How to protect yourself from someone tracking you with stalkerware or an AirTag | Kaspersky official blog
These days, it’s not just government agencies or private detectives who can spy on you. Tracking has become so easy and cheap that jealous spouses, car thieves, and even overly suspicious employers are doing it. They don’t have to peek around corners, hide in stores, or even get close to their target at all. A smartphone and a Bluetooth tracking beacon — like an Apple AirTag, Samsung Smart Tag or Chipolo — will do the job perfectly. According to one of the lawsuits filed against Apple, this method of spying is used in a variety of crimes — from stalking ex-partners to planning murders.
Luckily for all of us, there’s protection! As part of Kaspersky’s anti-stalking campaign, we’ll explain how you could be tracked and what you can do about it.
Online and offline tracking
Surveillance of a victim is typically carried out in one of two ways.
Method one: purely software-based. A commercial tracking app is installed on the victim’s smartphone — we call this category of apps stalkerware or spouseware. Such apps are often marketed as “parental control apps”, but they differ from legitimate parental controls because the app’s activity is kept hidden after installation. Most often, the app is entirely invisible on the device, though sometimes it disguises itself as something innocuous, like a messenger, game or photo-gallery app. Stalker apps can repeatedly transmit the victim’s geolocation to a server, send messages and other confidential data from the device to an attacker, and even activate the microphone to record audio.
The main drawback of stalkerware for the attacker is the difficulty of installation — it requires gaining access to the victim’s unlocked smartphone for some time. That’s why, in many cases, especially when it’s an ex-partner or car thief doing the stalking, they use the other method.
Method two: a wireless beacon. A tracking device is planted on the victim. In a car, it might be hidden in an inconspicuous spot, such as behind the license plate; for a person, the tracker could be slipped into a bag or among other personal items.
Originally, Bluetooth trackers — small devices about the size of a coin — were invented to help locate lost belongings such as keys, wallets or luggage. However, if planted on a target, their movements can be tracked in near real-time using a special app. Incidentally, many of today’s Bluetooth headphones also have built-in tracking functionality to make them easier to find — and these too can be used for stalking. So, if you happen to find a pair of fancy headphones lying around, don’t start thinking it’s your lucky day — they may have been deliberately planted in order to track your movements, even after you pair them with your own smartphone.
Tracking technology works even if the beacon is well beyond the Bluetooth range of the stalker’s smartphone: other smartphones help locate the “lost” item. Many of the latest Android and iOS devices report the location of nearby visible beacons to the central servers of Google or Apple. As a result, these tech giants are able to locate any beacon if there’s any modern Bluetooth-enabled smartphone with internet access nearby.
The most popular beacon is still the Apple AirTag, and Apple has gone to a lot of trouble since the first product launch to protect users from malicious use of the tracker. The latest AirTags start beeping to attract attention if they remain away from their owner’s smartphone for too long. However, attackers can easily bypass this protection by damaging the speaker on the tracker. Such hacked tags with disabled speakers can even by bought — easily.
How to protect yourself from surveillance
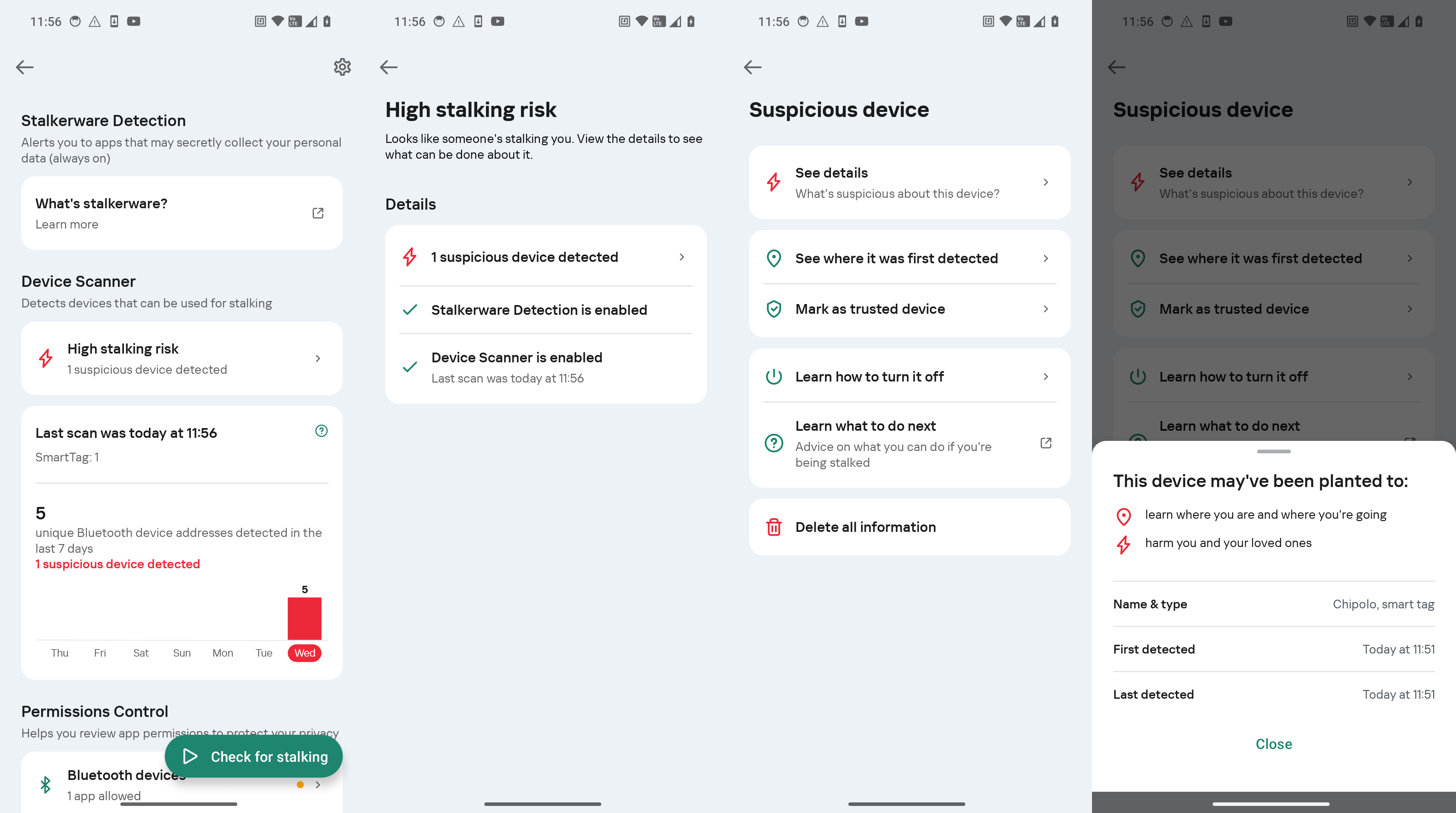
To safeguard yourself from both online and offline tracking, we recommend using Kaspersky for Android. This tool now includes the “Who’s spying on me” feature, which allows you to quickly detect surveillance.
Protection against tracking beacons. Fortunately, by their very nature, trackers can never be completely invisible, as they’re constantly signaling their presence via Bluetooth. A smartphone equipped with reliable protection can alert the user if an unregistered Bluetooth device is frequently detected nearby or in various different locations. If such a device moves around with you or stays close for too long, Kaspersky for Android will notify you.
Upon discovering a tracker, it’s essential to examine it closely. Sometimes, the situation may be innocent, such as if a family member you spend a lot of time with has a tracker attached to their keys. Occasionally, there may be trackers on rental vehicles or laptops (although rental companies are required to notify users and include this in the contract).
Protection against stalkerware. Kaspersky Premium detects known stalkerware apps. Oh, and by the way — did you know that Kaspersky products won a stalkerware detection test? If such apps — or even their installation files, whether downloaded by you or someone else — are found on your device, Kaspersky for Android will alert you immediately.
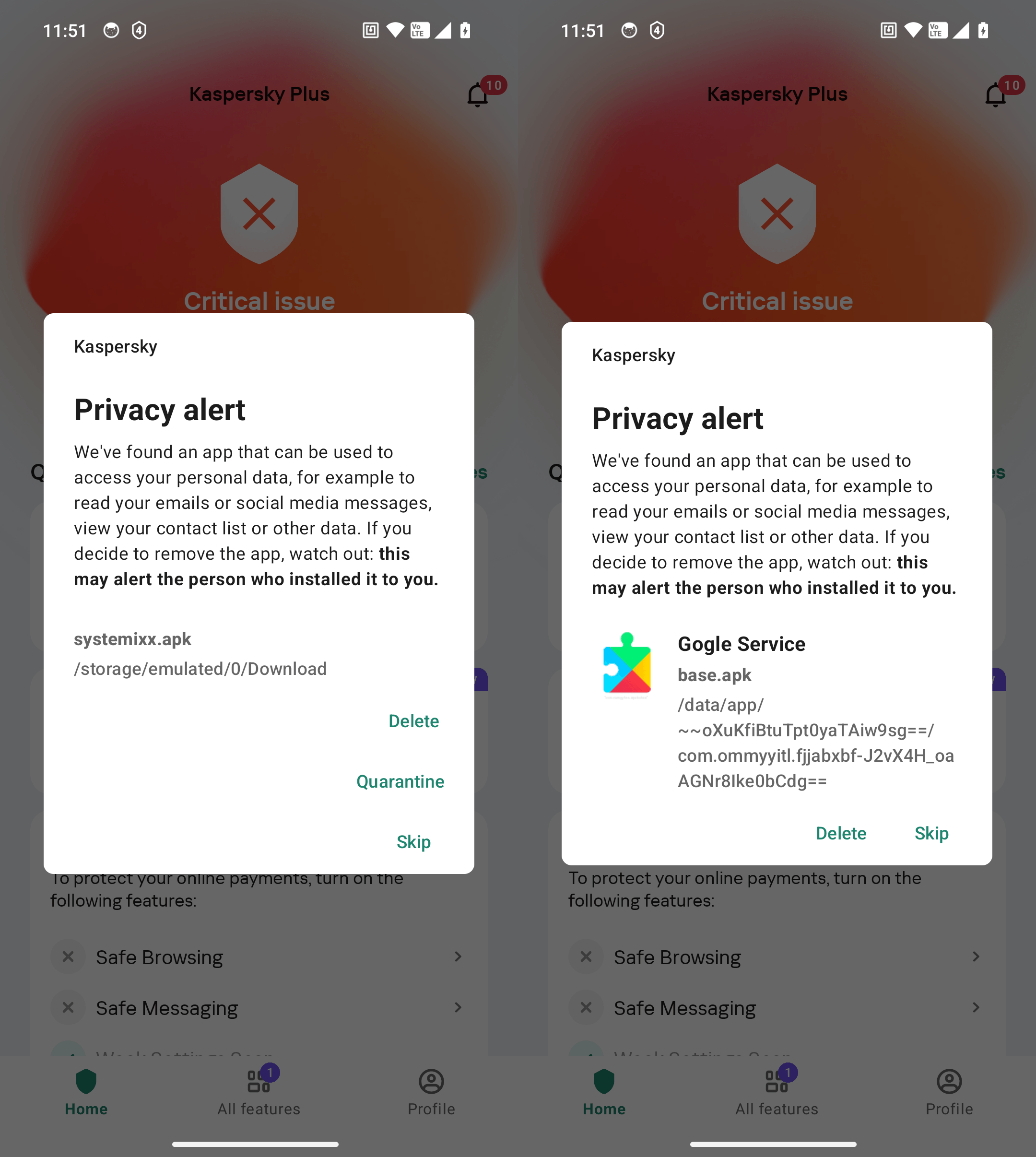
Kaspersky for Android detects both installed stalkerware apps (on the right) and their installation files (on the left)
Even users of the free version of Kaspersky for Android can scan for stalkerware. The only difference in this case between Kaspersky Premium and the free version is that in Kaspersky Premium, scanning is done automatically and continuously. In the free version of Kaspersky for Android, users need to manually initiate each scan.
Suspicious beacons that appear frequently in your vicinity will be listed and labeled in the Device Scanner section.
Meanwhile, the permission-control feature regularly checks the access of apps to your camera, microphone, location and Bluetooth, so you can quickly identify suspicious new apps.
Additional precautions Several general security and cyber-hygiene measures can make it harder for anyone to track you, and are recommended for all users:
- Never leave personal items unattended. This applies especially to digital devices that are powered on.
- Set up biometric authentication on your smartphone.
- Set the auto-lock screen time to 30 seconds or less.
- Set up biometrics or a strong password for logging into your laptop, and always lock the screen if you leave your desk.
- Make a password necessary to install apps from the app store (you can do this on both iOS and Android).
- Disable the installation of apps from unknown sources on Android.
- Update all your apps at least once a month and delete any that you no longer use.
- Never share your passwords with anyone. If you’ve ever shared them with anyone, or you suspect they may have been intercepted, seen or guessed — change them immediately.
- Avoid logging into personal accounts on shared devices at home or at work, and certainly don’t do this in libraries, hotels or cafes. If you absolutely have to log in, make sure to log out afterwards.
- Use a password manager, create a unique password for each account, and enable two-factor authentication.
- Be careful with what you share on social media and in messengers — avoid disclosing details that reveal your location, daily routine, or social circle.
For individuals at higher risk of stalking (say, from an unwanted admirer, disaffected spouse or business partner), here is a more comprehensive list of precautions, including physical safety and legal protection measures.
What to do if you detect surveillance
If you’ve discovered a beacon or tracking app and ruled out any innocent explanations, consider the possible reasons for why you might be under surveillance.
For those involved in domestic violence or serious conflicts, physical safety is the priority. Therefore, in such cases, it’s important not to reveal that you’ve detected the surveillance, but instead contact the police or dedicated support organizations. Likewise, it’s essential that the smartphone or beacon doesn’t end up in a location that would indicate the discovery (for example, a police station). You can either leave the smartphone at home while you go to the police, or arrange to meet a support group in a safe place. For more detailed advice on such tricky cases, consult our anti-stalking awareness guide.
If the risk of violence is low, you should still contact the police. Hand over the spy tracker, and let law enforcement create a digital copy of your smartphone to gather evidence of infection (if present). After that, you can remove the stalkerware from your smartphone.
Kaspersky official blog – Read More