No Threats Left Behind: SOC Analyst’s Guide to Expert Triage
A SOC is where every second counts. Amidst a flood of alerts, false positives, and ever-short time, analysts face the daily challenge of identifying what truly matters — before attackers gain ground.
That’s where alert triage comes in: the essential first step in detecting, prioritizing, and responding to threats efficiently. Done right, it defines the overall effectiveness of a SOC or MSSP and determines how well an organization can defend itself.
Spoiler Alert About Alerts
Here’s your spoiler for today: good triage starts with great threat intelligence.
ANY.RUN’s Threat Intelligence Lookup doesn’t just enrich alerts — it rewrites the rules of triage by turning scattered IOCs into instant context. But we’ll get there. Let’s start from the analyst’s desk, where the real noise begins.
Why Triage Is the Heartbeat of the SOC
Behind every successful SOC, there’s a smooth triage flow that keeps chaos under control. It’s not just about filtering alerts. It’s about shaping the SOC’s rhythm and resilience.
When analysts perform triage effectively:
- They build the first and strongest defense layer against real attacks.
- They ensure human attention is spent where it matters most.
- They create a foundation for accurate detection and response metrics like MTTD and MTTR.
- They make security predictable and measurable, not reactive and random.
The Daily Puzzle: Making Sense of a Thousand Pings
The challenge is not a lack of data — it’s too much of it. The toughest barriers to effective triage include:
- Alert overload — When every ping demands attention, focus becomes the first casualty.
- False positives — Automation can cry wolf more often than it should.
- Threat complexity —Today’s attackers employ sophisticated techniques designed to evade detection.
- Context gaps — An IP is just an IP until you know its story.
- Time compression — Analysts often have seconds, not minutes, to make judgment calls.
- Data silos — TI feeds, SIEMs, and sandboxes don’t always talk to each other.
The result? Valuable threats risk getting buried under a pile of meaningless noise.
Speed, Precision, and the Numbers That Matter
In triage, speed without accuracy is chaos, and accuracy without speed is luxury. That’s why SOCs track their efficiency through key metrics. KPIs aren’t just for bosses—they’re your triage compass. Track these to benchmark progress and spot bottlenecks:
| KPI | Description | Target Benchmark | Why It Matters for Triage |
|---|---|---|---|
| Mean Time to Detect (MTTD) | Average time from threat emergence to alert generation. | Measures triage speed in spotting signals amid noise. | |
| Mean Time to Respond (MTTR) | Time from alert to containment/remediation. | Highlights routing efficiency—faster triage feeds faster responses. | |
| False Positive Rate | Percentage of alerts dismissed as non-threats. | Low rates mean better prioritization; high ones signal fatigue. | |
| Alert Closure Rate | Alerts triaged per analyst per shift. | 50-100 | Gauges productivity without burnout. |
| Escalation Rate | % of alerts bumped to higher tiers. | Reflects triage accuracy—fewer escalations mean empowered Tier 1. | |
| Wrong Verdict Rate | Misclassified alerts (internal audit). | Tracks skill gaps; aim for continuous improvement via training. |
High-performing SOCs balance speed and certainty by using intelligence enrichment to cut decision time without cutting quality. Those KPIs are not just numbers; they’re the story of how well your triage works.
From Metrics to Meaning: Why Triage Drives Business Outcomes
Triage might look like a technical process, but its impact is strategic. Understanding how your triage work supports broader business objectives, helps you make better decisions, and communicate your value effectively.
For SOCs and MSSPs, efficient triage is a business differentiator:
- Fewer false positives mean less analyst burnout and higher client capacity.
- Faster incident validation means better SLA performance and client trust.
- Smarter prioritization reduces wasted time and investigation costs.
- Structured triage data improves long-term visibility and readiness.
In short, triage is where operational efficiency meets customer confidence — and where the SOC’s reputation is quietly built every day.
Turning Alerts into Insight: How ANY.RUN TI Lookup Changes the Game
ANY.RUN’s Threat Intelligence Lookup is a comprehensive threat intelligence service that provides instant access to detailed information about files, URLs, domains, and IP addresses. It enables analysts to explore IOCs, IOBs, and IOAs using over 40 search parameters, basic search operators, and wildcards. The data is derived from millions of live malware sandbox analyses run by a community of 15K corporate SOC teams.
When you encounter suspicious artifacts, you can query the service to obtain behavioral analysis, threat classification, and historical context — all within seconds.
Here’s what it brings to the triage table:
Instant IOC Enrichment
Drop in any hash, IP, or domain and see how it ties to known malware families, timelines, and campaigns — in seconds. Let’s take for example a suspicious IP spotted in the traffic:
domainName:”23.ip.gl.ply.gg”
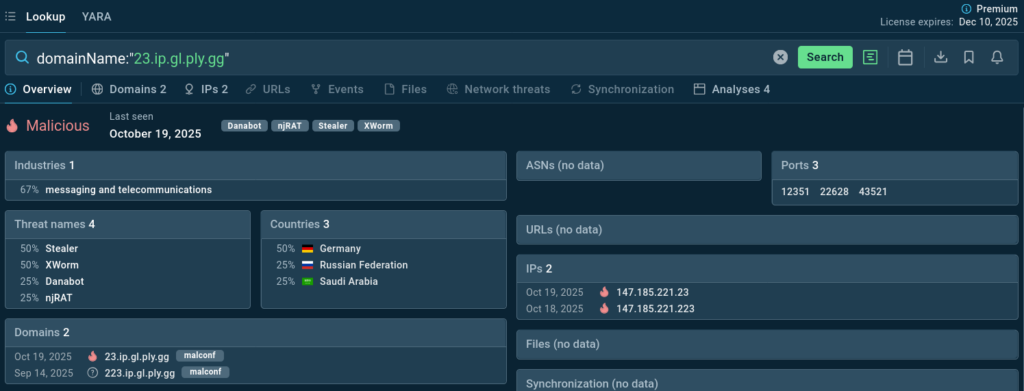
In an instant, one knows that the domain is linked to several notorious trojans and has been spotted in recent incidents thus being certainly malicious and actively used.
Real-Time Malware Activity Stats
The “Malware Threats Statistics” feature spotlights live, active infrastructures, showing which malware families are truly circulating today.
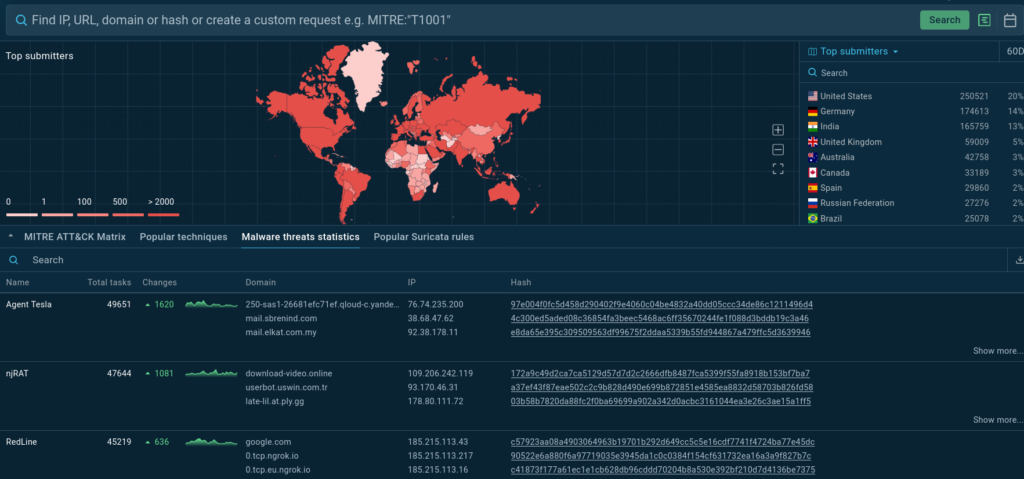
This tab can also be a source of recent IOCs for monitoring and detection.
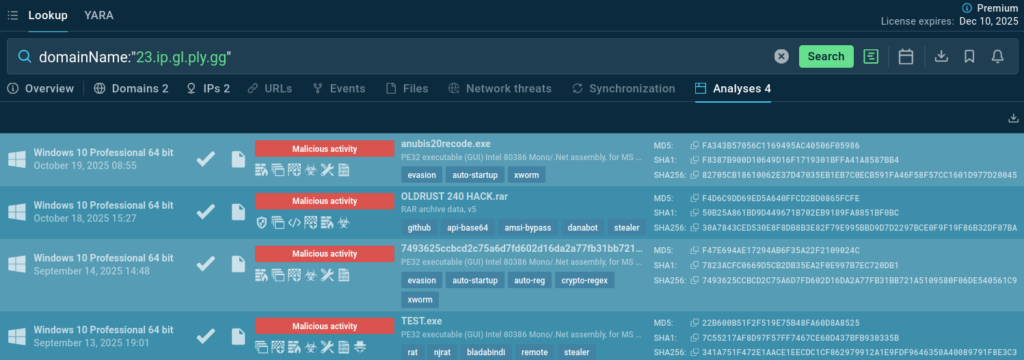
Behavioral Pivoting
With one click, analysts can move from static enrichment to dynamic ANY.RUN sandbox reports, verifying behavior firsthand.
Risk-Based Prioritization
TI Lookup reveals which alerts link to active C2s or payloads, helping teams focus on what’s actually dangerous.
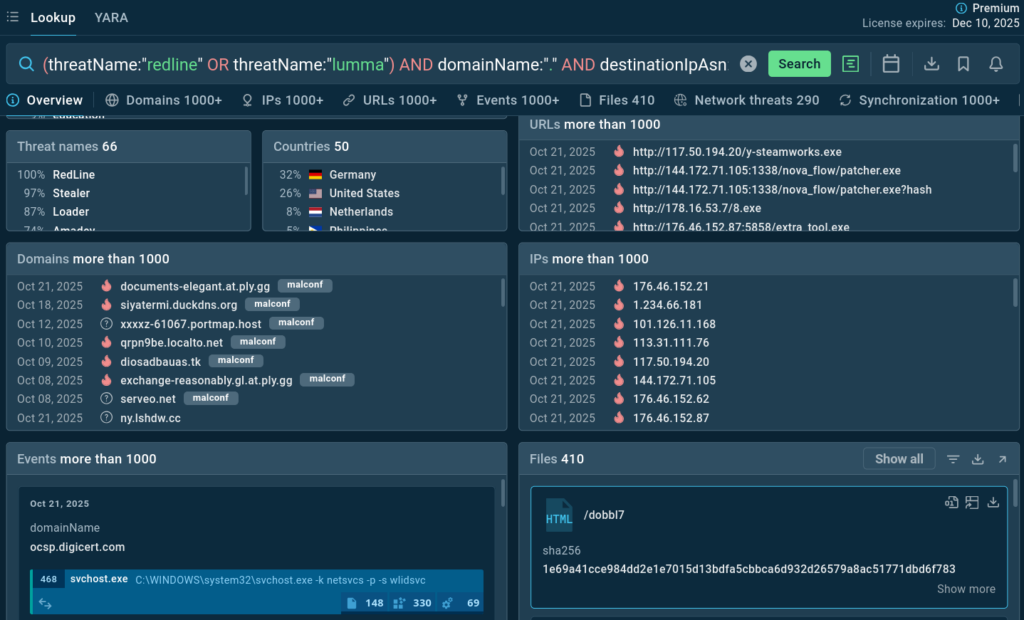
For example, certain malware families are known to use specific DGA-domains implementations. The following query targets these associations:
(threatName:”redline” OR threatName:”lumma”) AND domainName:”.” AND destinationIpAsn:”cloudflare”
Analyst Efficiency Background
With TI Lookup, teams unlock the next level:
- Faster Triage: Two-second access to millions of past analyses confirms if an IOC belongs to a threat, cutting triage time.
- Smarter Response: Indicator enrichment with behavioral context and TTPs guide precise containment strategies.
- Fewer Escalations: Tier 1 analysts can make decisions independently, reducing escalations to Tier 2.
Shared Knowledge, Unified Context
Lookup data can feed SIEMs or case systems, keeping the entire SOC aligned on the same intelligence. For native seamless integrations and connections to SIEM solutions try ANY.RUN’s Threat Intelligence Feeds.
Building Your Expert Triage Practice
Beyond tools and technology, developing expert triage skills requires deliberate practice and continuous improvement. Here are strategies to enhance your capabilities:
Develop Pattern Recognition
Over time, you’ll begin recognizing patterns in threats and false positives. Certain types of alerts consistently prove benign, while others frequently indicate genuine threats. Document these patterns and share them with your team to build collective knowledge. Keep TI Lookup at hand to check alerts in case you are not sure and calibrate your threat radar.
Create Decision Trees
For common alert types, develop decision trees that guide your triage process. It’ll reduce cognitive load, freeing mental resources for complex cases.
Maintain a Knowledge Base
Document your triage decisions, especially for ambiguous or challenging cases. Include the reasoning behind your decisions and the outcomes.
Continuous Learning
The threat landscape evolves constantly, requiring ongoing education. Dedicate time to reading threat intelligence reports, studying new attack techniques, and learning from post-incident reviews. This investment in knowledge pays dividends in improved triage accuracy.
Take Care of Yourself
Analyst fatigue is real and impacts your performance. Take regular breaks, maintain work-life balance, and don’t hesitate to ask for support when workload becomes overwhelming. Your long-term effectiveness depends on sustainability, not short-term heroics.
Conclusion: Mastering the Art and Science of Triage
Alert triage combines technical skills, analytical thinking, and sound judgment. As an analyst, you’re not just processing alerts. You’re making critical decisions that protect your organization from sophisticated threats while managing resource constraints and time pressure.
The challenges you face are significant: overwhelming alert volumes, persistent false positives, complex threats, and the ever-present risk of fatigue. However, by understanding these challenges and leveraging solutions like ANY.RUN’s Threat Intelligence Lookup, you can transform your triage practice from reactive firefighting to proactive threat hunting.
The future of security operations depends on analysts who can work both fast and smart. With the right approach, tools, and mindset, you can meet the challenges of modern threat detection while building a rewarding and sustainable career in cybersecurity.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our Interactive Sandbox simplifies malware analysis of threats that target both Windows, Linux, and Android systems.
Combined with Threat Intelligence Lookup and Feeds, businesses can expand threat coverage, speed up triage, and reduce security risks.
Request trial of ANY.RUN’s services to test them in your organization →
The post No Threats Left Behind: SOC Analyst’s Guide to Expert Triage appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

