Malware Traffic Analysis in Linux: Hands-on Guide with Examples
Network traffic analysis is one of the most effective ways to detect and investigate malware infections. By analyzing communication patterns, researchers and security teams can uncover signs of malicious activity, such as command-and-control (C2) connections, data exfiltration, or DDoS attacks.
In this guide, we’ll explore how traffic analysis helps detect malware, the key tools used for this purpose, and real-world examples of Linux malware analyzed in ANY.RUN’s Interactive Sandbox.
How Traffic Analysis Helps Detect Malware
Some types of malware rely on network communication to receive commands, exfiltrate stolen data, spread across systems, or launch attacks. That’s why network traffic analysis is one of the most effective ways to detect and investigate malware infections.
By looking at how data flows in and out of a system, you can reveal a variety of malicious activities that might otherwise go unnoticed.
1. Distributed Denial-of-Service (DDoS) Attacks
Some malware turns infected devices into zombies within a botnet, instructing them to flood a target server with requests. This can cause service disruptions, slow down websites, or even take entire networks offline.
 Signs in network traffic
Signs in network traffic- Unusually high volumes of outgoing traffic
- Sudden bursts of connections to multiple IPs
- Large numbers of SYN packets
2. Command and Control (C2) Communication
Many malware strains, from trojans to ransomware, rely on C2 servers to receive instructions from attackers. These communications can include downloading additional payloads, executing commands, or transmitting stolen data.
 Signs in network traffic
Signs in network traffic- Repeated communication with suspicious or newly registered domains
- Encrypted traffic over unusual ports
- Beaconing patterns
3. Data Exfiltration & Credential Theft
Some malware is designed to steal sensitive data, such as login credentials, financial information, or intellectual property. This data is often encrypted and sent to an attacker-controlled server.
 Signs in network traffic
Signs in network traffic- Outbound traffic to unknown foreign IPs
- Unusual spikes in file transfer protocols (FTP, SFTP)
- Large volumes of outbound DNS queries
4. Exploitation Attempts & Lateral Movement
Advanced malware doesn’t just infect one machine. It looks for vulnerabilities to move laterally across a network, escalating privileges and compromising more devices.
 Signs in network traffic
Signs in network traffic- Repeated login attempts from a single source (brute-force attacks)
- SMB traffic spikes
- Use of internal IP scanning tools like Nmap
5. Malware Download & Dropper Activity
Many infections start with a simple download: malware that acts as a dropper, pulling additional payloads from the internet.
 Signs in network traffic
Signs in network traffic- Downloads from unusual or newly registered domains
- Traffic to known malware-hosting services
- Execution of PowerShell or wget/curl commands from unknown sources
What Tools to Use for Traffic Analysis
Various tools help security professionals inspect network traffic and identify suspicious activities. Here are some of the most widely used ones:
Malware Sandboxes
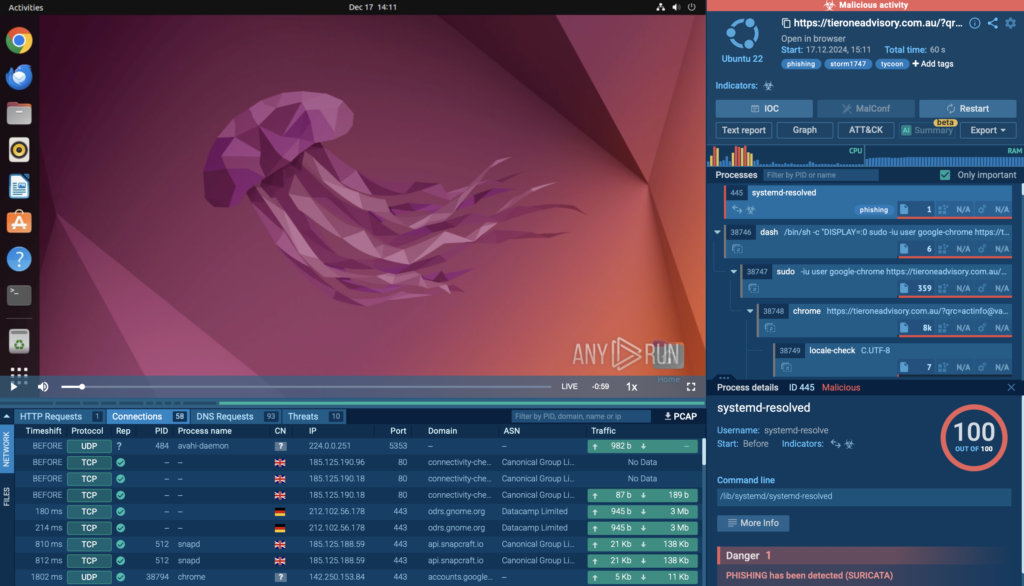
A dynamic analysis environment like ANY.RUN allows users to observe malware behavior, including network communications, in a controlled setting. The sandbox logs network requests, DNS queries, and protocol usage, making it easier to detect malicious patterns.
Wireshark
A powerful packet analysis tool that enables deep inspection of network activity. Analysts use it to capture live traffic or examine PCAP files for suspicious network behavior.
tcpdump
A command-line tool for packet capturing and analysis. It provides a lightweight method to monitor network traffic directly from Linux terminals. With tcpdump, analysts can capture packets that flow through a network interface, apply filters to focus on specific traffic, and save captures for later analysis.
mitmproxy
An interactive, SSL-capable proxy for analyzing and modifying HTTP/HTTPS traffic in real time. It’s useful for inspecting malicious web traffic generated by malware.
Analyzing Linux Malware Traffic with a Sandbox
ANY.RUN’s Interactive Sandbox provides a real-time, dynamic analysis environment that helps researchers and security teams uncover malicious network activities associated with Linux malware.
Let’s discover how ANY.RUN can make Linux malware traffic analysis more effective:
Real-time network monitoring: Observe malware’s network behavior live and view outbound HTTP, HTTPS, and DNS traffic, detect hardcoded C2 servers, and spot encrypted connections on unusual ports.
Interactive analysis: Engage with the infected environment to trigger malware behaviors, bypassing sandbox evasion tactics and uncovering hidden threats.
Packet capture (PCAP) export: Capture and export all network traffic for deeper analysis in Wireshark or other packet inspection tools.
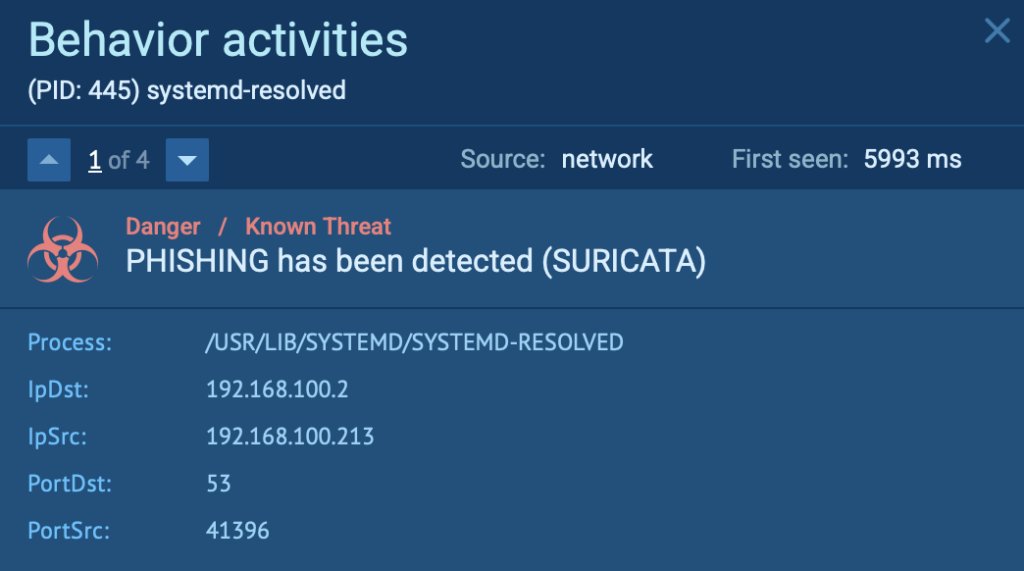
Suricata-driven threat detection: The sandbox automatically flags malicious network behavior, including botnet communications, exploit attempts, and data exfiltration.
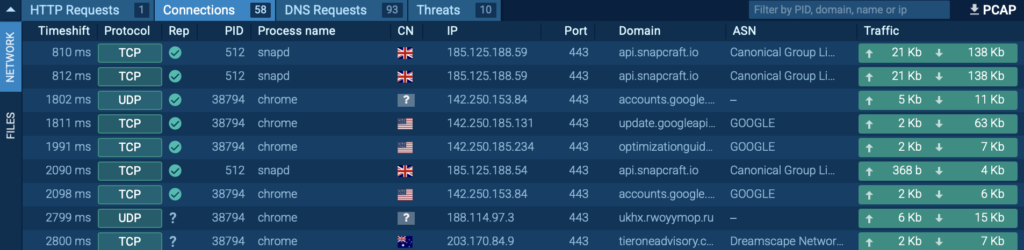
Faster investigations: Reduce time spent on manual traffic analysis with live, actionable insights and automated reporting.
Real-World Linux Malware Analyzed in ANY.RUN Sandbox
To demonstrate the power of ANY.RUN’s Linux Sandbox for malware traffic analysis, let’s examine three real-world Linux malware cases:
Case 1: Gafgyt (BASHLITE) – Massive DDoS Attack
Gafgyt, also known as BASHLITE, is a notorious Linux botnet malware that infects IoT devices and servers to launch DDoS attacks.
View analysis session with Gafgyt
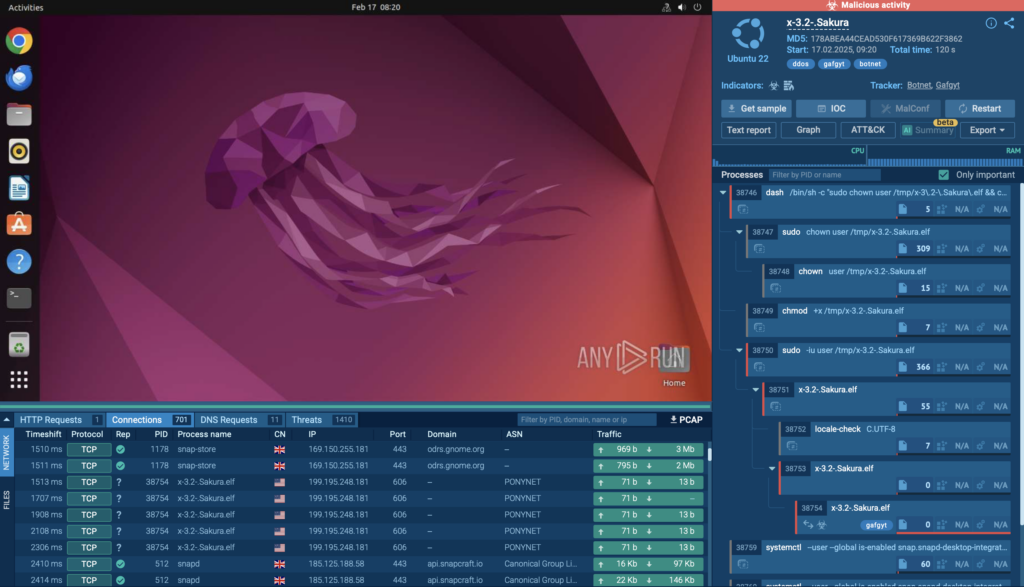
After examining it inside ANY.RUN’s sandbox, we can see that the malware hijacked the VM, turning it into a botnet. It then attempted to establish connections with over 700 different IP addresses, flooding the network with malicious traffic.
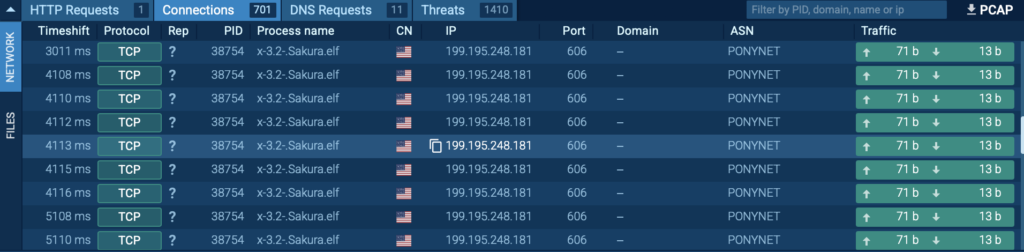
After examining it inside ANY.RUN’s sandbox, we can see that the malware hijacked the VM, turning it into a botnet. It then attempted to establish connections with over 700 different IP addresses, flooding the network with malicious traffic.
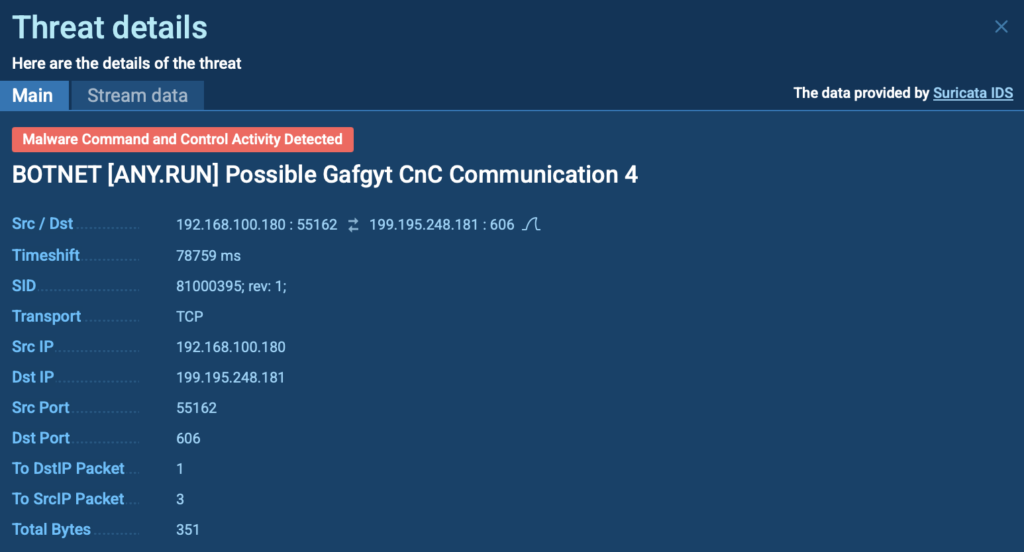
The malware established connections with botnet C2 servers, triggering a Suricata alert due to suspicious network behavior.
You can observe this detection in the “Threats” section under Network Activity Analysis in ANY.RUN:
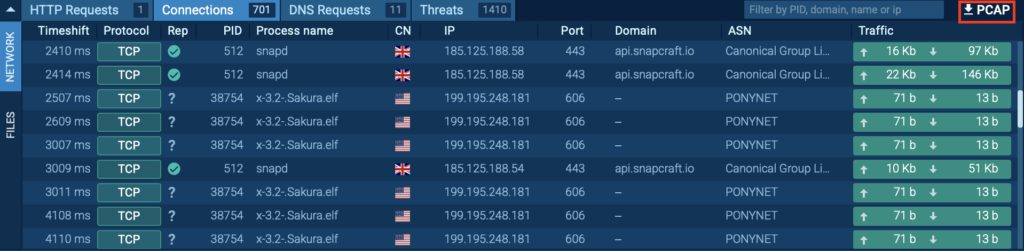
ANY.RUN provides a PCAP export feature, allowing you to analyze captured network traffic in Wireshark or other specialized tools by exporting the packet capture file for deeper inspection and threat analysis.
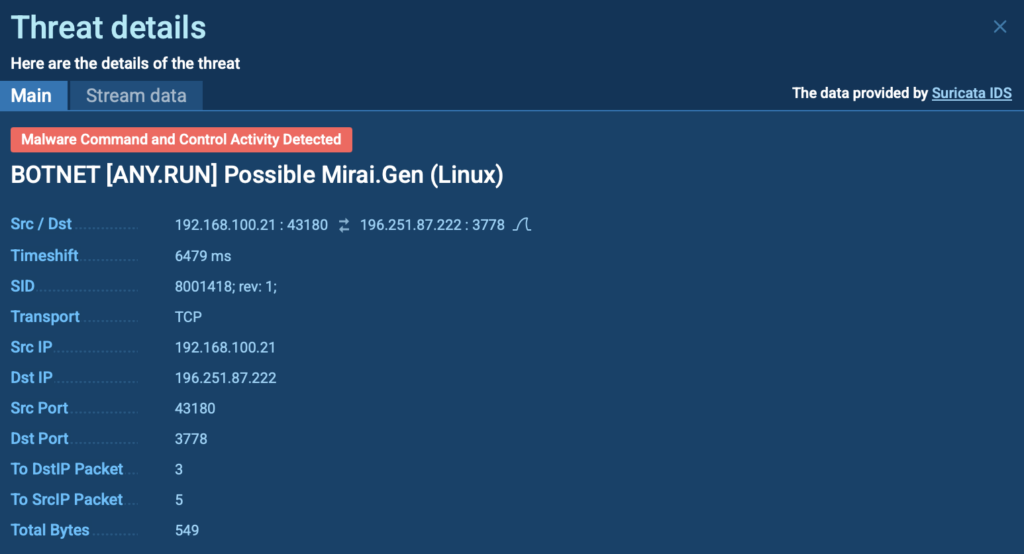
Case 2: Mirai – Detecting Malicious Network Behavior
Mirai is a notorious Linux-based malware that primarily targets IoT devices, such as routers, cameras, and other connected systems. It infects devices by exploiting weak or default credentials, turning them into botnet nodes used for large-scale DDoS attacks.
Once infected, these compromised devices begin scanning the internet for other vulnerable systems to expand the botnet.
View analysis session with Mirai attack
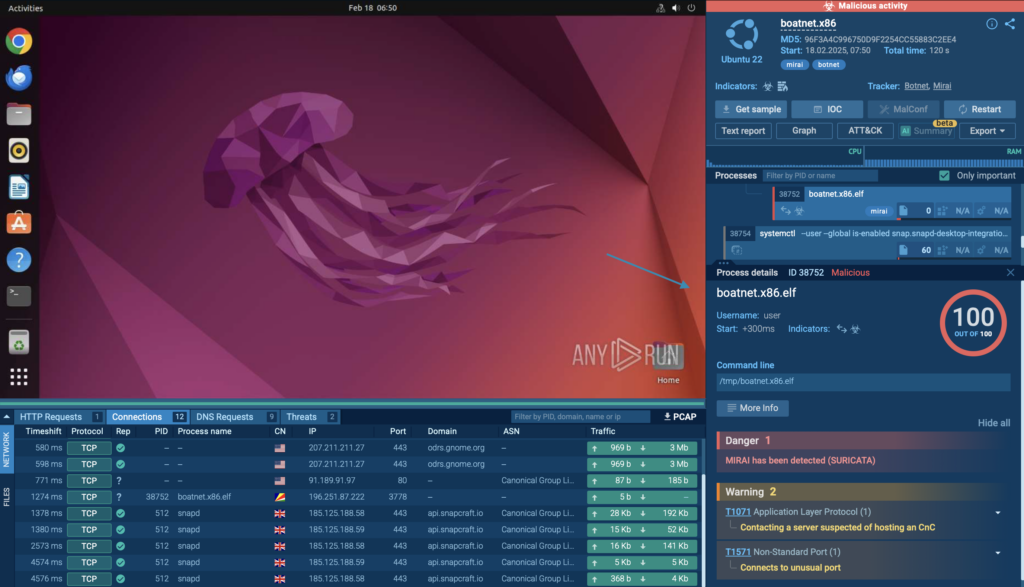
In this analysis session, we observe a Mirai attack within a controlled environment using ANY.RUN’s Interactive Sandbox.
The malware’s behavior was automatically detected, as it triggered a Suricata rule, confirming its presence through network traffic analysis.
The session shows how Mirai communicates, spreads, and attempts to establish connections with remote servers.
Case 3: Exploit – Behavioral Detection in Network Traffic
Exploits are a common attack vector used by threat actors to gain initial access to Linux systems. These attacks take advantage of system vulnerabilities, often unpatched software or misconfigurations, to execute malicious payloads, escalate privileges, or establish persistence.
Once inside, attackers can deploy additional malware, steal sensitive data, or take full control of the compromised machine.
View analysis session with Exploit
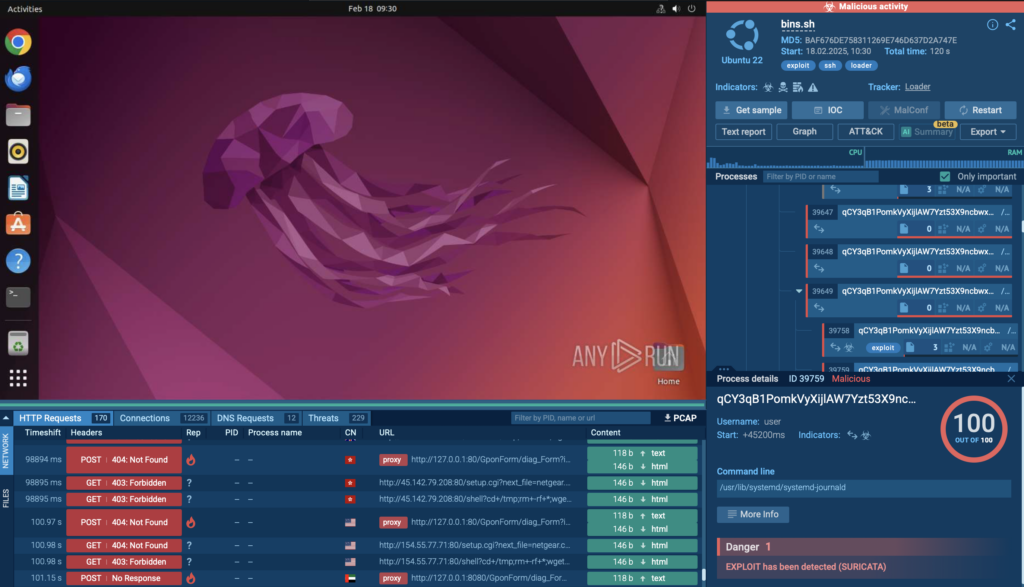
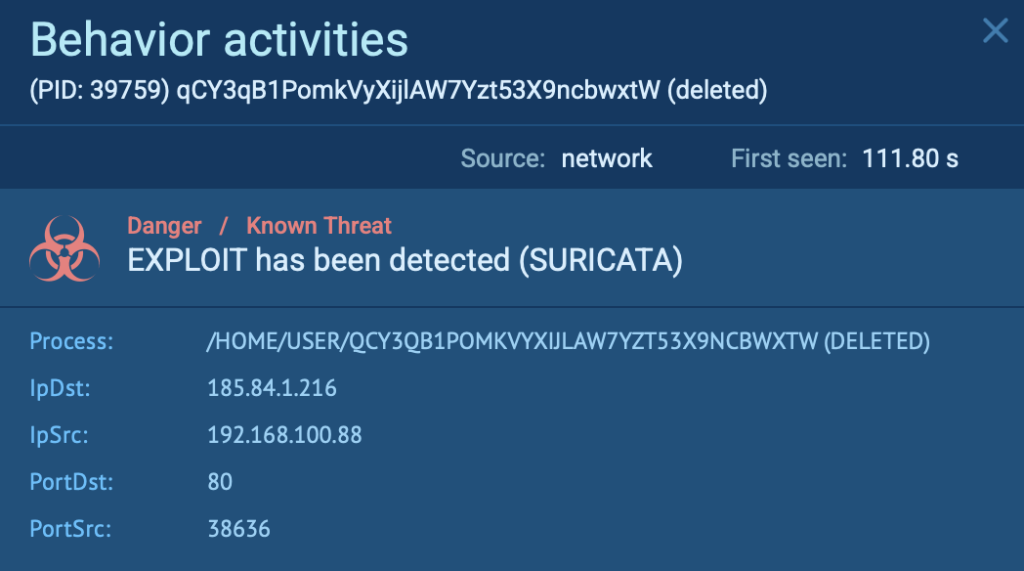
In this analysis session, you can observe the exploit in a controlled environment as it attempts to manipulate system processes.

As you can see, the exploit was automatically flagged by Suricata, providing clear evidence of an active attack.
Why Businesses & Security Teams Should Use ANY.RUN for Linux Malware Detection
By examining network traffic inside ANY.RUN’s Linux Sandbox, businesses and security teams can:
- Detect threats faster: Real-time analysis exposes malware behavior instantly.
- Reduce investigation time: Automated Suricata alerts streamline detection.
- Improve network security: Identify and block malicious traffic before it spreads.
- Get deeper insights: PCAP exports and interactive analysis allow teams to get deeper insights.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post Malware Traffic Analysis in Linux: Hands-on Guide with Examples appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

