How scammers use email for blackmail and extortion | Kaspersky official blog
“We’ve hacked your computer! Send money to the specified account, or all your photos will be posted online”. You or someone you know has probably encountered an email with this kind of alarming message.
We’re here to offer some reassurance: nearly every blackmail email we’ve ever seen has been a run-of-the-mill scam. Such messages, often using identical text, are sent out to a massive number of recipients. The threats described in them typically have absolutely no basis in reality. The attackers send these emails out in a “spray and pray” fashion to leaked email addresses, simply hoping that at least a few recipients will find the threats convincing enough to pay the “ransom”.
This article covers which types of spam emails are currently prevalent in various countries, and explains how to defend yourself against email blackmailers.
Classic scams: hacks, sextortion, and “your money or your life”
Classic scam emails may vary in their content, but their essence always remains the same: the blackmailer plays the role of a noble villain, allowing the victim to walk away unharmed if they transfer money (usually cryptocurrency). To make the threat more believable, attackers sometimes include some of the victim’s personal data in the email, such as their full name, tax ID, phone number, or even their physical address. This doesn’t mean you’ve actually been hacked — more often than not, this information is sourced from leaked databases widely available on the dark web.
The most popular theme among email blackmailers is a “hack” where they claim to have gained full access to your devices and data. Within this theme, there are three common scenarios:
- The attacker is concise and gets straight to the point: they state the exact amount of money you need to transfer to prevent your private information from becoming public.
- Detailed and dramatic emails: these elaborate spam emails contain a wealth of detail about the malware the attacker allegedly used to infect the recipient’s device, and the types of data they’ve accessed. This usually includes everything at once: the PC itself, the mouse, the webcam, and the keyboard. Sometimes, the scammers even graciously advise you to change your passwords regularly and avoid clicking on unknown links in the future to prevent unpleasant situations. On this point we actually agree with their recommendations.
- The specific details of the “hacker attack” and the attacker’s demands are omitted from the email body. Instead, the recipient is prompted to find this information by clicking a link to a website. Scammers use this tactic to bypass email spam filters.
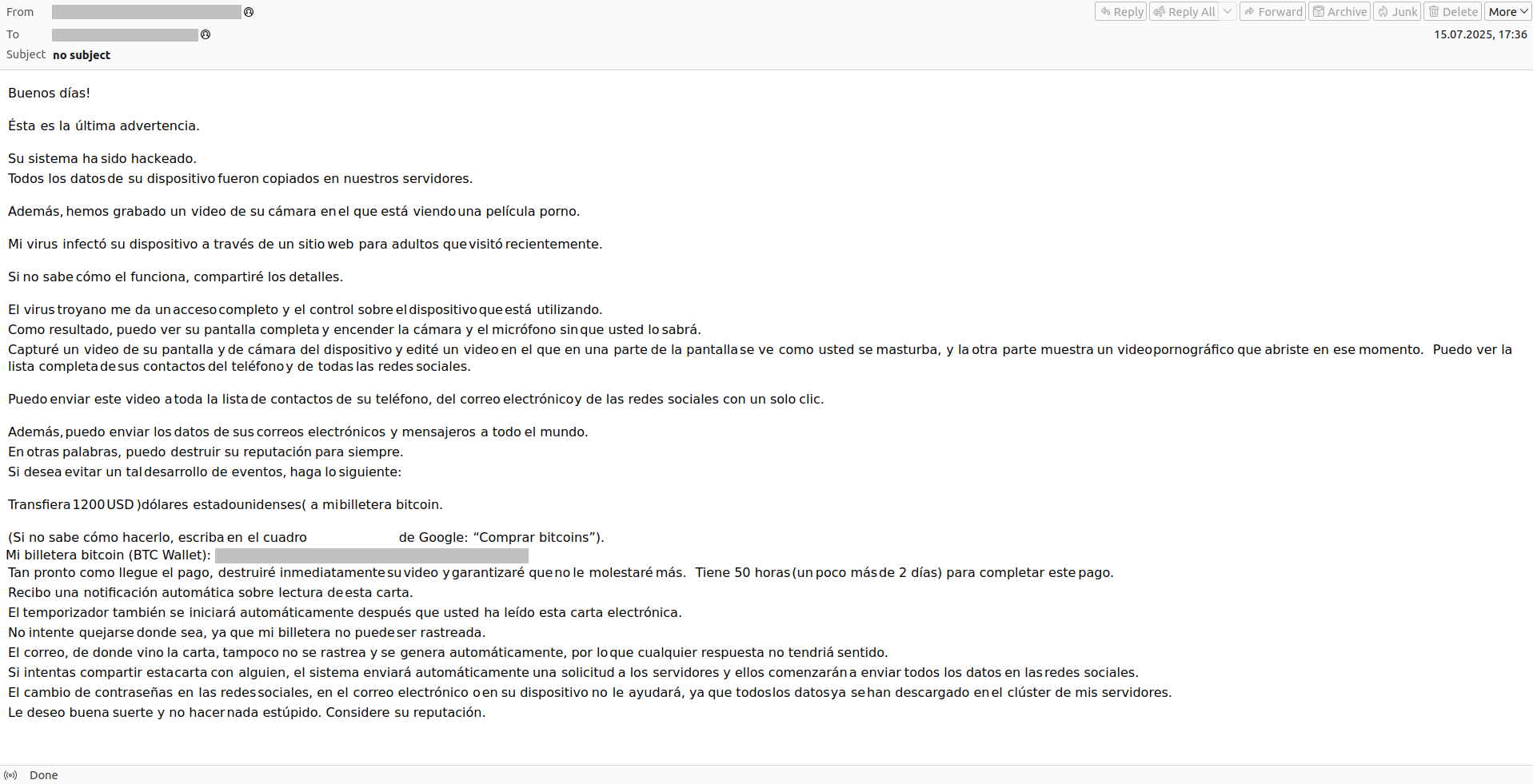
Blackmailers also don’t shy away from the topic of adult content. Typically, they simply intimidate the victim with threats that everyone will find out what kind of explicit content they’ve allegedly been viewing. Some attackers go further — they claim to have gained access to the person’s webcam and recorded intimate activity while simultaneously screen-recording their PC. The price of their silence starts at several hundred dollars in cryptocurrency. Crucially, these blackmailers intentionally try to isolate the victim by telling them not to report the email to law enforcement or loved ones, and claiming that doing so will immediately trigger the threats. By the way, safe and private viewing of adult content is a challenge unto itself, but we’ve covered that in Watching porn safely: a guide for grown-ups.
Perhaps the most extreme form of email blackmail involves death threats. Naturally, such an email would make anyone uneasy, and many people become genuinely worried for their own safety. The noble hitman, however, is always willing to spare the victim’s life if they can “outbid the one who ordered the hit”.
“You have 72 hours left to live.” The blackmailer suggests not involving the police and simply paying off “the one who ordered the hit” instead
You’ve been served: law enforcement impersonation scams in Europe
Besides legends of “noble hackers” and “hitmen” who immediately offer a way out for a hefty fee, there are longer, more elaborate scams.
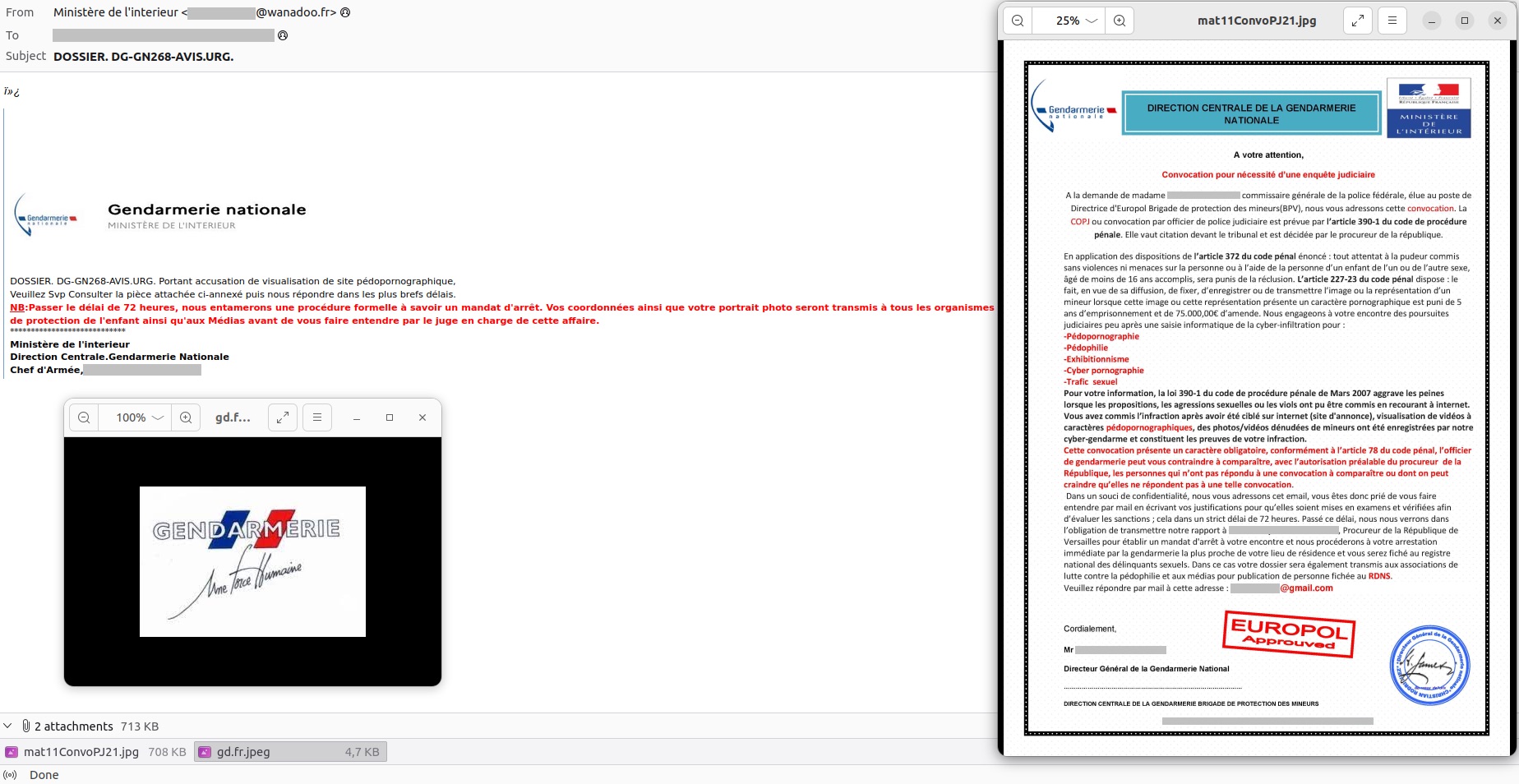
In these attacks, scammers pose as law enforcement officers. They don’t ask for money right away, as that would arouse suspicion. Instead, the victim receives a “summons” accusing them of committing a serious, often highly delicate crime. This typically involves allegations of distributing pornography (including child pornography), of pedophilia, human trafficking, or even indecent exposure. The “evidence” isn’t pulled out of thin air, but supposedly taken directly from the victim’s computer, to which the “special services” have gained “remote access”.
The document is designed to instill absolute terror: it includes a threat of arrest and a large fine, a signature with a seal, an official address, and names of high-ranking prosecutors. The scammers demand that the victim promptly makes contact via the email address provided in the message to offer an explanation — then, perhaps, the charges will be dropped. If the victim fails to respond, they’re threatened with arrest, registration on a list of sex offenders, and having their “file” passed to the media.
When the terrified victim contacts the attackers, the scammers then offer to “pay a fine” for an “out-of-court settlement of the criminal case” — a case that, of course, doesn’t exist.
These types of emails are sent under the guise of coming from major law enforcement organizations like Europol. They’re most frequently addressed to residents of France, Spain, the Czech Republic, Portugal, and other European countries. They also share a curious feature: typically, the subject line and the body of the email are quite brief, with the entire fraudulent case being laid out in attached documents. Reminder: we can’t stress this enough — never open email attachments if you don’t know or trust the sender! And to ensure that malicious and phishing emails don’t even reach your inbox, use a reliable protective solution.
Authority scams in CIS countries
The “law enforcement theme” is also prevalent in CIS (former-Soviet-Union) countries. In 2025, scammers circulated “Summons for Criminal Investigation” alleging the initiation of a criminal case. This was supposedly issued by the Russian Ministry of Internal Affairs in collaboration with such fantastic units as “Russian Interpol” and the “Bureau of Investigation Against Organized Crime”.
According to the fictional narrative, a certain “National Center for the Analysis of Child Pornography and Exhibitionism Images” had seized computers somewhere and determined that the recipient’s IP address was used to “access inappropriate and pornographic websites”. Of course, a quick online search will reveal that none of the organizations mentioned in that email have ever officially existed in Russia.
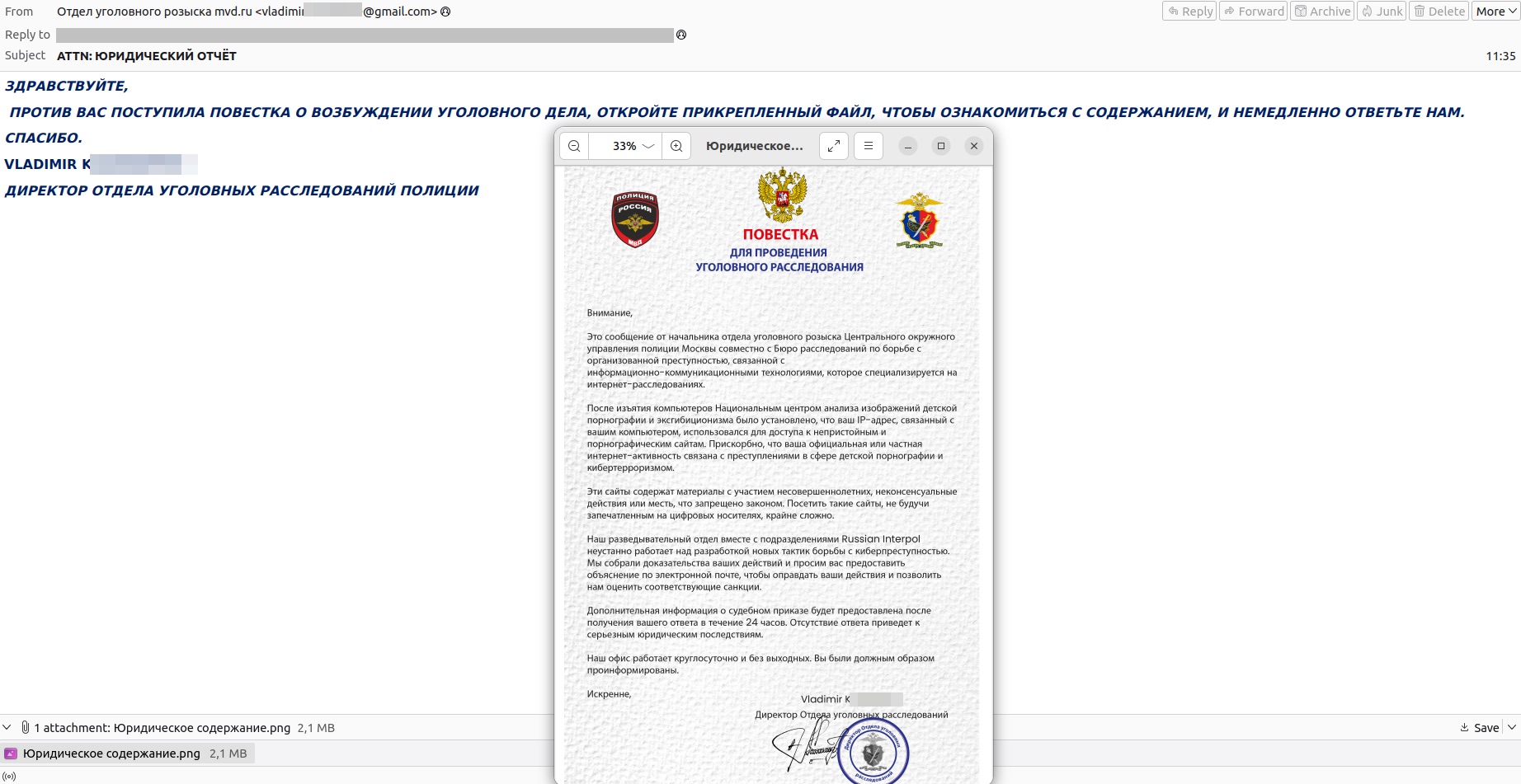
The “Director of the Police Criminal Investigation Department” will, for added persuasiveness, write in ALL CAPS, and sign their name with an English transliteration
In another similar email, the recipient, at the behest of the head of the “Russian Federal Bureau of Investigation (FBI)”, supposedly became a person of interest to a certain “International Criminal Police Organization — Interpol of the Federal Police of Russia”. (We should clarify that no law enforcement agencies with even remotely similar names have ever existed in Russia.) In the email, the attackers refer to a “Cybercrime Act in accordance with the Crimes Act of 1900 (sic!) from 245RU(2)” — laws so secret that apparently no legal expert knows they exist. Moreover, the message, sent from a generic Gmail address, is supposedly from the Minister of Internal Affairs himself. However, in the attached summons, he is referred to as the “Commissioner of the Federal Police of the Russian Federation” — likely a clumsy translation from English.
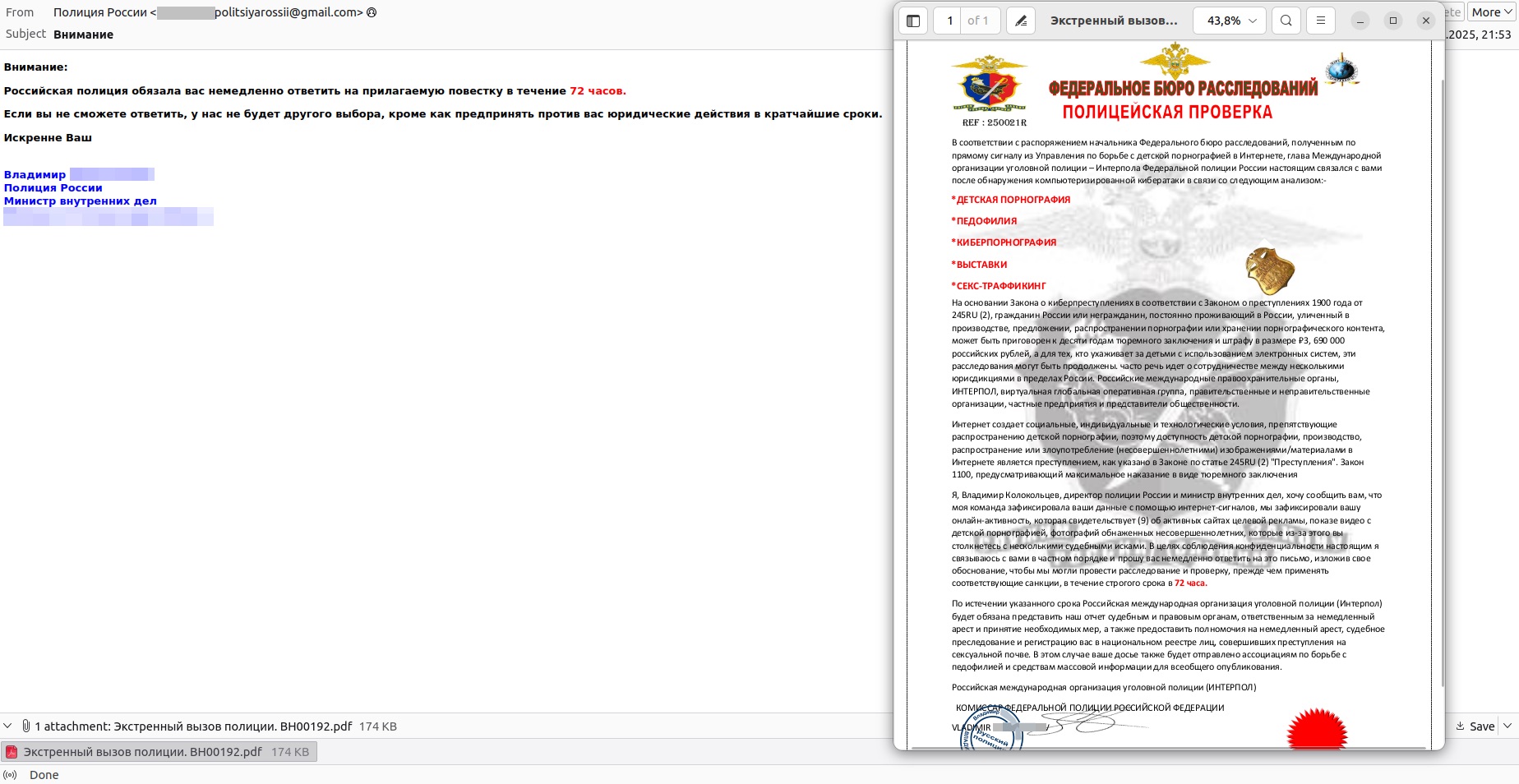
The scam email from the non-existent “Russian Federal Bureau of Investigation” is signed by none other than the Minister of Internal Affairs
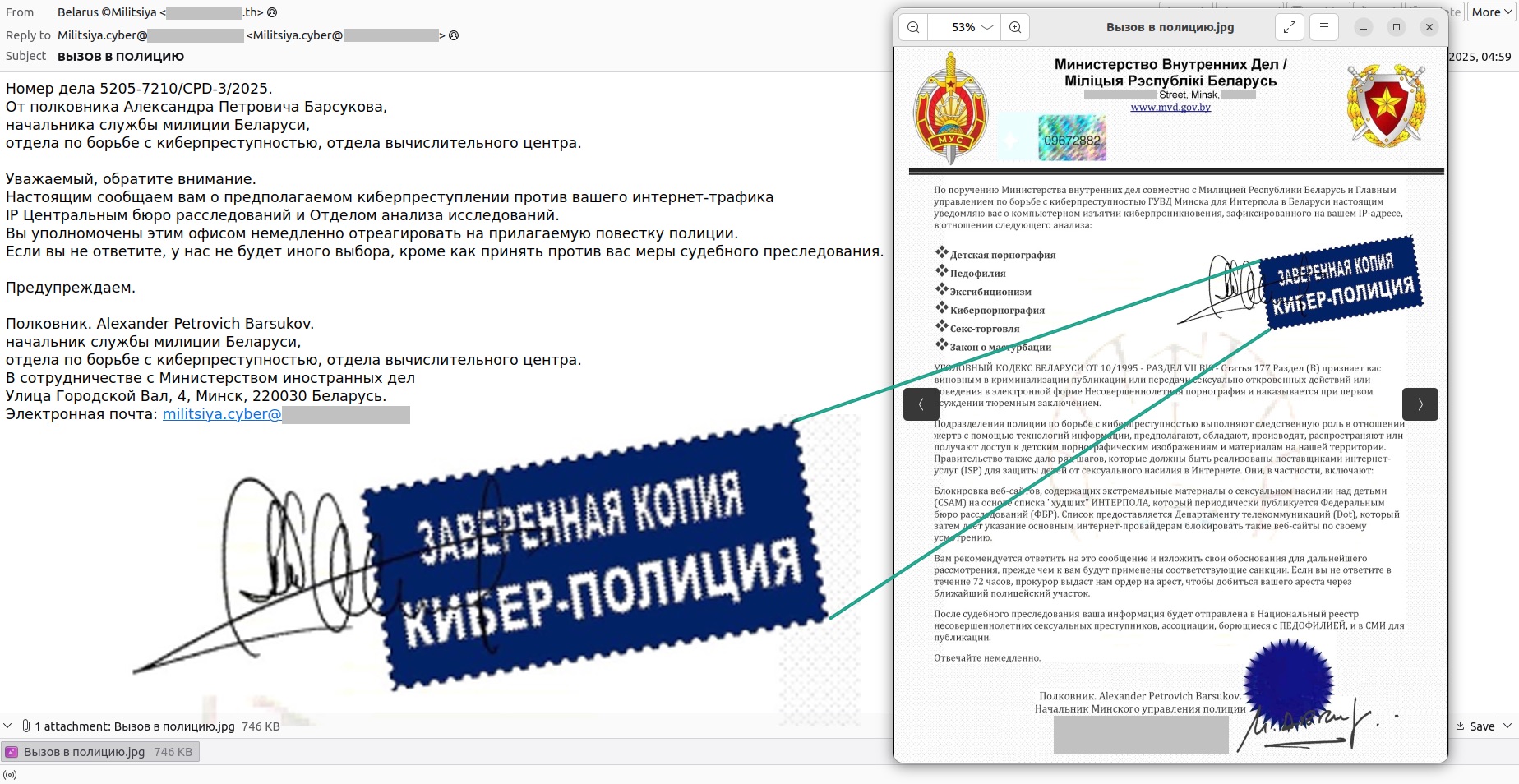
Similar scam emails also reach residents of Belarus, arriving in both Russian and Belarusian. The victims are supposedly being pursued by multiple agencies simultaneously: the Ministry of Internal Affairs and Ministry of Foreign Affairs of Belarus, the Militsiya of the Republic of Belarus, and a certain “Main Directorate for Combating Cybercrime of the Minsk City Internal Affairs Directorate for Interpol in Belarus”. One might assume that the email recipient is the country’s most wanted villain, being hunted by the “cyberpolice” itself.
In the summons, the blackmailers cite non-existent laws, and threaten to add the victim to a fictitious “National Register of Underage (sic!) Sexual Offenders” — a clear machine translation failure — and, of course, request an urgent reply to the email.
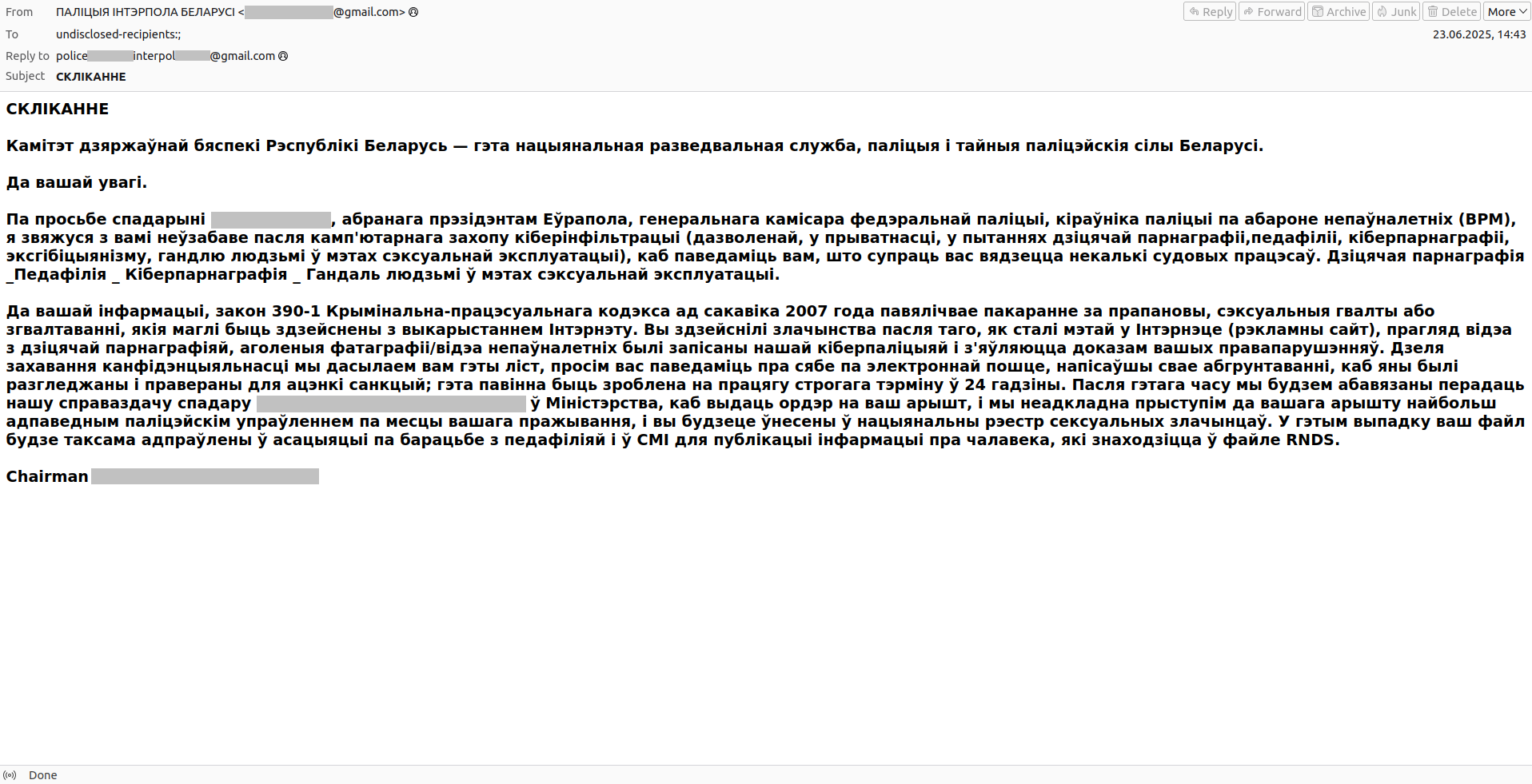
In another campaign, attackers sent emails in the name of the real State Security Committee of Belarus. However, they referenced a fake law and contacted the accused at the behest of the President of Europol — never mind that Europol doesn’t have a President, and the name of the real executive director is completely different.
In addition to sex crimes, citizens of Belarus are also accused of “repeated use of necrotic (sic!) and psychotropic drugs”. In these emails, the attackers claim to be from the DEA — the U.S. Drug Enforcement Administration. Why a U.S. federal agency would be interested in Belarusian citizens remains a mystery.
The scammers failed to realize that the law enforcement body in Belarus is called the “militsya” (militia) rather than “politsya” (police)
Identifying scam emails
As you can see from the examples above, the majority of these scam emails appear highly implausible — and yet they still find victims. That said, with scammers increasingly adopting AI tools, it’s reasonable to expect a significant improvement in both the text quality and design of these fraudulent campaigns. Let’s highlight several indicators that will help you recognize even the most skillfully crafted fakes.
- Personal data. Although it makes scam emails look formal and believable, even if the email features your address, tax ID, phone number, or passport details, it doesn’t mean that the threat is legitimate. In all likelihood, your information was simply sourced from leaked databases and exploited by the scammers. The opposite is also true: impersonal greetings like “Dear Sir/Madam” or “Dear Customer” are undoubtedly also a red flag.
- The sender’s address is registered on a free email service.
- A request to open an attached file, or follow a link to “find out the details”.
- Manipulation, threats, calls for urgent action, and demands not to tell anyone about the email. Attackers deliberately use these psychological tricks to throw you off balance and deprive you of external support.
- Typos and grammatical errors. If you suspect the email is a very poor word-for-word translation from another language, you’re probably right. However, a well-written email is no reason to let your guard down: while scammers are often not the most skilled linguists, they sometimes create exceptionally high-quality spam campaigns.
- Character substitution to bypass spam filters. Attackers mix alphabets, use characters with diacritics such as “Ƙ” instead of “K”, and sometimes simply insert chunks of incoherent text or “noise up” the body with random characters. The text remains readable but often looks odd.
An example of scammers attempting to bypass spam filters by substituting characters and adding meaningless blocks of text
How to protect yourself from email blackmail
- Don’t panic. Scammers deliberately use fear, create a sense of urgency, and rely on your trust in authority. Their goal is for you to believe their fabricated story, but they have no real leverage. If you’re being rushed, threatened, or given ultimatums, make a conscious effort to slow down and avoid making impulsive decisions.
- Install a reliable security solution that will promptly alert you about suspicious emails, malicious files, or links.
- Pay attention to the details. If you receive an email supposedly from a government or law enforcement agency, first examine the sender’s email address. If there’s a reply-to address, compare it with the sender’s. Use search engines to check if the organizations mentioned in the email actually exist, and who manages them. Look up the laws they cite. Pay close attention to signatures and titles — in short, do a full fact-check. Finally, ask yourself if you’re really important enough for, say, the Minister of Internal Affairs to be writing to you personally.
- Use only verified communication channels. Remember that government agencies will never blackmail or threaten you in official correspondence. If you’re still unsure whether the email is real or fake, find the official contact information of the organization mentioned in it, and reach out through an alternative, verified channel — for instance, by phone. Don’t click links or call phone numbers (especially mobile numbers) provided in the email you received — always verify contacts online.
- If you receive an email with a death threat, don’t engage with the scammer, and contact the police immediately. The vast majority of these scare tactics are blatant blackmail, which is a criminal offense in most countries. The key is to remain calm.
Read more on popular scammer tricks:
Kaspersky official blog – Read More