How to Prevent a Ransomware Attack on a Business: A Lynx Malware Use Case
Lost documents, stolen code, exposed customer data, and a falling stock price are all common consequences of just one click on a ransomware file. To avoid this problem, you need proper security tools and, most importantly, knowledge of how ransomware attacks are carried out.
This quick guide will explain how ransomware works and the simple steps you can take to protect your business.
What is ransomware
Ransomware is a type of malicious software designed to block access to a computer system or data until a sum of money (ransom) is paid. It typically encrypts the victim’s files, making them inaccessible, and demands payment to provide the decryption key. The ransom demands can range from hundreds to thousands of dollars, often paid in cryptocurrencies like Bitcoin to maintain anonymity.
What is double extortion ransomware
Double extortion is a technique where attackers not only encrypt the victim’s data but also exfiltrate (steal) it. They threaten to leak the stolen data publicly if the ransom is not paid, adding an additional layer of pressure on the victim to comply.
This technique increases the likelihood of payment, as victims face both data loss and potential reputational damage or legal consequences from data breaches.
Why your company may become a target of ransomware
The chance of your company to become a potential target of ransomware depends on several factors:
- Size and Industry: Larger organizations and those in critical industries like healthcare, finance, and government are often targeted due to their sensitive data and higher likelihood of paying substantial ransoms.
- Cybersecurity Posture: Companies with weak or outdated cybersecurity measures are more vulnerable. This includes lack of regular software updates, inadequate backup strategies, and insufficient employee training on cybersecurity best practices.
- Data Value: Organizations that handle valuable or sensitive data, such as personal information, intellectual property, or confidential business data, are more attractive targets.
- Public Profile: High-profile companies or those with a significant public presence may be targeted for the potential reputational damage that a data breach could cause.
- Previous Incidents: Companies that have experienced cybersecurity incidents in the past may be seen as easier targets, especially if they have not adequately addressed the vulnerabilities that led to the previous attacks.
How criminals prepare and deliver ransomware
Setup process
Most criminals use ready-made ransomware-as-a-service builders to create and configure their malware. These builders allow them to specify various parameters of the ransomware, such as the ransom message, amount, and Bitcoin address for payment.
Consider the Chaos ransomware, which provides a builder that allows the operator to set up their custom variant of the malware by clicking a few buttons.
View analysis of the Chaos builder
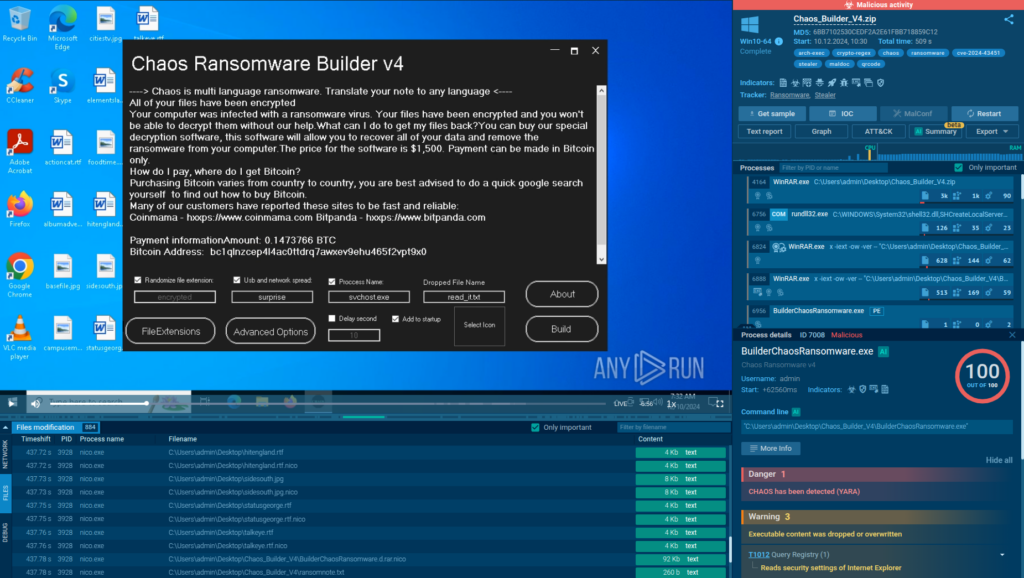
To safely examine the Chaos builder and its executable, we need to upload it to a cloud sandbox like ANY.RUN.
As shown by Nico Knows Tech in this YouTube video, attackers can configure their Chaos build to choose the ransom message and amount, as well as set the extension for the encrypted files.
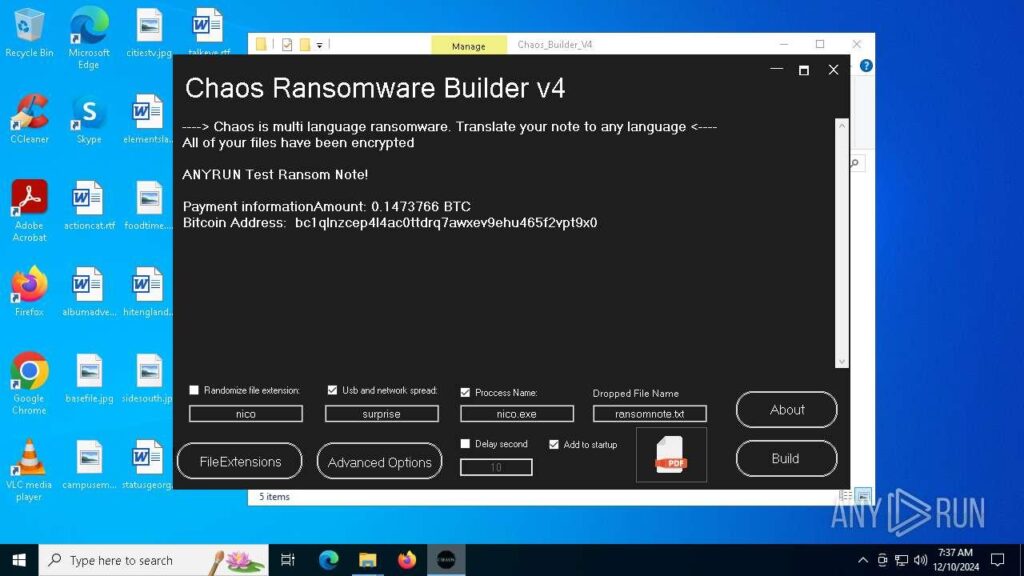
As a means of disguise, attackers can change the logo of the main malicious executable file to a PDF one. Coupled with the hidden extension, this can trick users into opening it, thinking it is a standard document.
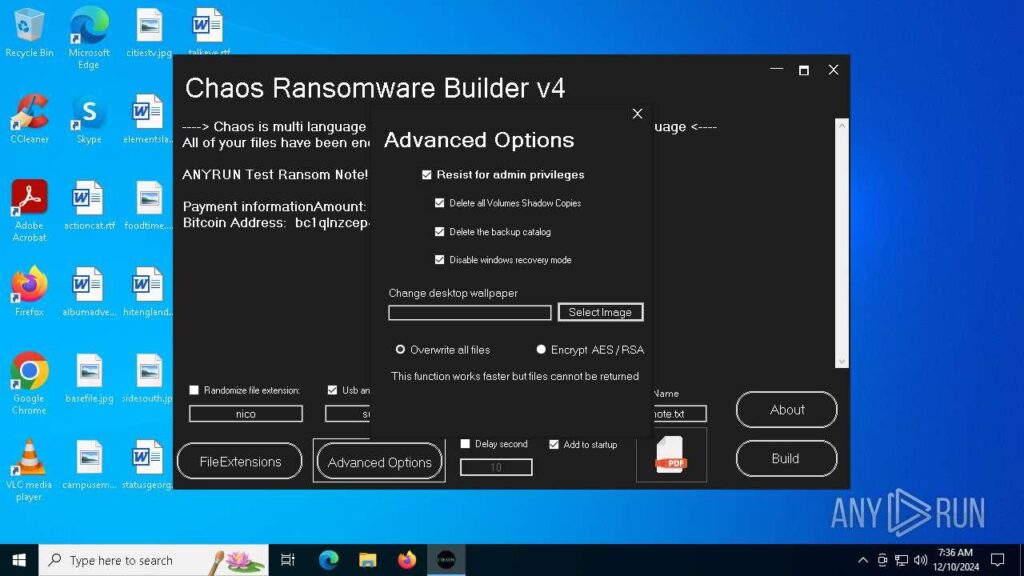
To avoid detection by antivirus and other security solutions, the builder makes it possible to enable deleting shadow copies, disabling system recovery, and overwriting files to make them unrecoverable.
Delivery
After this quick setup process, the criminals are ready to distribute the ransomware among their targets. There are many delivery methods, but here are three common ones:
- Emails that include malicious file attachments, such as PDFs or Word documents, which execute ransomware when opened.
- Emails that contain links to compromised websites or malicious downloads, manipulating users into downloading and executing ransomware.
- Malicious advertisements on websites like Google that redirect users to sites hosting ransomware.
A Ransomware Attack Example: Lynx
Let’s now see what happens once the malware file arrives at the target’s system.
For this, we can take a look at the Lynx ransomware, which was recently reviewed by PC Security Channel.
The operators behind this threat maintain a public website containing a list of their victims along with samples of stolen documents. One of the latest cases was a large electricity provider from Romania, Electric Group, that serves over 3.8 million people.
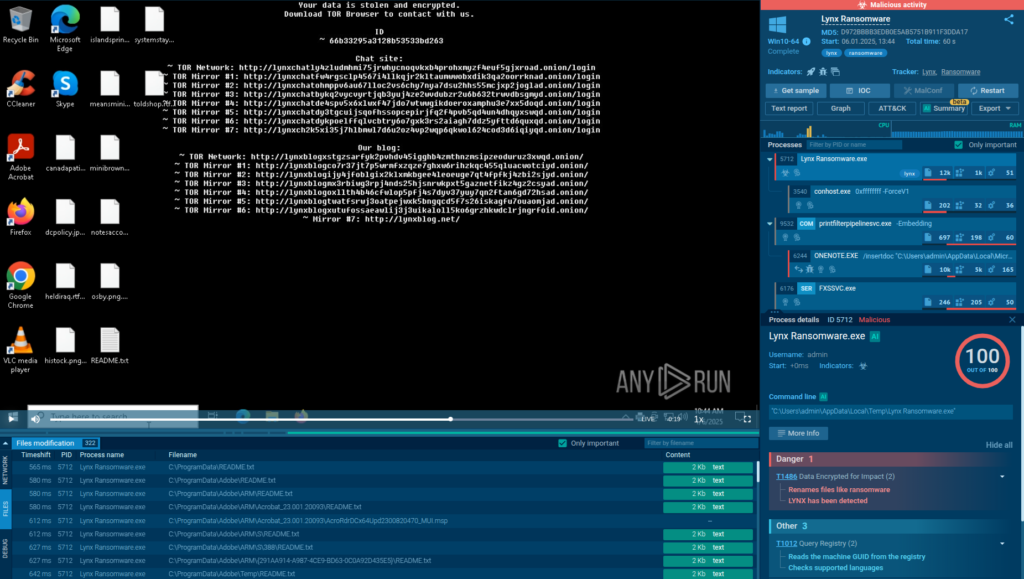
Thanks to ANY.RUN’s Interactive Sandbox, we can study the entire chain of attack and see exactly how this threat operates in a safe virtual environment.
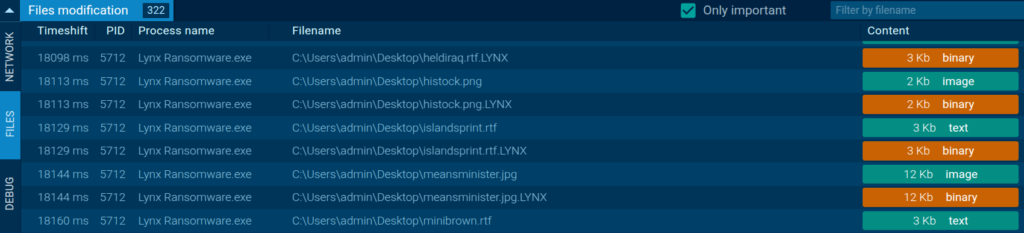
As soon as we upload and launch the malicious executable file in ANY.RUN’s cloud-based sandbox, the malware begins encrypting files on the system and changing their extension to .LYNX.
It also drops a ransom note and replaces the desktop wallpaper with the ransom text, which contains a link to a TOR site via which the attackers expect the victim to contact them.
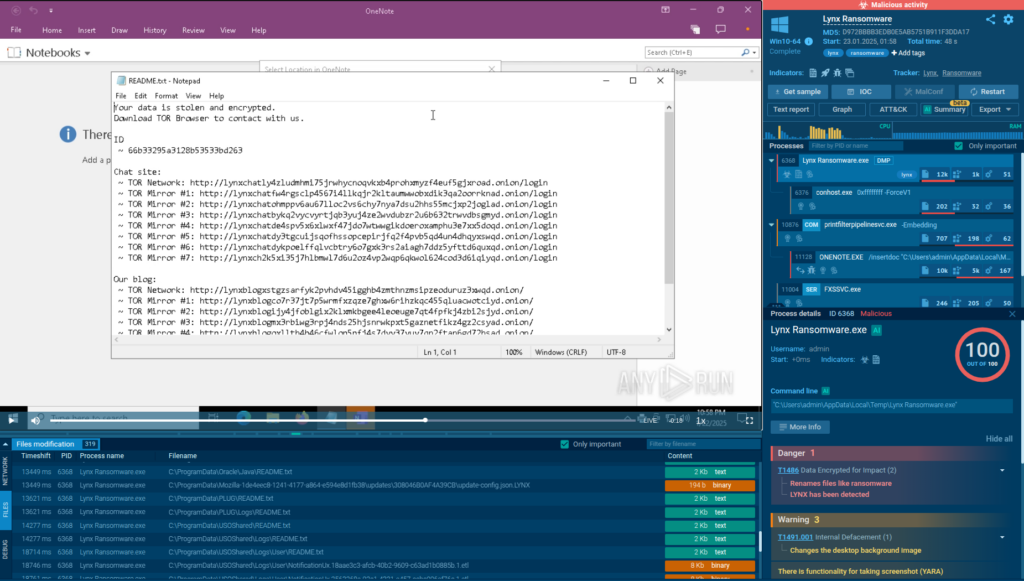
ANY.RUN’s interactivity lets us manually open the README.txt dropped by Lynx to see the message.
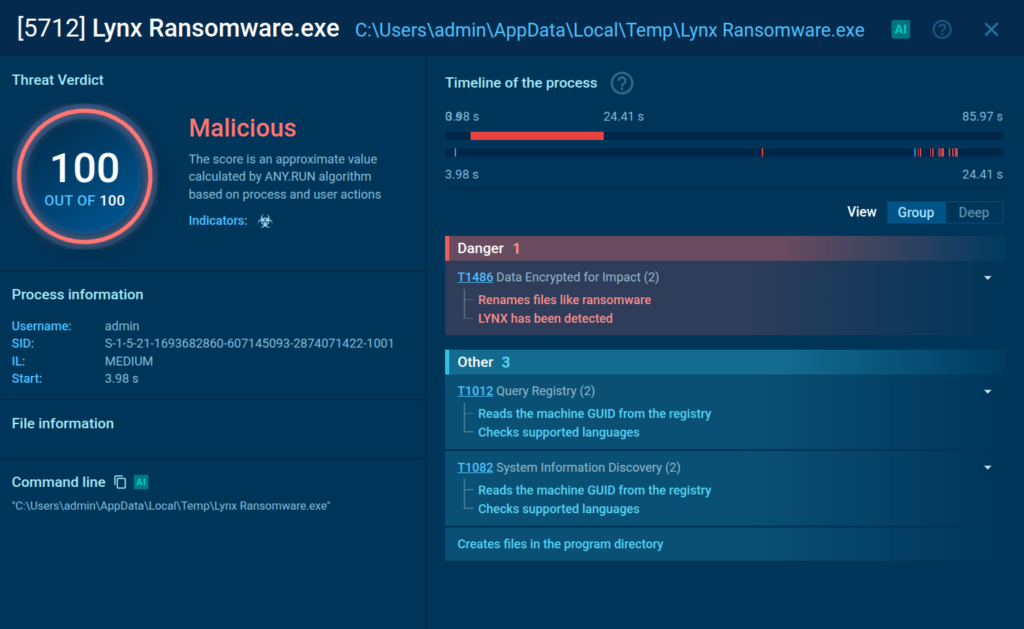
The ANY.RUN sandbox detects all the malicious activities performed by Lynx and marks them with signatures.
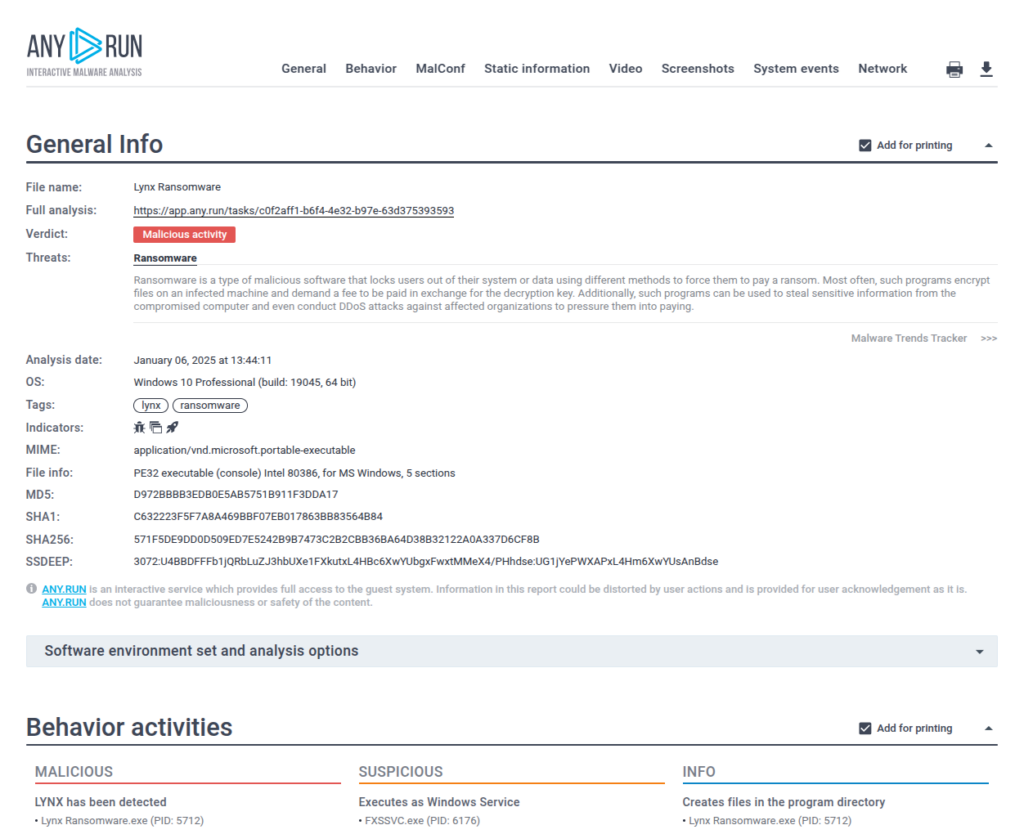
The sandbox also generates a comprehensive report on the analyzed threat sample that can be shared with all the stakeholders in the company.
How Sandboxing Helps Businesses Prevent Ransomware Attacks
As demonstrated by the Lynx analysis, sandbox tools like ANY.RUN provide you with a safe, secure, and private environment for detonating and exploring all the suspicious files and URLs you may come across in your day-to-day activities.
Whether it is a phishing email, an unusual executable, or an office document asking you to enable macros, uploading these to ANY.RUN’s Interactive Sandbox is the best course of action you can take to check these files for any possible threat and quickly make a decision on whether to engage with them further on your own system.
More than 500,000 security professionals use ANY.RUN for proactive analysis to:
- Simplify and speed up threat analysis for SOC team members at all levels, saving time and increasing productivity.
- Accelerate the alert triage process and reduce the workload through fast operation speeds, a user-friendly interface, and smart automation.
- Safely examine sensitive data in a private mode, ensuring compliance with cybersecurity and data protection requirements.
- Gain access to detailed insights into malware’s behavior and better understand threats to streamline incident response.
- Collaborate with team members, share results, and coordinate efforts efficiently during incident handling.
- Optimize the cost of responding to incidents by accessing detailed data with ANY.RUN’s interactive analysis, which helps in developing new detection and protection methods.

Conclusion
Taking proactive measures to understand and mitigate ransomware threats is vital for business security. Tools like ANY.RUN’s Interactive Sandbox offer a fast, simple, and effective solution for analyzing potential threats, enabling businesses to prevent attacks from compromising their infrastructure. By integrating such tools into your security strategy, you can enhance your cybersecurity posture and protect your business from the far-reaching consequences of ransomware attacks.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post How to Prevent a Ransomware Attack on a Business: A Lynx Malware Use Case appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


