AI Sigma Rules: Scale Threat Detection, Drive Down MTTR
Security teams face thousands of alerts every single day. Many of them don’t clearly show whether there’s a true threat behind them. Investigation slows down, analysts lose time on low-value signals, and important findings are often buried in noise.
AI Sigma Rules change this routine. With this new capability in ANY.RUN’s Interactive Sandbox, SOC teams can not only see the source of malicious activity in the standard Sigma format but also use the generated rules across their entire environment. Every confirmed threat now actively improves how your SOC detects the next one and speeds up response.
The Challenge: From Alert Overload to Actionable Knowledge
Most SOCs struggle to turn threats they identify into reusable, scalable detection logic. The obstacles pile up quickly:
- Hard to share knowledge: Insights often stay with the analyst who handled the case instead of becoming team-wide detection logic.
- Manual rule creation: Turning attack behavior into a working rule takes time, testing, and trial-and-error.
- Dependency on a few experts: Only senior engineers usually know how to write or adapt rules for each platform.
- Slow improvement cycles: Even when analysts uncover something important, converting it into broader protection takes too long.
All of this results in the same issue: SOCs fix individual incidents, but the lessons don’t consistently carry over into stronger detection coverage.
How ANY.RUN Solves It with AI Sigma Rules
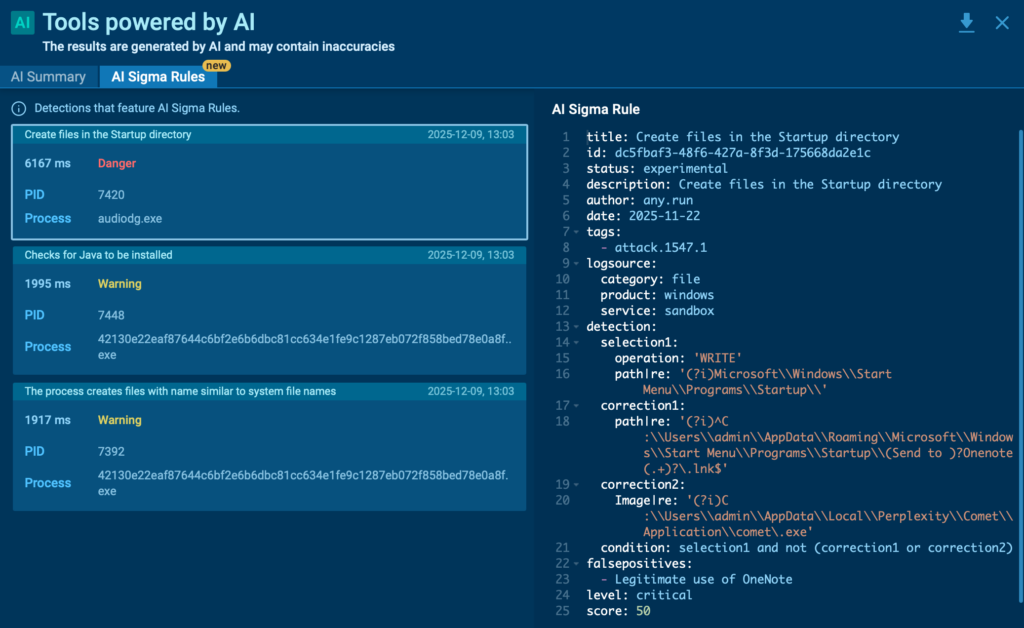
AI Sigma Rules automate one of the slowest and most error-prone parts of detection engineering: turning real attack behavior into usable detection logic.
Instead of manually translating sandbox findings into rules, teams receive a ready-to-review Sigma rule built directly from the recorded malicious activity.
Each rule is generated from what actually happened during execution; the same events, processes, and fields analysts already trust during investigation. As a result, the detection logic stays closely tied to real attacker behavior, not assumptions or static indicators.
With AI Sigma Rules, SOC teams can:
- Understand the root cause of detections by seeing the exact events and fields that triggered them.
- Leverage industry-standard threat descriptions for seamless integration with security workflows.
- Deploy rules directly to SIEM, SOC, or EDR tools to strengthen defenses.
- Accelerate incident response by reducing mean time to resolve (MTTR).
For security leaders, this changes the value of every investigation. A confirmed detection no longer ends with a closed alert but becomes a chance to strengthen the whole infrastructure.
How AI Sigma Rules Work
Let’s take a closer look at how you can quickly get an actionable Sigma rule inside ANY.RUN’s Interactive Sandbox.
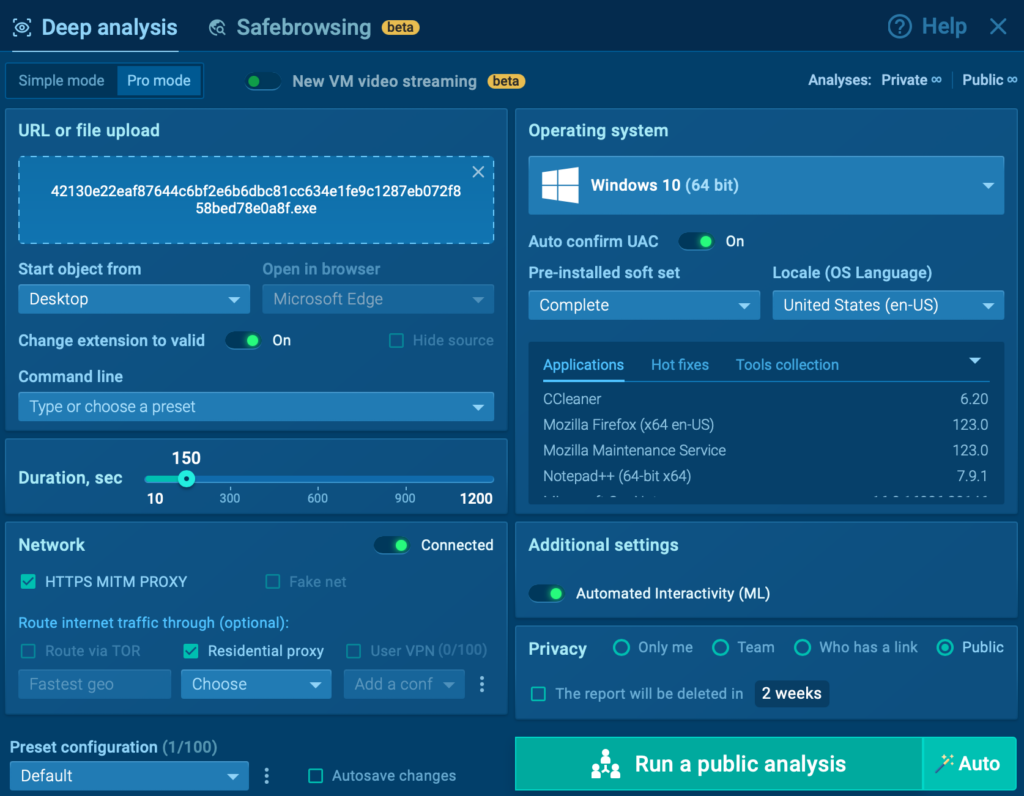
1. Submit a suspicious file or URL
Run the sample in ANY.RUN’s Interactive Sandbox to observe its behavior in real time.
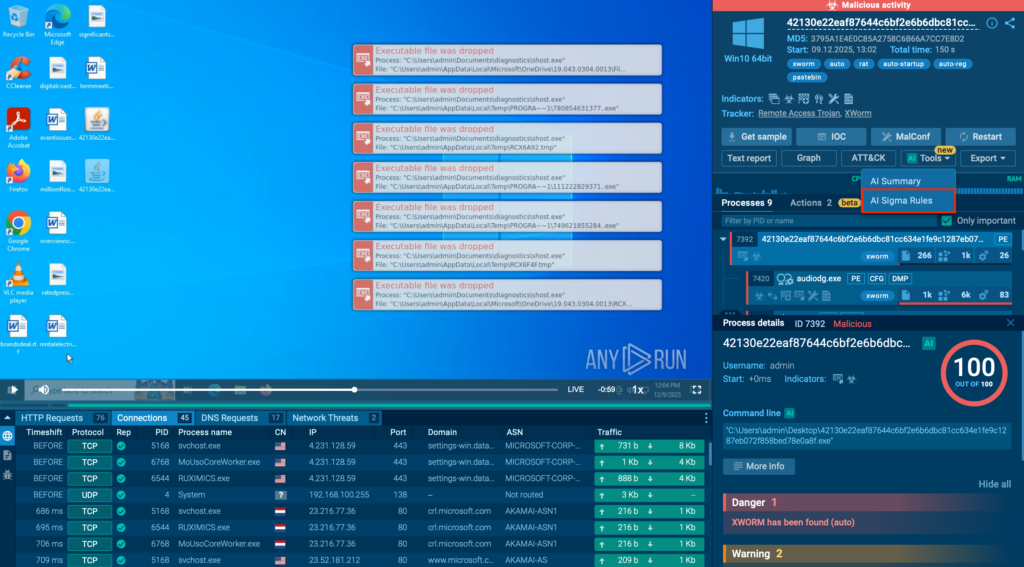
2. Wait for a detection to trigger
As soon as malicious activity is confirmed, the sandbox highlights the event and prepares the data behind it.
3. Open the AI Sigma Rules panel
Inside the detection view, you’ll see a generated Sigma rule that reflects the exact logic behind the alert, including key event fields and matching conditions.
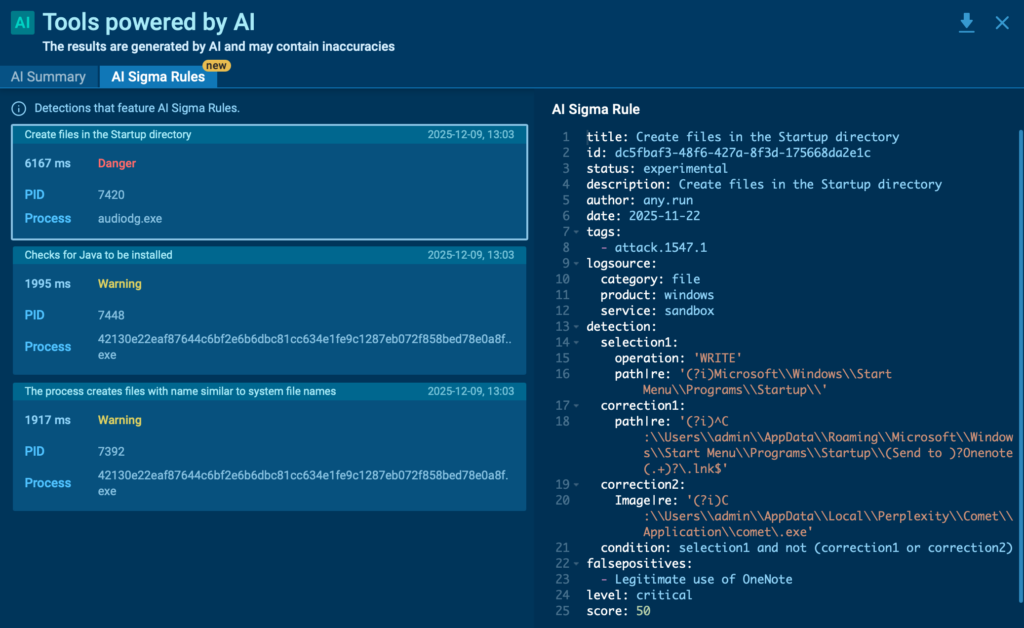
4. Copy or export the rule for deployment
Use it as a correlation rule, hunting query, or alert in your SIEM, EDR, or other detection layers. From there, analysts can fine-tune and activate the rule in minutes.
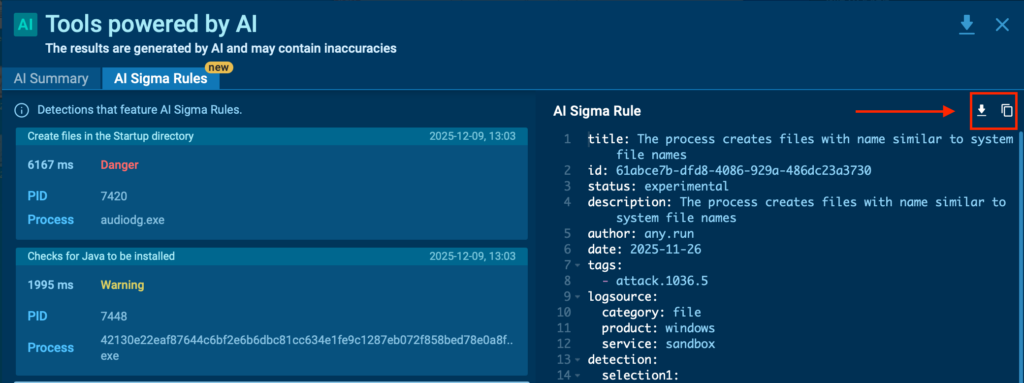
This creates a short, repeatable path that lets SOCs like yours detect this malicious pattern every time it pops up.
How AI Sigma Rules Benefit SOC Teams
AI Sigma Rules change how SOC teams scale what they learn from real attacks. Here’s how that impact shows up in day-to-day operations:
- Reduce MTTR: Cut the time from first detection to live rule by giving analysts a ready Sigma rule instead of a blank page. Minimize the investigation and handover time because the logic behind the alert is already clear and reviewable.
- Increase detection coverage: Expand protection by turning every important detection into a reusable Sigma rule that can run across your SIEM, EDR, and other tools. Close more gaps, faster, with behavior-based rules tied to real attacks your team has seen.
- Boost analyst throughput: Free analysts from low‑value rule drafting by auto generating the first version of each rule. Let them focus on validation, tuning, and decisions rather than copy paste work. Result: less routine work, fewer errors, higher decision speed.
- Strengthen MSSP offerings: Scale one investigation into protection for many tenants by reusing the same Sigma rules. Show customers and auditors clear, transparent logic that proves how your SOC turns incidents into durable detections.
- Raise Enterprise SOC maturity: Unify detection language across Tier 1, 2, and 3 with a shared Sigma format. Make it easier to share rules, onboard new analysts, and review what really protects the business, not just what generated tickets.
Try AI Sigma Rules in Your SOC
AI Sigma Rules are now part of the ANY.RUN Sandbox Enterprise plan, giving teams a faster way to turn real threats into live detection logic.
Want to see how much time it can save your analysts?
Request a demo and walk through the workflow with our experts.
Conclusion
With AI Sigma Rules, SOCs no longer lose valuable insights to case notes or fragmented tooling. Every confirmed threat becomes an opportunity to strengthen the entire detection stack. As attackers evolve and environments grow more complex, this ability to turn daily investigations into continuous improvement becomes a real advantage. ANY.RUN brings that capability directly into the analyst workflow, making better detection not just possible, but repeatable.
About ANY.RUN
ANY.RUN, a leading provider of interactive malware analysis and threat intelligence solutions, helps security teams investigate threats faster and make more confident decisions. Used by over 15,000 organizations and 500,000 analystsworldwide, the service combines real-time sandbox analysis with actionable threat intelligence to support daily SOC operations.
With features like interactive malware execution, automated detections, threat intelligence lookup, and now AI Sigma Rules, ANY.RUN enables teams to move from investigation to prevention with greater speed and clarity. It supports Windows, Linux, and Android environments and integrates seamlessly into modern security stacks.
The post AI Sigma Rules: Scale Threat Detection, Drive Down MTTR appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

