ANY.RUN Sandbox & Microsoft Sentinel: Less Noise, More Speed for Your SOC
SOC teams may waste hours daily manually enriching alerts and switching between tools, delaying response. ANY.RUN’s Microsoft Sentinel Connector fixes this by introducing fast, accurate, and interactive sandbox analysis into Sentinel’s workflow, so alerts get auto-processed, enriched with IOCs, and prioritized in seconds.
Here’s how you can speed up response times, filter out false positives, and focus on real threats without leaving your existing workspace.
Maximize Your SOC’s Efficiency
ANY.RUN’s Interactive Sandbox is a cloud-based solution offering security teams immediate, real-time access to Windows, Linux, and Android virtual environments for investigating suspicious files and URLs.
With the Microsoft Sentinel connector, SOCs and MSSPs can automate triage and enrich alerts with actionable verdicts and IOCs to:
- Cut MTTR by up to 21 minutes per incident by eliminating manual steps and speeding up analysis.
- Boost threat detection by up to 36% thanks to ANY.RUN’s powerful capabilities to catch threats missed by standard security tools.
- Increase team productivity by up to 3x through automation to free up analysts for high-value tasks.
- Reduce alert overload, filtering false positives and prioritizing high-risk incidents.
- Detect and respond to attacks early with clear, actionable threat insights.
- Save resources and optimize costs by using your existing MS Sentinel setup without extra infrastructure expenses.
To expand threat coverage further, security teams can also utilize ANY.RUN’s Threat Intelligence Feeds connector for Microsoft Sentinel.
It supplies a continuous stream of fresh, actionable IOCs extracted from attack data across 15K SOCs around the world straight to your Microsoft Sentinel environment, helping you proactively detect the latest malware active right now.
How ANY.RUN’s Sandbox Improves Microsoft Sentinel Workflows
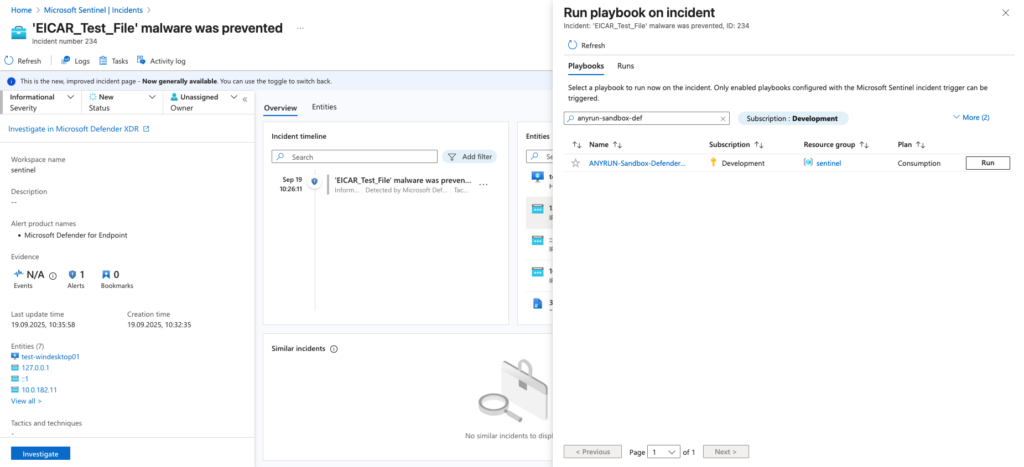
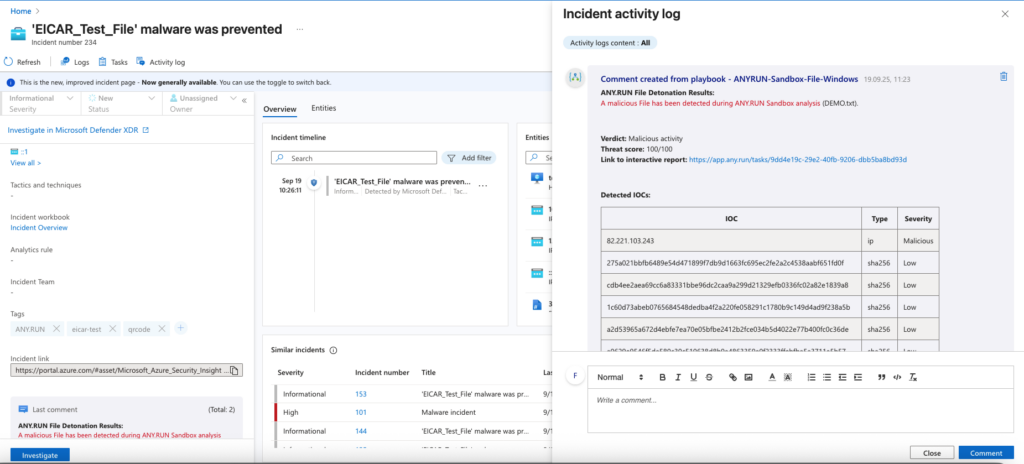
With the connector, SOC teams can analyze files and links right from Sentinel alerts: either with one click or automatically. You’ll instantly get the verdict, risk score, IOCs, and a link to the full analysis, while Sentinel’s threat database updates automatically.
All analyses via the connector are launched in the Automated Interactivity mode. This means the sandbox will automatically perform the investigation, including by clicking links, opening files, and launching payloads on its own to ensure full attack detonation.
As a result, security teams can:
- Automate alert enrichment by getting verdicts and IOCs to assess incidents quickly.
- Speed up and simplify triage with one-click analyses of files/attachments/links without the need for manual uploads or switching tools.
- Prioritize threats automatically by checking incidents’ severity for faster decision-making.
- Extract IOCs effortlessly, pulling IPs, domains, and hashes into Sentinel’s Threat Intelligence.
- Respond to incidents faster thanks to ready-made analysis results and reports enabling quicker containment and remediation.
How to Set Up Malware Sandbox Connector for Microsoft Sentinel
Follow the official instruction to connect ANY.RUN’s Interactive Sandbox with your Microsoft Sentinel workspace.
Please note that you need an API Key for it to work. To receive your key, please reach out to your account manager or request a demo access as part of the 14-day trial.
About ANY.RUN
Trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and other critical industries, ANY.RUN helps security teams investigate threats faster and with greater accuracy.
Our Interactive Sandbox accelerates incident response by allowing you to analyze suspicious files in real time, watch behavior as it unfolds, and make confident, well-informed decisions.
Our Threat Intelligence Lookup and Threat Intelligence Feeds strengthen detection by providing the context your team needs to anticipate and stop today’s most advanced attacks.
Ready to see the difference?
Start your 14-day trial of ANY.RUN today →
The post ANY.RUN Sandbox & Microsoft Sentinel: Less Noise, More Speed for Your SOC appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
