SOC & Business Success with ANY.RUN: Real-World Results & Cases
Running a SOC today means constant trade-offs: too many alerts, not enough people, strict SLAs, and attacks that keep getting smarter. Most leaders aren’t asking for “the next cool product” but a proof that something actually cuts time, risk, and workload in real environments like theirs.
Thousands of organizations already rely on ANY.RUN to reduce analyst load, resolve phishing cases faster, cut unnecessary escalations, and speed up detection so incidents are contained before they reach the business.
Here we are bringing that evidence together. Let’s look at the results from different industries, how teams use ANY.RUN across Tier 1/2/3, and why it became a core part of their SOC operations, so if you’re still hesitating, you can see exactly what teams like yours are achieving with it.
What Real Teams Achieve with ANY.RUN: Proven Results Across Industries
When you look across banks, MSSPs, transport companies, and healthcare providers, the pattern is the same: once ANY.RUN becomes part of daily SOC operations, teams move faster, reduce noise, and prevent incidents earlier.
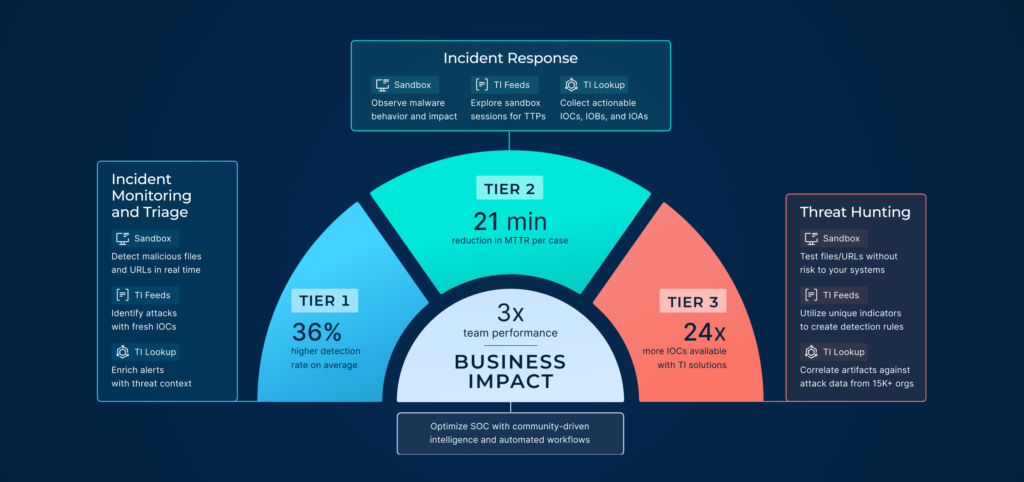
Here are the outcomes customers report consistently:
- 94% of users report faster phishing and malware triage in real SOC workflows.
- 76% faster phishing triage for a healthcare MSSP (from 30–40 minutes down to 4–7 minutes).
- 50%+ reduction in malware investigation and IOC extraction time.
- Tier-1 closure rates rising from ~20% to around 70% after giving Tier 1 full behavioral evidence.
- 30–55% fewer false escalations thanks to richer context and verdict confidence.
- 21 minutes average MTTR reduction in SOCs that integrated ANY.RUN into their workflows.
- 15 seconds MTTD for phishing and malware threats which allows analysts to accelerate their SIEM/SOAR investigations.
- Insights from ANY.RUN’s solutions helped SOC and MSSP teams stop hundreds of ransomware attempts before they ever touched production systems.
MSSP Success Case: Faster Threat Analysis Without Expanding the Team
Expertware is a European MSSP with over 18 years of experience, providing SOC services to organizations across banking, insurance, retail, telecom, and other industries. Their cyber intelligence operations team supports multiple customers at once, where speed and depth of analysis directly impact SLAs.
Challenge
Before adopting ANY.RUN’s Interactive Sandbox, malware investigations required manually building and maintaining reverse-engineering environments. This slowed response times, limited visibility into full attack chains, and made it harder to scale analysis across multiple customers without adding workload.
Outcome
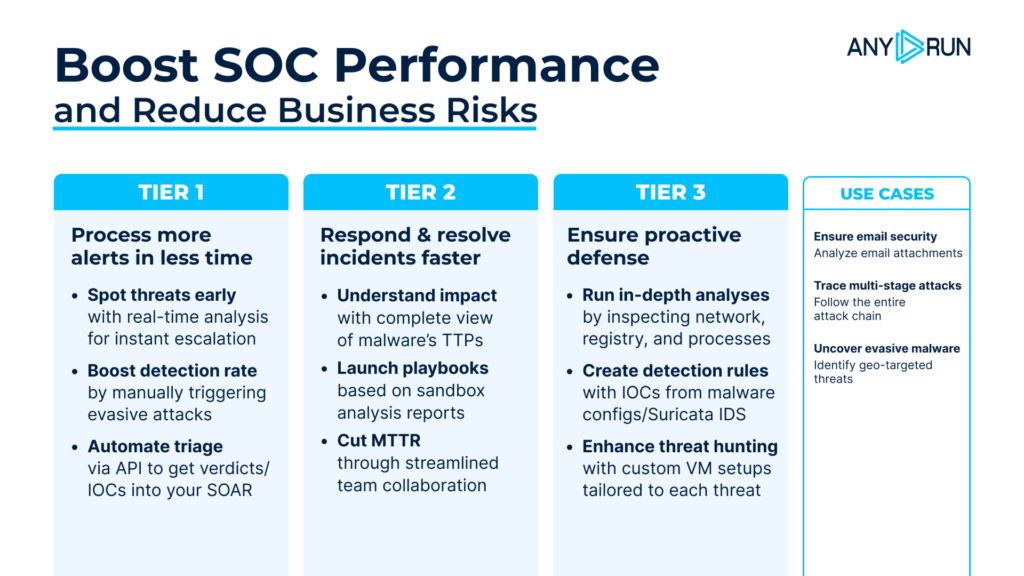
Expertware standardized a single analysis cycle centered on interactive execution and fast intelligence sharing:
- Execute and observe: Suspicious files and phishing samples are detonated to expose full behavior and multi-stage chains.
- Analyze in depth: Analysts interact with malware in real time to uncover obfuscation, memory-only stages, and C2 infrastructure.
- Extract and share: Indicators and findings are mapped, documented, and shared across SOC and IR teams to speed decisions.
This approach removed the need for custom VMs and reduced friction across investigations.
Results
- Over 50% reduction in malware investigation and IOC extraction time
- Faster turnaround on customer incidents without increasing staff
- Clear visibility into full kill chains, including fileless and memory-based stages
- Easier collaboration through shared, interactive analysis reports
- Improved SLA performance by resolving cases earlier in the workflow
Healthcare MSSP Success Case: Faster Phishing Triage Without SLA Risk
A mid-sized MSSP specializing in healthcare supports hospitals, clinics, and labs across thousands of endpoints. Operating in a highly regulated environment, the SOC had to balance strict SLAs, audit requirements, and a growing volume of phishing and malware alerts.
Challenge
As the customer base expanded, Tier 1 and Tier 2 teams were overwhelmed. Multi-stage phishing emails with redirects, QR codes, and CAPTCHA checks often took 30–40 minutes per case, driving escalations, slowing response, and putting SLA commitments at risk.
Outcome

The MSSP standardized a single operational triage cycle combining sandbox execution, threat intelligence, and detection feeds:
- Early execution with the Interactive Sandbox cuts phishing triage by 76%, reducing analysis from 30–40 minutes to 4–7 minutes, while giving Tier 1 full visibility into real malware behavior.
- Richer context through Threat Intelligence Lookup improves decision confidence, driving 34% fewer false escalations and enabling Tier 1 closure rates to rise from 20% to 70%.
- Live intelligence via Threat Intelligence Feeds keeps detections current as attacker infrastructure rotates, resulting in faster MTTR and fewer false positives across automated workflows.
- Continuous monitoring of active attacks affecting 15,000+ organizations enables early detection of the latest threats.
Results
Since we implemented new solutions, every investigation now comes with evidence and threat data, from MITRE tags to screenshots. This made reporting faster and extra work fell off our shoulders.
- 76% reduction in phishing triage time (from 30–40 minutes down to 4–7 minutes)
- Higher Tier-1 closure rates with fewer escalations to Tier 2
- Stronger SLA stability across multiple healthcare customers
- Audit-ready investigations with clear execution evidence and context
- A shift from reactive response to proactive, repeatable defense
Banking Success Case: Faster Analysis, Stronger Security Outcomes
A Brussels-based investment bank (750 employees) runs cybersecurity with a lean team of 12, where people often switch between threat analysis and incident response depending on what’s happening.
Challenge
When the Head of Cybersecurity joined, the security setup was “messier” than expected, and the team was getting swamped with alerts daily. Improving efficiency meant fixing the workflow, and a malware sandbox quickly became a top priority.
Outcome
The number of ransomware and credential stealing attempts we have prevented thanks to the sandbox is already in the hundreds.
After integrating ANY.RUN as part of a broader workflow overhaul, results showed up almost immediately. In the first week, the team was able to process alerts and threat analysis at least twice as fast, helping avoid incident response and recovery costs through timely actions.
Results
- 2× faster alert processing and threat analysis (visible in the first week)
- Better understanding of malware behavior through VM control (browsing websites, downloading, executing files)
- A faster, more practical approach than running custom-built VMs on isolated machines that take significant preparation
- Prevented hundreds of ransomware and credential-stealing attempts over time
- Stopped a supplier email attack by detonating the email, opening a password-protected ZIP, identifying a loader, and seeing it download and initiate ransomware in the VM, then blocking the email across the organization and warning other departments
Transport Company Success Case: Real-Time Visibility into Active Cyber Attacks
A multinational transport company operating across North America, Latin America, and Europe relies heavily on email to communicate with clients, contractors, and suppliers. With a 30-person security team, staying ahead of active attacks required a threat hunting approach that scaled without adding manual work.
Challenge
Attacker infrastructure changes rapidly, making static indicators and public reports outdated within days. Manually tracking phishing campaigns, malware activity, and CVEs relevant to the transport industry consumed time and made prioritization difficult.
Outcome

The team standardized a continuous threat hunting cycle that turns fresh execution data into detections:
- Confirm reality with an interactive sandbox: Detonate suspicious samples to capture behavior and extract high-confidence artifacts.
- Expand to campaign scope: Subscribe to TI Lookup’s Search Updates, pivot across related IOCs/IOAs/IOBs, domains, hosts, and historical activity.
- Operationalize fast: Use TI Feeds to push validated indicators into existing security workflows so detections stay current.
Results
- Near real-time visibility → faster decisions while attacks are still active.
- Quicker IOC/IOA/IOB discovery → shorter time to contain relevant threats.
- Less manual research → more capacity without extra headcount.
- Clear active vs. expired prioritization → steadier SLAs, fewer wasted cycles.
- Fresher detection updates → fewer repeat incidents as infrastructure rotates.
Trusted by Security Teams Worldwide
ANY.RUN is a part of daily security operations across industries where mistakes are expensive and downtime isn’t an option.
Today, organizations rely on ANY.RUN in real production environments across:
- 3,102 IT & technology companies
- 1,778 financial institutions
- 1,354 manufacturing organizations
- 919 healthcare providers
- 1,059 government entities
- 460 energy companies
- 347 transportation & logistics businesses

This trust shows up consistently in independent reviews:
- 4.7 / 5 on G2 — praised for speed, visibility, and day-to-day usability
- 4.8 / 5 on Gartner Peer Insights — recognized for real-world impact on SOC performance

This broad adoption across regulated, high-risk industries reinforces one thing:
ANY.RUN scales not just technically, but operationally; across teams, regions, and security maturity levels.
If teams in finance, healthcare, government, and critical infrastructure rely on it daily, it’s because it delivers results where stakes are highest.
Why These Results Repeat Across Teams and Industries
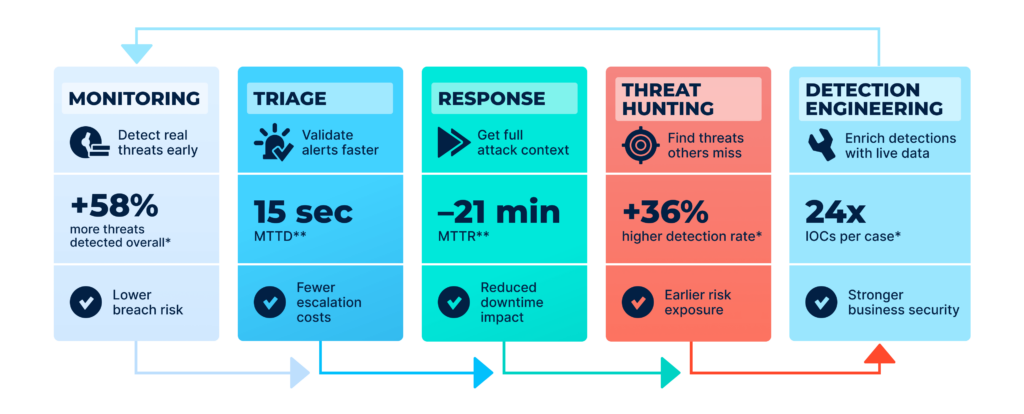
These outcomes show up in very different environments for one reason: high-performing teams don’t treat investigations as one-off incidents. They run a consistent, repeatable way of working that turns uncertainty into clarity fast and keeps that clarity flowing across the whole operation.
What makes the difference:
- Decisions are based on evidence, not assumptions
Teams don’t wait for “maybe” signals to become obvious. They confirm what’s happening early, so risk doesn’t quietly grow in the background.
- Context reaches the right people at the right moment
Frontline triage gets enough clarity to close routine cases confidently, while deeper work is reserved for what truly needs it.
- Response stays steady even when attackers change tactics
As infrastructure rotates and methods evolve; teams don’t fall back into manual chase mode. They keep coverage current and avoid repeating the same work.
- Workflows are built for scale, not heroics
The process holds up under load, across shifts, and across customers, which is why SLAs stabilize and burnout drops.
That’s why the same gains keep showing up: faster decisions, less noise, and fewer business-impacting incidents.
Ready to See What Results Like These Look Like in Your Environment?
Every SOC operates under different constraints; tools, team size, industry pressure, compliance rules. What doesn’t change is the cost of slow decisions, unnecessary escalations, and incidents that reach the business before they’re contained.
The teams featured here didn’t rebuild everything from scratch. They focused on shortening time-to-verdict, giving frontline staff better clarity, and keeping detection current as attacks evolved. The result was less noise, steadier SLAs, and fewer incidents turning into business problems.
If you’re weighing whether a change will actually move the needle, not in theory, but in daily operations, these results show what’s possible when security work becomes faster, clearer, and easier to scale.
See what faster decisions look like in practice, run your SOC with ANY.RUN.
About ANY.RUN
ANY.RUN is a core part of modern security operations, helping teams make faster, more confident decisions across Tier 1, Tier 2, and Tier 3. It fits into existing workflows without friction and strengthens the entire investigation lifecycle; from early validation to deeper analysis and ongoing threat awareness.
By revealing real attacker behavior, adding context where it’s missing, and keeping detections aligned with how threats actually evolve, ANY.RUN helps SOCs reduce noise, shorten response times, and limit business impact.
Today, more than 600,000 security specialists and 15,000 organizations worldwide rely on ANY.RUN to accelerate triage, cut unnecessary escalations, and stay ahead of phishing and malware campaigns that don’t stand still.
FAQ
ANY.RUN helps SOC teams reduce alert overload, speed up investigations, and lower unnecessary escalations by providing real execution evidence of threats early in the workflow. This allows analysts to make faster, more confident decisions instead of relying on assumptions or incomplete signals.
ANY.RUN reduces triage time by allowing analysts to safely execute suspicious files, links, and emails in an interactive sandbox and immediately observe real attacker behavior. Customers report up to a 76% reduction in phishing triage time and 50%+ faster malware investigations as a result.
Organizations using ANY.RUN consistently report:
– Faster phishing and malware triage (94% of users)
– 30–55% fewer false escalations
– Tier-1 closure rates increasing from ~20% to ~70%
– An average 21-minute MTTR reduction
– Earlier detection, with phishing MTTD as low as 15–20 seconds
ANY.RUN gives Tier 1 analysts enough behavioral evidence to confidently close routine cases, while Tier 2 and Tier 3 analysts can interact with malware in real time and enrich isolated artifacts with actionable intel to uncover obfuscation, memory-only stages, and full kill chains. This reduces bottlenecks and ensures work is handled at the right tier.
Yes. Multiple MSSPs and enterprise SOCs report faster case resolution and steadier SLAs without hiring additional staff. By standardizing investigation workflows and reducing manual research, teams handle higher alert volumes with the same resources.
By confirming real threat in seconds and providing fresh intel as attacker infrastructure changes, ANY.RUN gives SOC teams actionable evidence for faster containment.
Which industries rely on ANY.RUN in real production environments?
ANY.RUN is used daily across high-risk and regulated industries, including finance, healthcare, government, manufacturing, energy, and transportation. More than 15,000 organizations worldwide rely on it to scale investigations, reduce noise, and improve SOC decision-making.
The post SOC & Business Success with ANY.RUN: Real-World Results & Cases appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

