How MSSP Expertware Uses ANY.RUN’s Interactive Sandbox for Faster Threat Analysis
At ANY.RUN, we love hearing about clients’ experiences. Quality feedback helps us improve and gives new and existing users a clearer understanding of our tools in actual security scenarios.
That’s why when we spoke with Augustin Alexandrovici, who leads Cyber Intelligence Operations at Expertware, we knew we had to share our conversation.
Check out the highlights to see how a Managed Security Service Provider employs ANY.RUN in its operations.
Company Overview
Expertware is a leading IT consultancy with over 18 years of experience, specializing in cybersecurity and Security Operations Center (SOC) services. With a dedicated team of over 30 cyber experts, we can seamlessly build or extend internal teams to address evolving threats and ensure robust protection for businesses.
Our expertise spans AI and machine learning, full-stack development, IT architecture, and business optimization. Having completed over 500 successful projects for leading European clients across industries such as banking, insurance, retail, telecom, and more, we deliver innovative, high-impact solutions that foster growth and resilience.
What Made Expertware Look for a Malware Sandbox
We started looking for a sandbox, because we wanted to offer to our customers an in-depth view of security incidents targeting their IT Infrastructure.
Before, we had to manually set up reverse-engineering environments, which was a time-consuming process. The extra steps required slowed down our ability to analyze and respond to malware threats in an efficient way.
We also wanted to improve the average turnaround time for malware investigations to make operations faster and be able to process more threats.
Another challenge we sought to address was the limited visibility into attacks. We needed a solution that would present us with an intuitive and streamlined view of threats’ entire kill chain.
With all of these taken into consideration, ANY.RUN’s sandbox became our choice.
ANY.RUN has enabled us to actually interact with malicious files on the fly, which saves us from risky manual setups and cuts down on the resources we allocate to daily tasks
One of the main factors behind our decision was the interactivity. It instantly solved the problem of building and maintaining our custom VMs for malware analysis. ANY.RUN has enabled us to actually interact with malicious files on the fly, which saves us from risky manual setups and cuts down on the resources we allocate to daily tasks.
How Expertware Use ANY.RUN
Our organization has been using ANY.RUN for over a year. Initially, we started with a proof of concept (POC) phase to see how it would fit into our SOC workflow, and we found it very effective, so we fully integrated it soon afterwards.
Now we use all the core products provided by ANY.RUN: the Interactive Sandbox, TI Feeds, and Threat Intelligence Lookup complementing and enriching our SIEMBIOT cyber security. Our team relies on them for malware analysis, dynamic execution of files, and rapid threat intelligence analysis.
We use the sandbox specifically for:
- Malware Investigations: We submit suspicious files for dynamic analysis to observe malicious behavior, network indicators, and potential dropper actions.
- Phishing Analysis: We examine advanced phishing campaigns to see how attachments or malicious scripts are executed within a controlled environment.
- Indicator Extraction and Mapping: We extract IOCs, map the full scope of the attack to the MITRE ATT&CK framework, and quickly integrate them into our threat intelligence feeds and detection systems.
- Training & Collaboration: We share interactive reports across the SOC and Incident Response teams to facilitate collaborative analysis and help junior analysts develop their skills.
Examples of Cyber Threats ANY.RUN Helps Address
At Expertware, we routinely confront threats like advanced infostealers (e.g., RedLine, Raccoon Stealer), persistent backdoors (like NanoCore or Remcos), and botnet malware (such as Emotet). ANY.RUN’s Interactive Sandbox and real-time analysis tools are invaluable in helping us quickly detect, investigate, and neutralize these evolving threats.
Notable Use Case: XLoader Phishing Attack
One notable case involved a highly obfuscated phishing campaign distributing XLoader malware in a multi-stage infection chain. Initially, the malicious attachment was a seemingly benign Microsoft Office document containing VBA macros. Once the macro was enabled, it executed a PowerShell command that retrieved additional payloads from a remote server.
This was followed by fileless techniques, such as reflective loading of DLLs directly into memory, making static detection difficult. When we ran the sample in ANY.RUN’s Interactive Sandbox, we could manually walk through each stage of the infection process. Specifically:
- Macro Execution: We triggered the VBA macro inside the sandbox, capturing real-time logs of spawned processes (e.g., powershell.exe) and network connections.
- Decoding the PowerShell Script: The script was obfuscated using string concatenation and base64 encoding. ANY.RUN’s interactive approach lets us step through and decode the script in real time, exposing the URLs used for Command & Control.
- Memory Analysis: By pausing and resuming processes, we pinpointed the exact moment the additional payload was written directly to memory. This was crucial in revealing the second-stage DLL that XLoader injected, bypassing traditional on-disk detection.
- Network Traffic Inspection: We observed the malware connecting to its C2 infrastructure, sending beacon requests with system reconnaissance data. ANY.RUN’s detailed packet capture allowed us to extract and analyze these indicators (e.g., domain names, IP addresses, and request parameters).
- Persistence Mechanisms: XLoader used several registry-based techniques to maintain persistence. We tracked registry changes within the sandbox session, which helped us craft custom detection rules in our SIEM and endpoint solutions.
Without the ability to dynamically interact with the malware (e.g., clicking through the macros, responding to execution prompts, and examining in-memory behavior), many of these steps would have remained hidden, especially given the extensive use of fileless and obfuscation techniques. ANY.RUN gave us the granularity to uncover each stage, correlate events, and produce comprehensive IOCs to better protect our environment and inform our incident response.
In short, ANY.RUN’s interactive approach was critical in dissecting this complex multi-stage XLoader campaign and swiftly mitigating its impact across our network.
Security and Operational Improvements After Adopting ANY.RUN
With ANY.RUN, our malware investigation and IOC extraction processes have seen over a 50% reduction in turnaround time.
The time saved in malware investigations means threats are contained and remediated faster, right? So, I believe the real added value is the opportunity to reduce potential damage. Which is really the one and only scope of our work.
With ANY.RUN, our malware investigation and IOC extraction processes have seen over a 50% reduction in turnaround time
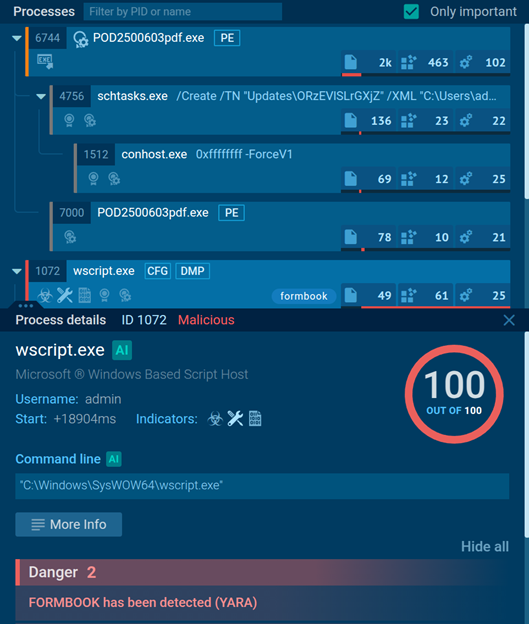
The visual process tree and network analysis allow us to see an attack’s full scope in one place, which really speeds up our containment and remediation processes.
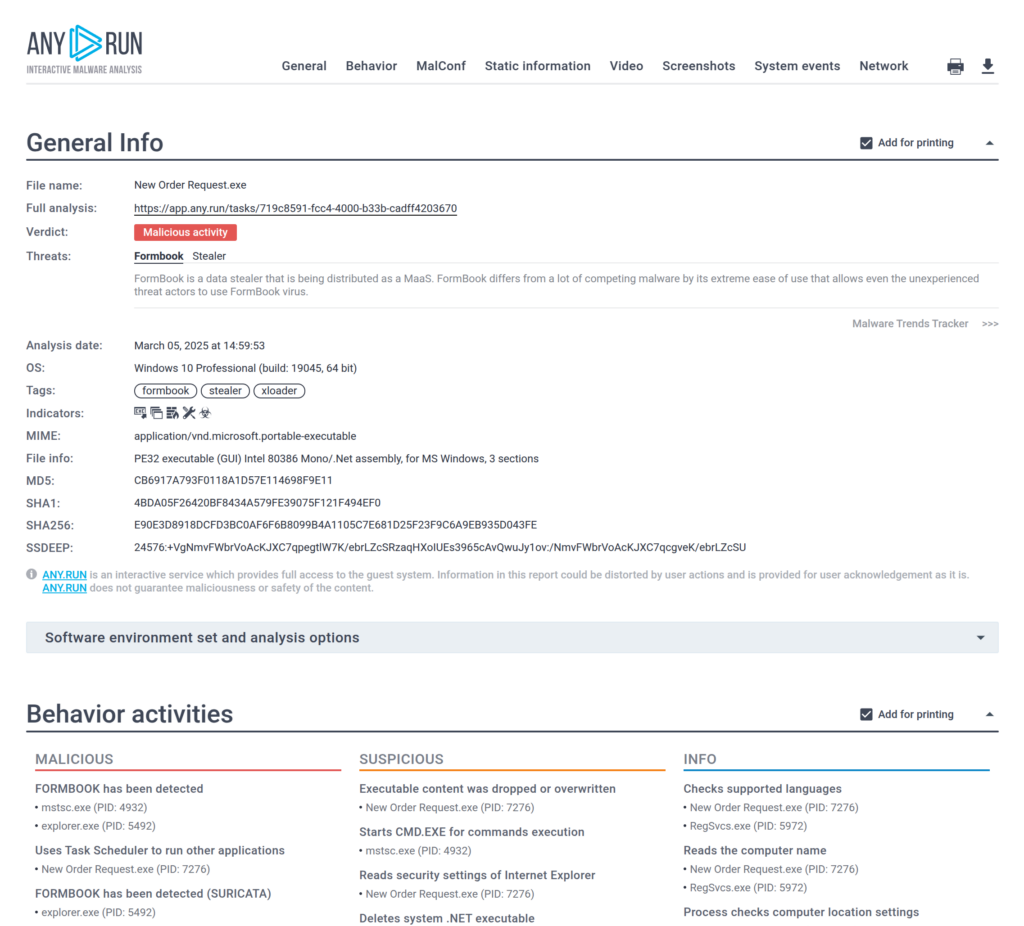
Plus, collaborating got easier—everyone’s on the same page when we can share those interactive reports.
Implementation Challenges and Solutions
To integrate ANY.RUN into our SIEM and SOAR platforms for real-time data flow, we used APIs and custom scripts, supported by OpenCTI integration. Initial challenges included interoperability issues with our Filigran system, data formatting mismatches, and security constraints. Collaboration with vendors and iterative testing resolved these issues, achieving reliable performance.
To help colleagues fully utilize ANY.RUN’s interactive features, we conducted in-house training sessions. These covered the platform’s core functionalities, best practices for malware analysis, and real-time collaboration techniques. This ensured all team members, from junior analysts to experienced responders, could effectively use the new workflows and maximize the platform’s capabilities.

Employee Feedback
Our employees are generally very positive about ANY.RUN’s products. Analysts appreciate the intuitive interface and the ability to manipulate malware in real-time. Junior analysts find it educational, since they can watch suspicious processes unfold step by step, learning about Tactics, Techniques, and Procedures (TTPs) in a hands-on manner. Senior analysts value the time savings and the visual clarity of the results.
Junior analysts find it educational, since they can watch suspicious processes unfold step by step
Advice for Those Planning to Integrate ANY.RUN
We advise starting with a pilot project on the most suspicious files—you’ll see the value right away. Take advantage of ANY.RUN’s API documentation and support channels to make integration smoother. And if you’re training new analysts, definitely have them dive into the interactive side of things. It’s a real game-changer.
Plans
We’re upping our SOC game by adding more automation. ANY.RUN’s API integration makes it easy to connect with our CTI/SOAR platform, so when something malicious is detected, it can trigger containment steps automatically. ANY.RUN will be a core piece of our future setup.
Conclusion
A big thank you to Augustine and Expertware for sharing their insight into the day-to-day operations of a security team during our meeting. The expertise and unique perspectives you provided as part of the interview will help other organizations understand the benefits of integrating ANY.RUN’s Interactive Sandbox for stronger security.
If you are using ANY.RUN’s products and willing to share your experiences with the community, please send us an email at content@any.run.
About ANY.RUN
ANY.RUN supports over 15,000 organizations across industries such as banking, manufacturing, telecommunications, healthcare, retail, and technology, helping them build stronger and more resilient cybersecurity operations.
With our cloud-based Interactive Sandbox, security teams can safely analyze and understand threats targeting Windows, Linux, and Android environments in less than 40 seconds and without the need for complex on-premise systems. Combined with our Threat Intelligence solutions, TI Lookup, YARA Search, and Feeds, we equip businesses to speed up investigations, reduce security risks, and improve team’s efficiency.
The post How MSSP Expertware Uses ANY.RUN’s Interactive Sandbox for Faster Threat Analysis appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

