Release Notes: ANY.RUN & ThreatQ Integration, 3,000+ New Rules, and Expanded Detection Coverage
October brought another strong round of updates to ANY.RUN, from a new ThreatQ integration that connects our real-time Threat Intelligence Feeds directly into one of the industry’s leading TIPs, to hundreds of new signatures and rules that sharpen network and behavioral detection.
With 125 new behavior signatures, 17 YARA rules, and 3,264 Suricata rules, analysts can now spot emerging threats faster and with greater precision. Together with the ThreatQ connector, these improvements make it easier for SOCs and MSSPs to enrich alerts, automate response, and gain deeper visibility into live attack activity.
Product Updates
Expanding Threat Intelligence Reach: ANY.RUN & ThreatQ
October brought another major milestone to ANY.RUN’s growing ecosystem; a new integration that links ANY.RUN’s Threat Intelligence Feeds directly with ThreatQ, one of the industry’s leading Threat Intelligence Platforms (TIPs).
This integration helps SOC teams and MSSPs gain real-time visibility into active global threats, cut investigation time, and strengthen detection accuracy across phishing, malware, and network attack surfaces.
Now, analysts using ThreatQ can automatically ingest fresh, high-confidence IOCs gathered from live sandbox investigations of malware samples detonated by 15,000+ organizations and 500,000+ analysts worldwide.
How this update helps security teams:
- Early detection: Indicators are streamed into ThreatQ the moment they appear in ANY.RUN sandbox sessions, helping teams spot threats before they hit endpoints or networks.
- Expanded coverage: Up to 99% unique IOCs from recent phishing and malware attacks provide visibility beyond traditional feeds.
- Faster, smarter response: Each IOC includes a link to its sandbox analysis, giving full behavioral context for rapid validation and containment.
- Lower analyst workload: Feeds are filtered to include only verified malicious indicators, cutting false positives and Tier-1 triage time.
Simple Setup, Instant Impact
The connector works through the STIX/TAXII protocol, ensuring full compatibility with existing ThreatQ environments. Security teams can configure feeds to update hourly, daily, or on a custom schedule; no custom development or infrastructure changes required.
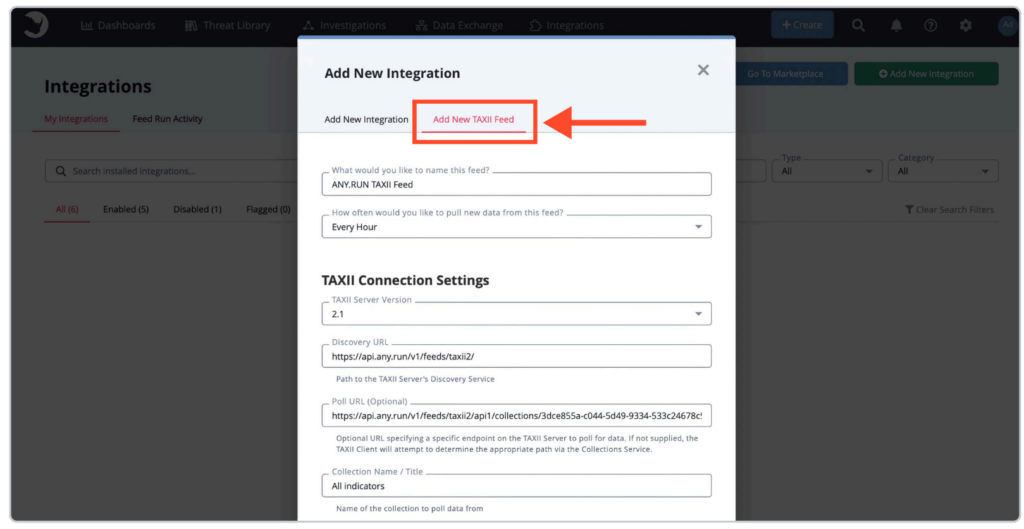
For detailed information, see ANY.RUN’s TAXII connection documentation.
Threat Coverage Update
In October, our team continued to strengthen detection capabilities so SOCs can stay ahead of new and evolving threats:
- 125 new behavior signatures were added to improve coverage across ransomware, loaders, stealers, and RATs, helping analysts detect persistence and payload activity earlier in the attack chain.
- 17 new YARA rules went live in production, expanding visibility into credential-dumping tools, network scanners, and new loader families.
- 3,264 new Suricata rules were deployed, enhancing detection for phishing, APT infrastructure, and evasive network behaviors.
These updates enable analysts to gain faster, more confident verdicts in the sandbox and enrich SIEM, SOAR, and IDS workflows with fresh, actionable IOCs.
New Behavior Signatures
This month’s updates focus on helping analysts catch stealthy activity earlier in the attack chain. The new behavior signatures detect payload downloads, privilege escalation attempts, and persistence mechanisms used by modern ransomware, stealers, and loaders.
We also expanded coverage of mutex detections and legitimate administrative tools often abused by attackers. Together, these improvements provide clearer visibility into real-world execution flow and strengthen automated classification in the sandbox.
Highlighted families and techniques include:
New YARA Rules
In October, we added 17 new YARA rules focused on detecting emerging malware families, credential-dumping utilities, and reconnaissance tools increasingly used in modern attack chains.
These additions strengthen both automated detection and manual hunting, helping analysts identify threats that blend malicious code with legitimate administrative software.
Several new rules were built directly from live samples analyzed in the sandbox, capturing real payloads, shellcode fragments, and memory artifacts tied to loaders, stealers, and botnets. This ensures faster and more reliable classification when scanning new samples or correlating incidents across environments.
Highlighted YARA rules include:
- Maverick: Detection for a recently active loader family observed in targeted phishing campaigns.
- ChaosBot: Identifies obfuscated botnet samples distributing info-stealers via Discord channels.
- Hexa: Flags packed binaries linked to a new modular backdoor variant.
- Pmdump: Detects credential-dumping activity using memory process extraction tools.
- Task Manager DeLuxe: Identifies legitimate system tools often repurposed for lateral movement.
- Network Scanner: Flags reconnaissance utilities used to map internal networks.
- Yapm: Detects process-management tools frequently abused for privilege escalation.
- TaskExplorer: Expands visibility into post-exploitation tool use.
- Ophcrack: Detection of password-recovery tools commonly found in attacker toolkits.
New Suricata Rules
This month, the detection team delivered 3,264 new Suricata rules to improve coverage of phishing activity, APT operations, and evasive web-based malware behavior.
These updates expand network visibility for SOCs and MSSPs, helping analysts detect malicious traffic even when it hides behind trusted services or multi-stage redirects.
Highlighted additions include:
- Tycoon 2FA Domain Chain (sid:85004273, 85004828, 85005024): New heuristic rules based on set of web-resources loaded in specific order by Tycoon client-side code
- Patchwork APT Payload Retrieval via HTTP (sid:85004317): Detects HTTP requests for payload used by Patchwork APT
- Microsoft 365 themed Phishing Attempt (sid:85004831): Identifies mismatch of MS365 authorization URL chain being used on fake websites
About ANY.RUN
ANY.RUN supports more than 15,000 organizations worldwide across industries such as banking, manufacturing, telecom, healthcare, and technology, helping them build faster, smarter, and more resilient cybersecurity operations.
Our cloud-based interactive sandbox enables teams to safely analyze threats targeting Windows, Linux, and Android systems in real time. Analysts can observe every system and network action, interact with running samples, and extract IOCs in under 40 seconds; all without complex infrastructure setup.
Combined with Threat Intelligence Lookup and Threat Intelligence Feeds, ANY.RUN helps SOCs accelerate investigations, reduce noise, and improve detection accuracy. Teams can easily integrate these capabilities into SIEM and SOAR systems to automate enrichment and streamline response.
Ready to see it in action?
Start your 14-day trial of ANY.RUN
The post Release Notes: ANY.RUN & ThreatQ Integration, 3,000+ New Rules, and Expanded Detection Coverage appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
