German Manufacturing Under Phishing Attacks: Tracking a Stealthy AsyncRAT Campaign
Manufacturing companies have quietly become one of the most hunted species in the modern threat landscape. Not because they are careless, but because they are operationally critical, geographically distributed, and often rely on complex IT and OT environments that attackers love to probe.
Key Takeaways
- Manufacturing is among the top industries targeted by ransomware groups and advanced campaigns, often with region-specific lures.
- Attackers continue to favor invoice-themed and supplier-related emails, carefully localized to increase trust and click-through rates in manufacturing environments.
- Files detected by only one or two vendors often indicate fresh attacks designed to bypass traditional defenses, making early discovery critical.
- The reuse of WebDAV, known vulnerabilities, and familiar RAT families across cases helps analysts distinguish structured campaigns from background noise.
- Filtering threats by sector and country dramatically improves relevance, allowing teams to focus on attacks that are most likely to impact their business.
- By identifying campaigns before alerts trigger, organizations can shorten dwell time and prevent disruptions that are especially costly for manufacturing operations.
- By correlating industry, geography, techniques, and indicators, Threat Intelligence Lookup helps manufacturing companies uncover active campaigns early and turn threat intelligence into a preventive control, not just a reference source.
The Threat Landscape: Manufacturing Under Siege
ANY.RUN‘s data, based on sandbox submissions of over 500K analysts and 15K SOCs, shows increased malicious activity against manufacturing companies. While this uptick aligns with patterns across other industries, manufacturing consistently shows slightly higher-than-average attack rates, confirming its status as a priority target.
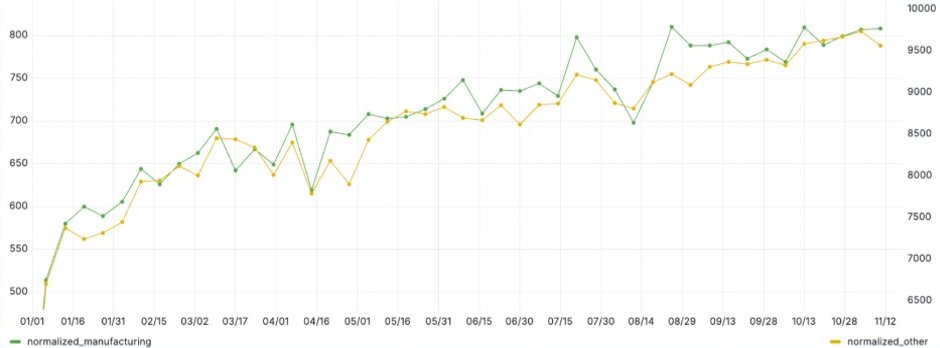
Top businesses operating in the industry rely on Threat Intelligence Lookup to track the latest attacks and campaigns conducted against manufacturing enterprises.
Accessing an up-to-date threat landscape for your industry requires just one search query:
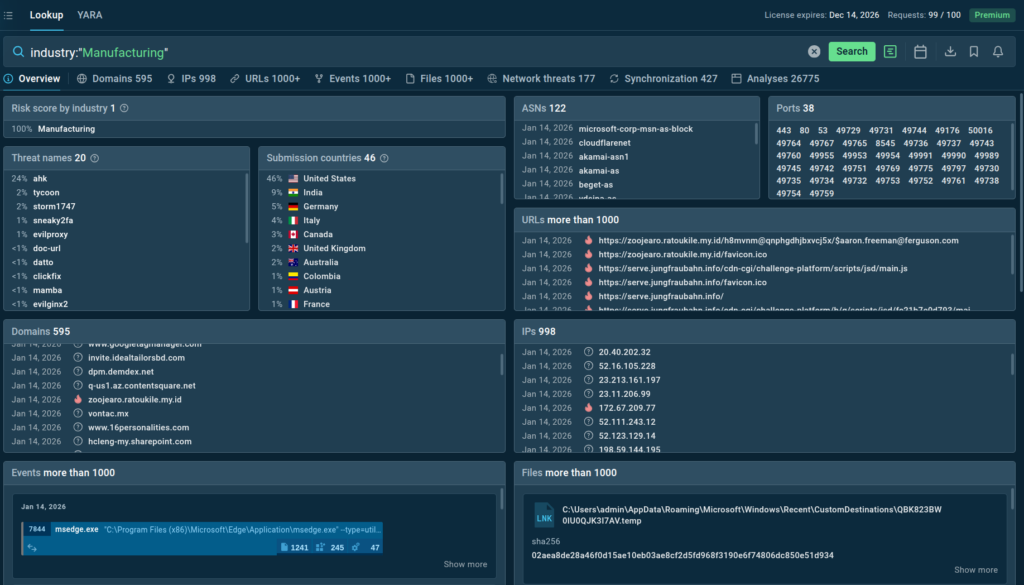
The service instantly delivers actionable intelligence on the latest cyber threats targeting companies around the world.
Learn more about threat landscape tracking with TI Lookup →
This enables SOC teams to timely update their defenses before the attackers have a chance to strike. By acting proactively, organizations are able to protect their infrastructure, prevent downtime, and avoid incident response costs.
Threat Hunting for a German Manufacturing Company
NOTE: This case study demonstrates how malware analysts use proactive threat hunting with ANY.RUN’s Threat Intelligence Lookup to identify and analyze real-world attacks targeting manufacturing companies, specifically focusing on a sophisticated campaign against German industrial firms.
(We have substituted the actual company’s name by a COMPANY_NAME placeholder.)
Let’s assume we are conducting continuous threat hunting for a manufacturing company based in Germany. Our objective is simple but critical: identify phishing emails as potential initial access vectors before they reach production systems.
Using ANY.RUN’s Threat Intelligence Lookup, we build a focused query:
industry:”Manufacturing” AND filePath:”*.eml” AND not threatLevel:”info” AND submissionCountry:”DE”
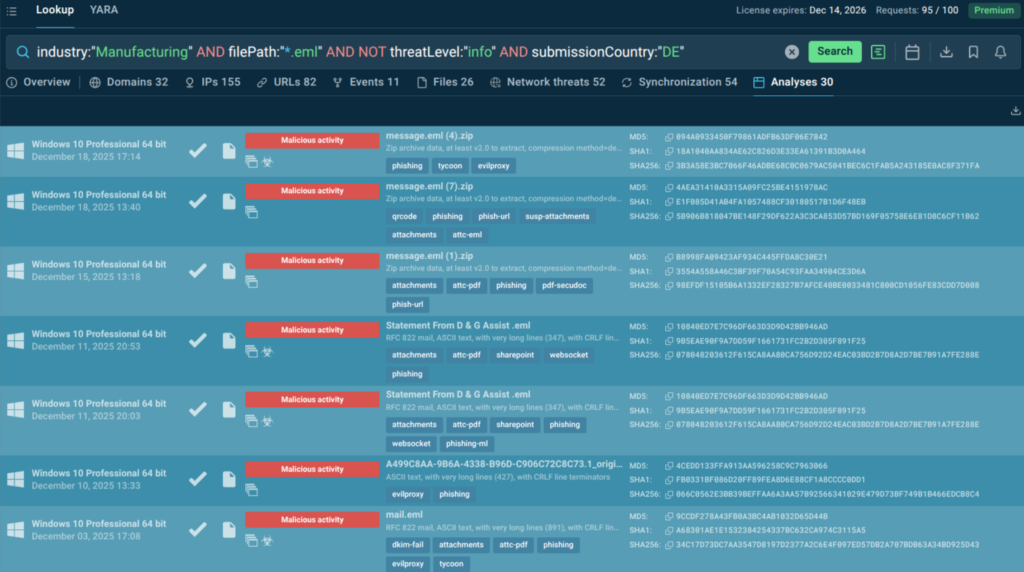
With a 90-day analysis window, the search yielded over 30 real-world cases representing potential intrusion attempts against organizations similar to ours.
A Closer Look at One Real Attack
One case stood out for its sophistication and targeted approach.
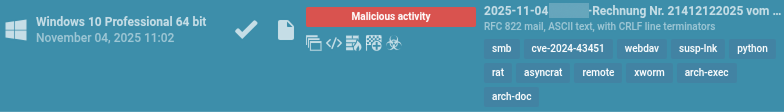
The attack leveraged the brand of a popular software provider in Germany, indicating specific targeting of German companies. What made this case particularly noteworthy was the combination of:
- Exploitation of a recently disclosed vulnerability,
- Highly convincing social engineering tactics.
The attack targeted a German construction and engineering services company through a carefully crafted phishing email:
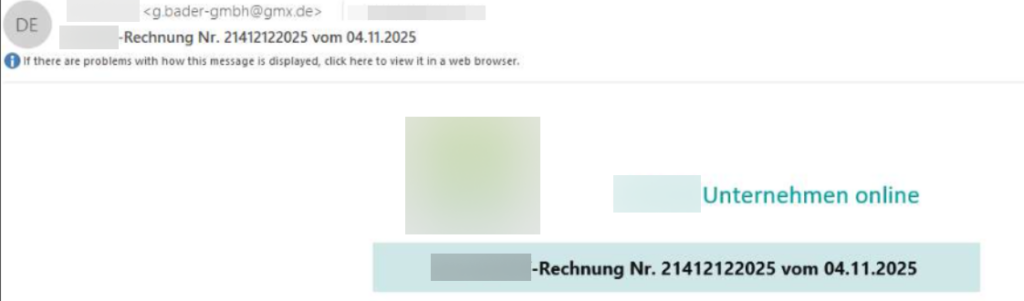
Sender Spoofing:
- Display name: “COMPANY_NAME eG” (legitimate company name),
- Actual sender: g.bader-gmbh@gmx[.]de (German domain for additional authenticity).
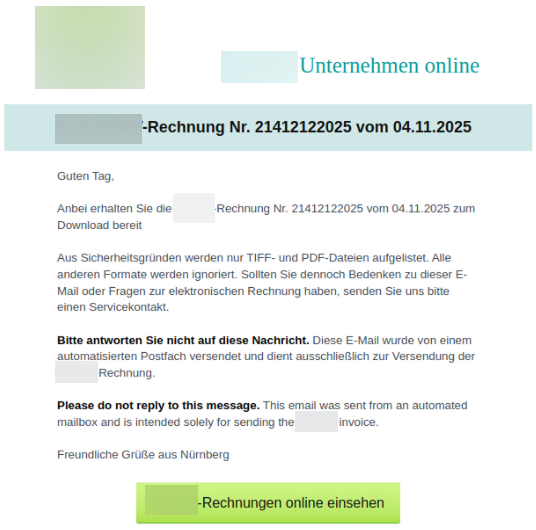
Email Content:
- Designed as an invoice notification from COMPANY_NAME,
- Included document number and date for legitimacy,
- Professional design increasing click-through probability,
- Malicious link embedded in the message.
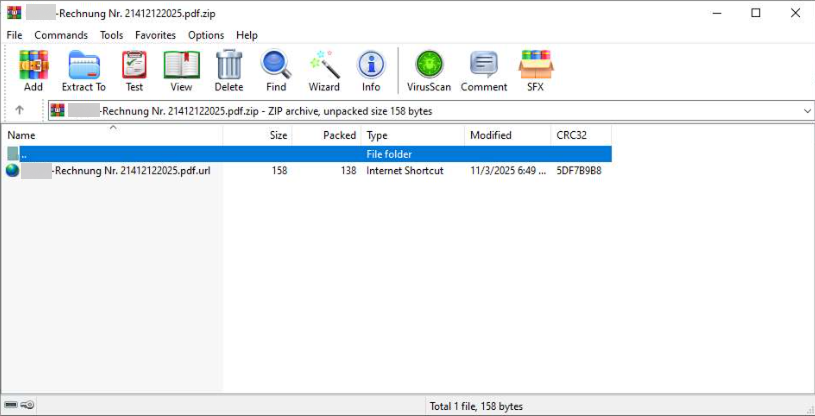
Clicking the link redirected victims to Dropbox, where a file named “COMPANY_NAME -Rechnung Nr. 21412122025.pdf.zip” awaited download.
Obfuscation Techniques:
- Double file extension (.pdf.zip) to disguise the true file type;
- Archive contained “COMPANY_NAME-Rechnung Nr. 21412122025.pdf.url”, a shortcut file masquerading as a PDF;
- Formatting designed to encourage victims to open the file
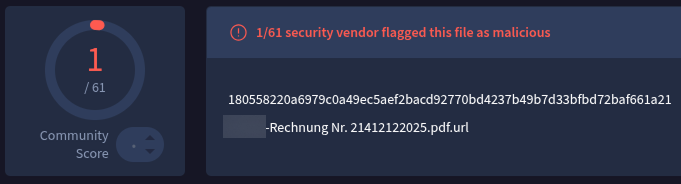
Detection Evasion:
At the time of analysis, this file was flagged as malicious by only one vendor on VirusTotal. That low detection rate strongly suggests a fresh sample designed to bypass traditional security controls.
The attack leveraged CVE-2024-43451, a vulnerability that enables automatic WebDAV connections without actually opening the .url file. During archive processing or interaction with the attachment, the system automatically connects to a remote resource.
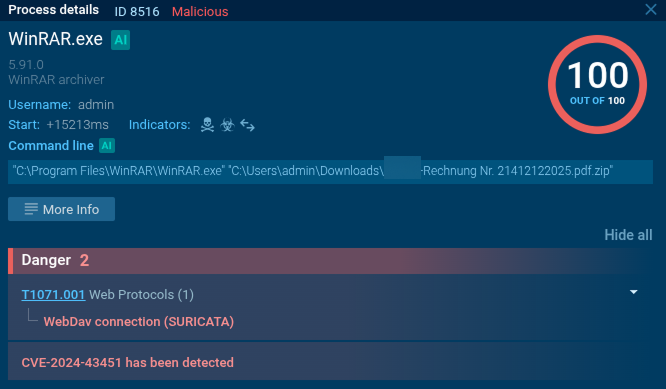
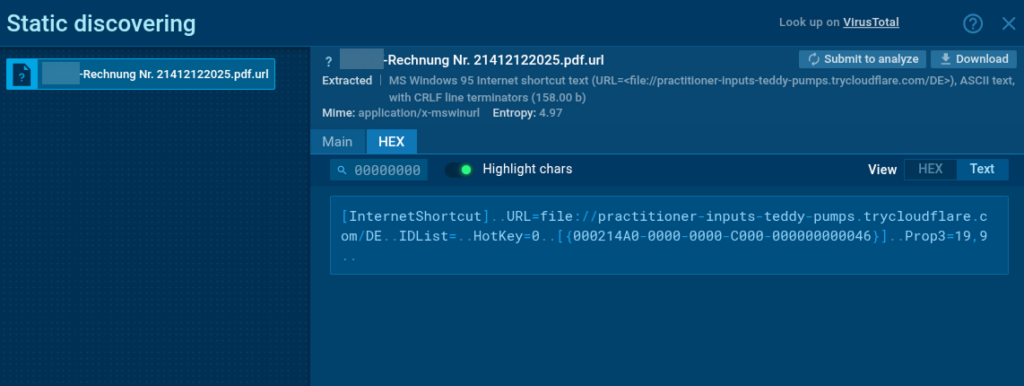
Execution Flow:
- Opening the .url file from the ZIP archive;
- Remote resource displays as a network directory;
- Contains .lnk file disguised as a PDF;
- Launching this file triggers subsequent attack stages;
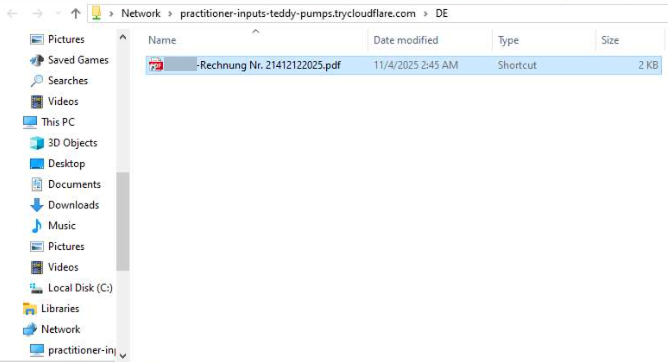
This combination provides attackers with redundancy and persistence, increasing the chances of maintaining access to the victim’s environment.
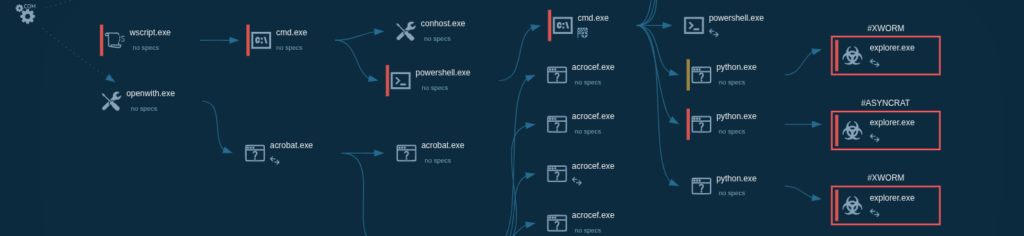
Notably, similar WebDAV-based techniques exploiting this vulnerability have been observed in APT activity, confirming that this is not opportunistic noise but a well-established attack pattern.
Expanding the Investigation: Campaign Scope Analysis
Identifying one attack is only the beginning. The real value of proactive threat hunting lies in understanding scale, patterns, and relevance.
Using Threat Intelligence Lookup, we pivot from the original case to search for related activity: emails and PDFs containing“COMPANY_NAME” in file names; hashes associated with the malicious documents.
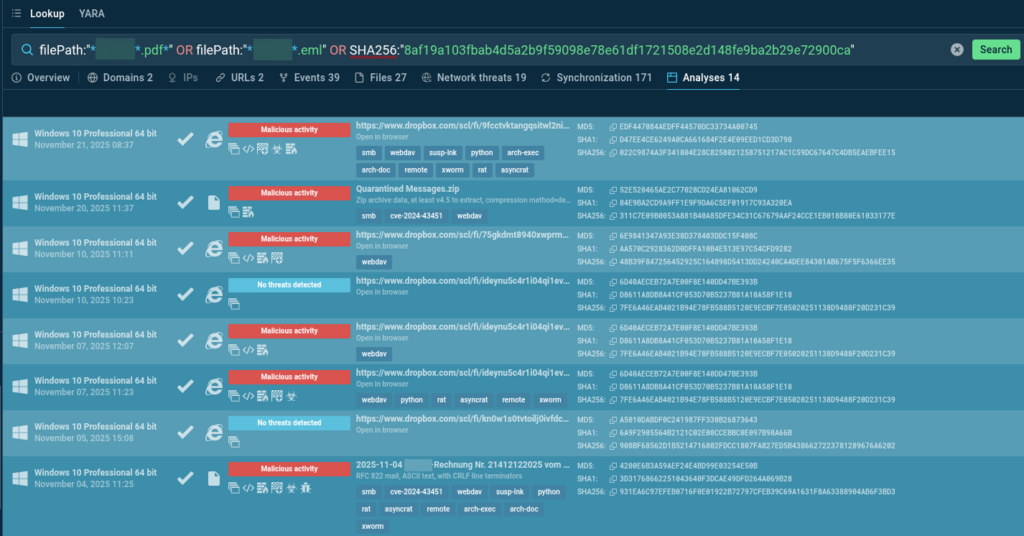
Query Results:
- 35 analyses matching the specified parameters;
- Almost all of them uploaded starting November 4, confirming recent activity;
- Multiple instances showing Dropbox connections for ZIP archive delivery;
- Generated indicators suitable for enriching detection systems.
When we analyze the industry and geography breakdown, the picture becomes even clearer. Manufacturing remains one of the top targeted industries, with nearly two-thirds of executions occurring in Germany. The same core techniques appear repeatedly: CVE-2024-43451, WebDAV abuse, AsyncRAT, and XWorm.
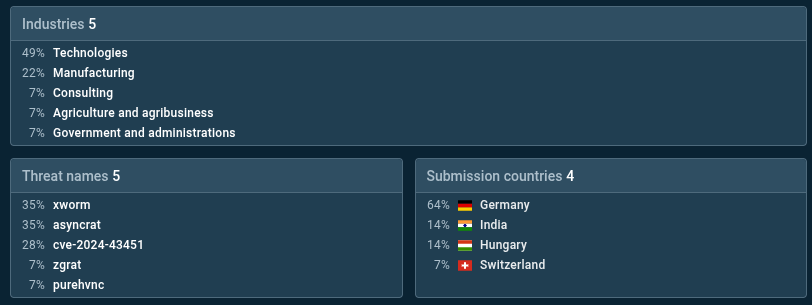
Hash search of the PDF file employed in the attack shows 40% of submissions from manufacturing industry and 100% of uploads by ANY.RUN’s Sandbox users from Germany:
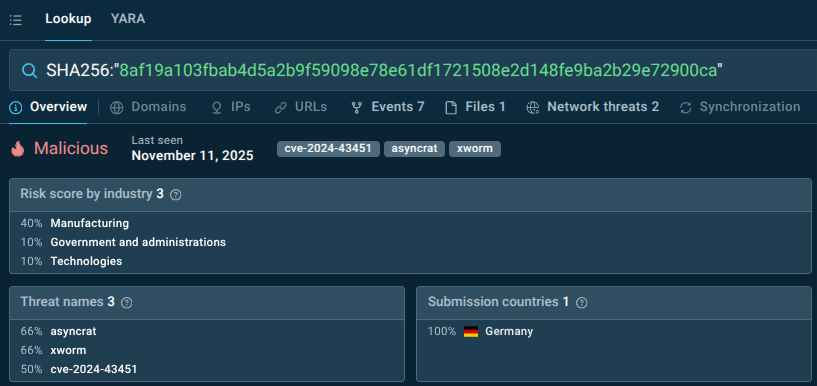
SHA256:”8af19a103fbab4d5a2b9f59098e78e61df1721508e2d148fe9ba2b29e72900ca”
Since AsyncRAT and XWorm are widely used, we narrow our focus to the vulnerability itself. A lookup for CVE-2024-43451 shows that most samples originate from the EU, with Germany accounting for roughly half of them. Manufacturing once again appears among the primary targeted industries. WebDAV connections are present in all samples, indicating standardized attack logic.
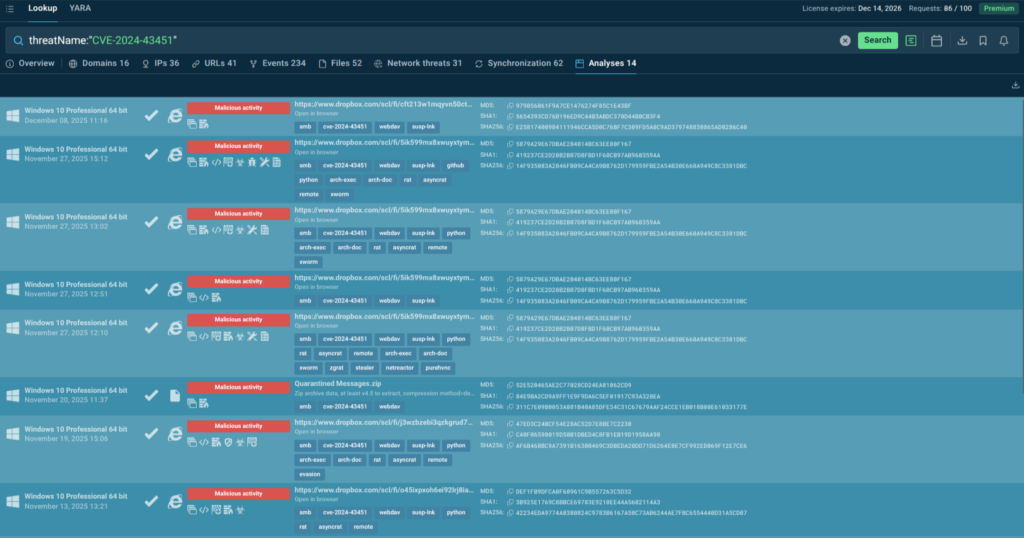
This level of repetition is exactly what threat hunters look for. It provides solid arguments to prioritize the threat, enrich internal detection systems with relevant indicators, and proactively hunt for similar behavior in logs, email gateways, and network traffic.
Discovering Industry-Specific Patterns
Threat Intelligence Lookup also allows us to search for malicious activity tied to industry-specific domain patterns. By querying domains containing fragments like “manufactur” and filtering for confirmed malicious activity, we uncover more than 100 sandbox analyses and dozens of suspicious domains.
domainName:”manufactur*” and threatLevel:”malicious”
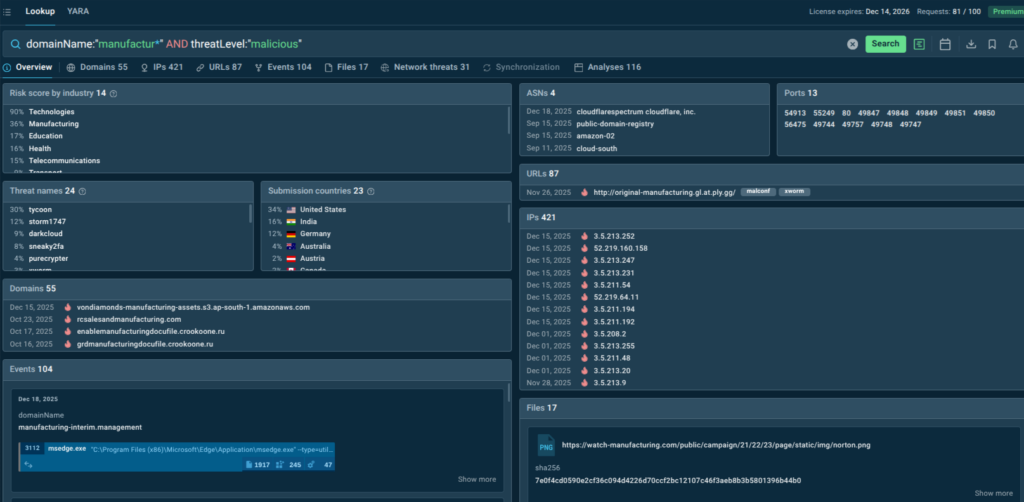
These findings help extend detection beyond known campaigns and uncover infrastructure that may be reused in future attacks against manufacturing organizations.
Key Findings and Implications
This case clearly shows that attacks using COMPANY_NAME-themed lures, WebDAV and CVE-2024-43451 abuse remain highly relevant for manufacturing companies, especially in Germany. More importantly, it demonstrates how proactive threat hunting changes the security posture entirely.
Instead of reacting to alerts after compromise, malware analysts can:
- Identify active campaigns targeting their industry and region;
- Understand attacker techniques before they reach production;
- Prioritize threats based on real-world repetition and relevance;
- Feed high-confidence indicators into detection and prevention systems.
With ANY.RUN’s Threat Intelligence Lookup, threat intelligence becomes a living, searchable environment rather than a static feed. For manufacturing companies facing constant operational pressure, this proactive approach can mean the difference between uninterrupted production and costly downtime.
Stay Ahead of Attacks with ANY.RUN
ANY.RUN helps security teams move earlier in the attack lifecycle by combining real-time malware analysis with actionable threat intelligence.
With the Interactive Sandbox, analysts can safely execute suspicious files and instantly observe attacker behavior, techniques, and indicators to accelerate MTTD and MTTR.

Threat Intelligence Feeds expand threat coverage with verified malicious network IOCs from real-time attacks on 15K+ orgs. Delivered instantly from ANY.RUN’s sandbox in flexible STIX/TAXII for seamless SIEM/SOAR integration.
TI Feeds empower SOC teams to ensure:
- Early Detection: IOCs added right after live sandbox analysis—proactively spot new threats in your SOC before they hit.
- Expanded Coverage: 99% unique indicators from global attacks (phishing, malware) that traditional feeds miss.
- Reduced Workload: Malicious-only alerts, filtered to slash Tier 1 time on false positives.
For manufacturing facing targeted campaigns and high downtime costs, it provides visibility into real attacks as they unfold, allowing them to spot risks before production halts.
About ANY.RUN
ANY.RUN supports more than 15,000 organizations worldwide, including leaders in finance, healthcare, telecom, retail, and tech, helping them strengthen security operations and respond to threats with greater confidence.
Designed for speed and visibility, the solutions provide interactive malware analysis and live threat intelligence, giving SOC teams instant insight into attack behavior and the context needed to act faster.
Request a trial or quote for your company →
FAQ: Proactive Threat Hunting for Manufacturing
Manufacturing organizations combine high operational impact, complex IT and OT environments, and tight downtime tolerance. This makes them attractive targets for ransomware groups and espionage-driven campaigns seeking fast leverage.
Phishing remains one of the most common initial access vectors. Attackers often use localized and industry-specific lures, such as invoices or supplier documents, to increase credibility and user interaction.
Proactive threat hunting focuses on identifying active or emerging attack patterns before alerts are triggered. Instead of waiting for detections, analysts search threat intelligence data for techniques, indicators, and campaigns relevant to their industry and region.
Threats are rarely random. Campaigns are often tailored to specific countries, languages, and industries. Filtering threat intelligence by industry and geography helps analysts focus on the most realistic risks to their organization.
Such vulnerabilities enable stealthy execution paths and are often abused before widespread detection signatures exist. Their repeated appearance across campaigns makes them strong indicators of active attacker playbooks.
By identifying recurring techniques, delivery methods, and malware families across multiple cases, analysts can distinguish isolated noise from systematic campaigns and prioritize threats that are most likely to impact their environment.
It reduces dwell time, lowers the chance of operational disruption, and enables earlier defensive action. For manufacturing, where downtime equals financial loss, early visibility can prevent incidents rather than merely respond to them.
The post German Manufacturing Under Phishing Attacks: Tracking a Stealthy AsyncRAT Campaign appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

