How ANY.RUN Helps Healthcare Organizations Against Ransomware: Interlock Case Study
Ransomware attacks have become a relentless threat to the healthcare sector, exposing sensitive patient data, disrupting life-saving treatments, and placing lives at risk. With healthcare systems underfunded and critical infrastructure vulnerable, cybercriminals find this sector an easy and lucrative target.
In recent years, ransomware attacks have not only caused financial losses but have also shaken public trust in healthcare organizations. Hospitals, medical service providers, and even blood donation centers have been hit, leaving a trail of chaos.
This article highlights how healthcare organizations can benefit from ANY.RUN‘s Interactive Sandbox and Threat Intelligence Lookup to identify, investigate, and analyze ransomware attacks, using a real-world case study of the Interlock ransomware group.
The Impact of Ransomware on Healthcare
Before we dive deeper into how ANY.RUN helps counter such threats, let’s examine how devastating ransomware attacks can be across the healthcare sector.
| UnitedHealth | 190 million records stolen in the largest healthcare breach |
| Ascension | 5.6 million patients affected in a Black Basta ransomware attack. |
| Kootenai Health | 464,000 patient records leaked. |
| ConnectOnCall | Exposed the health data of over 910,000 patients in a breach of its SaaS system. |
| Medusind | A December 2023 breach impacted 360,000 individuals, exposing sensitive billing and health information. |
| Anna Jaques Hospital | Ransomware exposed sensitive health data for over 316,000 patients, disrupting critical medical services. |
What’s at stake?
- Loss of patient trust: Exposed personal and health information undermines confidence in healthcare providers.
- Operational disruption: Hospitals and medical facilities are forced to halt services, delaying critical treatments.
- Financial strain: Organizations face ransom demands, legal fees, and recovery costs, compounding the impact.
Why Healthcare Is a Prime Target
- Sensitive data: Patient records are incredibly valuable on the black market. Ransomware groups exploit this by encrypting data and demanding payments for decryption.
- Critical infrastructure: Many healthcare systems cannot afford prolonged downtime due to their role in patient care.
- Underfunded cybersecurity: Many healthcare providers operate on tight budgets, often prioritizing patient services over robust IT defenses.
- Slow detection: A common issue is the inability to identify and respond to attacks in their early stages, which allows ransomware to spread undetected.
Interlock Group: Active Ransomware Threat to Healthcare
Interlock is a ransomware actor that engages in double-extortion.
In late 2024, the Interlock ransomware group launched targeted attacks against multiple healthcare facilities in the United States, causing significant disruptions and exposing sensitive patient data:
- Brockton Neighborhood Health Center: Breached on October 20, 2024, undetected until December 17, 2024.
- Legacy Treatment Services: Attack detected on October 26, 2024.
- Drug and Alcohol Treatment Service: Breach discovered on October 24, 2024.
How ANY.RUN Helps at Different Stages of Interlock Attacks
ANY.RUN provides healthcare organizations with proactive tools to analyze and investigate ransomware attacks at various stages.
Let’s discover how by having a look at the Interlock ransomware group. The stages of the attack are taken from one of the most detailed reports on the threat from Talos, released on January 14, 2025.
1. Initial Compromise (TA0001)
At this stage, the Interlock ransomware group uses the Drive-by Compromise technique to gain access to the victim’s infrastructure.
Drive-by Compromise: How It Happened
The Interlock ransomware group either compromised or newly registered a phishing website, as evidenced by recent registration data in Whois. This phishing site was designed to appear as a news feed, complete with links for downloading software. Unwary users visiting the site were tricked into downloading malicious files.
Here is how ANY.RUN’s Threat Intelligence Lookup could be used by analysts at this stage of the attack.
Early Detection of Malicious Domains
By querying the domain apple-online.shop, ANY.RUN found that users first flagged and analyzed the website on September 6, 2024, almost a month before public mentions of the group appeared in this report.
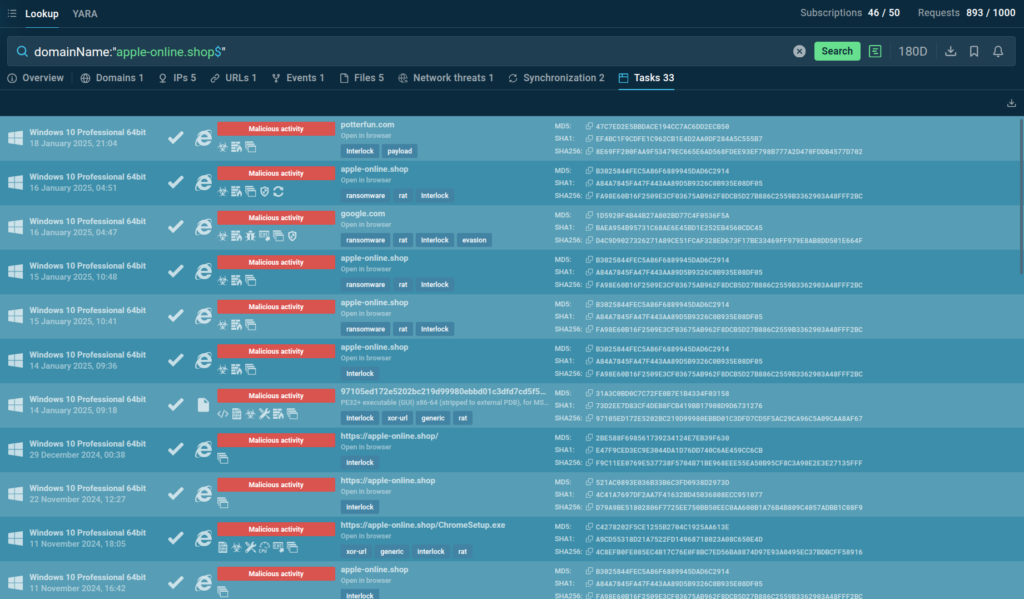
This means ANY.RUN detected suspicious activity nearly two months before the Talos report was published.
Thanks to ANY.RUN’s access to public samples of the latest cyber threats from around the world, users of TI Lookup were able to identify Interlock’s domain as malicious before public reports. With such early detection, healthcare organizations can take preventative measures long before public alerts are raised.
Understanding Website Content
With the help of ANY.RUN’s Interactive Sandbox, you can view how the malicious website looked like and what content was used to deceive users. By analyzing such sites, healthcare organizations can train employees to recognize and avoid similar threats in the future.
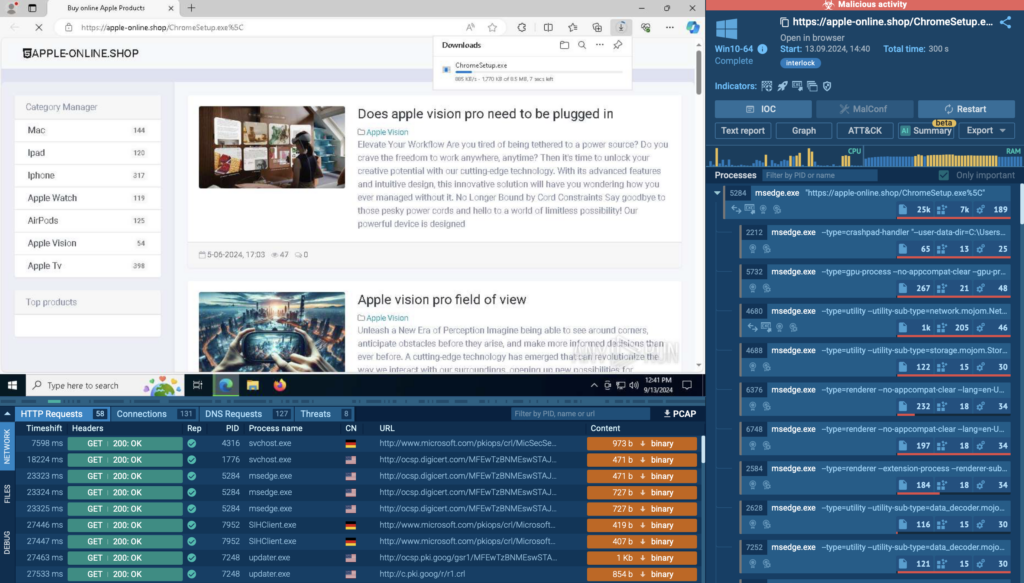
The virtual machine allows anyone to see the behavior of this threat and interact with it in real time.
Expanding on Known Threat Information
ANY.RUN’s data can also enrich users’ existing knowledge of the attack.
While reports stated that the attackers used malware disguised as a Google Chrome updater, ANY.RUN uncovered additional tactics, such as mimicking MSTeams and MicrosoftEdge updates (evident in filenames like MSTeamsSetup.exe and MicrosoftEdgeSetup.exe).
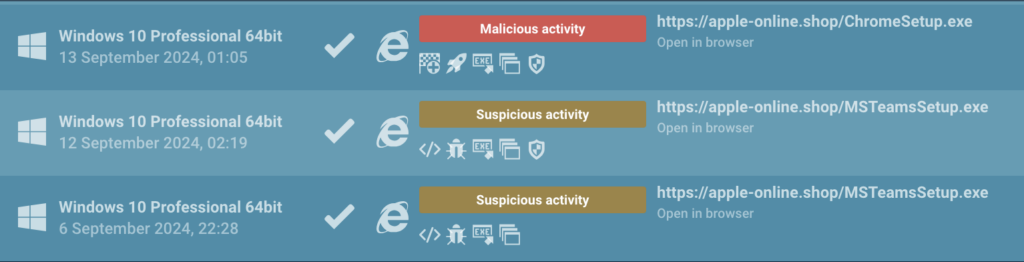
This shows that by identifying alternative disguises used for malware, ANY.RUN equips organizations to anticipate a broader range of file disguises utilized by Interlock.
IOCs and File Analysis
Reports mentioned a specific file named upd_2327991.exe used in the attack. ANY.RUN’s database reveals additional files with similar naming conventions, such as:
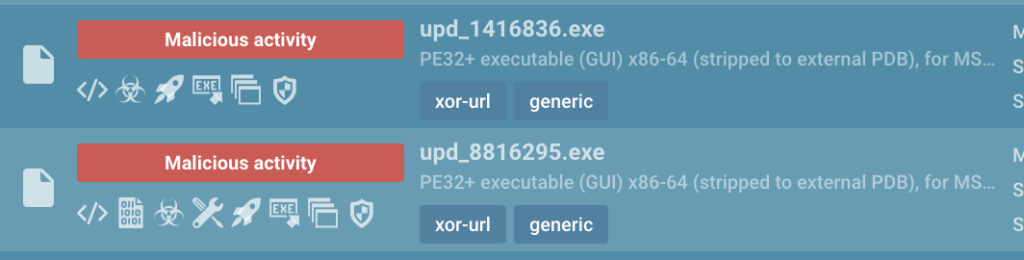
This suggests that the attackers generated file names using random alphanumeric patterns. Each file had distinct hash values (SHA256), which serve as unique Indicators of Compromise (IOCs):
- 8d911ef72bdb4ec5b99b7548c0c89ffc8639068834a5e2b684c9d78504550927
- 97105ed172e5202bc219d99980ebbd01c3dfd7cd5f5ac29ca96c5a09caa8af67
The analysis showed that with the help of ANY.RUN’s TI Lookup and Interactive Sandbox, healthcare organizations facing Interlock ransomware attacks could:
- Discover the Start Date of Attacks: Get information about the first activities of the attacking group, which often happen before public reports.
- Study the Attacker’s Setup: Identify the domains, IP addresses, and other parts of the attacker’s setup to learn more about their tactics and methods.
- Improve Detection Systems: Collect additional IOCs to configure defensive mechanisms and improve attack detection.
2. TA0002: Execution
Once attackers gain initial access, the Execution phase begins. This stage involves deploying malicious payloads or executing harmful commands on the compromised device. In the Interlock ransomware attacks, users unknowingly launch a fake updater file, triggering the execution of malware and allowing attackers to establish control over the victim’s system.
How Interlock Group Executes Their Attacks
The reports revealed that the attackers leveraged Remote Access Tools (RATs), which provided them with full control of the infected machine. By disguising these RATs as legitimate software, such as Chrome, MSTeams, or Microsoft Edge updaters, the attackers ensured that their actions remained unnoticed until significant damage was done.
Detecting Encrypted URLs in Fake Updaters
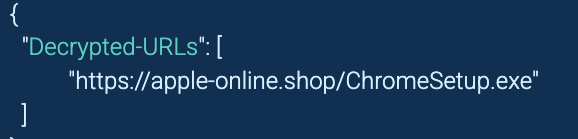
With ANY.RUN Sandbox, analysts could uncover that the fake-updater contained encrypted URLs used to communicate with the attackers’ infrastructure. For example, the xor-url tag in ANY.RUN revealed hidden URLs within the malware’s configuration files.
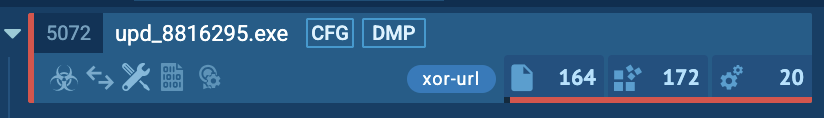
By clicking on the CFG (Configuration) option in the sandbox, analysts can view decrypted URLs. These insights provide actionable intelligence about the malware’s communication methods and help identify similar patterns in future attacks.
Using YARA Search to Find More Samples
ANY.RUN’s YARA Search functionality allowed researchers to create a rule for detecting RAT samples linked to the attack.
Here’s an example of a YARA rule tailored for identifying Interlock’s disguised RAT samples:
rule Interlock_RAT {
strings:
$ = "/MSTeamsSetup.exe\" xor
$ = "/ChromeSetup.exe\" xor
$ = "/MicrosoftEdgeSetup.exe\" xor
condition:
any of them
} This YARA rule uncovered over 44 new malicious files, each representing a new indicator.
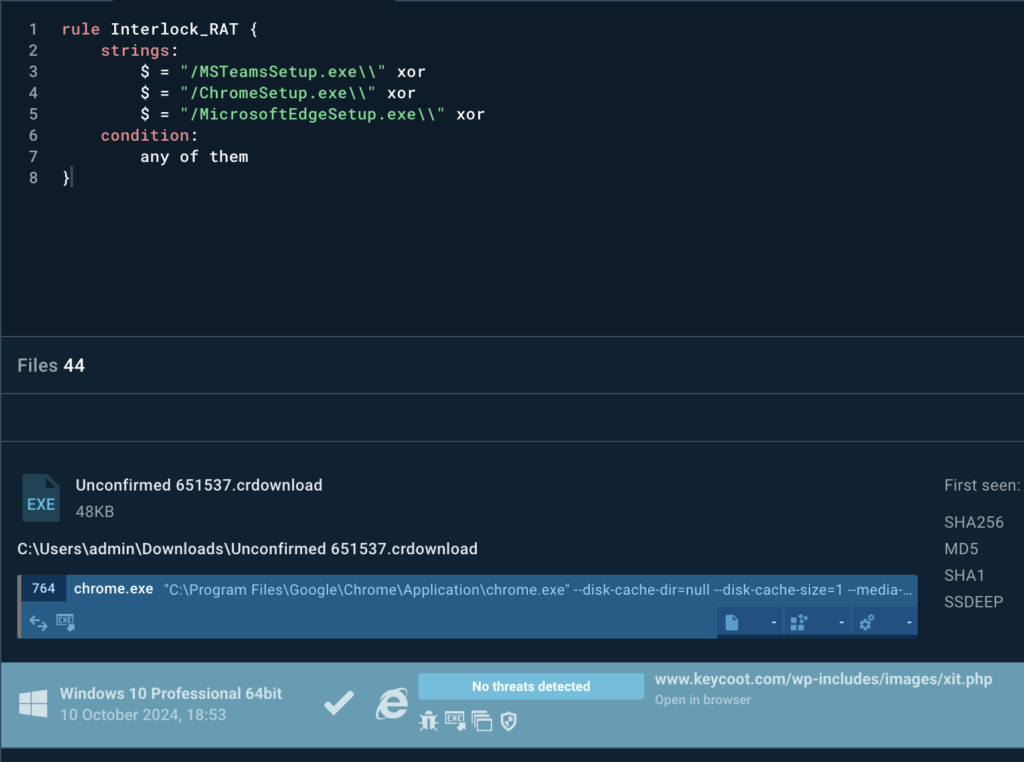
These IOCs can be added to detection systems, expanding the scope of protection.
Discovering Additional IOCs
In addition to detecting malicious files, ANY.RUN’s sandbox session revealed network IOCs such as URLs and IP addresses that previously were not covered in other reports.
The URL shown above was not included in the detailed report from Talos.
Had the organizations encountering this URL and payload used ANY.RUN’s Interactive Sandbox, they would be able to run the RAT in a safe virtual environment and see its malicious nature. This could have prevented them from detonating the payload on their own systems.
During Execution, ANY.RUN helps users:
- Discover IOCs: Find additional file and network IoCs, including those found in configurations.
- Find Unknown Threats: Discover previously unknown threats.
- Analyze Threats: Safely explore suspicious URLs and detonate payloads.
3. TA0006: Credential Access
Once attackers gain the ability to execute commands on a compromised system, their next move often involves stealing access credentials. In the Interlock ransomware attack, the group employed a custom stealer tool to gather and exfiltrate these credentials.
How Credential Stealing Works in This Attack
- The attackers’ stealer was designed to collect sensitive data, including usernames, passwords, and other access credentials.
- According to vendor reports, the stolen data was stored in a file named “chrgetpdsi.txt.” This file served as a repository for harvested credentials before exfiltration.
Let’s use TI Lookup to find more information on the stealer:
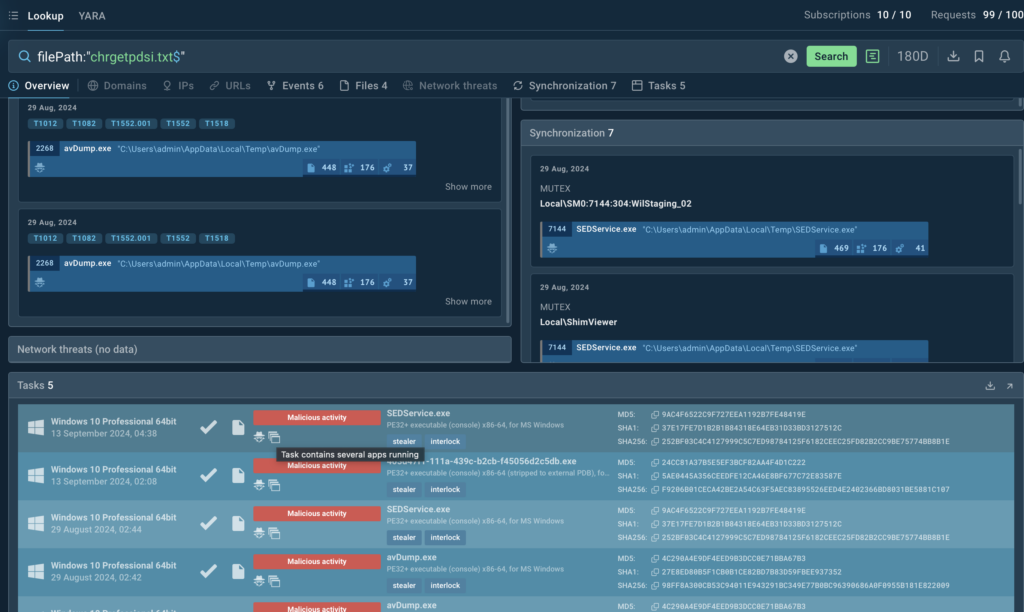
As a result, we see that the Stealer had been detected by ANY.RUN as early as August 2024, well before users began investigating the compromised domain.

Early detection of malicious tools like this Stealer provides security teams with actionable intelligence to defend against evolving threats.
4. TA0008: Lateral Movement
At the Lateral Movement phase, attackers aim to spread across the network, gaining access to additional systems and resources.
The Interlock ransomware group moved laterally within networks using legitimate remote administration tools like Putty, Anydesk, and RDP. These tools are often abused by attackers to access additional systems undetected.
| TI Lookup Queries | |
|---|---|
| Putty | threatName:”putty” |
| Anydesk | threatName:”anydesk” |
| RDP | threatName:”rdp” |
The ANY.RUN Sandbox excels at identifying the presence of these tools when they are abused for malicious purposes.
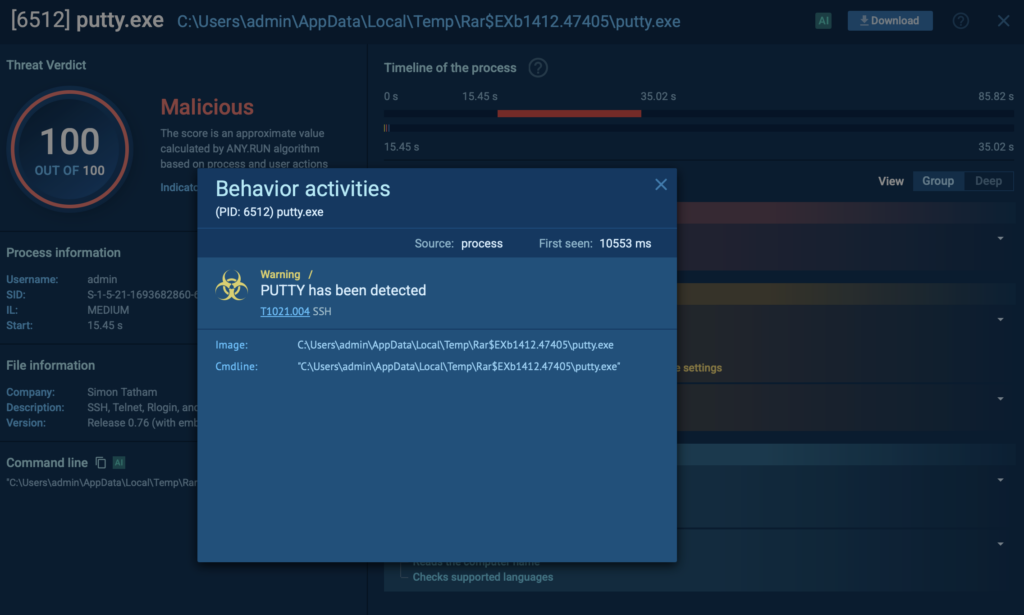
By executing suspicious files in a controlled environment, ANY.RUN can:
- Detect the execution of Putty, Anydesk, or RDP-related activities.
- Provide detailed insights into how these tools are being used by attackers.

5. TA0010: Data Exfiltration
In the Data Exfiltration phase, attackers transfer stolen data out of the victim’s network. The Interlock ransomware group used Azure cloud storage to exfiltrate data.
Inside the ANY.RUN sandbox, you can see the system configuration data being sent to a Command and Control (C2) server via the RAT.
ANY.RUN captures data sent by the RAT to attacker-controlled servers. For this example, logs revealed information sent to IP 217[.]148[.]142[.]19 over port 443:
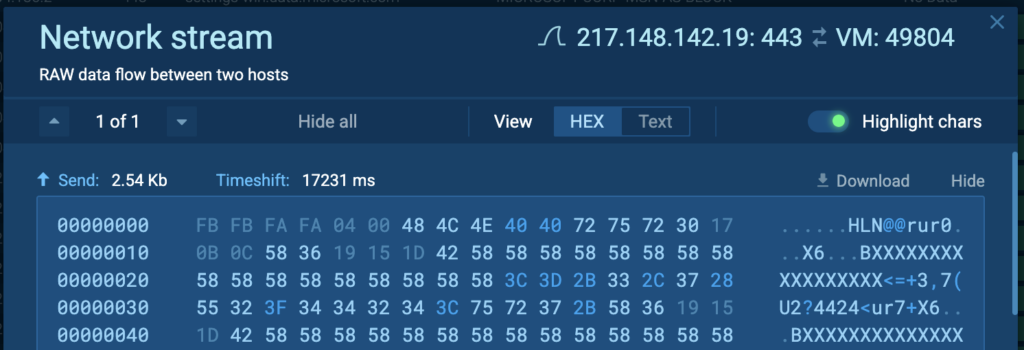
Using tools like CyberChef, we can decrypt the logged traffic (e.g., XOR-encrypted data) to identify what attackers exfiltrated.
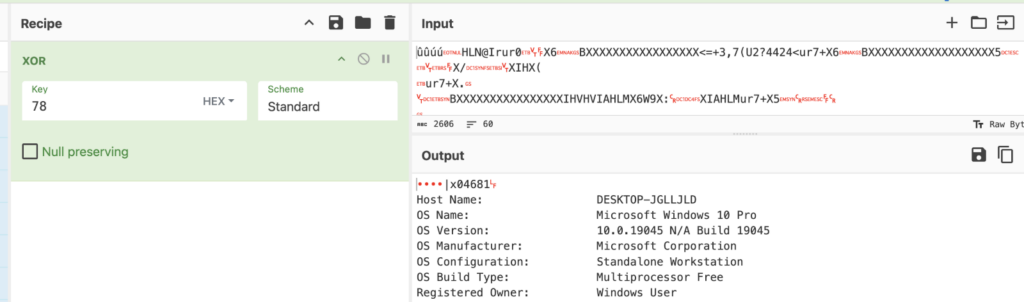
Thus, during the Data Exfiltration phase, ANY.RUN Sandbox logs traffic sent to external systems, allowing analysts to identify exactly what data is being transmitted to the attacker’s server.
ANY.RUN’s Key Benefits for Healthcare Organizations
ANY.RUN empowers healthcare organizations with fast, safe, and effective tools to investigate and analyze cyber threats:
- Pin malicious indicators to actual threats to gain a better understanding of the risks your organization is facing.
- Receive in-depth reports with IOCs, TTPs, and malware behavior summaries.
- Simplify and speed up threat analysis for SOC team members at all levels, saving time and increasing productivity.
- Accelerate the alert triage process and reduce the workload through fast operation speeds, a user-friendly interface, and smart automation.
- Safely examine sensitive data in a private mode, ensuring compliance with cybersecurity and data protection requirements.
- Gain access to detailed insights into malware’s behavior and better understand threats to streamline incident response.
- Collaborate with team members, share results, and coordinate efforts efficiently during incident handling.
- Optimize the cost of responding to incidents by accessing detailed data with ANY.RUN’s interactive analysis, which helps in developing new detection and protection methods.
Conclusion
ANY.RUN can be an invaluable tool at various stages of ransomware attacks. During incident investigations, TI Lookup can provide critical data on the threat at hand. Running malware in the ANY.RUN Sandbox before executing it on a local machine allows for a proactive identification of the threat and thorough analysis of its behavior.
By combining ANY.RUN’s tools, healthcare organizations can not only enhance the understanding of the threats’ capabilities but also ensure that they are identified and mitigated effectively.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post How ANY.RUN Helps Healthcare Organizations Against Ransomware: Interlock Case Study appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

