What’s Inside ANY.RUN’s Cyber Threat Intelligence Feeds?
ANY.RUN’s Threat Intelligence (TI) feeds provide an invaluable solution for organizations seeking to detect and mitigate the latest malware and phishing campaigns, attacks, and cybercriminal tactics.
But what exactly is inside these feeds, and how can they help companies strengthen their cybersecurity?
Let’s dive into the details.
What Are ANY.RUN’s Threat Intelligence Feeds?
ANY.RUN’s Threat Intelligence (TI) feeds are a comprehensive collection of Indicators of Compromise (IOCs) that can expand security systems’ threat detection capabilities. These feeds don’t just give you the basics, they go deep, providing malicious IPs, URLs, domains, file hashes, and even links to actual analysis sessions, showing you how threats behave.
Where does this data come from? An international community of over 500,000 researchers and cybersecurity pros who upload and analyze real-world malware and phishing samples every day to ANY.RUN’s Public submissions repository.
With TI Feeds from ANY.RUN, organizations can:
- Expand Threat Coverage: Extend your security systems’ ability to detect emerging malware and phishing attacks.
- Improve Incident Response: Enrich incident response processes with contextual data from the feeds, providing deeper insights into threats and their behaviors.
- Strengthen Security Posture: Ensure proactive defense against new and evolving threats.
- Optimize Threat Hunting: Streamline threat hunting activities, identifying and investigating potential threats more efficiently.
Key Features of ANY.RUN’s CTI Feeds
Here’s what makes ANY.RUN’s CTI feeds valuable for cybersecurity teams:
- Fresh Data: Contain data extracted from the latest public samples uploaded to our interactive sandbox by a global network of over 500,000 security professionals.
- Actionable Indicators: Supply indicators from decompressed traffic, memory dumps, and malware configurations along with those manually collected by our team of malware analysts, as well as data from partners and OSINT sources.
- Contextual Information: Offer more than just IOCs by providing direct links to full sandbox analysis sessions that include memory dumps, network traffic, and events.
- Rigorous Pre-Processing: Use advanced algorithms and proprietary technology for data filtering and validation.
- Continuous Updates: Updated every few hours, helping security teams stay ahead of emerging threats and respond quickly to new threats.
- STIX and MISP Formats: Deliver threat intelligence feeds in the STIX and MISP formats, making it easy for security teams to integrate our data into their existing infrastructure.
- API Support: Integrate into existing security systems via API for real-time threat updates and automated responses.
What’s Inside ANY.RUN’s CTI Feeds?
The IOCs include information on malicious IP addresses, domain names, and URLs, enriched with contextual details such as related files and ports. Here’s a closer look at what’s inside:
IP addresses
IP addresses are important for detecting and preventing malicious network activity. They serve as digital markers of cybercriminal operations, often linked to Command-and-Control (C2) servers or phishing campaigns.
By analyzing IP addresses, cybersecurity teams can:
- Identify malicious sources: Pinpoint harmful traffic and proactively block it.
- Trace attack origins: Gain insights into the geolocation and tactics of attackers.
- Monitor threat patterns: Detect repeated use of IPs across campaigns.
- Enhance network security: Use IP-based firewalls and intrusion prevention systems (IPS) to block unwanted traffic.
Example:
type: ipv4-addr
id: ipv4-addr--75725b48-17a3-575d-a5de-b5d9798bde8d
value: 103.168.67.9
created: '2024-06-13T06:26:00.704Z'
modified: '2024-06-13T06:26:00.704Z'
external_references:
- source_name: ANY.RUN task 11ce507f-d535-4bf1-8973-989d7654017a
url: https://app.any.run/tasks/11ce507f-d535-4bf1-8973-989d7654017a
labels:
- RedLine
related_objects:
- relationship_type: contains
source_ref: ipv4-addr--75725b48-17a3-575d-a5de-b5d9798bde8d
target_ref: file--49ef9153-94eb-5d05-bac2-19a54738afab
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 90
revoked: falseANY.RUN’s TI feeds don’t just list malicious IPs. They provide detailed context that turns raw data into actionable insights for cybersecurity teams. This enriched information helps assess the behavior and impact of each IP. Here’s what’s usually included:
- External references: Links to relevant sandbox sessions.
- Label: Name of the malware family or campaign.
- Detection timestamps: “Created” and “Modified” dates provide a timeline to understand if a threat is ongoing or historical.
- Related objects: IDs of files and network indicators related to the object in question.
- Score: Value representing the severity level of the IOC.
- Revoked: Field indicating whether the IOC has been invalidated.
Domains
Domains play a crucial role in hosting malicious content, phishing campaigns, and distributing malware. They are often used as staging points for cyberattacks, making them a key focus for threat detection and mitigation.
ANY.RUN’s TI feeds provide comprehensive information about domains, including all the details available for IP addresses, such as threat names, types, detection timestamps, and related file hashes.
Example:
type: domain-name
id: domain-name--f17dd142-08ac-54cb-bb88-97f1e07fb6fc
value: mail.sdil.ac.ir
created: '2024-06-10T21:13:17.465Z'
modified: '2024-06-17T13:37:53.620Z'
external_references:
- source_name: ANY.RUN task 64e1d470-dcd4-4d78-b1f0-aa4d9bd6f225
url: https://app.any.run/tasks/64e1d470-dcd4-4d78-b1f0-aa4d9bd6f225
- source_name: ANY.RUN task 090c21da-a050-4f88-bb09-1bae142df1cb
url: https://app.any.run/tasks/090c21da-a050-4f88-bb09-1bae142df1cb
labels:
- AgentTesla
related_objects:
- relationship_type: contains
source_ref: domain-name--f17dd142-08ac-54cb-bb88-97f1e07fb6fc
target_ref: file--dbee2af2-3be4-5e2a-9bf3-94e3fe8637b3
- relationship_type: contains
source_ref: domain-name--f17dd142-08ac-54cb-bb88-97f1e07fb6fc
target_ref: file--9794dd40-085a-5c84-8d95-70cbd8efcf1d
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 100
revoked: falseKeep in mind that domains provide a higher-level view of malicious activity, often connecting multiple IPs or malware instances within a single campaign.
URLs
URLs play a significant role in cybercriminal operations, often serving as gateways to distribute malware, execute phishing campaigns, or redirect users to malicious content. Their flexibility and ease of use make them a preferred tool for attackers.
How URLs are used:
- Malware delivery: Embedded in emails or websites, URLs download malware or redirect to exploit kits.
- Phishing campaigns: Lead users to fake websites designed to steal sensitive information.
- Command-and-Control (C2): Facilitate communication between malware and attackers for issuing commands or data exfiltration.
- Exploitation and redirection: Redirect victims to malicious sites hosting drive-by downloads or exploits.
By analyzing URLs, cybersecurity teams can uncover attack patterns, block harmful traffic, and prevent unauthorized access to systems and data.
Example:
type: url
id: url--001c0f70-93f8-583d-96ce-7c260da3a193
value: http://www.goog1evip15.com/dogw/
created: '2024-06-11T21:35:59.640Z'
modified: '2024-06-11T21:35:59.640Z'
external_references:
- source_name: ANY.RUN task 55051854-38c4-4d03-a70a-6dd2ce3d89ca
url: https://app.any.run/tasks/55051854-38c4-4d03-a70a-6dd2ce3d89ca
labels:
- Formbook
related_objects: []
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 100
revoked: falseNote that URLs often serve as entry points for malicious activity, acting as gateways for malware delivery, phishing attacks, or redirection to exploit kits, making them critical for identifying and mitigating cyber threats.
Additional Indicators in ANY.RUN’s TI Feeds
In addition to the core Indicators of Compromise (IOCs) such as URLs, domains, and IPs, ANY.RUN’s CTI feeds include a wealth of contextual information.
This additional data enriches the IOCs, offering deeper insights into the nature and behavior of each indicator.
Files
For file indicators, ANY.RUN’s CTI feeds provide detailed information to help identify and assess malicious files. Here are the key data fields included:
Example:
type: file
id: file--249382b0-209d-5904-b725-b47663c6c412
hashes:
SHA-256: d564eb94afb174fe3b854de086eda2a4e015d778a9aea9806e79f82044eac74e
SHA-1: 14b96459dff641245aea6dacd34512830d945ee2
MD5: 5edee175c5003771dea841893ea46602
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 100
file_name: d564eb94afb174fe3b854de086eda2a4e015d778a9aea9806e79f82044eac74e.exe
- type: url
id: url--d65b67ec-39f2-5309-8cc9-56e016b6a48f
value: http://109.248.151.196/rvBZyVEAb230.bin
created: '2024-06-11T18:44:15.898Z'
modified: '2024-06-11T18:44:15.898Z'
external_references:
- source_name: ANY.RUN task 35d75e14-c1a2-418c-b98f-f7d58cca93cb
url: https://app.any.run/tasks/35d75e14-c1a2-418c-b98f-f7d58cca93cb
labels:
- guloader
related_objects:
- relationship_type: contains
source_ref: url--d65b67ec-39f2-5309-8cc9-56e016b6a48f
target_ref: file--249382b0-209d-5904-b725-b47663c6c412
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 100
revoked: falsePorts
Port indicators describe network activities related to specific port usage, offering insights into malicious connections.
Example:
type: port
id: port--60027215-4cf1-5773-bef7-62051468dbd3
port_value: 5555
created: '2024-06-16T02:32:35.010Z'
modified: '2024-06-16T02:32:35.010Z'
labels:
- NjRat
related_objects:
- relationship_type: services
source_ref: domain-name--8ee2a029-d3e7-53f1-84fb-bee3008c0060
target_ref: port--60027215-4cf1-5773-bef7-62051468dbd3
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 100Integrate ANY.RUN’s TI Feeds
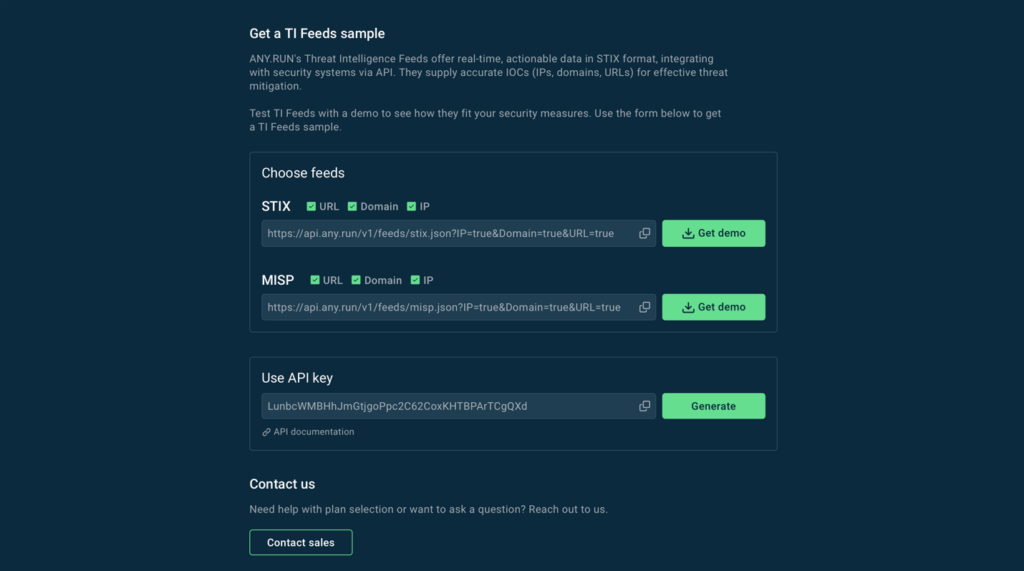
You can test ANY.RUN’s Threat Intelligence Feeds in STIX and MISP formats completely for free by getting a free demo sample here.
ANY.RUN also runs a dedicated MISP instance that you can syncronize your server with or connect to your security solutions. To get started, contact our team via this page.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Get a 14-day free trial of ANY.RUN’s Threat Intelligence service →
The post What’s Inside ANY.RUN’s Cyber Threat Intelligence Feeds? appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

