PE32 Ransomware: A New Telegram-Based Threat on the Rise
Editor’s note: The current article is authored by Mauro Eldritch, offensive security expert and threat intelligence analyst. You can find Mauro on X.
There’s no shortage of ransomware these days. It’s everywhere, lurking in email attachments, hiding in cracked software, and making headlines almost daily. While some ransomware groups vanish or rebrand, new names step in to take their place, keeping security teams in a constant state of alert.
One of the latest strains making the rounds is PE32 Ransomware, a newcomer that’s quickly gaining attention online, including on Twitter. Despite its amateur execution, it manages to encrypt files, communicate over Telegram, and cause real damage.
PE32: Key Takeaways
In this report, Mauro Eldritch takes a closer look at how PE32 works, how it communicates, and why its chaotic behavior still poses a real threat.
- Fast encryption: Starts encryption after a simple prompt; targets visible folders like Desktop.
- Unique ransom setup: Two payment tiers: one to unlock files, another to stop data leaks.
- Telegram C2: Communicates entirely via Telegram Bot API; bot token is exposed in the code.
- Easy to analyze: ANY.RUN makes it simple to extract bot data and monitor activity.
- Messy & loud: Drops marker files, triggers disk repair, and encrypts even useless files.
- No stealth: No obfuscation or evasion tricks; relies on basic Windows libraries.
- Immature but active: Still evolving, but already a threat due to poor security hygiene.
Execution Flow and Initial Behavior
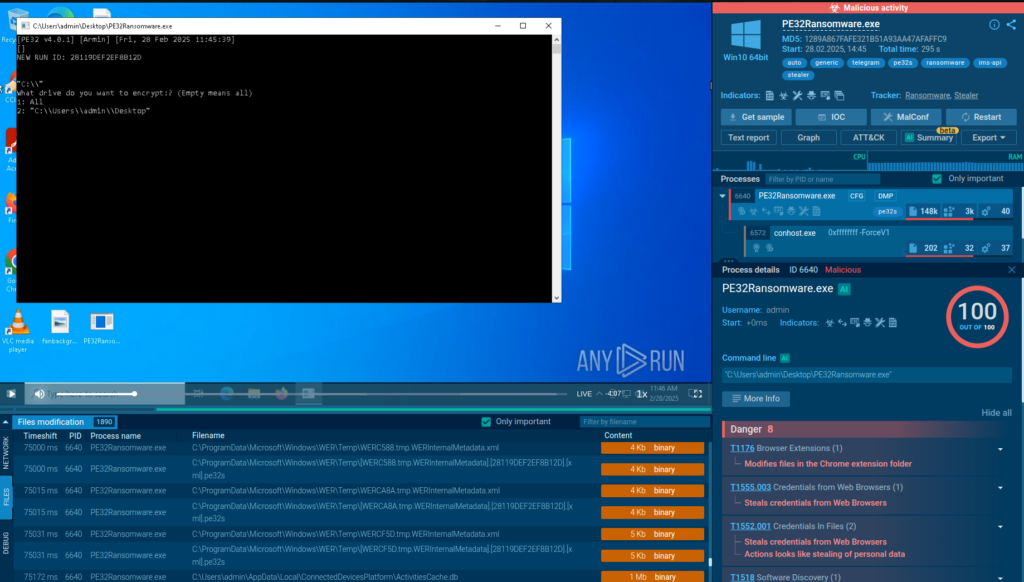
When executed, the sample waits for the operator’s input to determine whether it should encrypt only the folder where it was dropped or the entire system (see Image 2).
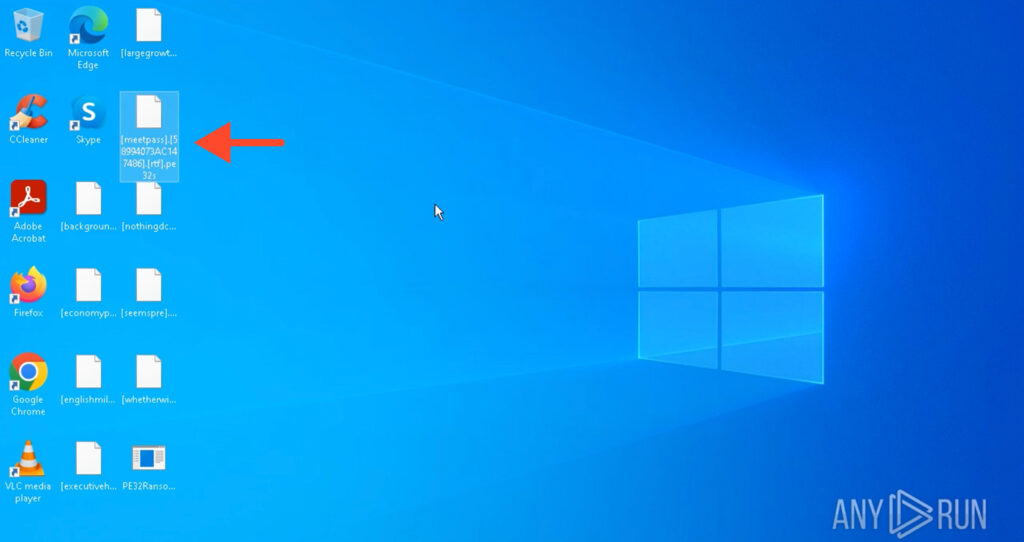
However, regardless of this selection, it immediately starts noisily encrypting the most visible locations, such as the desktop, appending the .pe32s extension (see Image 3).
Encrypted Desktop files with .pe32s extension
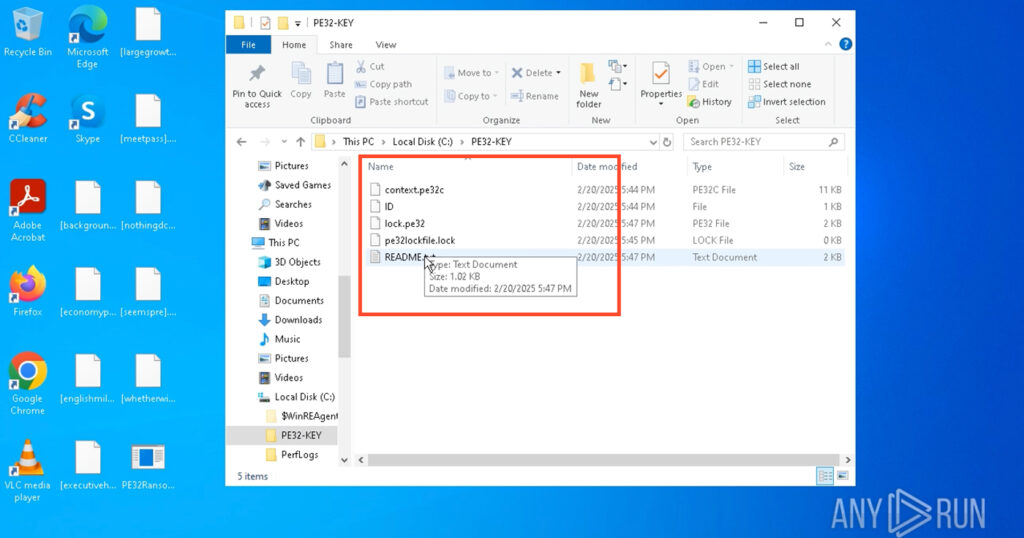
Instead of dropping a ransom note directly onto the Desktop (as most ransomware does), PE32 creates a folder named PE32-KEY in the root of the C: drive. This folder contains several internal files used during execution:
- context.pe32c, lock.pe32, pe32lockfile.lock – for internal tracking and state
- ID – stores the victim’s unique identifier
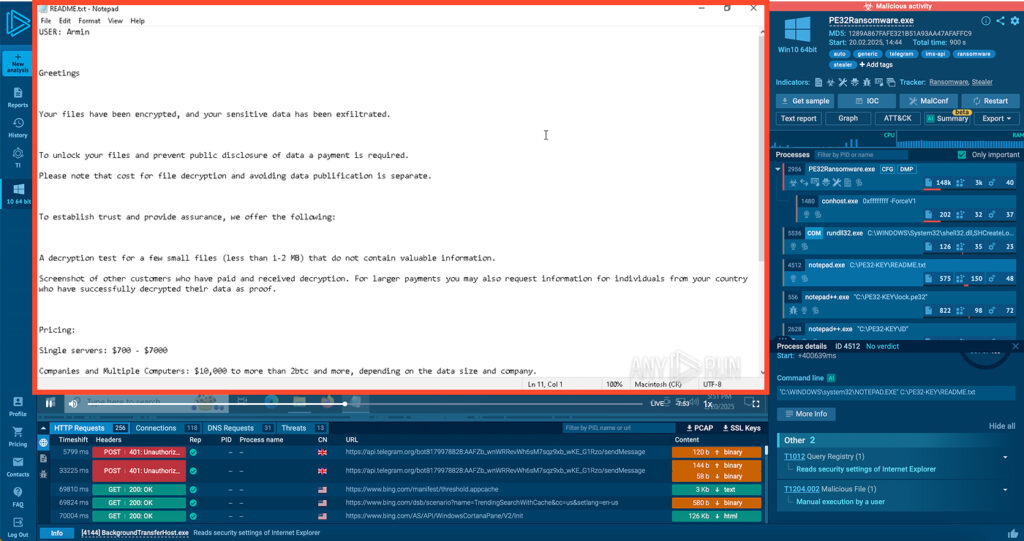
- README.txt – the actual ransom note
PE32 ransom note
The ransom note stands out for its two-tiered payment model: one fee to unlock encrypted files, and another to prevent stolen data from being leaked. This approach differs from most ransomware strains, which typically bundle both into a single payment.
Prices vary widely:
- $700 to $7,000 for individual machines or servers
- $10,000 to 2 BTC (or more) for corporate targets
Victims are instructed to reach out via Telegram. If that fails, the attackers provide a Gmail address as a backup contact method, another sign of their operational inexperience.
Telegram C2: Loud, Exposed, and Easy to Abuse
Once PE32 finishes prompting the attacker for encryption scope, it hides its process window and shifts to background mode. From there, it begins broadcasting its activity to a hardcoded Telegram group via the Bot API.
The first message looks like this:
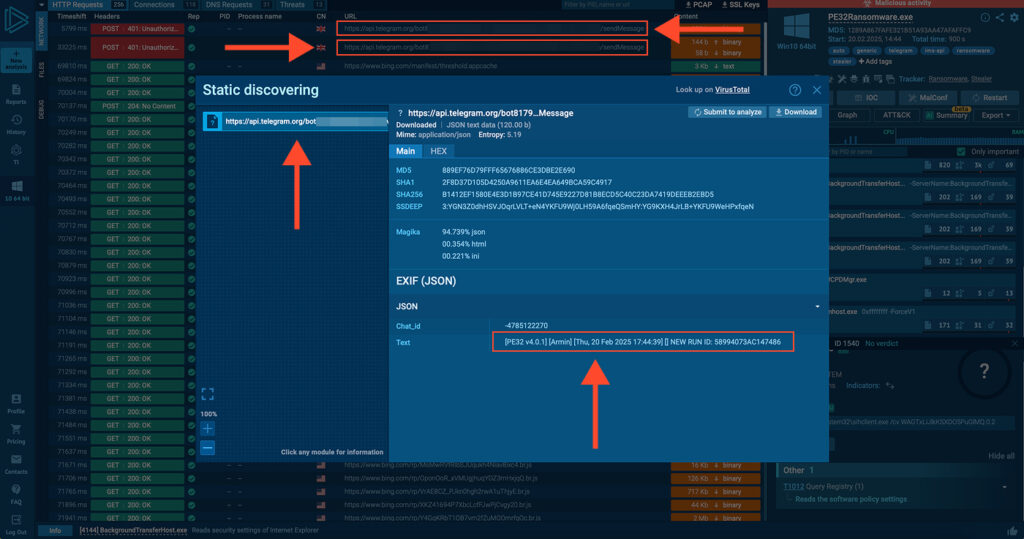
”[PE32 v4.0.1] [Armin] [Thu, 20 Feb 2025 17:44:39] []
NEW RUN ID: 58994073AC147486]”If using Telegram as a C2 channel wasn’t already an OPSEC disaster, the actors also expose their Bot Token and Group Chat ID.
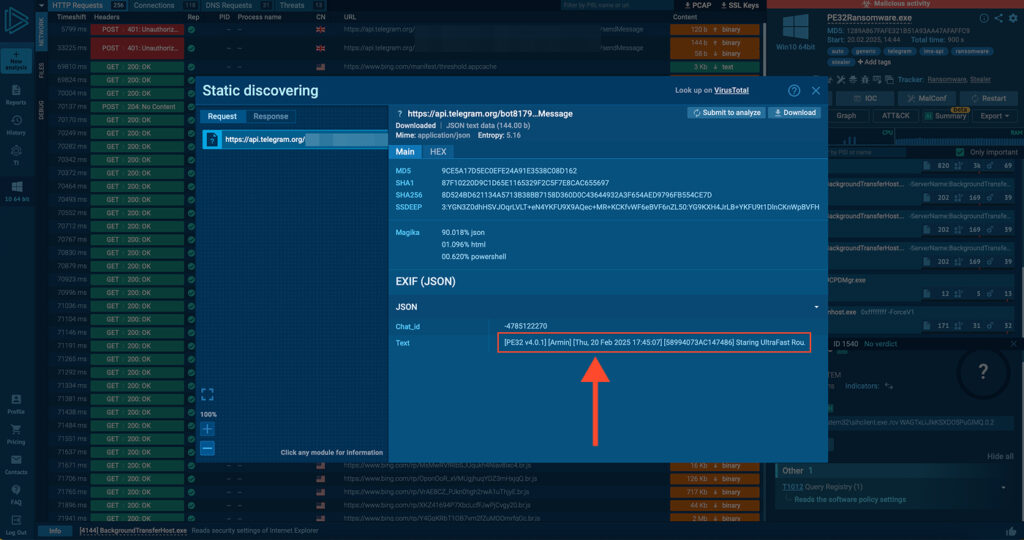
The malware then begins reporting its lifecycle to the Telegram group, detailing every step of its execution, as seen below:[Text Wrapping Break]
“[PE32 v4.0.1] [Armin] [Thu, 20 Feb 2025 17:45:07] [58994073AC147486]
Staring UltraFast Round C:\”PE32 struggles to process certain files (or their extensions—misspelled as “extentions” in its messages):
“[PE32 v4.0.1] [Armin] [Thu, 20 Feb 2025 17:47:08] [58994073AC147486]
Unknown Extentions:
[...]
odbc: 1 0MB
en_gb_e: 1 0MB
fr_fr_p: 1 0MB
xls4: 1 0MB
xls6: 1 0MB
xsx: 1 0MB
nettcp: 1 0MB
xls8: 1 0MB
access: 1 0MB”The encryption cycle concludes with three messages. The first one confirms that the “UltraFast” cycle has been completed, followed by two more messages indicating that the “Fast” and “Slow” cycles have also finished successfully.
“[PE32 v4.0.1] [Armin] [Thu, 20 Feb 2025 17:47:08] [58994073AC147486]
UltraFast Compeleted C:\”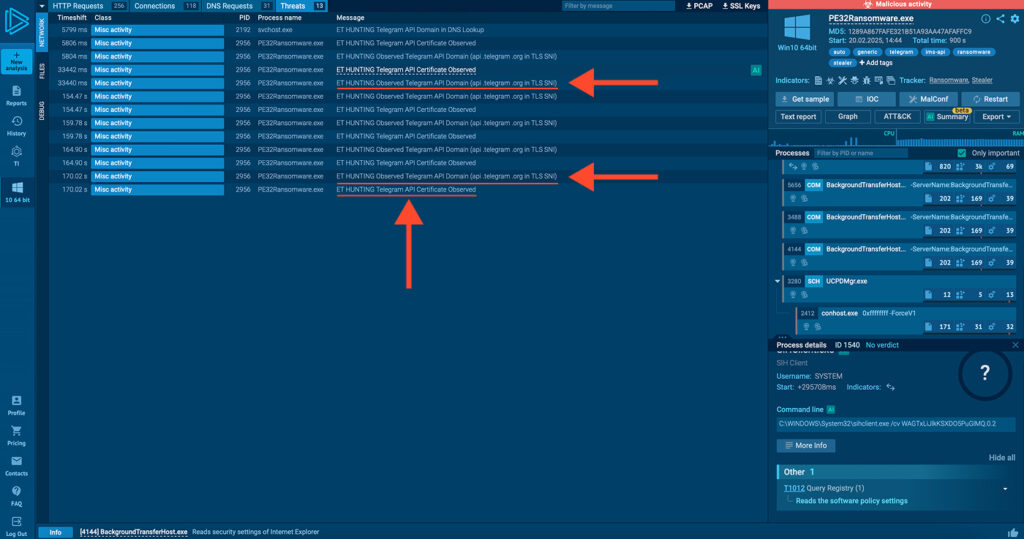
With no observable DNS or HTTP requests, we can confirm that this strain of PE32 Ransomware relies exclusively on Telegram Bots for communication. This tactic is commonly observed in the MaaS scene, particularly with certain Stealers, but is rarely used in the RaaS ecosystem.
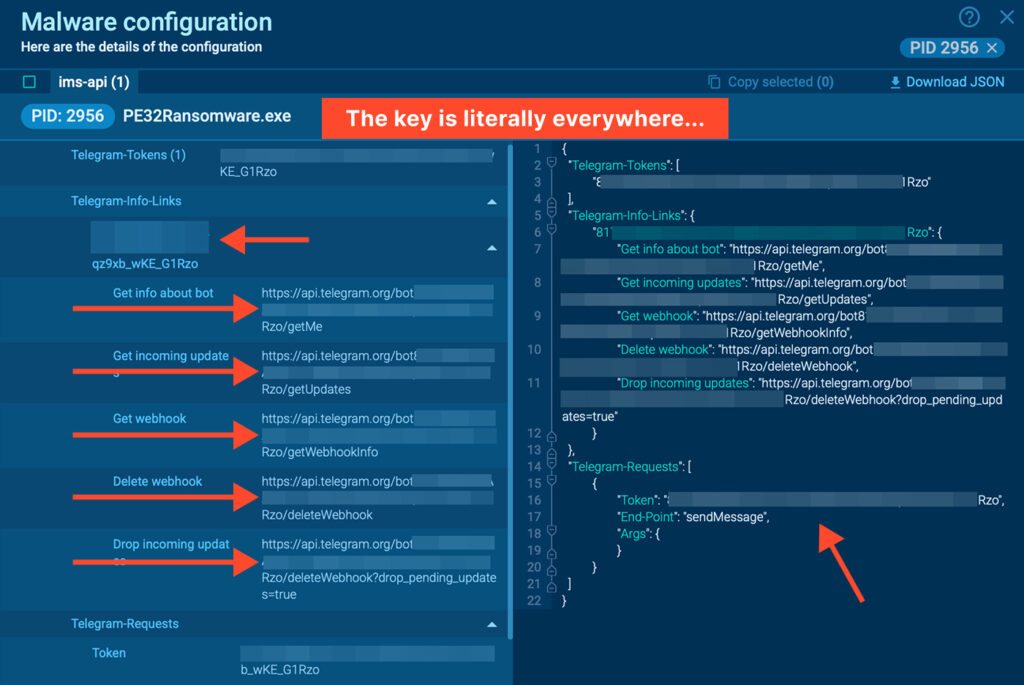
CFG Dumping with ANY.RUN
ANY.RUN’s Interactive Sandbox provides a CFG extraction function, allowing analysts to inspect the malware’s internal configuration. Unsurprisingly, the Telegram Bot Token is scattered throughout the code, making it trivially easy to trace the adversarial infrastructure—it’s almost impossible to miss, even by accident.
Armed with this token, anyone can easily flood the attacker’s C2 with fake requests or worse, use the bot’s key to impersonate the bot and send messages to any Telegram user.
By feeding the bot token into third-party tools like Matkap, threat hunters can automate the retrieval of all data exchanged through the bot, ranging from communications to encrypted files, and even victims’ encryption or decryption keys, as long as they were sent to or received from the bot.
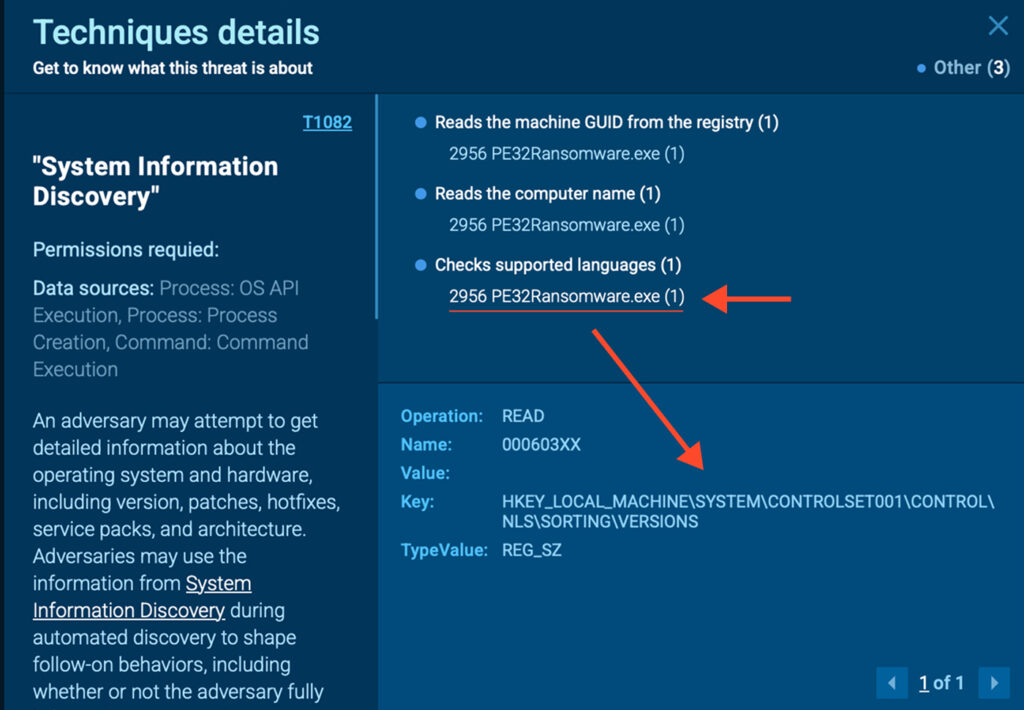
A Chaotic Codebase
Beyond its network behavior, PE32 operates like a typical ransomware strain. It collects system information such as the computer’s GUID, hostname, software policy settings, and supported languages, a common technique used to avoid infecting machines in specific regions, likely to minimize legal consequences.
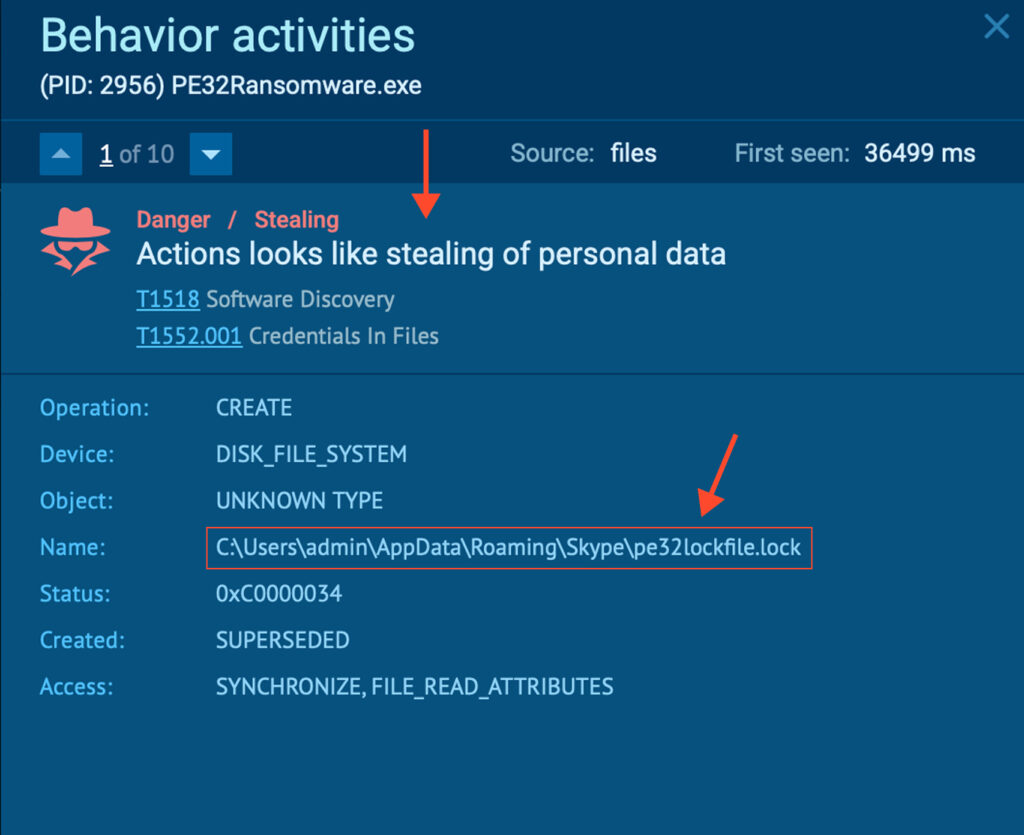
PE32’s untidy nature makes it somewhat difficult to read and profile. For instance, it places a file named “pe32lockfile.lock” in every locked folder, likely as a flag indicating “I was here already.”
But when dropping the “pe32lockfile.lock” file in directories like the ones belonging to Skype, Firefox or Chrome, it trips a good portion of detection rules, so it’s a behaviour worth nothing.
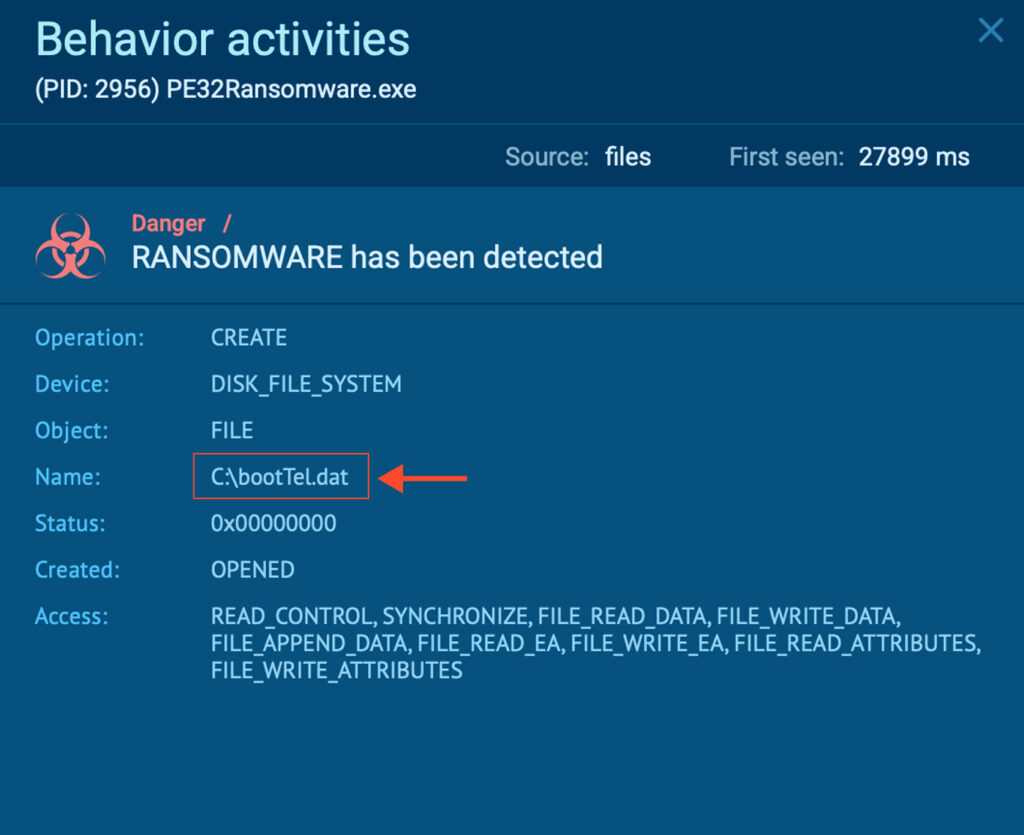
The chaos doesn’t stop there. PE32 also drops C:bootTel.dat, a legitimate Windows telemetry file associated with chkdsk.exe (Disk Checker). Although harmless on its own, the creation of this file is directly tied to the ransomware’s activity.
By aggressively encrypting files across the C: drive, including non-critical system files, PE32 ends up triggering the disk repair utility. While it doesn’t halt system functionality, it does cause Windows to initiate self-repair checks, providing an additional footprint of the malware’s presence.
With this, we now have additional indicators of PE32’s activity.
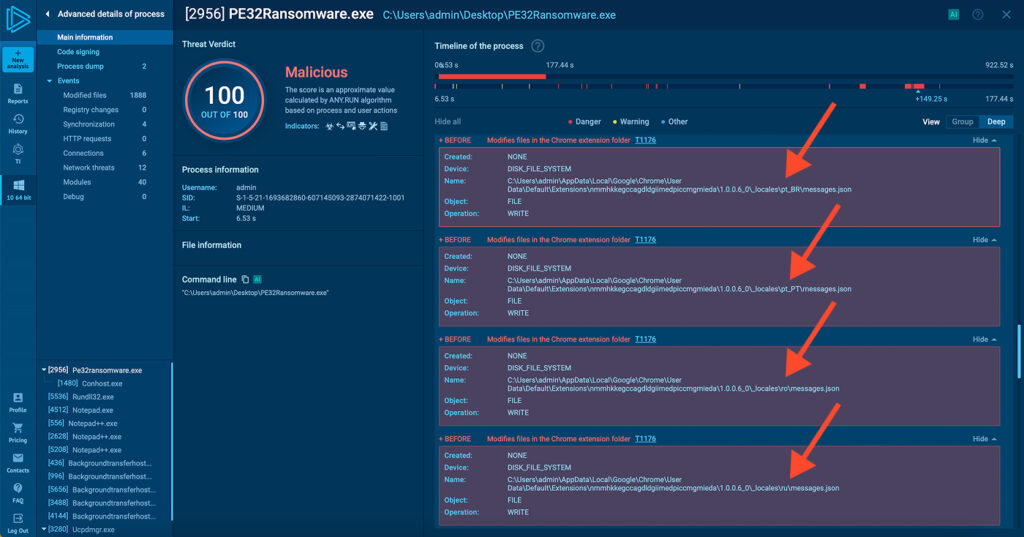
PE32 shows no logic in file selection. It encrypts everything in sight, regardless of extension or value. Chrome’s language packs (messages.json), static resources like .gif and .css files, and even incomplete extension data are all locked without discrimination.
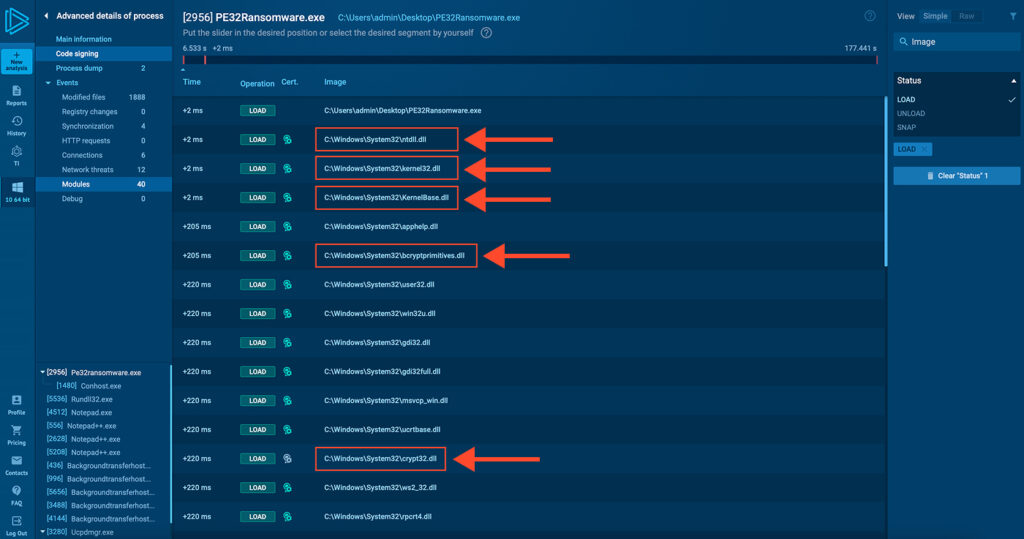
On the technical side, PE32 keeps things simple. There’s no use of exotic libraries or obfuscated function calls. It relies on the classic combo of ntdll.dll and kernel32.dll to execute processes and manipulate files, while crypt32.dll and bcrypt.dll handle encryption.
It depends on schannel.dll, Windows’ native TLS/SSL to reach its C2 channel using HTTPS, and that’s it. Plain and simple!

TTPs & IOCs
Dissecting PE32 is challenging due to its unpredictable and erratic behavior. The ransomware triggers numerous detections, some legitimate, others the result of its careless execution, which can complicate analysis and lead to false trails.
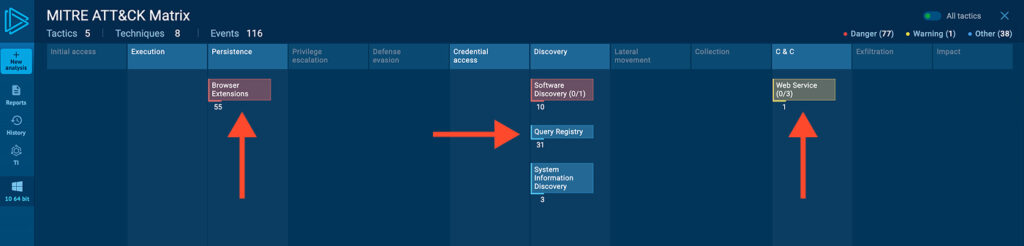
Fortunately, ANY.RUN’s automatic ATT&CK matrix and IOC collection make this task significantly easier. These features help analysts quickly identify behaviors and map them to known techniques, significantly reducing investigation time.
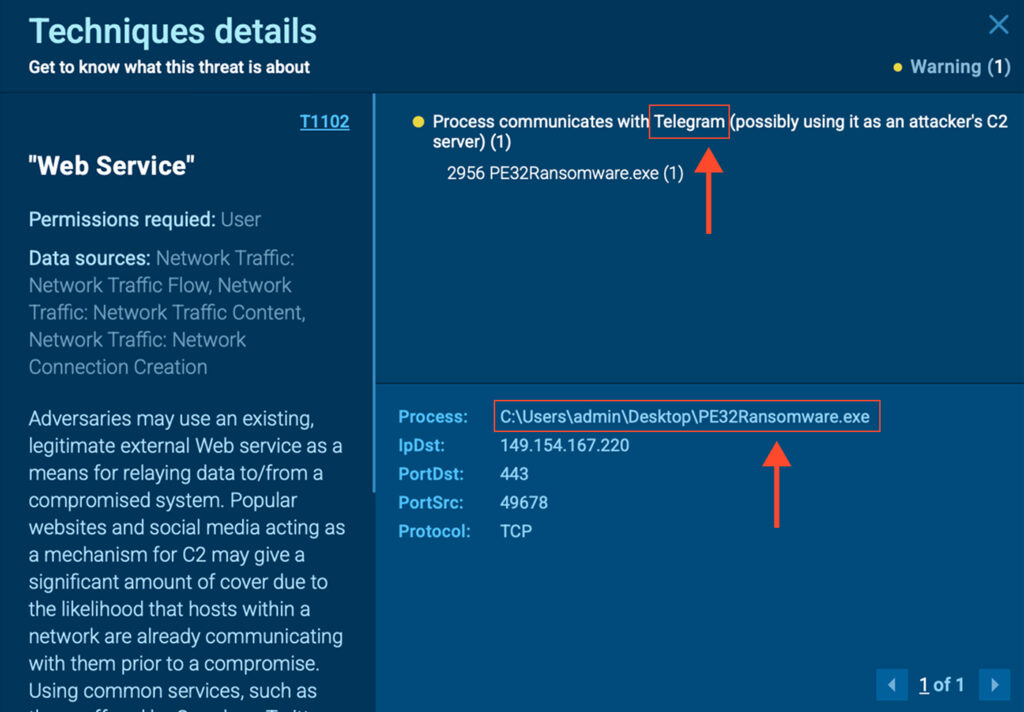
One of the most notable techniques observed is T1102 – Web Service Communication, specifically communication via Telegram. Although not the most advanced tactic, it provides a clear indication of PE32’s reliance on a basic and exposed C2 channel.
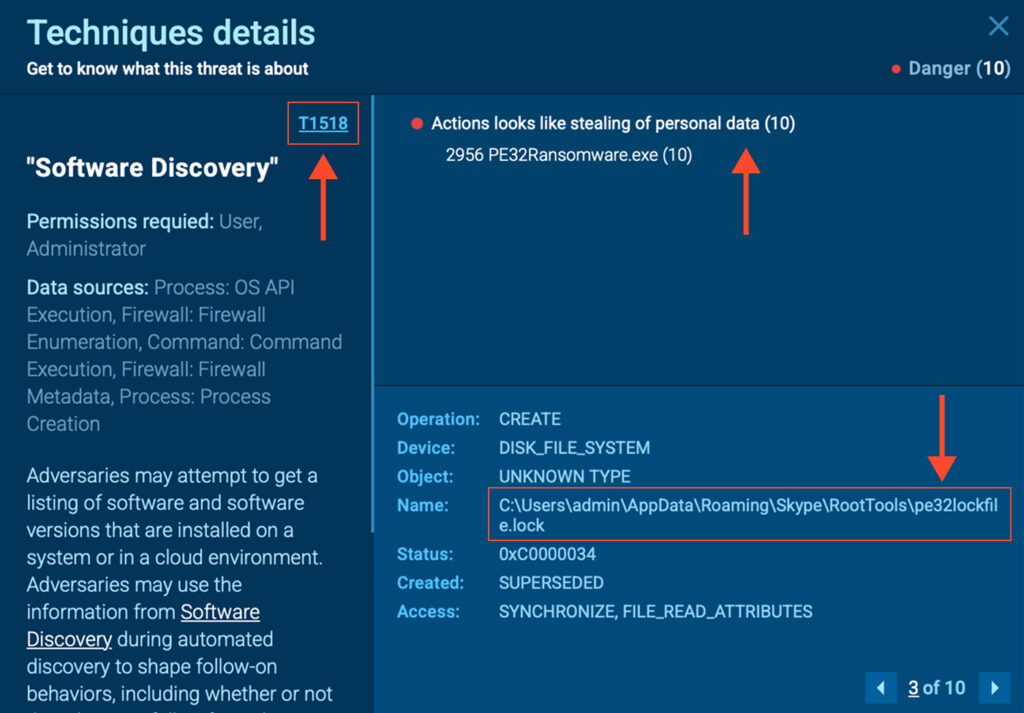
This behavior aligns with early-stage or poorly maintained ransomware, which typically lacks data exfiltration capabilities and instead focuses solely on encryption and basic status reporting. In this context, T1102 serves as a valuable early signal for identifying similar threats in the wild.
PE32 Threat Impact
The PE32 ransomware campaign introduces notable risks despite its unsophisticated design:
- For end users: Victims face potential data loss, system instability, and financial pressure from ransom demands. The dual-payment model adds further psychological manipulation by threatening data exposure.
- For organizations: While PE32 currently lacks data exfiltration, its ability to disrupt operations, encrypt shared resources, and leave behind recoverable indicators (e.g., lock files, telemetry triggers) makes it a growing concern, especially if it evolves.
- For security teams: The use of Telegram as a C2 channel, combined with erratic behavior and non-selective encryption, can complicate detection and response. Its reliance on public communication channels also introduces new monitoring and containment challenges.
- For the broader threat landscape: PE32 highlights a trend toward low-effort, fast-deploy ransomware strains, crafted with minimal obfuscation, relying on common tools, yet still capable of causing damage. Its open infrastructure and careless coding make it accessible for copycats and opportunistic attackers.
Conclusion
The analysis of PE32 Ransomware reveals how even basic, poorly coded malware can disrupt systems, encrypt valuable data, and leverage public platforms like Telegram for command and control.
While it lacks advanced evasion or data theft capabilities, PE32 reflects the growing trend of fast-deploy, low-effort ransomware strains that still pose a real threat to individuals and organizations.
By analyzing PE32 in real time using ANY.RUN’s Interactive Sandbox, we were able to fully observe its execution flow, uncover its communication channels, and extract key artifacts, without relying solely on static reverse engineering.
Here’s how this kind of analysis brings value:
- Faster threat detection: Catch suspicious encryption activity and exposed infrastructure early.
- Full behavioral visibility: Monitor system changes, communication attempts, and encryption logic in real time.
- Reduced investigation time: Quickly correlate observable behavior with known techniques and IOCs.
- Improved incident response: Collect and share actionable indicators across teams.
- Stronger threat intelligence: Identify attacker mistakes, such as hardcoded credentials and bot tokens.
Try ANY.RUN’s Interactive Sandbox today
Collect Indicators of Compromise
SHA256:15cb6bd05a35fdbd9a7e53b092a1b0537c64cb5df08ee0262479c0cc24eafd8a
FilePath:C:PE32-KEYID
SHA256:5946bdeb8b7bf0603e99cefb15c083a37352fa8a916b2664bbb9f9027f44985b
FilePath:C:PE32-KEYREADME.txt
SHA256:c6ddc9c2852eddf30f945a50183e28d38f6b9b1bbad01aac52e9d9539482a433
Filename:PE32.exe
SHA256:098ee778fca1bfd809499dac65f528ea727f2aee9c6eaf79fe662d9261086e4a
FilePath:C:PE32-KEYcontext.pe32c
SHA256:9e561018034479df1493addca30f1d031b9185e1d66f15333b8ea79d16acf64b
FilePath:C:PE32-KEYlock.pe32
References:
Matkap tool: github.com/0x6rss/matkap
Sandbox analysis: https://app.any.run/tasks/58b336b0-baec-48bb-9675-b2f3d352b63c
The post PE32 Ransomware: A New Telegram-Based Threat on the Rise appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


