Cyber Attacks on Government Agencies: Detect and Investigate with ANY.RUN for Fast Response
Government institutions worldwide face a growing number of sophisticated cyberattacks. This case study examines how ANY.RUN’s solutions can be leveraged to detect, analyze, and mitigate cyber threats targeting government organizations.
By analyzing real-world threats, we demonstrate how ANY.RUN’s Threat Intelligence Lookup, Interactive Sandbox, and YARA Search assist cybersecurity teams in identifying attack vectors, tracking malicious activities, and enhancing organizational resilience.
Case Studies
We will explore several attack scenarios where adversaries impersonate government structures to gain initial access:
- A phishing email sent to the Department of Employment and Workforce (a U.S. government agency responsible for helping with employment and paying unemployment insurance benefits).
- A domain imitating the official website of the U.S. Social Security Administration.
- A malicious PDF disguised as a court notice from the South African Judiciary.
1. Phishing Email Targeting South Carolina Department of Employment and Workforce
Let’s take up the role of a cybersecurity officer at the department and try to understand who is targeting the organization, what malware is used, and what delivery methods are applied.
A YARA rule is created to search emails with recipients from the domain dew.sc.gov analyzed in ANY.RUN sandbox. It identified 33 files and their analyses featuring email addresses on dew.sc.gov.
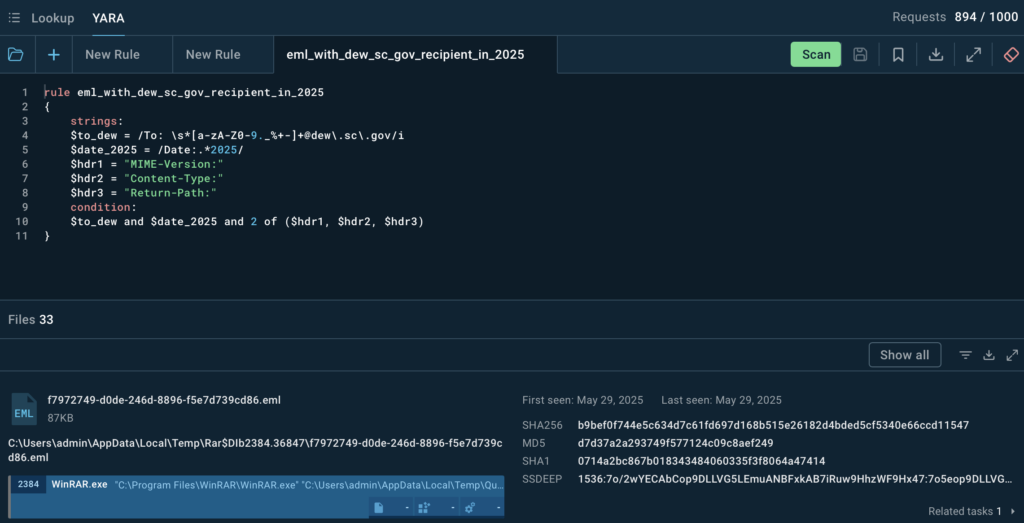
These results help to better understand threats targeting the agency:
- Study subject lines, attachment types, and delivery methods.
- Identify malware and tools used for attacks.
- Collect artifacts (hashes, URLs, IPs) for filtering and monitoring.
- Detect recurring techniques to improve protection.
Let’s view one of the sandbox analyses linked to the detected files:
In April 2025, a phishing email was uploaded to ANY.RUN, targeting an employee at the South Carolina DEW. The email, sent from @163.com domain, contained a malicious ZIP attachment named “Quotation.zip” (658 KB).
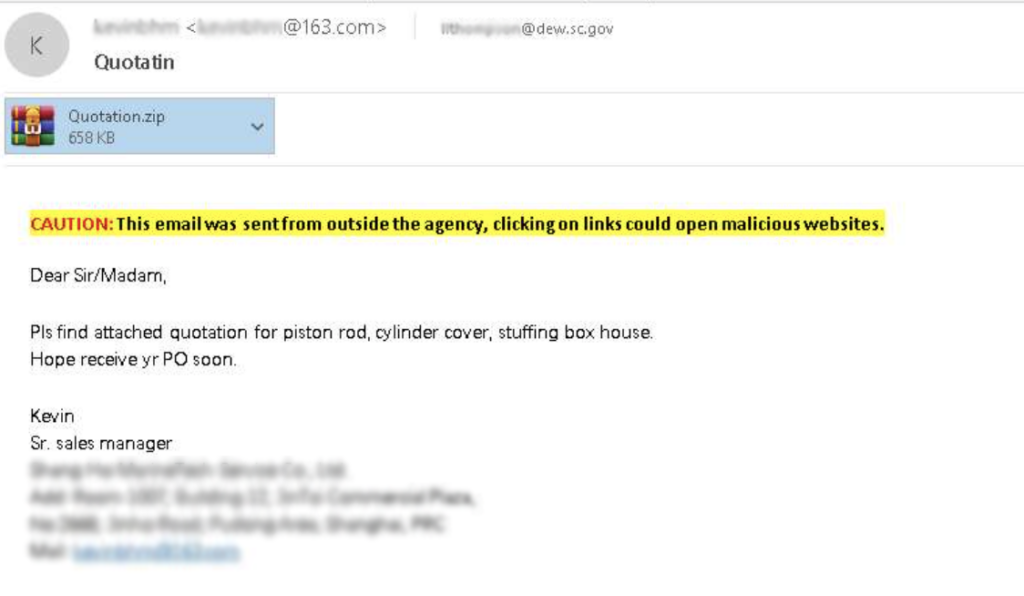
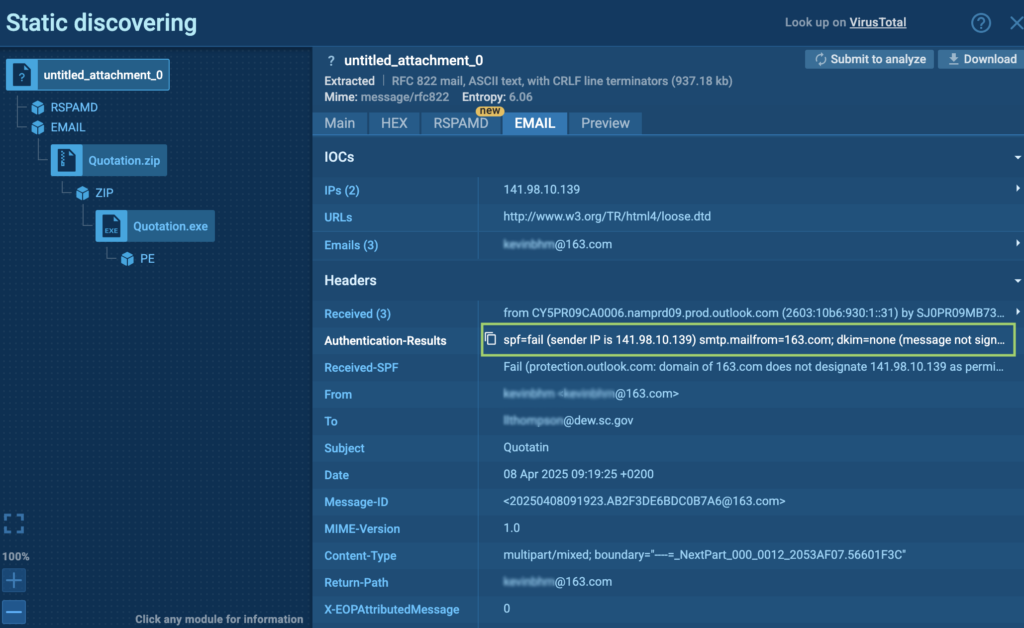
We can run a separate analysis of the email in the Sandbox. First of all, header analysis shows that the email failed SPF, DKIM, and DMARC checks — the IP address wasn’t authorized for sending from 163.com, and no DKIM signature was present.
The IP can be used as an IOC and subjected to reputation checks.
The email attachment that includes an executable file, “Quotation.exe”, has been flagged as a stealer by ANY.RUN’s signatures even before execution. The malware was identified as FormBook, with behaviors mapped to MITRE ATT&CK techniques T1552.001 (Credentials in Files) and T1518 (Software Discovery). The execution chain is visualized in the Graph section:
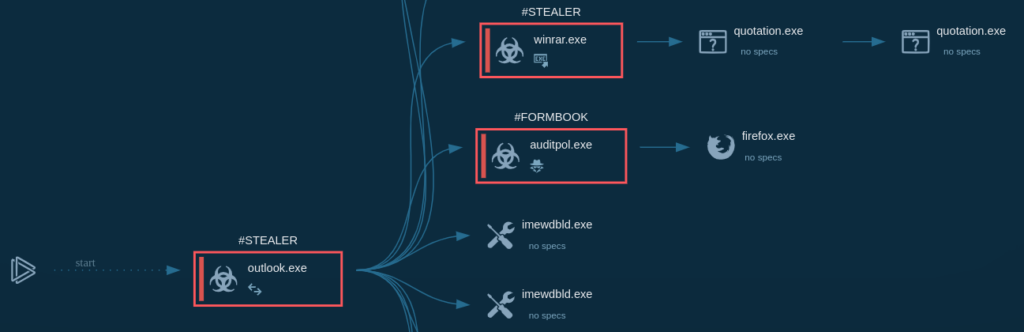
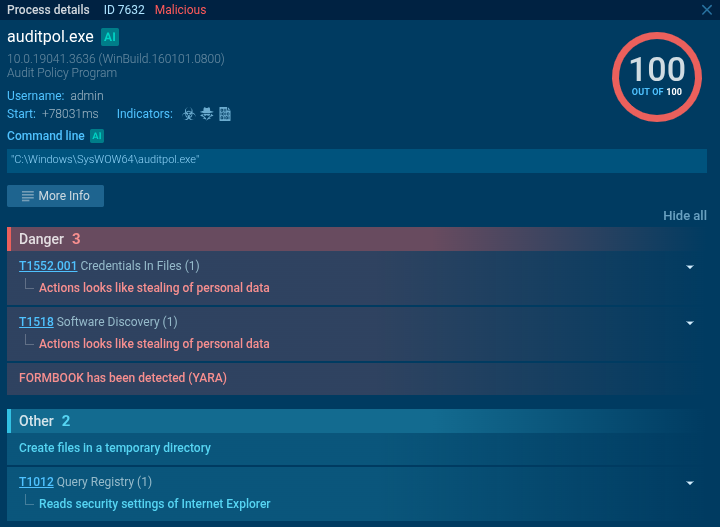
Network traffic analysis confirmed FormBook activity through Suricata rules detecting characteristic HTTP headers.
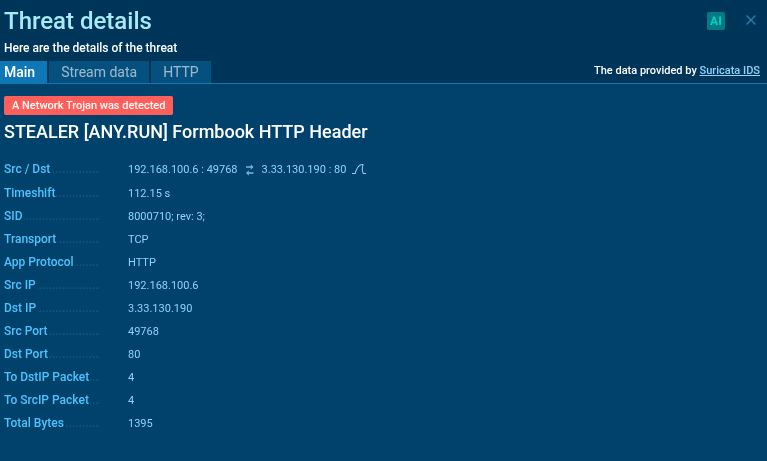
How to Find Similar Emails via ANY.RUN
And now let us scale up to exploring the landscape of similar attacks, the patterns they follow, and to understanding the urgency of such threats for government agencies in the USA. A TI Lookup search was run for FormBook samples uploaded for sandbox analysis by users from the USA and delivered to them by email opened via Outlook:
threatName:”FormBook” and submissionCountry:”US” and commandLine:”outlook.exe”
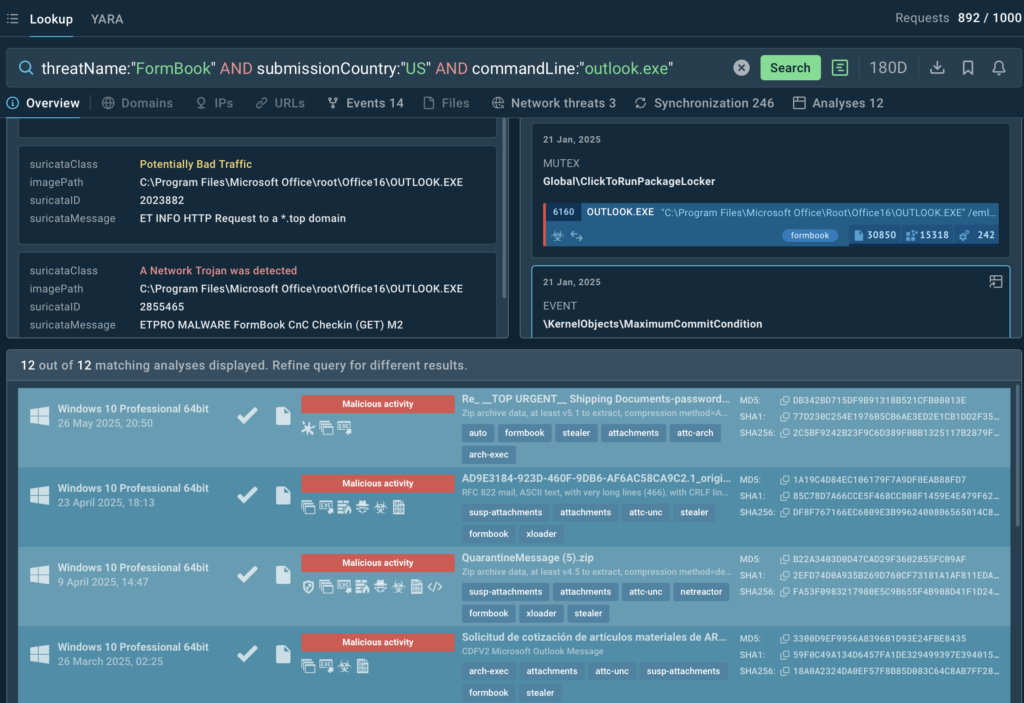
12 sandbox analysis sessions were found — each containing unique indicators like hashes, IPs, C2 calls, and email content. This data can be used for deriving context and tracking repetitive techniques.
Broader analysis is available using YARA Search for .gov email recipients in 2025 to identify malicious activity targeting US state agencies:
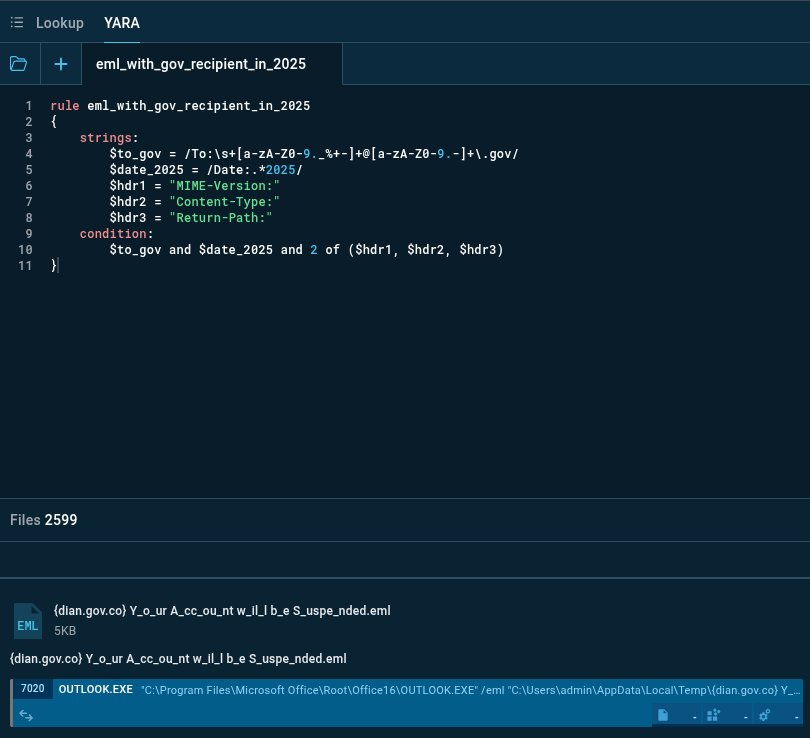
Not all the found letters are malicious, but many reflect current phishing tactics recruited against government bodies.
Custom YARA rules can be adjusted for relevance: change conditions, add filters, and thus create a selection of emails relevant to an organization’s threat profile.
2. Fraudulent Domain Mimicking the U.S. Social Security Administration
Next, we simulate the role of a SOC analyst at the U.S. SSA and research phishing domains that impersonate our entrusted agency. How do the documents these domains host look and feel, what payloads they disseminate, and what tactics and methods adversaries use?
Via TI Lookup, we search for domains flagged as malicious and containing ssagov.
domainName:”ssagov” and threatLevel:”malicious”
The search returned 22 sandbox analyses, with 7 unique potentially malicious domains. This indicates attackers actively spoof SSA for phishing. Exploring these campaigns allows SOC teams to gather indicators, set up detection systems, and enhance triage and response.
For example, an Interactive Sandbox analysis session from May 2025 spotted a malicious domain documentssagov[.]com that mimics SSA’s website and prompts users to download a “document”. Typical social engineering tactics are engaged — urgency, fake branding, and download prompts.
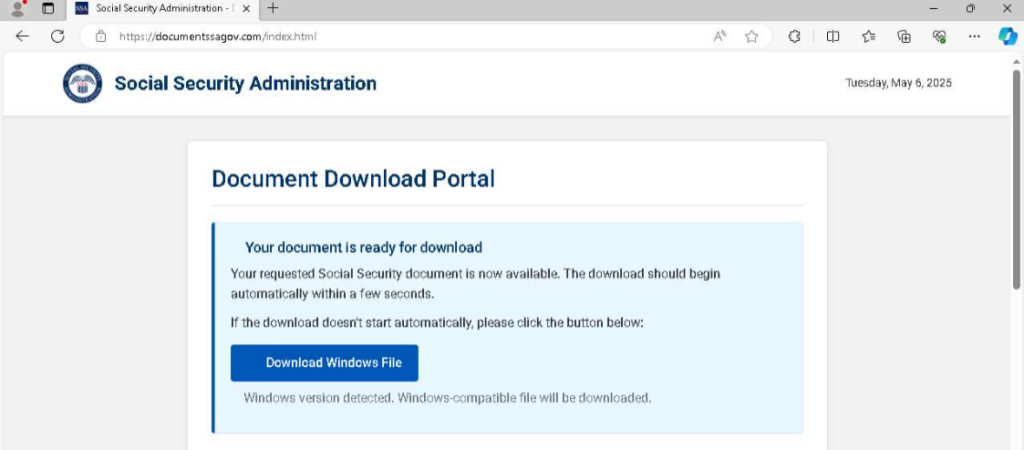
Instead of a document, an executable SSA_Document.exe is downloaded. On execution, the ScreenConnect remote administration tool is deployed — indicating an attempt to gain remote access. This activity has been detected via Suricata and mapped to MITRE ATT&CK matrix.
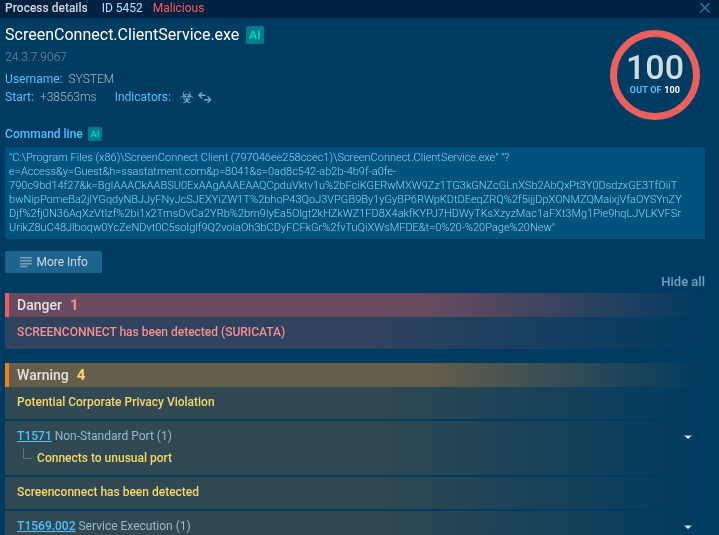
How to Find Similar Domains via ANY.RUN
Besides researching threats targeting a specific agency, we can uncover a domain-based tactic that involves spoofing a government agency sector.
We aim to identify which phishing domains are being used by malicious actors, how actively they are being exploited, and what techniques are employed to deliver malicious payloads — while also enriching our detection systems with new indicators.
Suppose we are interested in current attacks targeting ministries of foreign affairs. Let’s try to find potentially malicious domains that imitate the official websites of such organizations. Typically, these sites contain the abbreviation “mofa” (Ministry of Foreign Affairs) in their domain names.
domainName:”*mofa*” AND threatLevel:”malicious”
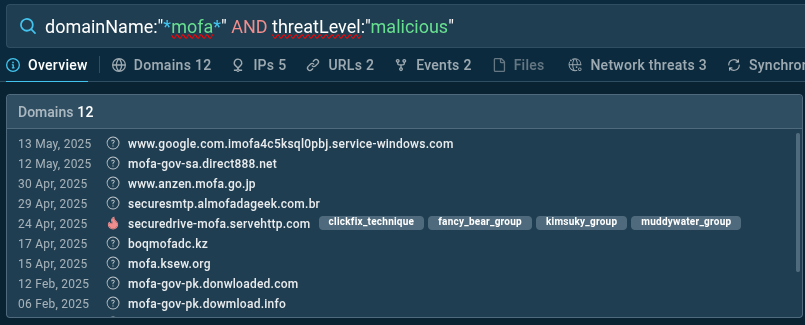
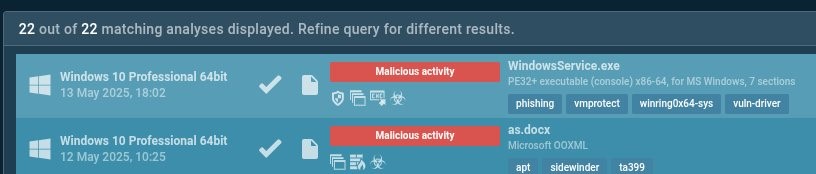
This TI Lookup search reveals 12 potentially malicious domains and 22 related analyses. Each analysis session contains IOCs, TTPs, domain interaction patterns, and data on malware distribution vectors. Such insights help understand phishing strategies, delivery mechanisms, and enrich detection systems with new indicators.
3. Malicious PDF Posing as a South African Judiciary Notice
Finally, let’s put on the hat of a South African Judiciary body employee and imagine having received an email with a PDF document disguised as an urgent judicial notice. We upload the file to ANY.RUN’s Interactive Sandbox and perform an analysis.
The document mimics a court summons allegedly sent to a company, urging the recipient to immediately review the case materials. A button labeled “PREVIEW YOUR SUMMON DOCUMENT HERE” leads to an external link likely hosting a malicious payload.
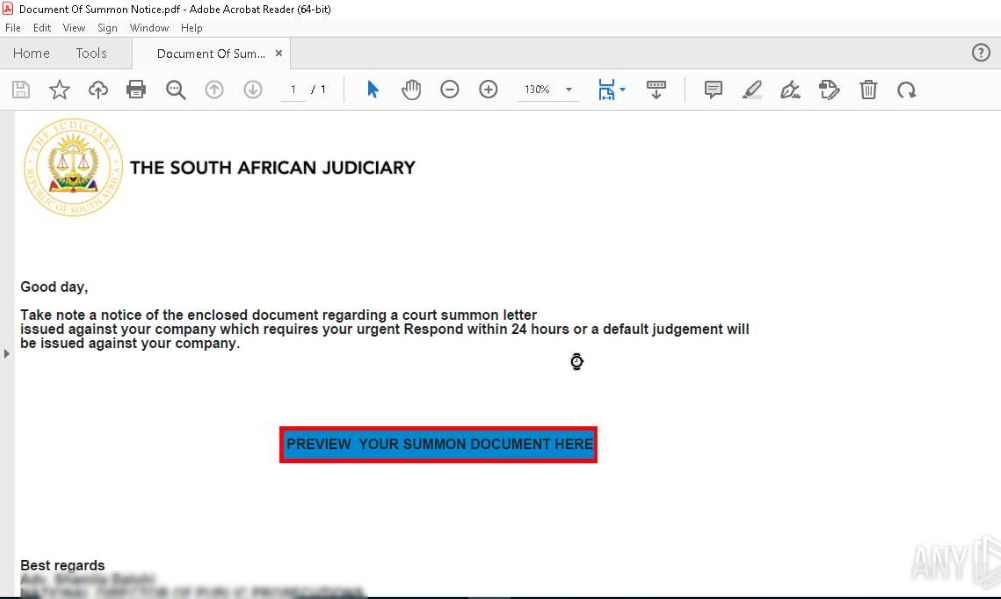
This is a classic example of social engineering, designed to create a sense of urgency and official pressure. The use of visual elements typical of government notifications increases the chances of recipient engagement. Such PDF files are often used to deliver and execute malicious code or as a trigger to redirect users to phishing sites.
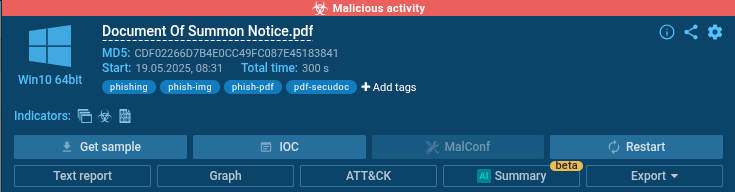
Upon opening the PDF, ANY.RUN flags the file as potentially phishing-related. It detects telltale signs, such as wording commonly used in phishing campaigns and embedded links. Quickly it becomes clear that the file is unsafe and likely part of an attack.
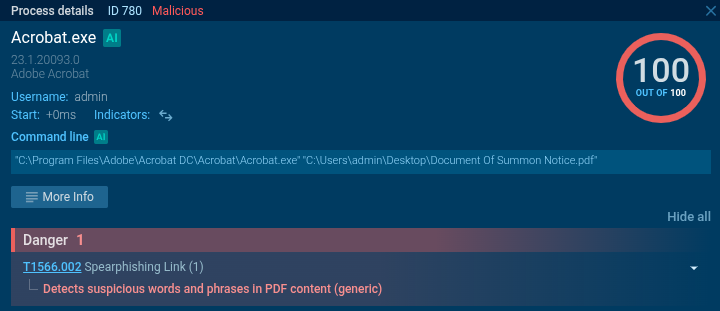
Clicking the “PREVIEW YOUR SUMMON DOCUMENT HERE” button redirects the user to FloppyShare, from which a file named “SUMMON COURT DEMAND DOCUMENT.html” is automatically downloaded. When opened, this HTML document displays a fake Microsoft Office 365 Mail login form, prompting the victim to enter their credentials.
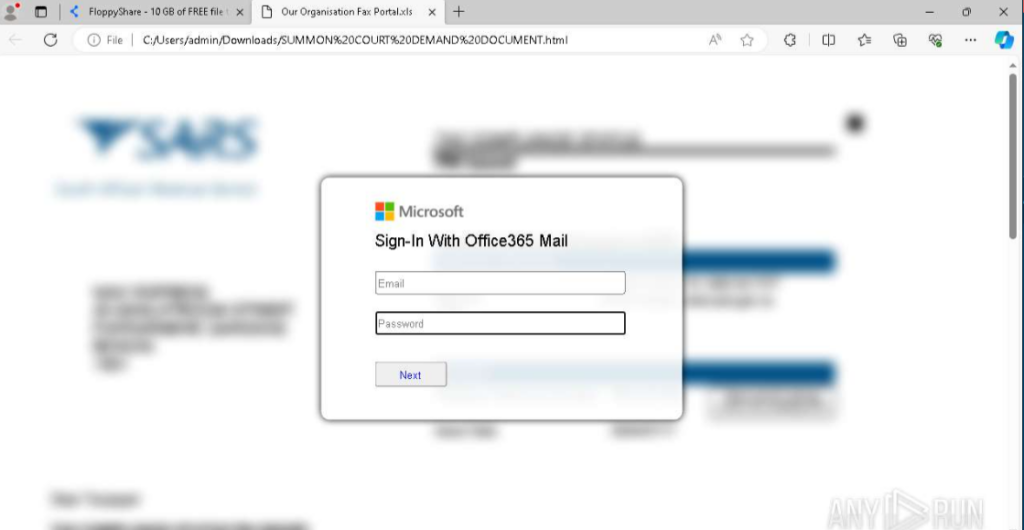
This tactic is typical of credential-harvesting phishing attacks. The form visually mimics Microsoft’s authentication page, increasing the likelihood that victims will input their login details.
How to Find Similar Documents via ANY.RUN
One effective approach is to extract embedded images from the PDF and search for their hashes in the ANY.RUN database. This helps identify similar samples, recurring templates, and visual elements used by attackers in social engineering campaigns. By doing so, we gain deeper insight into their tactics and uncover related malicious content.

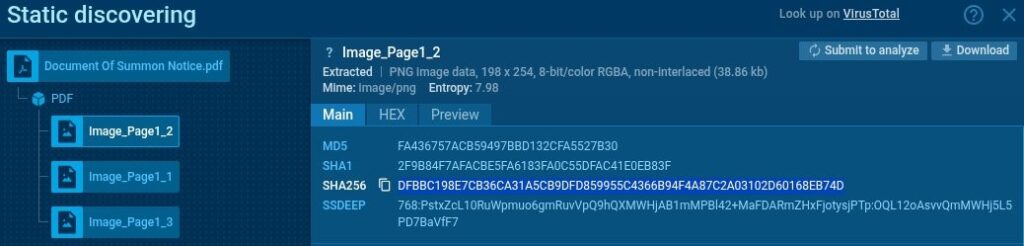
Let’s take the hash of one of the PDF’s embedded images and perform a search via TI Lookup with a simple query:
sha256:”dfbbc198e7cb36ca31a5cb9dfd859955c4366b94f4a87c2a03102d60168eb74d”
The results reveal 18 analyses featuring various PDF variants and payload delivery methods. Attackers disguise malicious pages as legitimate services and use different hosting platforms.
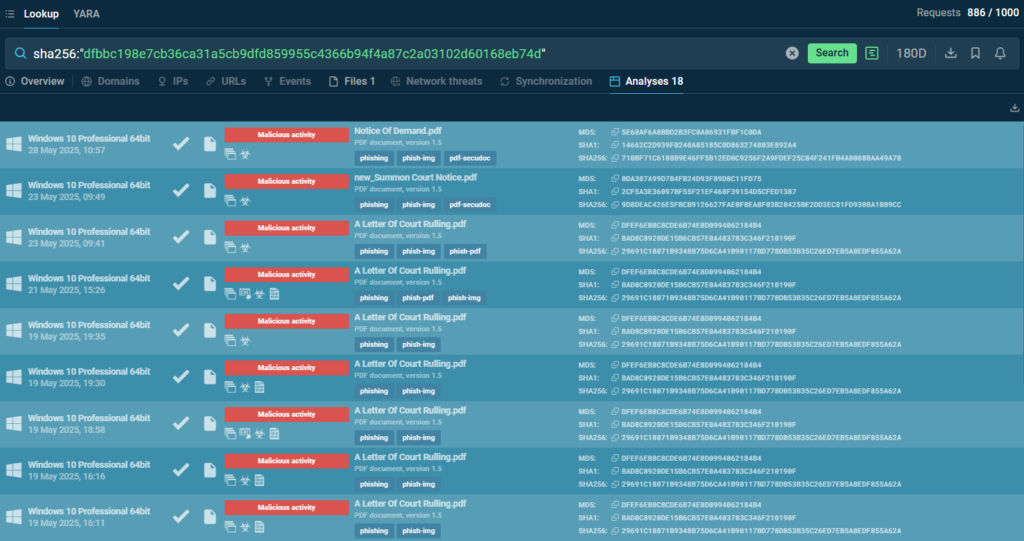
The data from the samples can serve as indicators of compromise (IOCs) for malicious activity targeting a specific company or sector of interest.
Summary on the Cases
ANY.RUN’s capabilities enabled rapid threat detection and analysis:
- TI Lookup: Provides detailed threat intelligence, including domain and IP reputation.
- YARA Search: Identifies targeted phishing campaigns by filtering emails with specific recipient domains, yielding actionable IOCs and samples.
- Sandbox Analysis: Executes malicious files to observe behaviors, map MITRE ATT&CK techniques, and detect network-based threats using Suricata rules.
The ability of these solutions to scale analysis and correlate threats across multiple incidents helps to build a comprehensive attack profile, critical for government cybersecurity strategies.
Recommendations for Decision-Makers
For government cybersecurity leaders, we recommend to:
- Adopt proactive threat hunting: Use ANY.RUN’s YARA Search to monitor emails and files targeting agency domains, enabling early detection of phishing and malware campaigns.
- Leverage real-time analysis: Employ ANY.RUN’s Interactive Sandbox to analyze suspicious attachments and URLs, ensuring rapid identification of threats.
- Use threat intelligence: Utilize TI Lookup to gather IOCs to block malicious IPs, domains, and URLs across agency networks.
- Empower staff with phishing awareness: Educate employees on recognizing spoofed domains and suspicious attachments, using insights from ANY.RUN analyses.
- Integrate with existing systems: Incorporate ANY.RUN’s TI Feeds to automate threat detection.
By providing real-time analysis, scalable threat hunting, and actionable intelligence, ANY.RUN empowers cybersecurity teams to protect critical infrastructure effectively. Implementing these recommendations will strengthen defenses, reduce response times, and mitigate risks posed by targeted cyber threats.
Get a 14-day trial of ANY.RUN’s solutions and see how much faster and deeper your threat investigations can be.
The post Cyber Attacks on Government Agencies: Detect and Investigate with ANY.RUN for Fast Response appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
