LOLBin Attacks Explained with Examples: Everything SOC Teams Need to Know
Some attacks smash the door open. LOLBins just borrow your keys and walk right in.
They’re tricky because tools everyone trusts suddenly start doing things that don’t match their usual job; loading odd-looking modules, decoding files that shouldn’t need decoding, or quietly handing work off to hidden PowerShell scripts. At first glance it all feels normal, but a closer look shows a payload slowly being set up in the background.
For analysts, the real challenge is noticing that shift before it grows into a full incident.
Let’s take a closer look at what’s hiding behind LOLBin attacks, and how advanced SOC teams uncover them in minutes without much effort.
What Are LOLBin Attacks?
LOLBin attacks occur when threat actors repurpose legitimate Windows system binaries (rundll32, certutil, mshta, powershell, regsvr32, etc.) to carry out malicious actions. These tools are built into every system, signed by Microsoft, and widely used by normal applications, which is why attackers rely on them.
Using LOLBins, adversaries can:
- Load disguised or renamed DLLs
- Decode or unpack payloads using built-in utilities
- Trigger PowerShell or script execution indirectly
- Execute code completely in memory
- Blend malicious steps into routine system activity
This approach lets attackers avoid dropping obvious malware and makes early-stage execution appear clean and legitimate.
Why LOLBin Attacks Are a Real Risk for Businesses?

The real problem isn’t the binaries themselves but how much visibility your SOC loses when attackers hide behind them. When malicious activity runs inside trusted system tools, the early signs of an intrusion become dramatically harder to catch.
Here’s what makes them dangerous:
- Normal on the surface: Activity is routed through tools the environment already trusts.
- Minimal forensic evidence: In-memory execution leaves few files to investigate.
- Weak signature coverage: Microsoft-signed binaries rarely trigger basic detection rules.
- Extended dwell time: Attackers gain more space for lateral movement and credential access.
- Harder investigations: Clean-looking events force analysts to dig deeper to find the real issue.
- Higher SOC workload: The team must identify subtle behavior shifts instead of relying on clear indicators.
This means attackers can establish footholds, unpack payloads, or run loaders while the environment still appears clean, leading to late detection and higher incident impact.
The Fastest Way to Reveal LOLBin Abuse: How ANY.RUN Makes It Obvious
LOLBin attacks only work when no one can see what’s really happening behind those trusted Windows binaries. ANY.RUN removes that advantage by showing analysts the full behavior in real time; not just the file name or the process label, but the actual actions taking place underneath.
With ANY.RUN’s sandbox, “normal-looking” activity turns into something you can spot immediately:
- Process behavior becomes clear at a glance: rundll32 loading a strange module, certutil decoding an unexpected file, mshta spawning hidden PowerShell… every unusual step is visible right away.
- Parent–child chains tell the full story: Instead of digging through logs, you see exactly who launched what, and whether it fits normal usage patterns.
- Command lines show the truth: Encoded strings, odd export calls, Temp-folder payloads, and hidden flags are exposed instantly.
- In-memory actions are no longer invisible: Even when attackers avoid dropping files, the sandbox reveals decoded scripts, loader behavior, and execution flow.
- Artifacts stay captured: Renamed DLLs, extracted archives, decrypted payloads, and cleanup attempts can all be reviewed without rushing or digging.
- Analysis becomes interactive: Analysts can click deeper, replay events, and confirm suspicions in minutes instead of piecing everything together manually.
Instead of guessing whether a trusted binary is being misused, ANY.RUN shows the exact behavior clearly, quickly, and with the context you need to act confidently.
Real-Time LOLBin Attacks Revealed Inside ANY.RUN in Minutes
Here are a few real LOLBin attacks captured and analyzed inside ANY.RUN.
Take a look at how these techniques unfold in real time, and see how easily your team can expose the same behavior using interactive analysis.
1. LOLBin RUNDLL32.EXE
ATT&CK® Technique: T1218.011 – Rundll32
What this attack is:
A trusted Windows utility used to load and run a disguised module, letting attackers execute their payload under a legitimate process.
See this RUNDLL32 attack exposed live inside ANY.RUN:
→ Gh0st RAT delivered through rundll32
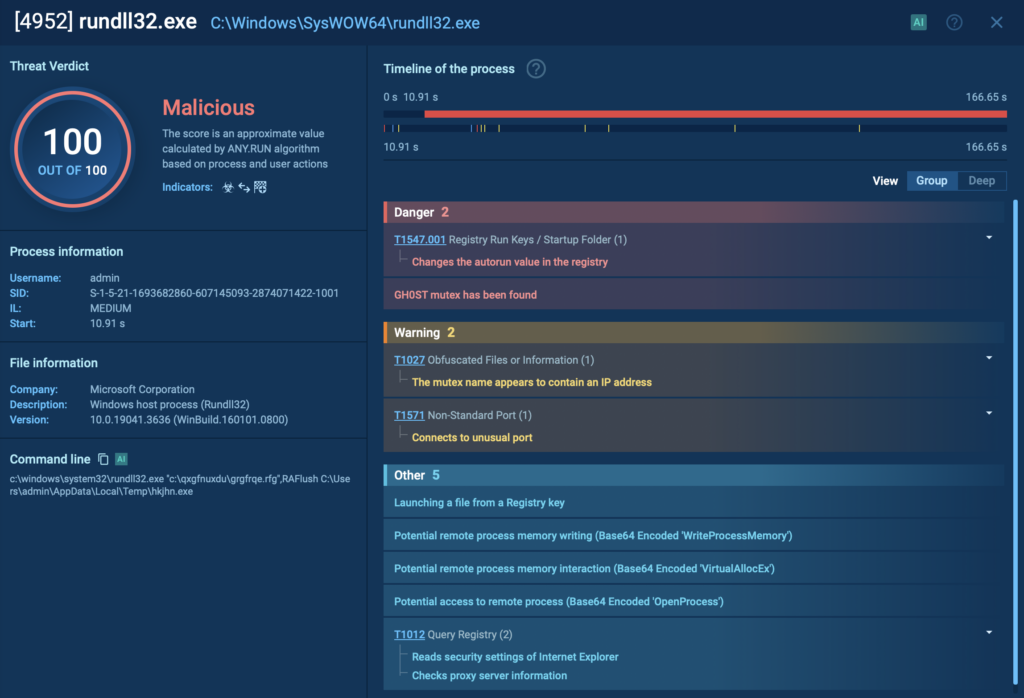
Gh0st RAT launches the legitimate rundll32.exe, which then loads a disguised module named grgfrqe.rfg from an unusual directory. The file isn’t a typical DLL at first glance; the strange extension is intentionally chosen to bypass simple “.dll” rules and blend into the system.
Once loaded, rundll32 calls an export named RAFlush and passes it a path to a temporary executable: C:UsersadminAppDataLocalTemphkjhn.exe.
From there, the chain unfolds:
- Load: rundll32 loads the renamed DLL (grgfrqe.rfg)
- Invoke: The RAFlush export is executed
- Drop/execute: The module drops, unpacks, or runs hkjhn.exe inside %Temp%
- Cleanup: Temporary files are removed to reduce traces
This is a typical LOLBin pattern: a trusted binary quietly executing hidden functionality while the malicious module stays disguised and difficult to catch without behavioral visibility.
Use this ANY.RUN’s TI Lookup query to explore similar samples and collect IOCs:
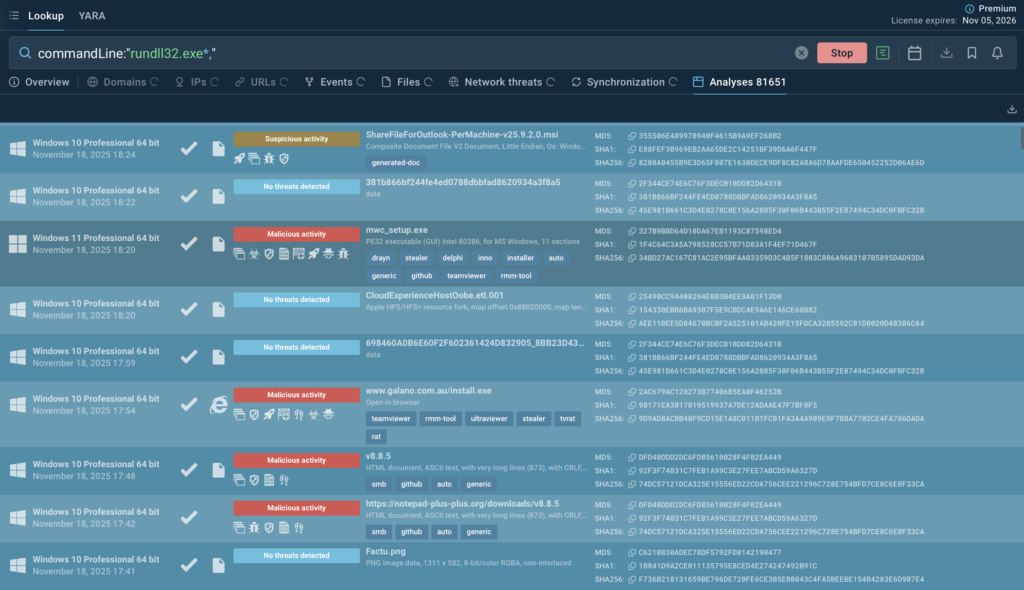
2. LOLBin CERTUTIL.EXE
ATT&CK® Technique: T1140 – Deobfuscate/Decode Files or Information
What this attack is:
A built-in Windows tool misused to decode, transform, or prepare hidden payloads before execution; all under the guise of a legitimate system operation.
See this CERTUTIL attack exposed live inside ANY.RUN:
→ PXAStealer decoding and unpacking files through certutil
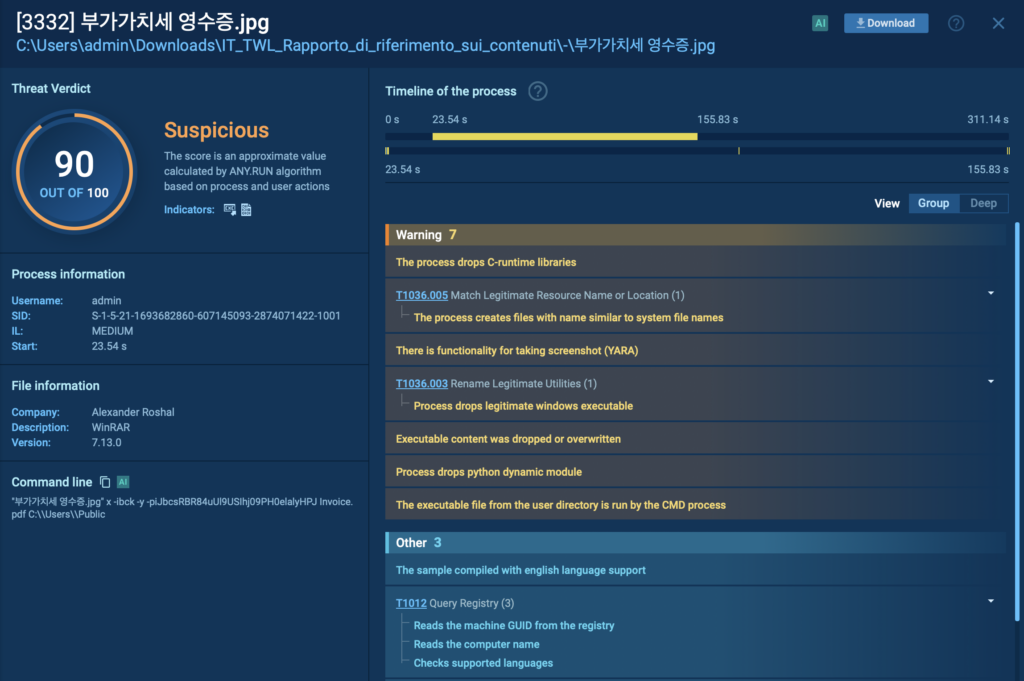
PXAStealer uses certutil.exe to quietly decode a disguised file named DA 성형외과 재무 보고서.pdf. Although it appears to be a harmless PDF, certutil converts it into Invoice.pdf, which is not a document at all but a RAR archive.
The attack continues as a renamed instance of WinRAR, disguised as a JPEG image (부가가치세 영수증.jpg), unpacks the archive using the password
iJbcsRBR84uUl9USIhj09PH0elalyHPJ.
The execution flow looks like this:
- Decode: certutil transforms the fake PDF into an archive
- Extract: The disguised WinRAR instance unpacks it
- Execute: The payload inside the archive is launched
- Cleanup: Files are removed or hidden to minimize traces
This combination, a trusted decoding tool + disguised content + hidden extraction, is a classic LOLBin chain designed to slip past basic detection and appear routine unless investigated behaviorally.
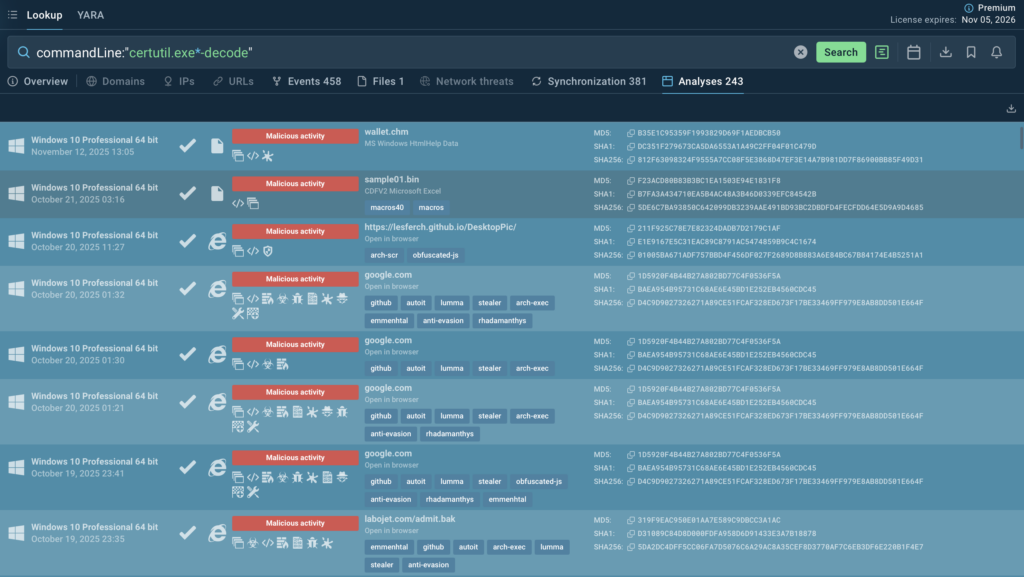
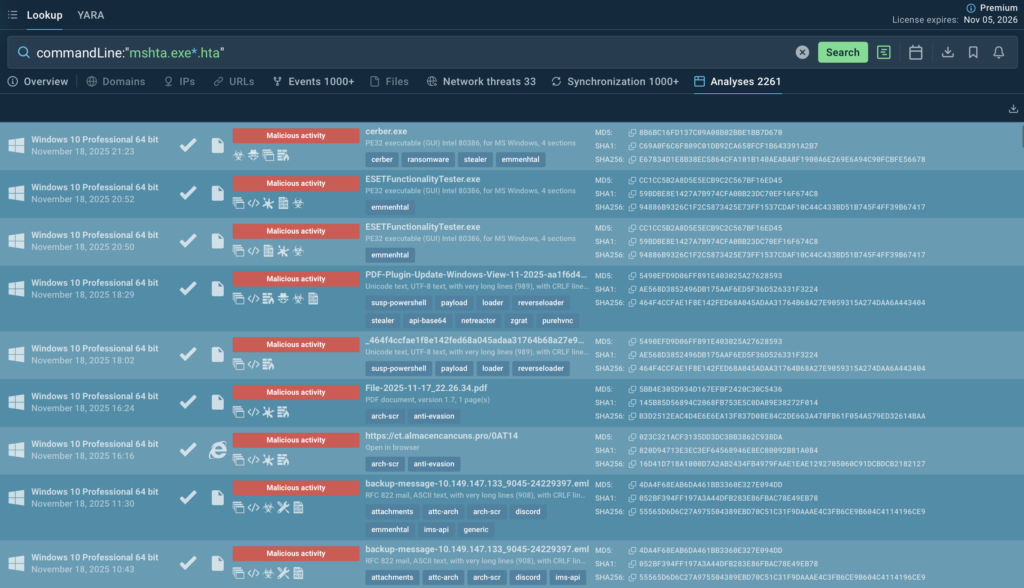
Check out more sessions of this attack and gather related IOCs using this TI query:
commandLine:”certutil.exe*-decode”
3. LOLBin MSHTA.EXE
ATT&CK® Technique: T1218.005 – Mshta
What this attack is:
A trusted Windows utility used to execute HTA-based scripts that trigger hidden PowerShell activity, enabling in-memory execution without leaving clear artifacts.
See this MSHTA attack exposed live inside ANY.RUN:
→ ReverseLoader executed through mshta + hidden PowerShell
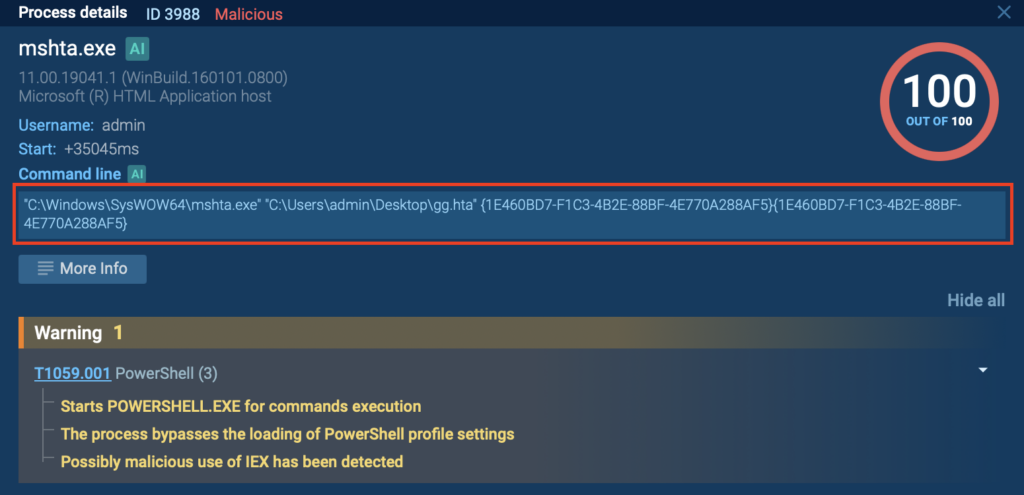
In this attack chain, mshta.exe launches an HTA file named gg.hta from the user’s desktop. The HTA isn’t a simple script; it contains obfuscated logic that immediately spawns a PowerShell process configured to stay out of sight.
PowerShell is executed with:
- -NoProfile
- -WindowStyle Hidden
- A Base64-encoded command decoded and passed into Invoke-Expression
This allows the payload to run entirely in memory, without dropping a traditional file on disk.
Here’s how the chain unfolds:
- Deliver: The HTA file is delivered locally or through a link
- Execute: mshta runs the HTA script as a trusted system tool
- Decode & run: PowerShell decodes the Base64 string and executes the logic
- Stealth: Hidden windows and in-memory execution conceal most traces
This mshta + encoded PowerShell combination is a well-known method for quietly loading backdoors, RATs, and script-based loaders while appearing to use legitimate system components.
Check out more sessions of similar attacks and gather relevant data using this TI query:
Strengthening Defenses Against LOLBin Techniques
For SOC managers, stopping LOLBin abuse starts with improving how the team spots unusual behavior inside trusted system tools. These attacks don’t announce themselves, so the goal is to create clearer visibility and reduce the time analysts spend guessing what’s happening.
Focus on behavior, not the binary: Even legitimate tools like rundll32, certutil, and mshta become suspicious when they load odd modules, decode files, or trigger hidden PowerShell. Building detections around these behaviors helps the team surface threats that signatures often miss.
Give analysts a simple triage path: Most LOLBin alerts look harmless at first. A lightweight checklist, parent process, command line, execution path, and any decoding or script activity, keeps investigations consistent and prevents early-stage activity from slipping by.
Use sandbox analysis to confirm suspicious cases quickly: Instead of piecing clues together from logs, ANY.RUN gives analysts the full picture in seconds: process chains, decoded content, dropped components, and in-memory activity. This cuts investigation time and helps the team act confidently.
Add small policy controls where possible: Limiting execution from user-controlled folders or applying basic PowerShell restrictions reduces the surface attackers can exploit without disrupting normal operations.
A few focused improvements like these help SOC managers turn LOLBin activity from a hidden risk into something the team can catch early and handle efficiently.
About ANY.RUN
ANY.RUN is a leading provider of interactive malware analysis and threat intelligence solutions, built to give SOC teams the visibility they need when traditional tools fall short.
Today, 15,000+ organizations worldwide use ANY.RUN to speed up investigations, strengthen detection pipelines, and give their teams a clearer view of what’s really happening on their endpoints.
SOC teams using ANY.RUN report measurable improvements, including:
- 3× boost in SOC efficiency
- 95% faster initial triage
- Up to 58% more threats identified
- 21-minute reduction in MTTR per incident
Give your team the visibility they need: Try ANY.RUN now
The post LOLBin Attacks Explained with Examples: Everything SOC Teams Need to Know appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
