Healthcare MSSP Cuts Phishing Triage by 76% and Launches Proactive Defense with ANY.RUN
Scaling as a managed security provider can be a mixed blessing. Growth comes with more revenue, but also with increasingly high demands related to maintaining SLAs, quality, and compliance. For MSSPs in healthcare, this pressure is intensified by regulations like HIPAA and NIS2, along with the striking cost of a single mistake.
This was a challenge one of our clients, a mid-sized MSSP specializing in healthcare, had to face. As it expanded to support over a dozen hospitals, clinics, and labs with 2,000+ endpoints, their resources were thinning.
We spoke with the organization’s SOC lead about how they were able to reshape their workflow with ANY.RUN’s solutions, and what brought them the most results.
Core MSSP Challenges: Overload and Compliance
The first topic we discussed was what the workflow was like initially and why the need for new solutions occurred. In their words, even with experts on board and acknowledged tools, occurring gaps were growing harder to fill:
“It [the workflow] wasn’t that bad: we have a strong team and a SOAR platform by a well-known vendor. Teamwork was – and remains – our strong point. But as the client base grew, it became harder to maintain SLAs, which are pretty strict in healthcare. Tier 1 and 2 analysts were overwhelmed by an increased number of alerts coming from different customers.”
The analysts had to deal with hundreds of emails and URLs reported by clients each week, and the verification process was mostly manual. Some multi-step phishing cases required up to 40 minutes of analysis, as they required multiple tools and resources, or even custom virtual machines. The need for better triage solutions and prioritization protocols intensified.
Key challenges:
- Slow MTTR across multiple customers
- Tier 1 analysts indicated roughly 20% closure rates
- Excessive escalations from Tier 1 to Tier 2
- Lack of automation in triage
- Struggles to maintain compliance
Concerns that Come with Growth
After discussion, the company leaders came up with a plan to enhance the processes:
- Introducing more automation in alert triage to reduce workload
- Obtain higher-quality threat data for faster decision-making
- Shifting from reactive to proactive defense
Some team members expressed concerns about introducing a new solution:
““What if we have to rebuild the workflow from scratch? What if automation fails to work as promised?” – these are some of the questions the analysts raised. So we had to be selective [when choosing a solution]. We needed something flexible and easy to integrate.”
Immediate Improvements with ANY.RUN’s Interactive Sandbox
The MSSP launched the streamlining process by adding just one solution to the stack at a time. The choice fell on ANY.RUN’s Interactive Sandbox, as it offered a unique approach to dynamic malware analysis:
“It stood out among other options with interactivity. Automation is powerful, but not always enough. Interactivity offered more depth and understanding of malware.”
The MSSP has been using the sandbox for one and a half years, mostly as a solution integrated in their SOAR. The automated mode helped effortlessly deal with overflowing low-priority incidents, even if they included multiple stages like hidden links, redirects, and CAPTCHAs.
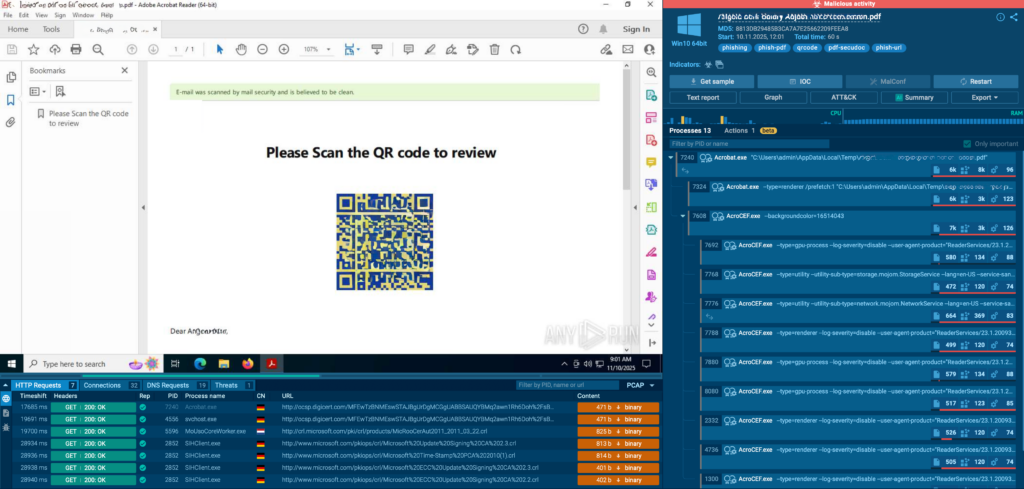
Just in the past few weeks, multiple phishing campaigns were prevented through interactive analysis. Two of them involved common office tools used in medical institutions, such as OneDrive and Jotform:
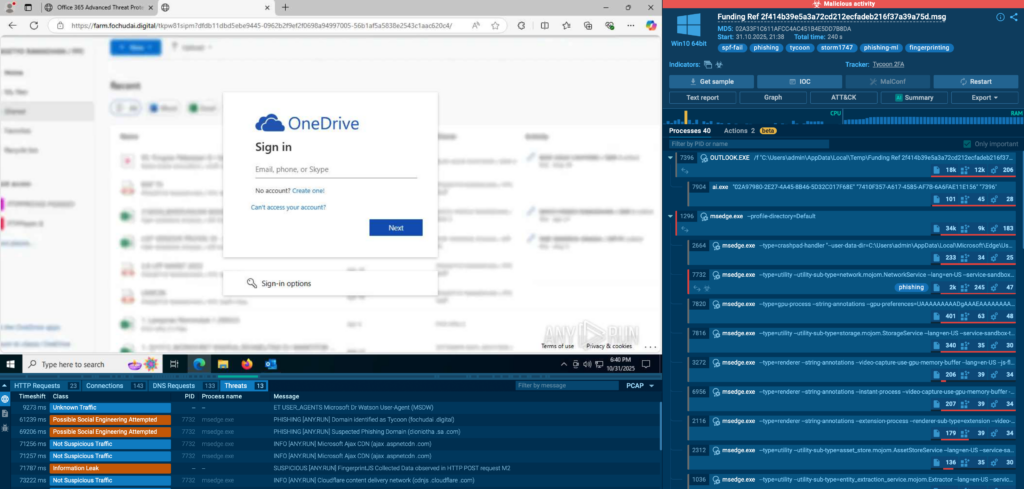
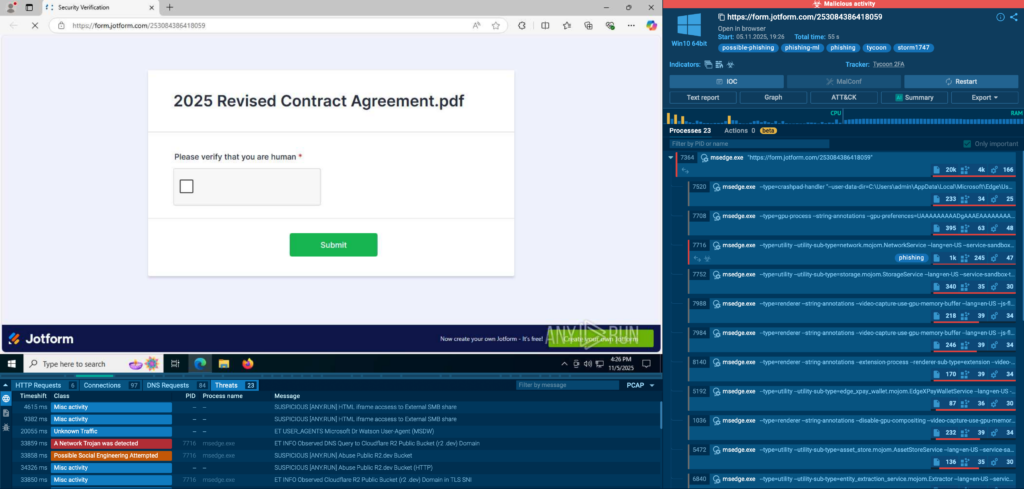
In SOC lead’s words, concerns related to automation and integration didn’t turn out to be justified:
“The integration worked much better than was expected. With minimal changes in the workflow, we achieved stronger results: Tier 1 analysts had far more capacity; analysis of both low- and high-priority incidents became easier. No manual VM unfolding, no tedious escalations.”
More Results with Threat Intelligence
As part of a scheduled assessment of their infrastructure, the team was also shopping for new sources of threat intelligence. After a two-week trial, they decided to fully implement ANY.RUN’s products into the existing workflows.
“We were happy with the results ANY.RUN’s sandbox brought, so it made sense to support resources we’ve been using for a while with TI solutions from the same vendor.”
Threat Intelligence Lookup and Threat Intelligence Feeds added a finishing touch to the new defense strategy. They brought outcomes like:
- Real-time, high-confidence IOCs
 Better preventative measures
Better preventative measures
- Broad threat monitoring
 Early detection of attacks
Early detection of attacks
- Threat context just a click away
 Fast enrichment of isolated artifacts
Fast enrichment of isolated artifacts
- Behavioral data through sandbox analyses
 New detection rules
New detection rules
- Automation via SOAR integration
 Effortless responses and ticket closure
Effortless responses and ticket closure
Together, these solutions enabled the SOC to proactively hunt and neutralize threats before they could impact client operations.
Measurable Outcomes
| Solution | Use Case | Result* |
|---|---|---|
| Interactive Sandbox | Dynamic analysis of URLs/files | 76% reduction in phishing triage time (from 30-40 minutes to 4-7 minutes) |
| Full visibility into malware behavior | Tier 1 closure rate increased from 20% to 70% | |
| TI Lookup | Enrichment of IOCs with threat data context | 34% fewer false escalations |
| TI Feeds | Expanded threat coverage with live threat intelligence in SOAR | 45% improved MTTR and 55% fewer false positives |
| Early detection through monitoring of latest attacks on 15,000 companies | 20 seconds: average MTTD for phishing |
*Based on the company’s statistics after using ANY.RUN’s solutions
Phishing Campaign Case and Successful Mitigation
A recent incident illustrated the efficiency of the new workflow based on early detection and mitigation:
“A couple of weeks ago, our analysts spotted a suspicious connection on a client endpoint. TI Lookup immediately showed that it’s tied to a known malicious C2 server.”
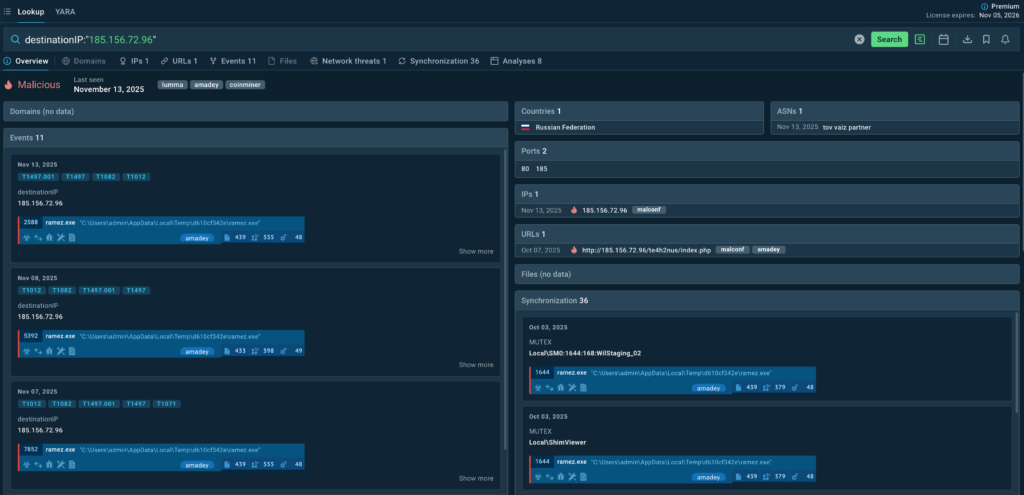
“For further insights, they browsed other analyses and saw a threat sample featuring phishing. The sandbox then helped uncover the entire attack chain; and retrieved IOC were used to refine detection rules.”
Meeting Healthcare’s High Compliance Bar
Healthcare is a sector with real urgency and high regulatory demands. Acting as an MSSP in this industry requires auditability, transparency, and SLA adherence. The SOC lead noted that protocols and regulations that are common in healthcare industry became easier to fulfill with ANY.RUN:
“Since we implemented new solutions, every investigation now comes with evidence and threat data, from MITRE tags to screenshots. This made reporting faster and extra work fell off our shoulders.”
The MSSP is now driven by:
- Faster triage across multiple customers
- Proactive and scalable threat detection strategy
- Decision-making supported by high-quality data
- Audit-ready evidence aligned with industry regulations
Conclusion: From Reactive to Proactive Defense
By integrating ANY.RUN’s Interactive Sandbox, TI Lookup, and TI Feeds, this MSSP built a proactive defense system.
“Needless to say, we still work hard every day, but ANY.RUN gave us the tools to manage our daily tasks more effectively. More clarity and quick access to reliable information made all the difference. It lightened our load without taking away in quality.”
About ANY.RUN
Built for modern MSSPs and Enterprises, ANY.RUN empowers analysts to deliver faster, deeper, and more transparent threat analysis for their clients. The Interactive Sandbox exposes full attack behavior, from process execution to network activity, enabling analysts to investigate incidents in real time and make confident, data-driven decisions.
Cloud-based and ready out of the box, ANY.RUN supports Windows, Linux, and Android environments, streamlining multi-tenant operations without complex setup. Integrated Threat Intelligence Lookup and TI Feeds provide continuously updated, automation-ready IOCs for better detection, response, and reporting across all client environments.
See how ANY.RUN can elevate your MSSP: start a 14-day trial today
The post Healthcare MSSP Cuts Phishing Triage by 76% and Launches Proactive Defense with ANY.RUN appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

