Fighting Telecom Cyberattacks: Investigating a Campaign Against UK Companies
Telecommunications companies are the digital arteries of modern civilization. Compromise a major telecom operator, and you don’t just steal data — you gain the power to intercept communications, manipulate network traffic, and bring entire regions offline.
Every day, ANY.RUN’s solutions process thousands of threat samples, and hidden within them are patterns of activity targeting telecom operators. Some are opportunistic, others are advanced and carefully orchestrated.
In this report, we’ll walk through real-world attacks where threat actors weaponized telecom brand trust to launch attacks. We’ll also show how analysts can detect these threats, extract indicators of compromise (IOCs), and strengthen defenses.
Key Takeaways
- Telecommunications under siege: The telecom sector faced sustained growth in malicious activity from May-July 2025, with 56% of observed APT campaigns targeting telecom and media companies.
- Brand impersonation is weaponized trust: Attackers systematically abuse telecom brand recognition, using familiar logos, official-looking domains, and corporate communication styles to bypass human skepticism and technical filters.
- Pattern recognition defeats mass campaigns: Simple YARA rules can expose large-scale operations.
- Tycoon2FA phishing kit remains active: The phishing framework designed to steal Microsoft credentials and bypass two-factor authentication is a critical concern for enterprise telecom environments.
- Interactive Sandbox reveals multi-stage attack progression: ANY.RUN’s Interactive Sandbox captured the complete attack flow from the initial PDF attachment to the final phishing page. This real-time analysis exposed the redirection chain from legitimate-looking emails to DGA-generated domains (xjrsel.ywnhwmard[.]es), enabling early detection before credentials could be harvested.
- Proactive hunting scales defense: Combining YARA Search with Threat Intelligence Lookup transforms reactive incident response into proactive threat hunting, enabling security teams to build comprehensive defense before attacks succeed.
Recent Telecom Attack Dynamics
Attacks on communication operators can disrupt critical services, lead to leaks of confidential information, and be used as a springboard for large-scale cyber espionage operations.
According to Cyfirma, telecommunications and media industry were targeted in 9 out of 16 observed APT campaigns in May–July 2025, accounting for 56% of all cases. The peak activity occurred in May, followed by a slight decline in June and a renewed increase in July.
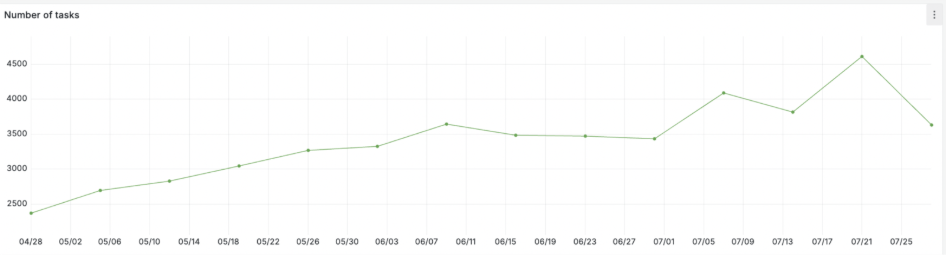
We at ANY.RUN have observed a steady increase in telecom-targeting attacks in May–July 2025. The Sandbox data shows a smoother continuous growth, reaching a maximum in July. This reflects the constant pressure of mass attacks.
In our Threat Intelligence Reports highlighting the activity of top APT groups, we also see an increased targeting of media and telecom campaigns in the recent attacks.
Analysis of Threats Targeting a Major Telecom Holding
Let’s take the perspective of an information security specialist at a huge British telecommunications holding company operating in approximately 180 countries and providing fixed-line, broadband internet, mobile communications, and pay-TV services.
Our goal is to determine how attackers spread malware, which families they use, which indicators can be collected, and the frequency, dynamics, and technical details of the attacks.

We will start with Threat Intelligence Lookup, which allows SOC teams to navigate a database of live attack data from 15,0000 organizations. Using TI Lookup’s YARA Search, we can create a simple rule to find all emails uploaded into the sandbox where the recipient field contains the holding’s domain. This allows us to identify malicious attachments and links aimed at its employees.
As a result of executing the YARA rule, dozens of files were discovered containing addresses with the corporation’s domain in the recipient field. Each of these files was linked to one or more analyses in ANY.RUN’s Sandbox, which also featured this domain, confirming the presence of potentially significant malicious activity directed at company employees.
ANY.RUN’s Interactive Sandbox allows security analysts to safely execute suspicious files and observe their behavior in real-time, capturing network communications, file modifications, and malicious redirections before they can impact production systems. This controlled environment reveals attack chains from initial email delivery through credential harvesting attempts.
Let us analyze one of the found emails.
View sandbox analysis of the malicious email

A Phishing Message Through a SOC Analyst Lens
On July 9, 2025, an email addressed to giova[xx.xx]stantini@[thedomain dot]com was uploaded to ANY.RUN. The sender was listed as Bt_Bt_xu86@ksi.com.pk with the display name “DocSgn.” The domain ksi[.]com[.]pk belongs to Khatib Sons International, a Pakistani metal company, and has no relation to the email content. Coupled with the “DocSgn” branding, this impersonated a well-known electronic document signature service to trick the recipient.
View sandbox analysis of the email

The subject line — “Re: Re: Completed: For Sales contract (h4nc)” — mimicked an ongoing conversation, a common social engineering tactic to reduce suspicion.
The email contained a PDF attachment and a form with a “Review and Sign” button in the body, luring the recipient to view and sign a supposed document.
Additionally, at least five similar emails were detected targeting other employees, with generic content not tailored to specific recipients — indicating a mass campaign.

Clicking the “Review and Sign” button redirected the user to a fake Microsoft login page hosted on xjrsel.ywnhwmard[.]es, a domain resembling a DGA-generated address, a common indicator of phishing or malicious resources.
This threat was identified as the Tycoon2FA phishing kit, known for spoofing Microsoft login pages and harvesting credentials.
Network-Level Detection
Suricata rules triggered on network activity associated with the Tycoon2FA kit. The alerts provided details such as MITRE ATT&CK technique T1566 (Phishing), the suspicious DGA-like domain, and connection metadata.

That’s exactly how ANY.RUN’s solutions help detect threats early, exposing phishing attempts before they do damage.
Searching for Similar Threats Targeting UK Companies
Using ANY.RUN’s Threat Intelligence Lookup, we’ve searched for samples uploaded from the UK containing the same PDF attachment. The query returned about 40 sandbox analyses, mostly from July 2025, including emails targeting a number of UK companies.
sha256:”689cdb319d8cae155516d9f8ddfbd0c99de048252e84f529e0ccc538523a5eba” and submissionCountry:”GB”

We’ve also identified repeating sender address patterns across multiple phishing emails, indicating automated mass distribution.
Sorting Out Emails with Specific Sender Pattern
Many malicious emails sent to telecom companies have fixed patterns for forming sender addresses in the From field. The structure looks as follows:
“._*” <*_*_*@*.com>
The display name usually began with “._” followed by a word in capital letters. The email address repeated a word twice, separated by underscores, followed by random characters before the @, and ending in .com.

This structure strongly suggests automated mass phishing.

Such a pattern is highly likely created automatically for mass mailings, so it can be used as a basis for a filtering rule that blocks similar emails.
A YARA rule was created to detect such emails in ANY.RUN’s database of malware samples. The rule revealed 16 files with the sender pattern, linked to multiple sandbox analyses. From these, we can extract senders’ addresses, email and attachment hashes, URLs, phishing domains, IPs, subjects, and other indicators.

This data allows analysts to assess the relevance of the threat, determine its timeframe and target organizations and countries. Based on this, you can prioritize this threat for your company and add indicators to the detection and response systems.
Tracking Telecom Impersonation Attacks
Let’s build a threat landscape where attackers use domains containing the element “telecom” in their names. We are interested in cases where such activity is classified as phishing to assess the scale, frequency, and targets of these attacks.
The search returned 86 analysis sessions, 70 related domains, and enriched context data such as headers, attachments, network artifacts, timelines, and submission geographies.
domainName:”telecom” AND threatName:”phishing” and threatLevel:”malicious”

These insights allow security teams to enrich TI sources, prioritize threats, identify campaign clusters, track temporal dynamics, update detection rules, and map related infrastructure.
How ANY.RUN Helps Telecom Companies Withstand the Growing Pressure of Phishing Attacks
Telecom companies are under constant fire from phishing campaigns that combine brand impersonation, malicious attachments, and fake domains. While attackers automate and scale their operations, security teams often struggle to keep up. ANY.RUN’s ecosystem of services provides telecom defenders with the tools to detect, investigate, and respond to these threats more effectively:
Interactive Sandbox

Quickly detonate suspicious emails, attachments, or links in a safe, interactive environment. Observe behavior in real time, identify phishing kits like Tycoon2FA, and capture artifacts such as malicious redirects, domains, or dropped files.
Threat Intelligence Feeds

Get continuously updated, actionable indicators of compromise (IOCs) drawn from global malware submissions. Telecom SOCs can integrate Threat Intelligence Feeds directly into SIEM or EDR systems to block known phishing infrastructure before it reaches employees or customers.
Threat Intelligence Lookup

Go beyond single-sample analysis by exploring related campaigns. With Threat Intelligence Lookup, analysts can pivot on domains, file hashes, or sender patterns to uncover broader phishing clusters targeting telecom brands. This makes it easier to map attacker infrastructure, understand campaign scope, and strengthen detection rules.
By combining these services, telecom companies gain both the depth to analyze individual phishing attempts and the breadth to track large-scale campaigns. This layered approach enables faster detection, better prioritization, and ultimately stronger resilience against persistent phishing pressure.
Conclusion
The analysis confirms that phishing attacks against telecom companies’ employees remain highly relevant, often used to steal credentials and bypass 2FA.
ANY.RUN’s TI Lookup and YARA Search allow analysts to research the attacks and the employed malware, find samples linked to a targeted company’s email addresses, and expose domains utilized for phishing. Security teams are able to gather valuable indicators (hashes, domains, IPs, headers) to enrich internal threat intelligence sources.
Pattern-based detection methods tailored to telecom-sector targeting can help identify new campaigns faster and reduce organizational risk.
About ANY.RUN
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN. Our services streamline malware and phishing investigations for organizations worldwide.
- Speed up triage and response: Detonate suspicious files using ANY.RUN’s Interactive Sandbox to observe malicious behavior in real time and collect insights for faster and more confident security decisions.
- Improve threat detection: ANY.RUN’s Threat Intelligence Lookup and TI Feeds provide actionable insights into cyber attacks, improving detection and deepening understanding of evolving threats.
Start 14-day trial of ANY.RUN’s solutions in your SOC today
The post Fighting Telecom Cyberattacks: Investigating a Campaign Against UK Companies appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

