Ransomware review: November 2023
This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim did not pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.
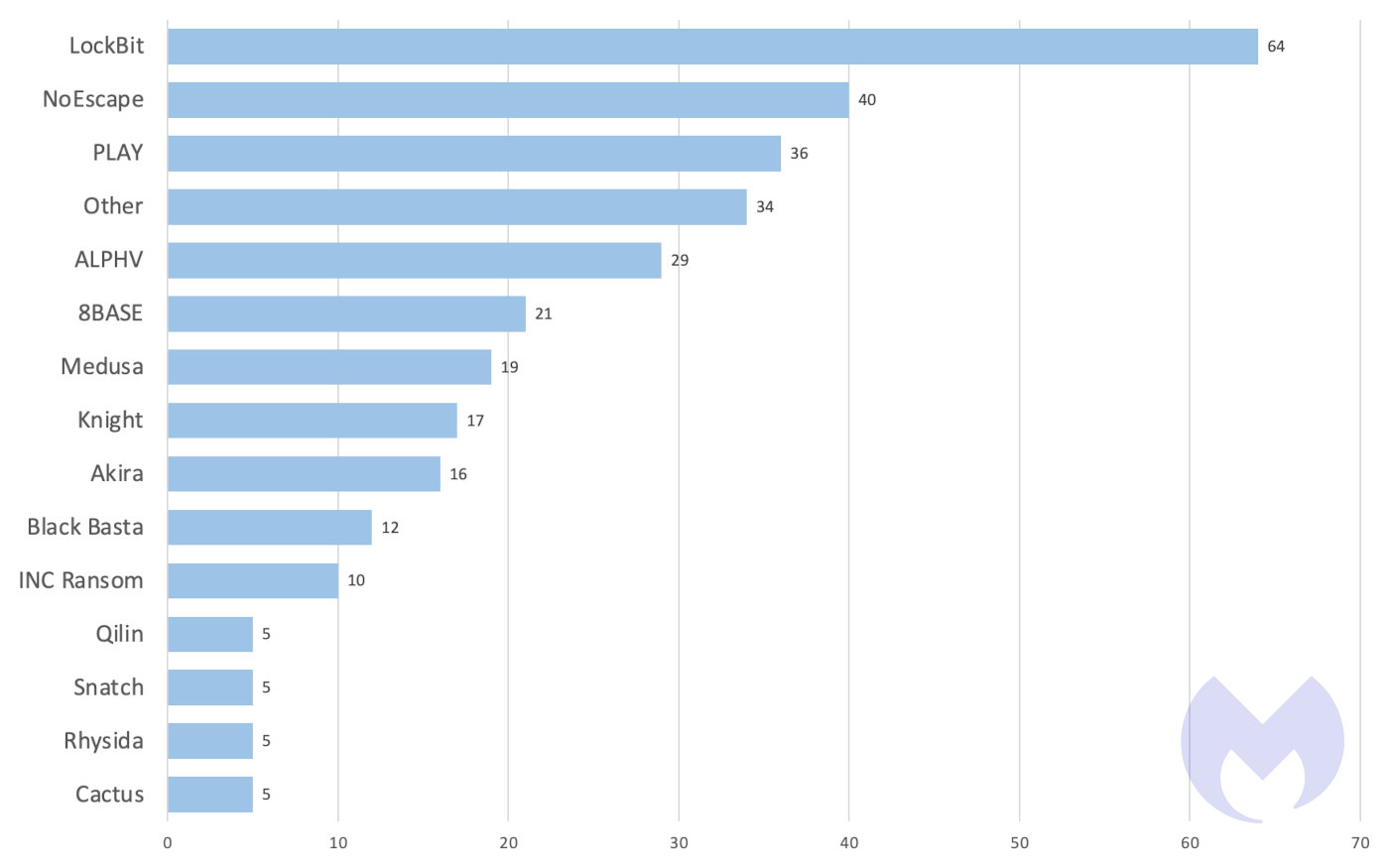
In October, 318 new victims were posted on ransomware leak sites. The top active gangs were LockBit (64), NoEscape (40), and PLAY (36). Major stories for the month included the takedown of several high-profile groups, including alleged Sony Systems attacker RansomedVC, new data shedding light on Cl0p’s education sector bias, and a deep-dive revealing the danger of the group behind September’s infamous casino attacks.
Last month three major ransomware groups—RansomedVC, Ragnar, and Trigona—were shut down, the first two by law enforcement and the third by Ukrainian hacktivists. Let’s dive into RansomedVC, a group which burst onto the scene in August and quickly gained notoriety for allegedly breaching several well-known companies. In late October, the lead hacker behind the group was seen on Telegram trying to sell the operation. Just days later, the account announced that it was “putting an end to” the group after learning that six of its affiliates may have been arrested. The group had posted 42 victims on their leak site at the time of their take down.
While law enforcement is yet to come forward confirming the RansomedVC arrests, the same is not true for RagnarLocker group, which Europol and Eurojust announced they had taken down last month. RagnarLocker started in 2019 and was responsible for numerous high-profile attacks against municipalities and critical infrastructure across the world. At the time of the takedown action, the group had posted a total of 42 victims on their leak site.
Trigona’s demise, on the other hand, was not at the hands of investigators but activists, highlighting the impact that broader geopolitical struggles can have on the ransomware landscape. In mid-October, the Ukrainian Cyber Alliance (UCA) breached the Trigona Confluence server and completely deleted and defaced their sites. Formed around 2016 to defend Ukraine’s cyberspace against Russian interference, the UCA used a public exploit for CVE-2023-22515 to gain access to Trigona infrastructure. Trigona is responsible for at least 30 attacks across various sectors since first emerging in October 2022.
Known ransomware attacks by ransomware group, October 2023
Known ransomware attacks by country, October 2023
Known ransomware attacks by industry sector, October 2023
In other October news, Resilience, a cyber insurance company, reported that 48% of all MOVEit cyberattack victims in its client base during the first half of 2023 were from the education sector. This suggests a possible targeting preference of the Cl0p campaign towards educational institutions. However, this figure might not fully represent the situation.
For instance, if Resilience has a higher proportion of clients in the education sector, it could bias the data towards that sector. On the other hand, data from Malwarebytes indeed indicates that while the education sector comprises only 3% of all MOVEit hosts, they account for 6% of the victims. However, this trend is likely not due to a deliberate focus by Cl0p, whose attacks were more opportunistic in scope, but rather because educational sectors often have fewer resources to promptly address vulnerabilities like those in MOVEit. Thus, the bias observed is more circumstantial than intentional. At any rate, given that the education sector frequently relies on third-party applications like MOVEit, the impact of Cl0p’s activities serves as a stark reminder for these institutions to adopt robust third-party security best practices.
Microsoft’s deep dive into Scattered Spider last month shed new light on the relatively new, albeit dangerous, ransomware gang who made headlines in September for attacking MGM Resorts and Caesar Entertainment. For small security teams, one of the most important findings about the group is their use of Living Of The Land (LOTL) techniques to avoid detection: Scattered Spider employs everyday tools like PowerShell for reconnaissance and stealthily alters network settings to bypass security measures. They also exploit identity providers and modify security systems, blending their malicious activities with normal network operations.
With the success of groups like Scattered Spider increasingly relying on LOTL attacks, it’s vital for defenders to focus on detecting anomalous activities within legitimate tools and network configurations. Strengthening monitoring and analysis capabilities can help identify and counter the subtle, sophisticated techniques employed by these ransomware gangs.
New(?) player: Hunters International
Hunters International is a new ransomware player suspected to be a rebrand of the Hive ransomware, which was shutdown in January 2023 by law enforcement. Despite Hunters International’s denial, claiming they are a distinct entity that purchased Hive’s source code, the overlap in their malware’s coding and functionality suggests a direct lineage from Hive.
Their activity, though limited, includes a notable attack on a UK school.
How to avoid ransomware
Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Malwarebytes – Read More