ANY.RUN & Microsoft Sentinel: Catch Emerging Threats with Real-Time Threat Intelligence
ANY.RUN now delivers Threat Intelligence (TI) Feeds directly to Microsoft Sentinel via the built-in STIX/TAXII connector. No complicated setups. No custom scripts. Only high-quality indicators of compromise (IOCs) to fortify your SOC and catch attacks early, keeping your business secure.
About the TI Feeds Connector for Microsoft Sentinel
ANY.RUN’s TI Feeds support a seamless, out-of-the-box connection to Microsoft Sentinel that delivers real-time threat intelligence directly into your workspace.
- Effortless Setup: Connect TI Feeds to Sentinel using the STIX/TAXII connector with your custom API key.
- Enhanced Automation: Sentinel’s playbooks, powered by Azure Logic Apps, automatically correlate IOCs with your logs, triggering alerts or actions like blocking IPs. This cuts manual work and speeds up response times.
- Cost Efficiency: Leverage your existing Sentinel setup without extra infrastructure costs. Fewer missed threats, thanks to high-fidelity IOCs, reduce the financial impact of breaches.
The IOCs enriched with links to sandbox sessions can be used in Sentinel’s analytics, letting you build custom rules, visualize threats, and prioritize incidents effectively.
What Makes ANY.RUN’s Threat Intelligence Feeds Unique
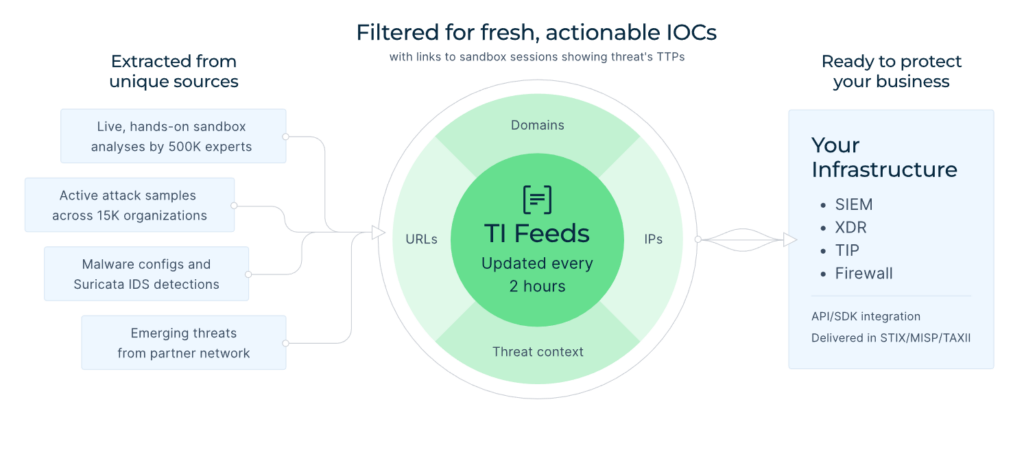
ANY.RUN’s TI Feeds deliver malicious IPs, domains, URLs that have been active for just hours, not days. We extract them from live sandbox analyses of the latest threats hitting 15,000+ organizations worldwide. Unlike post-incident reports that lag behind, our feeds update every two hours, sending active attack indicators straight to clients. This lets MSSPs and SOCs detect today’s threats early and effectively, keeping systems secure.
- Fresh Data: IOCs update every 2 hours from live attack detonations in ANY.RUN’s Interactive Sandbox.
- Rich Context: Each IOC links to sandbox sessions with full TTPs for deeper investigations.
- Low Noise: Pre-processing by expert analysts ensure near-zero false positives, saving your team time.
- Flexible Integration: Thanks to API, SDK, STIX/TAXII support, TI Feeds work seamlessly with SIEM/XDR/firewalls and other solutions.
How TI Feeds Help SOCs and MSSPs Spot Attacks in Time
Threats move fast. Malware and phishing can slip through if you’re not ready. ANY.RUN TI Feeds give SOCs and MSSPs the edge to detect and stop attacks before they impact. Our high-fidelity IOCs — IPs, domains, URLs — come enriched with context from ANY.RUN’s Interactive Sandbox, ensuring you act with precision.
- Catch Threats Early: Real-time IOCs enable preventive actions and rapid response to minimize damage.
- Boost Detection Rate: Near-zero false positives and pre-processing help ensure that your SOC never misses a threat.
- Lower Costs and Risks: Fewer undetected threats mean reduced financial and operational fallout. Fresh, reliable IOCs help you avoid costly breaches.
- Cut MTTR: Faster alert triage and a complete threat visibility thanks to linked sandbox analyses informs responders’ actions, helping them prevent threat spread and reduce damage.
- Improve SOC Performance: Automate threat processing, cutting manual tasks for SOC specialists and letting them prioritize top risks.
Receive Threat Intelligence Feeds in Microsoft Sentinel
Here is a detailed manual to guide your TI Feeds setup in Microsoft Sentinel. Should you need any assistance or have any questions, feel free to contact us.
Connecting to the STIX/TAXII server
- Open MS Sentinel and go to the Data connectors tab in the Configuration section.
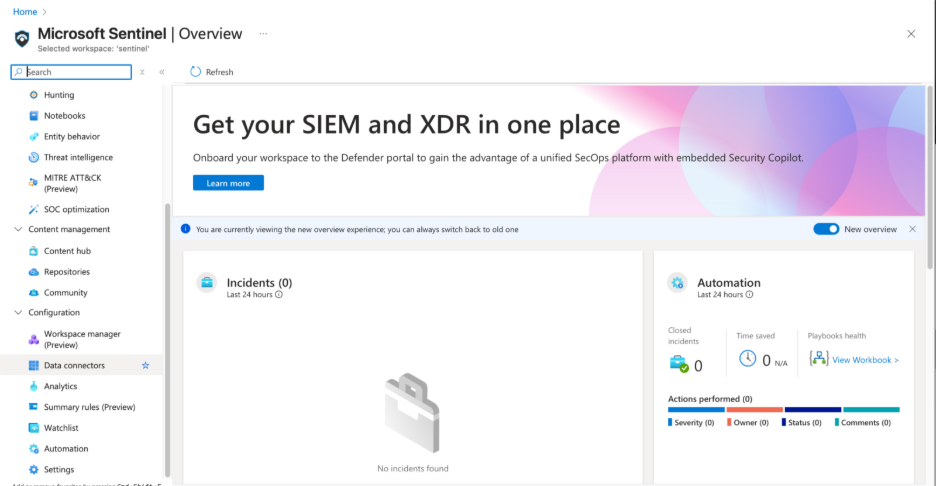
2. Search for the Threat Intelligence STIX/TAXII connector and click Open connector page.
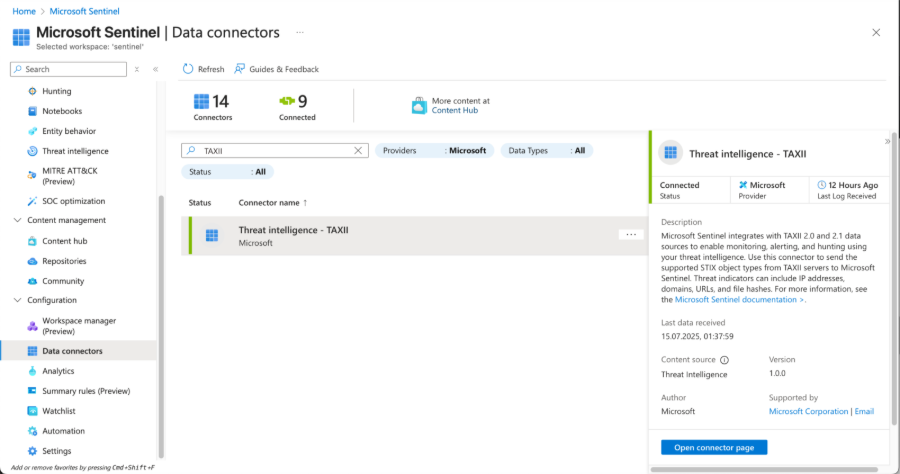
3. You will see the list of prerequisites for the connector to work. If you lack any of them, view this documentation by Microsoft.
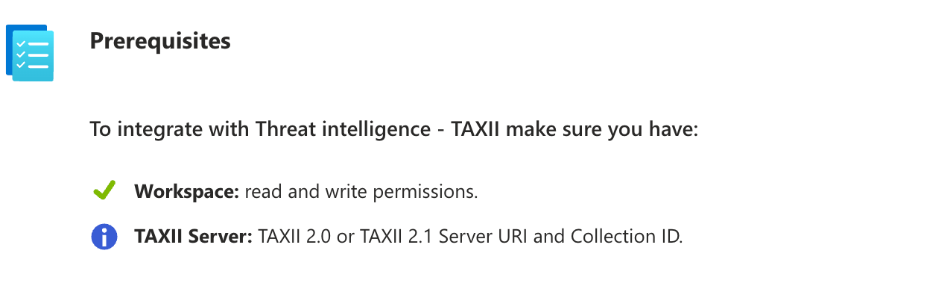
4. Fill out the Configuration form:
- Name the server via the Friendly name field
- Insert API root URL:
- Choose a Collection ID:
| Name | Description | ID |
|---|---|---|
| All indicators | Contains IOCs of all formats (IPs, Domains, URLs) | 3dce855a-c044-5d49-9334-533c24678c5a |
| IPs collection | Contains only IPs | 55cda200-e261-5908-b910-f0e18909ef3d |
| Domains collection | Contains only Domains | 2e0aa90a-5526-5a43-84ad-3db6f4549a09 |
| URLs collection | Contains only URLs | 05bfa343-e79f-57ec-8677-3122ca33d352 |
- Enter your Username and Password.
If you don’t have these credentials, contact your account manager at ANY.RUN or fill out this form.
You can also choose to import all available indicators or those that are one day, week, or month old via the field Import indicators. Another optional setting is Polling frequency that determines how often you’d like to connect to the STIX/TAXII server to retrieve new feeds: once a minute, once an hour, or once a day.
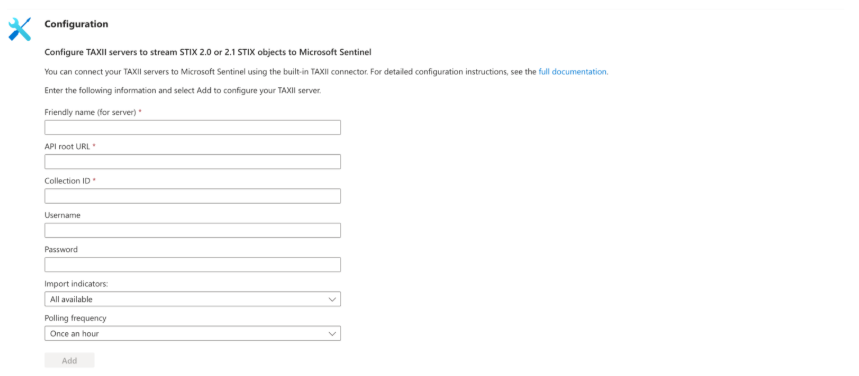
Finally, click Add, and you’re all set up.
If you need more information, see STIX/TAXII documentation by ANY.RUN.
Browsing indicators
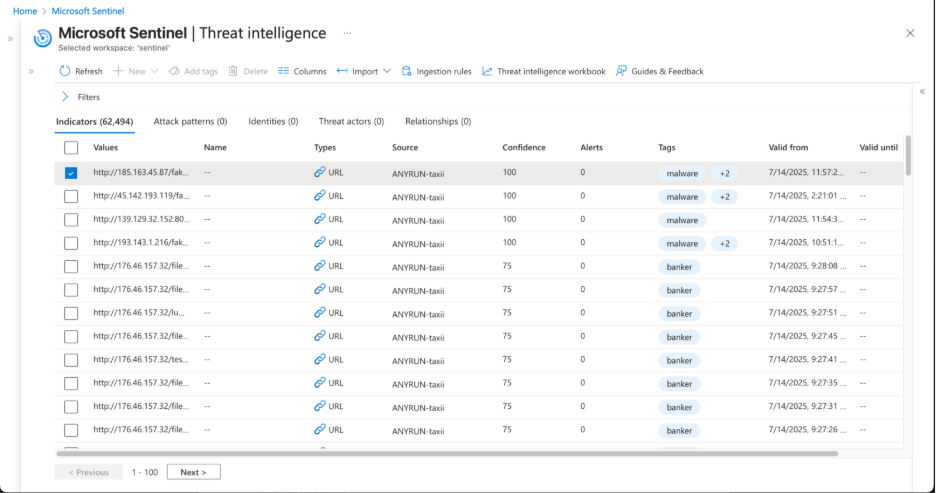
To access the indicators you’ve retrieved, go to the Threat intelligence tab.
You’ll find a table with fields describing each indicator:
- Values – indicator itself;
- Names – name of an indicator;
- Types – type of an indicator (IP, URL, or Domain);
- Sources – source of an indicator;
- Confidence – this rate determines our level of certainty on whether an indicator is malicious (50 – suspicious, 75 – likely malicious, 100 – malicious);
- Alerts – number of alerts related to an indicator;
- Tags – descriptors of an indicator;
- Valid from and Valid until – time period during which an indicator is considered valid.
Real-World Application Scenario
Here’s a typical flow your security operations can adopt:
1. Feed Setup: Your security team configures IOC ingestion from ANY.RUN into Microsoft Sentinel, where data is indexed and becomes searchable.
2. Automated Correlation: Sentinel continuously analyzes incoming logs from EDR systems, network equipment, proxies, email security, and other sources, automatically correlating them with ANY.RUN’s IOCs.
3. Alert Generation: When matches are detected (IP addresses, domains, file hashes), Sentinel creates security events and alerts.
4. Streamlined Triage: Alerts are routed to analysts for manual or semi-automated incident analysis, including log review, event correlation, and behavioral analysis.
5. Rapid Response: Depending on your configuration, the system can execute manual or automated responses including isolation, blocking, or escalation procedures.
How TI Feeds in MS Sentinel Boost SOC & MSSP Performance
Plug ANY.RUN’s feeds into Microsoft Sentinel with minimal setup, leveraging existing infrastructure, and benefit from:
- Faster Threat Detection: Fresh IOCs flow into your system quickly, accelerating identification of threats.
- Seamless Interoperability: No need to overhaul processes or tools — TI feeds work within your Sentinel environment.
- Enhanced Monitoring and Triage Capabilities: Expand your threat detection coverage with high-confidence indicators that improve both monitoring effectiveness and incident triage accuracy.
- Access to Unique Data: Gain insights from real-time analysis of attacks on 15,000 organizations, powered by ANY.RUN’s Interactive Sandbox.
- Cost Efficiency: Reduce setup costs by using a seamless STIX/TAXII connector.
- Process Continuity: Maintain existing workflows without disruption.
- Automation and Reduced Workload: Automate actions based on IOCs (e.g., flagging logs, isolating endpoints), freeing up SOC resources.
- Competitive Edge for MSSPs: Stand out with exclusive IOCs derived from cutting-edge research, enhancing your service offerings.
About ANY.RUN
ANY.RUN is trusted by more than 500,000 cybersecurity professionals and 15,000+ organizations across finance, healthcare, manufacturing, and other critical industries. Our platform helps security teams investigate threats faster and with more clarity.
Speed up incident response with our Interactive Sandbox: analyze suspicious files in real time, observe behavior as it unfolds, and make faster, more informed decisions.
Strengthen detection with Threat Intelligence Lookup and TI Feeds: give your team the context they need to stay ahead of today’s most advanced threats.
Want to see it in action? Start your 14-day trial of ANY.RUN today →
The post ANY.RUN & Microsoft Sentinel: Catch Emerging Threats with Real-Time Threat Intelligence appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

