How to Maintain Fast and Fatigue-Free Alert Triage with Threat Intelligence
Alert triage as one of the critical SOC and MSSP workflows implies evaluating, prioritizing, and categorizing security alerts to determine which threats require immediate attention and which can be safely dismissed or handled through automated processes.
Efficient alert triage, supported by robust threat intelligence, ensures that organizations stay ahead of adversaries while maintaining analyst productivity and morale. We shall see how it works on the example of ANY.RUN’s Threat Intelligence Lookup.
Why Triage is the Key to Efficiency
For SOCs, triage ensures that internal teams focus on high-priority incidents that could compromise critical systems or data. MSSPs, managing multiple clients, rely on triage to allocate resources efficiently across diverse environments, ensuring timely responses tailored to each client’s needs.
The triage process acts as the gateway between detection and action — the critical juncture where security alerts either trigger appropriate defensive measures or fade into background noise.
Challenges and Problems of Alert Triage
Alert triage is fraught with challenges that compromise its effectiveness in many organizations.
- Alert Overload: Modern SOCs generate thousands to millions of alerts daily from tools like SIEMs, EDRs, and network monitoring systems. Analysts can only investigate a fraction of these, leading to potential oversight of critical threats.
- False Positives: Many alerts are benign or irrelevant, consuming valuable time and resources.
- Lack of Context: Alerts often require analysts to manually gather data from disparate sources, slowing down investigations and increasing the risk of errors.
- Resource Constraints: Limited staffing and budget constraints stretch SOC teams thin, making it difficult to handle high alert volumes efficiently; the same goes for MSSPs managing multiple clients.
- Evolving Threats: The complexity and variety of modern cyberattacks demand constant adaptation, challenging analysts to stay ahead with limited tools and time.
These obstacles create inefficiencies, delay responses, and increase organizational risk.
Speed as a Critical Key Performance Indicator
Speed in alert triage, measured by metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), is a critical KPI for SOCs and MSSPs. Rapid triage minimizes the window of opportunity for attackers, reducing potential damage from breaches, data loss, or system downtime. For businesses, fast triage aligns with key objectives:
- Minimizing Financial Impact
- Protecting Customer Trust
- Operational Continuity
- Regulatory Compliance
Organizations with efficient triage processes can handle larger volumes of security data without proportionally increasing staff, improving operational efficiency and ROI on security investments.
Analyst Fatigue: The Hidden Threat to Security Effectiveness
Analyst fatigue occurs when security professionals become mentally and emotionally exhausted from processing endless streams of alerts, many of which prove to be false positives or low-priority events.
Cognitive overload increases when analysts must process more information than their mental capacity allows, leading to lower accuracy in threat assessment. Emotional exhaustion develops from the constant pressure of potentially missing critical threats, creating a state of chronic stress that affects both performance and well-being.
The business impact is profound and multifaceted. Fatigued analysts are more likely to miss genuine threats, increasing the exposure to successful attacks. They may also escalate false positives to avoid responsibility. High fatigue levels contribute to analyst turnover, creating recruitment and training costs while leaving organizations vulnerable during transition periods.
A negative feedback loop emerges where stressed analysts make more mistakes, leading to increased scrutiny and pressure, which further exacerbates fatigue. This cycle can devastate team morale.
Balancing Speed and Accuracy: The Dual Challenge of Analyst Overload
The “need for speed” in alert triage is inseparable from the problem of analyst overload and fatigue. SOCs and MSSPs must analyze threats, incidents, and artifacts quickly to contain risks, but this analysis must be accurate and comprehensive to avoid missing critical threats or wasting resources on false positives.
Solutions that streamline triage without sacrificing accuracy are essential for overcoming this paradox. You do not choose between speed and accuracy but develop systems and processes that enable both.
ANY.RUN’s Threat Intelligence Lookup: A Comprehensive Solution
ANY.RUN’s Threat Intelligence Lookup addresses both the speed and fatigue challenges by providing rapid, comprehensive threat context for indicators like files, URLs, domains, and IP addresses, and enabling teams to make informed decisions quickly.
Besides basic IOCs, this data contains attack and behavioral indicators including:
- file modifications,
- processes,
- network activity,
- TTPs mapped to the MITRE ATT&CK Matrix,
- malware configurations, Suricata IDS signatures.
The data is derived from investigations of real-world cyberattacks on over 15,000 companies using ANY.RUN’s services.
When analysts encounter suspicious artifacts during triage, they can quickly query the service to obtain detailed information about the threat. This eliminates the time-consuming process of manually researching threats across multiple sources.
TI Lookup Use Cases: Faster and Smarter Alert Triage
Instead of spending valuable time manually investigating suspicious artifacts, analysts can focus on higher-level analysis and decision-making. Here are a couple of examples.
1. Artifact Quick Check
A suspicious IP spotted in network connections can be checked against TI Lookup’s vast indicator database in a matter of seconds.
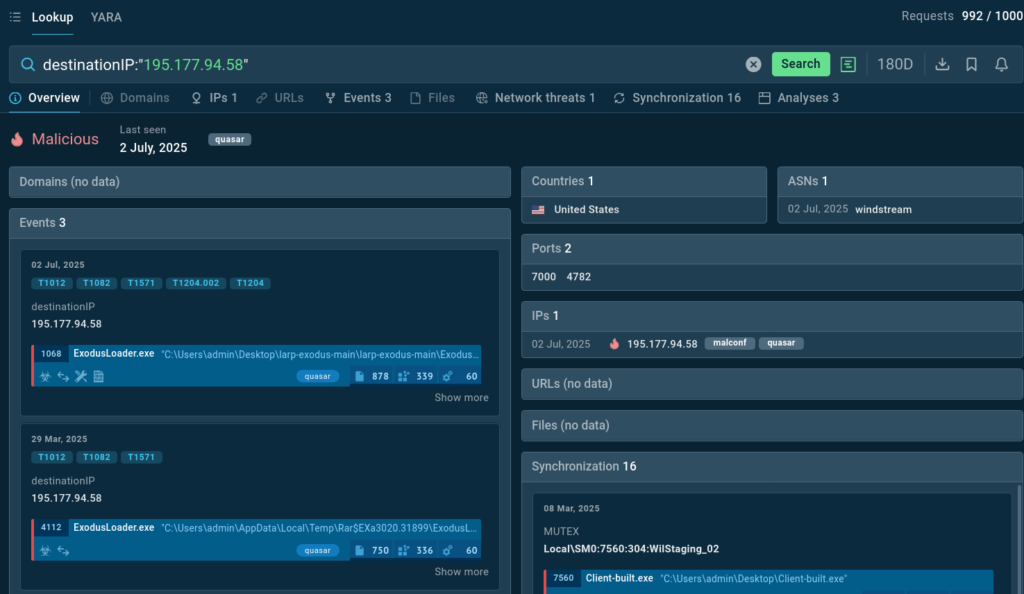
The IP address is exposed as malicious and a part of Quasar RAT inventory. It has been detected in recent malware samples, so it is an indicator of an actual threat.
2. Process Investigation
Suppose an analyst notices a legitimate utility like certutil.exe is used for retrieving content from an external URL. All they have to do is copy a snippet of command line contents and paste it into TI Lookup search bar with the CommandLine search parameter:
commandLine:”certutil.exe -urlcache -split -f http”
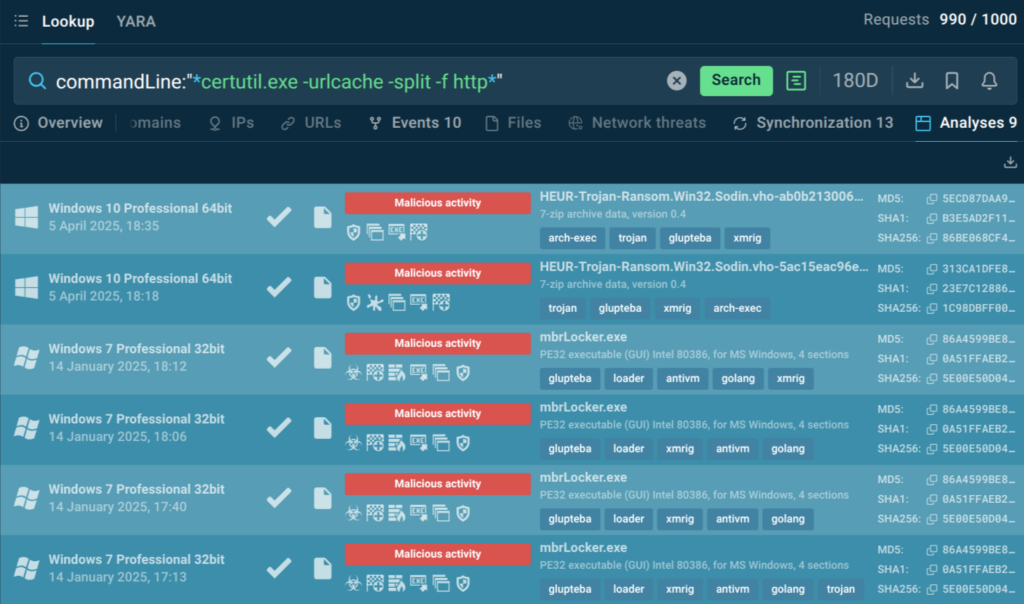
Switching to the Analyses tab of the search results, the analyst observes a selection of malware samples that performed this command during their execution chain. Now he knows that this behavior is typical for Glupteba trojan acting as a loader. Each sample analysis can be researched in depth and used for collecting IOCs.
3. Registry Change Understanding
Could it be okay if an app changes Windows registry key \CurrentVersion\Run responsible for default autoruns at system startup, by adding a command that initiates a script execution chain via mshta.exe using built-in VBScript? Query TI Lookup using RegistryKey and RegistryValue search parameters:
registryKey:”SOFTWAREMicrosoftWindowsCurrentVersionRun” AND registryValue:”mshtavbscript”
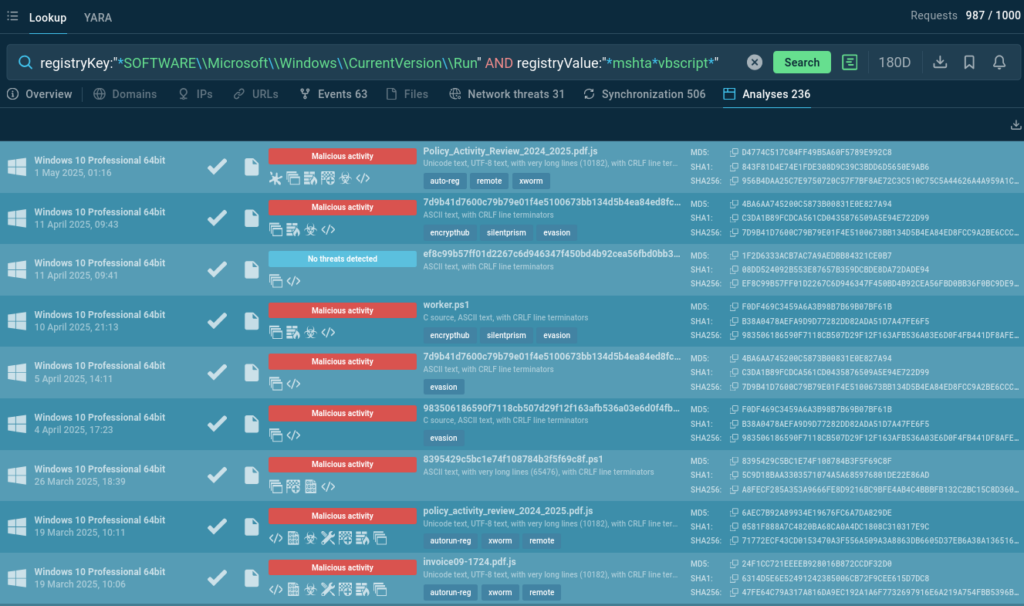
As we can notice looking at the found sandbox analyses, such registry modification is often associated with malware evasion and persistence techniques, and is typical for XWorm RAT.
4. Mutex detection
When a new malware emerges, the available intelligence on it can be scarce. Nitrogen ransomware became notorious for targeting the valuable and vulnerable financial sector back in mid-2024. For months, a single research report was the source of public data on this strain. It provided analysts with two IOCs and two IOBs, one of the formers was a mutex.
Before encrypting files, Nitrogen creates a unique mutex (nvxkjcv7yxctvgsdfjhv6esdvsx) to ensure only one instance of the ransomware runs at a time. The mutex can be used for Nitrogen detection, and searching for it via Threat Intelligence Lookup delivers Nitrogen samples detonated in the Interactive Sandbox.
syncObjectName:”nvxkjcv7yxctvgsdfjhv6esdvsx”
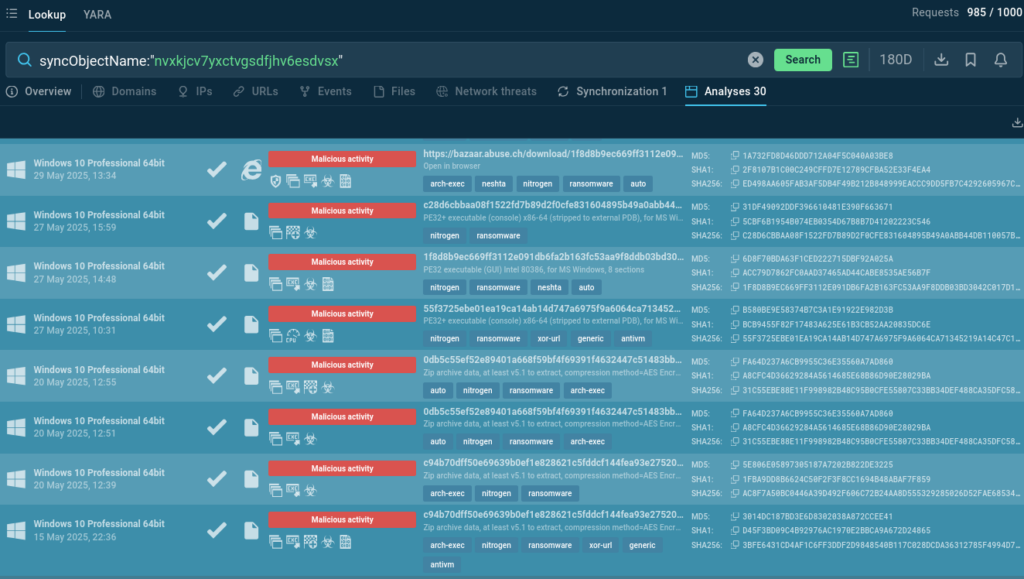
Each sample can be explored to enrich the understanding of the threat and gather additional indicators not featured in public research.
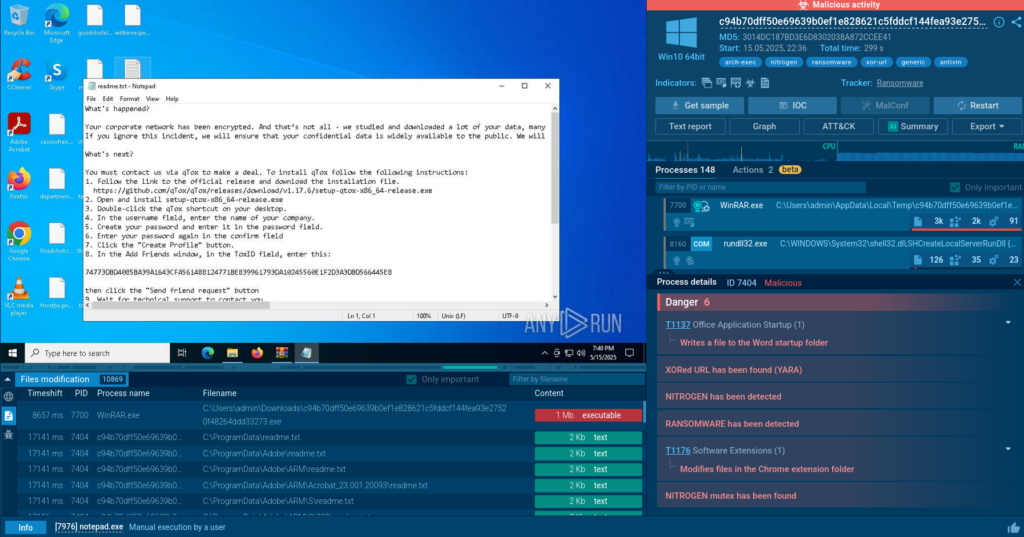
5. Payload recognition
File hashes as unique digital fingerprints of a particular file are popular indicators of compromise. TI Lookup supports md5, sha256 and sha1 search parameters, but also allows to use a file name as a query.
filePath:”Electronic_Receipt_ATT0001″
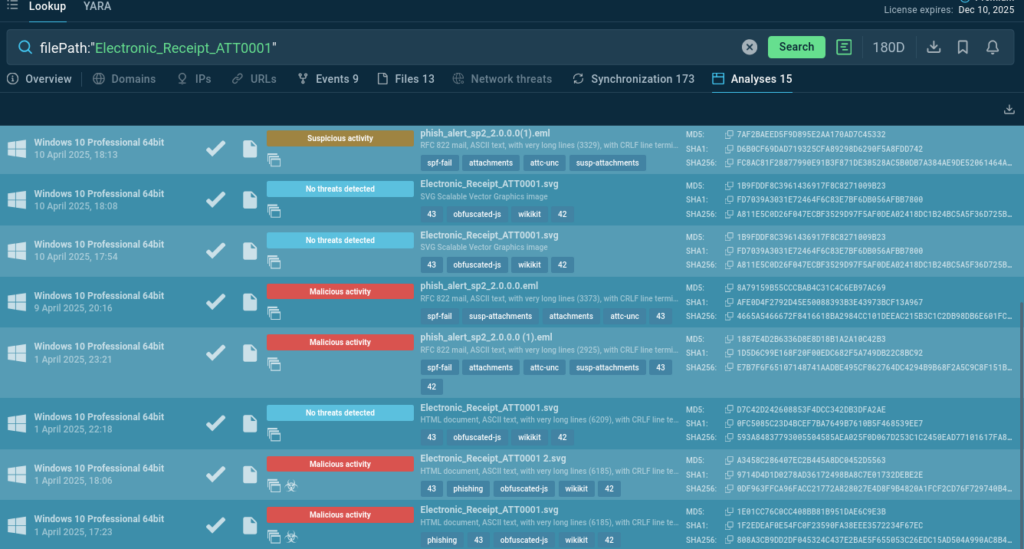
These lookup results show that a certain file name pattern can emerge in both malicious and benign samples: phishing kit campaigns often use filenames typical for popular documentation formats.
We can observe several samples of phishing attacks using the file with such name pattern in the Interactive Sandbox:
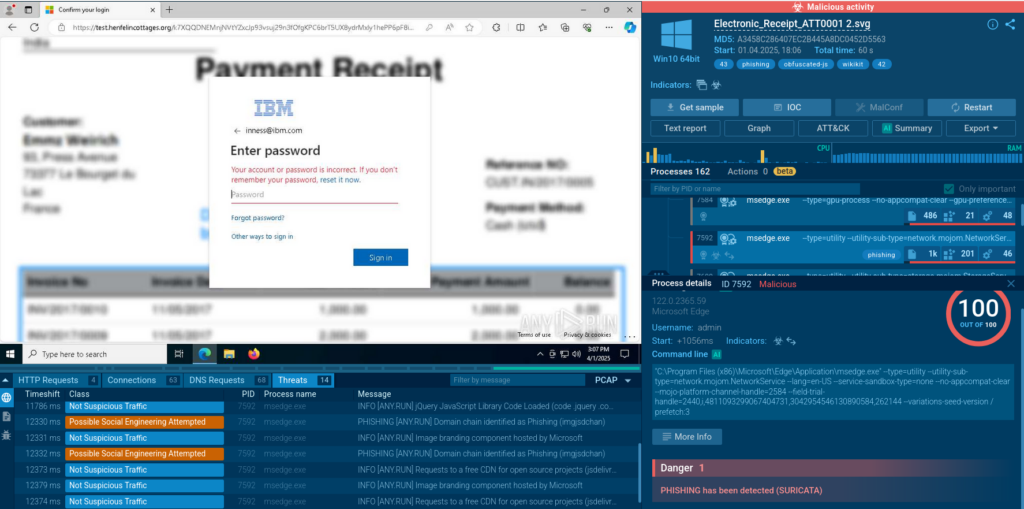
File name search can help understand the general mechanics of phishkit attacks and see a broader picture of emerging threats.
Fast, Fatigue-Free Alert Triage with Threat Intelligence
It’s up to you not to choose between speed and accuracy, nor to accept analyst fatigue as an unavoidable cost of doing business. Instead, embrace solutions that enable both rapid response and meticulous analysis.
ANY.RUN’s Threat Intelligence Lookup fuels this strategy by providing immediate, context-rich insights into suspicious artifacts and transforming reactive, manual investigations into proactive, informed decision-making. This translates into tangible business values:
- Enhanced Operational Efficiency: Teams can process a higher volume of alerts with existing staff, optimizing the return on investment in security tools and personnel.
- Reduced Organizational Risk: Faster and more accurate identification of genuine threats minimizes the window of opportunity for attackers, thereby reducing the likelihood of successful breaches, data loss, and system downtime.
- Improved Analyst Productivity and Morale: Automating the initial stages of threat intelligence gathering frees analysts from repetitive, cognitively taxing tasks.
- Preserved Customer Trust and Brand Reputation: Swift and effective handling of security incidents demonstrates a commitment to protecting sensitive data and maintaining operational integrity.
Investing in solutions like ANY.RUN’s Threat Intelligence Lookup is not just about technology; it’s about building a sustainable and resilient security posture that protects an organization’s financial health, its most valuable assets, and its people.
About ANY.RUN
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN. Our services streamline malware and phishing investigations for organizations worldwide.
- Speed up triage and response: Detonate suspicious files using ANY.RUN’s Interactive Sandbox to observe malicious behavior in real time and collect insights for faster and more confident security decisions.
- Improve threat detection: ANY.RUN’s Threat Intelligence Lookup and TI Feeds provide actionable insights into cyber attacks, improving detection and deepening understanding of evolving threats.
Start 14-day trial of ANY.RUN’s solutions in your SOC today
The post How to Maintain Fast and Fatigue-Free Alert Triage with Threat Intelligence appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
