Ransomware Attacks Have Surged 30% Since Q4 2025

Ransomware groups claimed more than 2,000 attacks in the last three months of 2025 – and they’re starting 2026 at the same elevated pace.
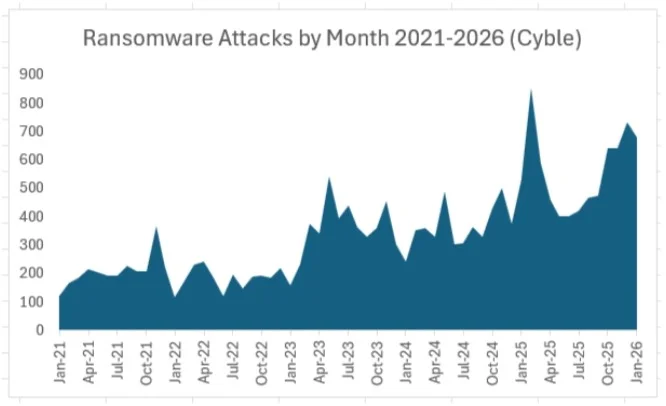
Cyble recorded 2,018 claimed attacks by ransomware groups in the fourth quarter of 2025, an average of just under 673 a month. The threat groups maintained that pace in January 2026, claiming 679 ransomware victims.
By comparison, in the first nine months of 2025, ransomware groups averaged 512 claimed victims a month, so the trend in the last four months has been more than 30% above the previous nine-month period. The chart below shows ransomware attacks by month since 2021.
Qilin Leads All Ransomware Groups as CL0P Returns
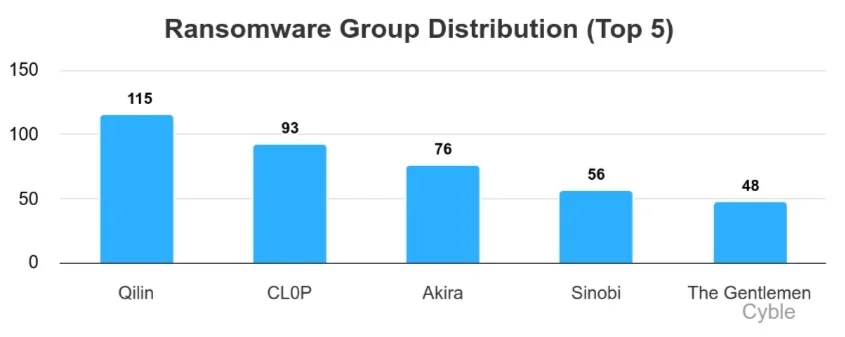
Qilin once again led all ransomware groups, with 115 claimed attacks in January. A resurgent CL0P has claimed scores of victims in the last two weeks, yet as of this writing had provided no technical details on the group’s latest campaign. Akira once again remained among the leaders with 76 claimed victims, while newcomers Sinobi and The Gentlemen rounded out the top five (chart below).
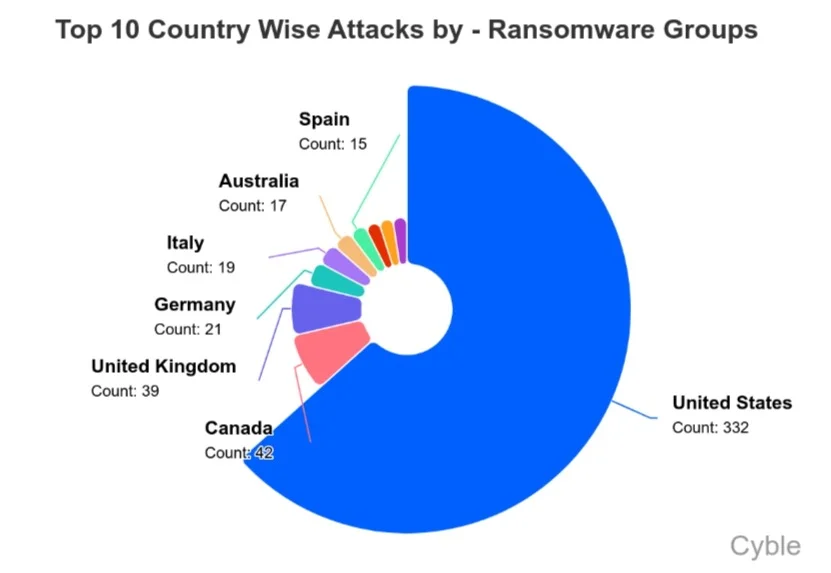
The U.S. once again was the most attacked country by a significant margin, accounting for just under half of all ransomware attacks in January (chart below). The UK and Australia experienced higher-than-usual attack volumes; CL0P’s recent campaign was a factor in both of those increases.
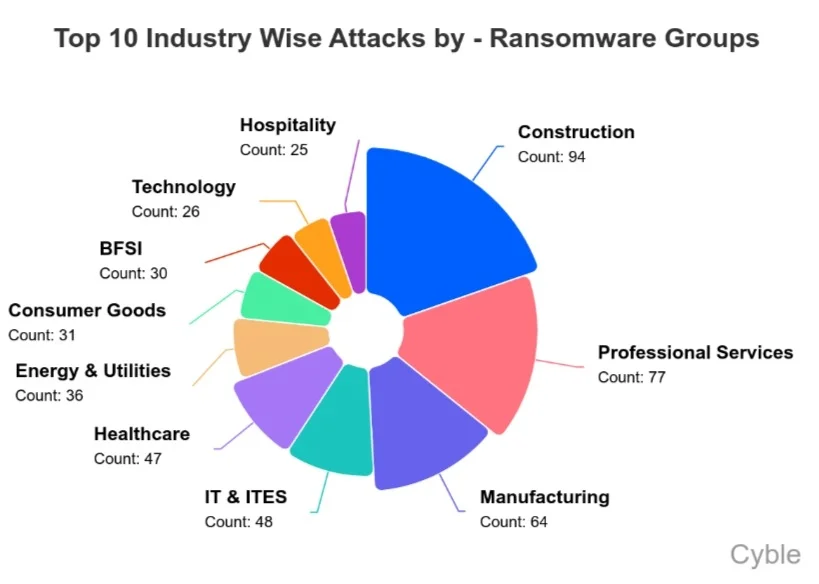
Construction, professional services, and manufacturing continue to lead the sectors hit by ransomware attacks, likely due to opportunistic threat actors targeting vulnerable environments (chart below). The IT industry also remains a frequent target of ransomware groups, likely due to the rich target the sector represents and the potential to pivot into downstream customer environments.
Recent Ransomware Attacks
Here are some of the most significant ransomware attacks that occurred in January, several of which had supply chain implications. Additional details will be provided in Cyble’s forthcoming January 2026 Threat Landscape Report, which will be published in the Research Reports section.
As CL0P tends to claim victims in clusters, such as its exploitation of Oracle E-Business Suite flaws that helped drive supply chain attacks to records in October, new campaigns by the group are noteworthy. Among the claimed victims in the latest campaign have been 11 Australia-based companies spanning a broad range of sectors such as IT and IT services, banking and financial services (BFSI), construction, hospitality, professional services, and healthcare.
Other claimed victims have included a U.S.-based IT services and staffing company, a global hotel company, a major media firm, a UK payment processing company, and a Canada-based mining company engaged in platinum group metals production.
The Everest ransomware group claimed responsibility for breaching a major U.S. manufacturer of telecommunications networking equipment and claimed to have exfiltrated 11 GB of data. Everest claims the data includes PDF documents containing sensitive engineering materials, such as electrical schematics, block diagrams, and service subsystem documentation.
Additional directories reportedly contain .brd files, which are printed circuit board (PCB) layout files detailing information critical to hardware manufacturing and replication. The group also shared multiple samples showing internal directories, engineering blueprints, and 3D design-related materials.
The Qilin ransomware group claimed responsibility for breaching a U.S.-based airport authority responsible for managing commercial aviation operations and related services. The group shared 16 data samples as proof-of-compromise. The materials suggest access to financial documents, telehealth-related reports, internal email correspondence, scanned identification documents, non-disclosure agreements (NDAs), and other confidential agreements, suggesting exposure of sensitive administrative and operational information.
The Sinobi ransomware group claimed a breach of an India-based IT services company providing digital transformation, cloud, ERP, and managed services. The threat group alleges the theft of more than 150 GB of data, including contracts, financial records, and customer data. Samples shared by the attackers indicate access to internal infrastructure, including Microsoft Hyper-V servers, multiple virtual machines, backups, and storage volumes.
The Rhysida ransomware group claimed responsibility for breaching a U.S. company providing life sciences and biotechnology instrumentation and solutions. According to the threat group, the allegedly stolen data has already been sold, though no information was provided regarding the buyer or the price at which the dataset was advertised.
The victim was listed as directly sold rather than placed under a traditional negotiation or countdown model. Despite this, samples remain accessible and indicate exposure of email correspondence, engineering blueprints, project documentation, and non-disclosure agreements (NDAs), suggesting compromise of both technical and corporate information.
The RansomHouse extortion group claimed responsibility for breaching a China-based electronics manufacturing company providing precision components and assembly services for global technology and automotive manufacturers. As evidence, RansomHouse published documentation indicating access to extensive proprietary engineering and production-related data. The shared materials reference confidential 3D CAD models (STEP/PRT), 2D CAD drawings (DWG/DXF), engineering documentation, printed circuit board (PCB) design data, Gerber files, electrical and layout architecture data, and manufacturing drawings. Notably, the group claims the compromised archives contain data associated with multiple major technology and automotive companies.
INC Ransom claimed responsibility for breaching a Hong Kong–based manufacturer supplying precision components to the global electronics and automotive industries. According to the group, approximately 200 GB of data was allegedly exfiltrated. The claimed dataset reportedly includes client-related information associated with more than a dozen major global brands, plus confidential contracts and project documentation for at least three major IT companies.
The Qilin ransomware group claimed responsibility for breaching a Taiwan-based company operating in the semiconductor and electronics manufacturing sector. According to the group, approximately 275 GB of data was allegedly exfiltrated. Based on the file tree information shared by Qilin, the dataset reportedly consists of 19,822 directories and 177,551 files, suggesting broad access to internal systems.
The Nitrogen ransomware group leaked more than 71 GB of data allegedly stolen from a U.S. company providing engineered components and systems for the automotive industry. According to the threat group, the exposed data includes sensitive corporate and technical information such as CAD drawings, accounts payable and receivable records, invoices, and balance sheet documentation. To substantiate its claims, Nitrogen published selected project blueprints and shared a file tree indicating the alleged theft of approximately 116,180 files, suggesting broad access to internal engineering and financial systems.
The Anubis ransomware group claimed responsibility for breaching an Italian government authority responsible for the management, regulation, and development of regional maritime port operations. According to the group, the compromised data includes incident and safety reports, logistics and operational data, port infrastructure layouts, audit results, internal reports, and business correspondence.
New Ransomware Groups
Among new ransomware groups that have emerged recently, Green Blood has launched an onion-based data leak site. While the group has not yet publicly named specific victims, it claims that affected organizations are located in India, Senegal, and Colombia. The group provides TOX ID and email-based communication channels for victim contact. Notably, malware samples associated with Green Blood have been observed in the wild. The ransomware encrypts files using the “.tgbg” extension and drops a ransom note titled “!!!READ_ME_TO_RECOVER_FILES!!!.txt”
A new ransomware-as-a-service (RaaS) operation named DataKeeper has surfaced, promoting an updated affiliate model referred to as CrystalPartnership RaaS. The group claims this approach improves trust by splitting ransom payments directly between the operator’s and affiliate’s Bitcoin addresses at the time of payment, removing reliance on centralized payout handling. DataKeeper is advertised as a Windows-focused ransomware toolkit. The operation claims to use a hybrid encryption scheme combining symmetric file encryption with RSA-4096 key protection, unique per-build identifiers, and TOR-based payment links. Encryption and decryption workflows are tied to a victim-specific ID, with decryption requiring delivery of a key file following payment.
The group emphasizes operational features such as in-memory execution, multithreaded encryption, optional shadow copy removal, network share targeting, and evading security controls.
The threat actor (TA) MonoLock announced a new RaaS operation on the RAMP cybercrime forum (the forum has since been seized by the FBI). MonoLock’s core design is based on Beacon Object Files (BoF), enabling full in-memory execution, reduced payload exposure, and centralized control from a single post-exploitation command-and-control (C2) instance without dropping files.
While BoF usage is common in Windows environments, MonoLock introduced a custom Linux ELF-based BoF loader, derived from the TrustedSec ELFLoader, adding chained execution, command packing, encryption, and in-memory deployment. The group promotes a “Zero Panel” extortion model, explicitly rejecting leak sites and Tor-based negotiation panels.
MonoLock claims that avoiding public extortion infrastructure reduces law enforcement exposure and leverages silence as negotiation pressure, minimizing reputational damage for victims. Affiliates are recruited under a 20% revenue share with a USD $500 registration fee, alongside a limited referral program running from January 11 to March 31.
Conclusion
The persistently high level of ransomware attacks – and the emergence of new ransomware groups eager to compete on features and price – highlight the urgent need for security teams to adopt a defense-in-depth cyber strategy. Cybersecurity best practices that can help build resilience against attacks include:
- Prioritizing vulnerabilities based on risk.
- Protecting web-facing assets.
- Segmenting networks and critical assets.
- Hardening endpoints and infrastructure.
- Strong access controls, allowing no more access than is required, with frequent verification.
- A strong source of user identity and authentication, including multi-factor authentication and biometrics, as well as machine authentication with device compliance and health checks.
- Encryption of data at rest and in transit.
- Ransomware-resistant backups that are immutable, air-gapped, and isolated as much as possible.
- Honeypots that lure attackers to fake assets for early breach detection.
- Proper configuration of APIs and cloud service connections.
- Monitoring for unusual and anomalous activity with SIEM, Active Directory monitoring, endpoint security, and data loss prevention (DLP) tools.
- Routinely assessing and confirming controls through audits, vulnerability scanning, and penetration tests.
Cyble’s comprehensive attack surface management solutions can help by scanning network and cloud assets for exposures and prioritizing fixes, in addition to monitoring for leaked credentials and other early warning signs of major cyberattacks.
Additionally, Cyble’s third-party risk intelligence can help organizations carefully vet partners and suppliers, providing an early warning of potential risks.
The post Ransomware Attacks Have Surged 30% Since Q4 2025 appeared first on Cyble.
Cyble – Read More

