
 Possible Possible |
 |
 Manual Manual |
| Cost efficiency |
 Medium Medium |
 |
 (Free) (Free) |
| Data privacy & local control |
 |
 Depends on provider Depends on provider |
 |
| Ideal for large SOCs & MSSPs |
 Sometimes Sometimes |
 |
 |
 — Yes
— Yes  — Partial / depends on setup
— Partial / depends on setup  — No
— No
Who Needs a Malware Sandbox and How They Use It
A malware sandbox is a daily necessity across different areas of cybersecurity. From SOC teams to threat intelligence analysts, everyone benefits from being able to see how malware behaves in a safe environment.

Here’s how different professionals rely on sandbox analysis:
- SOC teams: Use sandboxes to validate alerts and speed up triage. Instead of guessing whether a file is dangerous, they can watch its behavior in real time and prioritize responses accordingly.
- Incident responders: Reconstruct full attack chains after an intrusion. Sandbox reports reveal what files were dropped, which connections were made, and how the infection spread; key data for containment.
- Threat intelligence analysts: Extract indicators of compromise (IOCs), domains, and behavioral patterns to feed detection rules and threat databases.
- Researchers and malware analysts: Study new malware families in depth without risking production systems, documenting how they evolve or communicate with C2 servers.
- Managed security providers (MSSPs): Integrate sandbox results into client reports or monitoring workflows, adding measurable value to their detection and response services.
Sandbox vs Antivirus: Why Sandboxing Wins Against Unknown Threats
Antivirus software protects against threats that are already known. It scans files, compares them to a database of malware signatures, and blocks anything that matches. This method works well for common, well-documented attacks, but it struggles with new or changing ones.
Modern malware often hides its code, changes its structure, or uses encryption to stay invisible to signature-based tools. That’s where a malware sandbox makes all the difference.
Instead of checking what a file looks like, a sandbox watches what it does. It runs the file in a safe, isolated environment and tracks every move; the processes it starts, the files it creates, and the connections it tries to make. This approach, called behavior-based detection, exposes even the newest or most complex threats.
Simply put, antivirus tools stop what’s already known. A malware sandbox uncovers what’s new and unknown.
Used together, they give teams both quick protection and deeper visibility; a strong mix for modern cyber defense.
How Attackers Try to Evade Sandboxes and Why They Still Get Caught
As malware sandboxes become more advanced, attackers are learning to adapt. Some modern malware doesn’t simply run its code right away; it first checks where it’s running. If it senses it’s inside a sandbox, it may stay quiet, hoping to slip through undetected.
These are some of the most common tricks attackers use:
- Delaying execution: The malware waits several minutes or hours before acting, trying to outlast the sandbox’s observation time.
- Looking for virtual clues: It searches for signs that it’s inside a virtual machine, like specific file names, processes, or limited memory, and stops running if it finds them.
- Waiting for human activity: Some samples won’t execute until they detect mouse movement or clicks, assuming automated systems won’t simulate them.
- Checking network connections: Malware might reach out to its command-and-control server and only activate if it receives a valid response.
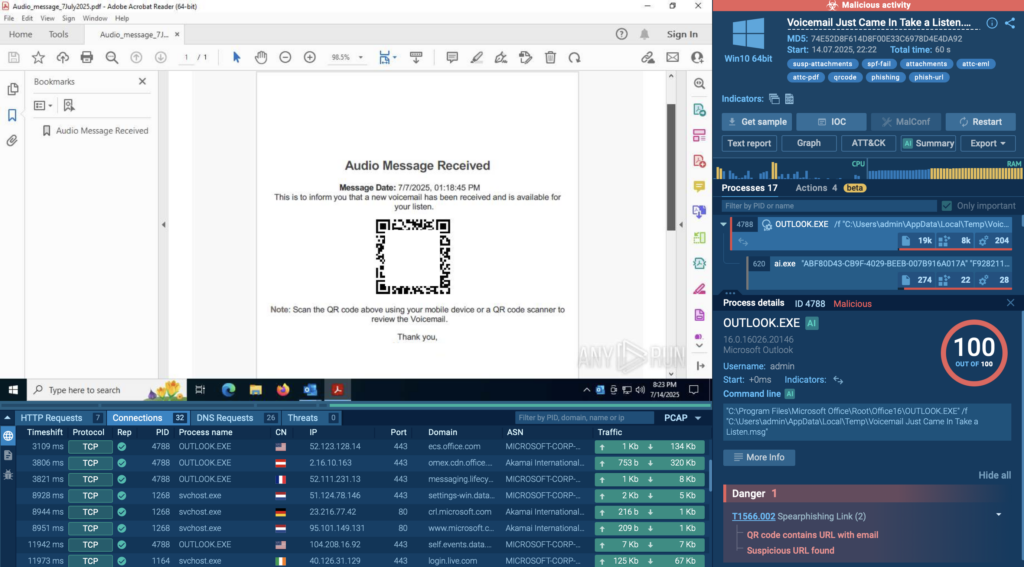
To keep up, modern malware analysis sandboxes have grown much smarter. They simulate human actions like typing and clicking, randomize virtual hardware details, and even extend analysis time to catch delayed behavior. Some advanced platforms also run the same sample across multiple environments to expose hidden logic or secondary payloads.
So yes, attackers keep trying to fool sandboxes. But as sandbox technology evolves, those tricks are becoming less effective. Each new generation of sandbox security makes it harder for malware to hide, ensuring analysts still see the full picture before damage is done.
How to Choose the Right Malware Sandbox
With so many sandbox solutions available, choosing the right one can be tricky. Some focus on quick verdicts, others on deep behavioral insights. The best choice depends on your goals; whether you’re running a SOC, enriching threat intelligence, or conducting malware research.
When evaluating options, start with what matters most: visibility. A good sandbox doesn’t just tell you that a file is malicious, it shows why. It should capture every action the sample performs: file system changes, registry edits, process trees, and network traffic. These behavioral details are what make sandbox analysis so powerful.
Realism is equally important. The closer the sandbox mimics a real system, the more accurate the results. Platforms that support multiple operating systems and simulate user activity (like mouse clicks or typing) are better at exposing evasive malware that would otherwise stay hidden.
Speed, scalability, and integration also matter. Cloud-based sandboxes process hundreds of samples in parallel, deliver reports within minutes, and connect easily to SIEM, SOAR, or threat intelligence systems. Structured exports in formats like JSON or STIX/TAXII make automation effortless.
Finally, consider privacy. If you work with sensitive or client data, make sure your sandbox offers private or isolated analysis modes.
When choosing your sandbox, think beyond detection. Look for visibility, speed, flexibility, and control; the qualities that help you understand how malware behaves and stop it before it spreads.
Why ANY.RUN Meets These Criteria
If you take those same criteria and apply them to ANY.RUN, you’ll see how closely the platform aligns with what modern security teams need.
| Factor | How ANY.RUN Delivers It |
|---|---|
| Behavioral visibility | Displays every system and network action in real time, with visualized process trees and detailed logs. |
| Realistic environment | Simulates genuine user behavior, forcing evasive malware to reveal its payloads. |
| Multiple OS environments | Supports Windows, Linux, Android analysis, with new profiles added regularly. |
| Interactivity | Analysts can click, type, and interact with running samples — exposing behavior that static tools miss. |
| Speed and scalability | Cloud infrastructure processes multiple samples in parallel, generating full reports in minutes. |
| Automation and integrations | Connects with SIEM, SOAR, and TI tools via API or webhook for seamless workflow automation. |
| Threat intelligence enrichment | Extracts IOCs, maps MITRE ATT&CK techniques, and links to related CVEs automatically. |
| Clear, exportable reports | Offers human-readable summaries and structured outputs (JSON, STIX/TAXII). |
| Privacy options | Private analysis mode ensures sensitive data stays isolated and secure. |
| Ease of use | Intuitive interface and quick setup make analysis accessible to any skill level. |
| Anti-evasion features | Randomized environments, user simulation, and adjustable runtime defeat stealthy malware tactics. |
| Managed lookups & history | Analysts can search past public or private sessions and track recurring threats. |
ANY.RUN combines what most teams need from a sandbox: visibility, control, and speed; all in a secure, interactive cloud environment. It helps analysts move faster, collaborate better, and uncover behaviors that traditional tools simply can’t see.
Teams Using ANY.RUN’s Interactive Sandbox Report Measurable Results:
- 95% of SOCs speed up investigations through real-time interaction and live analysis.
- Up to 3× higher SOC efficiency, with faster decision-making and automated data sharing.
- 21-minute reduction in mean time to respond (MTTR) per incident.
- 36% higher detection rate on average, uncovering hidden and multi-stage threats earlier.
- Up to 58% more threats detected overall, with behavioral visibility that static tools can’t match.
- 20% lower workload for Tier 1 analysts, as sandbox automation removes repetitive triage steps.
- 30% fewer Tier 1 → Tier 2 escalations, thanks to clearer, interactive analysis reports.
- 90% of threats visible within 60 seconds, allowing faster containment and less dwell time.
For businesses, that means lower risk exposure, more productive analysts, and faster containment of incidents, all without expanding headcount or infrastructure.
Frequently Asked Questions About Malware Sandboxes
Yes. Antivirus tools catch known threats using signatures, while a sandbox helps detect unknown or evolving malware by observing real behavior. Together, they form a stronger defense.
It’s extremely rare with modern platforms. Reputable sandboxes, especially cloud-based ones, use strict isolation layers to ensure any malicious code stays fully contained.
Most analyses complete in a few minutes. Cloud sandboxes are faster because they can run multiple sessions at once and generate reports almost instantly. For instance, 90% of sandbox analysis carried out inside ANY.RUN sandbox last around 60 seconds.
Static analysis examines code without executing it. Dynamic analysis, what a sandbox performs, actually runs the file to observe its real behavior and system impact.
Look for detailed behavioral reports, IOCs extraction, and options for interactivity or automation. If it helps you understand why a file is malicious, not just that it is, it’s doing its job well.
Yes, when privacy features are enabled. Some solutions, like the ANY.RUN sandbox, let users run fully private sessions where samples and results stay completely isolated.
Dynamic environments are especially useful for ransomware, downloaders, stealers, and phishing payloads; malware that changes behavior based on context or timing.
Many modern sandboxes like ANY.RUN’s Interactive Sandbox support API connections, STIX/TAXII feeds, and SIEM/SOAR integrations. This allows automatic data sharing and faster incident response.
About ANY.RUN
ANY.RUN, a leading provider of interactive malware analysis and threat intelligence solutions, makes this kind of investigation fast and accessible. The service processes millions of analysis sessions and is trusted by 15,000+ organizations and over 500,000 professionals worldwide.
Teams using ANY.RUN report measurable results; up to 3× higher SOC efficiency, 90% faster detection of unknown threats, and a 60% drop in false positives thanks to real-time interaction and behavior-based analysis.
Explore ANY.RUN’s capabilities during 14-day trial→
Discover how ANY.RUN can help your team detect faster, analyze deeper, and respond smarter.
The post What is a Malware Sandbox? Everything SOC Analysts and CISOs Need to Know appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
