How to Enrich IOCs with Actionable Threat Context: Tips for SOC Analysts
One solution can change everything. ANY.RUN’s Threat Intelligence Lookup is living proof of that.
By delivering a browsable source of threat data, it helps your SOC overcome challenges that have to be faced in order to reach higher detection rates and make smarter security decisions.
Find details on how to make the most of TI Lookup below.
Threat Intelligence Lookup: Context for Fatigue-Free Investigations
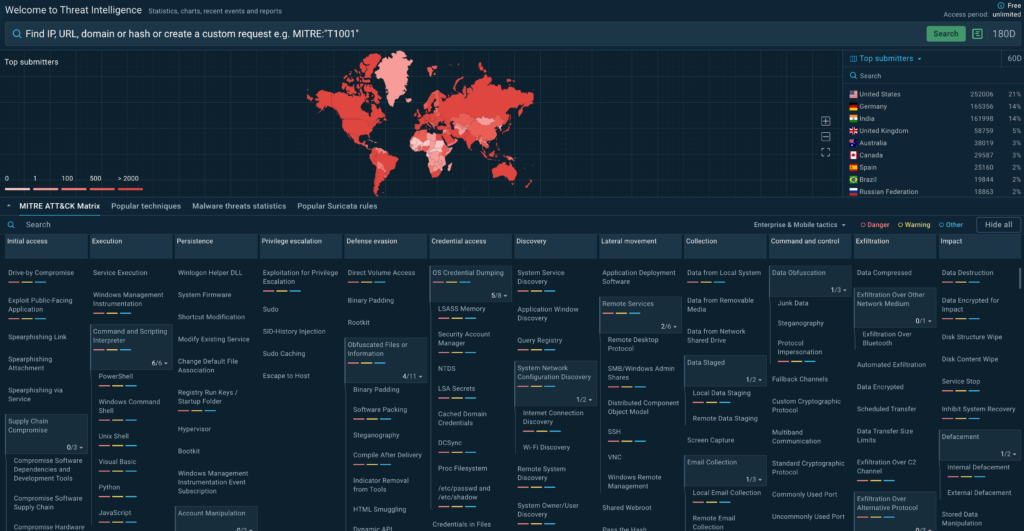
ANY.RUN develops essential solutions for SOCs, such as Threat Intelligence Lookup—a searchable database of threat data. Its goal is to bridge the threat intelligence gap for malware analysts by enriching indicators with actionable context.
TI Lookup makes it possible by providing swift access to data collected from millions of malware analyses done in ANY.RUN sandbox by experts who work for 15,000 companies all over the world. This lets you add context to your indicators and tap into this fresh, actionable data on attacks that just happened. The best part is—it’s available at no cost.
The free version of TI Lookup gives you access to 20 most recent sandbox analyses per query, unlocks key search fields (file hashes, URLs, domains, IPs, MITRE ATT&CK techniques, Suricata IDs, etc.), and makes it possible to create compound searches.
For free, you can achieve:
- Enriched Threat Investigations: Gain deeper insight into threats by connecting existing artifacts with real-world attacks.
- Accelerated Response: Reduce MTTR by quickly understanding threat behavior, objectives, and targets through sandbox analysis.
- Stronger Proactive Defense: Gather intelligence on emerging threats to act before they cause damage.
- Enhanced Team Expertise: Empower SOC analysts to study real-world attacks and adversary TTPs in live malware using the interactive MITRE ATT&CK matrix.
- Improved Detection Rules: Leverage intelligence from TI Lookup to refine SIEM, IDS/IPS, and EDR rules for stronger proactive defense.
Use Cases of TI Lookup’s Free Version
Register in TI Lookup for free, and you’ll be able to access actionable threat insights right away. Apply them in scenarios like these:
Enriching Network Indicators with Context
A practical example: you need to verify a domain to see if it’s tied to any malicious activities, and if yes, gain more info on it.
Enter it into TI Lookup and you’ll instantly see the result. The following domain, for instance, turned out to be malicious:
domainName: “technologyenterdo.shop”
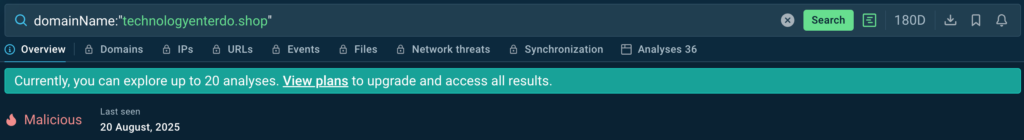
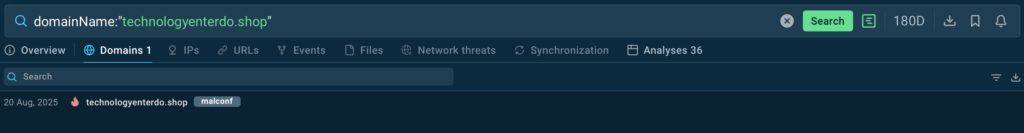
With a free plan, you can access up to 20 recent analysis sessions that involve it to enrich the indicator with reliable context. In addition to domains, the same can be done for IPs and URLs, also for free.
TI Lookup’s Premium plan would allow you to see even more information. For example, the fact that domain above is labeled with a “malconf” tag. This means that it was retrieved from the very heart of a malicious sample—malware configuration—by ANY.RUN’s experts. Indicators from configs offer trustworthy, valuable insights into the malware’s behavior and impact.
Exploring New Threat Samples
Since around 73% of attacks start with phishing, SOC teams should stay on the lookout for fresh threat samples that can potentially harm your company. One thing you can do is to monitor current TTPs in TI Lookup.
To narrow down your search, you can keep track of threats submitted by analysts from your country. For example, the following query will help you browse Tycoon threats detected in Germany:
threatName:”tycoon” AND submissionCountry:”de”
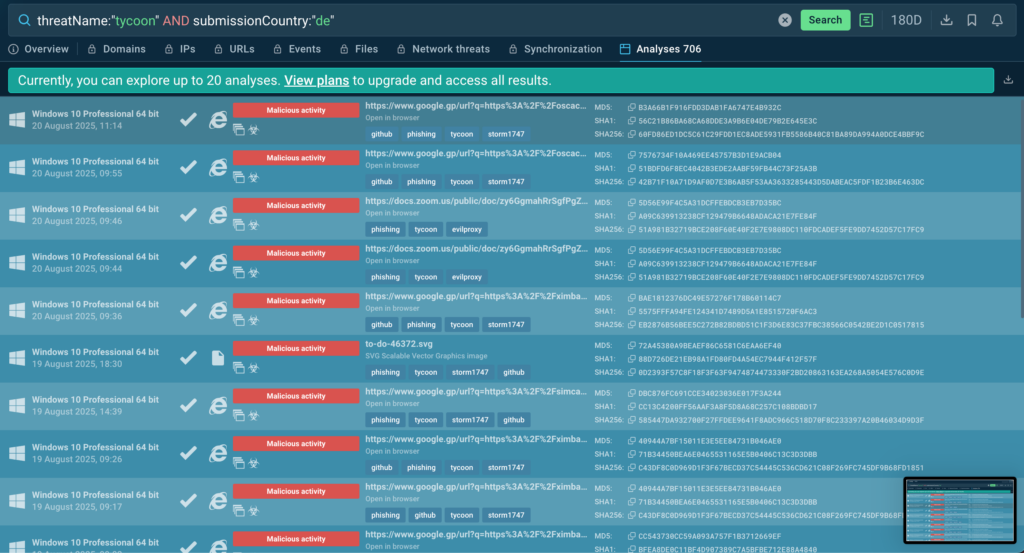
From there, you can collect indicators from search results and create or update your detection rules in order to stay ahead of potential threats.
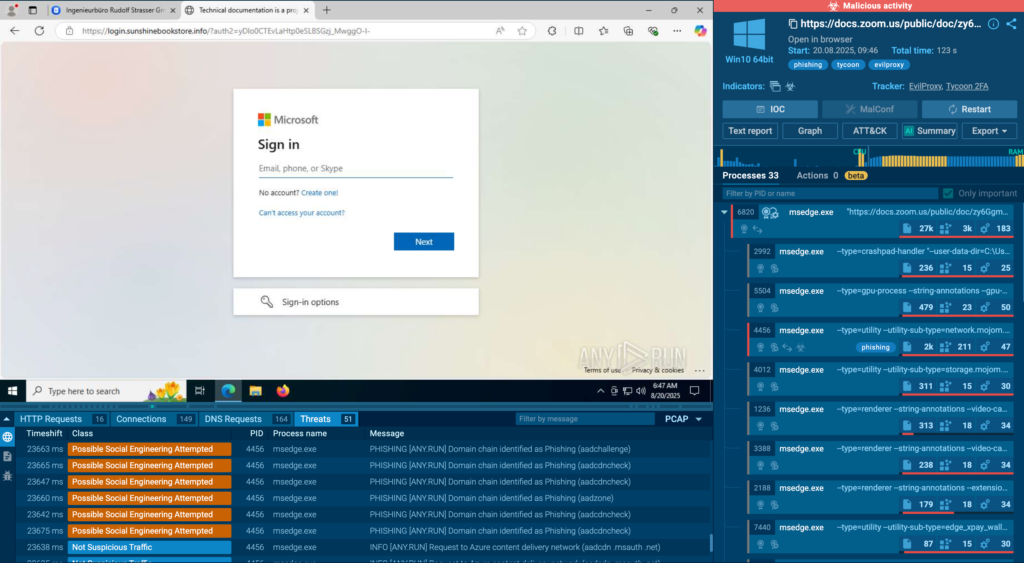
Checking File Hashes
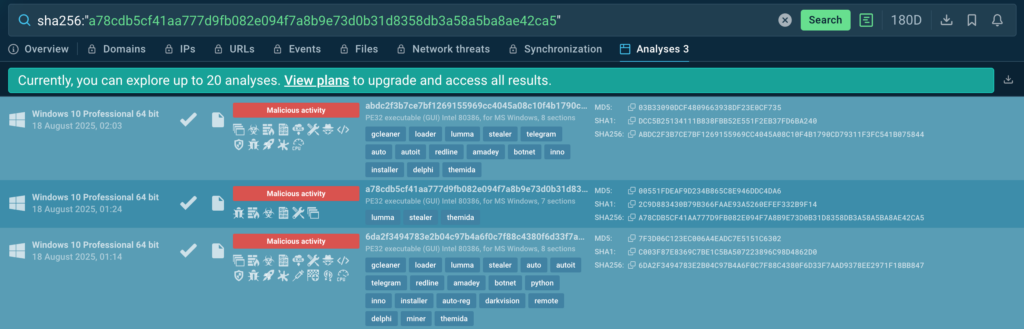
Another essential use case of TI Lookup is performing a quick check for an indicator. Let’s see if this hash is connected to any threats:
sha256:”a78cdb5cf41aa777d9fb082e094f7a8b9e73d0b31d8358db3a58a5ba8ae42ca5″
The verdict: it’s associated with Lumma. One simple query, and you’ve received trustworthy result based on actual threat investigations by other analysts.
Tracking Threats by TTPs
ANY.RUN also provides access to the interactive MITRE ATT&CK matrix that shows you real-world examples of threats active today. With it, you can learn about different TTPs recently used by threat actors and see how they look in action via ANY.RUN’s Interactive Sandbox.
For that, go to TI Lookup and click any TTP to dig deeper. For example, here are some of the results for T1068: Exploitation for Privilege Escalation:
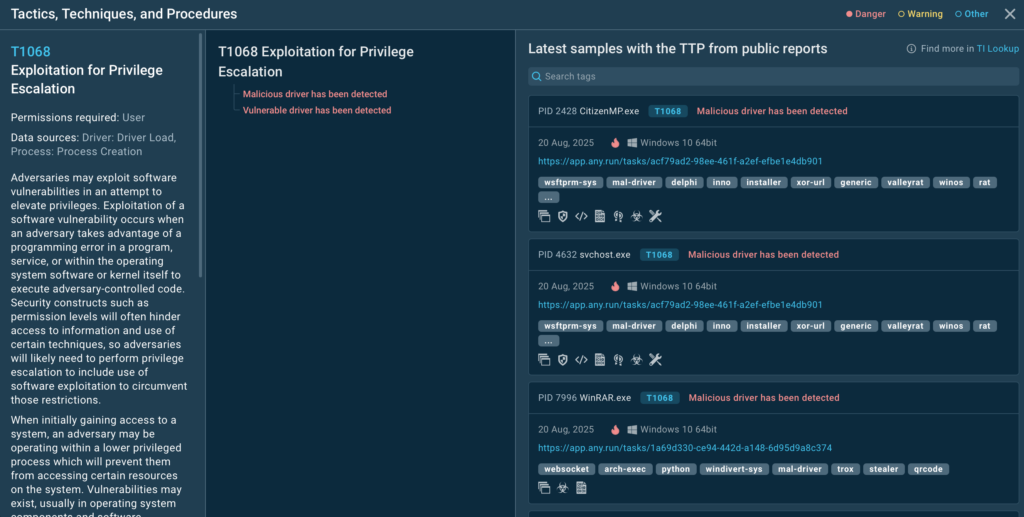
You see the description for this TTP and links to malicious samples that involve it. Click any analysis session to see the full detonation and retrieve indicators.
Transforming Your SOC for Proactive Security
TI Lookup’s free version gives you more than just a glimpse into threat intelligence. As we’ve shown above, it can be a powerful solution to a number of SOC challenges.
The Premium plan, however, gives you even more. It’s an enterprise-grade product, helping businesses across infrastructures:
- Speed Up and Automate Detection: Correlate alerts against a vast database of IOCs, IOBs, and IOAs, and integrate TI Lookup with your SIEM, TIP, or SOAR systems for real-time monitoring.
- Hunt and Investigate with Depth and Precision: Create and search custom YARA rules in ANY.RUN’s database and refine investigations with 40+ parameters and advanced operators.
- Stay Proactive and Informed: Set automated alerts for specific IOCs or patterns, and leverage TI Reports from expert analysts to track evolving malware trends across industries.
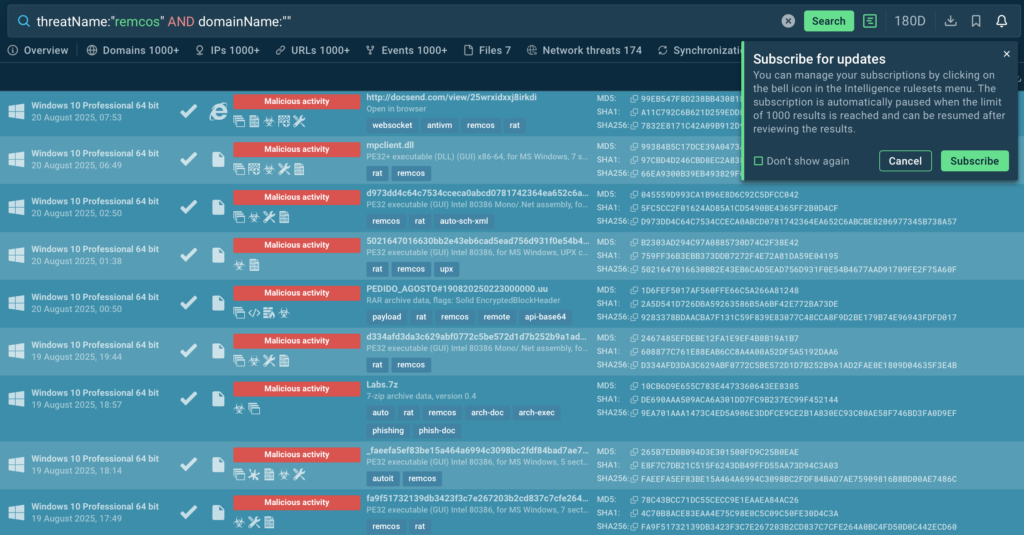
Among Premium features are Query Updates. They automate the process of indicator enrichment by keeping you subscribed to threats and indicators of interest. Enter any query, such as:
threatName:”remcos” AND domainName:””
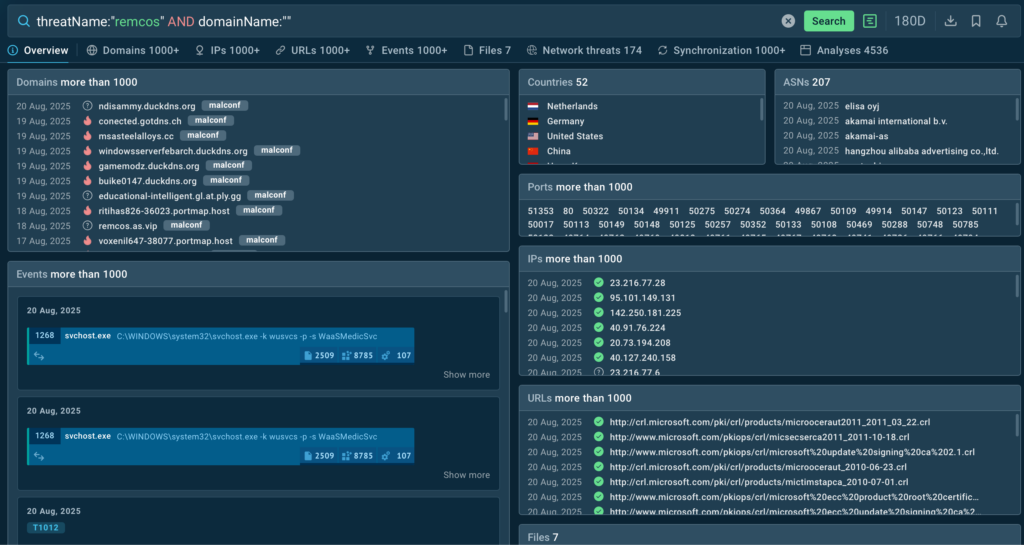
Click the bell icon, and you’ll start receiving fresh data on new samples that fit your query. As you can see, there are plenty:
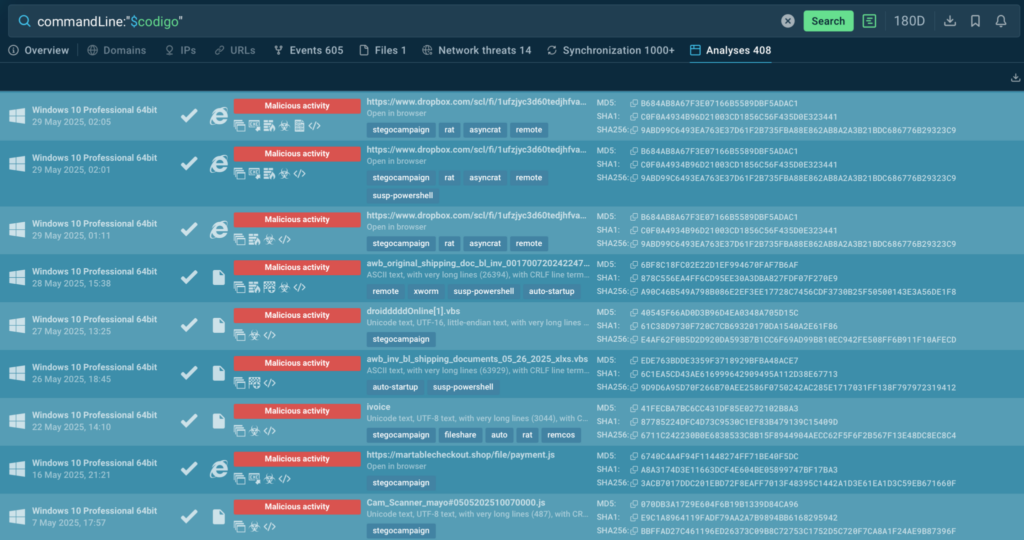
Another way to deepen your investigation is to browse Indicators of Behavior (IOBs). This allows you to research attacks using minor artefacts like a suspicious fragment of a command line. Type it in like so:
As a result, you’ll find out that this command line is actually related to AsyncRAT’s steganography attacks:
About ANY.RUN
Trusted by more than 500,000 security professionals and 15,000+ organizations across industries like finance, healthcare, and manufacturing, ANY.RUN empowers teams to investigate malware and phishing threats with speed and accuracy.
With ANY.RUN’s Interactive Sandbox, you can safely analyze suspicious files and URLs, observe live behavior, and extract key insights to dramatically reduce triage and decision-making time.
Tap into Threat Intelligence Lookup and TI Feeds to uncover IOCs, attacker tactics, and behavioral patterns linked to real-world threats for staying one step ahead of evolving attacks.
Experience ANY.RUN’s solutions firsthand to enhance your SOC workflow via a trial period
The post How to Enrich IOCs with Actionable Threat Context: Tips for SOC Analysts appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
